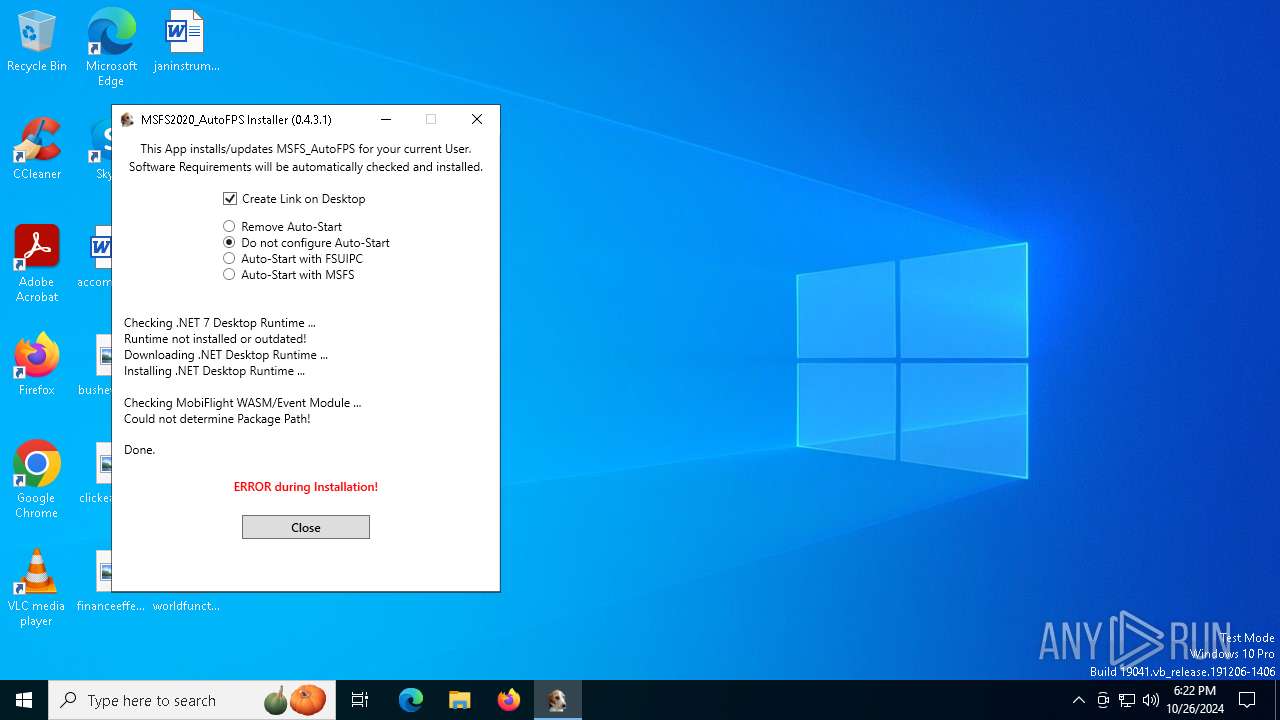
| File name: | MSFS_AutoFPS-installer-v0.4.3.1.exe |
| Full analysis: | https://app.any.run/tasks/0d80172b-34be-49a8-91ac-713a65393702 |
| Verdict: | Malicious activity |
| Analysis date: | October 26, 2024, 18:21:40 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64 Mono/.Net assembly, for MS Windows, 2 sections |
| MD5: | F71485172E24B64706D49C5E824BA070 |
| SHA1: | 3DA07BF5CFCD487D7BC5388A1A3908F30B165761 |
| SHA256: | 8603AFC5696C21FD08984C41DF8A198DF9C85BC4737B8591DB51396E995A7CAE |
| SSDEEP: | 49152:w66HbPDXxJDF63mhfikO+xsomnFbMNftxO4re9TbKJkY2zN/0bssW5zvi7xqTYxY:w/nbDACikGomn8fn1e9mkY2BukeYAAoG |
MALICIOUS
No malicious indicators.SUSPICIOUS
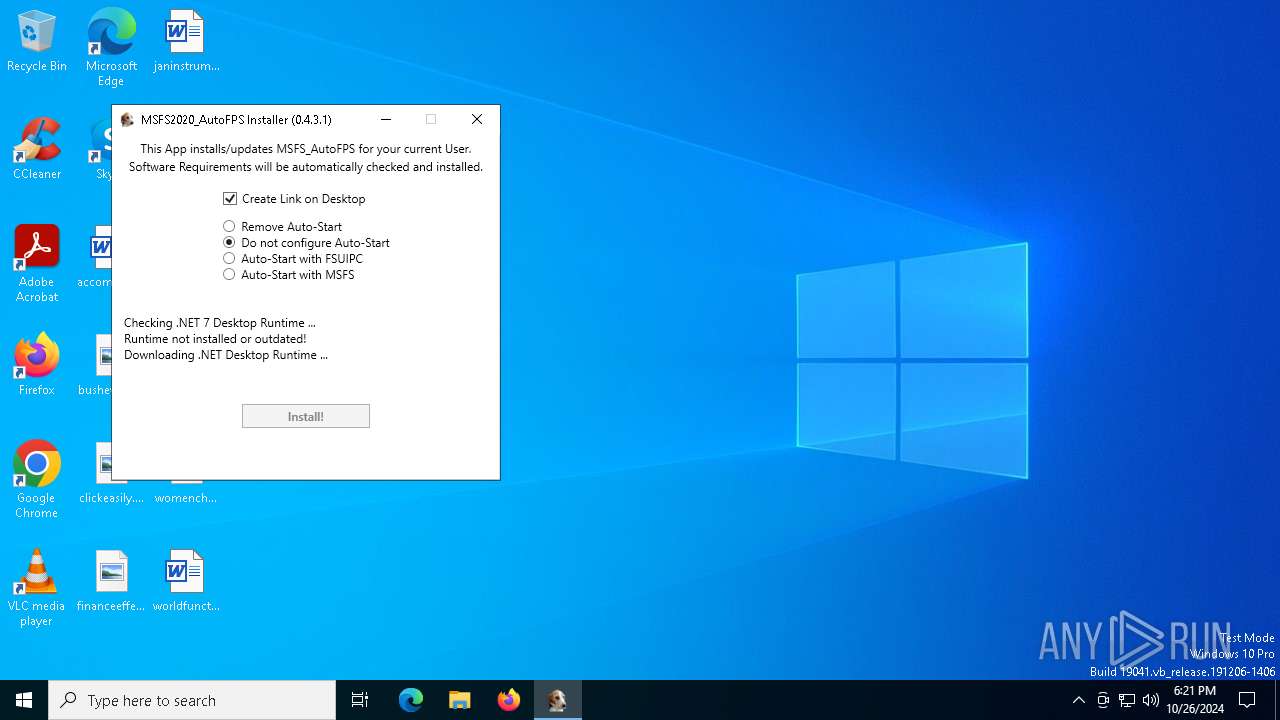
Command gets lists installed versions of .NET Runtime on the system
- cmd.exe (PID: 2708)
Starts CMD.EXE for commands execution
- MSFS_AutoFPS-installer-v0.4.3.1.exe (PID: 5828)
The executable file from the user directory is run by the CMD process
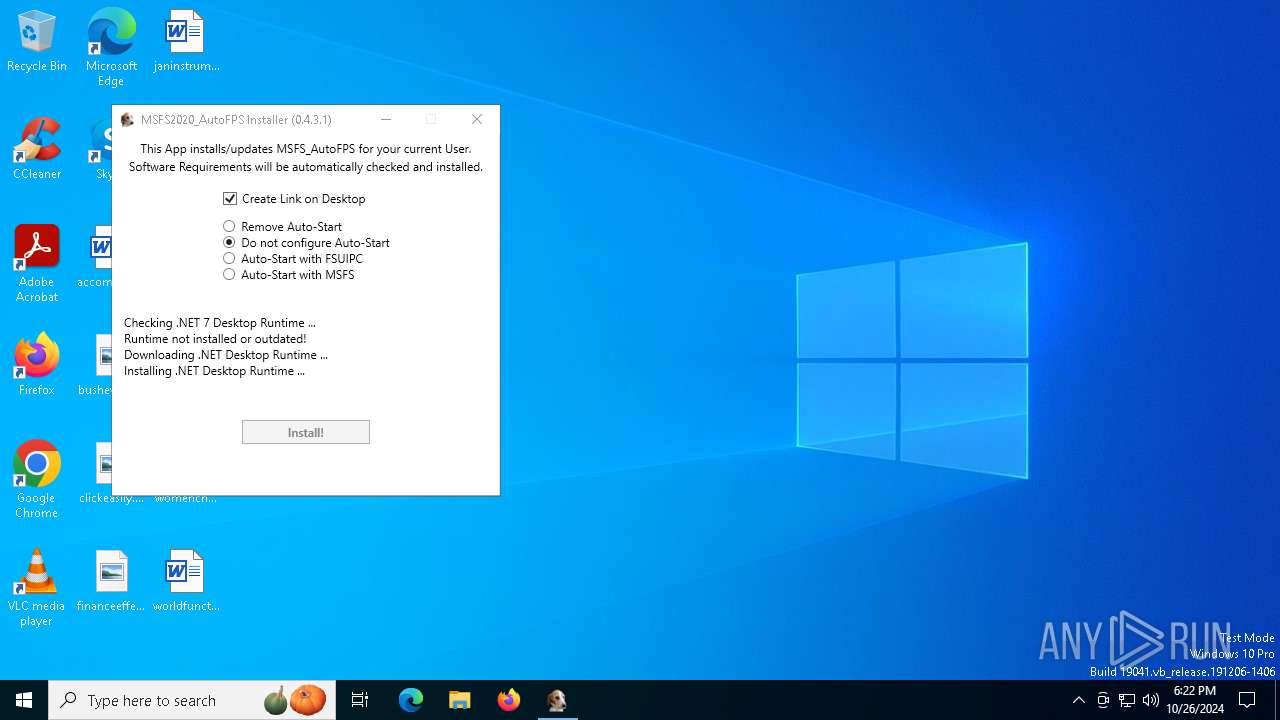
- windowsdesktop-runtime-7.0.20-win-x64.exe (PID: 5612)
Starts a Microsoft application from unusual location
- windowsdesktop-runtime-7.0.20-win-x64.exe (PID: 5612)
- windowsdesktop-runtime-7.0.20-win-x64.exe (PID: 3764)
- windowsdesktop-runtime-7.0.20-win-x64.exe (PID: 7096)
Executable content was dropped or overwritten
- windowsdesktop-runtime-7.0.20-win-x64.exe (PID: 5612)
- windowsdesktop-runtime-7.0.20-win-x64.exe (PID: 7096)
- windowsdesktop-runtime-7.0.20-win-x64.exe (PID: 3764)
Process drops legitimate windows executable
- windowsdesktop-runtime-7.0.20-win-x64.exe (PID: 5612)
- windowsdesktop-runtime-7.0.20-win-x64.exe (PID: 3764)
- windowsdesktop-runtime-7.0.20-win-x64.exe (PID: 7096)
- msiexec.exe (PID: 6396)
Searches for installed software
- windowsdesktop-runtime-7.0.20-win-x64.exe (PID: 3764)
The process drops C-runtime libraries
- msiexec.exe (PID: 6396)
Starts itself from another location
- windowsdesktop-runtime-7.0.20-win-x64.exe (PID: 3764)
INFO
Reads the computer name
- MSFS_AutoFPS-installer-v0.4.3.1.exe (PID: 5828)
- windowsdesktop-runtime-7.0.20-win-x64.exe (PID: 3764)
Checks supported languages
- MSFS_AutoFPS-installer-v0.4.3.1.exe (PID: 5828)
- windowsdesktop-runtime-7.0.20-win-x64.exe (PID: 5612)
- windowsdesktop-runtime-7.0.20-win-x64.exe (PID: 3764)
Reads the machine GUID from the registry
- MSFS_AutoFPS-installer-v0.4.3.1.exe (PID: 5828)
Reads the software policy settings
- MSFS_AutoFPS-installer-v0.4.3.1.exe (PID: 5828)
Create files in a temporary directory
- MSFS_AutoFPS-installer-v0.4.3.1.exe (PID: 5828)
- windowsdesktop-runtime-7.0.20-win-x64.exe (PID: 5612)
- windowsdesktop-runtime-7.0.20-win-x64.exe (PID: 3764)
Reads Environment values
- MSFS_AutoFPS-installer-v0.4.3.1.exe (PID: 5828)
Checks proxy server information
- MSFS_AutoFPS-installer-v0.4.3.1.exe (PID: 5828)
Disables trace logs
- MSFS_AutoFPS-installer-v0.4.3.1.exe (PID: 5828)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6396)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2047:01:27 08:57:47+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 48 |
| CodeSize: | 1415168 |
| InitializedDataSize: | 91136 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x0000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.4.3.1 |
| ProductVersionNumber: | 0.4.3.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | Installer App for MSFS2020_AutoFPS |
| CompanyName: | ResetXPDR |
| FileDescription: | MSFS2020_AutoFPS Installer |
| FileVersion: | 0.4.3.1 |
| InternalName: | Installer.exe |
| LegalCopyright: | Copyright © 2024 |
| LegalTrademarks: | - |
| OriginalFileName: | Installer.exe |
| ProductName: | MSFS2020_AutoFPS Installer |
| ProductVersion: | 0.4.3.1 |
| AssemblyVersion: | 0.4.3.1 |
Total processes
148
Monitored processes
13
Malicious processes
3
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1184 | "cmd.exe" /Cwindowsdesktop-runtime-7.0.20-win-x64.exe /install /quiet /norestart | C:\Windows\System32\cmd.exe | — | MSFS_AutoFPS-installer-v0.4.3.1.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1248 | C:\Windows\syswow64\MsiExec.exe -Embedding A6DA3C14CF8EC7B32FC79C795E2190F4 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2708 | "cmd.exe" /Cdotnet --list-runtimes | C:\Windows\System32\cmd.exe | — | MSFS_AutoFPS-installer-v0.4.3.1.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3764 | "C:\Users\admin\AppData\Local\Temp\{CFE204ED-6080-45DE-BE72-A1A2C742D441}\.cr\windowsdesktop-runtime-7.0.20-win-x64.exe" -burn.clean.room="C:\Users\admin\AppData\Local\Temp\windowsdesktop-runtime-7.0.20-win-x64.exe" -burn.filehandle.attached=556 -burn.filehandle.self=584 /install /quiet /norestart | C:\Users\admin\AppData\Local\Temp\{CFE204ED-6080-45DE-BE72-A1A2C742D441}\.cr\windowsdesktop-runtime-7.0.20-win-x64.exe | windowsdesktop-runtime-7.0.20-win-x64.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Desktop Runtime - 7.0.20 (x64) Exit code: 0 Version: 7.0.20.33720 Modules
| |||||||||||||||
| 4228 | C:\Windows\syswow64\MsiExec.exe -Embedding B789E6D74C3AD0303E8E17A159B27CED | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4380 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5612 | windowsdesktop-runtime-7.0.20-win-x64.exe /install /quiet /norestart | C:\Users\admin\AppData\Local\Temp\windowsdesktop-runtime-7.0.20-win-x64.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Desktop Runtime - 7.0.20 (x64) Exit code: 0 Version: 7.0.20.33720 Modules
| |||||||||||||||
| 5828 | "C:\Users\admin\AppData\Local\Temp\MSFS_AutoFPS-installer-v0.4.3.1.exe" | C:\Users\admin\AppData\Local\Temp\MSFS_AutoFPS-installer-v0.4.3.1.exe | explorer.exe | ||||||||||||
User: admin Company: ResetXPDR Integrity Level: MEDIUM Description: MSFS2020_AutoFPS Installer Exit code: 0 Version: 0.4.3.1 Modules
| |||||||||||||||
| 6300 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6396 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 228
Read events
10 303
Write events
881
Delete events
44
Modification events
| (PID) Process: | (5828) MSFS_AutoFPS-installer-v0.4.3.1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\MSFS_AutoFPS-installer-v0_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5828) MSFS_AutoFPS-installer-v0.4.3.1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\MSFS_AutoFPS-installer-v0_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (5828) MSFS_AutoFPS-installer-v0.4.3.1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\MSFS_AutoFPS-installer-v0_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (5828) MSFS_AutoFPS-installer-v0.4.3.1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\MSFS_AutoFPS-installer-v0_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (5828) MSFS_AutoFPS-installer-v0.4.3.1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\MSFS_AutoFPS-installer-v0_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (5828) MSFS_AutoFPS-installer-v0.4.3.1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\MSFS_AutoFPS-installer-v0_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (5828) MSFS_AutoFPS-installer-v0.4.3.1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\MSFS_AutoFPS-installer-v0_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (5828) MSFS_AutoFPS-installer-v0.4.3.1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\MSFS_AutoFPS-installer-v0_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5828) MSFS_AutoFPS-installer-v0.4.3.1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\MSFS_AutoFPS-installer-v0_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (5828) MSFS_AutoFPS-installer-v0.4.3.1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\MSFS_AutoFPS-installer-v0_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
485
Suspicious files
72
Text files
29
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5828 | MSFS_AutoFPS-installer-v0.4.3.1.exe | C:\Users\admin\AppData\Local\Temp\windowsdesktop-runtime-7.0.20-win-x64.exe | — | |
MD5:— | SHA256:— | |||
| 3764 | windowsdesktop-runtime-7.0.20-win-x64.exe | C:\Users\admin\AppData\Local\Temp\{2B68B224-8527-4D1A-B5A5-EE329E8D5E2F}\.ba\1041\thm.wxl | xml | |
MD5:E5FD798D4BBDD419A602423A699E2854 | SHA256:00AEC52B4564BC07302881FCFD510F7CCA535AC9E05CFD95A86738171626F6C4 | |||
| 3764 | windowsdesktop-runtime-7.0.20-win-x64.exe | C:\Users\admin\AppData\Local\Temp\{2B68B224-8527-4D1A-B5A5-EE329E8D5E2F}\.ba\1049\thm.wxl | xml | |
MD5:1D628F2E1DBAA25BDD8CF2D7F2A9CAF2 | SHA256:C7CC8E0BDD4F82DA33984F553B576412DF69C5E1E5B8479542D024CB6B41D050 | |||
| 3764 | windowsdesktop-runtime-7.0.20-win-x64.exe | C:\Users\admin\AppData\Local\Temp\{2B68B224-8527-4D1A-B5A5-EE329E8D5E2F}\.ba\1031\thm.wxl | xml | |
MD5:B45249A2238A5568B377E58D4CE89E9A | SHA256:0C4203A81DCD01D53378036AF78CFFCF9E9A5AF7754DFBDD56584AE74C21CC61 | |||
| 3764 | windowsdesktop-runtime-7.0.20-win-x64.exe | C:\Users\admin\AppData\Local\Temp\{2B68B224-8527-4D1A-B5A5-EE329E8D5E2F}\.ba\wixstdba.dll | executable | |
MD5:F68F43F809840328F4E993A54B0D5E62 | SHA256:E921F69B9FB4B5AD4691809D06896C5F1D655AB75E0CE94A372319C243C56D4E | |||
| 3764 | windowsdesktop-runtime-7.0.20-win-x64.exe | C:\Users\admin\AppData\Local\Temp\{2B68B224-8527-4D1A-B5A5-EE329E8D5E2F}\.ba\1033\thm.wxl | xml | |
MD5:D5070CB3387A0A22B7046AE5AB53F371 | SHA256:81A68046B06E09385BE8449373E7CEB9E79F7724C3CF11F0B18A4489A8D4926A | |||
| 3764 | windowsdesktop-runtime-7.0.20-win-x64.exe | C:\Users\admin\AppData\Local\Temp\{2B68B224-8527-4D1A-B5A5-EE329E8D5E2F}\.ba\1028\thm.wxl | xml | |
MD5:B9428C94444693B5E3A392C8D0B95170 | SHA256:C0413EDFD13FD27EEAB7B8CE60963668236466C48F4173C29F84093011C281AF | |||
| 3764 | windowsdesktop-runtime-7.0.20-win-x64.exe | C:\Users\admin\AppData\Local\Temp\{2B68B224-8527-4D1A-B5A5-EE329E8D5E2F}\dotnet_runtime_7.0.20_win_x64.msi | — | |
MD5:— | SHA256:— | |||
| 3764 | windowsdesktop-runtime-7.0.20-win-x64.exe | C:\Users\admin\AppData\Local\Temp\{2B68B224-8527-4D1A-B5A5-EE329E8D5E2F}\.ba\1040\thm.wxl | xml | |
MD5:347BE63418F507E7F2A086726E96FCA8 | SHA256:344ACD0D3665BA489EB30EBC0F902C625E1AD33A4E2B5BA7CDD7E463658D5557 | |||
| 3764 | windowsdesktop-runtime-7.0.20-win-x64.exe | C:\Users\admin\AppData\Local\Temp\{2B68B224-8527-4D1A-B5A5-EE329E8D5E2F}\.ba\1046\thm.wxl | xml | |
MD5:88CB193F0B0C15023D789E0F8FCE3E03 | SHA256:4D6A2D306ABE77E7DBDB2609F6198B4CF99B3F9DC15B9DC72951592AD2F64384 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
40
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6396 | msiexec.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6276 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6276 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5652 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4004 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6396 | msiexec.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5640 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4360 | SearchApp.exe | 92.123.104.61:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5828 | MSFS_AutoFPS-installer-v0.4.3.1.exe | 199.232.210.172:443 | download.visualstudio.microsoft.com | FASTLY | US | whitelisted |
4004 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4004 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
download.visualstudio.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |