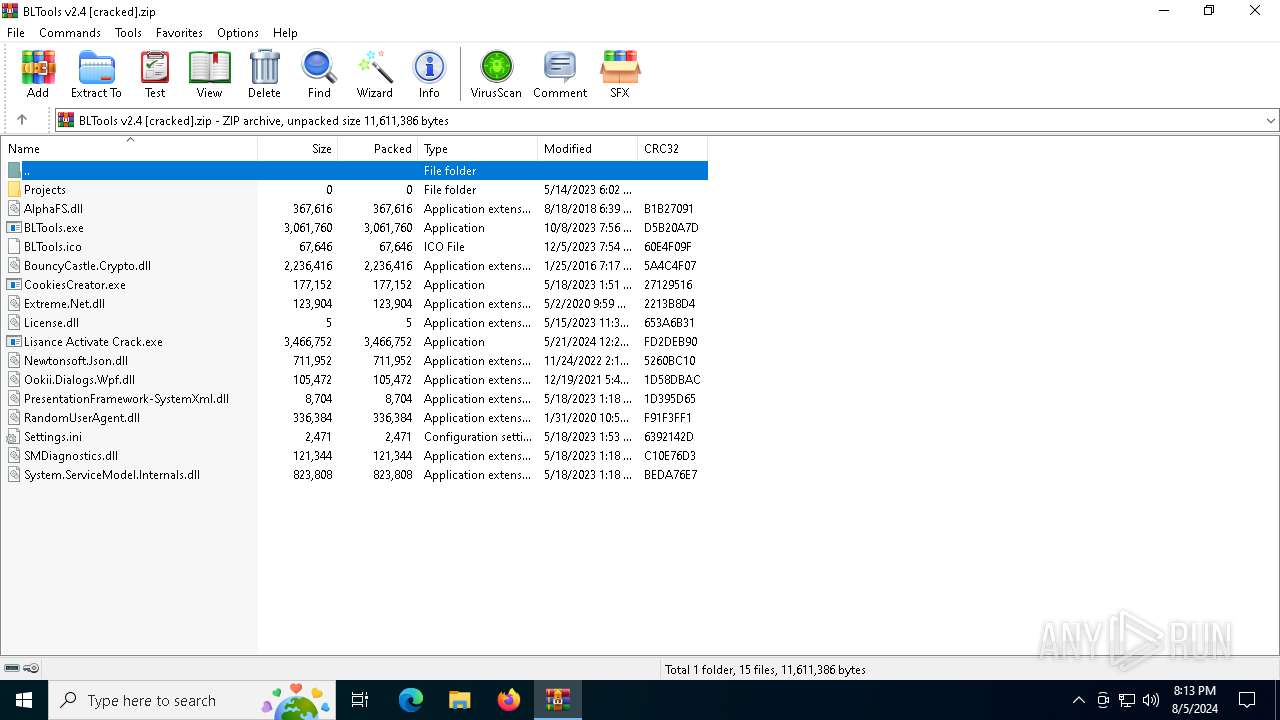
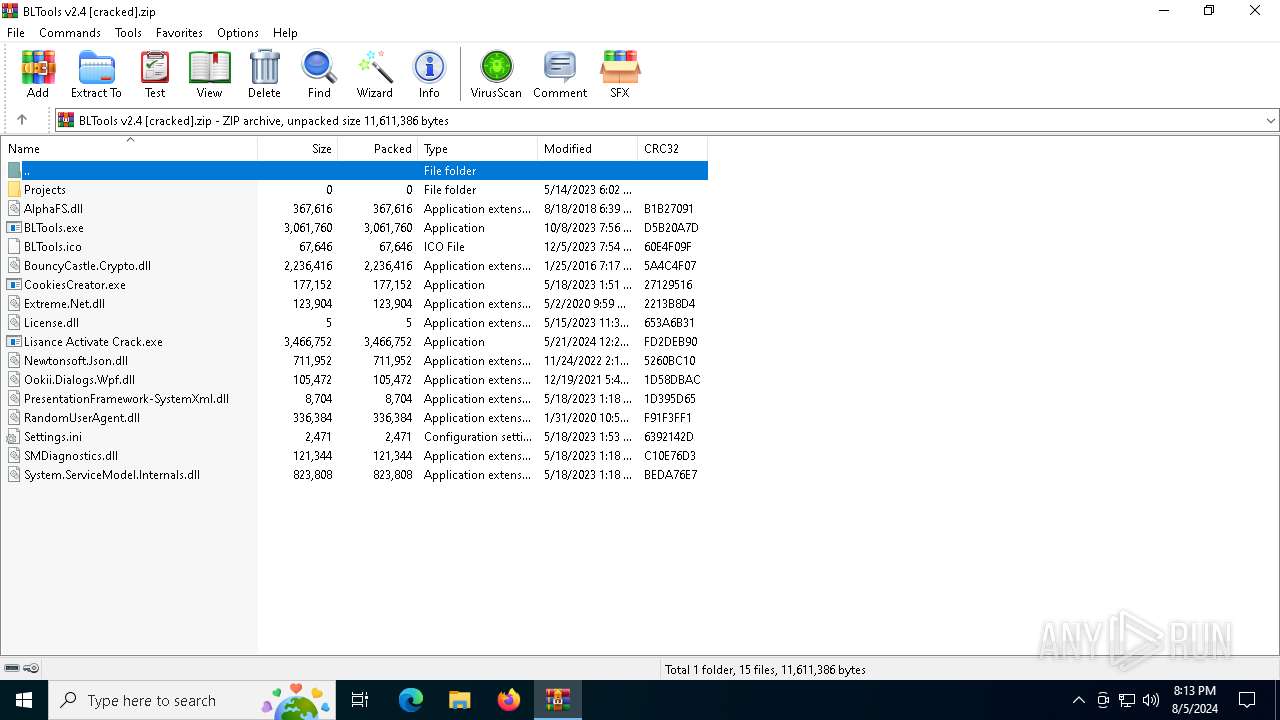
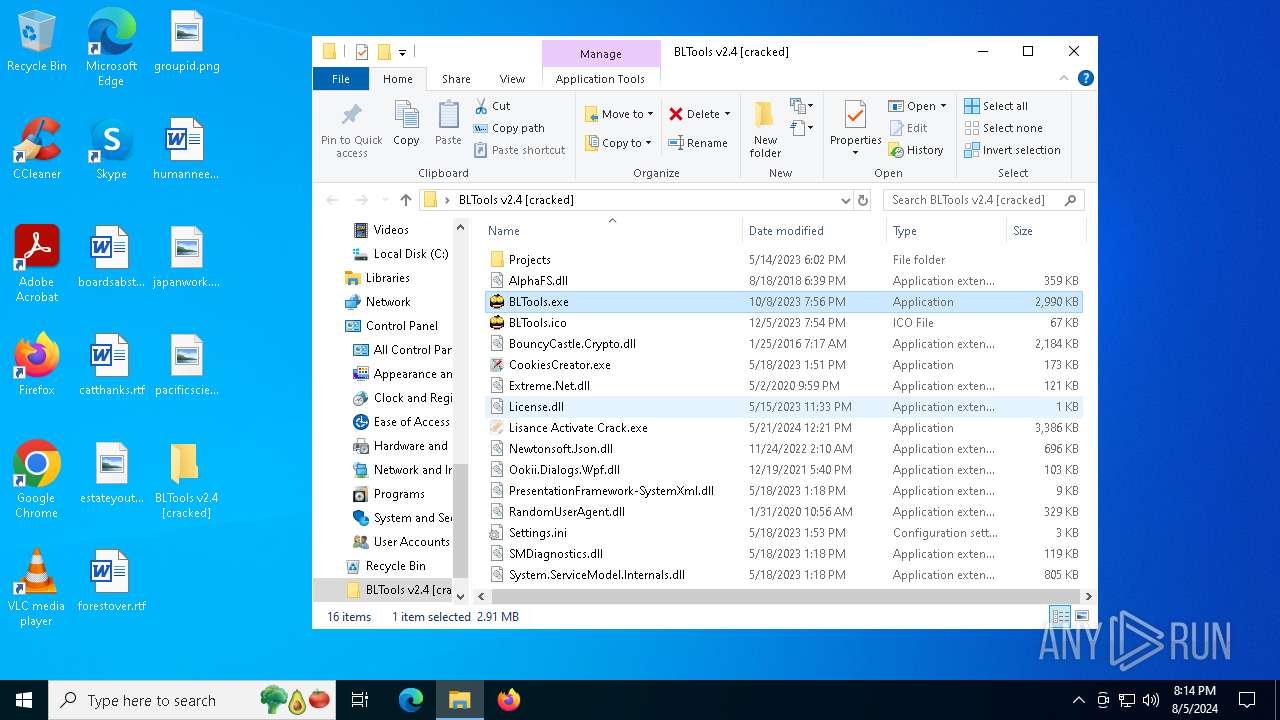
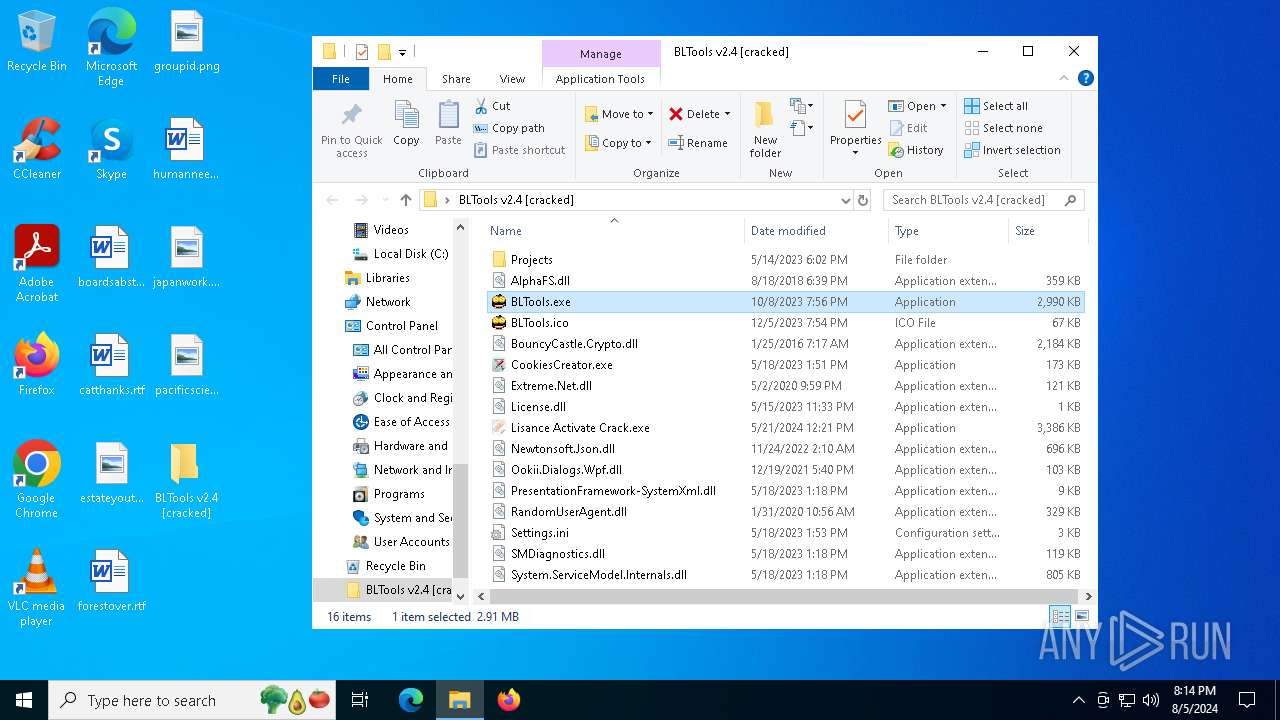
| File name: | BLTools v2.4 [cracked].zip |
| Full analysis: | https://app.any.run/tasks/ea35f827-ea2f-490a-aa50-86846c26abd0 |
| Verdict: | Malicious activity |
| Analysis date: | August 05, 2024, 20:13:34 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 40FF3FC085FE496C78B00DA6947F5850 |
| SHA1: | B217187B9C29EF8575A32527D7040ED67D316ACA |
| SHA256: | 86B09840179ABF2B2A60E14008862771EE58BFE207240711EA27F100B7E3C814 |
| SSDEEP: | 98304:uQc1iztGC2cxQt1eJ10cRcKVwJ35hiHztO8IDLXWWVH2P0eUGP71SBA24F9MjZJA:i7WU8u8cYb |
MALICIOUS
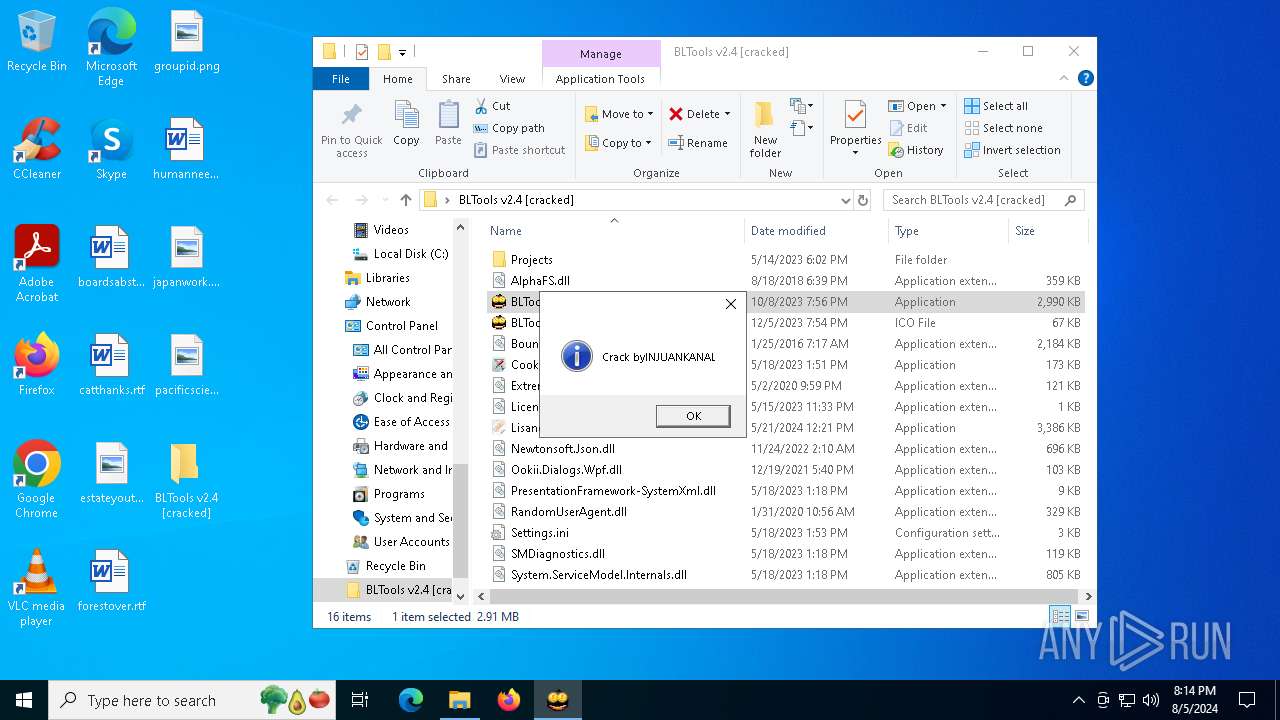
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6400)
- BLTools.exe (PID: 6360)
- Dizxte.png (PID: 6196)
Xcopy is used to copy an executable file into an image
- xcopy.exe (PID: 1860)
- xcopy.exe (PID: 6768)
- xcopy.exe (PID: 4604)
- xcopy.exe (PID: 6536)
Starts PowerShell from an unusual location
- cmd.exe (PID: 4784)
- cmd.exe (PID: 3164)
Changes the autorun value in the registry
- BLTools.exe (PID: 6360)
- Dizxte.png (PID: 6196)
- BLTools.exe (PID: 1452)
Dynamically loads an assembly (POWERSHELL)
- Dizxte.png (PID: 4296)
- Dizxte.png (PID: 6196)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 6400)
- xcopy.exe (PID: 6536)
- Dizxte.png (PID: 6196)
Reads security settings of Internet Explorer
- BLTools.exe (PID: 6360)
- Dizxte.png (PID: 4296)
- Dizxte.png (PID: 6196)
Reads the date of Windows installation
- BLTools.exe (PID: 6360)
- Dizxte.png (PID: 4296)
Executing commands from a ".bat" file
- BLTools.exe (PID: 6360)
- cmd.exe (PID: 6592)
- Dizxte.png (PID: 4296)
- cmd.exe (PID: 6684)
- cmd.exe (PID: 6332)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 6592)
- BLTools.exe (PID: 6360)
- cmd.exe (PID: 4784)
- cmd.exe (PID: 6684)
- cmd.exe (PID: 6332)
- Dizxte.png (PID: 4296)
- cmd.exe (PID: 3164)
Process copies executable file
- cmd.exe (PID: 6592)
- cmd.exe (PID: 4784)
- cmd.exe (PID: 6332)
- cmd.exe (PID: 3164)
Application launched itself
- cmd.exe (PID: 4784)
- BLTools.exe (PID: 6360)
- cmd.exe (PID: 6684)
- cmd.exe (PID: 6332)
- cmd.exe (PID: 3164)
- BLTools.exe (PID: 1452)
- cmd.exe (PID: 6592)
Starts a Microsoft application from unusual location
- Dizxte.png (PID: 4296)
- Dizxte.png (PID: 6196)
The executable file from the user directory is run by the CMD process
- Dizxte.png (PID: 4296)
- Dizxte.png (PID: 6196)
Starts application with an unusual extension
- cmd.exe (PID: 4784)
- cmd.exe (PID: 3164)
Checks Windows Trust Settings
- Dizxte.png (PID: 4296)
- Dizxte.png (PID: 6196)
Executable content was dropped or overwritten
- BLTools.exe (PID: 6360)
- Dizxte.png (PID: 6196)
- xcopy.exe (PID: 6536)
Uses base64 encoding (POWERSHELL)
- Dizxte.png (PID: 4296)
- Dizxte.png (PID: 6196)
Reverses array data (POWERSHELL)
- Dizxte.png (PID: 4296)
- Dizxte.png (PID: 6196)
Found regular expressions for crypto-addresses (YARA)
- Dizxte.png (PID: 6196)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6400)
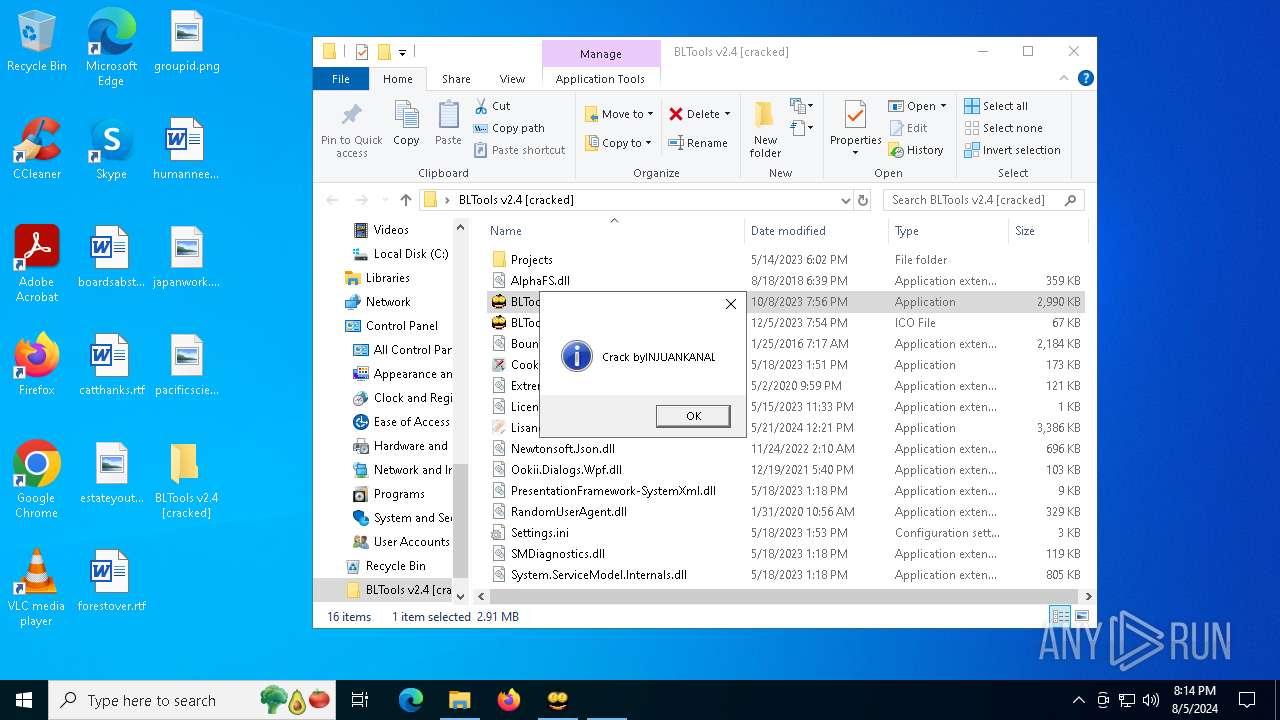
Manual execution by a user
- BLTools.exe (PID: 6360)
- BLTools.exe (PID: 1452)
- Lisance Activate Crack.exe (PID: 6252)
Reads the computer name
- BLTools.exe (PID: 6360)
- Dizxte.png (PID: 4296)
- Dizxte.png (PID: 6196)
- BLTools.exe (PID: 1452)
- Lisance Activate Crack.exe (PID: 6252)
Checks supported languages
- BLTools.exe (PID: 6360)
- Dizxte.png (PID: 4296)
- Dizxte.png (PID: 6196)
- BLTools.exe (PID: 1452)
- Lisance Activate Crack.exe (PID: 6252)
Process checks computer location settings
- BLTools.exe (PID: 6360)
- Dizxte.png (PID: 4296)
Create files in a temporary directory
- BLTools.exe (PID: 6360)
- xcopy.exe (PID: 6312)
- Dizxte.png (PID: 4296)
- Dizxte.png (PID: 6196)
- xcopy.exe (PID: 6536)
Reads the machine GUID from the registry
- BLTools.exe (PID: 6360)
- Dizxte.png (PID: 4296)
- Dizxte.png (PID: 6196)
- Lisance Activate Crack.exe (PID: 6252)
- BLTools.exe (PID: 1452)
Drops the executable file immediately after the start
- xcopy.exe (PID: 6536)
Reads Environment values
- Dizxte.png (PID: 4296)
- Dizxte.png (PID: 6196)
Creates files or folders in the user directory
- BLTools.exe (PID: 6360)
- Dizxte.png (PID: 6196)
Reads the software policy settings
- Dizxte.png (PID: 4296)
- Dizxte.png (PID: 6196)
Found Base64 encoded access to processes via PowerShell (YARA)
- cmd.exe (PID: 3164)
- Dizxte.png (PID: 6196)
Found Base64 encoded file access via PowerShell (YARA)
- cmd.exe (PID: 3164)
- Dizxte.png (PID: 6196)
Found Base64 encoded compression PowerShell classes (YARA)
- cmd.exe (PID: 3164)
- Dizxte.png (PID: 6196)
Found Base64 encoded reflection usage via PowerShell (YARA)
- cmd.exe (PID: 3164)
- Dizxte.png (PID: 6196)
Found Base64 encoded text manipulation via PowerShell (YARA)
- cmd.exe (PID: 3164)
- Dizxte.png (PID: 6196)
.NET Reactor protector has been detected
- Dizxte.png (PID: 6196)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2018:08:18 21:39:52 |
| ZipCRC: | 0xb1b27091 |
| ZipCompressedSize: | 367616 |
| ZipUncompressedSize: | 367616 |
| ZipFileName: | AlphaFS.dll |
Total processes
178
Monitored processes
49
Malicious processes
9
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 964 | "C:\Users\admin\Desktop\BLTools v2.4 [cracked]\BLTools.exe" | C:\Users\admin\Desktop\BLTools v2.4 [cracked]\BLTools.exe | — | BLTools.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: BLTools Exit code: 4294967295 Version: 2.4.0.0 Modules
| |||||||||||||||
| 1216 | "C:\Users\admin\Desktop\BLTools v2.4 [cracked]\BLTools.exe" | C:\Users\admin\Desktop\BLTools v2.4 [cracked]\BLTools.exe | — | BLTools.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: BLTools Exit code: 4294967295 Version: 2.4.0.0 Modules
| |||||||||||||||
| 1452 | "C:\Users\admin\Desktop\BLTools v2.4 [cracked]\BLTools.exe" | C:\Users\admin\Desktop\BLTools v2.4 [cracked]\BLTools.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: BLTools Exit code: 0 Version: 2.4.0.0 Modules
| |||||||||||||||
| 1488 | "C:\Users\admin\Desktop\BLTools v2.4 [cracked]\BLTools.exe" | C:\Users\admin\Desktop\BLTools v2.4 [cracked]\BLTools.exe | — | BLTools.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: BLTools Exit code: 4294967295 Version: 2.4.0.0 Modules
| |||||||||||||||
| 1568 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo F " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1860 | xcopy /d /q /y /h /i C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe C:\Users\admin\AppData\Local\Temp\Dizxte.png | C:\Windows\System32\xcopy.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extended Copy Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1860 | "C:\Users\admin\Desktop\BLTools v2.4 [cracked]\BLTools.exe" | C:\Users\admin\Desktop\BLTools v2.4 [cracked]\BLTools.exe | — | BLTools.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: BLTools Exit code: 4294967295 Version: 2.4.0.0 Modules
| |||||||||||||||
| 1984 | "C:\Users\admin\Desktop\BLTools v2.4 [cracked]\BLTools.exe" | C:\Users\admin\Desktop\BLTools v2.4 [cracked]\BLTools.exe | — | BLTools.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: BLTools Exit code: 4294967295 Version: 2.4.0.0 Modules
| |||||||||||||||
| 2064 | "C:\Users\admin\Desktop\BLTools v2.4 [cracked]\BLTools.exe" | C:\Users\admin\Desktop\BLTools v2.4 [cracked]\BLTools.exe | — | BLTools.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: BLTools Exit code: 4294967295 Version: 2.4.0.0 Modules
| |||||||||||||||
| 2680 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
21 470
Read events
21 431
Write events
39
Delete events
0
Modification events
| (PID) Process: | (6400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\BLTools v2.4 [cracked].zip | |||
| (PID) Process: | (6400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\BLTools v2.4 [cracked] | |||
| (PID) Process: | (6400) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000200000003000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
15
Suspicious files
2
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6400 | WinRAR.exe | C:\Users\admin\Desktop\BLTools v2.4 [cracked]\Lisance Activate Crack.exe | executable | |
MD5:3687DAF352D0764FC83F640FA165198A | SHA256:8ACE6E0A0A2ED86B3BBB7C7FEFCB8F5B4176B7143DD299D07DD07AD8C958F48A | |||
| 6400 | WinRAR.exe | C:\Users\admin\Desktop\BLTools v2.4 [cracked]\BLTools.ico | image | |
MD5:FE8D1D9038E246C569AAB6C5037E1580 | SHA256:AE90A3E783A4F4791B5B66CFFED27BFAA939A2CA55AF7F41CED2397D4D64F0F6 | |||
| 6400 | WinRAR.exe | C:\Users\admin\Desktop\BLTools v2.4 [cracked]\AlphaFS.dll | executable | |
MD5:F2F6F6798D306D6D7DF4267434B5C5F9 | SHA256:837F2CEAB6BBD9BC4BF076F1CB90B3158191888C3055DD2B78A1E23F1C3AAFDD | |||
| 6400 | WinRAR.exe | C:\Users\admin\Desktop\BLTools v2.4 [cracked]\License.dll | text | |
MD5:B08A5C34CF0A06615DA2CA89010D8B4F | SHA256:04CC5B3B49A7E9E9B6C66C7BE59A20992BF2653746B5D43829C383FB233F88FA | |||
| 6400 | WinRAR.exe | C:\Users\admin\Desktop\BLTools v2.4 [cracked]\Extreme.Net.dll | executable | |
MD5:F79F0E3A0361CAC000E2D3553753CD68 | SHA256:8A6518AB7419FBEC3AC9875BAA3AFB410AD1398C7AA622A09CD9084EC6CADFCD | |||
| 6400 | WinRAR.exe | C:\Users\admin\Desktop\BLTools v2.4 [cracked]\BLTools.exe | executable | |
MD5:E594A5273C5F54AAA59709309BBAC7CB | SHA256:EAD030C352A651B5A294E776ACE4C3BBAF1F6F7581C36EC3ECA301584F92B132 | |||
| 6400 | WinRAR.exe | C:\Users\admin\Desktop\BLTools v2.4 [cracked]\Ookii.Dialogs.Wpf.dll | executable | |
MD5:932EBB3F9E7113071C6A17818342B7CC | SHA256:285AA8225732DDBCF211B1158BD6CFF8BF3ACBEEAB69617F4BE85862B7105AB5 | |||
| 6400 | WinRAR.exe | C:\Users\admin\Desktop\BLTools v2.4 [cracked]\Newtonsoft.Json.dll | executable | |
MD5:715A1FBEE4665E99E859EDA667FE8034 | SHA256:C5C83BBC1741BE6FF4C490C0AEE34C162945423EC577C646538B2D21CE13199E | |||
| 6400 | WinRAR.exe | C:\Users\admin\Desktop\BLTools v2.4 [cracked]\SMDiagnostics.dll | executable | |
MD5:F1D92AC71001BCC24B99044EE675619F | SHA256:5DF3A2E0329D7668AD0F6C426F6E4C6D1ECD45225B2C39D96B15CD7B6A1BBE53 | |||
| 6400 | WinRAR.exe | C:\Users\admin\Desktop\BLTools v2.4 [cracked]\PresentationFramework-SystemXml.dll | executable | |
MD5:BE1A96C998147BFBEB5F635FE0C3428D | SHA256:D024E1CBECF038D59AE375552E4F47D2C737EAFCE7C68DA5EC8B2B02BECB297E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
40
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6860 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5140 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6832 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4936 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1420 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5336 | SearchApp.exe | 104.126.37.179:443 | www.bing.com | Akamai International B.V. | DE | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5140 | svchost.exe | 40.126.32.140:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
th.bing.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |