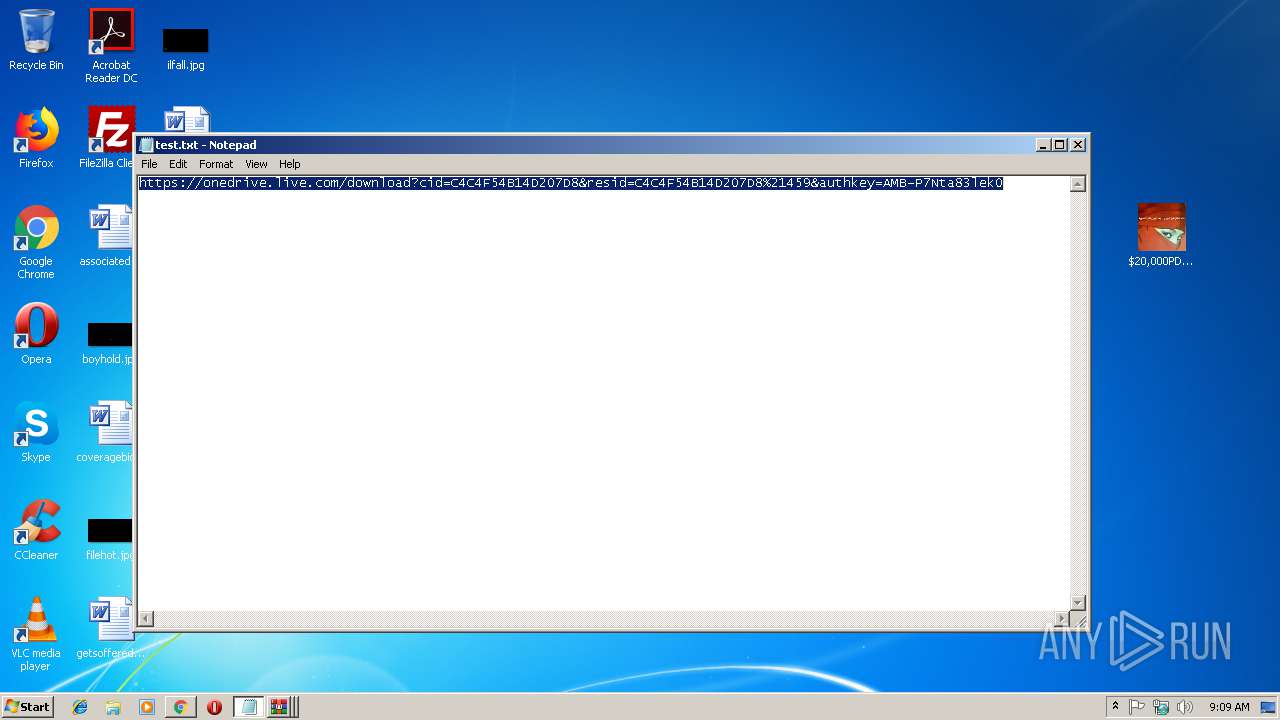
| File name: | test.txt |
| Full analysis: | https://app.any.run/tasks/6a6b90de-7b24-4c29-966a-0f191f3af786 |
| Verdict: | Malicious activity |
| Analysis date: | December 18, 2018, 09:08:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with no line terminators |
| MD5: | 24FA96F5E9F37377C1C7FAE80BCF7655 |
| SHA1: | 09BAABE881A55F4497D63F8CCDAD411721378F47 |
| SHA256: | 85D746D7AF0229B33B3C153FBCE99611E17BBC726D43FE4D5FBB93BC896A5F75 |
| SSDEEP: | 3:N8Ck3CTwKblLRUFHwFMHEAphvF0OrV:2CkST/ZSSGpp4S |
MALICIOUS
Application was dropped or rewritten from another process
- xhd.exe (PID: 3268)
- xhd.exe (PID: 3408)
- $20,000PDF.exe (PID: 2484)
- $20,000PDF.exe (PID: 2404)
- $20,000PDF.exe (PID: 4040)
- xhd.exe (PID: 2732)
- xhd.exe (PID: 3276)
- xhd.exe (PID: 2364)
- xhd.exe (PID: 3640)
- $20,000PDF.exe (PID: 2952)
- $20,000PDF.exe (PID: 3208)
- xhd.exe (PID: 2808)
- xhd.exe (PID: 1904)
- xhd.exe (PID: 4076)
- xhd.exe (PID: 2632)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2472)
- $20,000PDF.exe (PID: 2404)
Starts CMD.EXE for commands execution
- chkdsk.exe (PID: 2276)
Application launched itself
- xhd.exe (PID: 2808)
- WinRAR.exe (PID: 3064)
Drop AutoIt3 executable file
- $20,000PDF.exe (PID: 2404)
INFO
Reads Internet Cache Settings
- chrome.exe (PID: 2612)
Dropped object may contain Bitcoin addresses
- xhd.exe (PID: 3408)
- xhd.exe (PID: 2632)
- xhd.exe (PID: 2364)
- xhd.exe (PID: 2808)
- xhd.exe (PID: 3276)
- $20,000PDF.exe (PID: 2404)
Application launched itself
- chrome.exe (PID: 2612)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
78
Monitored processes
44
Malicious processes
3
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1144 | "C:\Windows\System32\NAPSTAT.EXE" | C:\Windows\System32\NAPSTAT.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Access Protection Client UI Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1904 | C:\Users\admin\AppData\Local\Temp\12781533\xhd.exe C:\Users\admin\AppData\Local\Temp\12781533\TBQJW | C:\Users\admin\AppData\Local\Temp\12781533\xhd.exe | — | xhd.exe | |||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script Exit code: 0 Version: 3, 3, 14, 5 Modules
| |||||||||||||||
| 2276 | "C:\Windows\System32\chkdsk.exe" | C:\Windows\System32\chkdsk.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Check Disk Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2348 | "C:\Windows\System32\chkdsk.exe" | C:\Windows\System32\chkdsk.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Check Disk Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2364 | "C:\Users\admin\AppData\Local\Temp\12781533\xhd.exe" lst=cjd | C:\Users\admin\AppData\Local\Temp\12781533\xhd.exe | — | $20,000PDF.exe | |||||||||||
User: admin Company: AutoIt Team Integrity Level: HIGH Description: AutoIt v3 Script Exit code: 0 Version: 3, 3, 14, 5 Modules
| |||||||||||||||
| 2400 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIa3064.13434\$20,000PDF.zip | C:\Program Files\WinRAR\WinRAR.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2404 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2472.13962\$20,000PDF.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2472.13962\$20,000PDF.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2472 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIa3064.13147\$20,000PDF.zip | C:\Program Files\WinRAR\WinRAR.exe | WinRAR.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2484 | "C:\Users\admin\Desktop\$20,000PDF.exe" | C:\Users\admin\Desktop\$20,000PDF.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 10 Modules
| |||||||||||||||
| 2548 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe | — | xhd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Services Installation Utility Exit code: 0 Version: 4.6.1055.0 built by: NETFXREL2 Modules
| |||||||||||||||
Total events
3 921
Read events
3 812
Write events
106
Delete events
3
Modification events
| (PID) Process: | (2684) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2612-13189597715130250 |
Value: 259 | |||
| (PID) Process: | (2612) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2612) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2612) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2612) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2612) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2612) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3516-13180984670829101 |
Value: 0 | |||
| (PID) Process: | (2612) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (2612) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
| (PID) Process: | (2612) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 2612-13189597715130250 |
Value: 259 | |||
Executable files
2
Suspicious files
60
Text files
131
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2612 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\482f4e35-356e-4d9d-a4b2-20e99cb2c8d0.tmp | — | |
MD5:— | SHA256:— | |||
| 2612 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2612 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2612 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\9b1c76dc-94b4-4708-9a6f-b0a9e76a37bd.tmp | — | |
MD5:— | SHA256:— | |||
| 2612 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:— | SHA256:— | |||
| 2612 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\CacheStorage\e6622492fa163609ddd4212f54512baa07929ed3\caecb3bd-7969-4305-84d6-3a376453ec73\index-dir\temp-index | — | |
MD5:— | SHA256:— | |||
| 2612 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF2475fc.TMP | text | |
MD5:— | SHA256:— | |||
| 2612 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2612 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2612 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF24760b.TMP | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
23
DNS requests
15
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2612 | chrome.exe | 216.58.206.3:443 | www.google.de | Google Inc. | US | whitelisted |
2612 | chrome.exe | 172.217.22.3:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2612 | chrome.exe | 172.217.16.202:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
2612 | chrome.exe | 216.58.207.35:443 | www.gstatic.com | Google Inc. | US | whitelisted |
2612 | chrome.exe | 13.107.42.13:443 | onedrive.live.com | Microsoft Corporation | US | malicious |
2612 | chrome.exe | 64.233.166.196:443 | apis.google.com | Google Inc. | US | unknown |
2612 | chrome.exe | 13.107.42.12:443 | jthsfw.am.files.1drv.com | Microsoft Corporation | US | suspicious |
2612 | chrome.exe | 172.217.22.68:443 | www.google.com | Google Inc. | US | whitelisted |
2612 | chrome.exe | 172.217.22.78:443 | sb-ssl.google.com | Google Inc. | US | whitelisted |
2612 | chrome.exe | 172.217.18.106:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
www.google.de |
| whitelisted |
www.gstatic.com |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
ssl.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
onedrive.live.com |
| shared |
jthsfw.am.files.1drv.com |
| whitelisted |
www.google.com |
| malicious |