| File name: | opener(1).exe |
| Full analysis: | https://app.any.run/tasks/917bf99e-da09-4255-b4ec-48bdd14238cb |
| Verdict: | Malicious activity |
| Analysis date: | May 09, 2025, 11:19:59 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 6 sections |
| MD5: | C1EB92FEE8B6423ED79570F75D519152 |
| SHA1: | 63F41AA86943FEE372D45D26B97B0B8693EFDC89 |
| SHA256: | 85D3B43C024F732E55D49A04DBC9DAEB0231F9D92E9ECBDC5DD19BE39F069736 |
| SSDEEP: | 98304:BKY7YbSb4Y6ZhkDQet54nHZUMtHfktEzafhOsE+XZ0Ommp43vOrPKjejYuAnZCrl:+crfk881mw2/ki73V |
MALICIOUS
Antivirus name has been found in the command line (generic signature)
- MsMpEng.exe (PID: 14236)
SUSPICIOUS
Executable content was dropped or overwritten
- opener(1).exe (PID: 728)
- CCleaner64.exe (PID: 3900)
- CCleaner64.exe (PID: 7728)
- uninstall.exe (PID: 8316)
- Un_A.exe (PID: 8540)
- CCleaner64.exe (PID: 8576)
- helper.exe (PID: 10832)
- helper.exe (PID: 14444)
- uninstaller.exe (PID: 12420)
- Un_A.exe (PID: 15356)
- GoogleUpdateSetup.exe (PID: 15704)
- GoogleUpdateSetup.exe (PID: 15940)
- unins000.exe (PID: 17252)
- _iu14D2N.tmp (PID: 17396)
- MicrosoftEdgeUpdateSetup.exe (PID: 10848)
The process drops C-runtime libraries
- opener(1).exe (PID: 728)
Process drops python dynamic module
- opener(1).exe (PID: 728)
Application launched itself
- opener(1).exe (PID: 728)
- CCleaner64.exe (PID: 7696)
- CCleaner64.exe (PID: 5964)
- CCleaner64.exe (PID: 7728)
- CCleaner64.exe (PID: 3900)
- setup.exe (PID: 6660)
- helper.exe (PID: 10832)
- identity_helper.exe (PID: 13104)
- identity_helper.exe (PID: 15380)
- setup.exe (PID: 13168)
- setup.exe (PID: 12920)
- Skype.exe (PID: 16660)
- unins000.exe (PID: 16668)
- setup.exe (PID: 17336)
- setup.exe (PID: 16556)
Loads Python modules
- opener(1).exe (PID: 4000)
There is functionality for taking screenshot (YARA)
- opener(1).exe (PID: 728)
- opener(1).exe (PID: 4000)
Process drops legitimate windows executable
- opener(1).exe (PID: 728)
- MicrosoftEdgeUpdateSetup.exe (PID: 16400)
- MicrosoftEdgeUpdateSetup.exe (PID: 10848)
- MicrosoftEdgeUpdate.exe (PID: 4376)
Reads security settings of Internet Explorer
- CCleaner64.exe (PID: 7696)
- CCleaner64.exe (PID: 5964)
- CCleaner64.exe (PID: 7728)
- OfficeC2RClient.exe (PID: 5936)
- CCleaner64.exe (PID: 3900)
- IntegratedOffice.exe (PID: 7328)
- OfficeC2RClient.exe (PID: 8856)
- officesvcmgr.exe (PID: 8188)
- IntegratedOffice.exe (PID: 8284)
- culauncher.exe (PID: 8412)
- OfficeC2RClient.exe (PID: 8476)
Reads the date of Windows installation
- CCleaner64.exe (PID: 7696)
- CCleaner64.exe (PID: 5964)
- CCleaner64.exe (PID: 3900)
- CCleaner64.exe (PID: 7728)
Reads Internet Explorer settings
- CCleaner64.exe (PID: 3900)
- CCleaner64.exe (PID: 7728)
Searches for installed software
- CCleaner64.exe (PID: 7728)
- CCleaner64.exe (PID: 3900)
- OfficeC2RClient.exe (PID: 8856)
- OfficeC2RClient.exe (PID: 8476)
Starts itself from another location
- uninstall.exe (PID: 8316)
- uninstaller.exe (PID: 12420)
- javaws.exe (PID: 14328)
- javaws.exe (PID: 9060)
- helper.exe (PID: 14444)
- unins000.exe (PID: 17252)
Checks for external IP
- CCleaner64.exe (PID: 7728)
- CCleaner64.exe (PID: 3900)
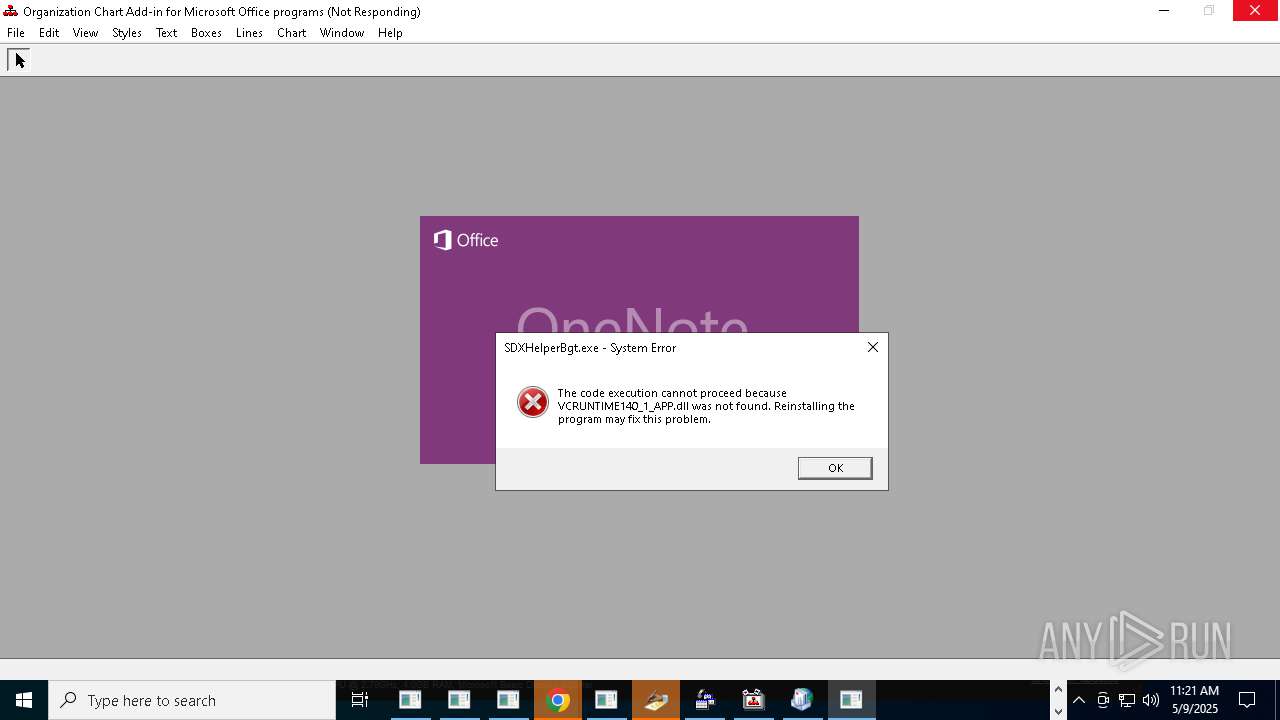
Executes application which crashes
- chrome_pwa_launcher.exe (PID: 9080)
- OfficeScrSanBroker.exe (PID: 13004)
- default-browser-agent.exe (PID: 9724)
- plugin-container.exe (PID: 12192)
- FLTLDR.EXE (PID: 6436)
- Microsoft.Mashup.Container.NetFX45.exe (PID: 14100)
- SenseAadAuthenticator.exe (PID: 10492)
- GUP.exe (PID: 9308)
- cookie_exporter.exe (PID: 16376)
- msedge_pwa_launcher.exe (PID: 16276)
- cookie_exporter.exe (PID: 11208)
- msedge_pwa_launcher.exe (PID: 15592)
- Microsoft.Mashup.Container.NetFX40.exe (PID: 5232)
Malware-specific behavior (creating "System.dll" in Temp)
- helper.exe (PID: 10832)
- helper.exe (PID: 14444)
- Un_A.exe (PID: 15356)
Starts application with an unusual extension
- unins000.exe (PID: 17252)
Starts a Microsoft application from unusual location
- MicrosoftEdgeUpdate.exe (PID: 12012)
- MicrosoftEdgeUpdateSetup.exe (PID: 10848)
- MicrosoftEdgeUpdate.exe (PID: 4376)
Uses ROUTE.EXE to obtain the routing table information
- iediagcmd.exe (PID: 9276)
Suspicious use of NETSH.EXE
- iediagcmd.exe (PID: 9276)
Uses REG/REGEDIT.EXE to modify registry
- Skype.exe (PID: 16660)
Process uses IPCONFIG to discover network configuration
- iediagcmd.exe (PID: 9276)
INFO
Checks supported languages
- opener(1).exe (PID: 728)
- opener(1).exe (PID: 4000)
- CCleaner64.exe (PID: 7696)
- CCleaner.exe (PID: 8188)
- CCleaner64.exe (PID: 5964)
- CCleanerReactivator.exe (PID: 7488)
- CCleanerBugReport.exe (PID: 8168)
- CCleanerPerformanceOptimizerService.exe (PID: 7704)
- wa_3rd_party_host_64.exe (PID: 2140)
- appvcleaner.exe (PID: 7768)
- CCleaner64.exe (PID: 3900)
- MavInject32.exe (PID: 7404)
- AppVShNotify.exe (PID: 4272)
- CCleaner64.exe (PID: 7728)
- IntegratedOffice.exe (PID: 7328)
- AppVShNotify.exe (PID: 8232)
- officesvcmgr.exe (PID: 8188)
- OfficeC2RClient.exe (PID: 5936)
- MavInject32.exe (PID: 8356)
- OfficeClickToRun.exe (PID: 7756)
- InspectorOfficeGadget.exe (PID: 8244)
- IMESharePointDictionary.exe (PID: 8724)
- IntegratedOffice.exe (PID: 8284)
- appvcleaner.exe (PID: 7280)
- OfficeC2RClient.exe (PID: 8856)
- OfficeC2RClient.exe (PID: 8552)
- mip.exe (PID: 8820)
- ShapeCollector.exe (PID: 8908)
- msinfo32.exe (PID: 9108)
- LICLUA.EXE (PID: 9176)
- culauncher.exe (PID: 8412)
- InspectorOfficeGadget.exe (PID: 7680)
- ShapeCollector.exe (PID: 9116)
- OfficeC2RClient.exe (PID: 8476)
- fzputtygen.exe (PID: 8480)
- fzsftp.exe (PID: 8752)
- filezilla.exe (PID: 8356)
- fzstorj.exe (PID: 8816)
- chrome_proxy.exe (PID: 6828)
- VSTOInstaller.exe (PID: 7404)
- InputPersonalization.exe (PID: 8776)
- uninstall.exe (PID: 8316)
- elevation_service.exe (PID: 8480)
- notification_helper.exe (PID: 8216)
- OfficeClickToRun.exe (PID: 8616)
- CCleaner64.exe (PID: 8576)
- chrome_pwa_launcher.exe (PID: 9080)
- Un_A.exe (PID: 8540)
- officesvcmgr.exe (PID: 8712)
Reads the computer name
- opener(1).exe (PID: 728)
- CCleaner.exe (PID: 8188)
- CCleaner64.exe (PID: 7696)
- CCleaner64.exe (PID: 5964)
- CCleanerPerformanceOptimizerService.exe (PID: 7704)
- CCleanerBugReport.exe (PID: 8168)
- AppVShNotify.exe (PID: 4272)
- CCleaner64.exe (PID: 3900)
- CCleaner64.exe (PID: 7728)
- OfficeClickToRun.exe (PID: 7756)
- InspectorOfficeGadget.exe (PID: 7680)
- AppVShNotify.exe (PID: 8232)
- OfficeC2RClient.exe (PID: 5936)
- InspectorOfficeGadget.exe (PID: 8244)
- officesvcmgr.exe (PID: 8188)
- IntegratedOffice.exe (PID: 7328)
- InputPersonalization.exe (PID: 8776)
- OfficeC2RClient.exe (PID: 8856)
- mip.exe (PID: 8820)
- ShapeCollector.exe (PID: 8908)
- ShapeCollector.exe (PID: 9116)
- msinfo32.exe (PID: 9108)
- LICLUA.EXE (PID: 9176)
- OfficeC2RClient.exe (PID: 8476)
- IntegratedOffice.exe (PID: 8284)
- culauncher.exe (PID: 8412)
- officesvcmgr.exe (PID: 8712)
- VSTOInstaller.exe (PID: 7404)
- filezilla.exe (PID: 8356)
- OfficeClickToRun.exe (PID: 8616)
- CCleaner64.exe (PID: 8576)
Create files in a temporary directory
- opener(1).exe (PID: 728)
- OfficeC2RClient.exe (PID: 5936)
- OfficeClickToRun.exe (PID: 7756)
- OfficeC2RClient.exe (PID: 8856)
- OfficeC2RClient.exe (PID: 8476)
- IntegratedOffice.exe (PID: 7328)
- uninstall.exe (PID: 8316)
- IntegratedOffice.exe (PID: 8284)
The sample compiled with english language support
- opener(1).exe (PID: 728)
- CCleaner64.exe (PID: 3900)
- CCleaner64.exe (PID: 7728)
- uninstall.exe (PID: 8316)
- CCleaner64.exe (PID: 8576)
- uninstaller.exe (PID: 12420)
- GoogleUpdateSetup.exe (PID: 15704)
- helper.exe (PID: 14444)
- GoogleUpdateSetup.exe (PID: 15940)
- MicrosoftEdgeUpdateSetup.exe (PID: 16400)
- MicrosoftEdgeUpdateSetup.exe (PID: 10848)
- MicrosoftEdgeUpdate.exe (PID: 4376)
Application launched itself
- AcroCEF.exe (PID: 7172)
- chrome.exe (PID: 9056)
- chrome.exe (PID: 7916)
- chrmstp.exe (PID: 8516)
- chrome.exe (PID: 10364)
- chrome.exe (PID: 10560)
- msedge.exe (PID: 11040)
- firefox.exe (PID: 5452)
- firefox.exe (PID: 8408)
- firefox.exe (PID: 2284)
- msedge.exe (PID: 8884)
Reads Environment values
- CCleaner.exe (PID: 8188)
- CCleaner64.exe (PID: 7696)
- CCleaner64.exe (PID: 5964)
- CCleaner64.exe (PID: 7728)
- CCleaner64.exe (PID: 3900)
- culauncher.exe (PID: 8412)
- CCleaner64.exe (PID: 8576)
PyInstaller has been detected (YARA)
- opener(1).exe (PID: 728)
- opener(1).exe (PID: 4000)
Process checks computer location settings
- CCleaner64.exe (PID: 7696)
- CCleaner64.exe (PID: 5964)
- OfficeC2RClient.exe (PID: 5936)
- IntegratedOffice.exe (PID: 7328)
- IntegratedOffice.exe (PID: 8284)
- OfficeC2RClient.exe (PID: 8476)
- CCleaner64.exe (PID: 3900)
- CCleaner64.exe (PID: 7728)
- OfficeC2RClient.exe (PID: 8856)
Reads the machine GUID from the registry
- CCleanerBugReport.exe (PID: 8168)
- appvcleaner.exe (PID: 7768)
- InspectorOfficeGadget.exe (PID: 7680)
- CCleaner64.exe (PID: 3900)
- CCleaner64.exe (PID: 7728)
- InspectorOfficeGadget.exe (PID: 8244)
- appvcleaner.exe (PID: 7280)
- culauncher.exe (PID: 8412)
- VSTOInstaller.exe (PID: 7404)
Reads CPU info
- CCleanerBugReport.exe (PID: 8168)
- CCleaner64.exe (PID: 7728)
- CCleaner64.exe (PID: 3900)
Reads Microsoft Office registry keys
- OfficeC2RClient.exe (PID: 5936)
- OfficeClickToRun.exe (PID: 7756)
- IntegratedOffice.exe (PID: 7328)
- officesvcmgr.exe (PID: 8188)
- IntegratedOffice.exe (PID: 8284)
- OfficeC2RClient.exe (PID: 8856)
- OfficeC2RClient.exe (PID: 8476)
- officesvcmgr.exe (PID: 8712)
- OfficeC2RClient.exe (PID: 8552)
Reads product name
- CCleaner64.exe (PID: 7728)
- CCleaner64.exe (PID: 3900)
Creates files in the program directory
- CCleaner64.exe (PID: 3900)
- CCleaner64.exe (PID: 7728)
Checks proxy server information
- OfficeClickToRun.exe (PID: 7756)
- OfficeC2RClient.exe (PID: 5936)
- IntegratedOffice.exe (PID: 7328)
- OfficeC2RClient.exe (PID: 8856)
- officesvcmgr.exe (PID: 8188)
- IntegratedOffice.exe (PID: 8284)
- OfficeC2RClient.exe (PID: 8476)
Reads the software policy settings
- CCleaner64.exe (PID: 3900)
- CCleaner64.exe (PID: 7728)
- IntegratedOffice.exe (PID: 7328)
- officesvcmgr.exe (PID: 8188)
- culauncher.exe (PID: 8412)
- IntegratedOffice.exe (PID: 8284)
Creates files or folders in the user directory
- InputPersonalization.exe (PID: 8776)
- officesvcmgr.exe (PID: 8188)
- filezilla.exe (PID: 8356)
FileZilla executable
- opener(1).exe (PID: 4000)
- uninstall.exe (PID: 8316)
FileZilla mutex has been found
- filezilla.exe (PID: 8356)
The sample compiled with arabic language support
- GoogleUpdateSetup.exe (PID: 15704)
- GoogleUpdateSetup.exe (PID: 15940)
The sample compiled with bulgarian language support
- GoogleUpdateSetup.exe (PID: 15704)
- GoogleUpdateSetup.exe (PID: 15940)
The sample compiled with czech language support
- GoogleUpdateSetup.exe (PID: 15704)
- GoogleUpdateSetup.exe (PID: 15940)
The sample compiled with german language support
- GoogleUpdateSetup.exe (PID: 15704)
- GoogleUpdateSetup.exe (PID: 15940)
The sample compiled with spanish language support
- GoogleUpdateSetup.exe (PID: 15704)
- GoogleUpdateSetup.exe (PID: 15940)
The sample compiled with Italian language support
- GoogleUpdateSetup.exe (PID: 15704)
- GoogleUpdateSetup.exe (PID: 15940)
The sample compiled with Indonesian language support
- GoogleUpdateSetup.exe (PID: 15704)
- GoogleUpdateSetup.exe (PID: 15940)
The sample compiled with korean language support
- GoogleUpdateSetup.exe (PID: 15704)
- GoogleUpdateSetup.exe (PID: 15940)
The sample compiled with french language support
- GoogleUpdateSetup.exe (PID: 15704)
- GoogleUpdateSetup.exe (PID: 15940)
The sample compiled with japanese language support
- GoogleUpdateSetup.exe (PID: 15704)
- GoogleUpdateSetup.exe (PID: 15940)
The sample compiled with polish language support
- GoogleUpdateSetup.exe (PID: 15704)
- GoogleUpdateSetup.exe (PID: 15940)
The sample compiled with portuguese language support
- GoogleUpdateSetup.exe (PID: 15704)
- GoogleUpdateSetup.exe (PID: 15940)
The sample compiled with swedish language support
- GoogleUpdateSetup.exe (PID: 15704)
- GoogleUpdateSetup.exe (PID: 15940)
The sample compiled with turkish language support
- GoogleUpdateSetup.exe (PID: 15704)
- GoogleUpdateSetup.exe (PID: 15940)
The sample compiled with chinese language support
- GoogleUpdateSetup.exe (PID: 15704)
- GoogleUpdateSetup.exe (PID: 15940)
The sample compiled with slovak language support
- GoogleUpdateSetup.exe (PID: 15704)
- GoogleUpdateSetup.exe (PID: 15940)
The sample compiled with russian language support
- GoogleUpdateSetup.exe (PID: 15704)
- GoogleUpdateSetup.exe (PID: 15940)
Prints a route via ROUTE.EXE
- ROUTE.EXE (PID: 9272)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:05:09 11:14:32+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.43 |
| CodeSize: | 172032 |
| InitializedDataSize: | 154624 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xce10 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
725
Monitored processes
553
Malicious processes
8
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | reg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 448 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4972 --field-trial-handle=2028,i,16024426338443704505,12986504286236887001,262144 --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 672 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 720 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5724 --field-trial-handle=2312,i,14600701987187880428,7681635510787193317,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 728 | "C:\Users\admin\AppData\Local\Temp\opener(1).exe" | C:\Users\admin\AppData\Local\Temp\opener(1).exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 732 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | ktab.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1120 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2524 -childID 2 -isForBrowser -prefsHandle 4072 -prefMapHandle 4068 -prefsLen 26876 -prefMapSize 244583 -jsInitHandle 1320 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {3d78e805-2b56-4a42-9c53-4195bb743600} 8408 "\\.\pipe\gecko-crash-server-pipe.8408" 11156d94a10 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1196 | "C:\Program Files (x86)\Microsoft\EdgeCore\122.0.2365.59\msedgewebview2.exe" | C:\Program Files (x86)\Microsoft\EdgeCore\122.0.2365.59\msedgewebview2.exe | — | opener(1).exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge WebView2 Exit code: 13 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1196 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2308 --field-trial-handle=2312,i,14600701987187880428,7681635510787193317,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1560 | "C:\Program Files\Windows Defender\NisSrv.exe" | C:\Program Files\Windows Defender\NisSrv.exe | — | opener(1).exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Network Realtime Inspection Service Exit code: 2147943463 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
334 909
Read events
326 942
Write events
7 343
Delete events
624
Modification events
| (PID) Process: | (3900) CCleaner64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Piriform\CCleaner |
| Operation: | write | Name: | DAST |
Value: 05/09/2025 11:20:29 | |||
| (PID) Process: | (3900) CCleaner64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Piriform\CCleaner |
| Operation: | write | Name: | T8062 |
Value: 0 | |||
| (PID) Process: | (3900) CCleaner64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Piriform\CCleaner |
| Operation: | write | Name: | UpdateBackground |
Value: 1 | |||
| (PID) Process: | (7728) CCleaner64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Piriform\CCleaner |
| Operation: | write | Name: | UpdateBackground |
Value: 1 | |||
| (PID) Process: | (5936) OfficeC2RClient.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (5936) OfficeC2RClient.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (5936) OfficeC2RClient.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (5936) OfficeC2RClient.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (5936) OfficeC2RClient.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (5936) OfficeC2RClient.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
Executable files
461
Suspicious files
1 339
Text files
281
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 728 | opener(1).exe | C:\Users\admin\AppData\Local\Temp\_MEI7282\_lzma.pyd | executable | |
MD5:D63E2E743EA103626D33B3C1D882F419 | SHA256:7C2D2030D5D246739C5D85F087FCF404BC36E1815E69A8AC7C9541267734FC28 | |||
| 728 | opener(1).exe | C:\Users\admin\AppData\Local\Temp\_MEI7282\_decimal.pyd | executable | |
MD5:21FCB8E3D4310346A5DC1A216E7E23CA | SHA256:9A0E05274CAD8D90F6BA6BC594261B36BFBDDF4F5CA6846B6367FE6A4E2FDCE4 | |||
| 728 | opener(1).exe | C:\Users\admin\AppData\Local\Temp\_MEI7282\api-ms-win-core-debug-l1-1-0.dll | executable | |
MD5:33BBECE432F8DA57F17BF2E396EBAA58 | SHA256:7CF0944901F7F7E0D0B9AD62753FC2FE380461B1CCE8CDC7E9C9867C980E3B0E | |||
| 728 | opener(1).exe | C:\Users\admin\AppData\Local\Temp\_MEI7282\api-ms-win-core-file-l1-2-0.dll | executable | |
MD5:1C58526D681EFE507DEB8F1935C75487 | SHA256:EF13DCE8F71173315DFC64AB839B033AB19A968EE15230E9D4D2C9D558EFEEE2 | |||
| 728 | opener(1).exe | C:\Users\admin\AppData\Local\Temp\_MEI7282\_socket.pyd | executable | |
MD5:566CB4D39B700C19DBD7175BD4F2B649 | SHA256:77EBA293FE03253396D7BB6E575187CD026C80766D7A345EB72AD92F0BBBC3AA | |||
| 728 | opener(1).exe | C:\Users\admin\AppData\Local\Temp\_MEI7282\VCRUNTIME140.dll | executable | |
MD5:32DA96115C9D783A0769312C0482A62D | SHA256:8B10C53241726B0ACC9F513157E67FCB01C166FEC69E5E38CA6AADA8F9A3619F | |||
| 728 | opener(1).exe | C:\Users\admin\AppData\Local\Temp\_MEI7282\api-ms-win-core-interlocked-l1-1-0.dll | executable | |
MD5:C6024CC04201312F7688A021D25B056D | SHA256:8751D30DF554AF08EF42D2FAA0A71ABCF8C7D17CE9E9FF2EA68A4662603EC500 | |||
| 728 | opener(1).exe | C:\Users\admin\AppData\Local\Temp\_MEI7282\_bz2.pyd | executable | |
MD5:684D656AADA9F7D74F5A5BDCF16D0EDB | SHA256:A5DFB4A663DEF3D2276B88866F6D220F6D30CC777B5D841CF6DBB15C6858017C | |||
| 728 | opener(1).exe | C:\Users\admin\AppData\Local\Temp\_MEI7282\api-ms-win-core-console-l1-1-0.dll | executable | |
MD5:E8B9D74BFD1F6D1CC1D99B24F44DA796 | SHA256:B1B3FD40AB437A43C8DB4994CCFFC7F88000CC8BB6E34A2BCBFF8E2464930C59 | |||
| 728 | opener(1).exe | C:\Users\admin\AppData\Local\Temp\_MEI7282\api-ms-win-core-datetime-l1-1-0.dll | executable | |
MD5:CFE0C1DFDE224EA5FED9BD5FF778A6E0 | SHA256:0D0F80CBF476AF5B1C9FD3775E086ED0DFDB510CD0CC208EC1CCB04572396E3E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
75
TCP/UDP connections
347
DNS requests
247
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.20.102.93:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.17.147.99:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3900 | CCleaner64.exe | GET | 200 | 95.100.146.48:80 | http://ncc.avast.com/ncc.txt | unknown | — | — | whitelisted |
7728 | CCleaner64.exe | GET | 200 | 95.100.146.48:80 | http://ncc.avast.com/ncc.txt | unknown | — | — | whitelisted |
7204 | SIHClient.exe | GET | 200 | 2.20.102.93:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7204 | SIHClient.exe | GET | 200 | 2.20.102.93:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6344 | Acrobat.exe | GET | 200 | 2.16.38.4:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAfy81yHqHeveu%2FpR5k1Jb0%3D | unknown | — | — | whitelisted |
7728 | CCleaner64.exe | GET | 200 | 142.250.185.131:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | whitelisted |
7728 | CCleaner64.exe | GET | 200 | 2.16.38.4:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.17.147.99:80 | crl.microsoft.com | Akamai International B.V. | CZ | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.20.102.93:80 | www.microsoft.com | RCS & RDS | RO | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
7944 | AcroCEF.exe | 95.100.184.205:443 | geo2.adobe.com | AKAMAI-AS | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
geo2.adobe.com |
| whitelisted |
p13n.adobe.io |
| whitelisted |
ncc.avast.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Misc activity | ET INFO External IP Lookup Service in DNS Query (ip-info .ff .avast .com) |
7728 | CCleaner64.exe | Misc activity | ET INFO Observed External IP Lookup Domain (ip-info .ff .avast .com) in TLS SNI |
3900 | CCleaner64.exe | Misc activity | ET INFO Observed External IP Lookup Domain (ip-info .ff .avast .com) in TLS SNI |
9708 | javaw.exe | Potentially Bad Traffic | ET INFO Vulnerable Java Version 1.8.x Detected |
9708 | javaw.exe | Potentially Bad Traffic | ET INFO Vulnerable Java Version 1.8.x Detected |
11348 | pwsh.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Front Door domain observed in TLS SNI ( .azurefd .net) |