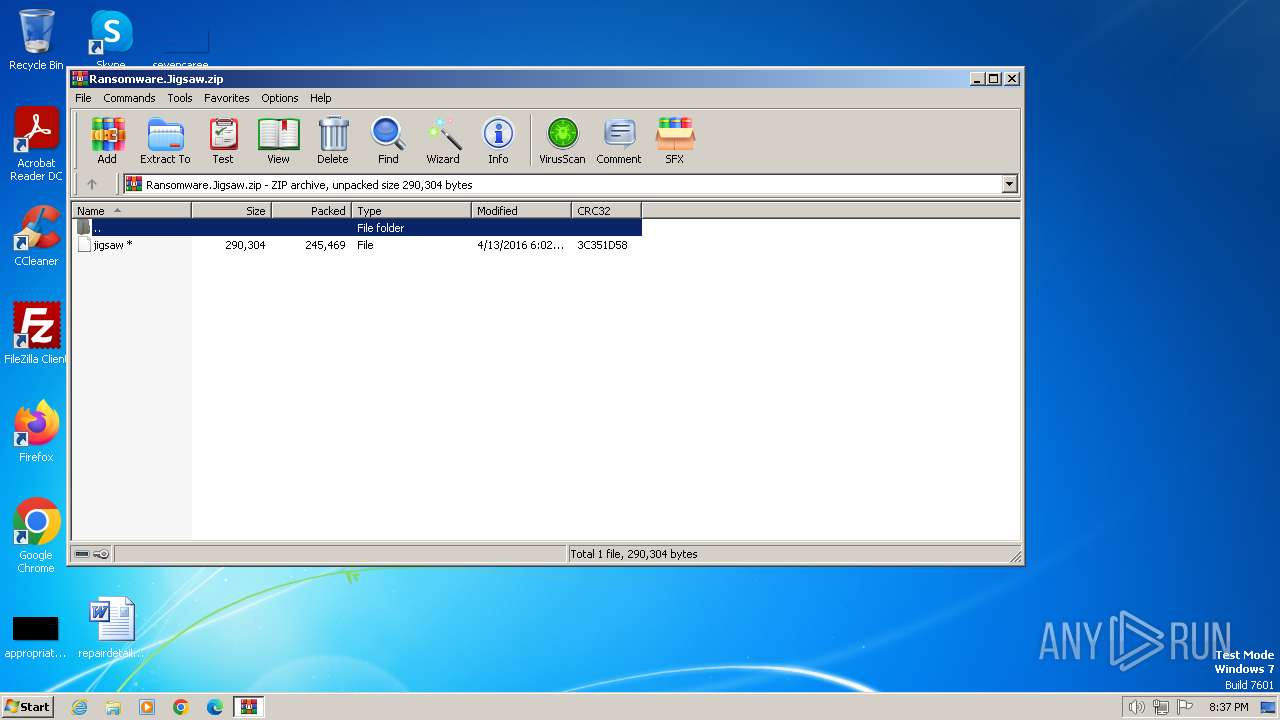
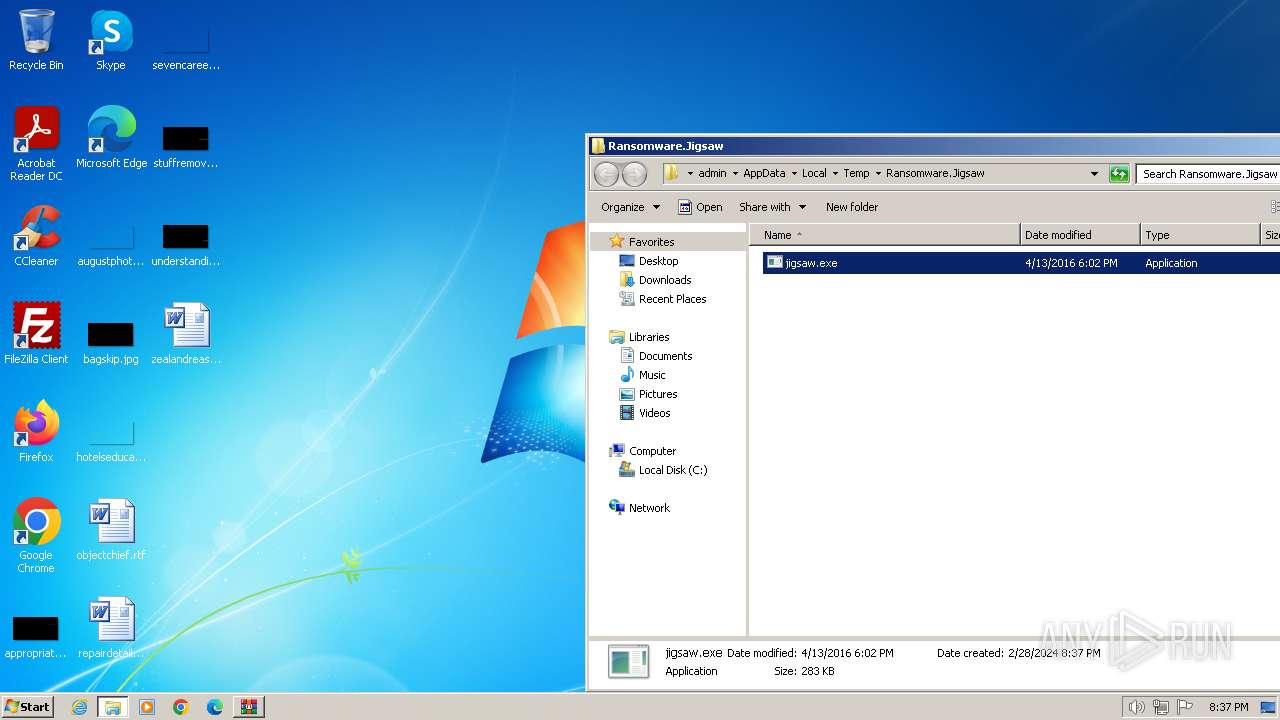
| File name: | Ransomware.Jigsaw.zip |
| Full analysis: | https://app.any.run/tasks/e8104c8a-78b4-4349-80e5-9f6d828e872f |
| Verdict: | Malicious activity |
| Analysis date: | February 28, 2024, 20:37:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 3AD6374A3558149D09D74E6AF72344E3 |
| SHA1: | E7BE9F22578027FC0B6DDB94C09B245EE8CE1620 |
| SHA256: | 86A391FE7A237F4F17846C53D71E45820411D1A9A6E0C16F22A11EBC491FF9FF |
| SSDEEP: | 3072:p7ykj3uuY4NsJD7kPdSRQLqas/pkPm9jvkEL60Uf7k2BgS6/aFybrNN5ZAdNstk7:p7ym3VNA7w8R5/rxv7O0yng0UtVw5NJ |
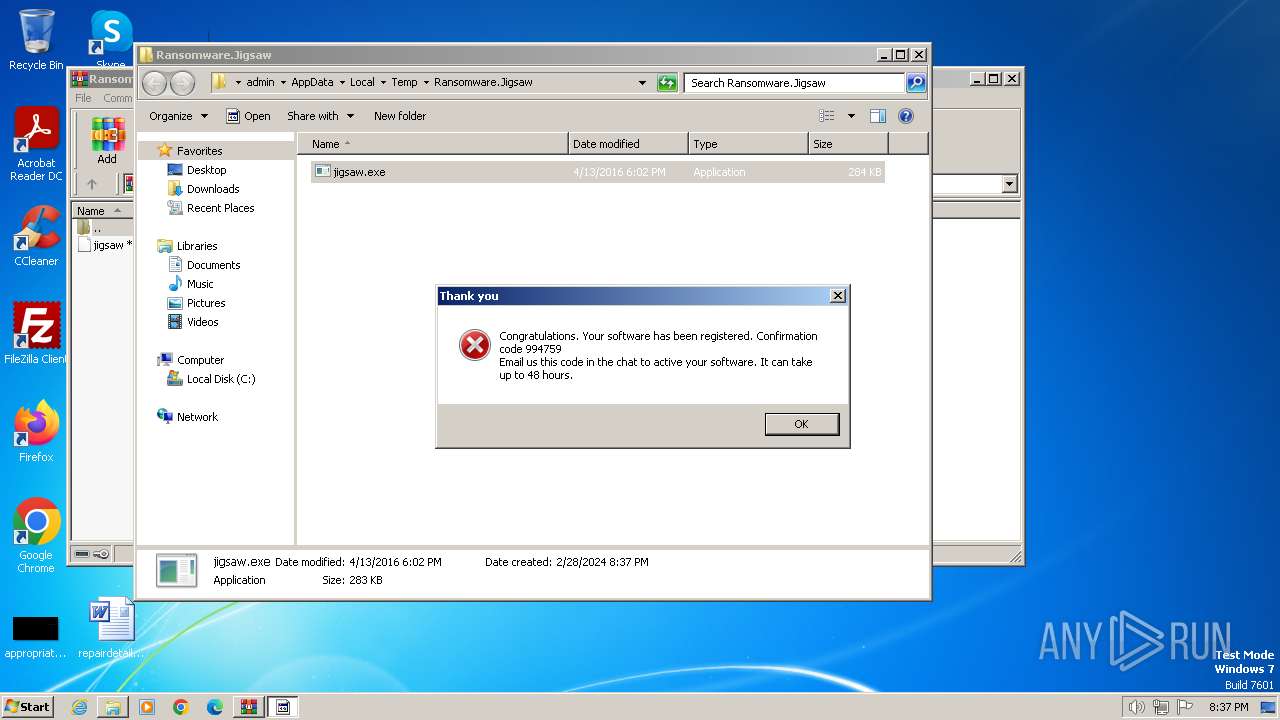
MALICIOUS
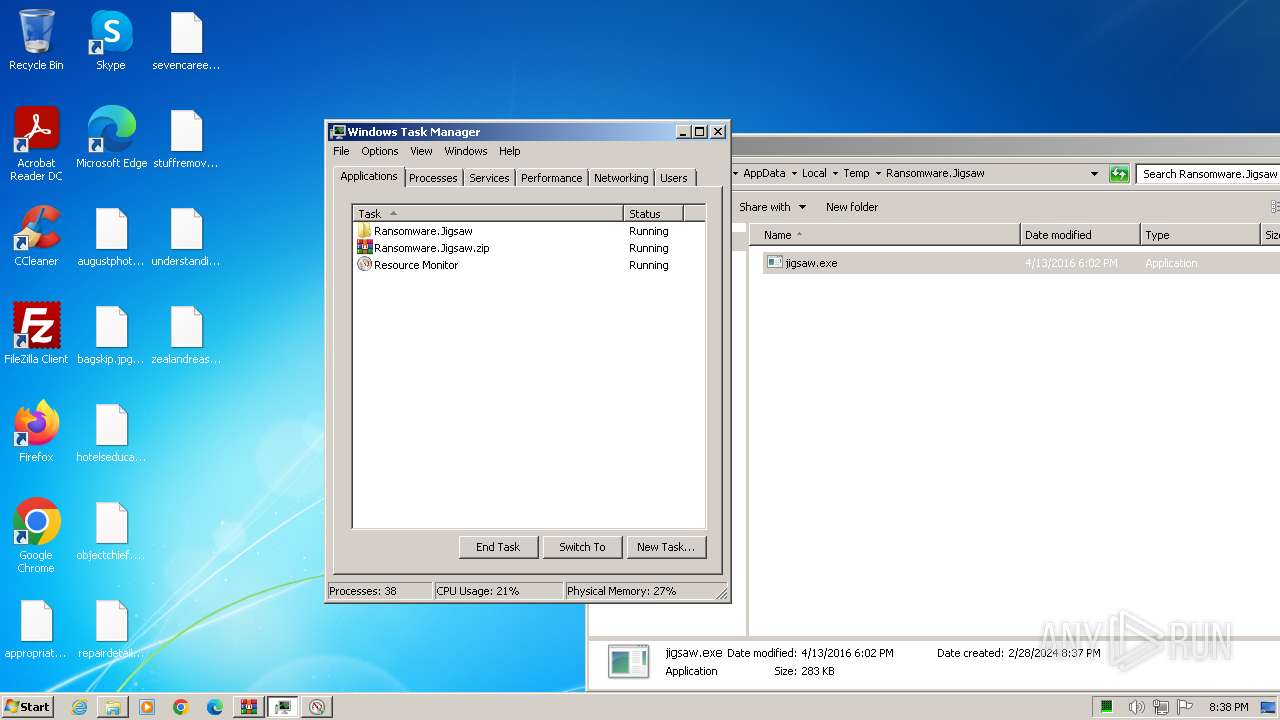
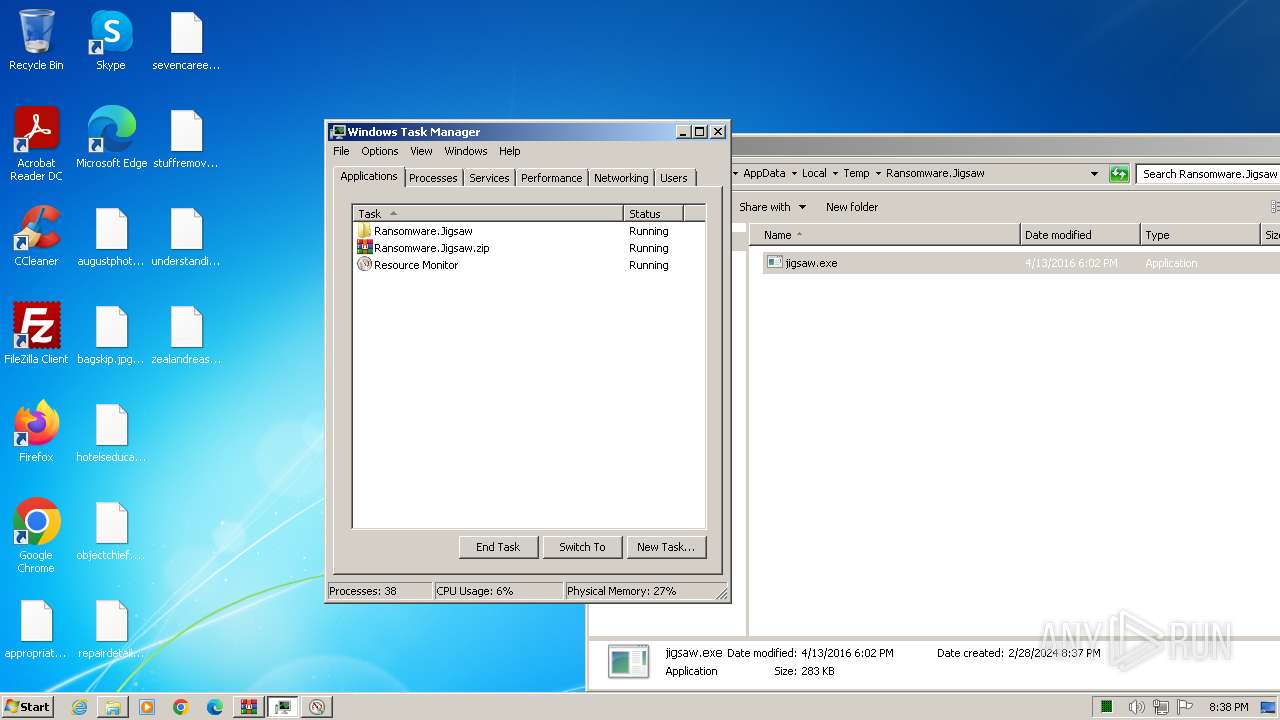
Drops the executable file immediately after the start
- jigsaw.exe (PID: 4060)
- WinRAR.exe (PID: 3240)
- drpbx.exe (PID: 4008)
Changes the autorun value in the registry
- jigsaw.exe (PID: 4060)
Actions looks like stealing of personal data
- drpbx.exe (PID: 4008)
SUSPICIOUS
Reads security settings of Internet Explorer
- jigsaw.exe (PID: 4060)
Executable content was dropped or overwritten
- jigsaw.exe (PID: 4060)
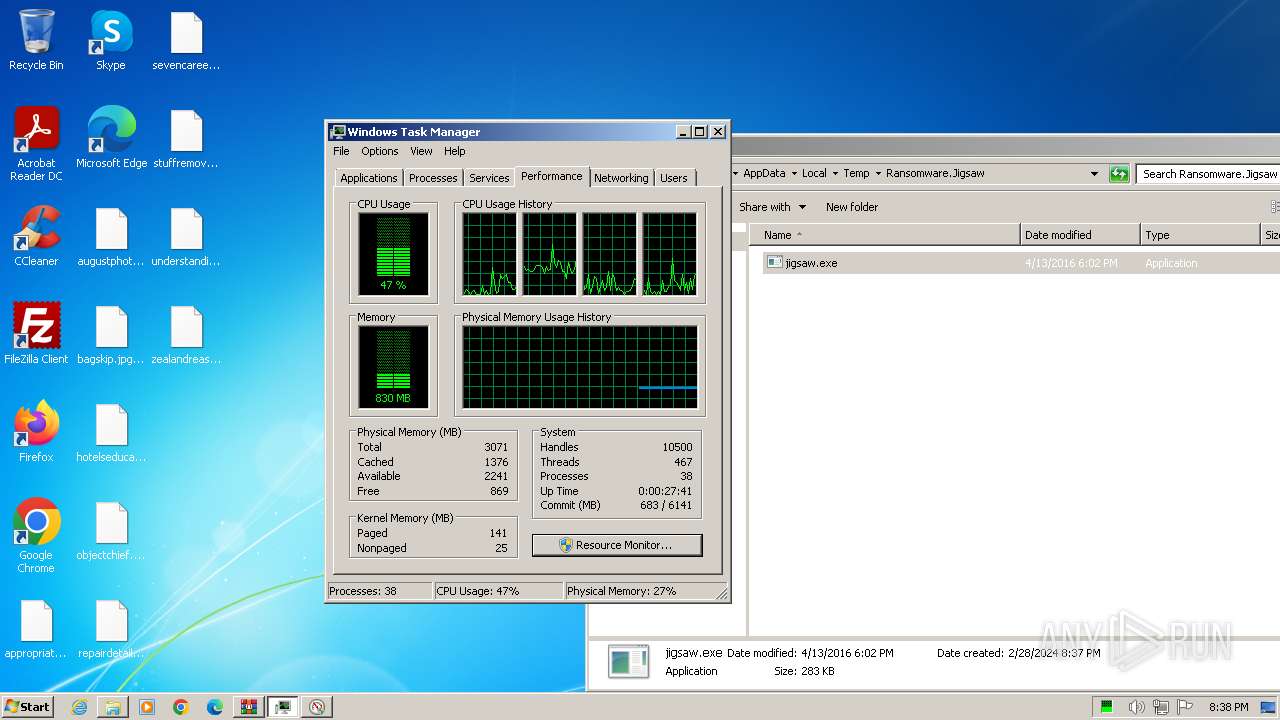
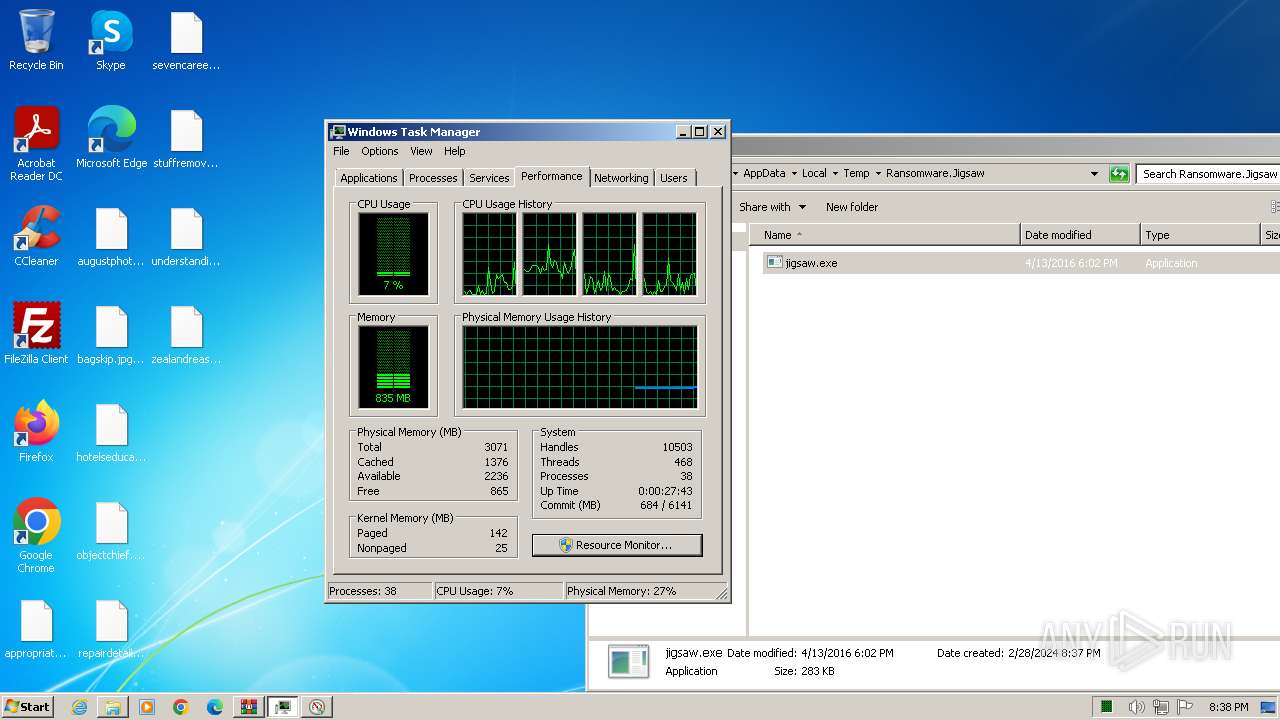
Reads the Internet Settings
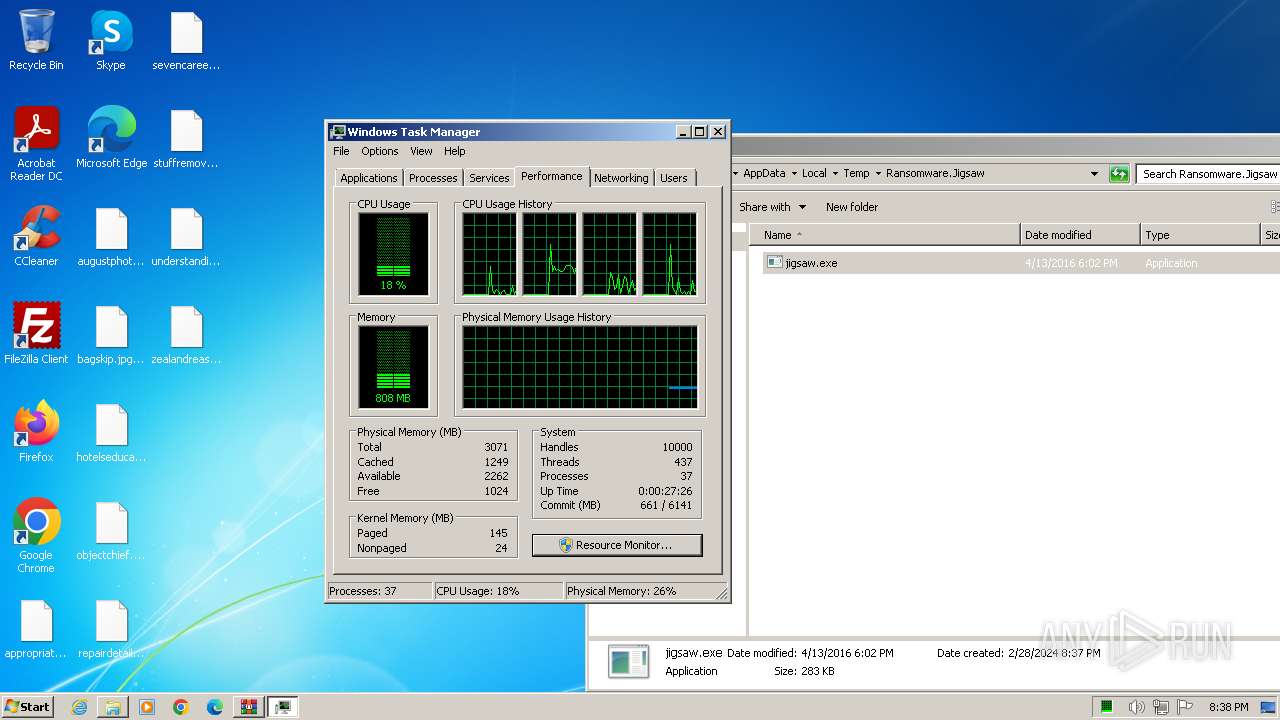
- jigsaw.exe (PID: 4060)
- taskmgr.exe (PID: 2756)
Starts itself from another location
- jigsaw.exe (PID: 4060)
Application launched itself
- taskmgr.exe (PID: 2756)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3240)
Checks supported languages
- jigsaw.exe (PID: 4060)
- drpbx.exe (PID: 4008)
Manual execution by a user
- jigsaw.exe (PID: 4060)
- rundll32.exe (PID: 2504)
- taskmgr.exe (PID: 2756)
Creates files or folders in the user directory
- jigsaw.exe (PID: 4060)
- drpbx.exe (PID: 4008)
Reads the computer name
- jigsaw.exe (PID: 4060)
Reads the machine GUID from the registry
- jigsaw.exe (PID: 4060)
- drpbx.exe (PID: 4008)
Creates files in the program directory
- drpbx.exe (PID: 4008)
Reads the time zone
- perfmon.exe (PID: 1992)
Reads security settings of Internet Explorer
- taskmgr.exe (PID: 2756)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2016:04:13 19:02:34 |
| ZipCRC: | 0x3c351d58 |
| ZipCompressedSize: | 245469 |
| ZipUncompressedSize: | 290304 |
| ZipFileName: | jigsaw |
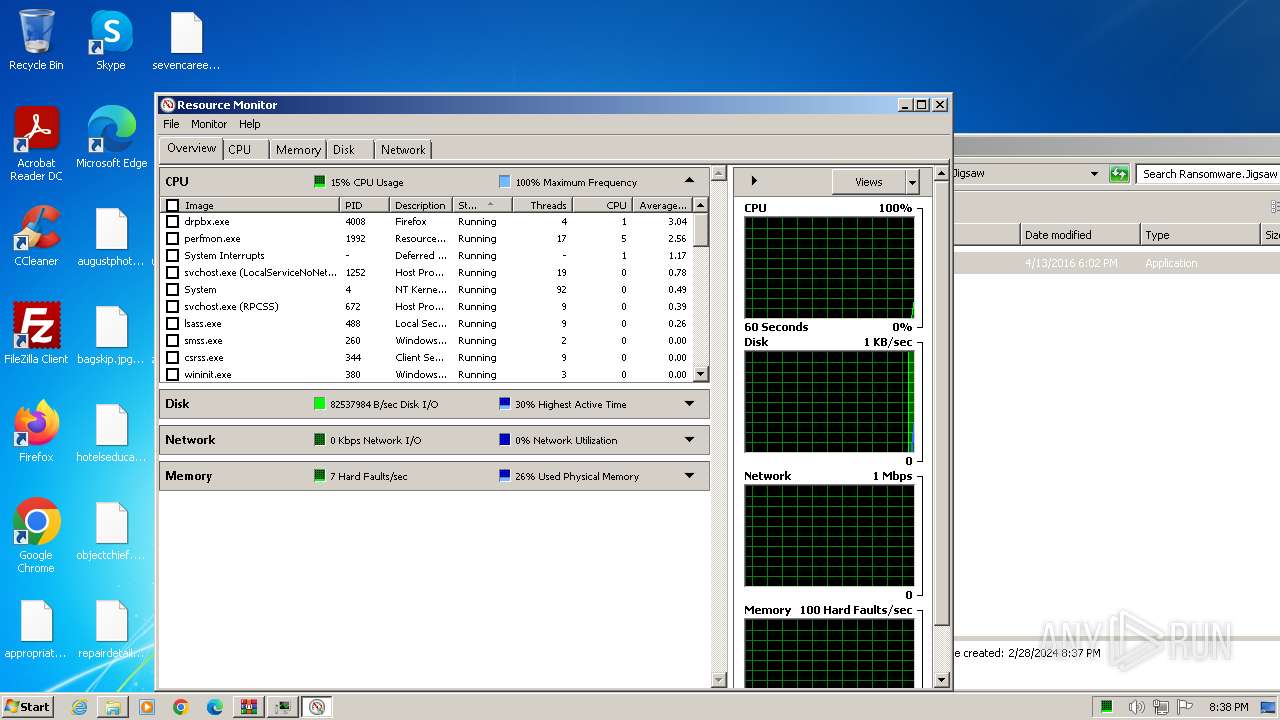
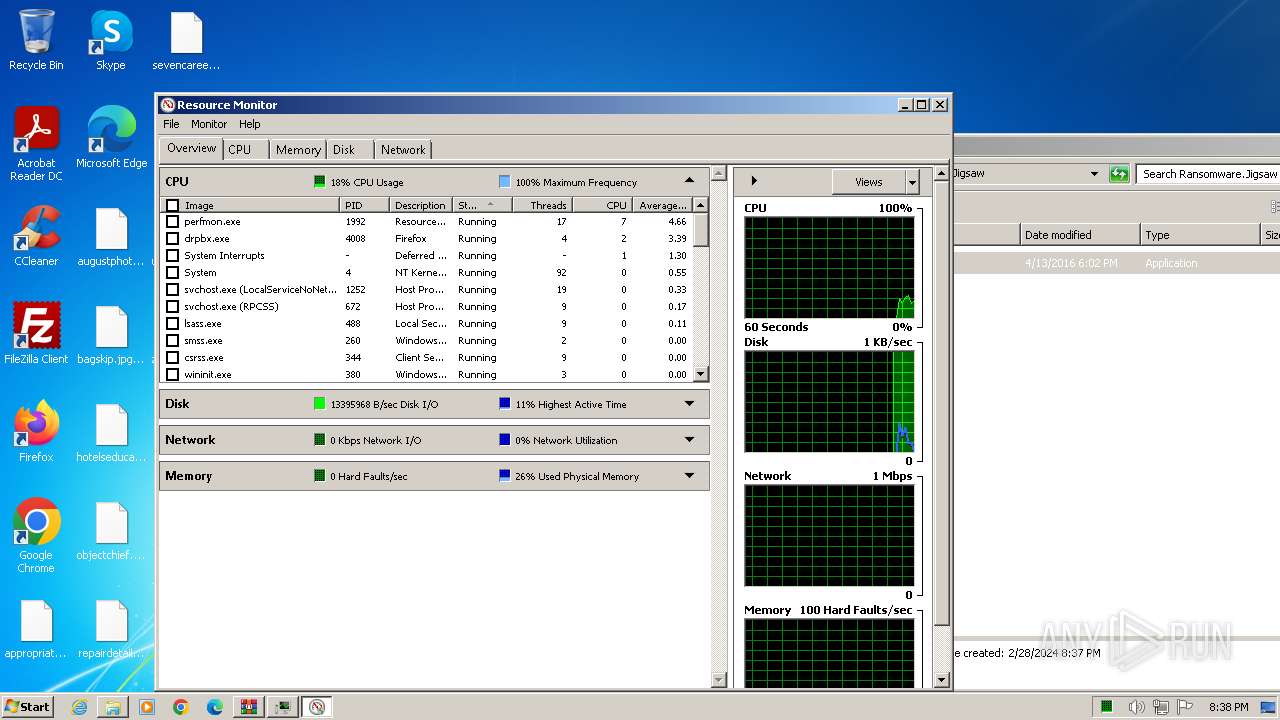
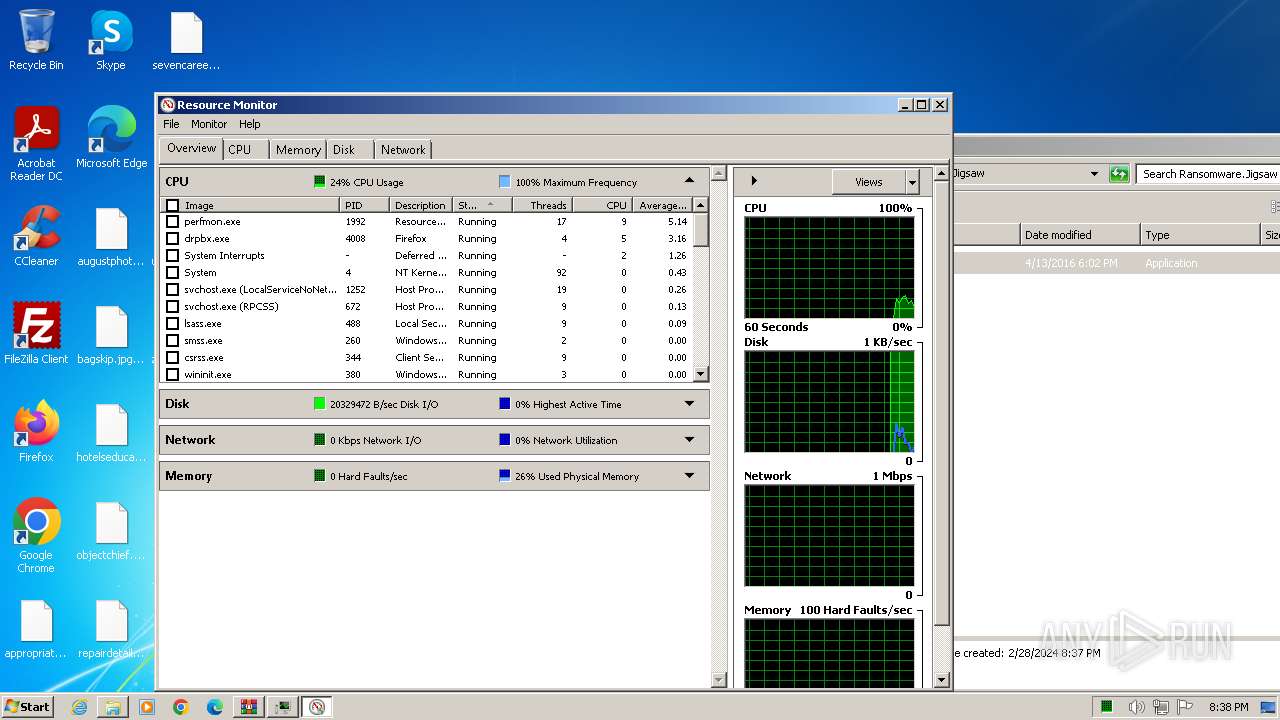
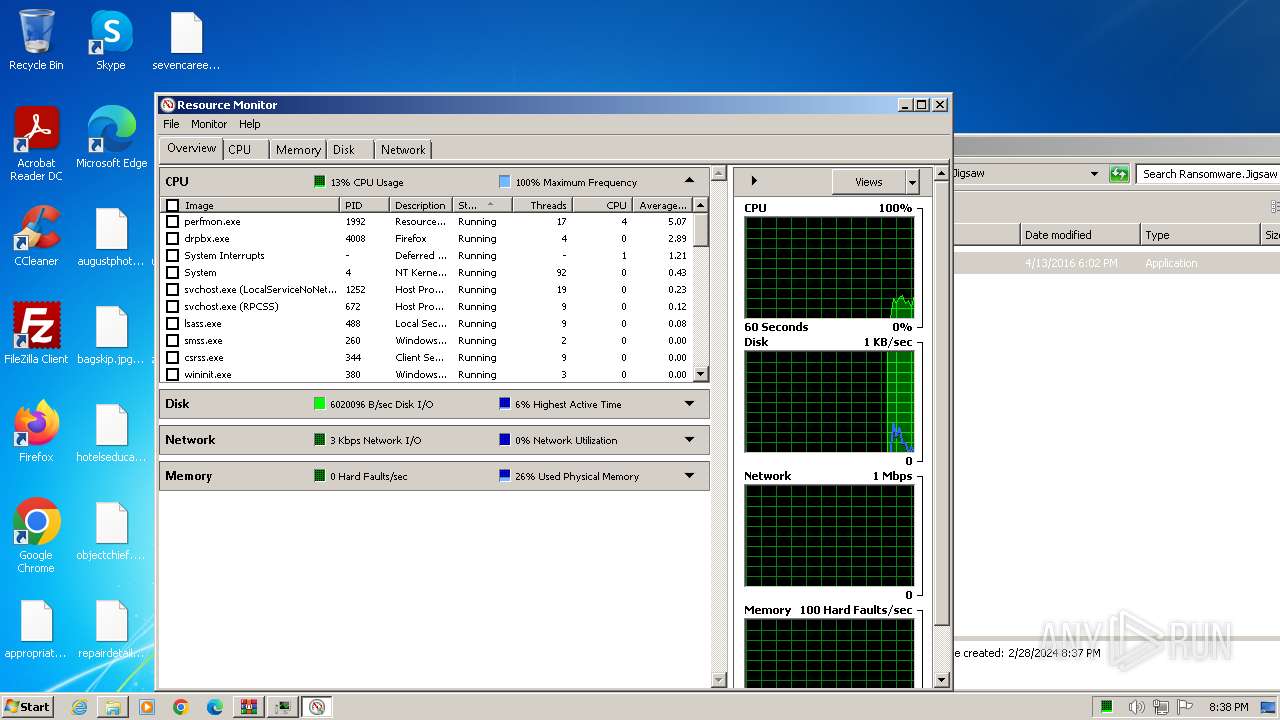
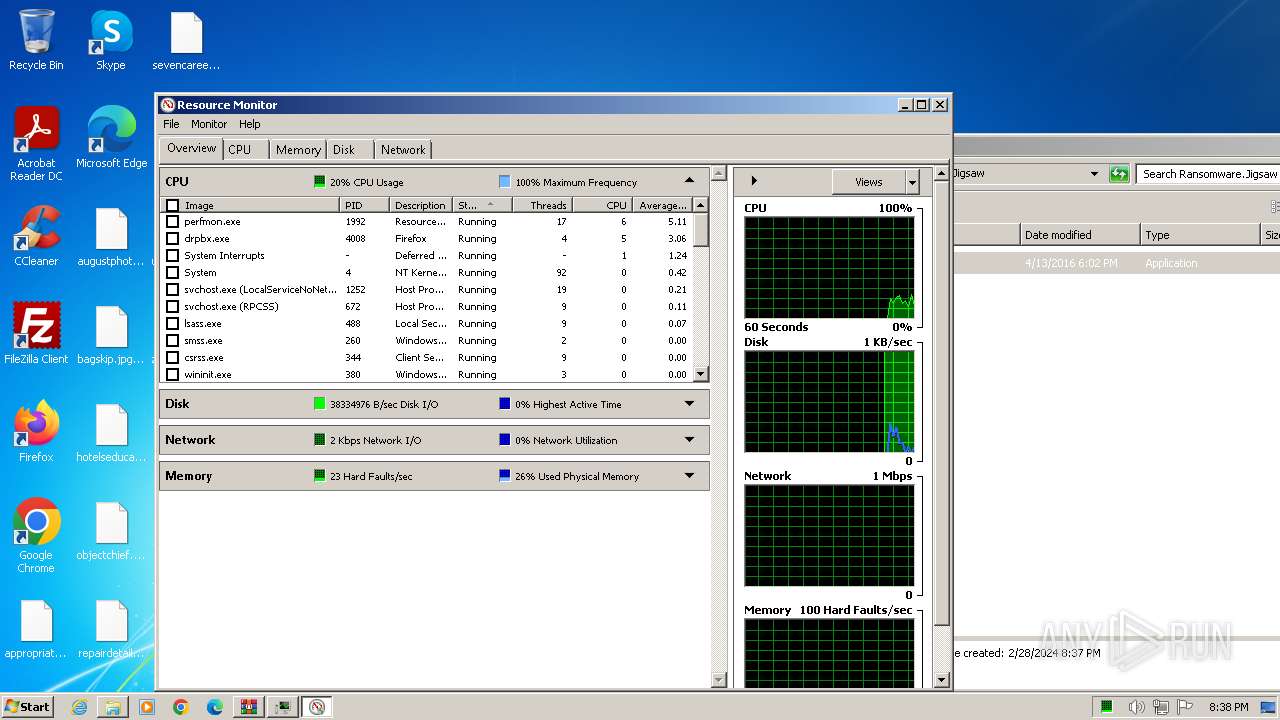
Total processes
56
Monitored processes
8
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1232 | "C:\Windows\system32\taskmgr.exe" /1 | C:\Windows\System32\taskmgr.exe | taskmgr.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Task Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1596 | "C:\Windows\system32\taskmgr.exe" /1 | C:\Windows\System32\taskmgr.exe | taskmgr.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1992 | "C:\Windows\System32\perfmon.exe" /res | C:\Windows\System32\perfmon.exe | taskmgr.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Resource and Performance Monitor Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
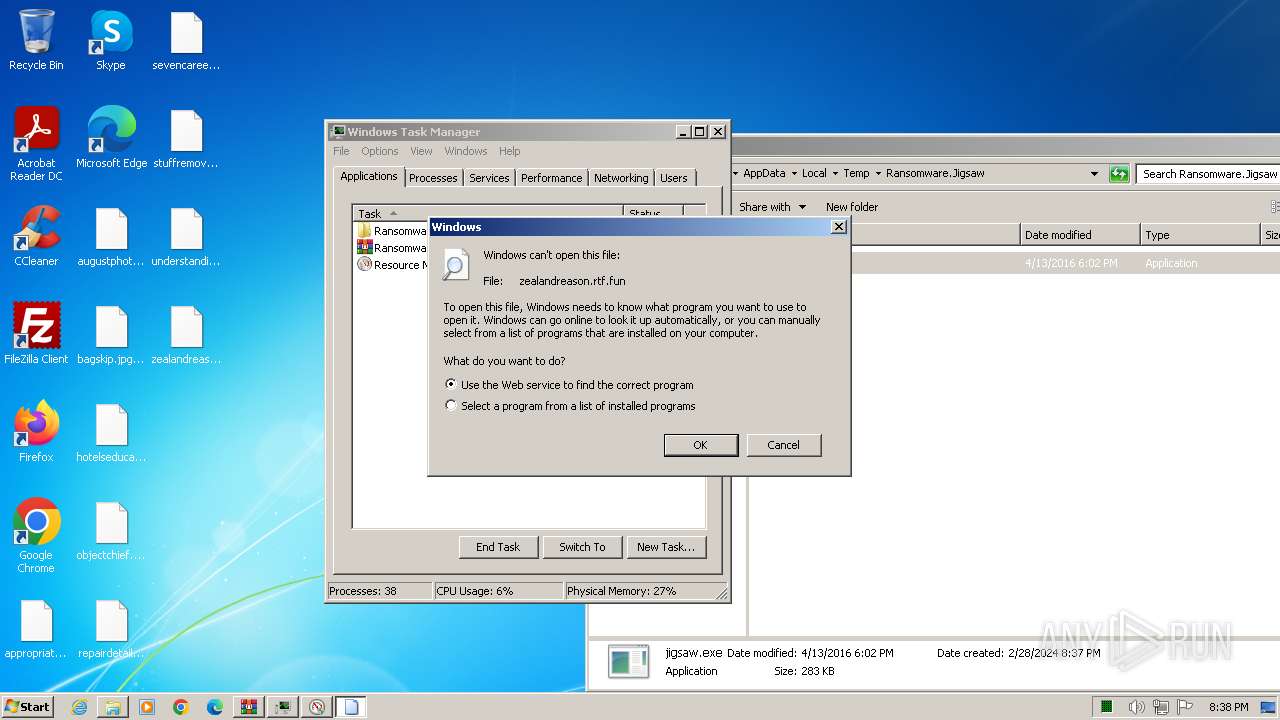
| 2504 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\zealandreason.rtf.fun | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2756 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\System32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3240 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Ransomware.Jigsaw.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4008 | "C:\Users\admin\AppData\Local\Drpbx\drpbx.exe" C:\Users\admin\AppData\Local\Temp\Ransomware.Jigsaw\jigsaw.exe | C:\Users\admin\AppData\Local\Drpbx\drpbx.exe | jigsaw.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Firefox Exit code: 0 Version: 37.0.2.5583 Modules
| |||||||||||||||
| 4060 | "C:\Users\admin\AppData\Local\Temp\Ransomware.Jigsaw\jigsaw.exe" | C:\Users\admin\AppData\Local\Temp\Ransomware.Jigsaw\jigsaw.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Firefox Exit code: 0 Version: 37.0.2.5583 Modules
| |||||||||||||||
Total events
31 446
Read events
31 411
Write events
35
Delete events
0
Modification events
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Ransomware.Jigsaw.zip | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
3
Suspicious files
697
Text files
3
Unknown types
1 035
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4008 | drpbx.exe | C:\Program Files\Notepad++\contextMenu.xml.fun | binary | |
MD5:BE71D95C47DFAD9533F15D52CF2566D5 | SHA256:2501FE92DDBF8D2AE4B05D348504D090268C0E7397188856F38E4E72C5D4E918 | |||
| 4060 | jigsaw.exe | C:\Users\admin\AppData\Roaming\Frfx\firefox.exe | executable | |
MD5:2773E3DC59472296CB0024BA7715A64E | SHA256:3AE96F73D805E1D3995253DB4D910300D8442EA603737A1428B613061E7F61E7 | |||
| 4008 | drpbx.exe | C:\Program Files\Notepad++\readme.txt.fun | binary | |
MD5:2C85760079EEEFECD7AFC78E17E71429 | SHA256:3909FEF7DD4C519B8FCCF7A717DD9FECFA84BB21C54332DB0C6E443F5AF284BD | |||
| 4060 | jigsaw.exe | C:\Users\admin\AppData\Local\Drpbx\drpbx.exe | executable | |
MD5:2773E3DC59472296CB0024BA7715A64E | SHA256:3AE96F73D805E1D3995253DB4D910300D8442EA603737A1428B613061E7F61E7 | |||
| 4008 | drpbx.exe | C:\Program Files\Notepad++\langs.model.xml.fun | binary | |
MD5:7473961B073EB91F779284580A72B17E | SHA256:211A665FE918DD3F64691A45EDBF5B9E9E385740EFE73E815439E94513EB870B | |||
| 4008 | drpbx.exe | C:\Program Files\Mozilla Firefox\private_browsing.VisualElementsManifest.xml.fun | binary | |
MD5:785DFBB301333EB396AD944721EB4755 | SHA256:5177A663D27F980E9DD5FE2DBCF69604DC518A361E1BA5639EAB57757829258C | |||
| 4008 | drpbx.exe | C:\Program Files\Notepad++\stylers.model.xml.fun | binary | |
MD5:D08290B0A29A17B244E72FBDDBE7A8CB | SHA256:1CF956464D997A8FBE1DC5BA8C0A293F84CCA9CA6B17E081E0A76B8E509599B6 | |||
| 4008 | drpbx.exe | C:\Program Files\WinRAR\License.txt.fun | binary | |
MD5:7AE45B8EF81B564F6839F1B5D2A3D6C3 | SHA256:B945701B3A8387E669BC6409FED40A085B93420E321F01845ABFFB46D28E791C | |||
| 4008 | drpbx.exe | C:\Program Files\WinRAR\Rar.txt.fun | binary | |
MD5:DBAE821F781AFDDDB14129F3D8E2F4EB | SHA256:FEF9DB86FF8028454C99AD0D187504DCE818A48AE078496F3DA93620B4FFDFFB | |||
| 4008 | drpbx.exe | C:\Program Files\WinRAR\rarnew.dat.fun | binary | |
MD5:2B4CCE4587D3D16C28BEF0B1C43FD63B | SHA256:5E47C760B0563379F444FFED52C1BF01C9F0A5901AF8E000861D209D8E3C8192 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
9
DNS requests
5
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.2:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
255.100.168.192.in-addr.arpa |
| unknown |
252.0.0.224.in-addr.arpa |
| unknown |
3.0.0.0.1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.2.0.f.f.ip6.arpa |
| unknown |
2.100.168.192.in-addr.arpa |
| unknown |