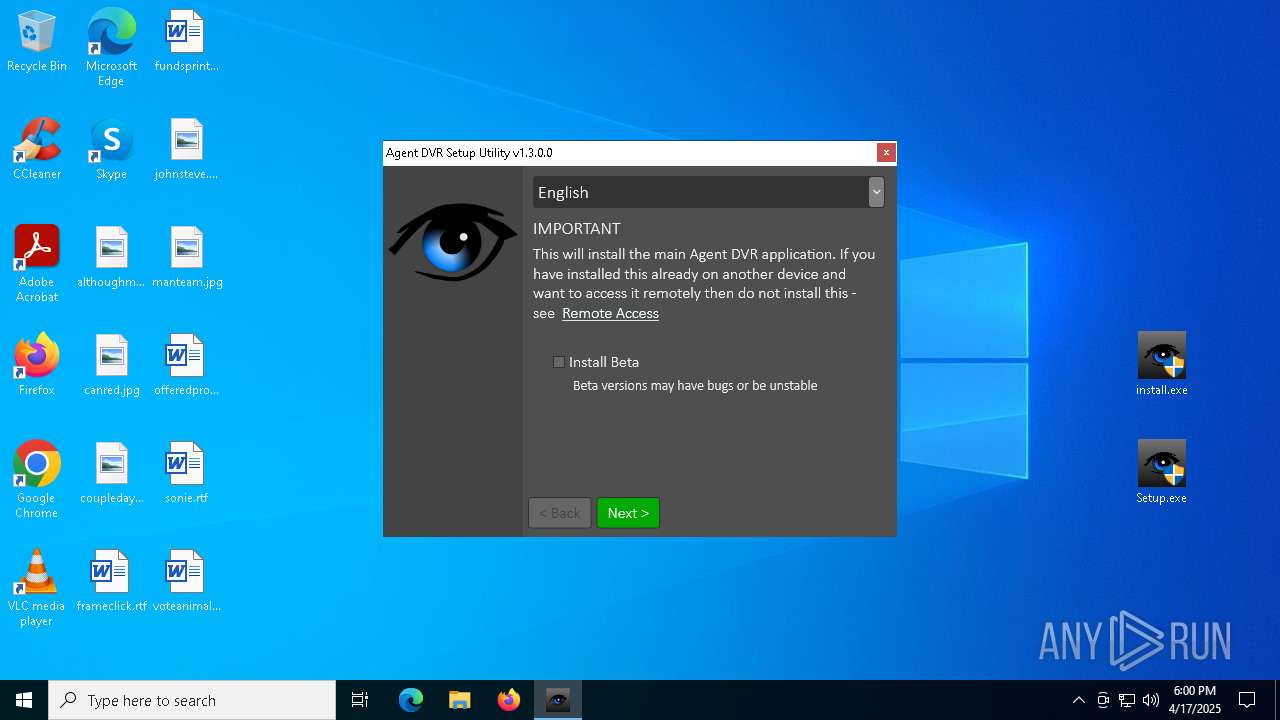
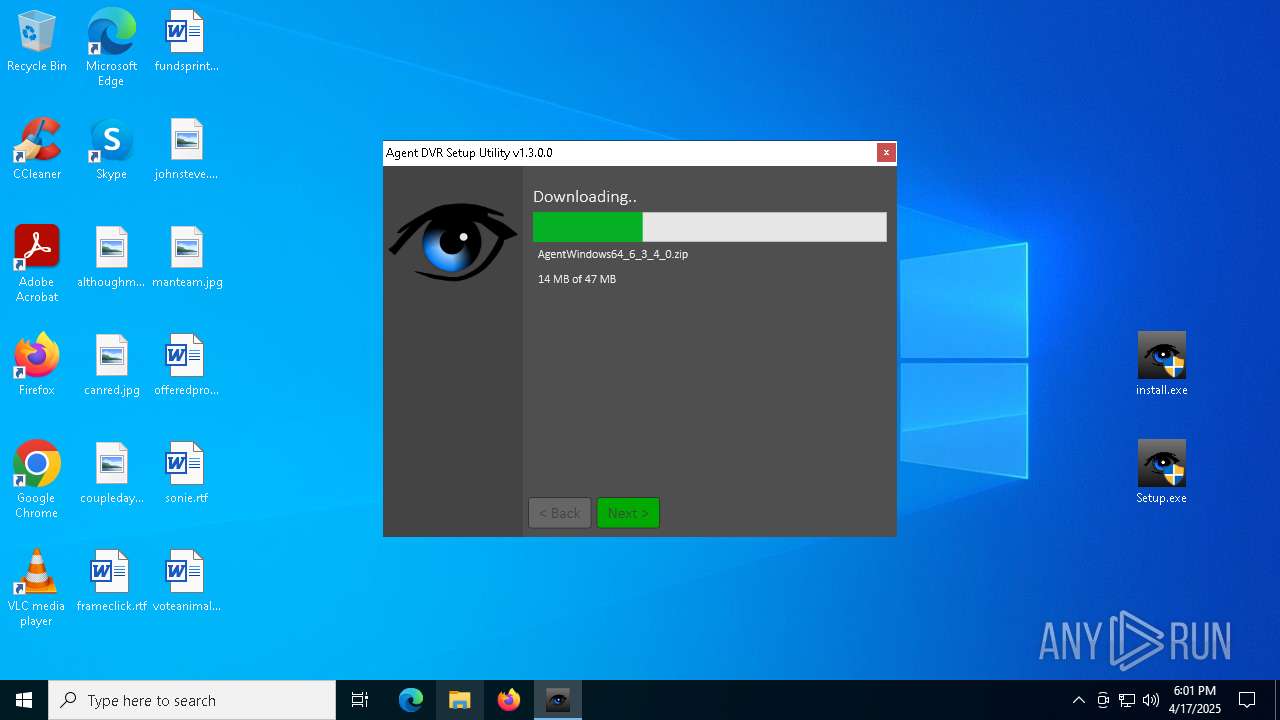
| File name: | Agent_Setup_Windows.zip |
| Full analysis: | https://app.any.run/tasks/5a48c79a-5f70-4d40-8eb1-8dd93b2d7269 |
| Verdict: | Malicious activity |
| Analysis date: | April 17, 2025, 18:00:22 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 8C7063B3E505BE4B56026D41C5EC7C38 |
| SHA1: | 95ED57D29EB4BDFC08CE9ECE8FD83C889F9C75B2 |
| SHA256: | 85C9D64E1AFDEF09C63716022448C72578DEF5DD8223A1FD42014DB97ED61384 |
| SSDEEP: | 6144:fHHY/I7SOtUOg/RtjaPT2ag51+8rcA+tLiVp+AVk2b9:fHHWLuUOgJRaL2aMMnp28iHx |
MALICIOUS
Changes the autorun value in the registry
- Setup.exe (PID: 5988)
SUSPICIOUS
Reads security settings of Internet Explorer
- Setup.exe (PID: 7844)
- install.exe (PID: 4040)
- Setup.exe (PID: 5988)
- AgentTray.exe (PID: 2268)
Reads the date of Windows installation
- install.exe (PID: 4040)
- Setup.exe (PID: 5988)
Adds/modifies Windows certificates
- install.exe (PID: 4040)
Windows service management via SC.EXE
- sc.exe (PID: 4300)
- sc.exe (PID: 8028)
Process drops legitimate windows executable
- Setup.exe (PID: 5988)
Searches for installed software
- Setup.exe (PID: 5988)
Creates a software uninstall entry
- Setup.exe (PID: 5988)
Creates a new Windows service
- sc.exe (PID: 5772)
Restarts service on failure
- sc.exe (PID: 5984)
The process drops C-runtime libraries
- Setup.exe (PID: 5988)
Executable content was dropped or overwritten
- Setup.exe (PID: 5988)
- Agent.exe (PID: 3896)
Executes as Windows Service
- Agent.exe (PID: 3896)
- WmiApSrv.exe (PID: 8512)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- Agent.exe (PID: 3896)
- Setup.exe (PID: 5988)
Uses NETSH.EXE to add a firewall rule or allowed programs
- Agent.exe (PID: 3896)
- Setup.exe (PID: 5988)
Starts SC.EXE for service management
- Agent.exe (PID: 5600)
The process executes VB scripts
- Setup.exe (PID: 5988)
Runs shell command (SCRIPT)
- wscript.exe (PID: 2772)
There is functionality for taking screenshot (YARA)
- Agent.exe (PID: 3896)
The process checks if it is being run in the virtual environment
- Agent.exe (PID: 3896)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7488)
Manual execution by a user
- Setup.exe (PID: 7844)
- Setup.exe (PID: 7796)
- firefox.exe (PID: 4408)
- install.exe (PID: 8160)
- install.exe (PID: 4040)
Checks supported languages
- Setup.exe (PID: 7844)
- Setup.exe (PID: 5988)
- Agent.exe (PID: 5600)
- Agent.exe (PID: 3896)
- turnserver.exe (PID: 7592)
- AgentTray.exe (PID: 2268)
- ffmpeg.exe (PID: 8832)
- install.exe (PID: 4040)
Reads the machine GUID from the registry
- Setup.exe (PID: 7844)
- Setup.exe (PID: 5988)
- AgentTray.exe (PID: 2268)
- Agent.exe (PID: 3896)
- ffmpeg.exe (PID: 8832)
- install.exe (PID: 4040)
Create files in a temporary directory
- Setup.exe (PID: 7844)
- Setup.exe (PID: 5988)
Reads the software policy settings
- install.exe (PID: 4040)
- Setup.exe (PID: 5988)
- slui.exe (PID: 7664)
- Agent.exe (PID: 3896)
- AgentTray.exe (PID: 2268)
- slui.exe (PID: 3024)
Checks proxy server information
- install.exe (PID: 4040)
- Setup.exe (PID: 5988)
- AgentTray.exe (PID: 2268)
- slui.exe (PID: 3024)
Process checks computer location settings
- install.exe (PID: 4040)
- Setup.exe (PID: 5988)
Creates files or folders in the user directory
- install.exe (PID: 4040)
Reads the computer name
- Setup.exe (PID: 5988)
- Agent.exe (PID: 5600)
- Agent.exe (PID: 3896)
- AgentTray.exe (PID: 2268)
- turnserver.exe (PID: 7592)
- Setup.exe (PID: 7844)
- install.exe (PID: 4040)
- ffmpeg.exe (PID: 8832)
Reads Environment values
- Setup.exe (PID: 5988)
Disables trace logs
- Setup.exe (PID: 5988)
- AgentTray.exe (PID: 2268)
Application launched itself
- firefox.exe (PID: 1052)
- firefox.exe (PID: 4408)
- chrome.exe (PID: 5380)
Creates files in the program directory
- Setup.exe (PID: 5988)
- Agent.exe (PID: 5600)
- Agent.exe (PID: 3896)
- wscript.exe (PID: 2772)
The sample compiled with english language support
- Setup.exe (PID: 5988)
- Agent.exe (PID: 3896)
Reads the time zone
- Agent.exe (PID: 3896)
Reads CPU info
- Agent.exe (PID: 3896)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:02:25 16:49:00 |
| ZipCRC: | 0xe8f4a72f |
| ZipCompressedSize: | 25698 |
| ZipUncompressedSize: | 179928 |
| ZipFileName: | install.exe |
Total processes
194
Monitored processes
61
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 660 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=1916 -parentBuildID 20240213221259 -prefsHandle 1852 -prefMapHandle 1832 -prefsLen 31031 -prefMapSize 244583 -appDir "C:\Program Files\Mozilla Firefox\browser" - {c29c902e-55f2-42f2-8acc-576326d77c8c} 1052 "\\.\pipe\gecko-crash-server-pipe.1052" 1c0e51ec110 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 776 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1040 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4300 -childID 2 -isForBrowser -prefsHandle 4292 -prefMapHandle 4288 -prefsLen 36588 -prefMapSize 244583 -jsInitHandle 1424 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {17d15fa7-fb81-4ecc-a68a-f7505160cebd} 1052 "\\.\pipe\gecko-crash-server-pipe.1052" 1c0eb958690 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1052 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1328 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | turnserver.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | "C:\Windows\System32\netsh.exe" advfirewall firewall add rule name="Agent DVR" dir=in action=allow program="C:\Program Files\Agent\Agent.exe" enable=yes | C:\Windows\System32\netsh.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
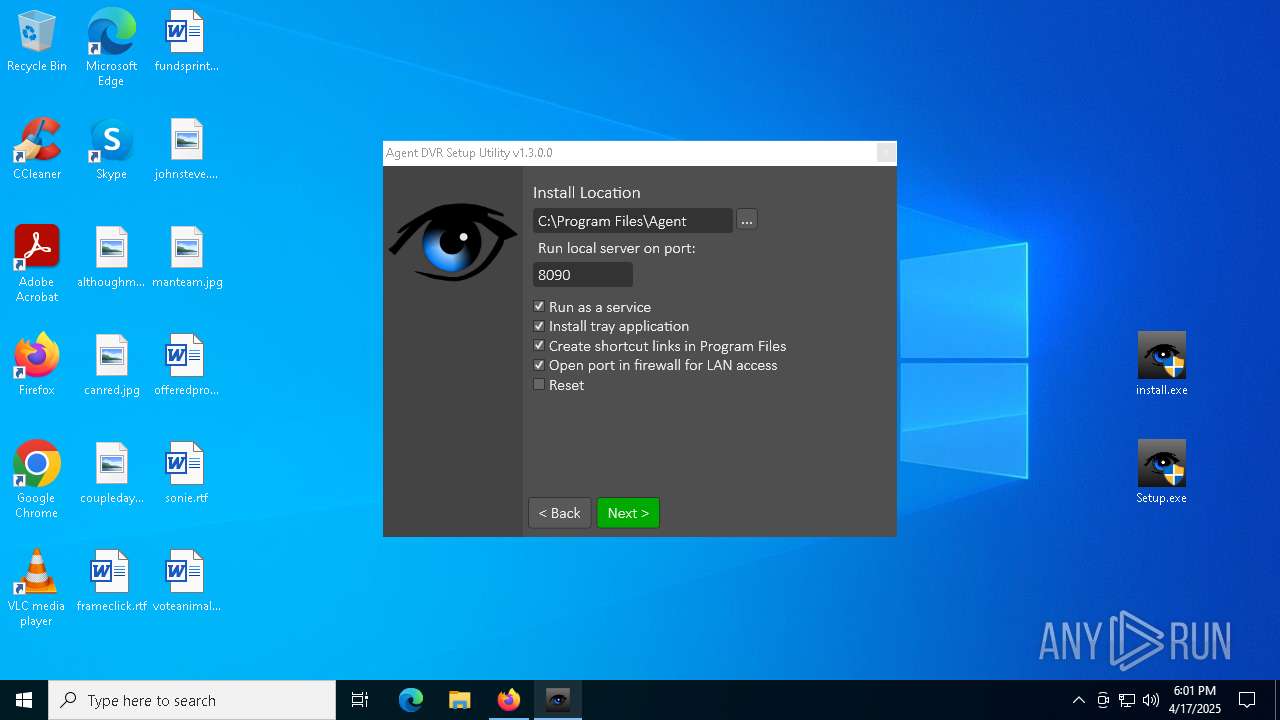
| 2268 | "C:\Program Files\Agent\AgentTray.exe" | C:\Program Files\Agent\AgentTray.exe | Setup.exe | ||||||||||||
User: admin Company: Developerinabox Integrity Level: HIGH Description: Agent DVR Controller Version: 1.3.1.0 Modules
| |||||||||||||||
| 2564 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2772 | "wscript.exe" "C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Agent DVR.lnk.vbs" | C:\Windows\System32\wscript.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 3024 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
45 839
Read events
45 728
Write events
105
Delete events
6
Modification events
| (PID) Process: | (7488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Agent_Setup_Windows.zip | |||
| (PID) Process: | (7488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (7488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
28
Suspicious files
322
Text files
113
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1052 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 7844 | Setup.exe | C:\Users\admin\AppData\Local\Temp\agent_setup_log.txt | text | |
MD5:5D312C49A3D028C81372027D21F6F7D9 | SHA256:D48F6B7AE83DFC23FDA2D5D99E40624DE2691FB58A13B277FF7DE0AA5AB4E50F | |||
| 7488 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7488.14161\Setup.exe | executable | |
MD5:7F36CB196CE497073B9D2CC7D1793244 | SHA256:0386F1FEBF11219DF5C384F713FBA077CB431286C17536AB118F870B1CF3E7EE | |||
| 4040 | install.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_93702E680A5530C052C8D2BA33A2225F | binary | |
MD5:049B26C855DC63FB4328D5C7C28844F3 | SHA256:540A039A8C96D2974899E5226689267A17150ACC610F9D546DEDF3EF417CA60C | |||
| 4040 | install.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_93702E680A5530C052C8D2BA33A2225F | binary | |
MD5:54D33E394143E3CBC07D9620A322B3BB | SHA256:F33BA345CC8BC122F9B7FAD4CCC2AB995E2AA1FBAC46A0899FD3BD0A1490BACE | |||
| 1052 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 7488 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7488.14161\install.exe | executable | |
MD5:A83179498C41F35FFD923ACD358E3ED1 | SHA256:5B818675030A3AC57C2B25FD8FF9CC2DBE24EB4F716B8496A9AFC8377300BD99 | |||
| 4040 | install.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\18E6B4A57A6BC7EC9B861CDF2D6D0D02_C3B142D2C5374581DC2FDFFDEDBDEDDB | binary | |
MD5:7C6D08F7DCAEDE3867C748892FD4CE17 | SHA256:A97CFEBE64D538A085707847E74924A34F46B7AEE55BD5412FF6A874512F8D6C | |||
| 1052 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 4040 | install.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\AEACCDA8653DD8D7B2EA32F21D15D44F_234749465267CDF080C05DF2EE0B531A | binary | |
MD5:DD07C586A94854E8B0DF320C79BAA06A | SHA256:6FC6801D3D3C7AE688796C962F19D4097D3776106225C6A5D5ABFB1360DDBFFF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
36
TCP/UDP connections
111
DNS requests
150
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4040 | install.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEEj8k7RgVZSNNqfJionWlBY%3D | unknown | — | — | whitelisted |
4040 | install.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSdE3gf41WAic8Uh9lF92%2BIJqh5qwQUMuuSmv81lkgvKEBCcCA2kVwXheYCEGIdbQxSAZ47kHkVIIkhHAo%3D | unknown | — | — | whitelisted |
4040 | install.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBQVD%2BnGf79Hpedv3mhy6uKMVZkPCQQUDyrLIIcouOxvSK4rVKYpqhekzQwCEQDad0xKTYspCIbxUvGaGkO8 | unknown | — | — | whitelisted |
7332 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7332 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1052 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
1052 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
1052 | firefox.exe | POST | 200 | 184.24.77.47:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
7084 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Agent.exe | Loading Open CV binary from default locations. Current directory: C:\Program Files\Agent; Additional load folder: C:\Program Files\Agent\dlls\x64
|
Agent.exe | Trying to load opencv_videoio_ffmpeg430_64.dll using default path.
|
Agent.exe | LoadLibraryEx("opencv_videoio_ffmpeg430_64.dll", 0, 4096) failed with error code 126: The specified module could not be found.
|
Agent.exe | LoadLibraryEx("opencv_videoio_ffmpeg430_64.dll", 0, 0) failed with error code 126: The specified module could not be found.
|
Agent.exe | Failed to load opencv_videoio_ffmpeg430_64.dll using default path
|
Agent.exe | !!! Failed to load opencv_videoio_ffmpeg430_64.dll.
|
Agent.exe | Found full path C:\Program Files\Agent\dlls\x64\cvextern.dll for cvextern.dll. Trying to load it.
|
Agent.exe | LoadLibraryEx("C:\Program Files\Agent\dlls\x64\cvextern.dll", 0, 4352) successfully loaded library.
|
Agent.exe | cvextern.dll loaded.
|