| File name: | dllhost.exe |
| Full analysis: | https://app.any.run/tasks/f1f58621-6f9b-45f5-ad79-31f8d2713d28 |
| Verdict: | Malicious activity |
| Analysis date: | June 16, 2024, 23:58:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows |
| MD5: | 10BD1E52C6A74E9203EB863F04B8B416 |
| SHA1: | 1885184B7EC5752873D5F683143EA13FB09355FD |
| SHA256: | 86E1911205E5A8D56B1A60FD418A9D665B7D50C8D3834DF8452AD80F5642E777 |
| SSDEEP: | 98304:8Da+YU6tpoxJJh3xsfmkGe7FEgsXXfajZYuU96A8qDkGa458UVfAzkcYCl2dd0Yu:v2Amuw |
MALICIOUS
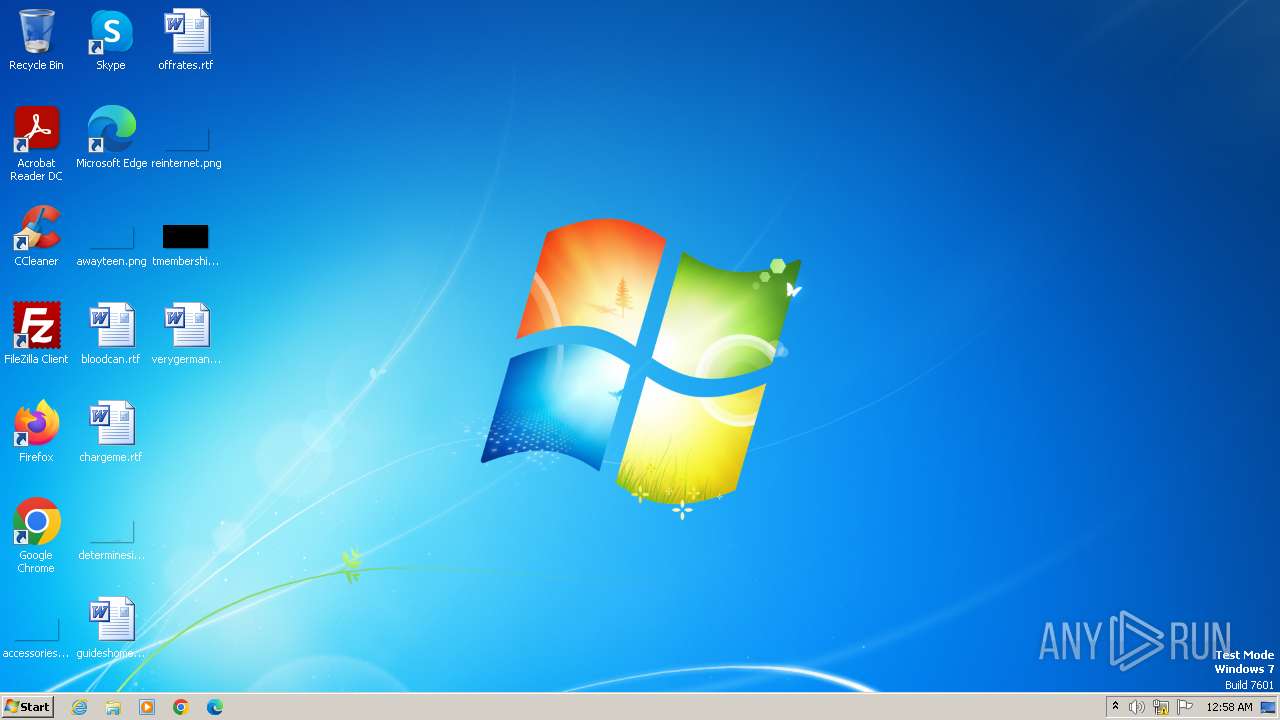
Drops the executable file immediately after the start
- dllhost.exe (PID: 3956)
SUSPICIOUS
Process drops legitimate windows executable
- dllhost.exe (PID: 3956)
Reads the Internet Settings
- dllhost.exe (PID: 3956)
- dllhost.exe (PID: 4016)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 3956)
Executable content was dropped or overwritten
- dllhost.exe (PID: 3956)
The process creates files with name similar to system file names
- dllhost.exe (PID: 3956)
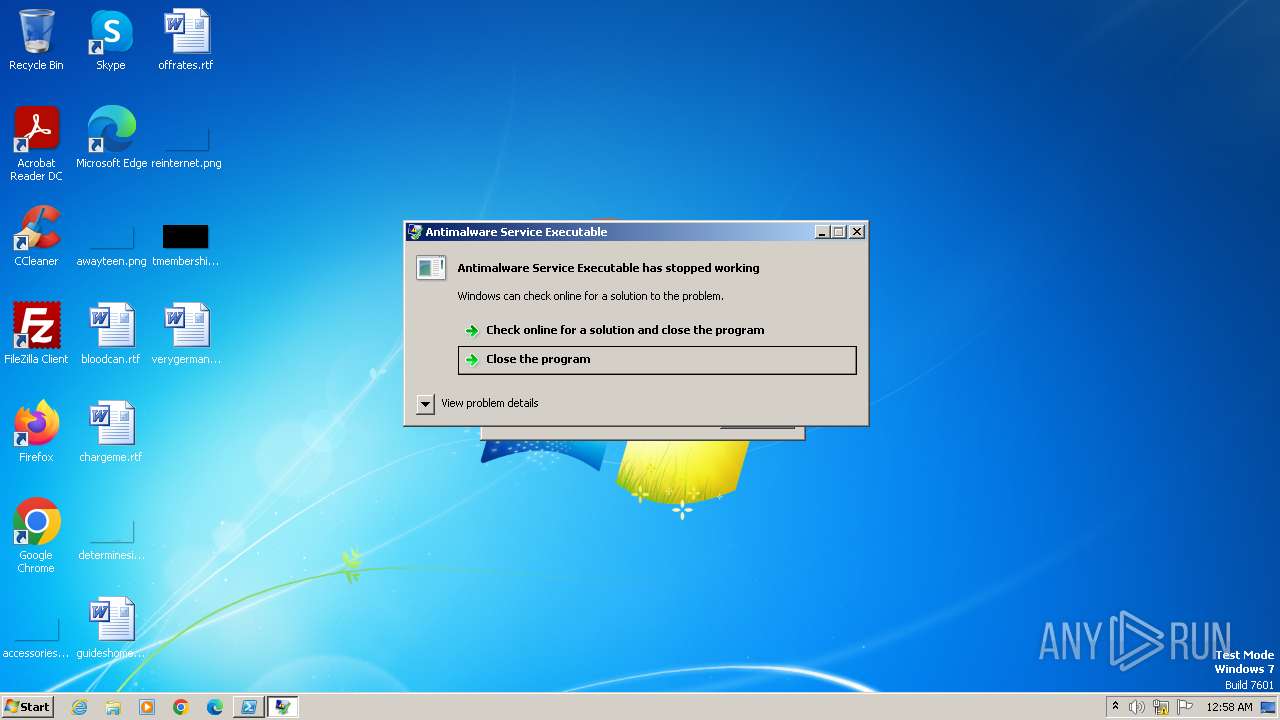
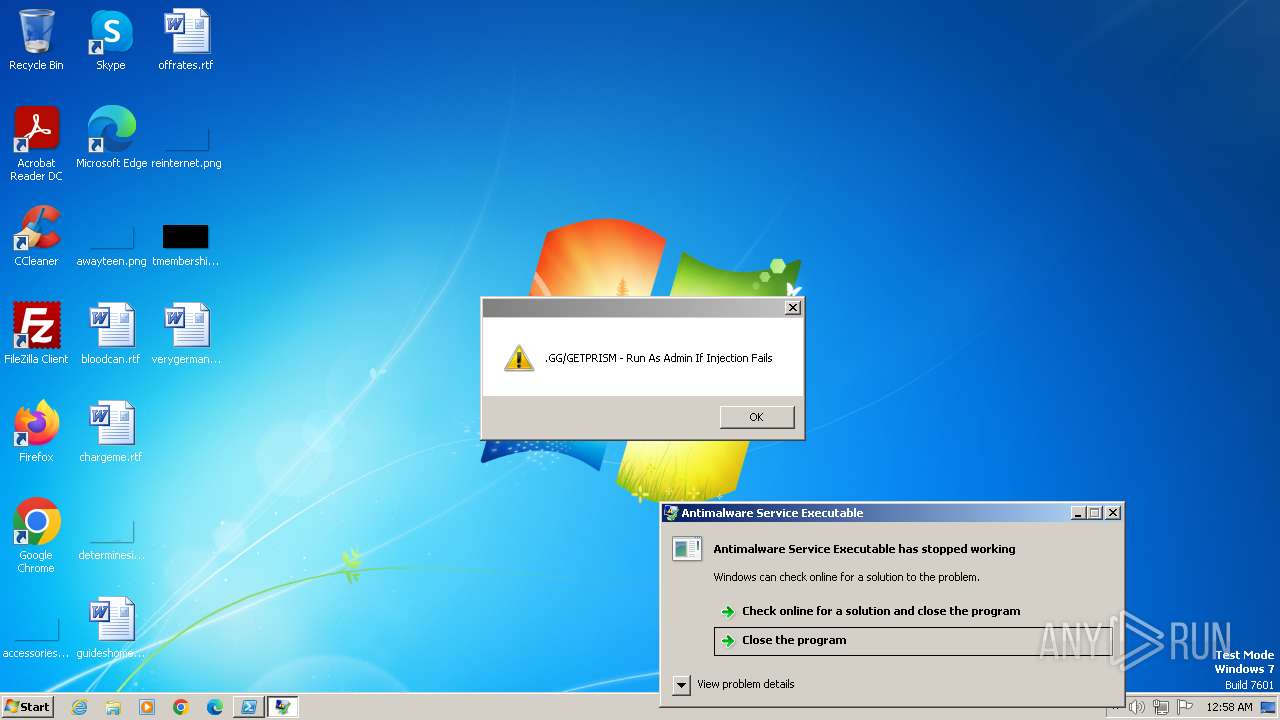
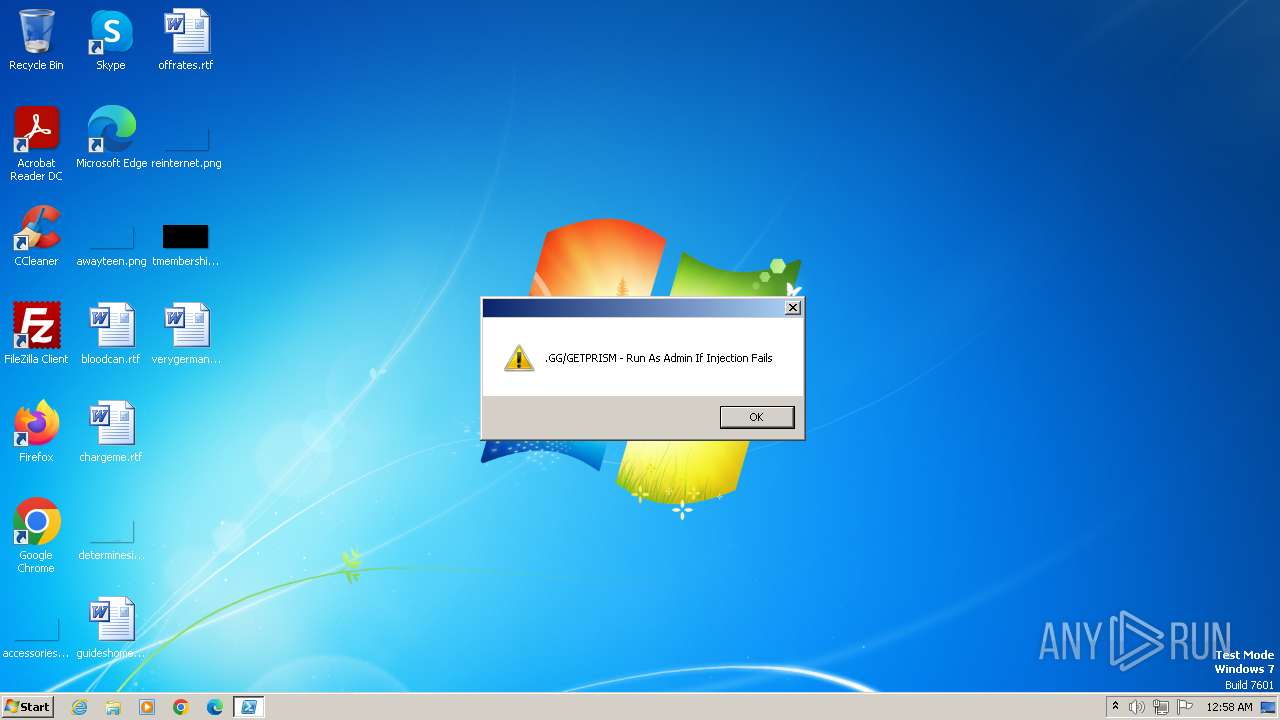
Starts POWERSHELL.EXE for commands execution
- dllhost.exe (PID: 3956)
BASE64 encoded PowerShell command has been detected
- dllhost.exe (PID: 3956)
Base64-obfuscated command line is found
- dllhost.exe (PID: 3956)
Checks for external IP
- dllhost.exe (PID: 4016)
INFO
Checks supported languages
- dllhost.exe (PID: 3956)
- dllhost.exe (PID: 4016)
- wmpnscfg.exe (PID: 2312)
Reads the computer name
- dllhost.exe (PID: 3956)
- dllhost.exe (PID: 4016)
- wmpnscfg.exe (PID: 2312)
Creates files or folders in the user directory
- dllhost.exe (PID: 3956)
Reads the machine GUID from the registry
- dllhost.exe (PID: 4016)
Reads Environment values
- dllhost.exe (PID: 4016)
Manual execution by a user
- wmpnscfg.exe (PID: 2312)
- explorer.exe (PID: 1056)
- notepad++.exe (PID: 2268)
Disables trace logs
- dllhost.exe (PID: 4016)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (61.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.6) |
| .exe | | | Win32 Executable (generic) (10) |
| .exe | | | Win16/32 Executable Delphi generic (4.6) |
| .exe | | | Generic Win/DOS Executable (4.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 0000:00:00 00:00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 2048 |
| InitializedDataSize: | 5299712 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x14d1 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
43
Monitored processes
6
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1056 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2268 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\dllhost.exe" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 2312 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3956 | "C:\Users\admin\AppData\Local\Temp\dllhost.exe" | C:\Users\admin\AppData\Local\Temp\dllhost.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3988 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -EncodedCommand "PAAjAGYAZABoACMAPgBBAGQAZAAtAFQAeQBwAGUAIAAtAEEAcwBzAGUAbQBiAGwAeQBOAGEAbQBlACAAUwB5AHMAdABlAG0ALgBXAGkAbgBkAG8AdwBzAC4ARgBvAHIAbQBzADsAPAAjAGsAYQB0ACMAPgBbAFMAeQBzAHQAZQBtAC4AVwBpAG4AZABvAHcAcwAuAEYAbwByAG0AcwAuAE0AZQBzAHMAYQBnAGUAQgBvAHgAXQA6ADoAUwBoAG8AdwAoACcALgBHAEcALwBHAEUAVABQAFIASQBTAE0AIAAtACAAUgB1AG4AIABBAHMAIABBAGQAbQBpAG4AIABJAGYAIABJAG4AagBlAGMAdABpAG8AbgAgAEYAYQBpAGwAcwAnACwAJwAnACwAJwBPAEsAJwAsACcAVwBhAHIAbgBpAG4AZwAnACkAPAAjAGYAcgBzACMAPgA=" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | dllhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 4016 | "C:\Users\admin\dllhost.exe" | C:\Users\admin\dllhost.exe | dllhost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Antimalware Service Executable Exit code: 2148734499 Version: 4.18.2104.5 Modules
| |||||||||||||||
Total events
6 341
Read events
6 291
Write events
50
Delete events
0
Modification events
| (PID) Process: | (3956) dllhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3956) dllhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3956) dllhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3956) dllhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (4016) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\dllhost_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4016) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\dllhost_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (4016) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\dllhost_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (4016) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\dllhost_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (4016) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\dllhost_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (4016) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\dllhost_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
Executable files
2
Suspicious files
3
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2268 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\session.xml | text | |
MD5:1ACF67FD8E9505408C30D8981DEE0BF1 | SHA256:D44A46DE52B853F2A30FCDBF9CAB6331D903F99FD552719B20086D9D1FC2B4DB | |||
| 3988 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
| 3988 | powershell.exe | C:\Users\admin\AppData\Local\Temp\w55cdlzs.zol.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2268 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\config.xml | xml | |
MD5:75DAF0C838CA0F9DAA89D4074A504E1B | SHA256:97901B6DEF410AA997B0E91A0FD0947EB3A26B7D5C83FD7228FDE04F981AC53C | |||
| 3956 | dllhost.exe | C:\Users\admin\AppData\Roaming\nexusloader.exe | executable | |
MD5:F8055956A195DE1C8F07D7999354AEBC | SHA256:4005D1F5489D023DA6F099A65281E292AB97A1B2AC1BB8A55B74FE7E5046EDDF | |||
| 3988 | powershell.exe | C:\Users\admin\AppData\Local\Temp\llgjbk3d.l0d.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3956 | dllhost.exe | C:\Users\admin\dllhost.exe | executable | |
MD5:4A7F75343AAA5A4D8D18ADD50CCF3139 | SHA256:34BE6A934FD45752E788F9BA20943C8E52D91732D76E9F30A5176E98DCCD956E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
5
DNS requests
1
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4016 | dllhost.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4016 | dllhost.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ip-api.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4016 | dllhost.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
4016 | dllhost.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
Process | Message |
|---|---|
dllhost.exe | CLR: Managed code called FailFast without specifying a reason.
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|