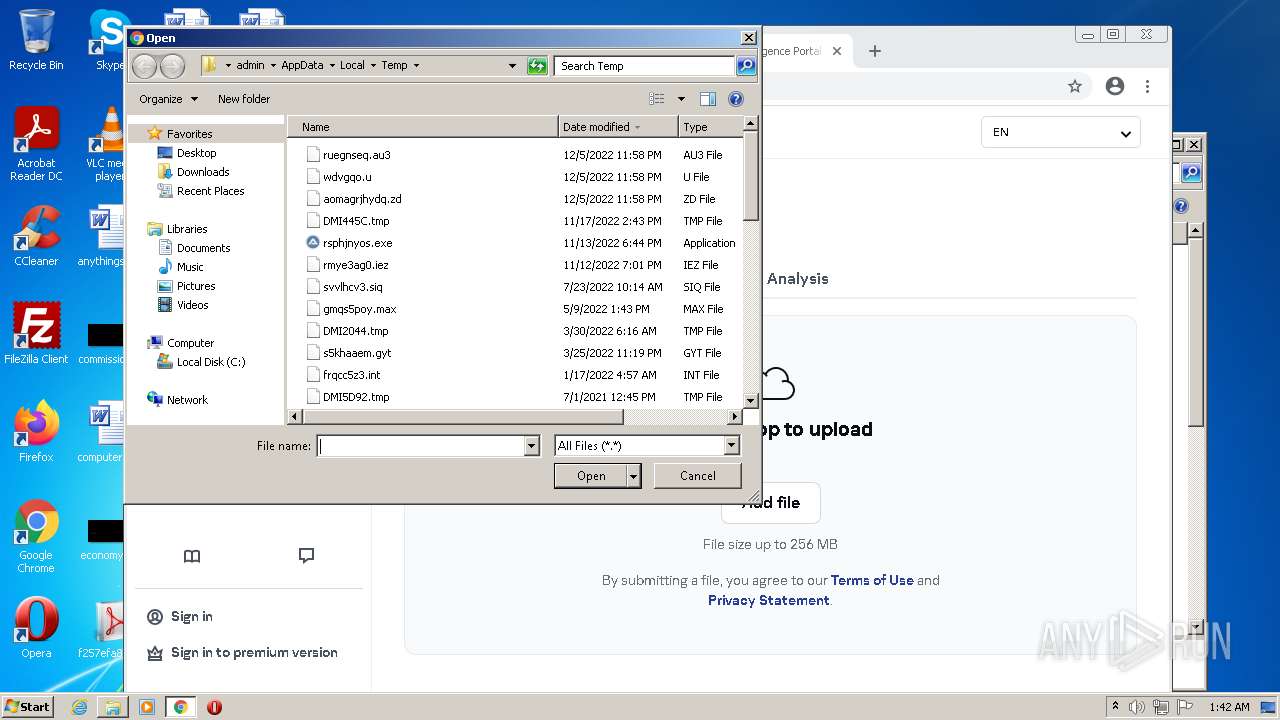
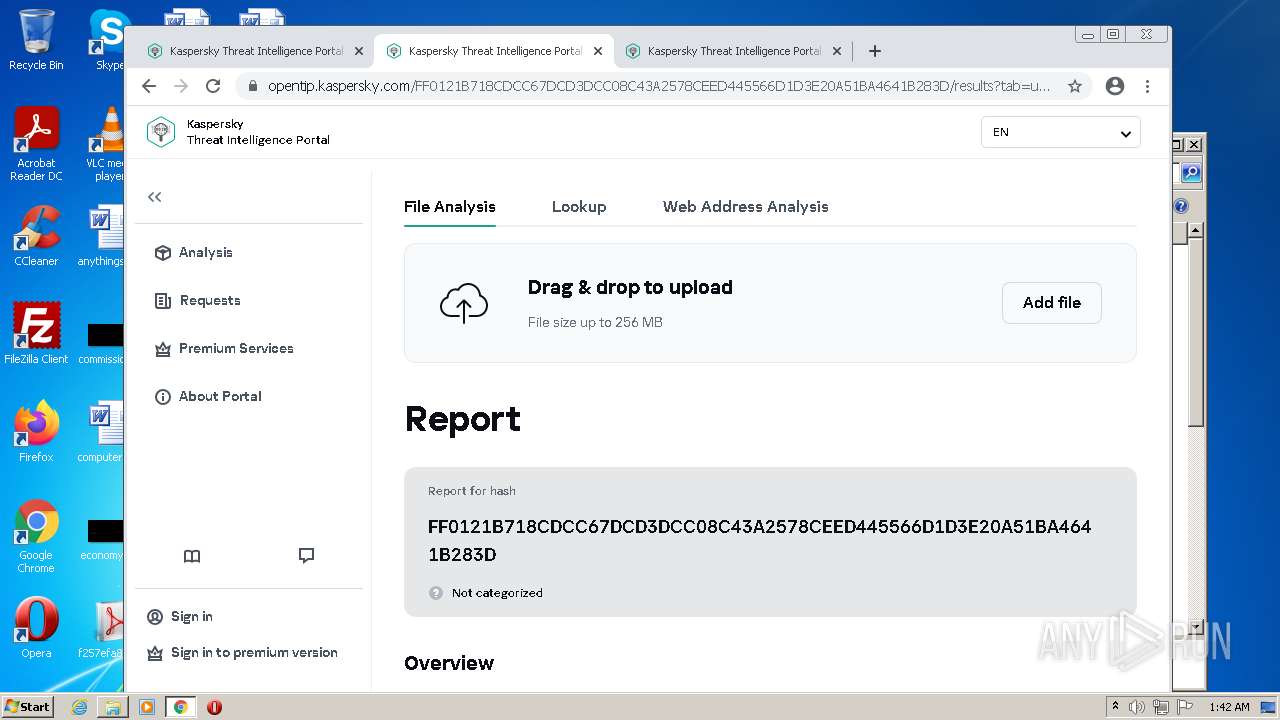
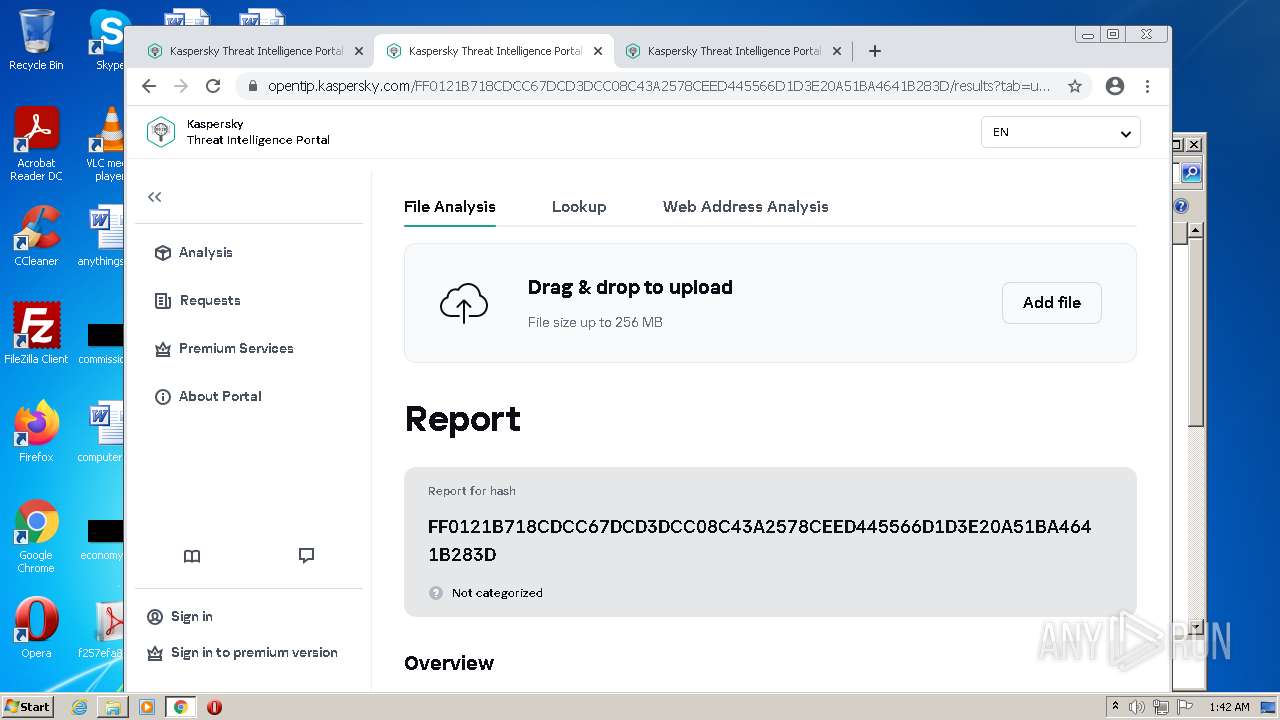
| File name: | Payment Advice - Advice Ref A1T4C80vSIxi ACH credits Customer Ref1093817130 Second Party Ref128141001808.PDF.exe |
| Full analysis: | https://app.any.run/tasks/a5ba7bc1-bd9d-4862-b740-c1c2ee94f0a4 |
| Verdict: | Malicious activity |
| Analysis date: | December 06, 2022, 01:40:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
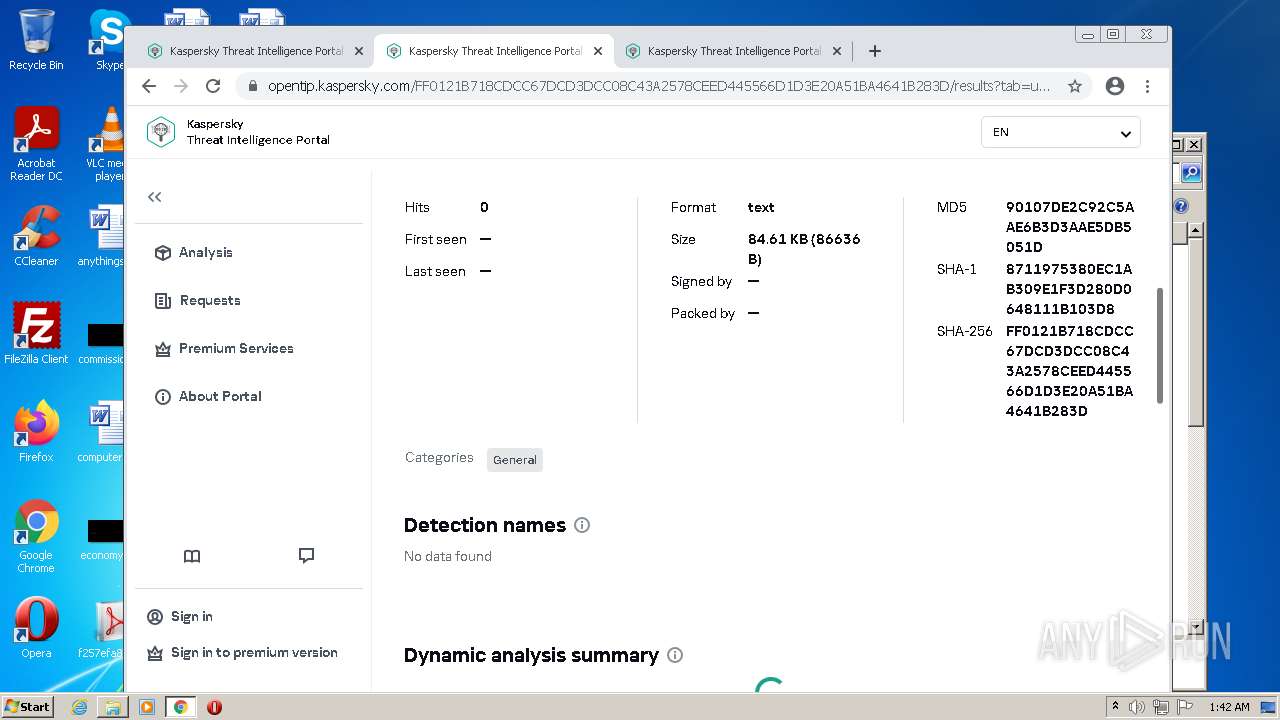
| MD5: | DFDE7866B2DE880F117836AA8D5B8ADC |
| SHA1: | 66006BB4A7D2A35841BFEA14ABF1536B20F7A974 |
| SHA256: | 862C17B77ECE5EB013BBE5CED057F1A635A80D4A21C43356AED77E19FADCC0E3 |
| SSDEEP: | 12288:OGlaKpWkdJ9pQ15Hzj4WlhjWPPvCLyZ+RvugSrmhktjxGty20qTszOFk:XlppWw9pC4pPPpkR0ymtjxUBYz0k |
MALICIOUS
Changes the autorun value in the registry
- rsphjnyos.exe (PID: 2328)
Application was dropped or rewritten from another process
- rsphjnyos.exe (PID: 2328)
- rsphjnyos.exe (PID: 1040)
Drops the executable file immediately after the start
- rsphjnyos.exe (PID: 2328)
SUSPICIOUS
Drops the AutoIt3 executable file
- rsphjnyos.exe (PID: 2328)
Executable content was dropped or overwritten
- rsphjnyos.exe (PID: 2328)
Application launched itself
- rsphjnyos.exe (PID: 2328)
INFO
Checks supported languages
- f257efa8-32ea-4e65-9941-663dc5424b4c.exe (PID: 2436)
- rsphjnyos.exe (PID: 2328)
Reads the computer name
- f257efa8-32ea-4e65-9941-663dc5424b4c.exe (PID: 2436)
Reads mouse settings
- rsphjnyos.exe (PID: 2328)
Manual execution by a user
- explorer.exe (PID: 3548)
- rundll32.exe (PID: 2876)
- chrome.exe (PID: 3776)
Reads Microsoft Office registry keys
- chrome.exe (PID: 1652)
Executable content was dropped or overwritten
- chrome.exe (PID: 3216)
Application launched itself
- chrome.exe (PID: 3776)
Drops the executable file immediately after the start
- chrome.exe (PID: 3216)
Drops a file that was compiled in debug mode
- chrome.exe (PID: 3216)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 2015-Dec-27 05:38:52 |
| Detected languages: |
|
DOS Header
| e_magic: | MZ |
|---|---|
| e_cblp: | 144 |
| e_cp: | 3 |
| e_crlc: | - |
| e_cparhdr: | 4 |
| e_minalloc: | - |
| e_maxalloc: | 65535 |
| e_ss: | - |
| e_sp: | 184 |
| e_csum: | - |
| e_ip: | - |
| e_cs: | - |
| e_ovno: | - |
| e_oemid: | - |
| e_oeminfo: | - |
| e_lfanew: | 216 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| NumberofSections: | 5 |
| TimeDateStamp: | 2015-Dec-27 05:38:52 |
| PointerToSymbolTable: | - |
| NumberOfSymbols: | - |
| SizeOfOptionalHeader: | 224 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 4096 | 23626 | 24064 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.41076 |
.rdata | 28672 | 4446 | 4608 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.14255 |
.data | 36864 | 110712 | 1536 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.22522 |
.ndata | 151552 | 32768 | 0 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | |
.rsrc | 184320 | 202592 | 202752 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.93641 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.90959 | 67624 | UNKNOWN | English - United States | RT_ICON |
2 | 7.96373 | 38581 | UNKNOWN | English - United States | RT_ICON |
3 | 5.17077 | 38056 | UNKNOWN | English - United States | RT_ICON |
4 | 5.22062 | 21640 | UNKNOWN | English - United States | RT_ICON |
5 | 5.1977 | 16936 | UNKNOWN | English - United States | RT_ICON |
6 | 5.26928 | 9640 | UNKNOWN | English - United States | RT_ICON |
7 | 5.3399 | 4264 | UNKNOWN | English - United States | RT_ICON |
8 | 5.49489 | 2440 | UNKNOWN | English - United States | RT_ICON |
9 | 5.20658 | 1128 | UNKNOWN | English - United States | RT_ICON |
103 | 3.03466 | 132 | UNKNOWN | English - United States | RT_GROUP_ICON |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
ole32.dll |
Total processes
99
Monitored processes
58
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 588 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1012,13474381226792037087,7178719556596208861,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3320 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 856 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1012,13474381226792037087,7178719556596208861,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=2940 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 920 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1012,13474381226792037087,7178719556596208861,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3024 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 988 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1012,13474381226792037087,7178719556596208861,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3668 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1000 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1012,13474381226792037087,7178719556596208861,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2184 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1040 | "C:\Users\admin\AppData\Local\Temp\rsphjnyos.exe" | C:\Users\admin\AppData\Local\Temp\rsphjnyos.exe | rsphjnyos.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script Exit code: 3221225477 Version: 3, 3, 14, 5 Modules
| |||||||||||||||
| 1072 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,13474381226792037087,7178719556596208861,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --instant-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=27 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3372 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1400 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1012,13474381226792037087,7178719556596208861,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3480 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1528 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1012,13474381226792037087,7178719556596208861,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2640 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1652 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1012,13474381226792037087,7178719556596208861,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3152 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
28 692
Read events
28 332
Write events
345
Delete events
15
Modification events
| (PID) Process: | (2328) rsphjnyos.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | eoruthnaadeju |
Value: C:\Users\admin\AppData\Roaming\jtcpo\ckdijf.exe "C:\Users\admin\AppData\Local\Temp\rsphjnyos.exe" "C:\Users\admin\AppData\Local\T | |||
| (PID) Process: | (3776) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3776) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3776) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3776) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3776) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3776) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3776) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3776) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3776) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
3
Suspicious files
207
Text files
198
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3776 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-638E9D98-EC0.pma | — | |
MD5:— | SHA256:— | |||
| 2436 | f257efa8-32ea-4e65-9941-663dc5424b4c.exe | C:\Users\admin\AppData\Local\Temp\aomagrjhydq.zd | binary | |
MD5:— | SHA256:— | |||
| 2436 | f257efa8-32ea-4e65-9941-663dc5424b4c.exe | C:\Users\admin\AppData\Local\Temp\nsfFB5E.tmp | binary | |
MD5:— | SHA256:— | |||
| 2436 | f257efa8-32ea-4e65-9941-663dc5424b4c.exe | C:\Users\admin\AppData\Local\Temp\wdvgqo.u | text | |
MD5:— | SHA256:— | |||
| 2436 | f257efa8-32ea-4e65-9941-663dc5424b4c.exe | C:\Users\admin\AppData\Local\Temp\ruegnseq.au3 | text | |
MD5:— | SHA256:— | |||
| 2756 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Cache\index | binary | |
MD5:— | SHA256:— | |||
| 2436 | f257efa8-32ea-4e65-9941-663dc5424b4c.exe | C:\Users\admin\AppData\Local\Temp\rsphjnyos.exe | executable | |
MD5:C56B5F0201A3B3DE53E561FE76912BFD | SHA256:237D1BCA6E056DF5BB16A1216A434634109478F882D3B1D58344C801D184F95D | |||
| 2940 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\CrashpadMetrics.pma | binary | |
MD5:03C4F648043A88675A920425D824E1B3 | SHA256:F91DBB7C64B4582F529C968C480D2DCE1C8727390482F31E4355A27BB3D9B450 | |||
| 2328 | rsphjnyos.exe | C:\Users\admin\AppData\Roaming\jtcpo\ckdijf.exe | executable | |
MD5:C56B5F0201A3B3DE53E561FE76912BFD | SHA256:237D1BCA6E056DF5BB16A1216A434634109478F882D3B1D58344C801D184F95D | |||
| 3776 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\493ca3ee-570f-49de-8b79-4afe090caf0b.tmp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
33
TCP/UDP connections
57
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
868 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | — | — | whitelisted |
868 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/YGkwa4MXjfWSuERyWQYP_A_4/aapLKTSZ439A-0g3nqJr3Q | US | — | — | whitelisted |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 37.8 Kb | whitelisted |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 37.7 Kb | whitelisted |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 8.56 Kb | whitelisted |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 23.4 Kb | whitelisted |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 31.7 Kb | whitelisted |
868 | svchost.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acjgztdbjqsnhhrv3mj6jj7z76ja_2896/jflookgnkcckhobaglndicnbbgbonegd_2896_all_mzwjwhzvfrv7zmanzi2bxlcnqi.crx3 | US | crx | 50.2 Kb | whitelisted |
868 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvZjE0QUFYTUR2NXNIakJsbE5jbXNrUkdfQQ/4.10.2391.0_oimompecagnajdejgnnjijobebaeigek.crx | US | crx | 50.2 Kb | whitelisted |
2756 | chrome.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | crx | 242 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2756 | chrome.exe | 34.104.35.123:80 | edgedl.me.gvt1.com | GOOGLE | US | whitelisted |
2756 | chrome.exe | 142.250.186.99:443 | update.googleapis.com | GOOGLE | US | whitelisted |
— | — | 34.104.35.123:80 | edgedl.me.gvt1.com | GOOGLE | US | whitelisted |
2756 | chrome.exe | 93.159.230.121:80 | opentip.kaspersky.com | Kaspersky Lab Switzerland GmbH | RU | unknown |
2756 | chrome.exe | 142.250.185.68:443 | www.google.com | GOOGLE | US | whitelisted |
2756 | chrome.exe | 142.250.185.78:443 | clients2.google.com | GOOGLE | US | whitelisted |
2756 | chrome.exe | 216.58.212.131:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
2756 | chrome.exe | 142.250.186.161:443 | clients2.googleusercontent.com | GOOGLE | US | whitelisted |
2756 | chrome.exe | 142.250.74.205:443 | accounts.google.com | GOOGLE | US | whitelisted |
— | — | 142.250.184.234:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
clients2.google.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| malicious |
clients2.googleusercontent.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
dns.msftncsi.com |
| shared |