| File name: | VMware Central Control V1.exe |
| Full analysis: | https://app.any.run/tasks/a34a7e6f-7945-4eec-9550-adec4b8a6192 |
| Verdict: | Malicious activity |
| Analysis date: | January 17, 2025, 14:21:07 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 12 sections |
| MD5: | E1C5C76BF4312317EBB3237650123990 |
| SHA1: | 9C668D395E235935B08B8A50C663A9A43EAF083D |
| SHA256: | 86D22B749B1947DA684FBA42B16EFACEA8152DEBBE64B39C7265C845DD85CC8B |
| SSDEEP: | 98304:ntWGKhcqj1BX+G/nWFJVUGGc2tdo34zQHxHOX/i4rS9KfgSFqu567Wfd8PDLw+Bg:IaJTWeu5pkm |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the BIOS version
- VMware Central Control V1.exe (PID: 6856)
INFO
Process checks whether UAC notifications are on
- VMware Central Control V1.exe (PID: 6856)
The sample compiled with english language support
- VMware Central Control V1.exe (PID: 6856)
Checks supported languages
- VMware Central Control V1.exe (PID: 6856)
Reads the computer name
- VMware Central Control V1.exe (PID: 6856)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:07:28 09:03:51+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 1015808 |
| InitializedDataSize: | 1404928 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x130f0b0 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Special build |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
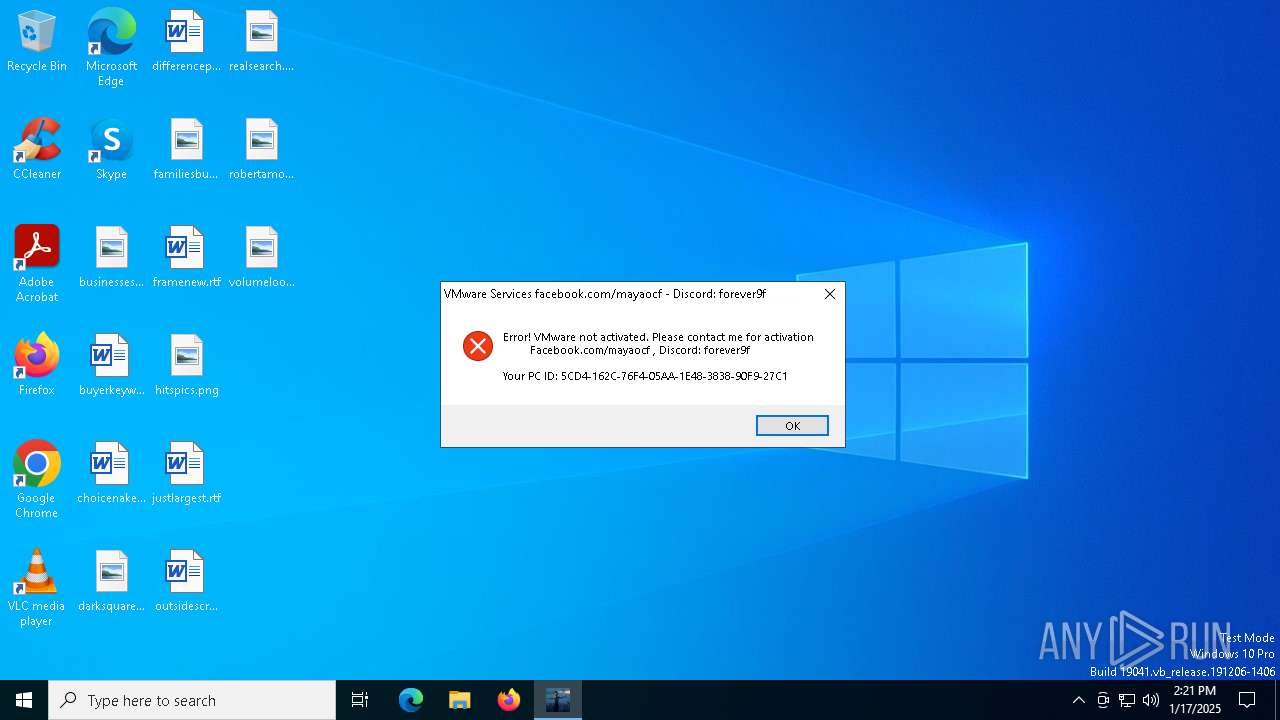
| CompanyName: | Facebook.com/mayaocf |
| FileDescription: | VMware Services 2024 |
| FileVersion: | Discord: forever9f |
| InternalName: | Facebook.com/mayaocf |
| LegalCopyright: | Facebook.com/mayaocf |
| LegalTrademarks: | Facebook.com/mayaocf |
| OriginalFileName: | Discord: forever9f |
| ProductName: | Facebook.com/mayaocf |
| ProductVersion: | Discord: forever9f |
| Comments: | Facebook.com/mayaocf |
Total processes
128
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 5300 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6668 | "C:\Users\admin\AppData\Local\Temp\VMware Central Control V1.exe" | C:\Users\admin\AppData\Local\Temp\VMware Central Control V1.exe | — | explorer.exe | |||||||||||
User: admin Company: Facebook.com/mayaocf Integrity Level: MEDIUM Description: VMware Services 2024 Exit code: 3221226540 Version: Discord: forever9f Modules
| |||||||||||||||
| 6856 | "C:\Users\admin\AppData\Local\Temp\VMware Central Control V1.exe" | C:\Users\admin\AppData\Local\Temp\VMware Central Control V1.exe | explorer.exe | ||||||||||||
User: admin Company: Facebook.com/mayaocf Integrity Level: HIGH Description: VMware Services 2024 Exit code: 0 Version: Discord: forever9f Modules
| |||||||||||||||
Total events
90
Read events
88
Write events
2
Delete events
0
Modification events
| (PID) Process: | (6856) VMware Central Control V1.exe | Key: | HKEY_CLASSES_ROOT\CompressedFolder\CLSID |
| Operation: | write | Name: | Compression Type (saxn9640t) |
Value: D05C641DDAE6A76F8D01E974 | |||
| (PID) Process: | (6856) VMware Central Control V1.exe | Key: | HKEY_CLASSES_ROOT\WOW6432Node\CLSID\{dd531996-bd01-5ab6-20be-5db01769} |
| Operation: | write | Name: | ProdID |
Value: 0F328F722951DAD42EEB076A | |||
Executable files
0
Suspicious files
3
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6856 | VMware Central Control V1.exe | C:\ProgramData\mntemp | binary | |
MD5:6317846692E2D44C394B0CE47F18855E | SHA256:FC4CA11B05D44977275FA55EA6ABF2D23E90E637FDA9182AC8B464EB9720EDBC | |||
| 6856 | VMware Central Control V1.exe | C:\ProgramData\knqttvli.pla | binary | |
MD5:09AF21ED02D8791094CA310F47CBA899 | SHA256:E2E8473CC53E69CCCE80CB4A7CDB2DDFE07398334FE9FA4678E741640F979047 | |||
| 6856 | VMware Central Control V1.exe | C:\ProgramData\oljusaxn.tps | binary | |
MD5:FB2C4A5FC779405327B2831EE505CC35 | SHA256:B8D2E6791199AC0D0FF951EE0CB923486196F4A114579F489CB008AAA7A0C0F0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
33
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.209.214.100:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.209.214.100:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6524 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5392 | SIHClient.exe | GET | 200 | 23.209.214.100:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5392 | SIHClient.exe | GET | 200 | 23.209.214.100:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | unknown |
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | unknown |
4712 | MoUsoCoreWorker.exe | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | unknown |
4712 | MoUsoCoreWorker.exe | 23.209.214.100:80 | www.microsoft.com | PT. Telekomunikasi Selular | ID | whitelisted |
— | — | 23.209.214.100:80 | www.microsoft.com | PT. Telekomunikasi Selular | ID | whitelisted |
5064 | SearchApp.exe | 2.19.122.26:443 | www.bing.com | Akamai International B.V. | DE | unknown |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4536 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| unknown |
www.microsoft.com |
| unknown |
google.com |
| unknown |
www.bing.com |
| unknown |
ocsp.digicert.com |
| unknown |
login.live.com |
| unknown |
go.microsoft.com |
| unknown |
settings-win.data.microsoft.com |
| unknown |
arc.msn.com |
| unknown |
fd.api.iris.microsoft.com |
| unknown |