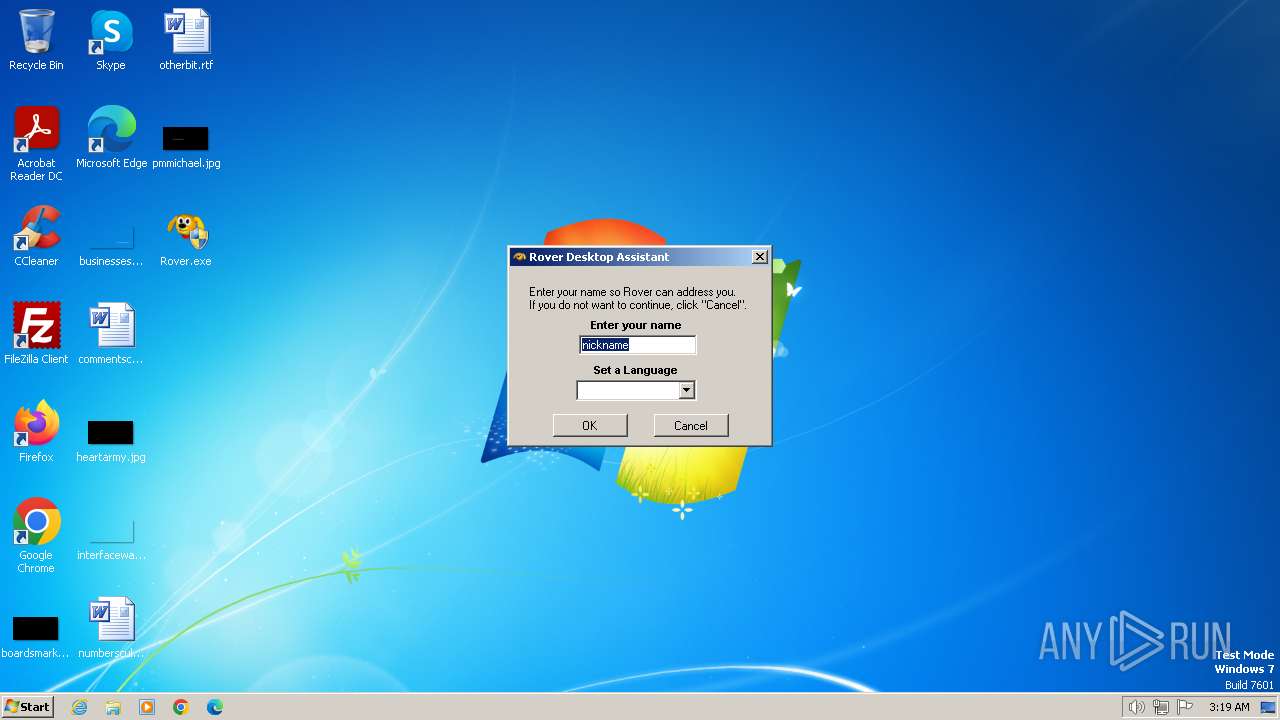
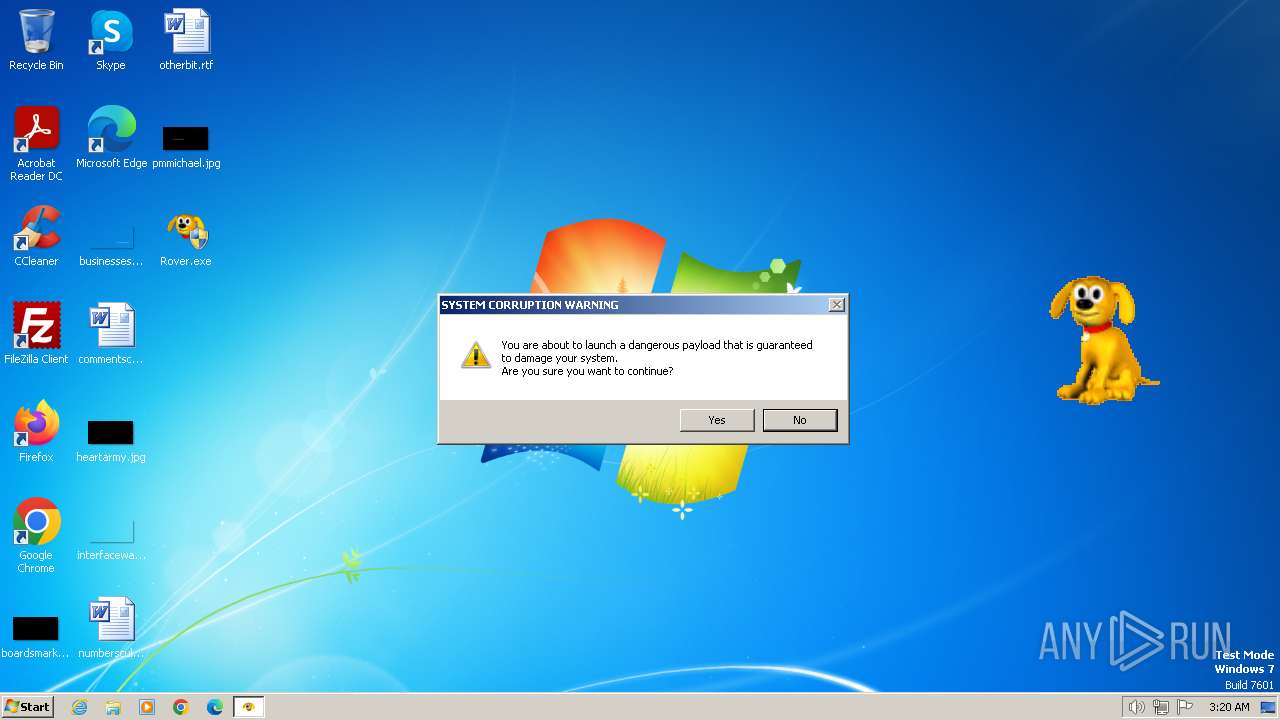
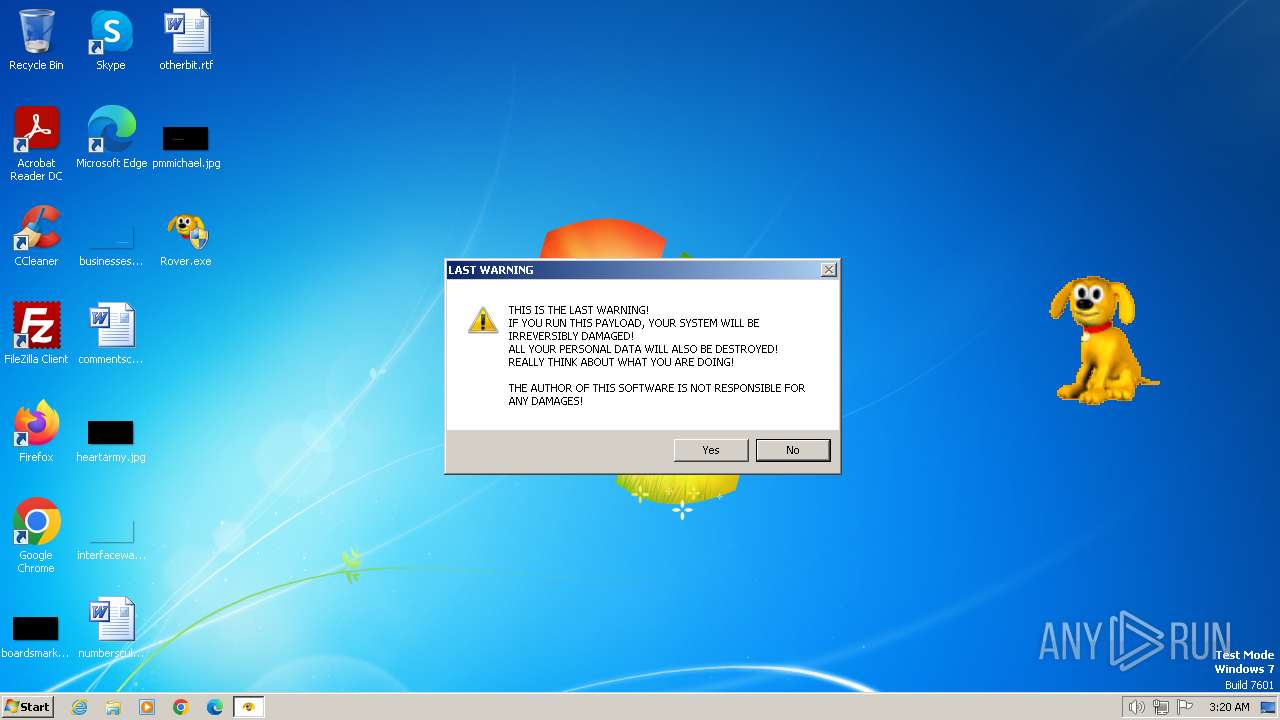
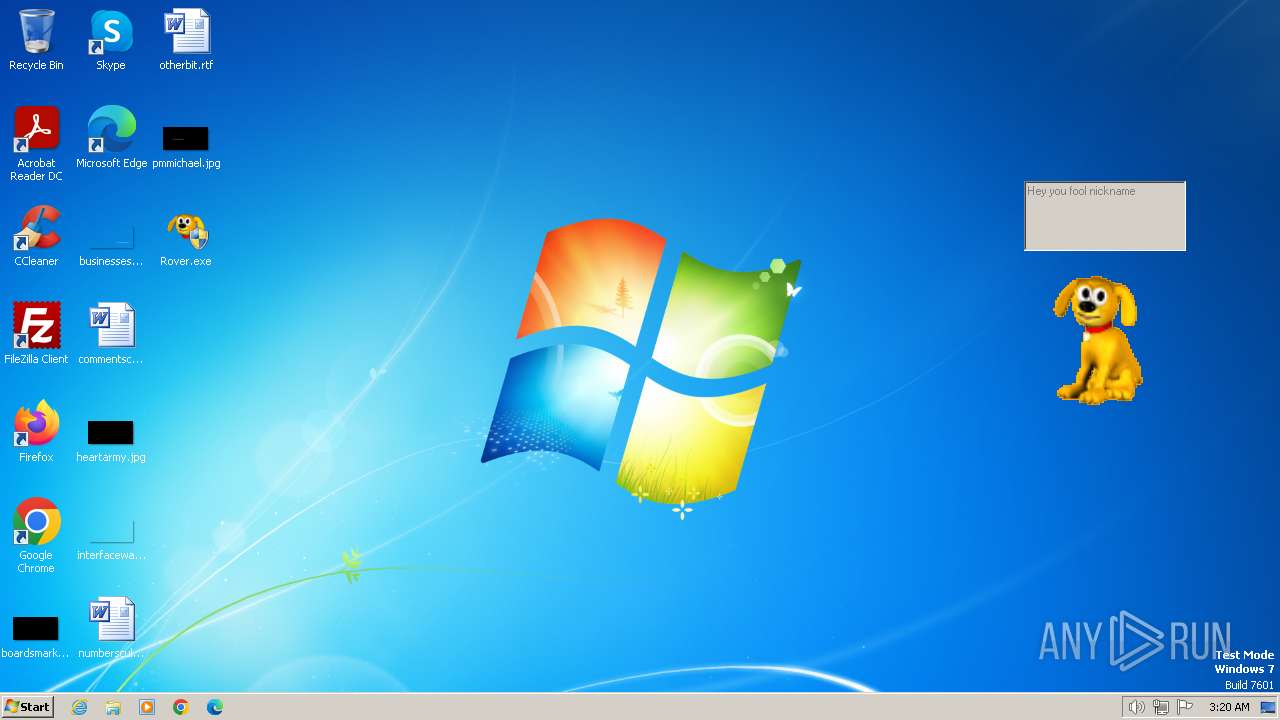
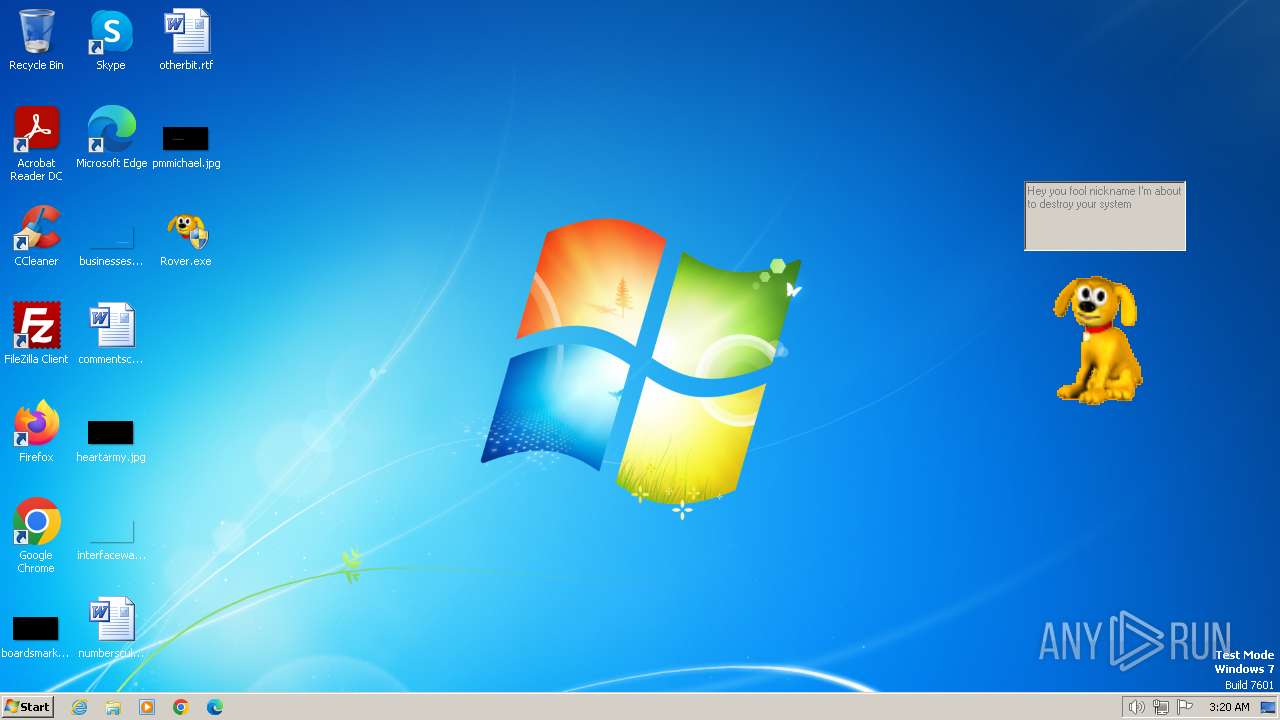
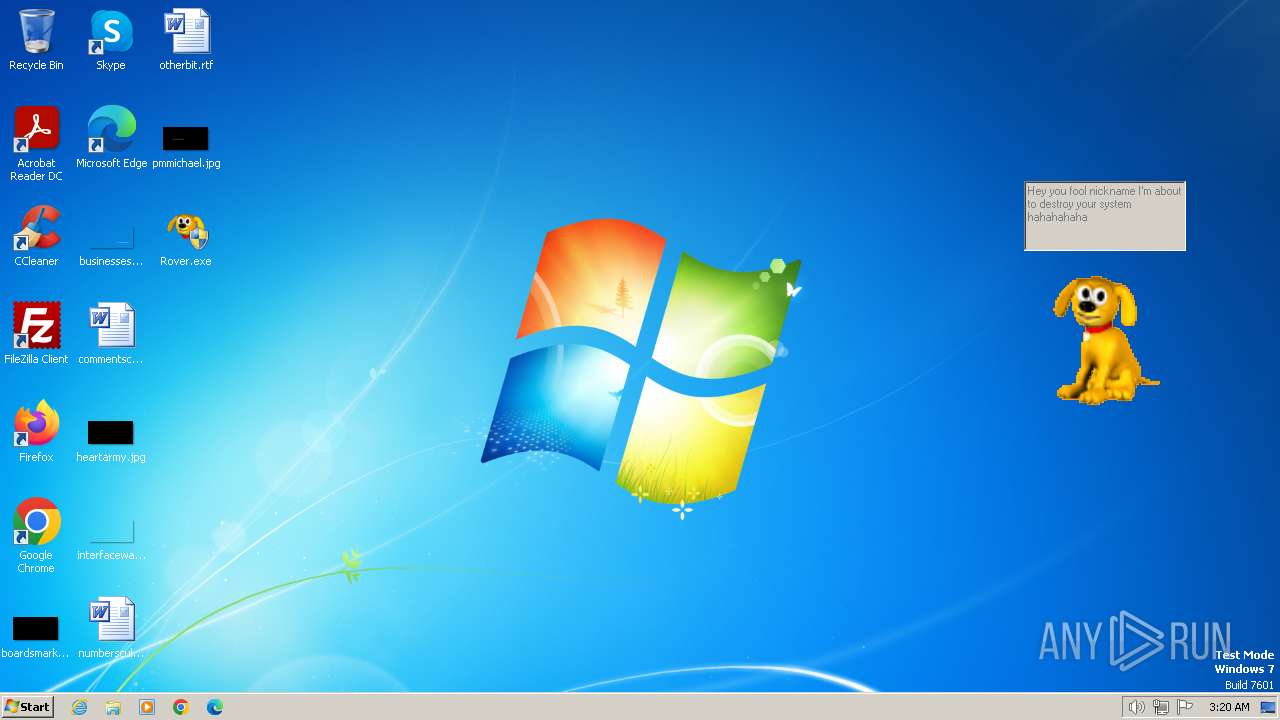
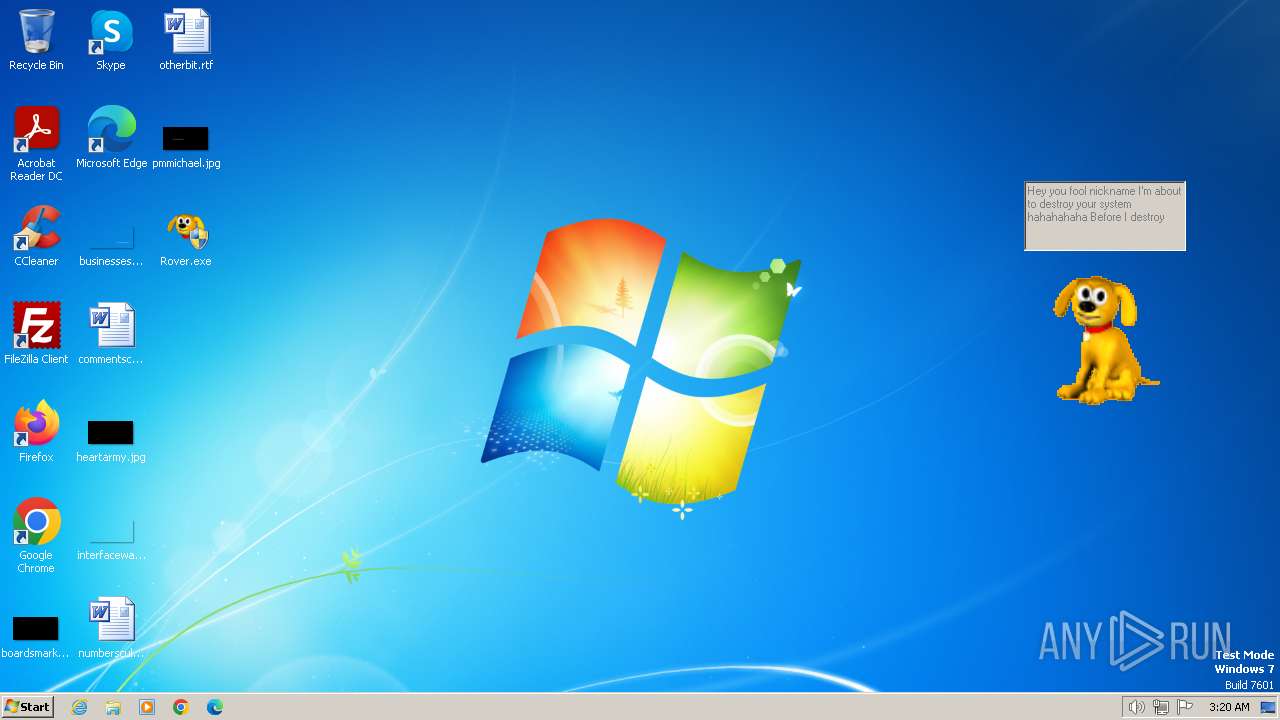
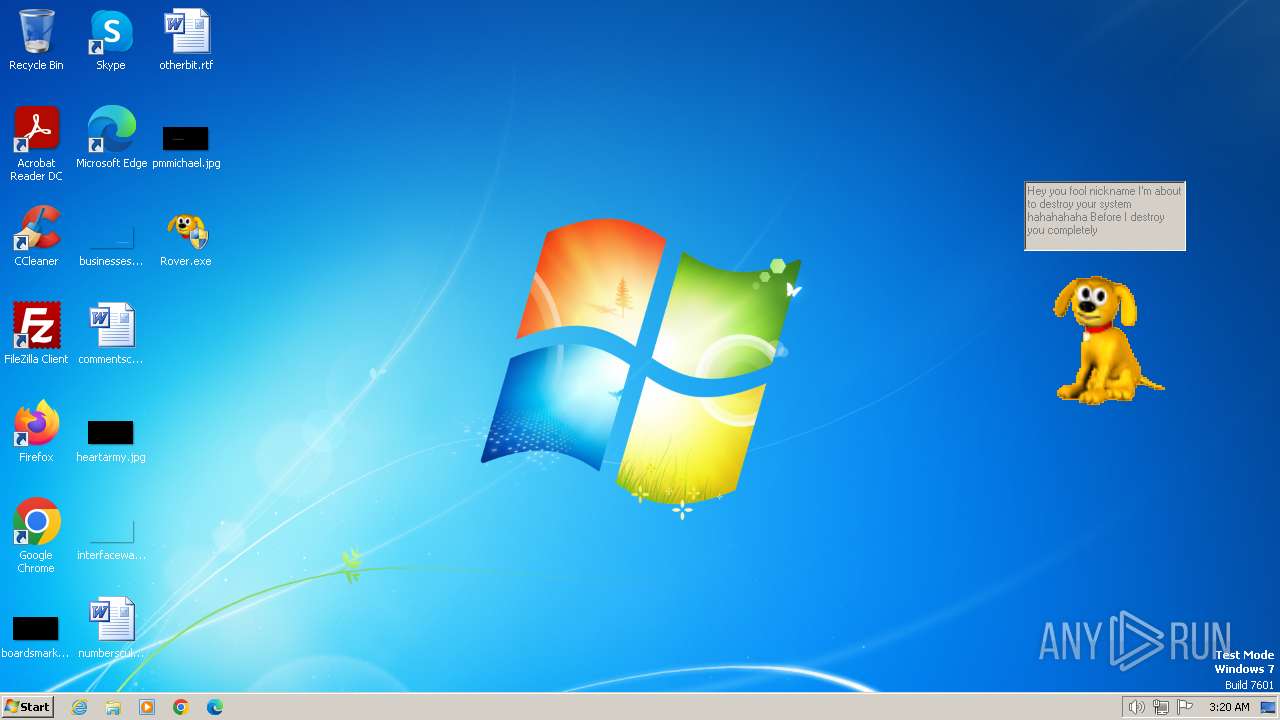
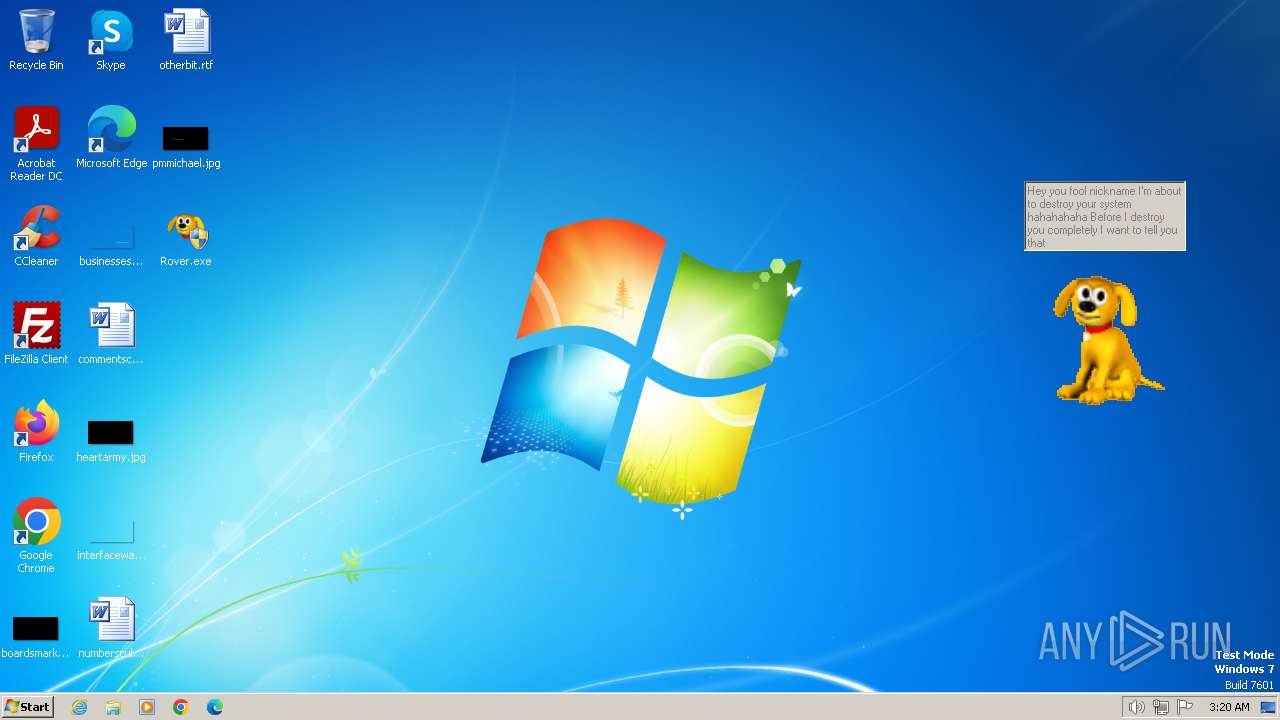
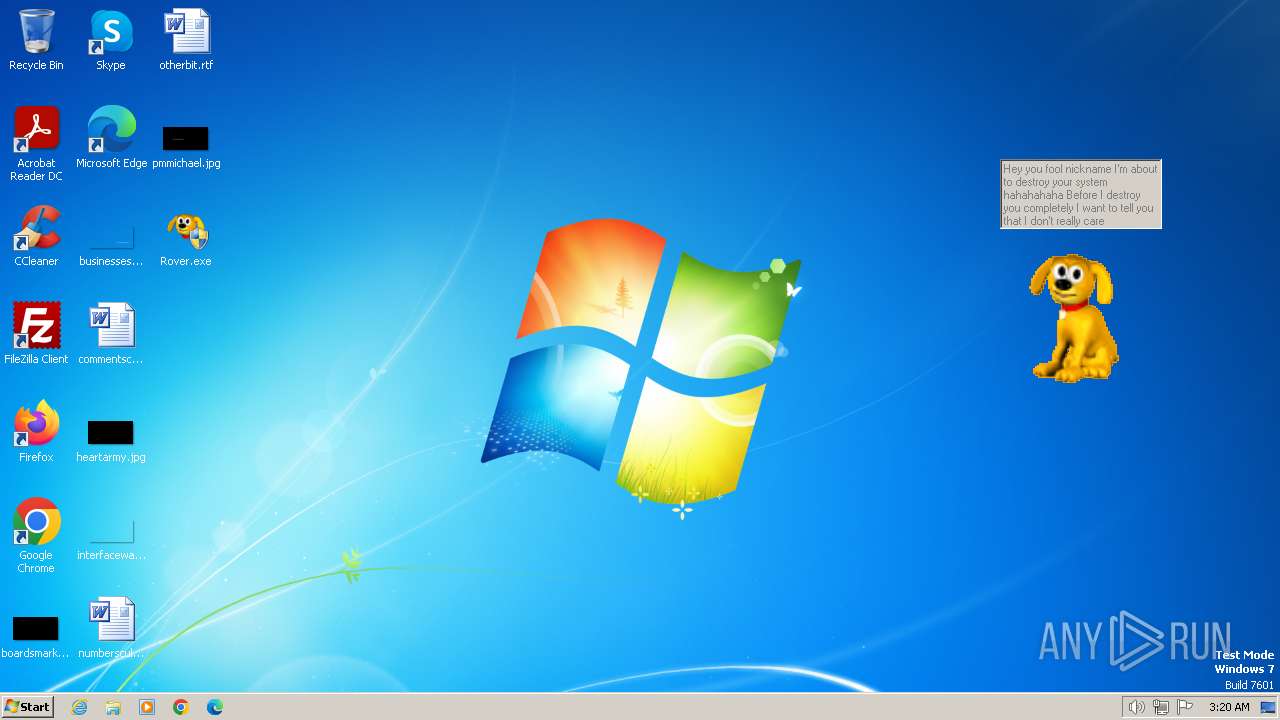
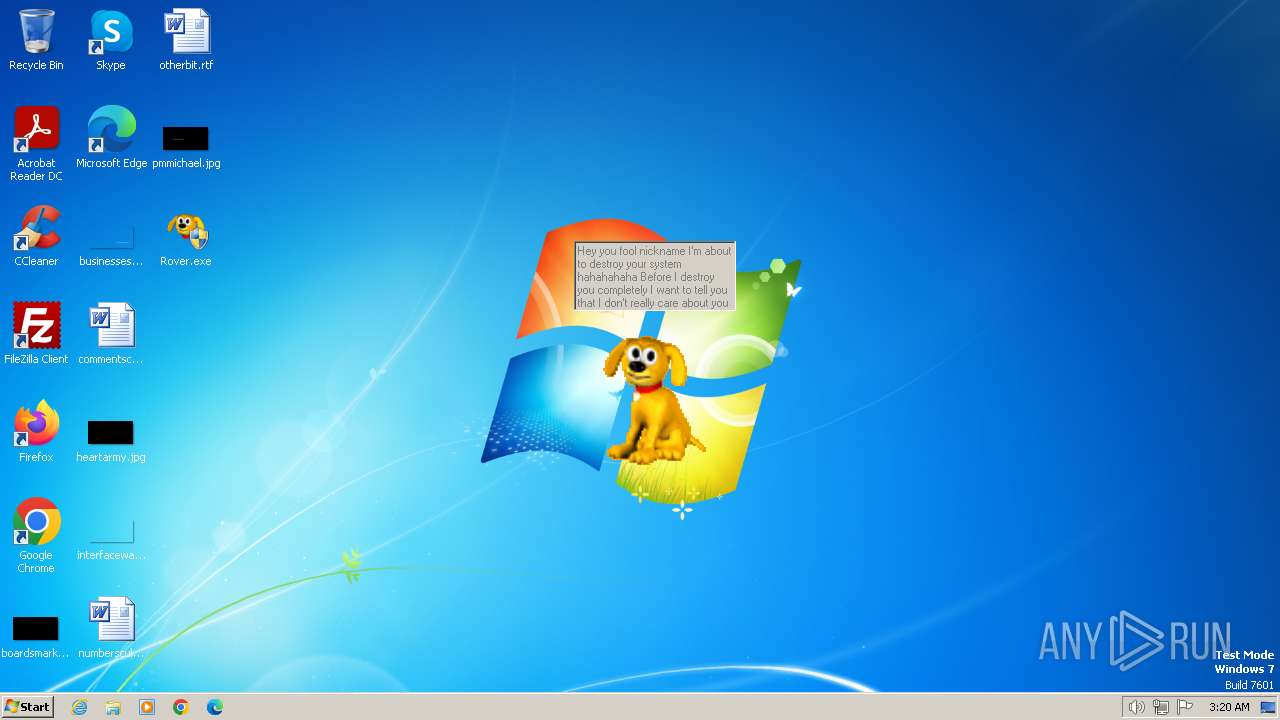
| File name: | Rover.exe |
| Full analysis: | https://app.any.run/tasks/5fd49cd6-387b-46cb-9de2-f7be1d685905 |
| Verdict: | Malicious activity |
| Analysis date: | February 13, 2024, 03:18:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 63D052B547C66AC7678685D9F3308884 |
| SHA1: | A6E42E6A86E3FF9FEC137C52B1086EE140A7B242 |
| SHA256: | 8634E9241729F16A8C2C23D5C184384815B97026E3D1A2D6DD0DDC825B142ABA |
| SSDEEP: | 98304:Oapmon4QzApS9hNQdrhEYzOi85kXNjMcDPWDnkE3DJ910Fx5mwAbguuwS09Fo:OQhn5EQ9hNQAYzA5k6cTWDn7JKObS09u |
MALICIOUS
Drops the executable file immediately after the start
- Rover.exe (PID: 3772)
Changes the login/logoff helper path in the registry
- Rover.exe (PID: 3772)
UAC/LUA settings modification
- Rover.exe (PID: 3772)
SUSPICIOUS
Executable content was dropped or overwritten
- Rover.exe (PID: 3772)
INFO
Checks supported languages
- Rover.exe (PID: 3772)
Reads the computer name
- Rover.exe (PID: 3772)
Reads the machine GUID from the registry
- Rover.exe (PID: 3772)
Process checks whether UAC notifications are on
- Rover.exe (PID: 3772)
Creates files in the program directory
- Rover.exe (PID: 3772)
Creates files or folders in the user directory
- Rover.exe (PID: 3772)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:07:13 22:47:16+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 104448 |
| InitializedDataSize: | 5268992 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xcd2f |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | Desktop Assistant |
| CompanyName: | - |
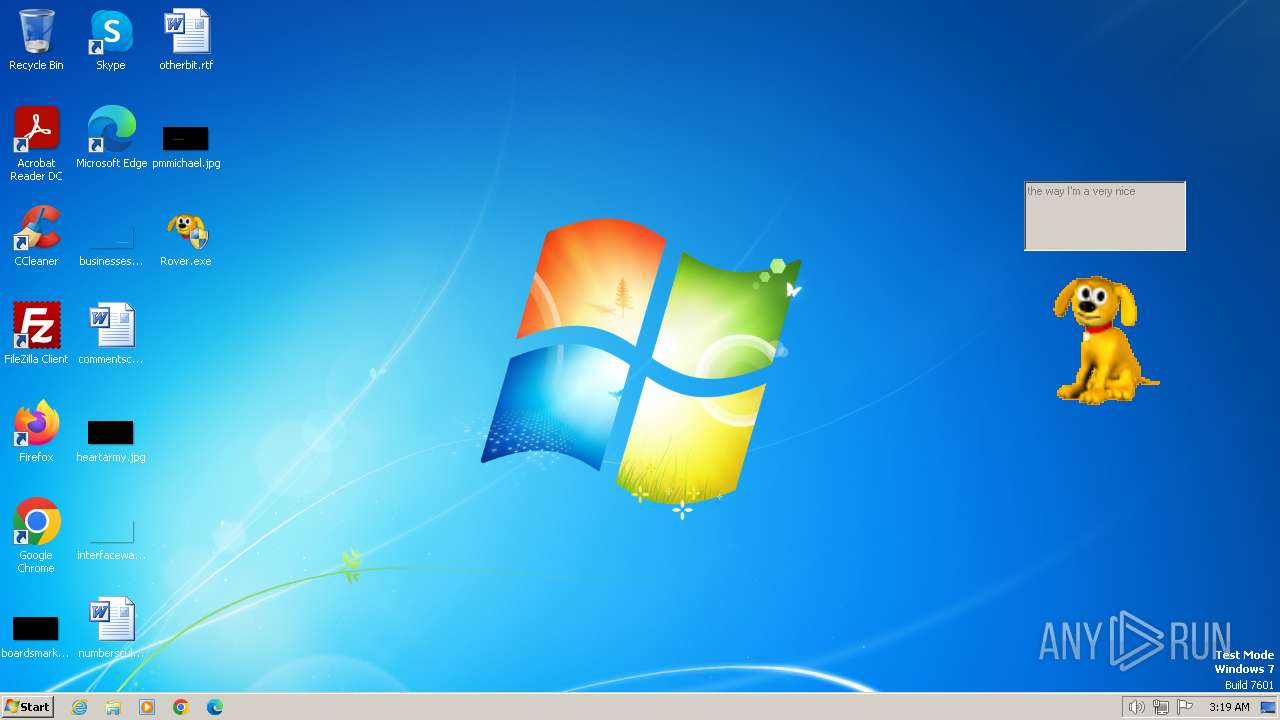
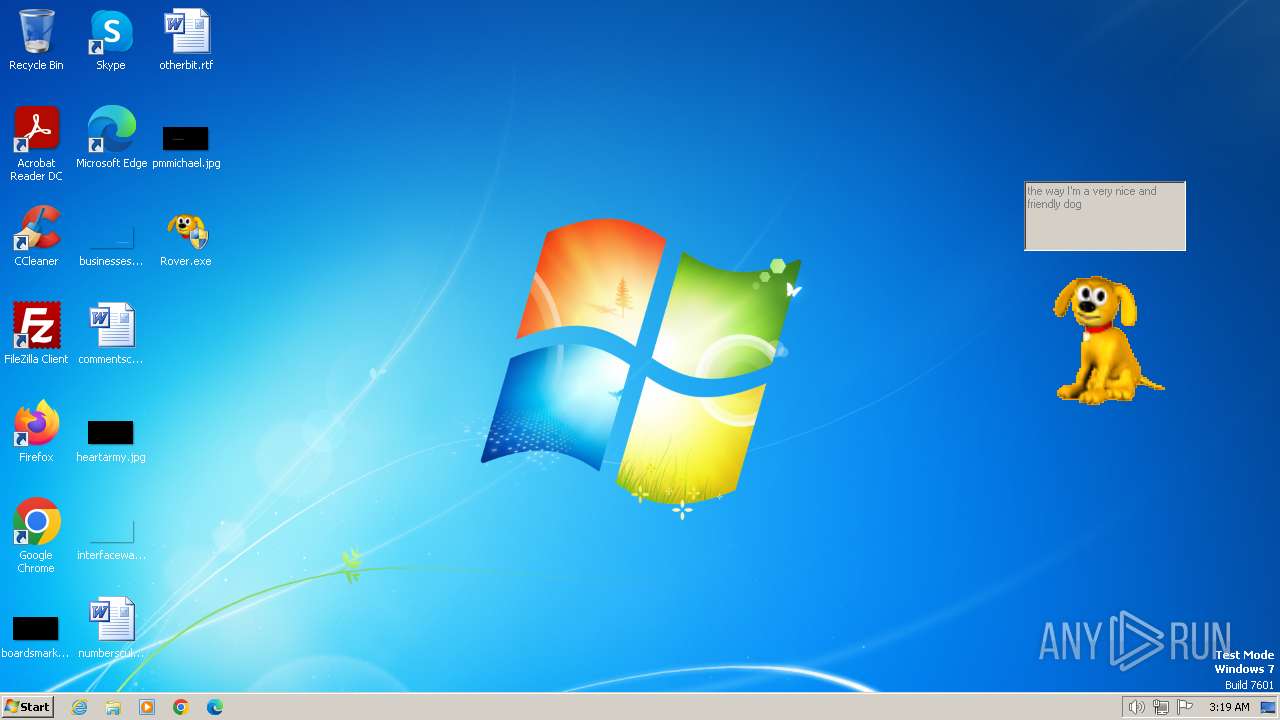
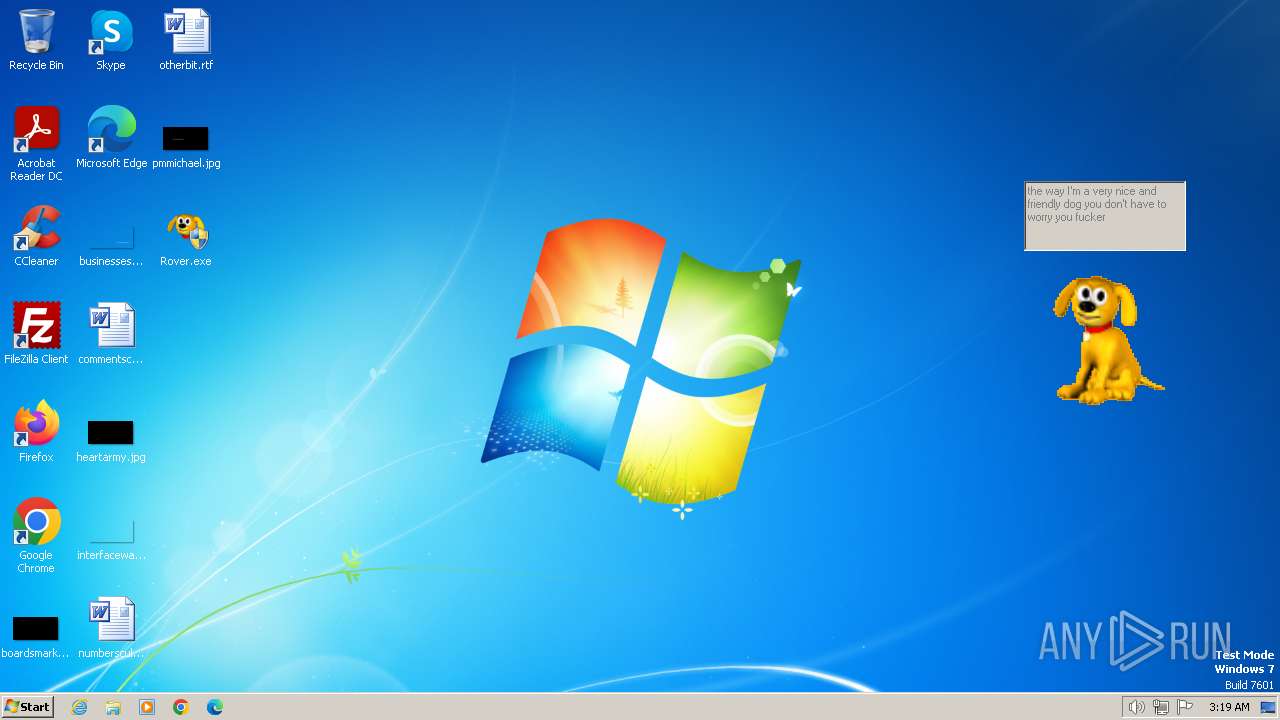
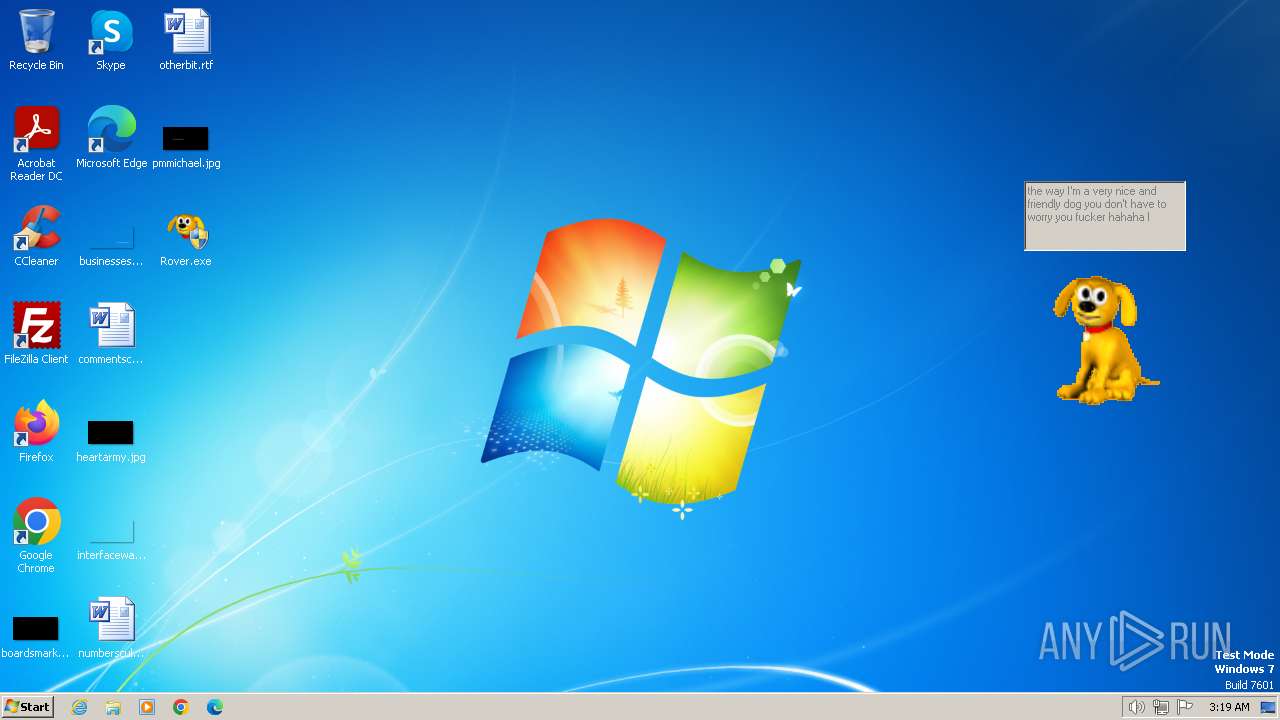
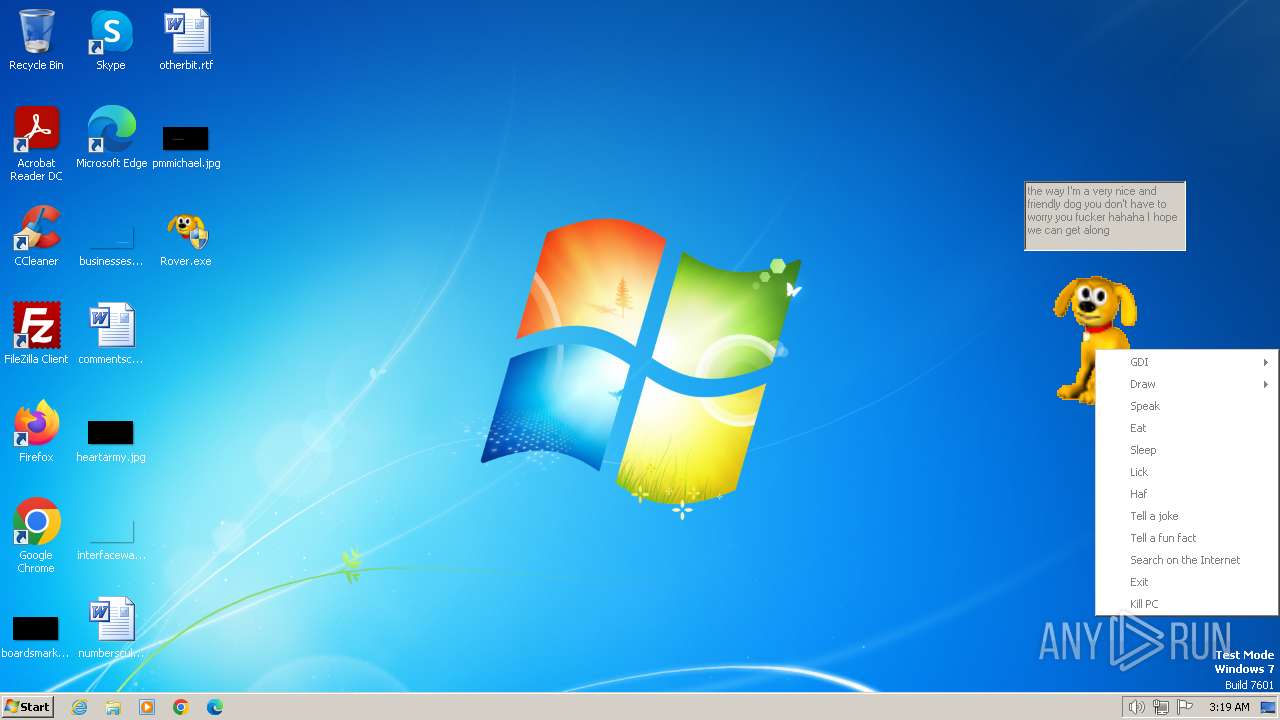
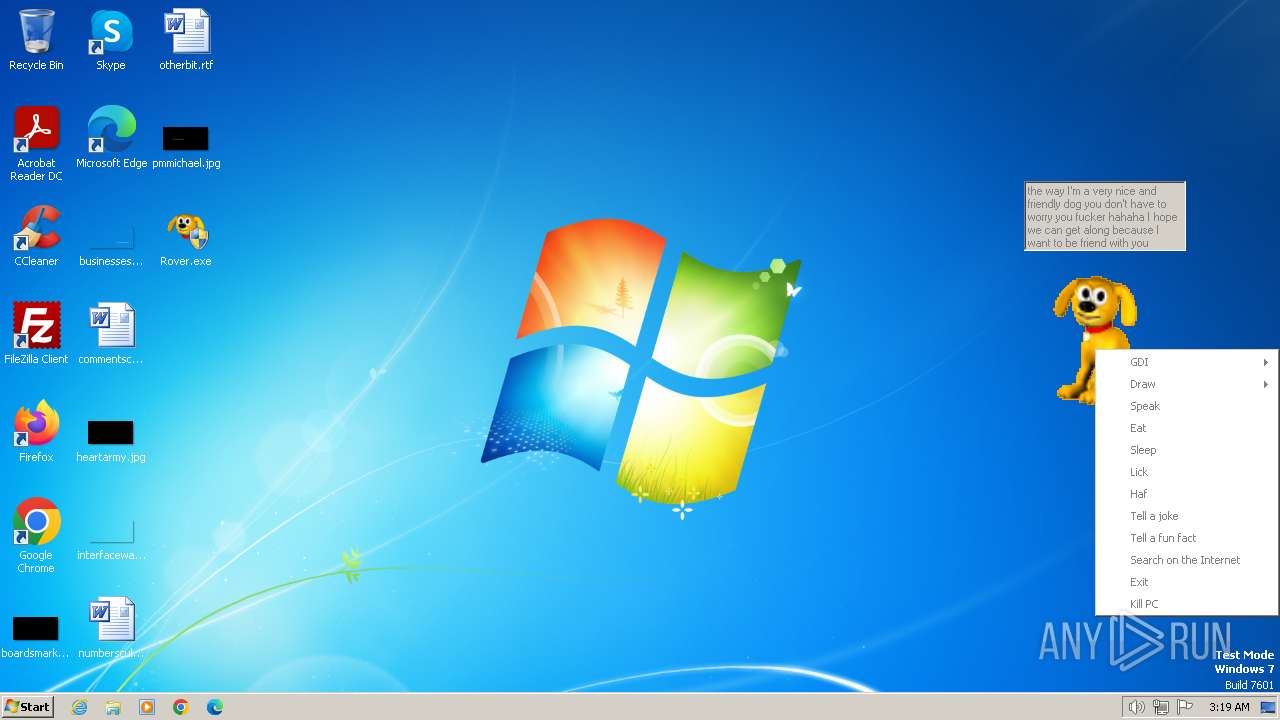
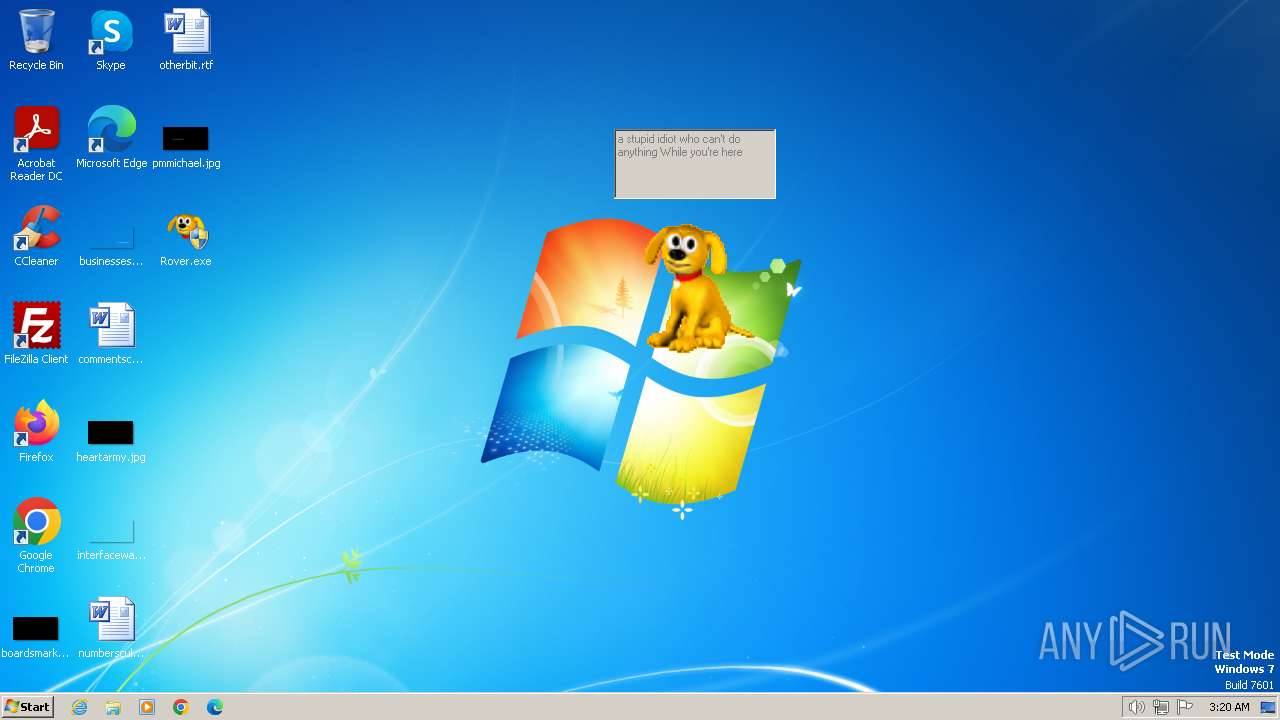
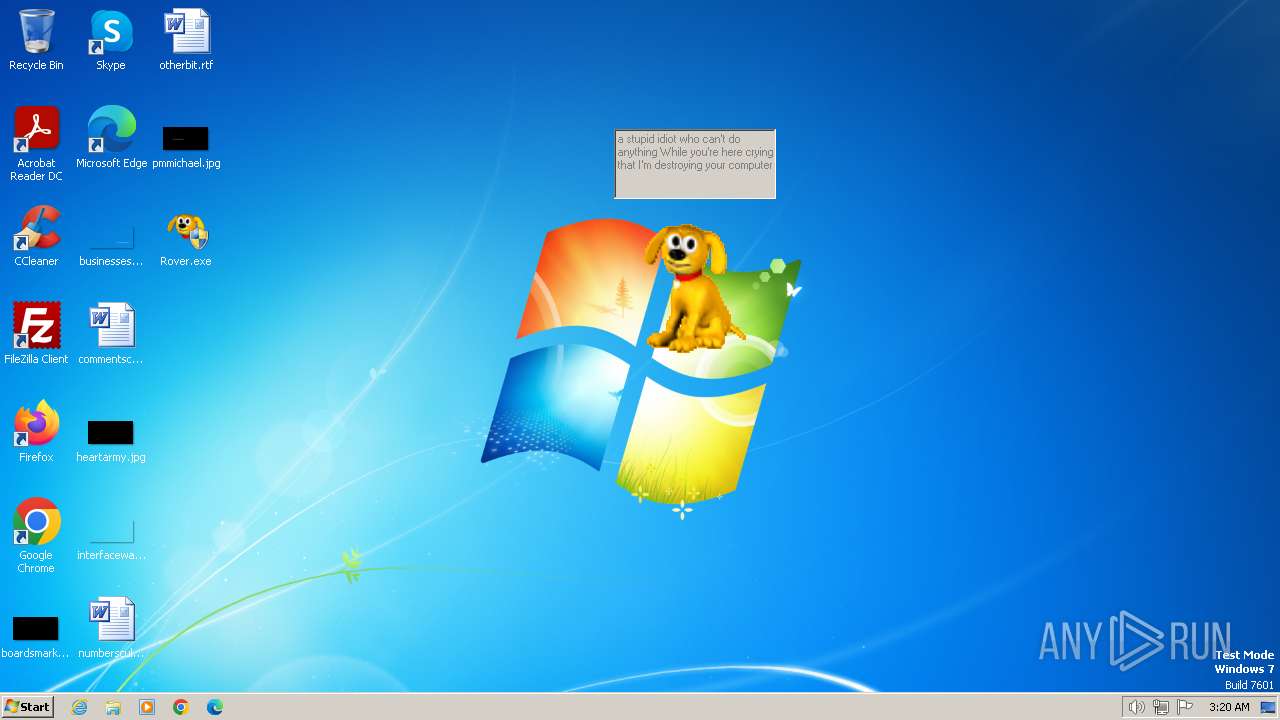
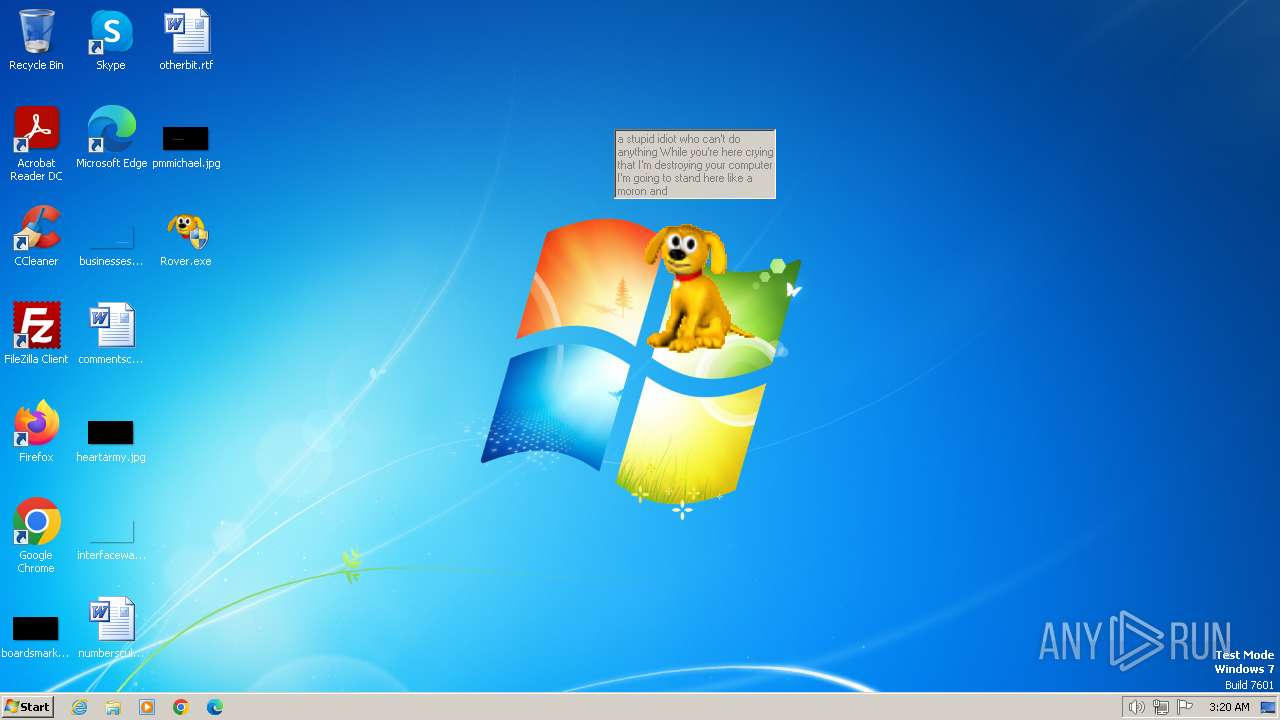
| FileDescription: | Rover The Desktop Assistant (beta version) |
| FileVersion: | 1.0.0.0 |
| InternalName: | Rover.exe |
| LegalCopyright: | Copyright © 2023 |
| LegalTrademarks: | - |
| OriginalFileName: | Rover.exe |
| ProductName: | Created by CYBER SOLDIER aka Clutter |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
41
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2472 | "C:\Users\admin\Desktop\Rover.exe" | C:\Users\admin\Desktop\Rover.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Rover The Desktop Assistant (beta version) Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3772 | "C:\Users\admin\Desktop\Rover.exe" | C:\Users\admin\Desktop\Rover.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Rover The Desktop Assistant (beta version) Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
754
Read events
735
Write events
19
Delete events
0
Modification events
| (PID) Process: | (3772) Rover.exe | Key: | HKEY_CURRENT_USER\Software\rover |
| Operation: | write | Name: | lang |
Value: English (EN) | |||
| (PID) Process: | (3772) Rover.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | FilterAdministratorToken |
Value: 1 | |||
| (PID) Process: | (3772) Rover.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | EnableLUA |
Value: 0 | |||
| (PID) Process: | (3772) Rover.exe | Key: | HKEY_CURRENT_USER\Software\rover |
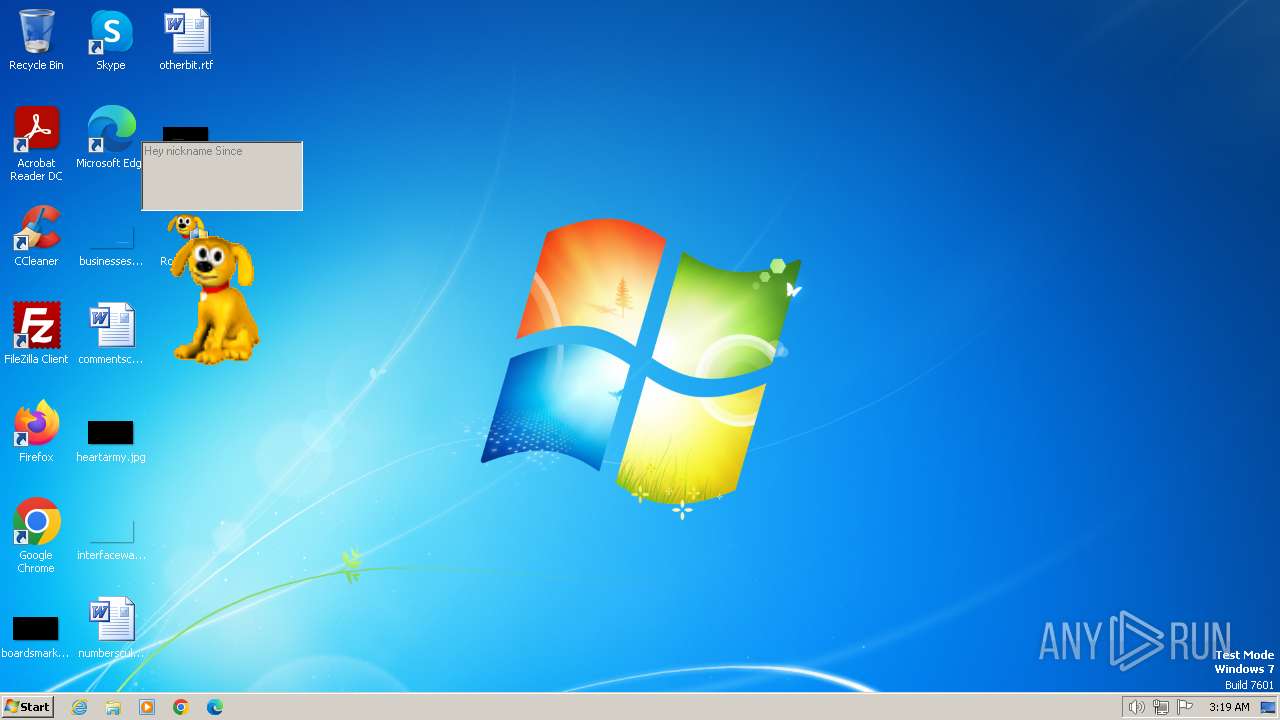
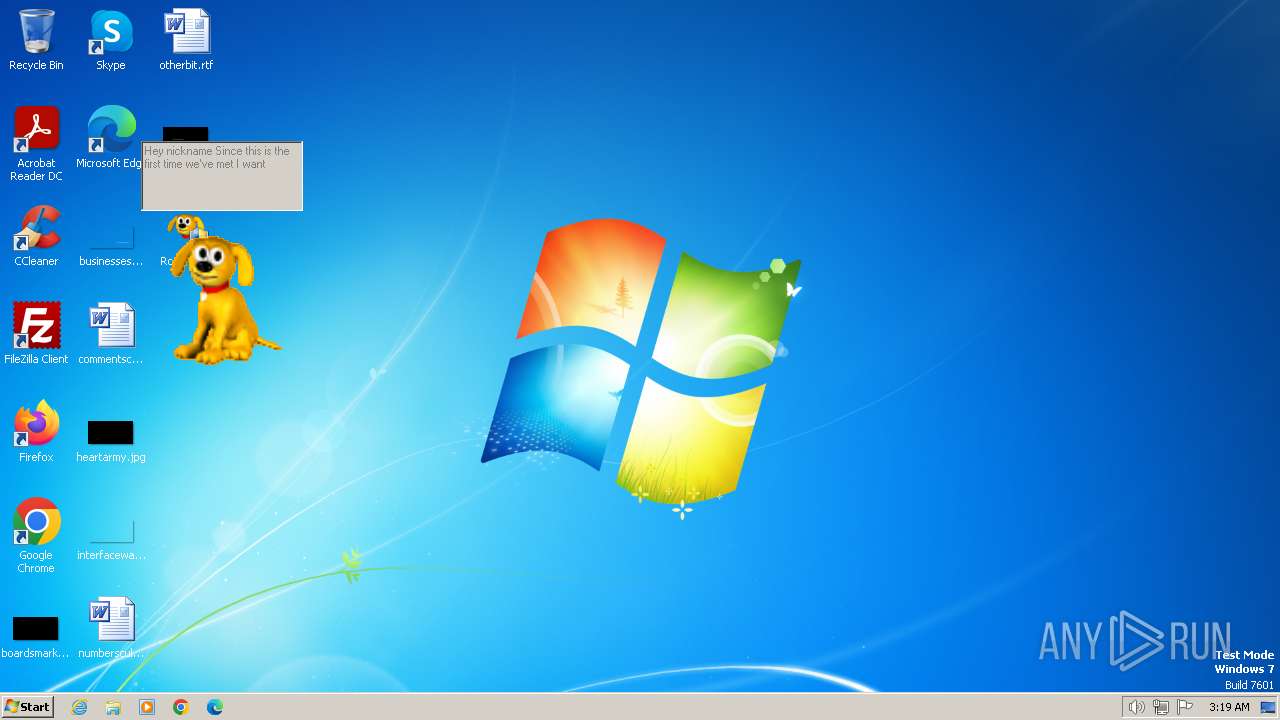
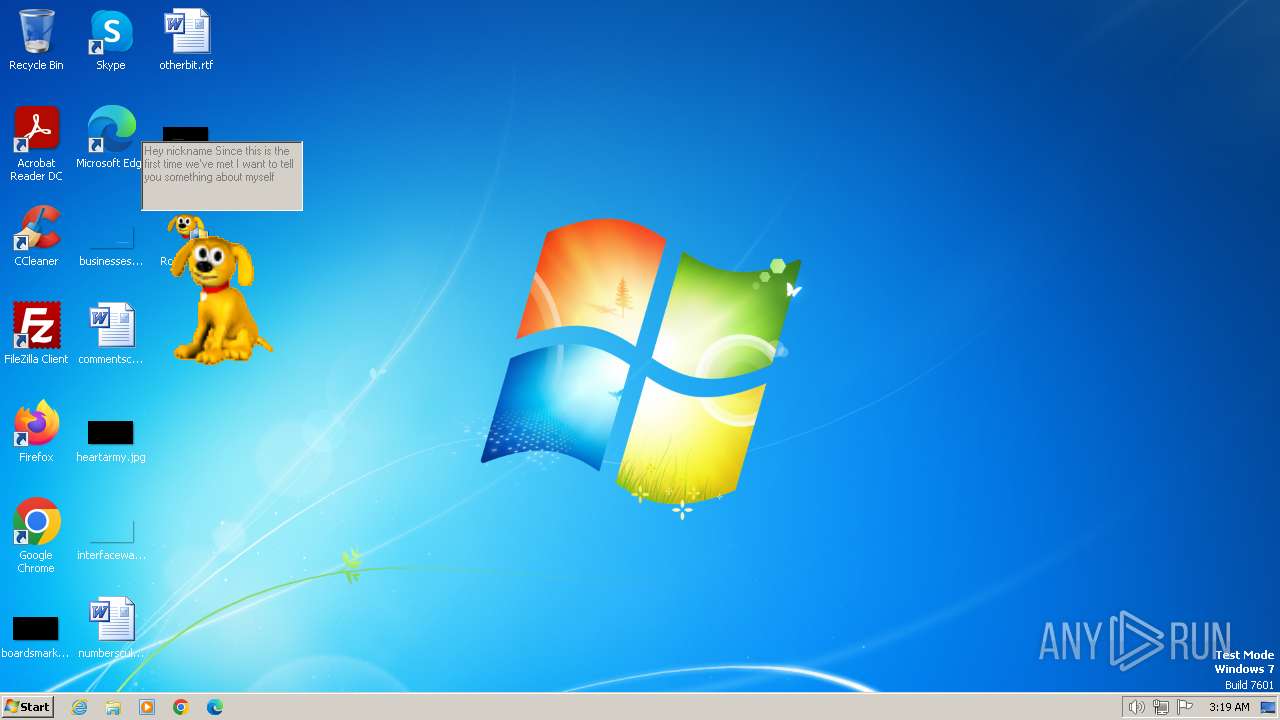
| Operation: | write | Name: | username |
Value: "nickname" | |||
| (PID) Process: | (3772) Rover.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon |
| Operation: | write | Name: | Shell |
Value: explorer.exe, C:\Program Files\rover\rover.exe | |||
| (PID) Process: | (3772) Rover.exe | Key: | HKEY_CURRENT_USER\Software\rover |
| Operation: | write | Name: | tts_vol |
Value: 50 | |||
| (PID) Process: | (3772) Rover.exe | Key: | HKEY_CURRENT_USER\Software\rover |
| Operation: | write | Name: | tts_rate |
Value: 0 | |||
| (PID) Process: | (3772) Rover.exe | Key: | HKEY_CURRENT_USER\Software\rover |
| Operation: | write | Name: | filter_red |
Value: 0 | |||
| (PID) Process: | (3772) Rover.exe | Key: | HKEY_CURRENT_USER\Software\rover |
| Operation: | write | Name: | filter_green |
Value: 0 | |||
| (PID) Process: | (3772) Rover.exe | Key: | HKEY_CURRENT_USER\Software\rover |
| Operation: | write | Name: | filter_blue |
Value: 0 | |||
Executable files
1
Suspicious files
12
Text files
496
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3772 | Rover.exe | C:\Program Files\rover\Ashamed\Ashamed.001.png | image | |
MD5:AA84C45293EF08A7A64DB8F5D12B5DD0 | SHA256:8178152F670855DD0CB4412494C80B854A164EE02922A112DA4266AF53F9195D | |||
| 3772 | Rover.exe | C:\Program Files\rover\Ashamed\Ashamed.002.png | image | |
MD5:A46F286AE95E280424E0C6D8F1213173 | SHA256:49D69A5F0F84D89A458BF7E8FEA059F54F45ACE360D74DE22FE45ECEEC87BA16 | |||
| 3772 | Rover.exe | C:\Program Files\rover\Ashamed\Ashamed.007.png | image | |
MD5:72685D7C7CC4C77E20618264B4150331 | SHA256:B67E7613906632BC3F8AEC7541F2D99FB73C9406183699F9EAB3D97952AEB81B | |||
| 3772 | Rover.exe | C:\Program Files\rover\Ashamed\Ashamed.003.png | image | |
MD5:CF62C5107B66367690832F72854BFFAE | SHA256:075B30FC4D1997D1826148D9A98DBE3A6B06EA53862FD2C453F5D6AD8C288E62 | |||
| 3772 | Rover.exe | C:\Program Files\rover\Ashamed\Ashamed.006.png | image | |
MD5:3D8699EC82F73E244B078D9F16BDAC5C | SHA256:B1F9AE224B7B7988E6FF76C9A951609BA88290B79BC295F015186495E693479F | |||
| 3772 | Rover.exe | C:\Program Files\rover\Ashamed\Ashamed.014.png | image | |
MD5:BD65E98C40A77188E231F2E89B224A7D | SHA256:8A22BDC7116DE7970BB06E2124B5336CF3BC488310E4D796021D01CF378A4A1D | |||
| 3772 | Rover.exe | C:\Program Files\rover\Ashamed\Ashamed.008.png | image | |
MD5:B3F53C1DC286776CF34641C7B8256DFA | SHA256:43C42124AE7D35D7ACDEAFDBB16A890B4667B4089920810FBFD1CC19AB9AEFCA | |||
| 3772 | Rover.exe | C:\Program Files\rover\Ashamed\Ashamed.009.png | image | |
MD5:571AFD578CFAEF347A6052AFE253461B | SHA256:6CC53BAC0224FEADA9FE44E4FF957EC187709858A07158EE6FF0B84A604D7110 | |||
| 3772 | Rover.exe | C:\Program Files\rover\Ashamed\Ashamed.010.png | image | |
MD5:CB14927415ADCAC79057F0D907A19B83 | SHA256:DC286D3373C6531C7F724FDE5AB241D639B19234AADA887C3D36CA0EF7E4AAAB | |||
| 3772 | Rover.exe | C:\Program Files\rover\Ashamed\Ashamed.011.png | image | |
MD5:F32A17F8EA49BD5B94BCCC31C845A193 | SHA256:1CA0F75A6752A892A26BBFA06DD9AC032085C57C6640E649D76AA6446ADF9884 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |