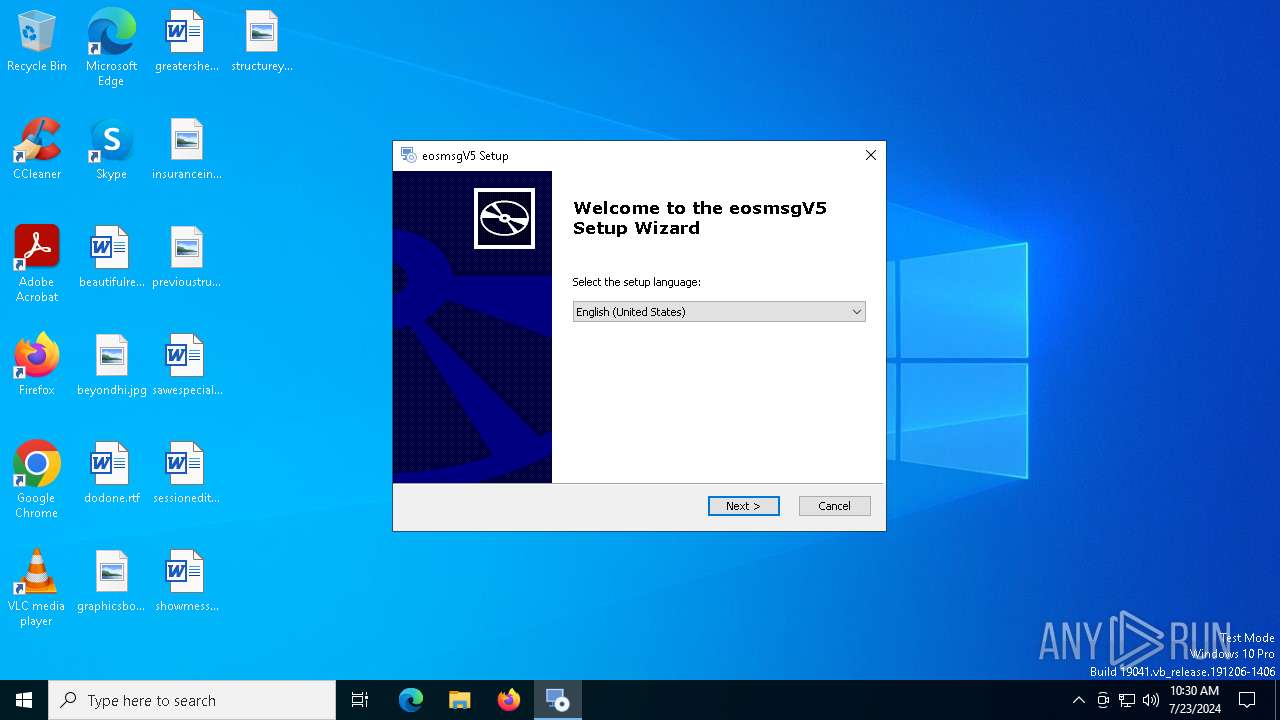
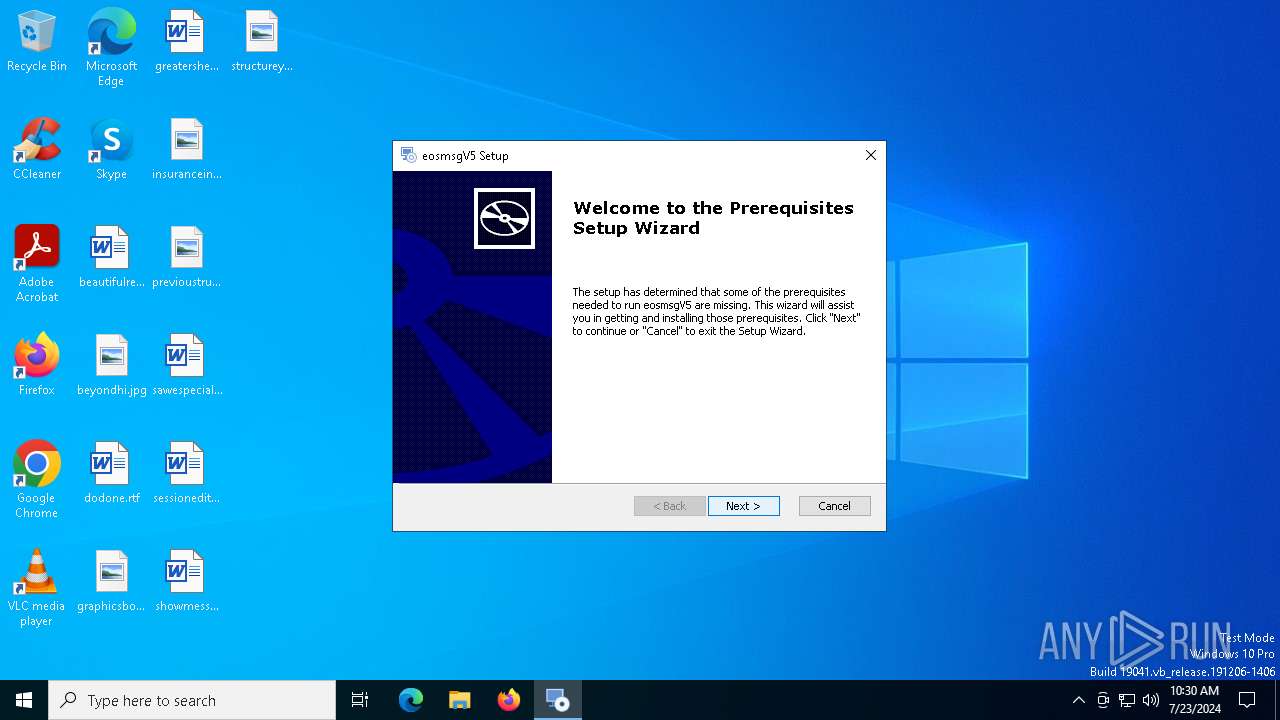
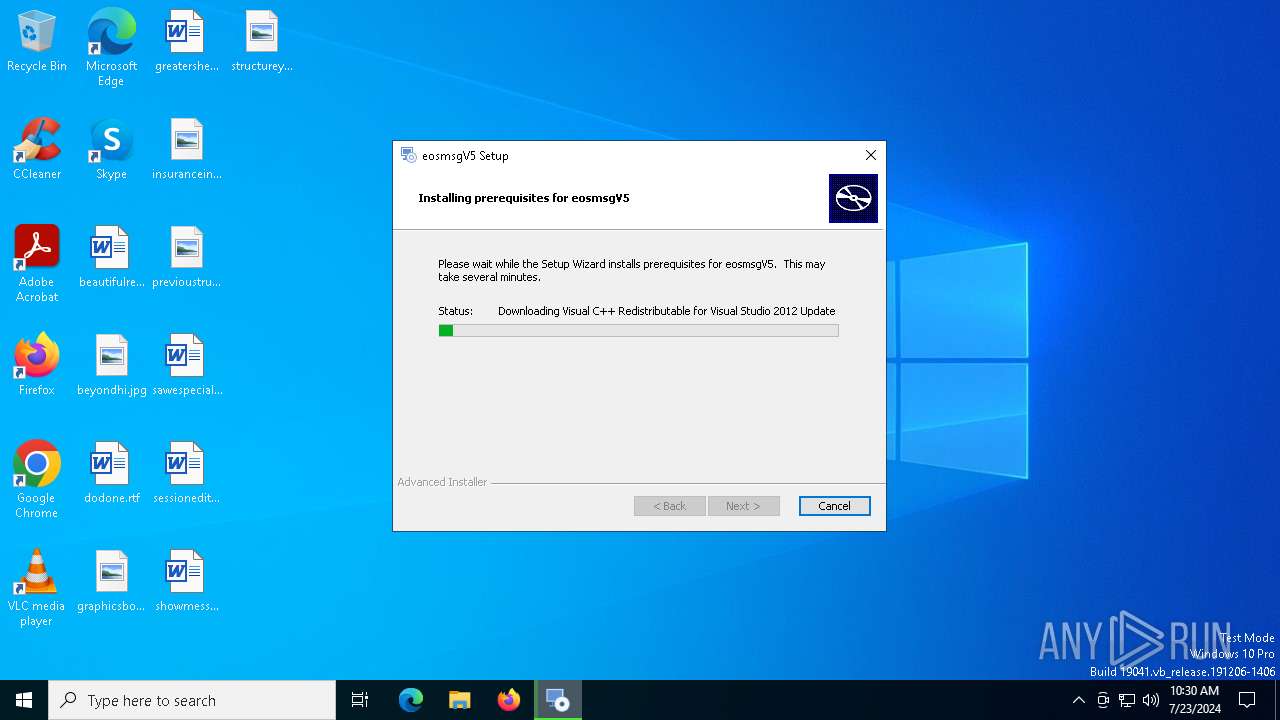
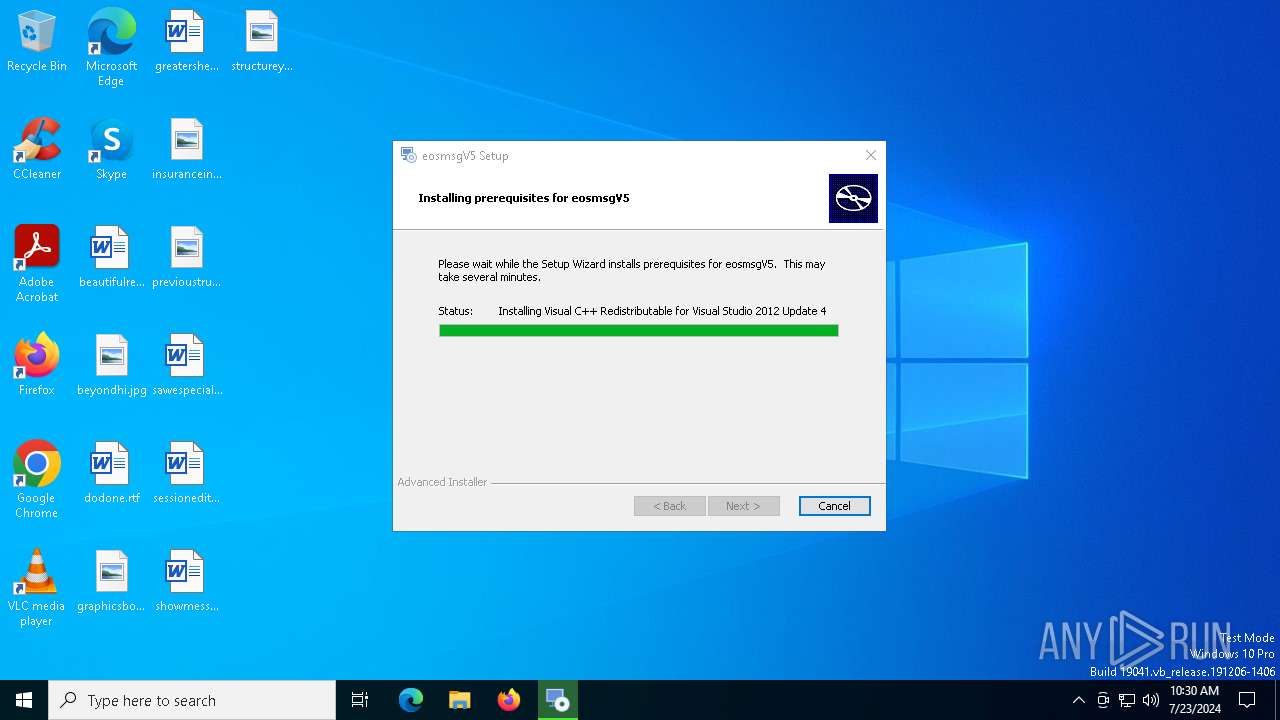
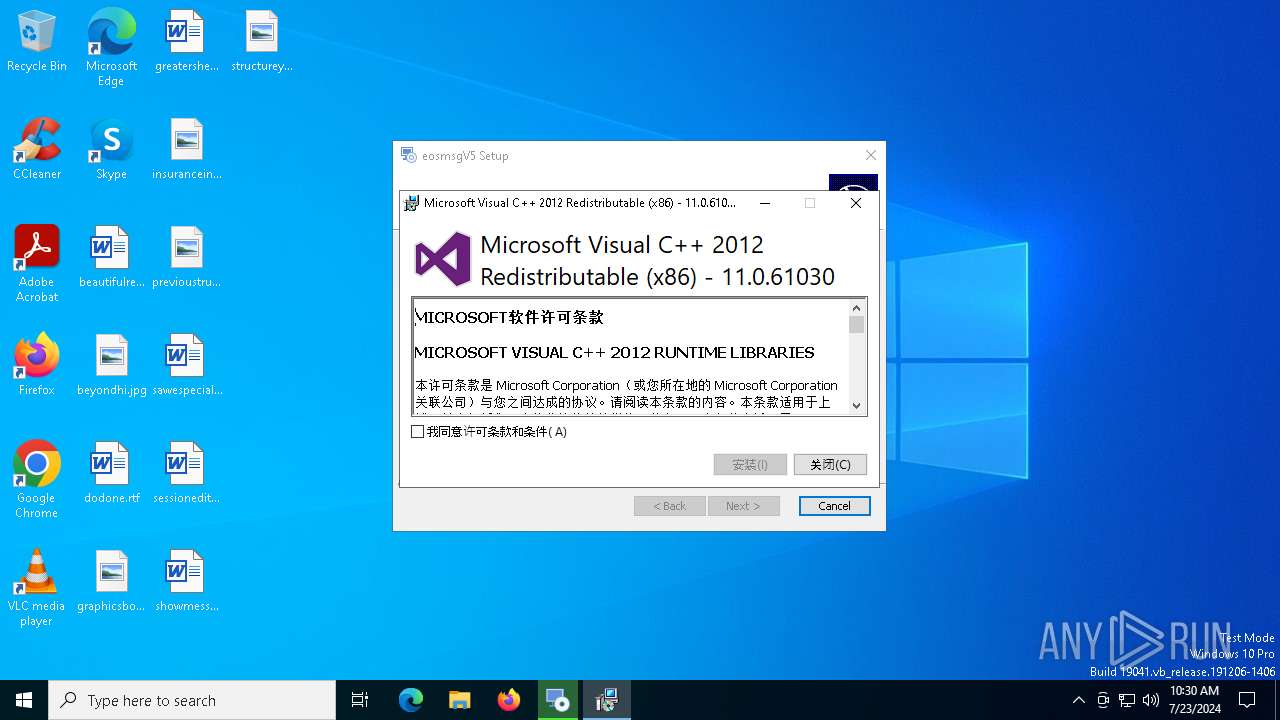
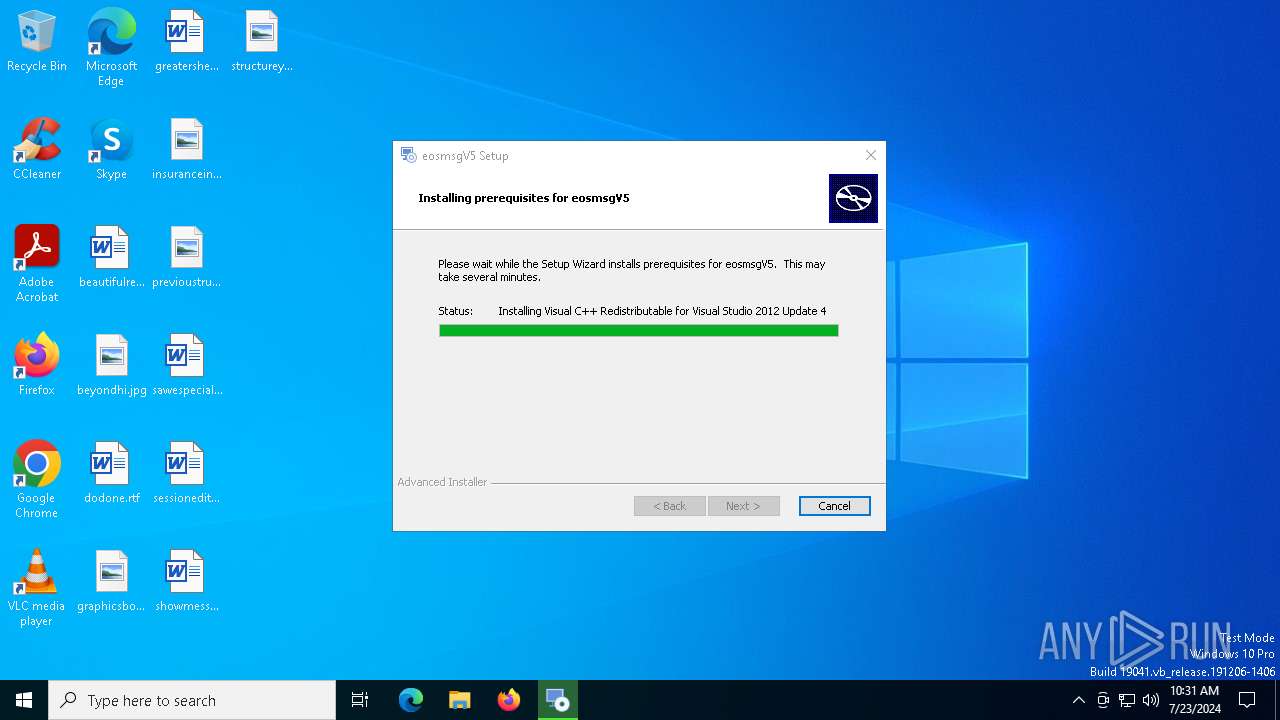
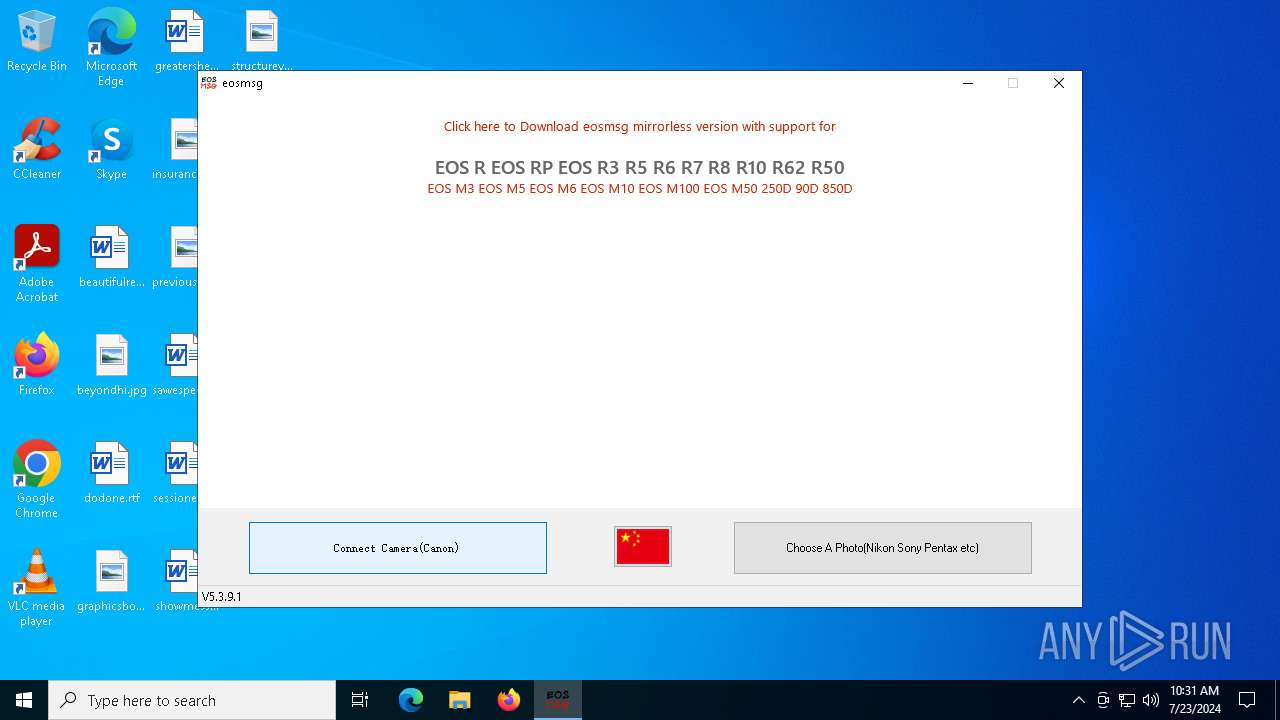
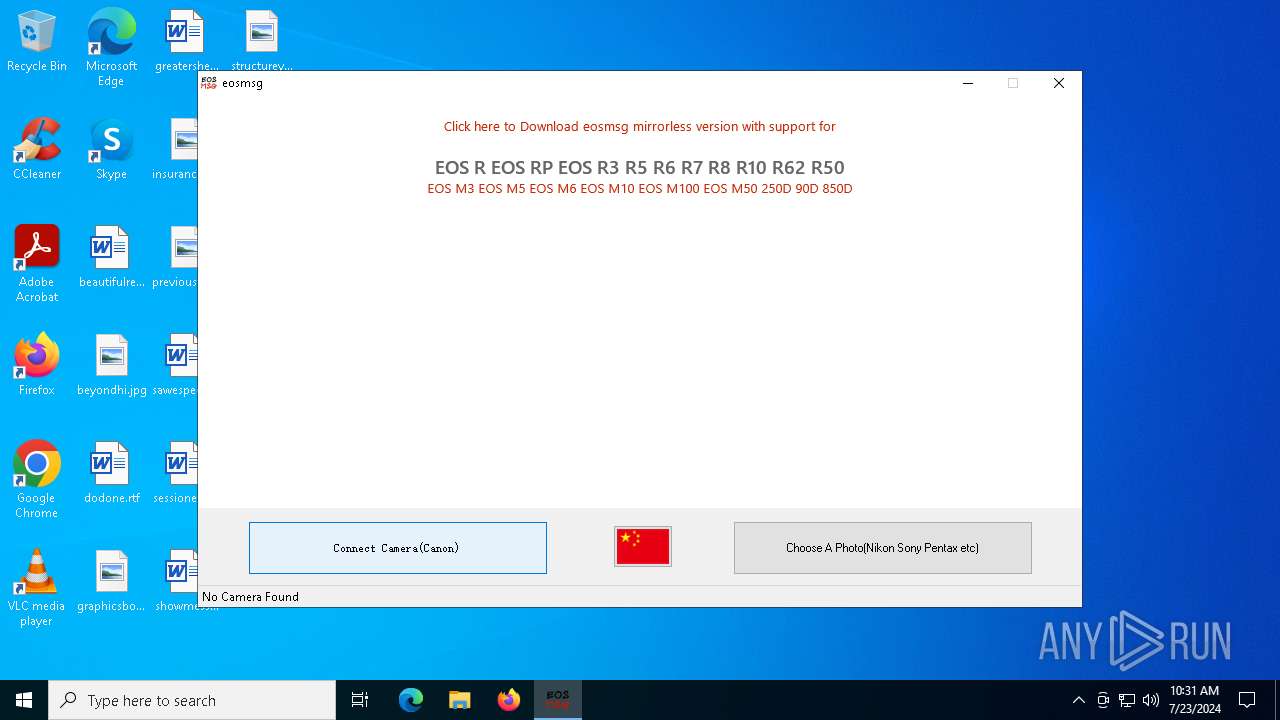
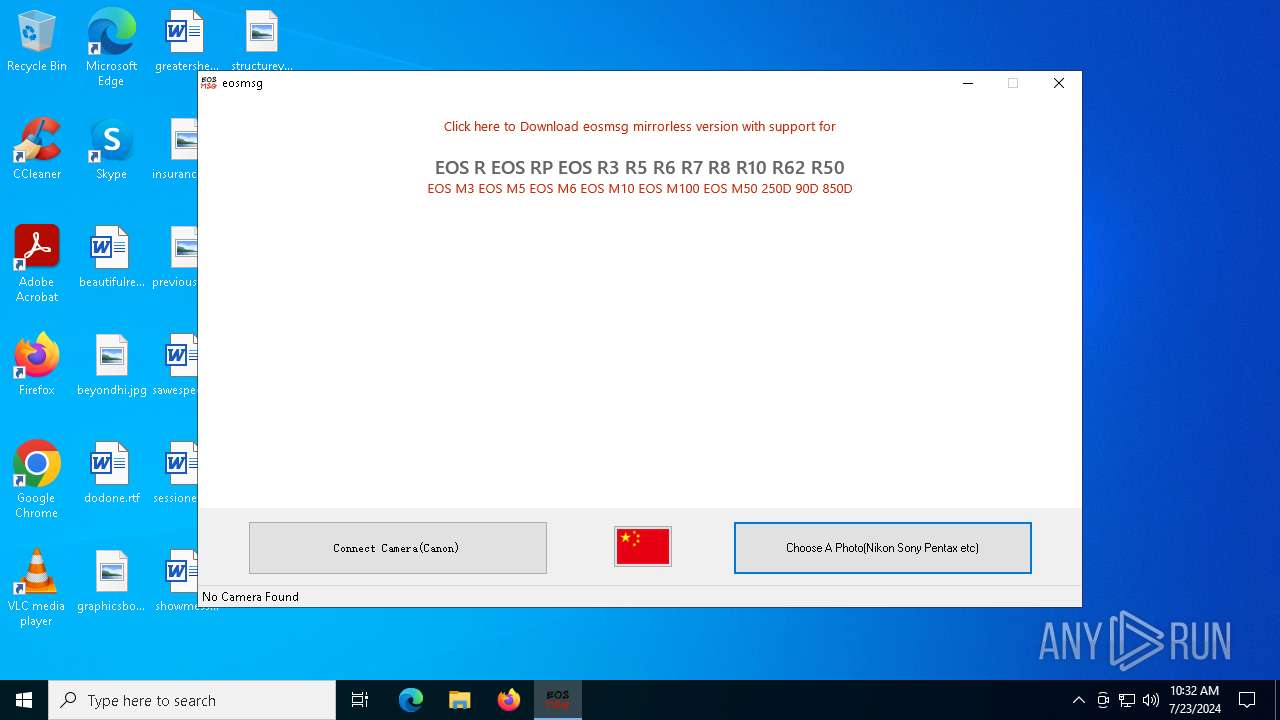
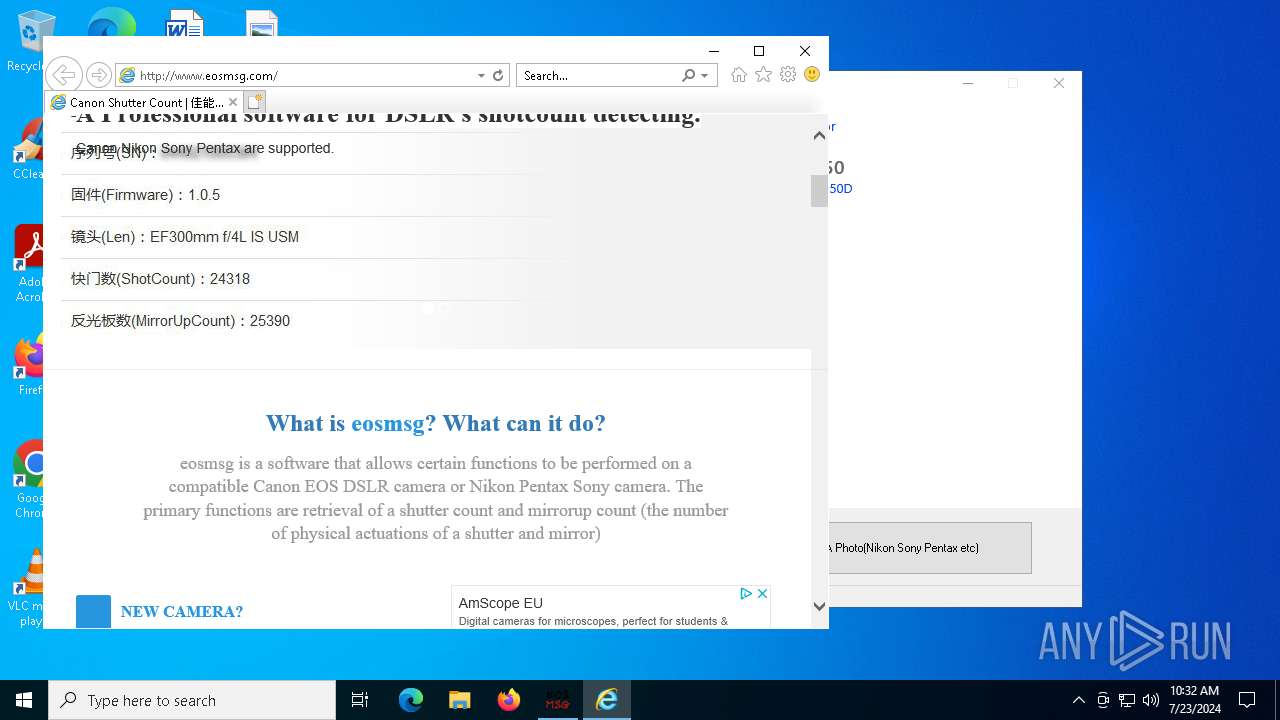
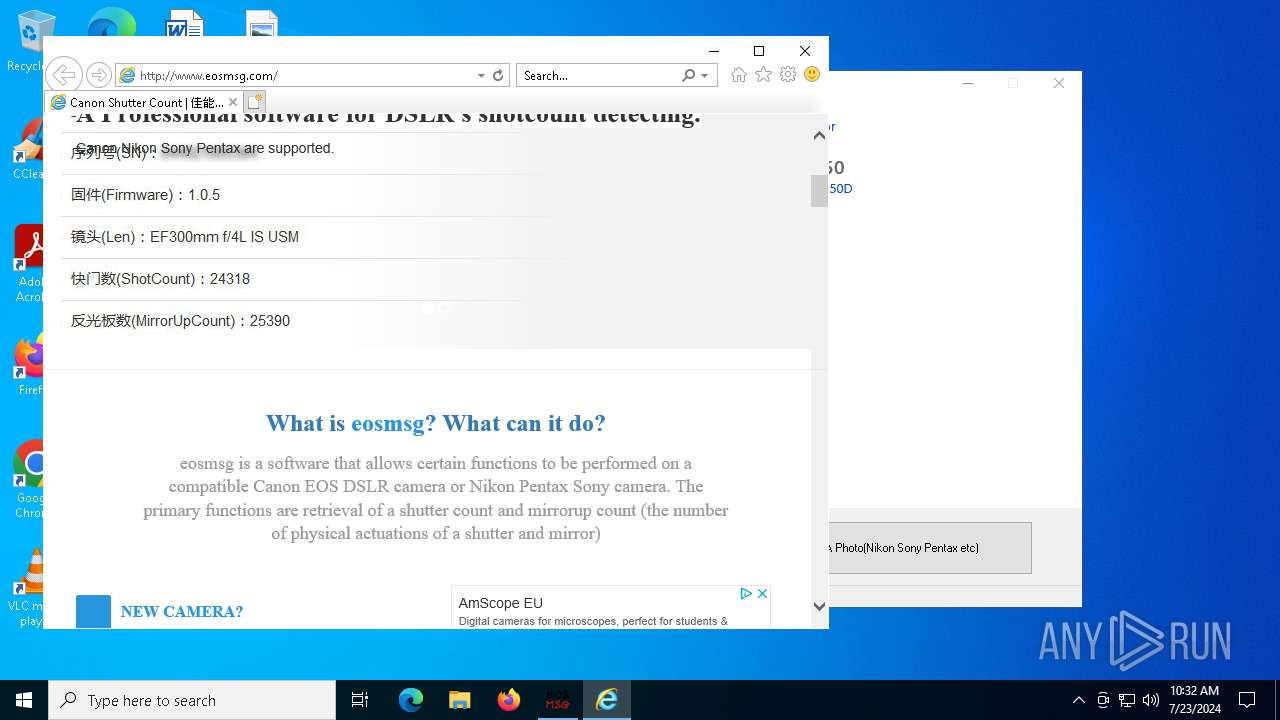
| File name: | eosmsg.exe |
| Full analysis: | https://app.any.run/tasks/06679e83-6368-44c9-b507-542a8f3348c5 |
| Verdict: | Malicious activity |
| Analysis date: | July 23, 2024, 10:30:20 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 410C352BCC8450296F66C7722CE259E4 |
| SHA1: | 9E6E8B67D8252B4C107BFD00CAC028DD80F065A1 |
| SHA256: | 8648D2B96B481F2B9815A39CAF128A13B08426E4C5A2BC0DB26A5F485DC71B1F |
| SSDEEP: | 98304:mcwRgT17K8714MmdAzKijHHCI00AYpO99NUD+vGx11yUpdPRxBBwv1a3N15uAwSL:+qPwCietDAVJU |
MALICIOUS
Drops the executable file immediately after the start
- eosmsg.exe (PID: 6484)
- vcredist_x86.exe (PID: 3204)
- vcredist_x86.exe (PID: 1256)
- msiexec.exe (PID: 6576)
- eosmsg.exe (PID: 2820)
Changes the autorun value in the registry
- eosmsg.exe (PID: 6484)
- vcredist_x86.exe (PID: 1256)
Scans artifacts that could help determine the target
- eosmsg.exe (PID: 2820)
SUSPICIOUS
Process drops legitimate windows executable
- eosmsg.exe (PID: 6484)
- vcredist_x86.exe (PID: 3204)
- vcredist_x86.exe (PID: 1256)
- msiexec.exe (PID: 6576)
Reads the Windows owner or organization settings
- eosmsg.exe (PID: 6484)
- msiexec.exe (PID: 6576)
Executable content was dropped or overwritten
- eosmsg.exe (PID: 6484)
- vcredist_x86.exe (PID: 3204)
- vcredist_x86.exe (PID: 1256)
- eosmsg.exe (PID: 2820)
Reads security settings of Internet Explorer
- eosmsg.exe (PID: 6484)
- vcredist_x86.exe (PID: 3204)
- vcredist_x86.exe (PID: 1256)
- eosmsg.exe (PID: 2820)
Checks Windows Trust Settings
- eosmsg.exe (PID: 6484)
- vcredist_x86.exe (PID: 1256)
- msiexec.exe (PID: 6576)
- eosmsg.exe (PID: 2820)
Reads the date of Windows installation
- eosmsg.exe (PID: 6484)
- vcredist_x86.exe (PID: 3204)
Searches for installed software
- vcredist_x86.exe (PID: 3204)
- dllhost.exe (PID: 2884)
- vcredist_x86.exe (PID: 1256)
Executes as Windows Service
- VSSVC.exe (PID: 6132)
Starts a Microsoft application from unusual location
- vcredist_x86.exe (PID: 1256)
Creates a software uninstall entry
- vcredist_x86.exe (PID: 1256)
The process creates files with name similar to system file names
- eosmsg.exe (PID: 2820)
Reads Microsoft Outlook installation path
- eosmsg.exe (PID: 2820)
Reads Internet Explorer settings
- eosmsg.exe (PID: 2820)
INFO
Creates files or folders in the user directory
- eosmsg.exe (PID: 6484)
- vcredist_x86.exe (PID: 1256)
- eosmsg.exe (PID: 2820)
Checks supported languages
- eosmsg.exe (PID: 6484)
- msiexec.exe (PID: 6576)
- msiexec.exe (PID: 7100)
- vcredist_x86.exe (PID: 1256)
- vcredist_x86.exe (PID: 3204)
- msiexec.exe (PID: 4052)
- eosmsg.exe (PID: 2820)
- msiexec.exe (PID: 7112)
- msiexec.exe (PID: 1320)
- ielowutil.exe (PID: 5836)
Reads Environment values
- eosmsg.exe (PID: 6484)
- msiexec.exe (PID: 7100)
- msiexec.exe (PID: 1320)
- msiexec.exe (PID: 7112)
Reads the computer name
- eosmsg.exe (PID: 6484)
- msiexec.exe (PID: 6576)
- msiexec.exe (PID: 7100)
- vcredist_x86.exe (PID: 3204)
- vcredist_x86.exe (PID: 1256)
- msiexec.exe (PID: 4052)
- msiexec.exe (PID: 1320)
- eosmsg.exe (PID: 2820)
- msiexec.exe (PID: 7112)
- ielowutil.exe (PID: 5836)
Create files in a temporary directory
- eosmsg.exe (PID: 6484)
- vcredist_x86.exe (PID: 3204)
- vcredist_x86.exe (PID: 1256)
Checks proxy server information
- eosmsg.exe (PID: 6484)
- vcredist_x86.exe (PID: 1256)
- slui.exe (PID: 1428)
- eosmsg.exe (PID: 2820)
Reads the machine GUID from the registry
- eosmsg.exe (PID: 6484)
- vcredist_x86.exe (PID: 1256)
- msiexec.exe (PID: 6576)
- eosmsg.exe (PID: 2820)
Reads the software policy settings
- eosmsg.exe (PID: 6484)
- vcredist_x86.exe (PID: 1256)
- msiexec.exe (PID: 6576)
- slui.exe (PID: 1428)
- eosmsg.exe (PID: 2820)
Process checks computer location settings
- eosmsg.exe (PID: 6484)
- vcredist_x86.exe (PID: 3204)
Creates files in the program directory
- vcredist_x86.exe (PID: 1256)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6576)
- msiexec.exe (PID: 1392)
Creates a software uninstall entry
- msiexec.exe (PID: 6576)
Drops the executable file immediately after the start
- msiexec.exe (PID: 1392)
Manual execution by a user
- eosmsg.exe (PID: 7084)
- eosmsg.exe (PID: 2820)
Process checks Internet Explorer phishing filters
- eosmsg.exe (PID: 2820)
.NET Reactor protector has been detected
- eosmsg.exe (PID: 2820)
Process checks whether UAC notifications are on
- eosmsg.exe (PID: 2820)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:10:18 09:57:08+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.33 |
| CodeSize: | 2438144 |
| InitializedDataSize: | 904704 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1ce346 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.3.9.1 |
| ProductVersionNumber: | 5.3.9.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | eosmsg |
| FileDescription: | eosmsgV5 Installer |
| FileVersion: | 5.3.9.1 |
| InternalName: | eosmsgV5 |
| LegalCopyright: | Copyright (C) 2023 eosmsg |
| OriginalFileName: | eosmsgV5.exe |
| ProductName: | eosmsgV5 |
| ProductVersion: | 5.3.9.1 |
Total processes
160
Monitored processes
21
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1256 | "C:\Users\admin\AppData\Local\Temp\{a55ac379-46b0-461a-95b1-fef5c08443f2}\.be\vcredist_x86.exe" -q -burn.elevated BurnPipe.{DA30B676-F22B-40FA-A648-9F8DC6320C7A} {5D50104F-737B-4F1A-BF2A-C3A0D4C5E44A} 3204 | C:\Users\admin\AppData\Local\Temp\{a55ac379-46b0-461a-95b1-fef5c08443f2}\.be\vcredist_x86.exe | vcredist_x86.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2012 Redistributable (x86) - 11.0.61030 Exit code: 0 Version: 11.0.61030.0 Modules
| |||||||||||||||
| 1320 | C:\Windows\syswow64\MsiExec.exe -Embedding E01BB7EF33E35CEF6D793553A754048C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1392 | "C:\WINDOWS\system32\msiexec.exe" /i "C:\Users\admin\AppData\Roaming\eosmsg\eosmsgV5 5.3.9.1\install\B7E5171\eosmsgV5.msi" AI_SETUPEXEPATH=C:\Users\admin\AppData\Local\Temp\eosmsg.exe SETUPEXEDIR=C:\Users\admin\AppData\Local\Temp\ EXE_CMD_LINE="/exenoupdates /forcecleanup /wintime 1721729704 " AI_MISSING_PREREQS="Visual C++ Redistributable for Visual Studio 2012 Update 4 x86" | C:\Windows\SysWOW64\msiexec.exe | eosmsg.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1428 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1432 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:12 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1476 | "C:\Program Files\Internet Explorer\iexplore.exe" -startmediumtab -Embedding | C:\Program Files\Internet Explorer\iexplore.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2820 | "C:\Program Files (x86)\eosmsg\eosmsgV5\eosmsg.exe" | C:\Program Files (x86)\eosmsg\eosmsgV5\eosmsg.exe | explorer.exe | ||||||||||||
User: admin Company: ShenZhen CammsG CO.LTD Integrity Level: HIGH Description: eosmsg Version: 5.3.9.1 Modules
| |||||||||||||||
| 2884 | C:\WINDOWS\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3204 | "C:\Users\admin\AppData\Roaming\eosmsg\eosmsgV5\prerequisites\Visual C++ Redistributable for Visual Studio 2012\vcredist_x86.exe" | C:\Users\admin\AppData\Roaming\eosmsg\eosmsgV5\prerequisites\Visual C++ Redistributable for Visual Studio 2012\vcredist_x86.exe | eosmsg.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Visual C++ 2012 Redistributable (x86) - 11.0.61030 Exit code: 0 Version: 11.0.61030.0 Modules
| |||||||||||||||
| 4052 | C:\Windows\syswow64\MsiExec.exe -Embedding C24D837AA79C0C57AAD358F55BE06300 C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
36 159
Read events
35 179
Write events
909
Delete events
71
Modification events
| (PID) Process: | (6484) eosmsg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6484) eosmsg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6484) eosmsg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6484) eosmsg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6484) eosmsg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | C__Users_admin_AppData_Local_Temp_eosmsg.exe |
Value: C:\Users\admin\AppData\Local\Temp\eosmsg.exe /exenoupdates /forcecleanup /wintime 1721729704 /exelang 1033 /prereqs "1" | |||
| (PID) Process: | (3204) vcredist_x86.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3204) vcredist_x86.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3204) vcredist_x86.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3204) vcredist_x86.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1256) vcredist_x86.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000F3D7686AEBDCDA01E8040000B0060000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
60
Suspicious files
102
Text files
80
Unknown types
24
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6484 | eosmsg.exe | C:\Users\admin\AppData\Roaming\eosmsg\eosmsgV5 5.3.9.1\install\holder0.aiph | — | |
MD5:— | SHA256:— | |||
| 6484 | eosmsg.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_6484\dialog.jpg | image | |
MD5:ABF1076064505DEE794FA7AED67252B8 | SHA256:FB0D133F05DE6AA6A7A3491AE532191A60C438B35D9FF7BFEC9E63131F6F0C73 | |||
| 6484 | eosmsg.exe | C:\Users\admin\AppData\Roaming\eosmsg\eosmsgV5 5.3.9.1\install\B7E5171\eosmsgV5.msi | executable | |
MD5:588DF0BEA72D627C9264679ACFD4E490 | SHA256:BBCE34E5809E580E58ABB0E578EC962A44AEEC1A3E944BCA8A1BE60D48156D24 | |||
| 6484 | eosmsg.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_6484\Up | image | |
MD5:FD64F54DB4CBF736A6FC0D7049F5991E | SHA256:C269353D19D50E2688DB102FEF8226CA492DB17133043D7EB5420EE8542D571C | |||
| 6484 | eosmsg.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_6484\exclamic | image | |
MD5:3FBB7DDBC13EDF109E3ACAA7A4A69A4E | SHA256:F8429073C7A83377AD754824B0B81040D68F8C1350A82FF4DCCF8BC4BF31F177 | |||
| 6484 | eosmsg.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_6484\custicon | image | |
MD5:BE6D2F48AA6634FB2101C273C798D4D9 | SHA256:0E22BC2BF7184DFDB55223A11439304A453FB3574E3C9034A6497AF405C628EF | |||
| 6484 | eosmsg.exe | C:\Users\admin\AppData\Local\Temp\shi1FE7.tmp | executable | |
MD5:84A34BF3486F7B9B7035DB78D78BDD1E | SHA256:F85911C910B660E528D2CF291BAA40A92D09961996D6D84E7A53A7095C7CD96E | |||
| 6484 | eosmsg.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_6484\repairic | image | |
MD5:915E40A576FA41DC5F8486103341673E | SHA256:BF21B2BC3E7253968405F3D244CDB1C136672A5BDB088B524A333264898A2D11 | |||
| 6484 | eosmsg.exe | C:\Users\admin\AppData\Local\Temp\MSI2046.tmp | executable | |
MD5:53EBDF6BC20011120B06E94DE66ADC51 | SHA256:997B258B3F6DD1448FD4D135A56C138813F45F728E57BE0EB1908DF5B68F031B | |||
| 6484 | eosmsg.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_6484\completi | image | |
MD5:C23AF89757665BC0386FD798A61B2112 | SHA256:031ED0378F819926D7B5B2C6C9367A0FB1CBAE40E1A3959E2652FE30A47D52F2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
40
TCP/UDP connections
116
DNS requests
57
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1256 | vcredist_x86.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | — | — | whitelisted |
6484 | eosmsg.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 106.225.241.86:80 | http://s11.cnzz.com/stat.php?id=4579601&web_id=4579601 | unknown | — | — | whitelisted |
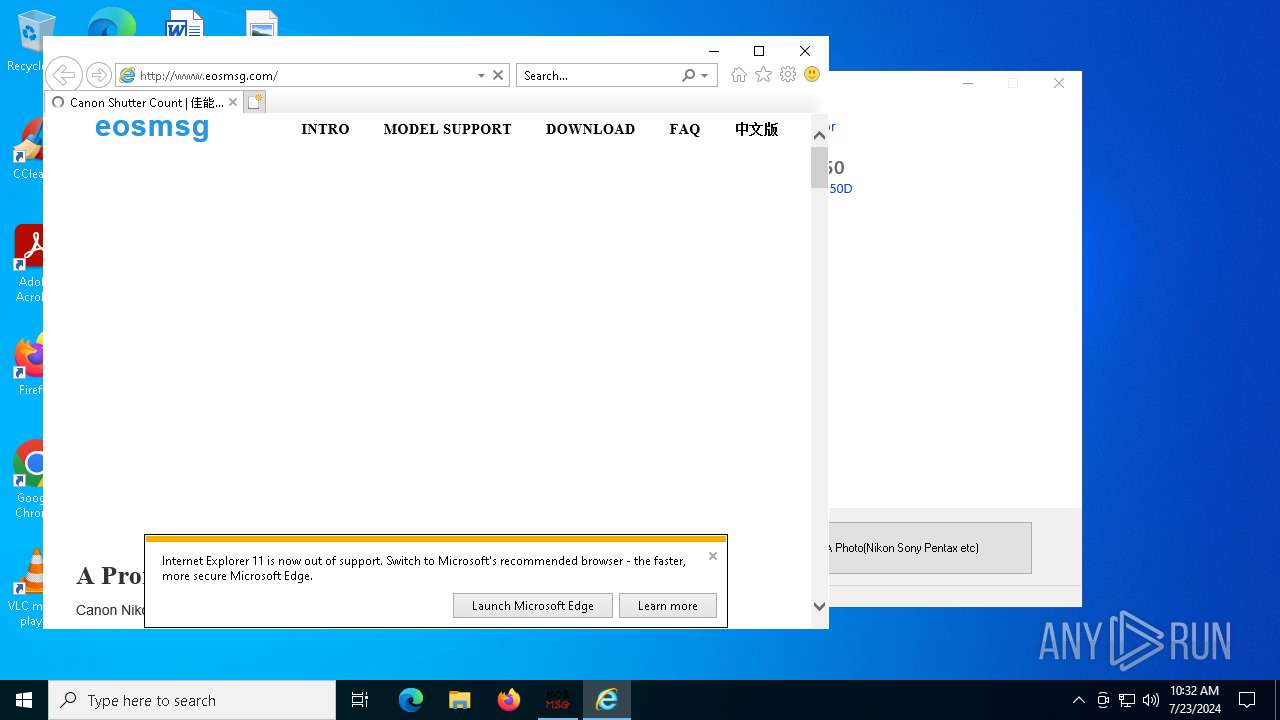
— | — | GET | 200 | 47.52.192.28:80 | http://www.eosmsg.com/css/blog-single.css | unknown | — | — | malicious |
— | — | GET | 200 | 47.52.192.28:80 | http://www.eosmsg.com/css/style.css | unknown | — | — | malicious |
— | — | GET | 200 | 47.52.192.28:80 | http://www.eosmsg.com/css/responsive.css | unknown | — | — | malicious |
— | — | GET | 200 | 47.52.192.28:80 | http://www.eosmsg.com/js/jquery.js | unknown | — | — | malicious |
1256 | vcredist_x86.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_08-31-2010.crl | unknown | — | — | whitelisted |
1256 | vcredist_x86.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | — | — | whitelisted |
2820 | eosmsg.exe | GET | 200 | 47.52.192.28:80 | http://www.eosmsg.com/styles/site.css | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 2.20.142.181:443 | — | Akamai International B.V. | DE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6012 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6184 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4204 | svchost.exe | 4.209.32.67:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
5368 | SearchApp.exe | 2.20.142.181:443 | — | Akamai International B.V. | DE | unknown |
5272 | svchost.exe | 20.190.159.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
7084 | backgroundTaskHost.exe | 2.20.142.181:443 | — | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
download.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |