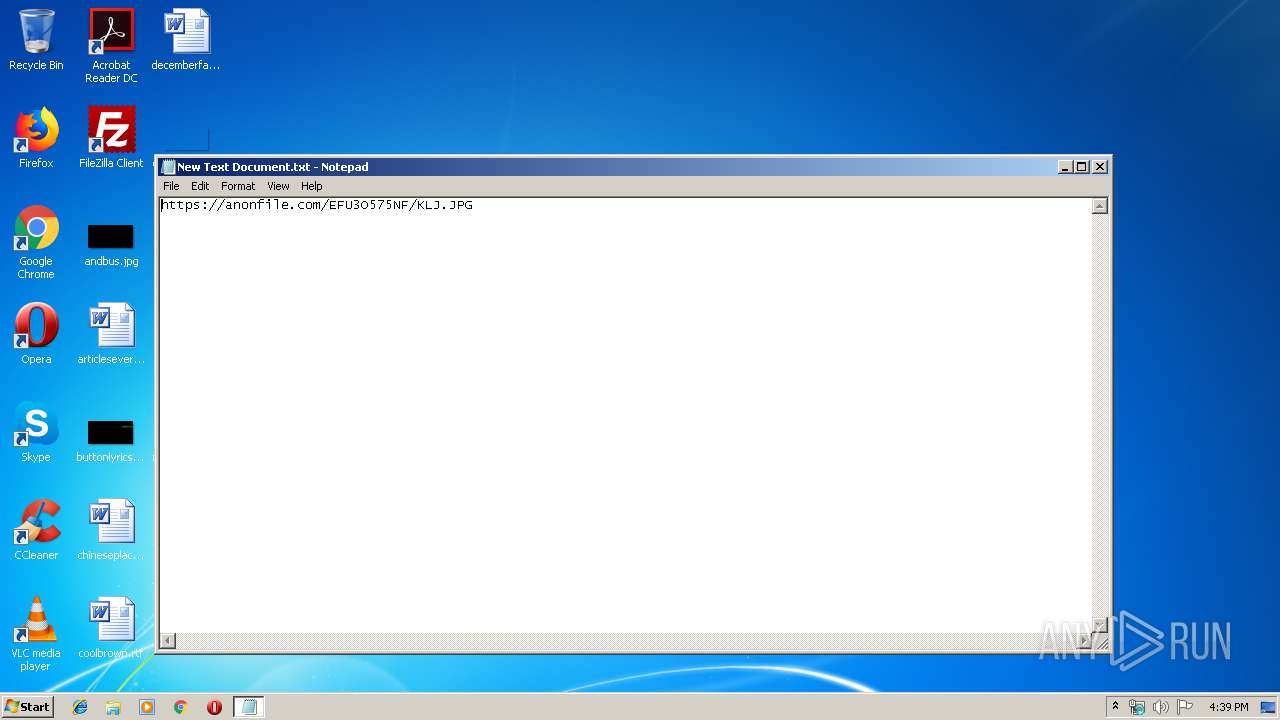
| File name: | New Text Document.txt |
| Full analysis: | https://app.any.run/tasks/b010dec0-7b1d-4329-8088-ab839efa4bd0 |
| Verdict: | Malicious activity |
| Analysis date: | October 09, 2019, 15:39:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with no line terminators |
| MD5: | 047EADA1C08B45202FE75723600AD429 |
| SHA1: | 2181F60DA557ADC4E054A7D89765A6EA441D9004 |
| SHA256: | 85E439E0EC75A8150015924EB95294F14162EE7F29ACE5C8AFE0E1FE6EF2E34F |
| SSDEEP: | 3:N8RGKQjrj19Qn:2gKeJ9Qn |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Manual execution by user
- opera.exe (PID: 1936)
Creates files in the user directory
- opera.exe (PID: 1936)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
32
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1144 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\New Text Document.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1936 | "C:\Program Files\Opera\opera.exe" | C:\Program Files\Opera\opera.exe | explorer.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: MEDIUM Description: Opera Internet Browser Exit code: 0 Version: 1748 Modules
| |||||||||||||||
Total events
202
Read events
144
Write events
58
Delete events
0
Modification events
| (PID) Process: | (1936) opera.exe | Key: | HKEY_CURRENT_USER\Software\Opera Software |
| Operation: | write | Name: | Last CommandLine v2 |
Value: C:\Program Files\Opera\opera.exe | |||
| (PID) Process: | (1936) opera.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
0
Suspicious files
32
Text files
22
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1936 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr8F2B.tmp | — | |
MD5:— | SHA256:— | |||
| 1936 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr8F5B.tmp | — | |
MD5:— | SHA256:— | |||
| 1936 | opera.exe | C:\Users\admin\AppData\Local\Opera\Opera\cache\sesn\opr00001.tmp | — | |
MD5:— | SHA256:— | |||
| 1936 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\HZ9NWR17C8SGN9E06HVM.temp | — | |
MD5:— | SHA256:— | |||
| 1936 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\operaprefs.ini | text | |
MD5:— | SHA256:— | |||
| 1936 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\tasks.xml | xml | |
MD5:— | SHA256:— | |||
| 1936 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opssl6.dat | binary | |
MD5:— | SHA256:— | |||
| 1936 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\16ec093b8f51508f.customDestinations-ms~RF189a85.TMP | binary | |
MD5:— | SHA256:— | |||
| 1936 | opera.exe | C:\Users\admin\AppData\Local\Opera\Opera\cache\CACHEDIR.TAG | text | |
MD5:E717F92FA29AE97DBE4F6F5C04B7A3D9 | SHA256:5BBD5DCBF87FD8CD7544C522BADF22A2951CF010AD9F25C40F9726F09EA2B552 | |||
| 1936 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\16ec093b8f51508f.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
33
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1936 | opera.exe | GET | 200 | 216.58.208.35:80 | http://ocsp.pki.goog/gts1o1/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDZ0XRmzo2h%2BwgAAAAAFPsF | US | der | 472 b | whitelisted |
1936 | opera.exe | GET | 200 | 192.35.177.64:80 | http://crl.identrust.com/DSTROOTCAX3CRL.crl | US | der | 896 b | whitelisted |
1936 | opera.exe | GET | 200 | 93.184.220.29:80 | http://s.symcb.com/pca3-g5.crl | US | der | 712 b | whitelisted |
1936 | opera.exe | GET | 200 | 93.184.220.29:80 | http://crl4.digicert.com/DigiCertGlobalRootG2.crl | US | der | 517 b | whitelisted |
1936 | opera.exe | GET | 200 | 2.20.189.244:80 | http://ocsp.int-x3.letsencrypt.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBR%2B5mrncpqz%2FPiiIGRsFqEtYHEIXQQUqEpqYwR93brm0Tm3pkVl7%2FOo7KECEgO4VdgpPDpsZKiHZKn8sXFI5w%3D%3D | unknown | der | 527 b | whitelisted |
1936 | opera.exe | GET | 200 | 93.184.220.29:80 | http://crl4.digicert.com/DigiCertHighAssuranceEVRootCA.crl | US | der | 528 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1936 | opera.exe | 185.26.182.94:443 | certs.opera.com | Opera Software AS | — | whitelisted |
1936 | opera.exe | 93.184.220.29:80 | crl4.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1936 | opera.exe | 185.26.182.93:443 | certs.opera.com | Opera Software AS | — | whitelisted |
1936 | opera.exe | 194.32.146.60:443 | anonfile.com | — | — | unknown |
1936 | opera.exe | 107.167.110.216:443 | sitecheck2.opera.com | Opera Software Americas LLC | US | malicious |
1936 | opera.exe | 192.35.177.64:80 | crl.identrust.com | IdenTrust | US | malicious |
1936 | opera.exe | 2.20.189.244:80 | ocsp.int-x3.letsencrypt.org | Akamai International B.V. | — | whitelisted |
1936 | opera.exe | 107.167.110.211:443 | sitecheck2.opera.com | Opera Software Americas LLC | US | suspicious |
1936 | opera.exe | 151.101.2.217:443 | vjs.zencdn.net | Fastly | US | suspicious |
1936 | opera.exe | 104.18.39.148:443 | shermore.info | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
certs.opera.com |
| whitelisted |
crl4.digicert.com |
| whitelisted |
anonfile.com |
| whitelisted |
sitecheck2.opera.com |
| whitelisted |
crl.identrust.com |
| whitelisted |
ocsp.int-x3.letsencrypt.org |
| whitelisted |
vjs.zencdn.net |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
shermore.info |
| whitelisted |
d3ud741uvs727m.cloudfront.net |
| whitelisted |