analyze malware
- Huge database of samples and IOCs
- Custom VM setup
- Unlimited submissions
- Interactive approach
| URL: | http://fctbank.top |
| Full analysis: | https://app.any.run/tasks/13cce2b3-752b-40ce-b704-b3e78f1e9165 |
| Verdict: | Malicious activity |
| Analysis date: | December 02, 2019, 23:06:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 1B658CCDD51A9BF9CF70A6FAA38B1699 |
| SHA1: | F770BD0BA4332B421588669659FE83A2DD813DDB |
| SHA256: | 85D1DAEA1DCA18659A684066EBF931ADA748BB5FB93547BC9348CCCE3152FA74 |
| SSDEEP: | 3:N1KYR6A:CYRZ |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Changes internet zones settings
- iexplore.exe (PID: 2412)
Reads Internet Cache Settings
- iexplore.exe (PID: 3228)
Creates files in the user directory
- iexplore.exe (PID: 3228)
- iexplore.exe (PID: 2412)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 3228)
Reads internet explorer settings
- iexplore.exe (PID: 3228)
Application launched itself
- iexplore.exe (PID: 2412)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
36
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 2412 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://fctbank.top" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 8.00.7600.16385 (win7_rtm.090713-1255) | ||||
| 3228 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2412 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | |
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 8.00.7600.16385 (win7_rtm.090713-1255) | ||||
Total events
465
Read events
365
Write events
98
Delete events
2
Modification events
| (PID) Process: | (2412) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2412) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2412) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2412) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2412) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2412) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000092000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2412) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {76DA799D-1558-11EA-AB41-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (2412) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (2412) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 2 | |||
| (PID) Process: | (2412) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E3070C00010002001700070009004E02 | |||
Executable files
0
Suspicious files
0
Text files
97
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2412 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2412 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3228 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\index.dat | dat | |
MD5:C89014871658E7B3D532888CF282C1EB | SHA256:0E478B3AFE1BFD923A0F2CF6798ADBC92587E8A76AB64AEDEE234A5AEDE54F51 | |||
| 3228 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DKEYJM0W\finsurance_top[1].txt | — | |
MD5:— | SHA256:— | |||
| 3228 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\index.dat | dat | |
MD5:A936C3F494F5B81E497304A30AAF1081 | SHA256:31A12C3DB215E481ABBEF673DED10BEE8349D0EC2E2E8C7ACC27E6968C49C0A4 | |||
| 3228 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\MSIMGSIZ.DAT | smt | |
MD5:66D20D9CF2322C4B662EA6E754325CD7 | SHA256:D6A4C1DF6554CDC6D56F1D92FD09F3D7991E3620151F00DB51D55C8EE260C3CC | |||
| 3228 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DKEYJM0W\finsurance_top[1].htm | html | |
MD5:6A974C08420511C2AEEA0603162C3C04 | SHA256:2AD77D1CA1D9488ED0A776C3D59A74C08F9617E87B3BB2197336923960967B19 | |||
| 3228 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@finsurance[1].txt | text | |
MD5:0F905B18E516175AAC5F77C99BBCEADB | SHA256:D7EB2A1FC8CDEDA5C6F708127BCE9EE3889A55C0540D5FD92DC0C469560CD3BD | |||
| 3228 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\index.dat | dat | |
MD5:1A46782E24D0B5237E246321520A6528 | SHA256:7D3CAFE057527A68AB9AB21E7336530E69FC1FDB39CB18B2D386F154ECE0803B | |||
| 3228 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\AAL4SL9H\desktop.ini | ini | |
MD5:4A3DEB274BB5F0212C2419D3D8D08612 | SHA256:2842973D15A14323E08598BE1DFB87E54BF88A76BE8C7BC94C56B079446EDF38 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
84
TCP/UDP connections
25
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
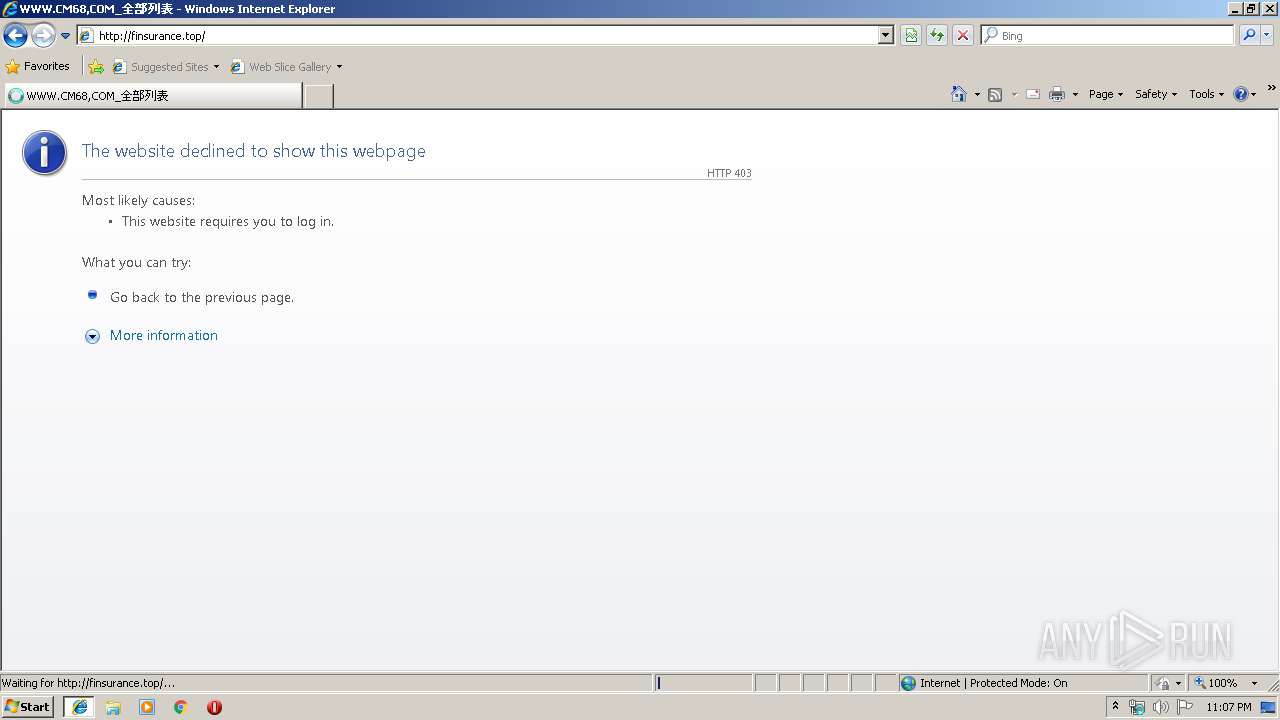
3228 | iexplore.exe | GET | 200 | 104.27.187.44:80 | http://finsurance.top/template/3457/css/templatemo_style.css | US | text | 2.44 Kb | suspicious |
3228 | iexplore.exe | GET | 200 | 104.27.187.44:80 | http://finsurance.top/ | US | text | 81.1 Kb | suspicious |
3228 | iexplore.exe | GET | 200 | 104.27.187.44:80 | http://finsurance.top/template/3457/images/header.png | US | image | 136 b | suspicious |
3228 | iexplore.exe | GET | 200 | 104.27.187.44:80 | http://finsurance.top/template/3457/images/gallery/gallery-item2.jpg | US | image | 12.8 Kb | suspicious |
3228 | iexplore.exe | GET | 403 | 47.52.69.31:80 | http://fctbank.top/ | HK | html | 209 b | suspicious |
3228 | iexplore.exe | GET | 200 | 104.27.187.44:80 | http://finsurance.top/template/3457/css/animate.css | US | text | 5.67 Kb | suspicious |
3228 | iexplore.exe | GET | 200 | 104.27.187.44:80 | http://finsurance.top/template/3457/images/gallery/gallery-item10.jpg | US | image | 25.3 Kb | suspicious |
3228 | iexplore.exe | GET | 200 | 104.27.187.44:80 | http://finsurance.top/template/3457/images/gallery/gallery-item11.jpg | US | image | 19.8 Kb | suspicious |
3228 | iexplore.exe | GET | 200 | 183.131.207.66:80 | http://ia.51.la/go1?id=20472569&rt=1575328046364&rl=1280*720&lang=en-us&ct=unknow&pf=1&ins=1&vd=1&ce=1&cd=32&ds=%25E8%25AD%25A6%25E5%2591%258A%253A%25E6%259C%25AA%25E6%25BB%25BF18%25E5%25B2%2581%25E8%2580%2585%25E8%25AB%258B%25E5%258B%25BF%25E9%2580%25B2%25E5%2585%25A5WWW.CM68%252CCOM!%25E6%259C%25AC%25E7%25AB%2599%25E5%2585%25B1%25E6%259C%2589&ing=1&ekc=&sid=1575328046364&tt=WWW.CM68%252CCOM_%25E5%2585%25A8%25E9%2583%25A8%25E5%2588%2597%25E8%25A1%25A8&kw=WWW.CM68%252CCOM&cu=http%253A%252F%252Ffinsurance.top%252F&pu= | CN | — | — | whitelisted |
3228 | iexplore.exe | GET | 200 | 104.27.187.44:80 | http://finsurance.top/template/3457/images/gallery/gallery-item6.jpg | US | image | 19.4 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2412 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3228 | iexplore.exe | 104.27.187.44:80 | finsurance.top | Cloudflare Inc | US | suspicious |
3228 | iexplore.exe | 47.52.69.31:80 | fctbank.top | Alibaba (China) Technology Co., Ltd. | HK | suspicious |
3228 | iexplore.exe | 183.131.207.66:80 | ia.51.la | DaLi | CN | malicious |
3228 | iexplore.exe | 61.135.185.248:80 | api.share.baidu.com | China Unicom Beijing Province Network | CN | unknown |
3228 | iexplore.exe | 220.242.139.165:443 | js.users.51.la | — | CN | unknown |
3228 | iexplore.exe | 104.24.104.114:80 | ginsurance.top | Cloudflare Inc | US | shared |
— | — | 104.27.187.44:80 | finsurance.top | Cloudflare Inc | US | suspicious |
3228 | iexplore.exe | 104.28.28.39:80 | hinsurance.top | Cloudflare Inc | US | suspicious |
2412 | iexplore.exe | 104.24.104.114:80 | ginsurance.top | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
fctbank.top |
| suspicious |
www.bing.com |
| whitelisted |
finsurance.top |
| suspicious |
js.users.51.la |
| whitelisted |
ia.51.la |
| whitelisted |
api.share.baidu.com |
| whitelisted |
ginsurance.top |
| suspicious |
hinsurance.top |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
3228 | iexplore.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
3228 | iexplore.exe | A Network Trojan was detected | ET INFO Suspicious HTML Decimal Obfuscated Title - Possible Phishing Landing Apr 19 2017 |
— | — | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
3228 | iexplore.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
3228 | iexplore.exe | A Network Trojan was detected | ET INFO Suspicious HTML Decimal Obfuscated Title - Possible Phishing Landing Apr 19 2017 |
3228 | iexplore.exe | A Network Trojan was detected | ET INFO Suspicious HTML Decimal Obfuscated Title - Possible Phishing Landing Apr 19 2017 |