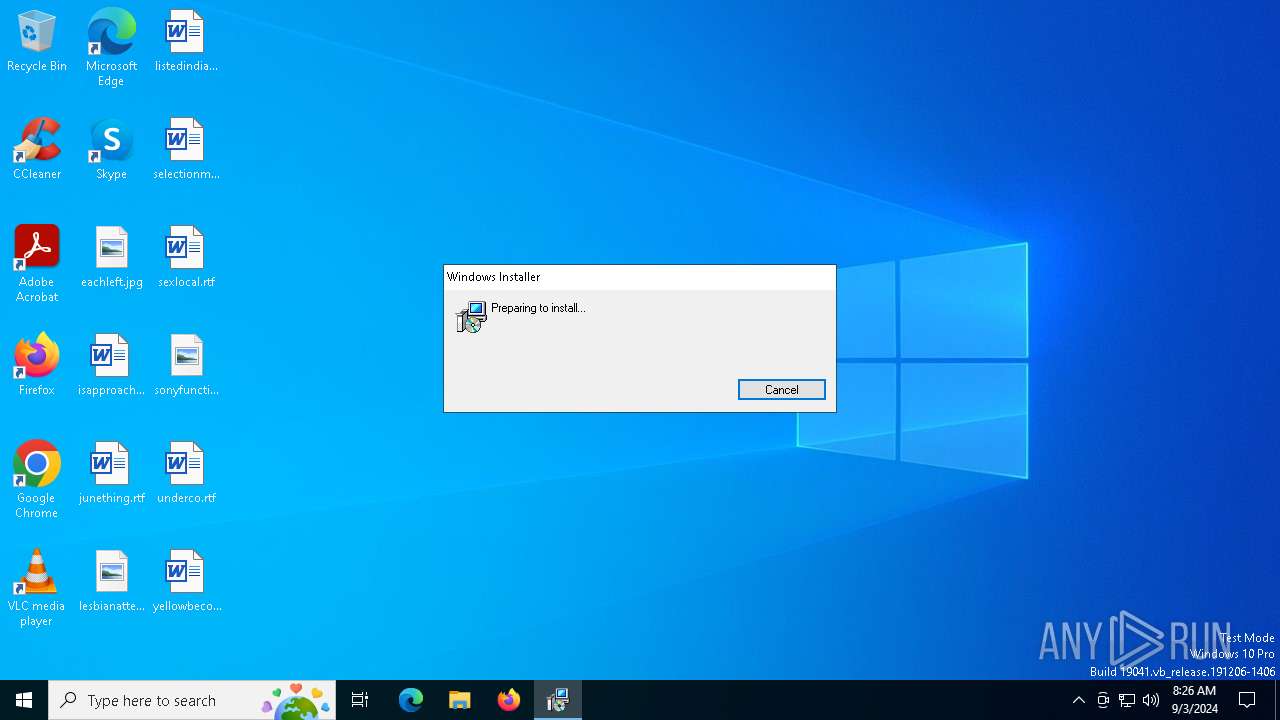
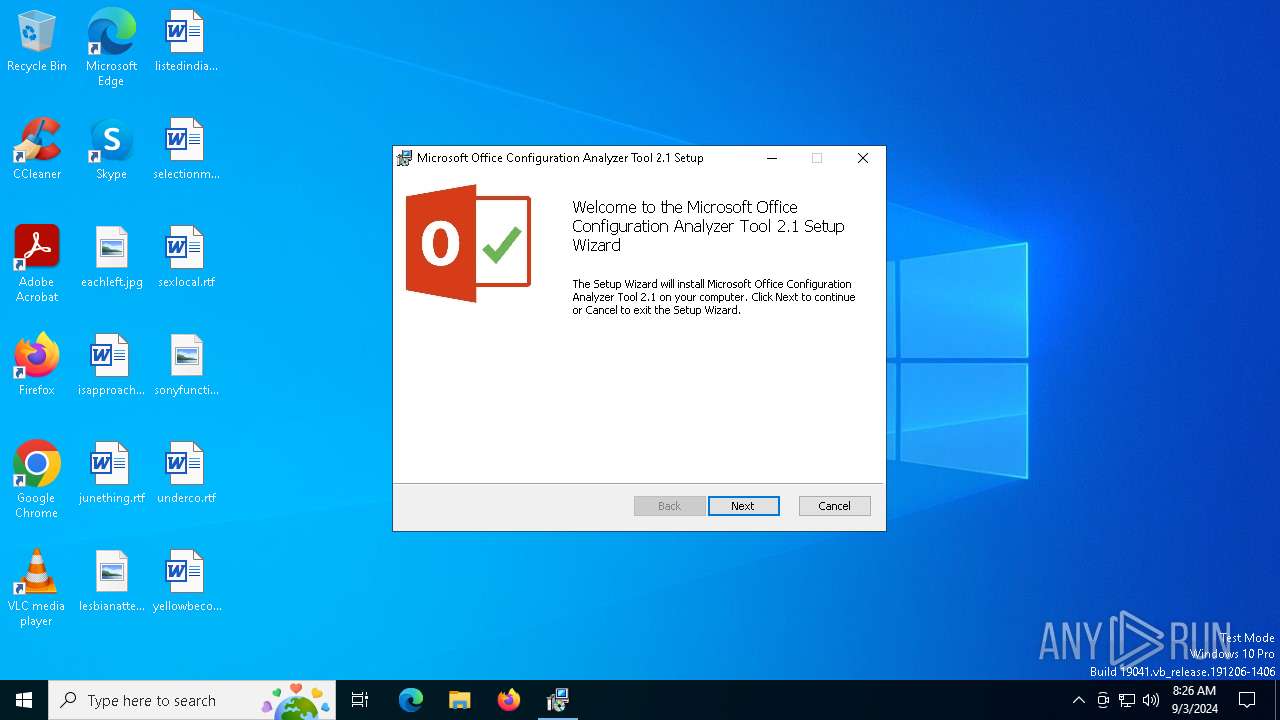
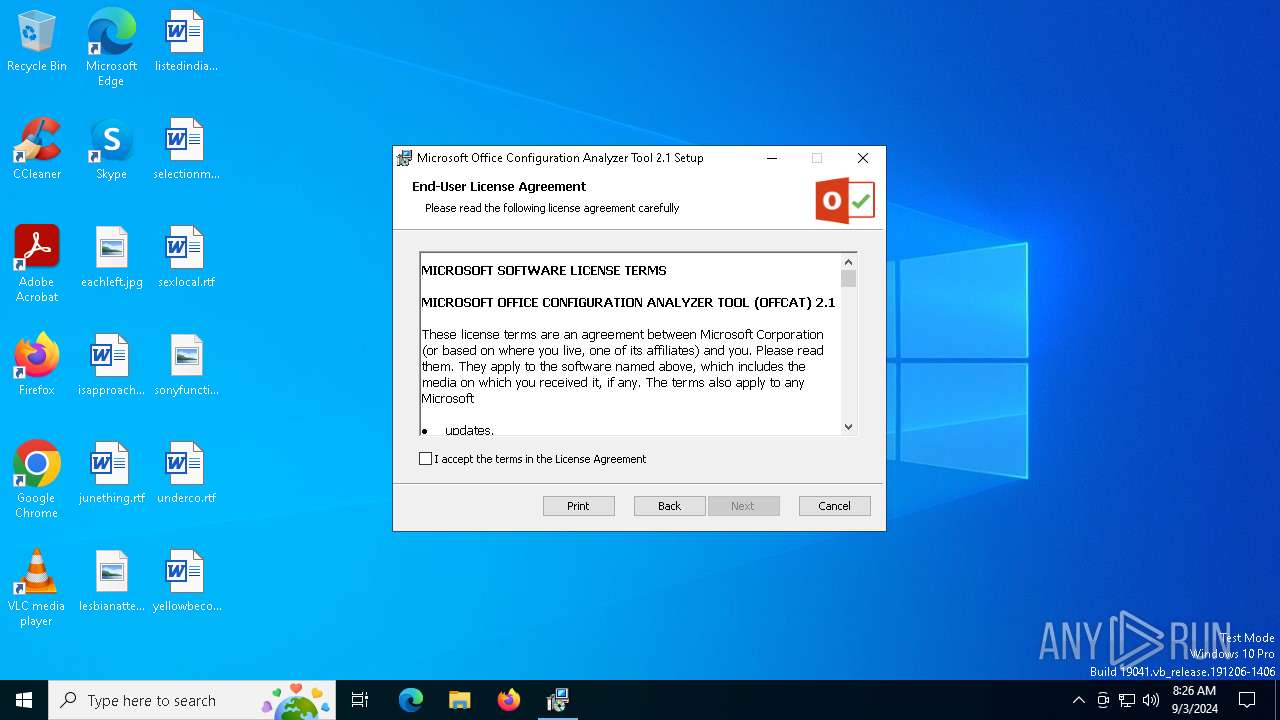
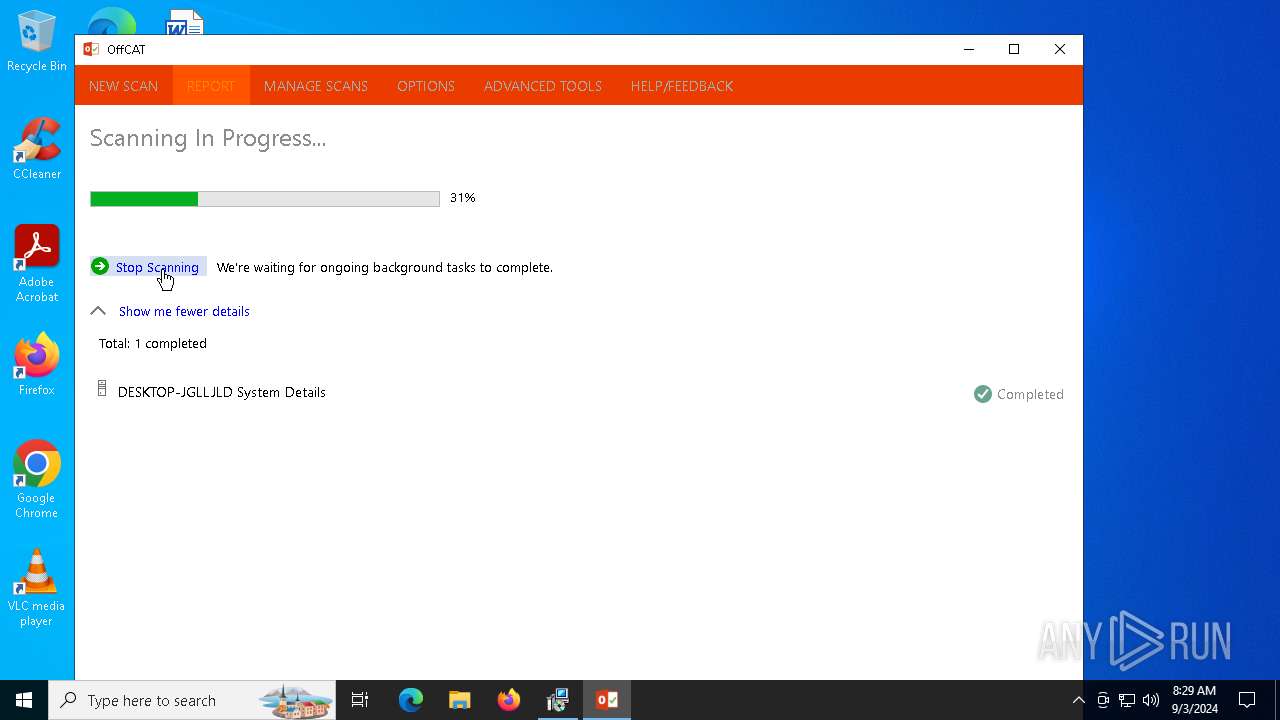
| File name: | OffCAT.msi |
| Full analysis: | https://app.any.run/tasks/2e0d5aa3-d615-4638-b796-d826d2c7d09b |
| Verdict: | Malicious activity |
| Analysis date: | September 03, 2024, 08:26:14 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Installation Database, Subject: Installs the Microsoft Office Configuration Analyzer Tool (OffCAT), Author: Microsoft Corporation, Keywords: Installer, Comments: This installer database contains the logic and data required to install Microsoft Office Configuration Analyzer Tool 2.1., Template: Intel;1033, Revision Number: {E7EFF1F2-E832-4F3B-8FC8-B2E0F1515BE9}, Create Time/Date: Thu Jan 28 16:45:12 2016, Last Saved Time/Date: Thu Jan 28 16:45:12 2016, Number of Pages: 200, Number of Words: 10, Name of Creating Application: Windows Installer XML Toolset (3.9.1208.0), Security: 2 |
| MD5: | 208D4F5A5839134AEEF2E1F77C6E1604 |
| SHA1: | A8006A822705020FEDF99334F1F31D660A07CCF2 |
| SHA256: | 86DFAAF74A70753D160E699AA9B3581EC194C81F0E11C4239CEA01231030B6E7 |
| SSDEEP: | 98304:yl0b+A2rMXP620/YypYGuX9TUQAeRKwMQSuqlt2VQ7IRDWV1fxjioy+b+qNHwrna:+N+OZmvNQ6VPysbsCj0GKWr5mYsFa |
MALICIOUS
Changes the autorun value in the registry
- msiexec.exe (PID: 3104)
Uses sleep, probably for evasion detection (SCRIPT)
- cscript.exe (PID: 6596)
SUSPICIOUS
Process drops legitimate windows executable
- msiexec.exe (PID: 6304)
- msiexec.exe (PID: 3104)
Checks Windows Trust Settings
- msiexec.exe (PID: 3104)
Executes as Windows Service
- VSSVC.exe (PID: 6020)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 3104)
Executable content was dropped or overwritten
- rundll32.exe (PID: 1776)
- rundll32.exe (PID: 5656)
- rundll32.exe (PID: 2080)
- rundll32.exe (PID: 6616)
The process creates files with name similar to system file names
- msiexec.exe (PID: 3104)
Searches for installed software
- rundll32.exe (PID: 1776)
Reads security settings of Internet Explorer
- OffCAT.exe (PID: 740)
Creates/Modifies COM task schedule object
- rundll32.exe (PID: 5656)
Reads the date of Windows installation
- OffCAT.exe (PID: 740)
Reads Internet Explorer settings
- OffCAT.exe (PID: 740)
The process executes VB scripts
- OffCAT.exe (PID: 740)
- cscript.exe (PID: 448)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 448)
- cscript.exe (PID: 5288)
- cscript.exe (PID: 6596)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 448)
Writes binary data to a Stream object (SCRIPT)
- cscript.exe (PID: 448)
Application launched itself
- cscript.exe (PID: 448)
Runs shell command (SCRIPT)
- cscript.exe (PID: 448)
Starts CMD.EXE for commands execution
- OffCAT.exe (PID: 740)
Using 'findstr.exe' to search for text patterns in files and output
- OffCAT.exe (PID: 740)
INFO
Creates files or folders in the user directory
- msiexec.exe (PID: 6304)
- OffCAT_RTS.exe (PID: 6344)
- OffCAT.exe (PID: 740)
- dxdiag.exe (PID: 6384)
- msiexec.exe (PID: 3104)
Checks proxy server information
- msiexec.exe (PID: 6304)
- OffCAT_RTS.exe (PID: 6344)
- OffCAT.exe (PID: 740)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 6304)
- rundll32.exe (PID: 6616)
- cscript.exe (PID: 448)
- dxdiag.exe (PID: 6384)
- cscript.exe (PID: 5288)
- cscript.exe (PID: 6596)
Checks supported languages
- msiexec.exe (PID: 6952)
- msiexec.exe (PID: 3104)
- msiexec.exe (PID: 1448)
- OffCAT.exe (PID: 740)
- OffCAT_RTS.exe (PID: 6344)
Create files in a temporary directory
- msiexec.exe (PID: 6952)
- rundll32.exe (PID: 1776)
- msiexec.exe (PID: 1448)
- rundll32.exe (PID: 6616)
- rundll32.exe (PID: 2080)
- OffCAT_RTS.exe (PID: 6344)
- cscript.exe (PID: 448)
- OffCAT.exe (PID: 740)
- dxdiag.exe (PID: 6384)
- rundll32.exe (PID: 5656)
Reads the computer name
- msiexec.exe (PID: 6952)
- msiexec.exe (PID: 3104)
- msiexec.exe (PID: 1448)
- OffCAT.exe (PID: 740)
- OffCAT_RTS.exe (PID: 6344)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6304)
- msiexec.exe (PID: 3104)
Reads the machine GUID from the registry
- msiexec.exe (PID: 3104)
- OffCAT.exe (PID: 740)
- OffCAT_RTS.exe (PID: 6344)
Reads the software policy settings
- msiexec.exe (PID: 6304)
- msiexec.exe (PID: 3104)
- OffCAT_RTS.exe (PID: 6344)
- OffCAT.exe (PID: 740)
- dxdiag.exe (PID: 6384)
Reads Microsoft Office registry keys
- msiexec.exe (PID: 3104)
- rundll32.exe (PID: 2080)
- OffCAT.exe (PID: 740)
Creates a software uninstall entry
- msiexec.exe (PID: 3104)
The process uses the downloaded file
- rundll32.exe (PID: 6616)
- OffCAT.exe (PID: 740)
- cscript.exe (PID: 448)
Process checks computer location settings
- OffCAT.exe (PID: 740)
Creates files in the program directory
- OffCAT.exe (PID: 740)
Reads Windows Product ID
- OffCAT.exe (PID: 740)
Reads Environment values
- OffCAT_RTS.exe (PID: 6344)
- OffCAT.exe (PID: 740)
Disables trace logs
- OffCAT_RTS.exe (PID: 6344)
- OffCAT.exe (PID: 740)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (93.3) |
|---|---|---|
| .pps/ppt | | | Microsoft PowerPoint document (5.2) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | Installs the Microsoft Office Configuration Analyzer Tool (OffCAT) |
| Author: | Microsoft Corporation |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install Microsoft Office Configuration Analyzer Tool 2.1. |
| Template: | Intel;1033 |
| RevisionNumber: | {E7EFF1F2-E832-4F3B-8FC8-B2E0F1515BE9} |
| CreateDate: | 2016:01:28 16:45:12 |
| ModifyDate: | 2016:01:28 16:45:12 |
| Pages: | 200 |
| Words: | 10 |
| Software: | Windows Installer XML Toolset (3.9.1208.0) |
| Security: | Read-only recommended |
Total processes
157
Monitored processes
30
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 448 | C:\WINDOWS\system32\cscript.exe "C:\Users\admin\AppData\Local\Temp\offcatscript_6c5ea79518df48cf8ae5576ba2f5eabe.vbs" //E:VBS //Nologo | C:\Windows\System32\cscript.exe | — | OffCAT.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 740 | "C:\Users\admin\AppData\Local\Microsoft\OffCAT\Offcat.exe" | C:\Users\admin\AppData\Local\Microsoft\OffCAT\OffCAT.exe | rundll32.exe | ||||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Description: Microsoft Office Configuration Analyzer Exit code: 0 Version: 2.1.6002.0128 Modules
| |||||||||||||||
| 1224 | cmd.exe /c echo %USERPROFILE%\Desktop | C:\Windows\System32\cmd.exe | — | OffCAT.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1436 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | findstr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1448 | C:\Windows\syswow64\MsiExec.exe -Embedding 6EE15385DC736AA62255B75D154B08F3 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1492 | C:\WINDOWS\system32\findstr.exe /r /i /c:"^[^\#]*autodiscover\.outlook\.com" C:\WINDOWS\system32\drivers\etc\hosts | C:\Windows\System32\findstr.exe | — | OffCAT.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1776 | rundll32.exe "C:\WINDOWS\Installer\MSI1BAB.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1252281 14 WixInstaller!WixInstaller.CustomActions.UninstallOffCAT12 | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2080 | rundll32.exe "C:\WINDOWS\Installer\MSI27B4.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1255359 22 WixInstaller!WixInstaller.CustomActions.SetResiliencyKeys | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3104 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3208 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
46 369
Read events
45 724
Write events
604
Delete events
41
Modification events
| (PID) Process: | (3104) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000FC09F100DBFDDA01200C000014180000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3104) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000FC09F100DBFDDA01200C000014180000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3104) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000446C3101DBFDDA01200C000014180000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3104) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000446C3101DBFDDA01200C000014180000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3104) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 480000000000000013D03301DBFDDA01200C000014180000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3104) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 480000000000000061973801DBFDDA01200C000014180000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3104) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (3104) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000C2D0AF01DBFDDA01200C000014180000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3104) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000009E33B201DBFDDA01200C000008080000E80300000100000000000000000000001DDBD0744E77744090B836D17F60433E00000000000000000000000000000000 | |||
| (PID) Process: | (6020) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000004A14BE01DBFDDA0184170000340A0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
46
Suspicious files
29
Text files
74
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3104 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 3104 | msiexec.exe | C:\Windows\Installer\1318bb.msi | — | |
MD5:— | SHA256:— | |||
| 3104 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{74d0db1d-774e-4074-90b8-36d17f60433e}_OnDiskSnapshotProp | binary | |
MD5:0B7F74D79A8701DA52E5AD1AC1CDBCF7 | SHA256:A11BE3FD322D2DF13D017400BBCCD4FEB20A4D1576E3C8A75CBD35E1E499B6B5 | |||
| 6952 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\CFGA64A.tmp | xml | |
MD5:84F2F872035A2B2007494208AC3B98C4 | SHA256:F5BA88B4A9928B710C9DBF757F0C4DEE5BC6B6A56985D5BFEBA8620C8AE65B6C | |||
| 3104 | msiexec.exe | C:\Windows\Installer\MSI1BAB.tmp | executable | |
MD5:BF28767C06A163F22E2A2954580268D0 | SHA256:93439BB1740255E6C0FB50A45E0D4253B453181C5636910FB51D4500297886D5 | |||
| 6304 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIA6A9.tmp | executable | |
MD5:DD2FED15306CBB7F32245077364A8FE1 | SHA256:1274CCA896F0FD797B330E5EA4605A080DA505B7E14FFBBF4181B61AC998C649 | |||
| 6304 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIA58F.tmp | executable | |
MD5:DD2FED15306CBB7F32245077364A8FE1 | SHA256:1274CCA896F0FD797B330E5EA4605A080DA505B7E14FFBBF4181B61AC998C649 | |||
| 1448 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\CFG1ABF.tmp | xml | |
MD5:84F2F872035A2B2007494208AC3B98C4 | SHA256:F5BA88B4A9928B710C9DBF757F0C4DEE5BC6B6A56985D5BFEBA8620C8AE65B6C | |||
| 3104 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:0B7F74D79A8701DA52E5AD1AC1CDBCF7 | SHA256:A11BE3FD322D2DF13D017400BBCCD4FEB20A4D1576E3C8A75CBD35E1E499B6B5 | |||
| 1776 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSI1BAB.tmp-\CustomAction.config | xml | |
MD5:1322E3C95294FF07B2409F3975131C5D | SHA256:FB109B8991A9878C19B6424E317165AF2812B8ED67645433DE7018DD79517DA7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
50
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6108 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7088 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7088 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6344 | OffCAT_RTS.exe | GET | 301 | 23.52.120.96:80 | http://www.microsoft.com/office/offcat/2.5/en/offcat.config.xml | unknown | — | — | whitelisted |
6344 | OffCAT_RTS.exe | GET | 301 | 23.52.120.96:80 | http://www.microsoft.com/office/offcat/2.5/en/offcat.config.xml | unknown | — | — | whitelisted |
6344 | OffCAT_RTS.exe | GET | 301 | 23.52.120.96:80 | http://www.microsoft.com/office/offcat/2.5/en/offcat.config.xml | unknown | — | — | whitelisted |
6344 | OffCAT_RTS.exe | GET | 301 | 23.52.120.96:80 | http://www.microsoft.com/office/offcat/2.5/en/offcat.config.xml | unknown | — | — | whitelisted |
6344 | OffCAT_RTS.exe | GET | 301 | 23.52.120.96:80 | http://www.microsoft.com/office/offcat/2.5/en/offcat.config.xml | unknown | — | — | whitelisted |
6344 | OffCAT_RTS.exe | GET | 301 | 23.52.120.96:80 | http://www.microsoft.com/office/offcat/2.5/en/offcat.config.xml | unknown | — | — | whitelisted |
6344 | OffCAT_RTS.exe | GET | 301 | 23.52.120.96:80 | http://www.microsoft.com/office/offcat/2.5/en/offcat.config.xml | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4316 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6304 | msiexec.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6108 | svchost.exe | 40.126.31.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6108 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
7088 | SIHClient.exe | 40.68.123.157:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7088 | SIHClient.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
support.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
OffCAT.exe | RTSUtility: RTSMode = 0
|
OffCAT_RTS.exe | RTSUtility: RTSMode = 0
|
OffCAT_RTS.exe | /////////////////////////////////////////////////////////////
|
OffCAT_RTS.exe | /////////////////////////////////////////////////////////////
|
OffCAT_RTS.exe | RTS Process (6344) Started at 9/3/2024 8:27:02 AM
|
OffCAT_RTS.exe | CrashDetectionService: Starting EventLogWatcher with *[System[(EventID = 1000) and (Provider/@Name = 'Application Error')]]
|
OffCAT.exe | Writing telemetry values for path = UserAction/OptionChanged
DataDirectory = ********
|
OffCAT_RTS.exe | Writing telemetry values for path = RtsDownloadFile
url = http://www.microsoft.com/office/offcat/2.5/en/offcat.config.xml
|
OffCAT_RTS.exe | Writing telemetry values for path = UserAction/Startup/RTS
|
OffCAT.exe | Writing telemetry values for path = UserAction/Startup/OffCAT
|