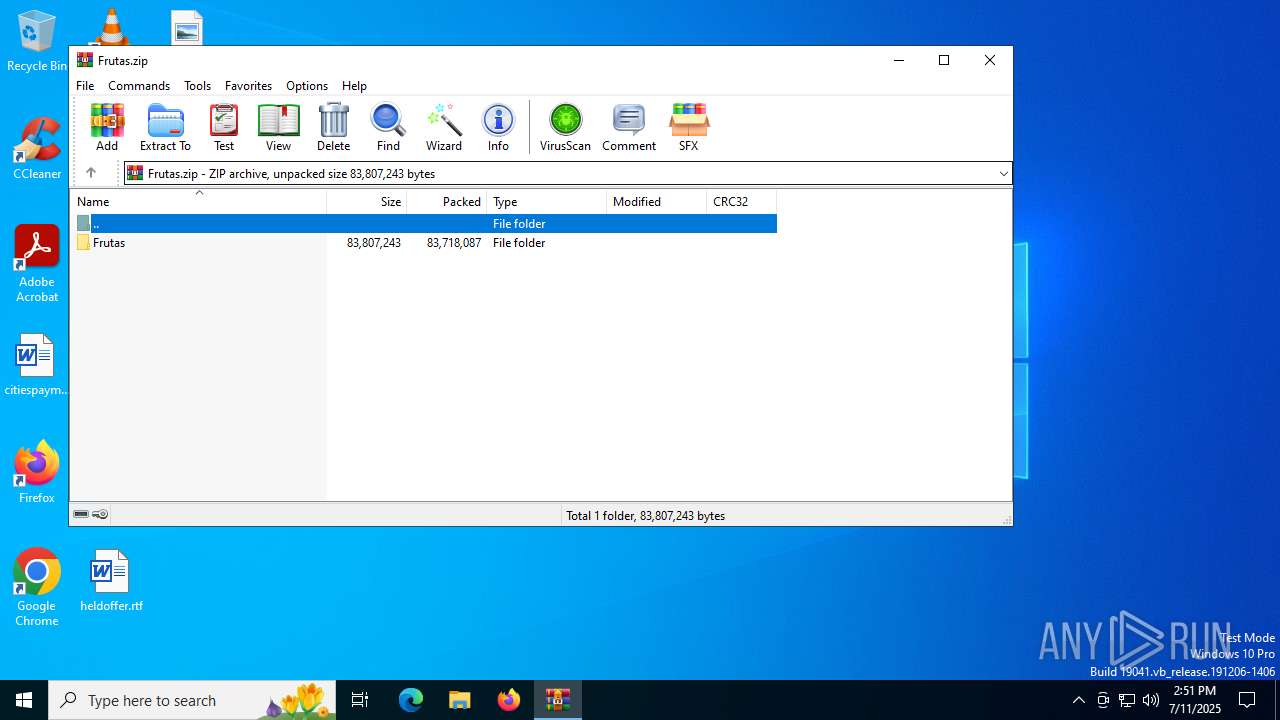
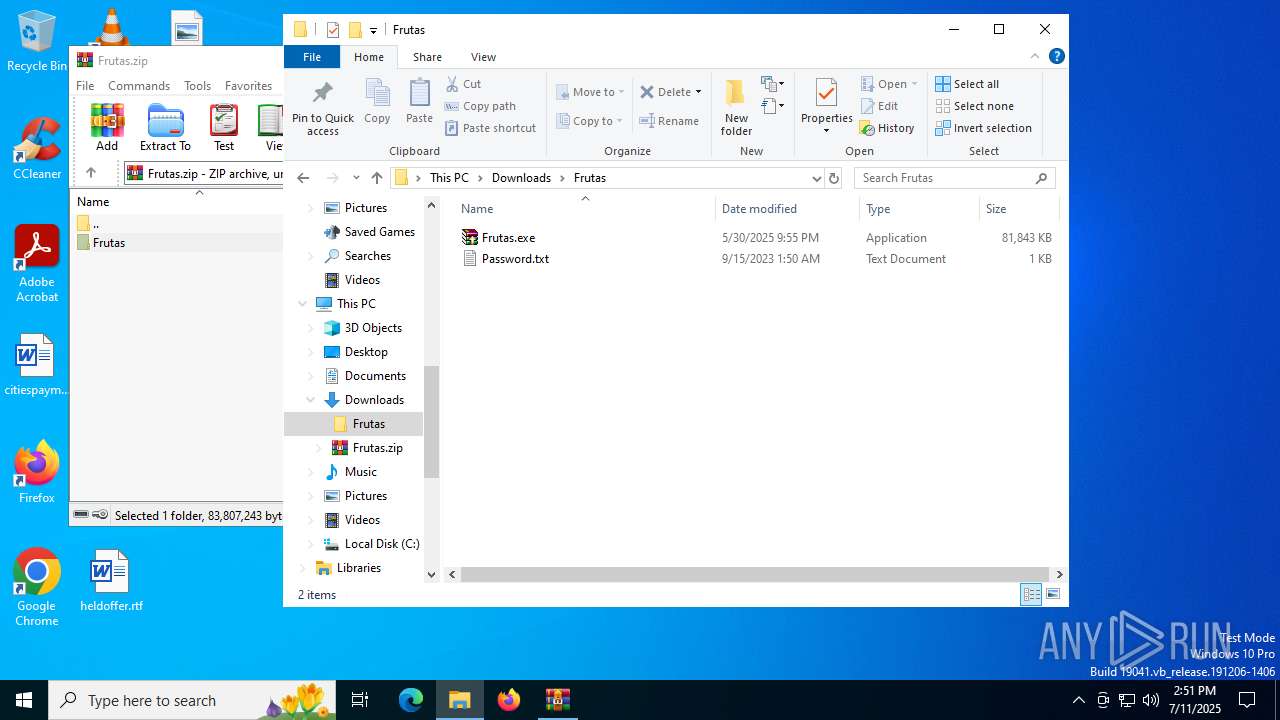
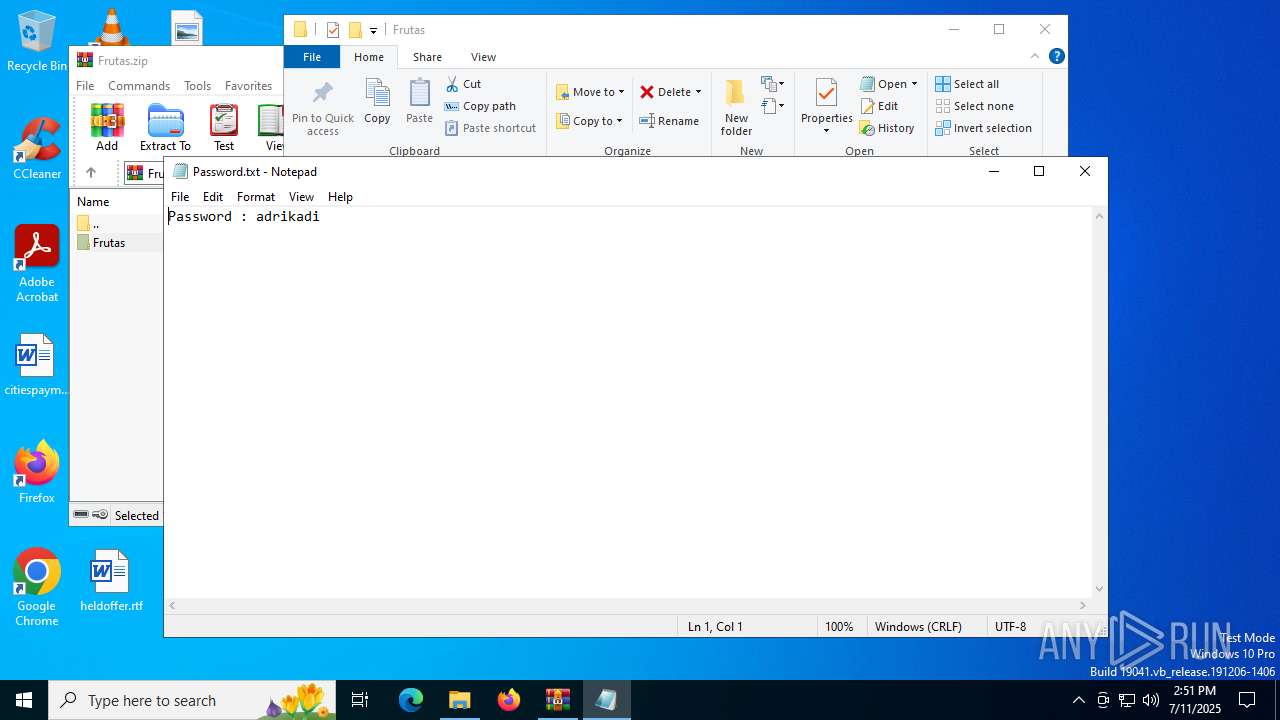
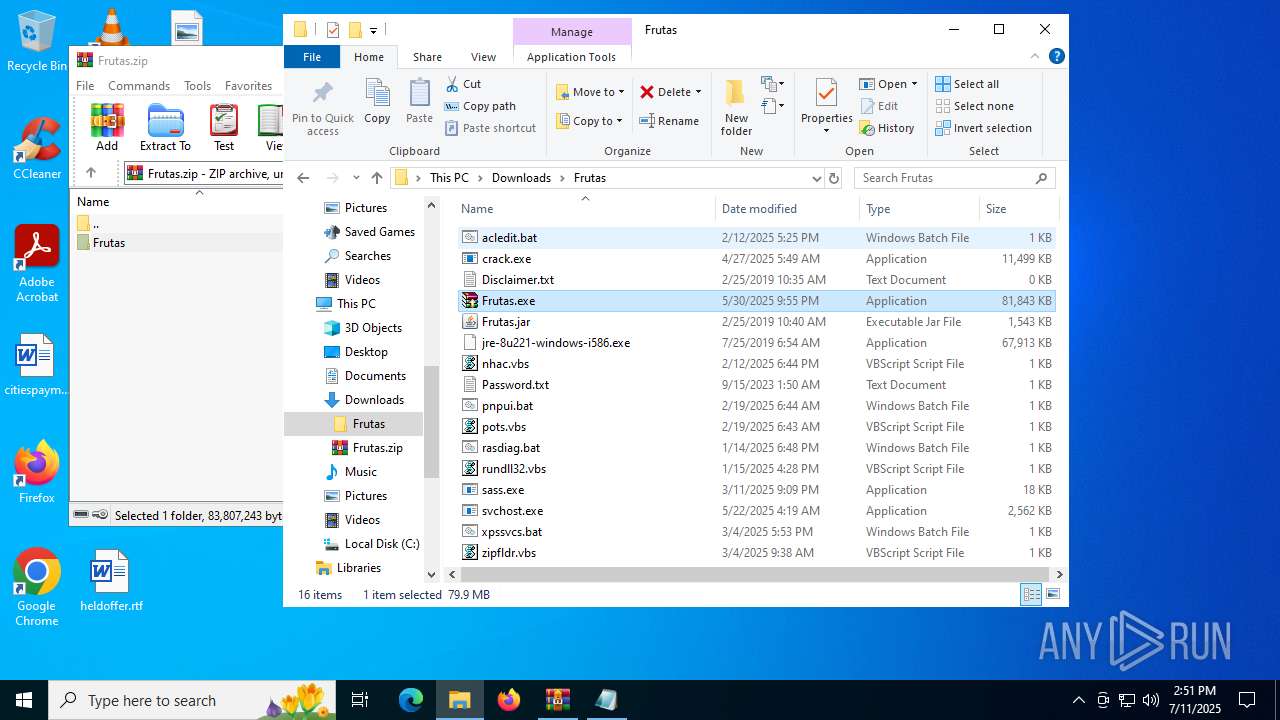
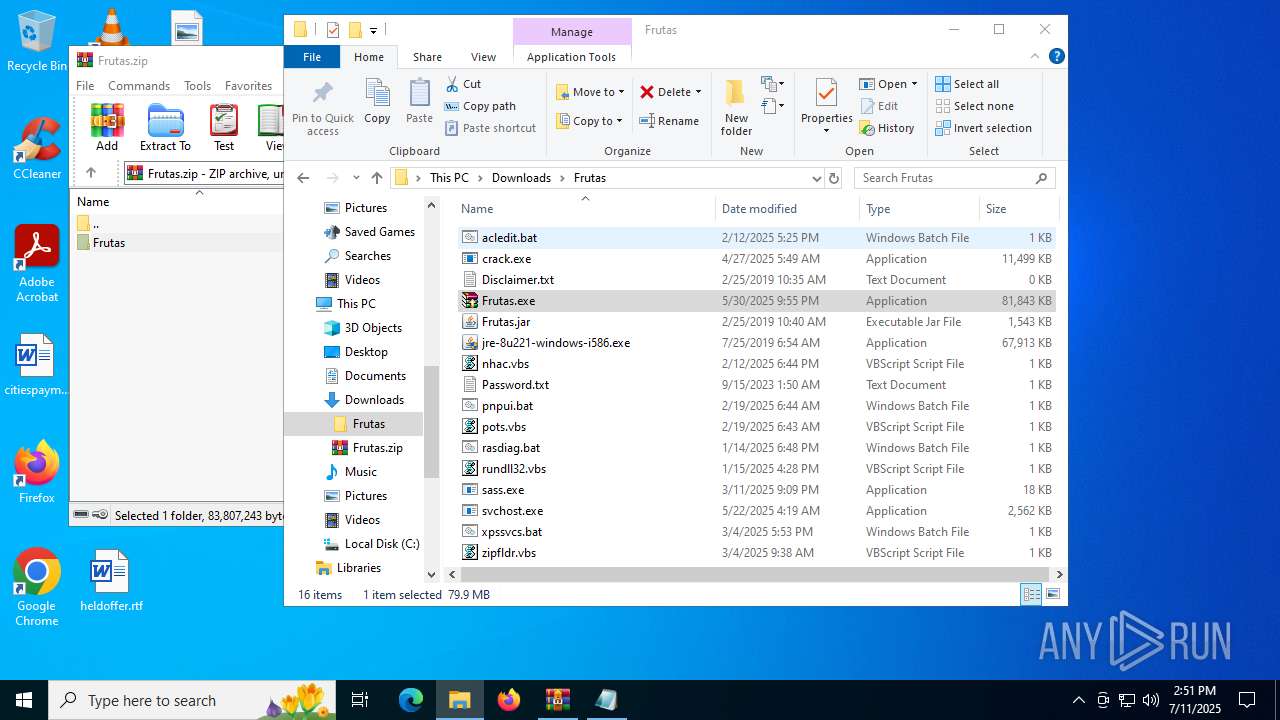
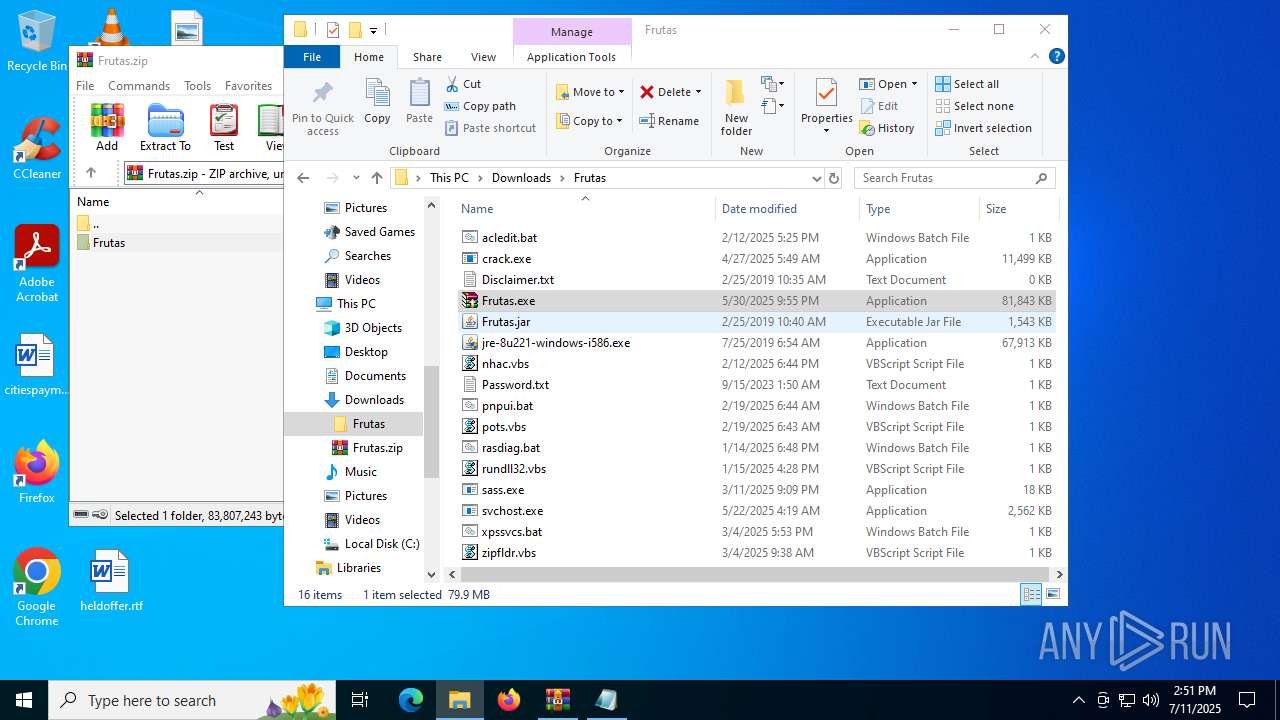
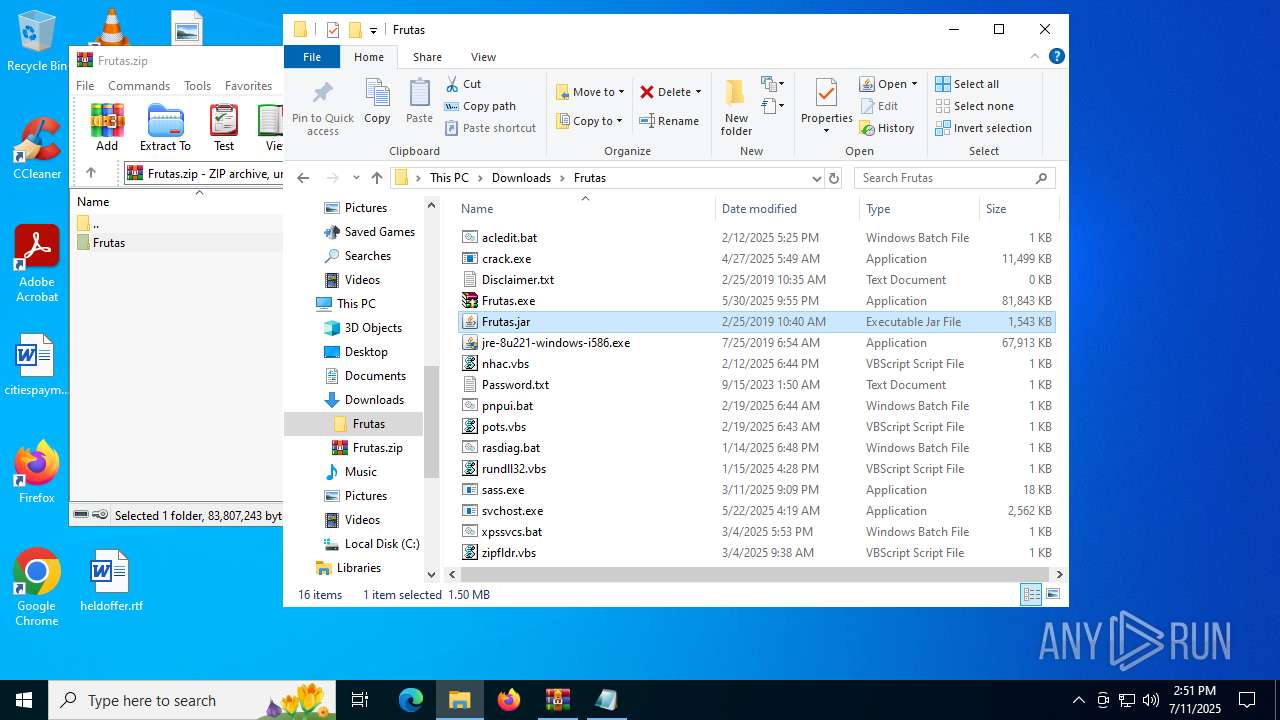
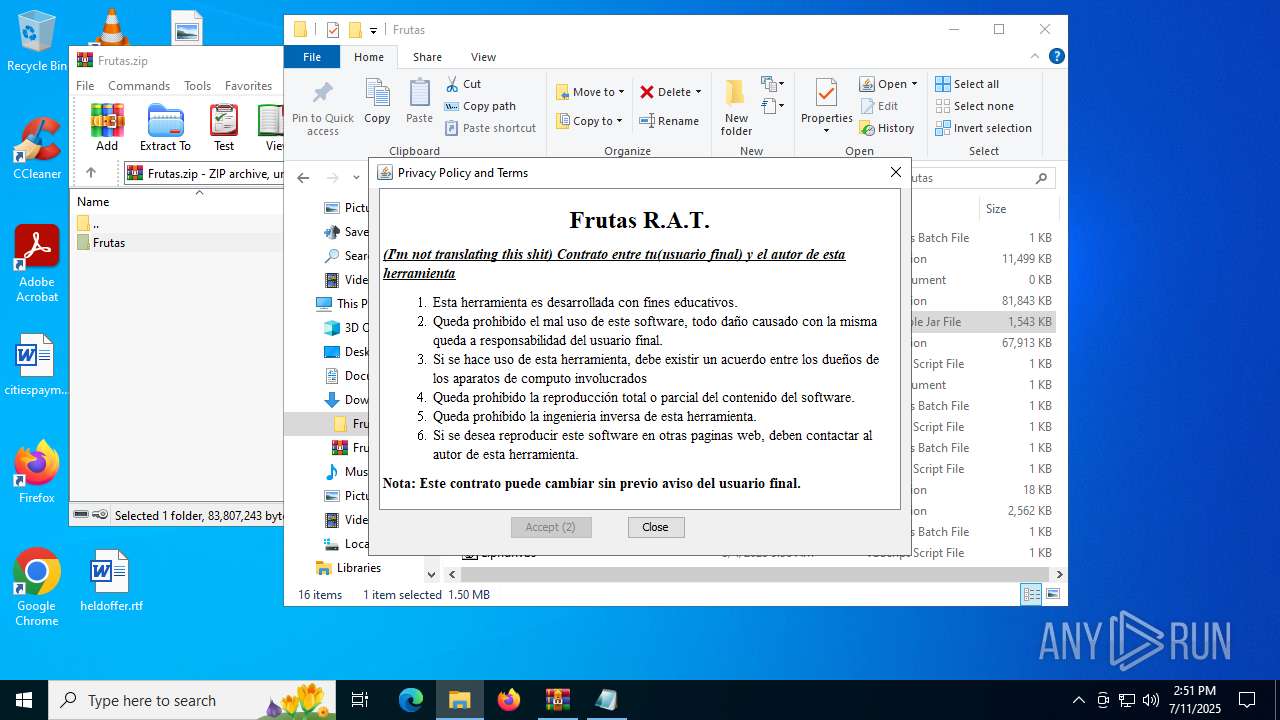
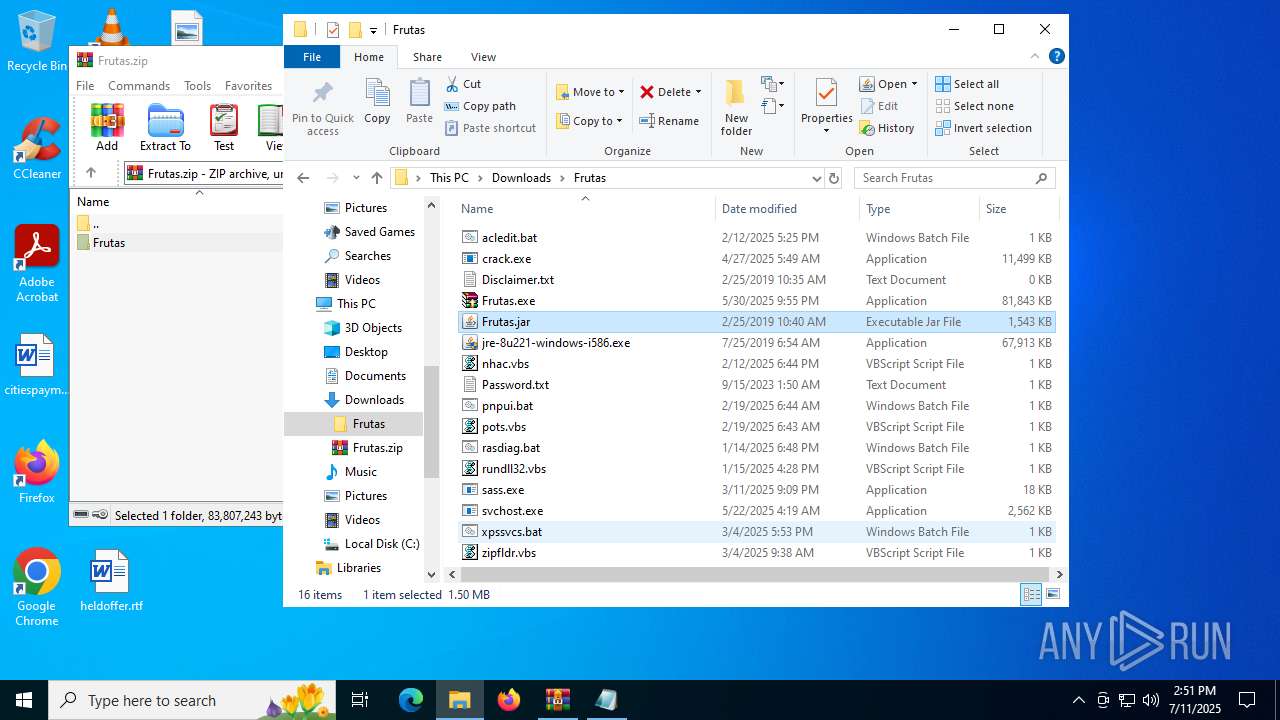
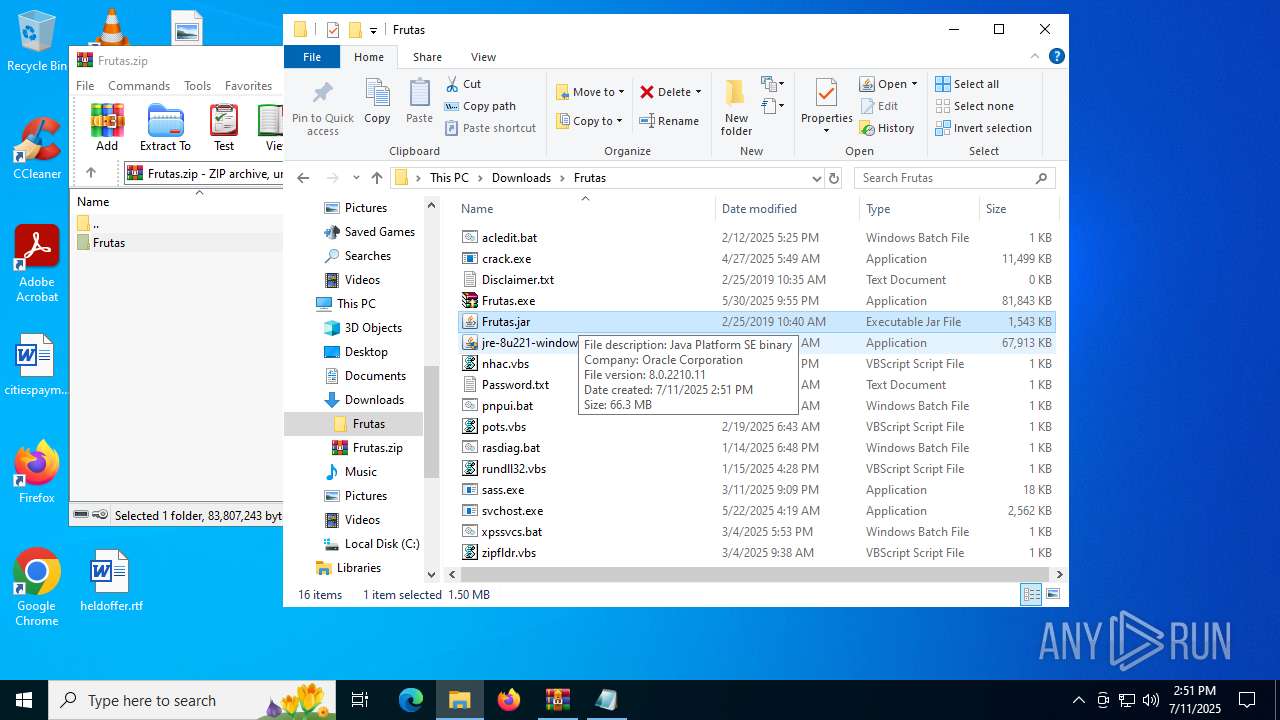
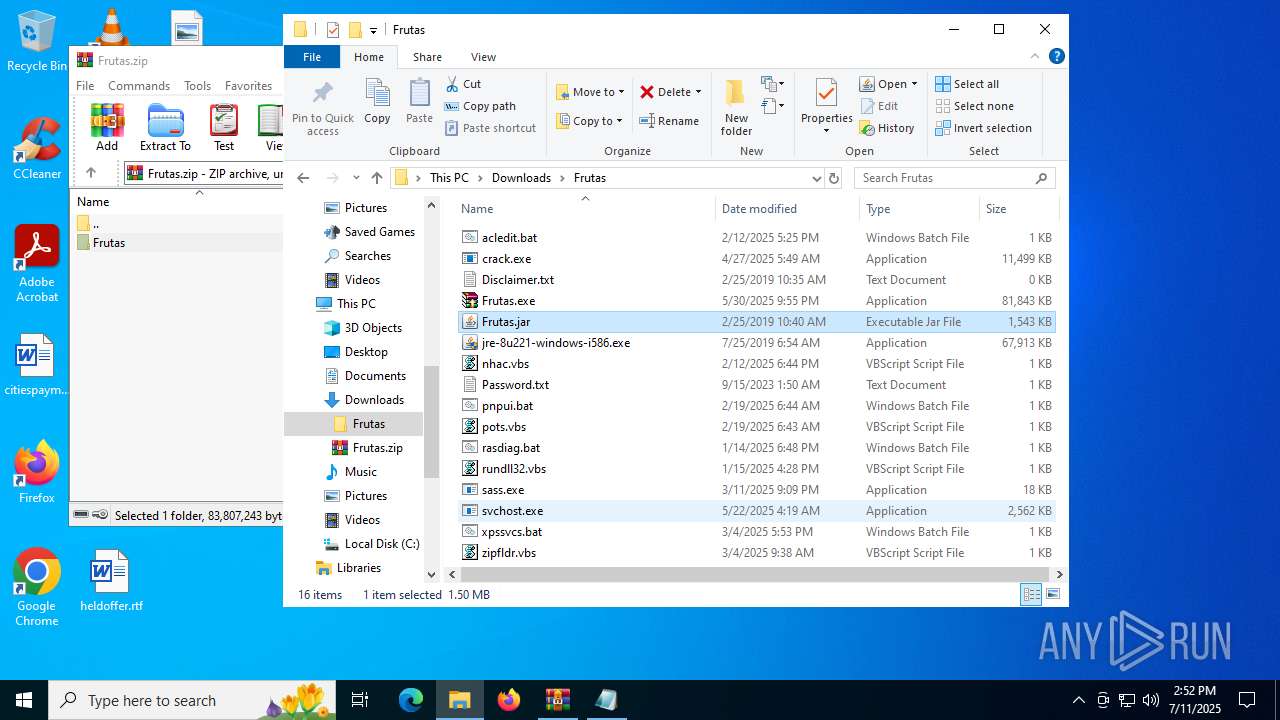
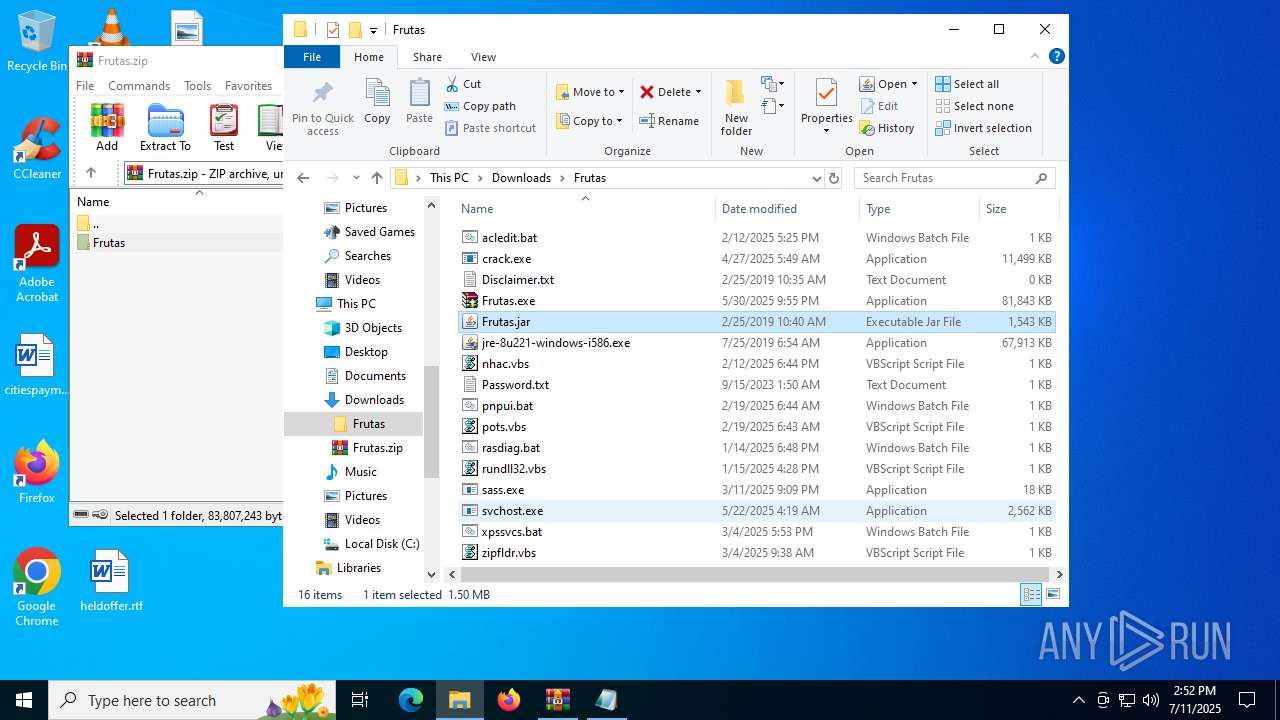
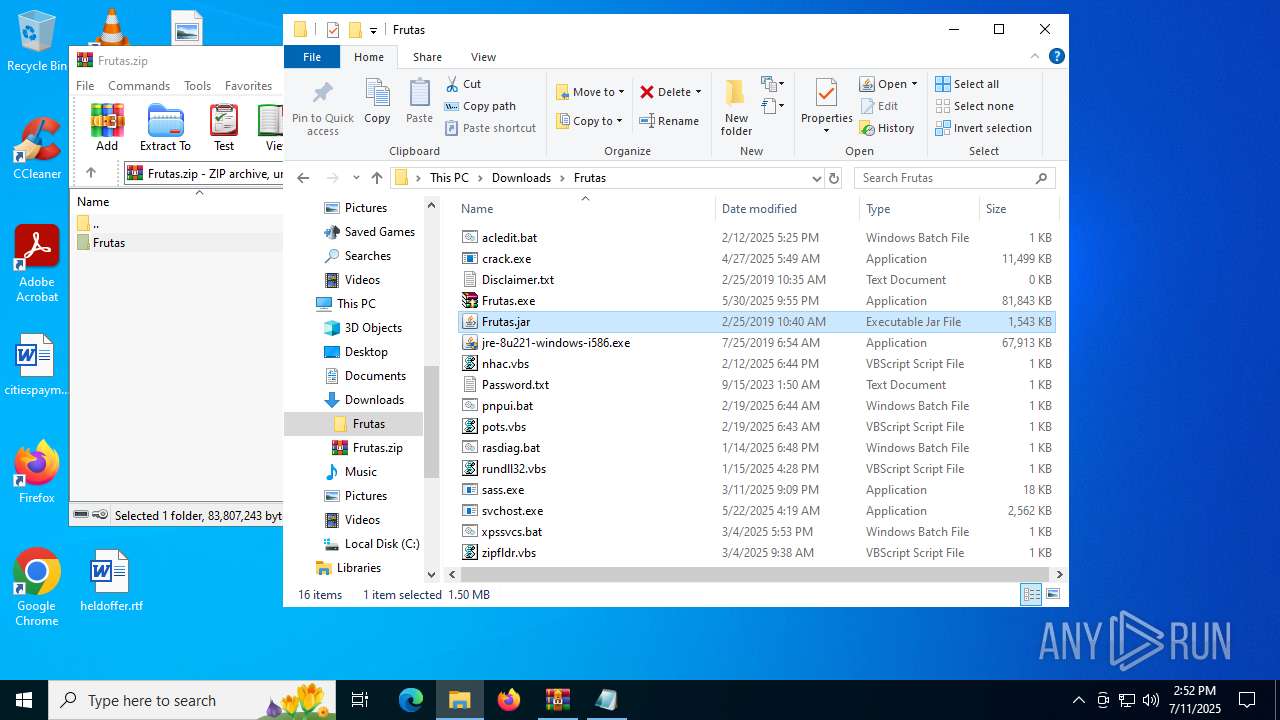
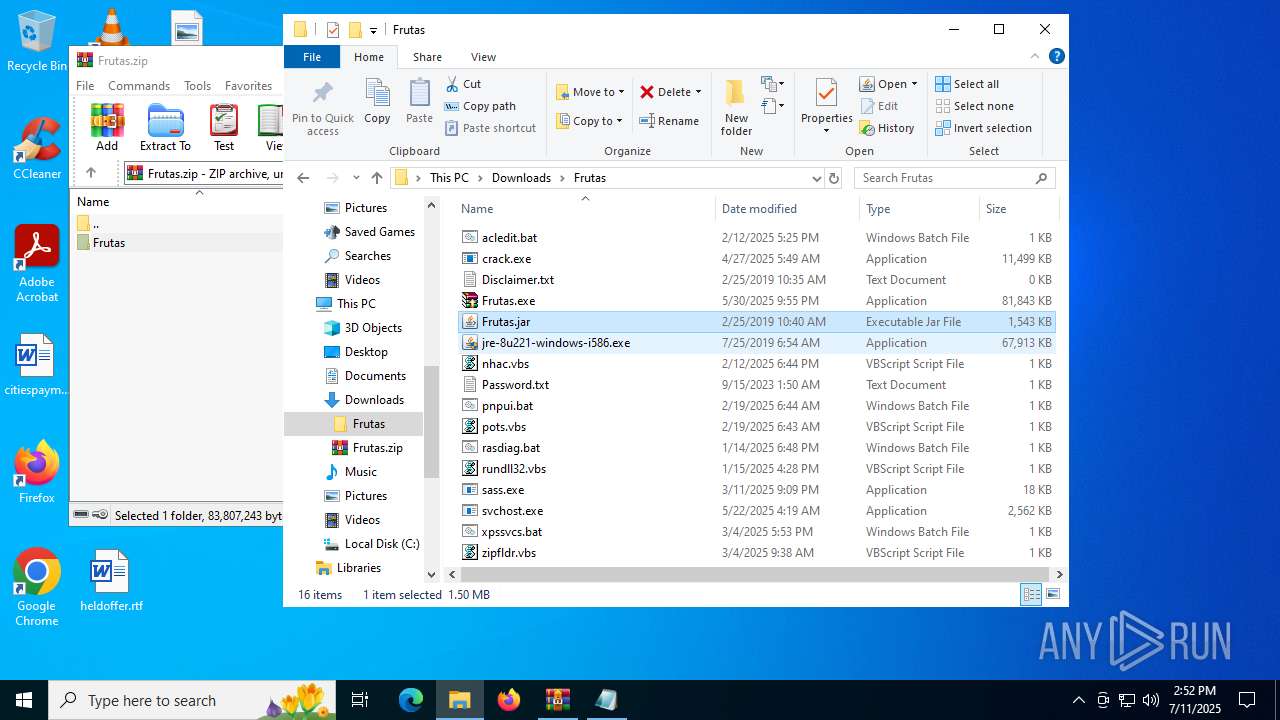
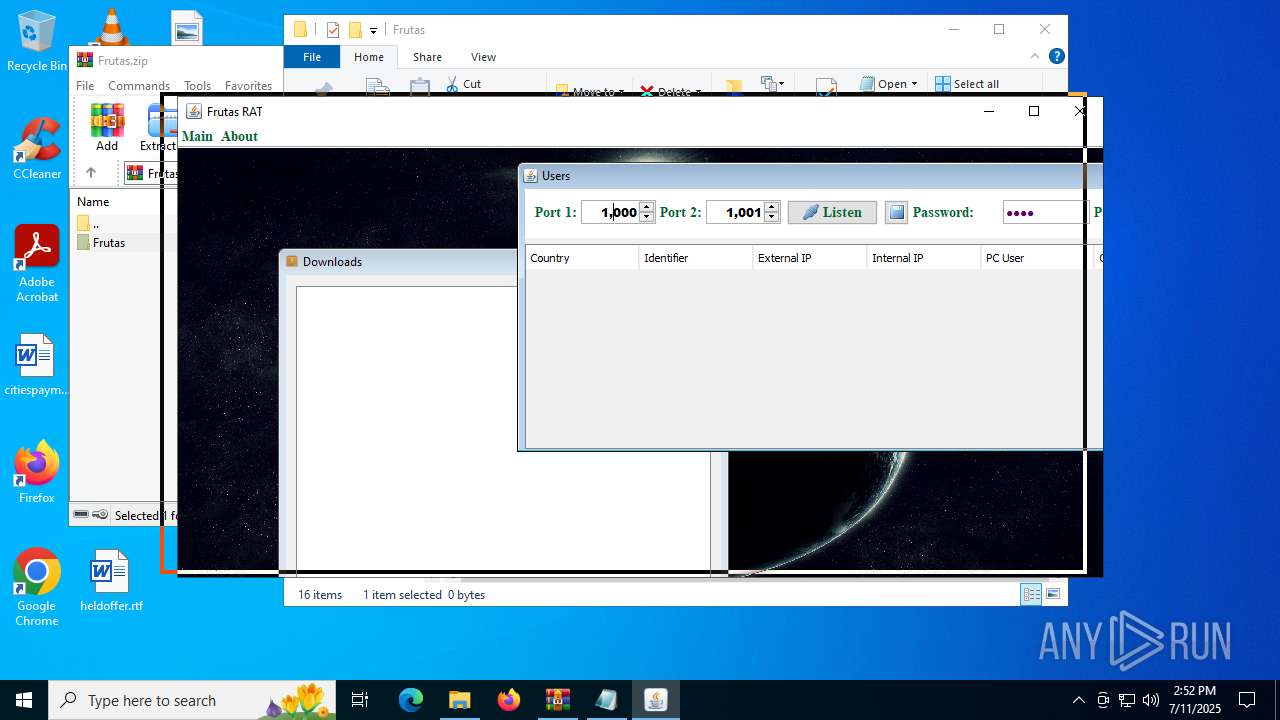
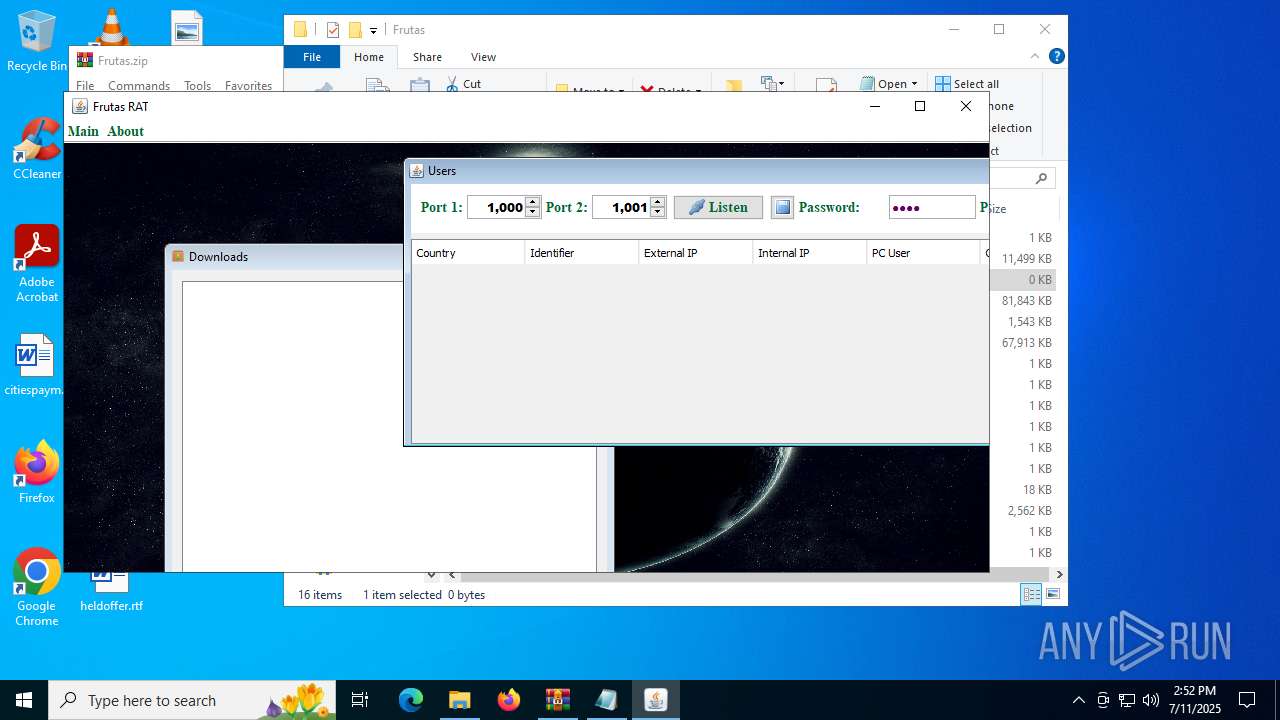
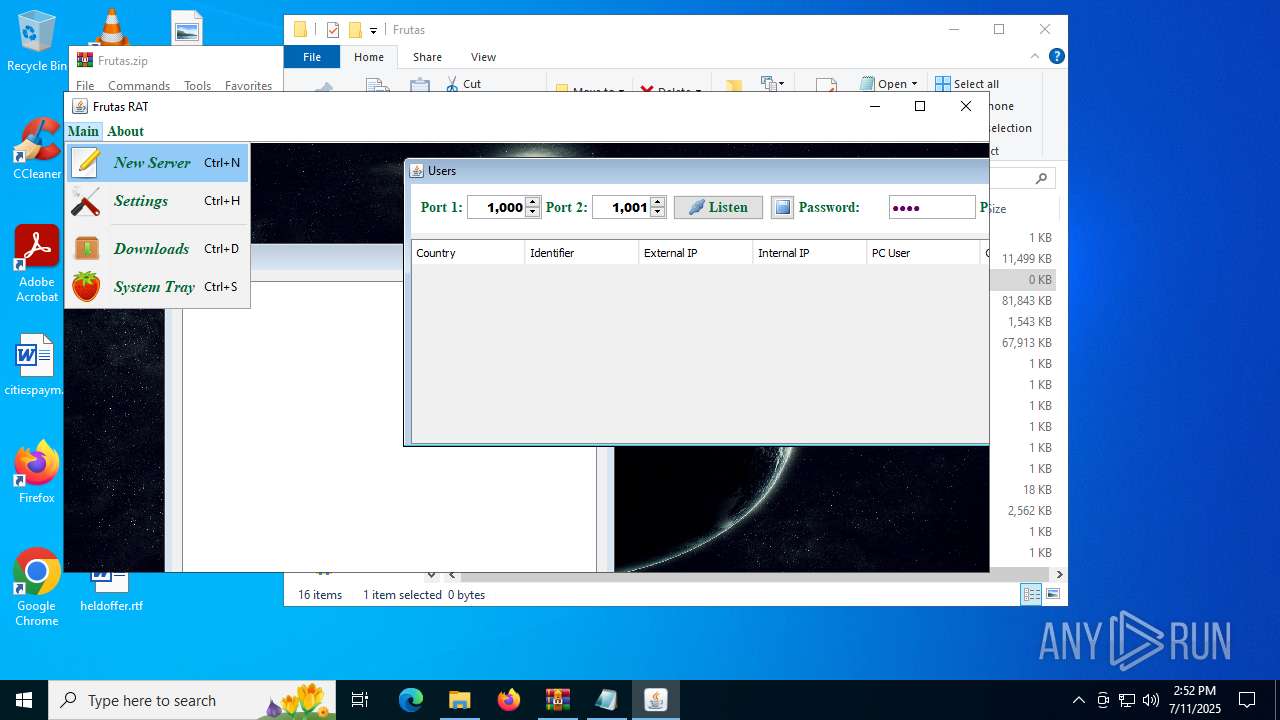
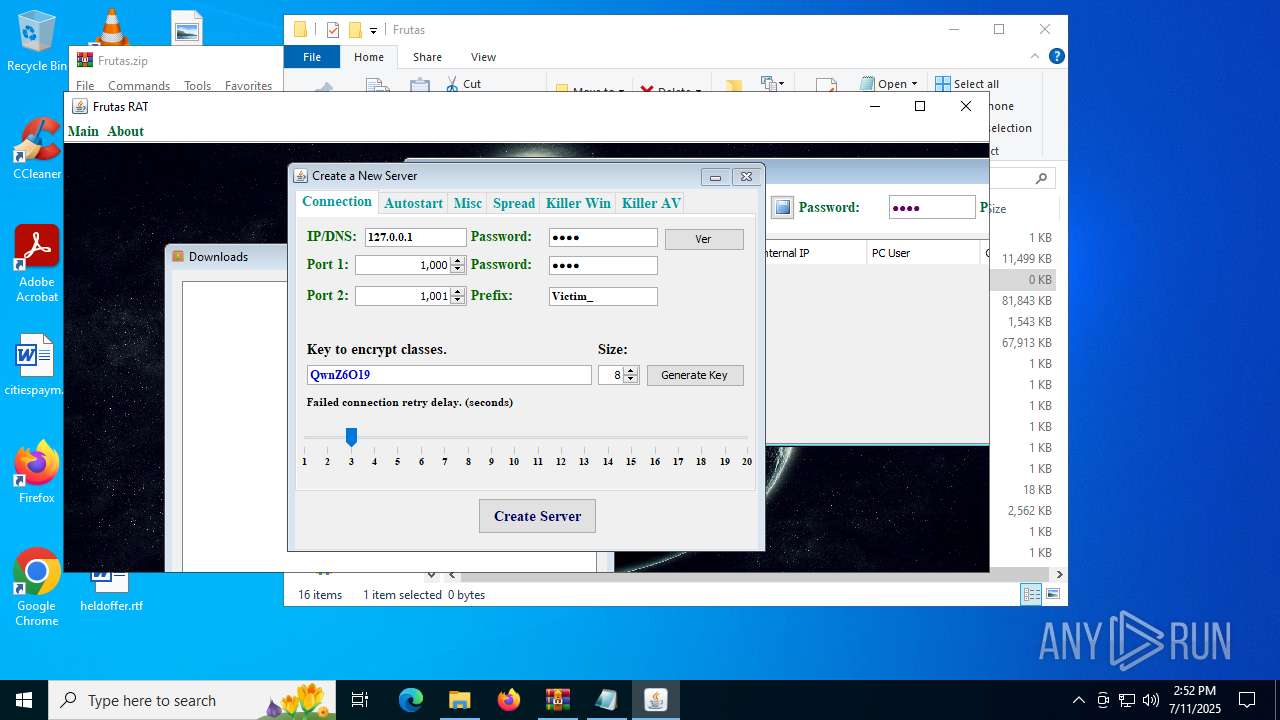
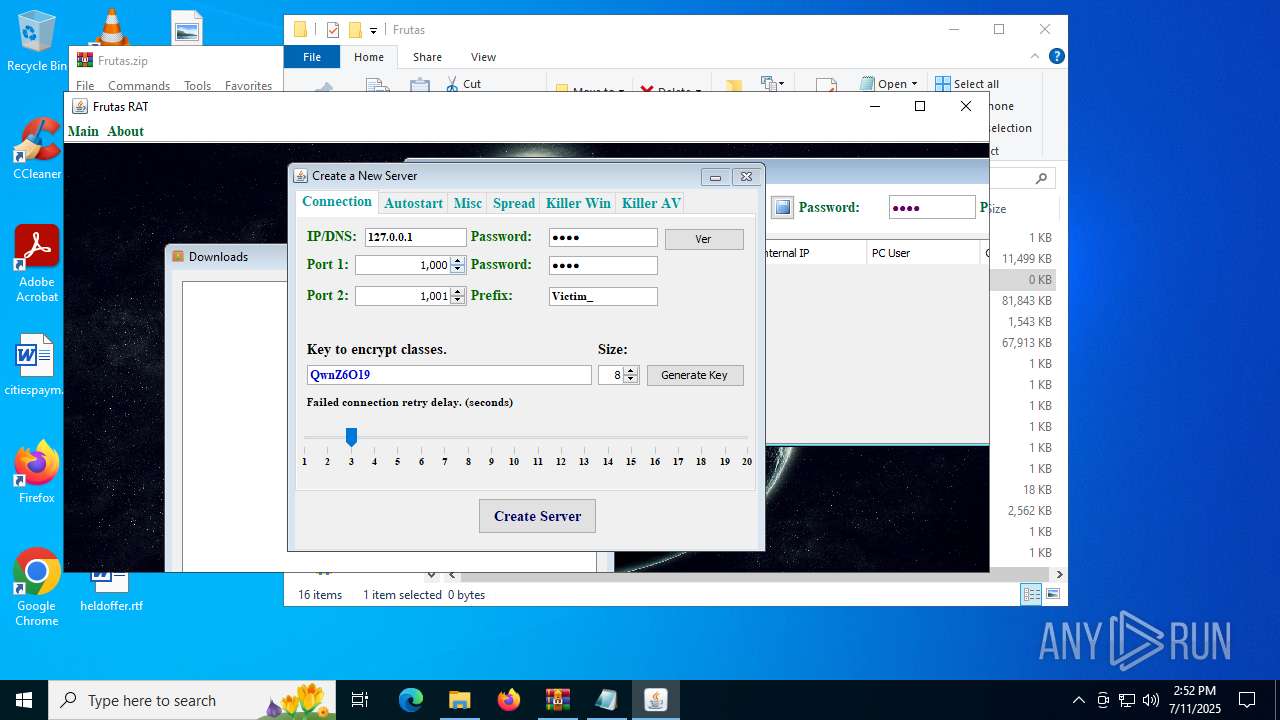
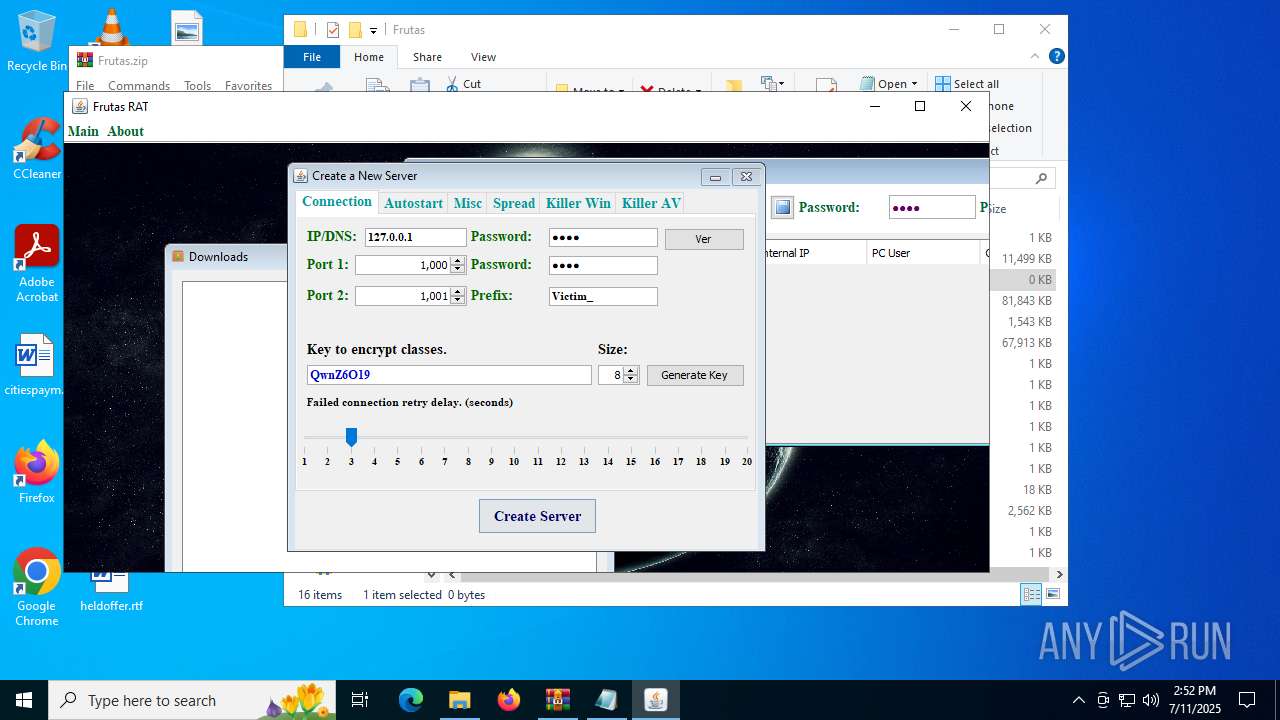
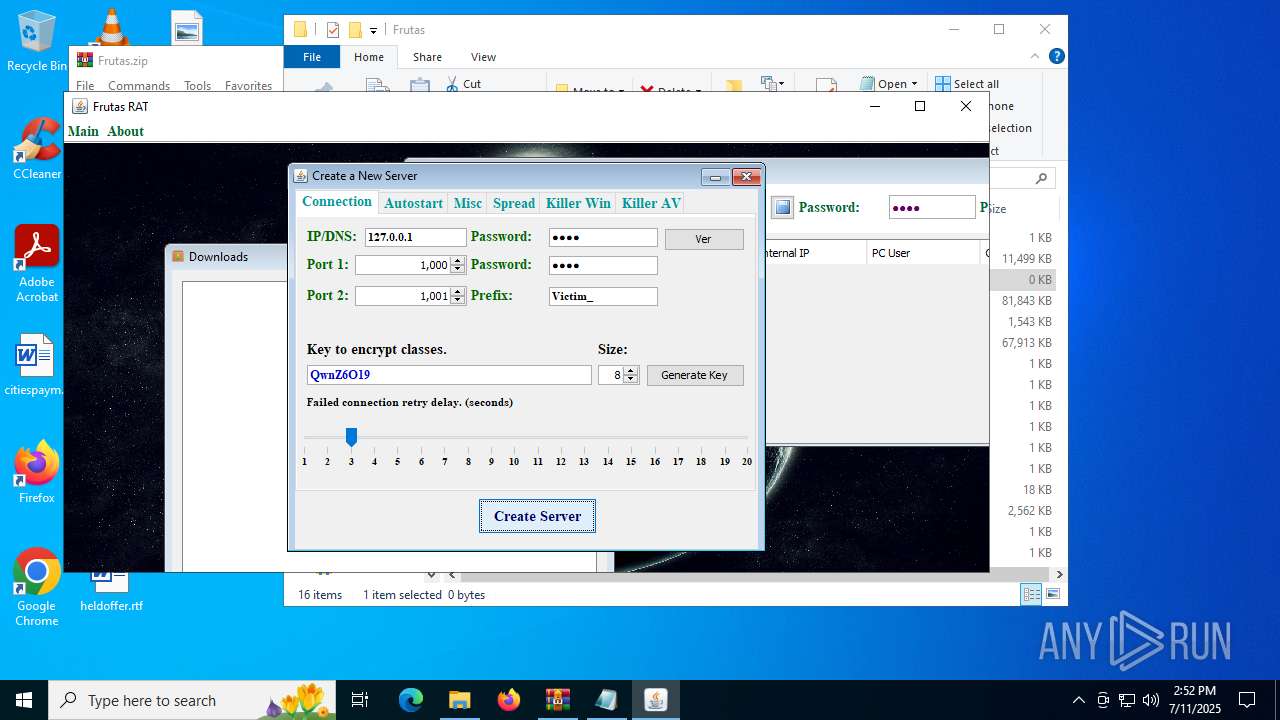
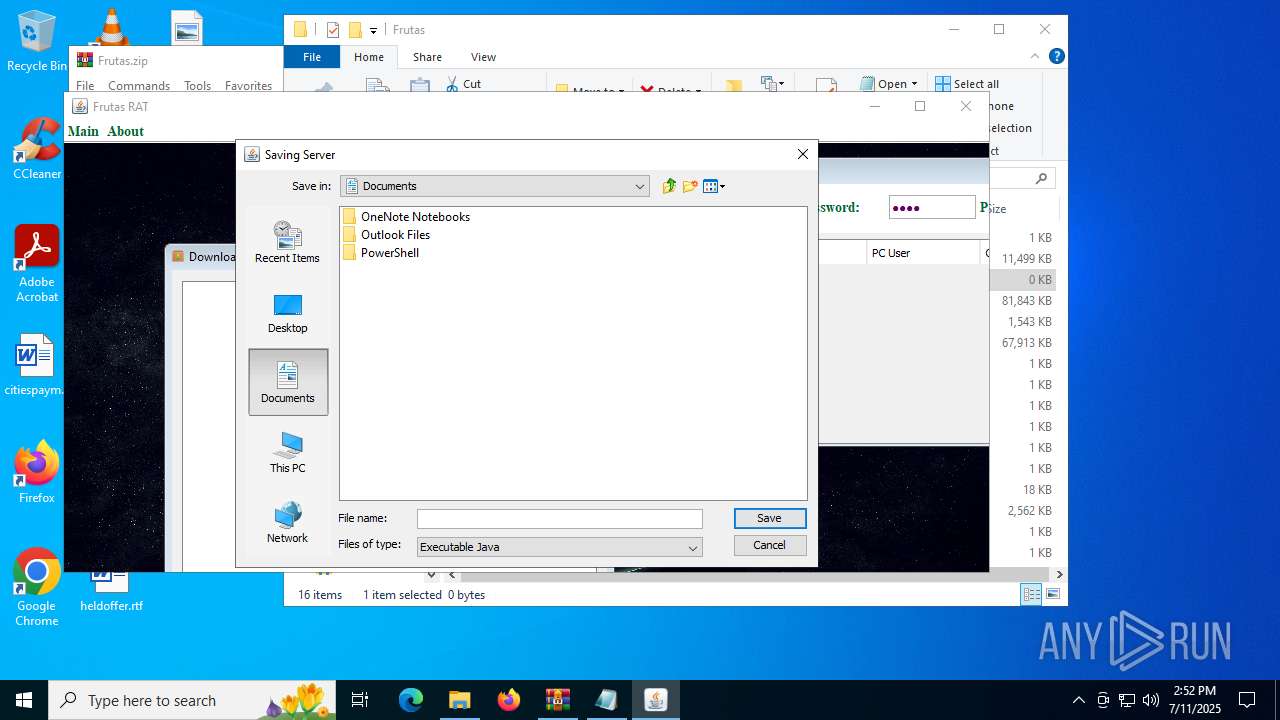
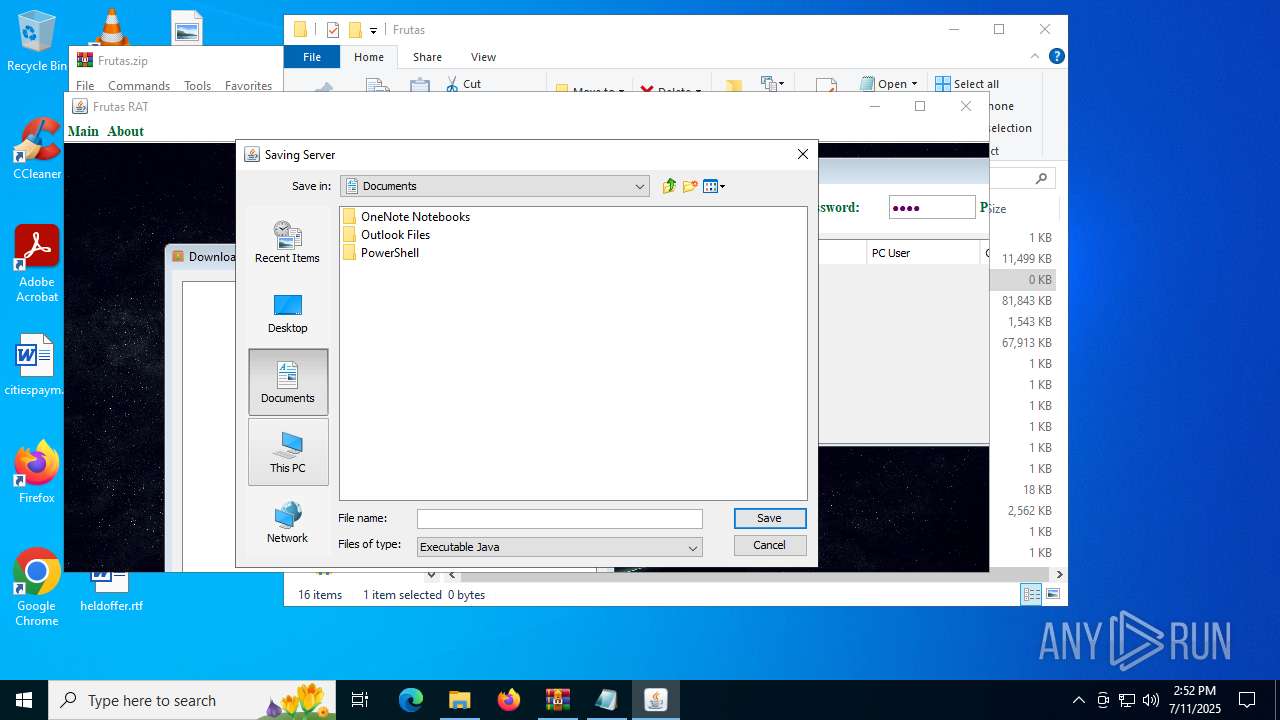
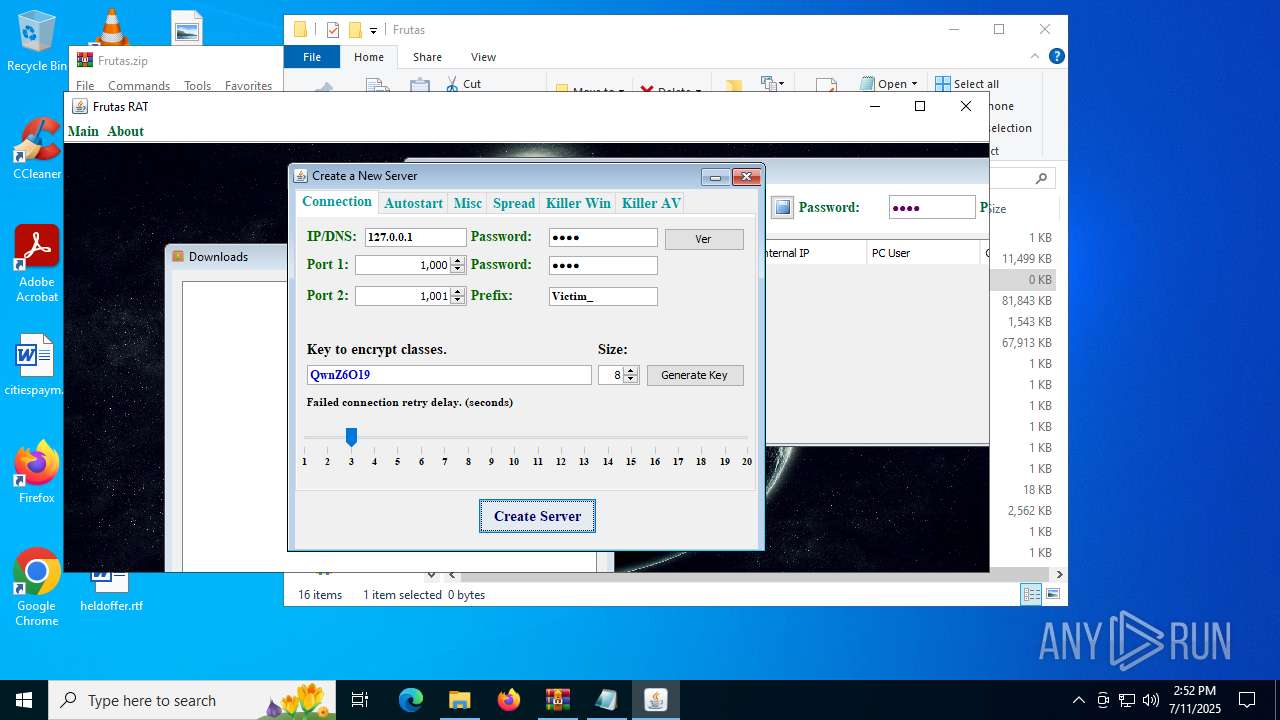
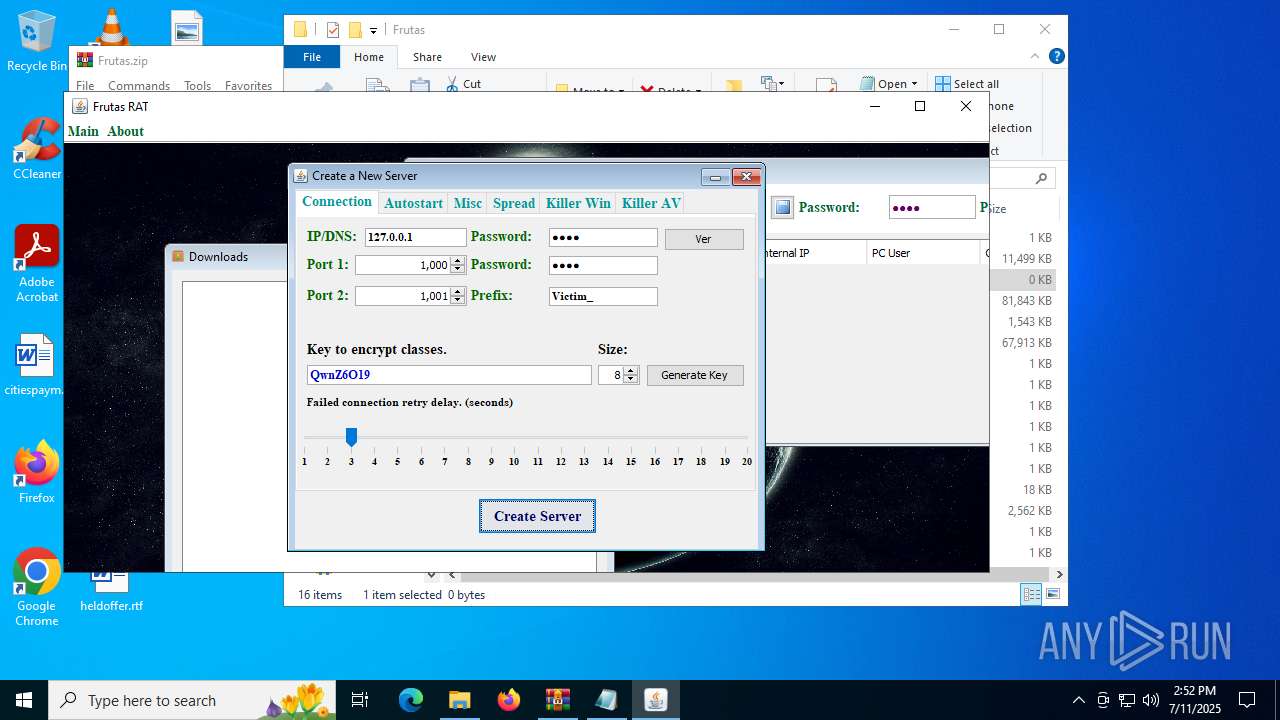
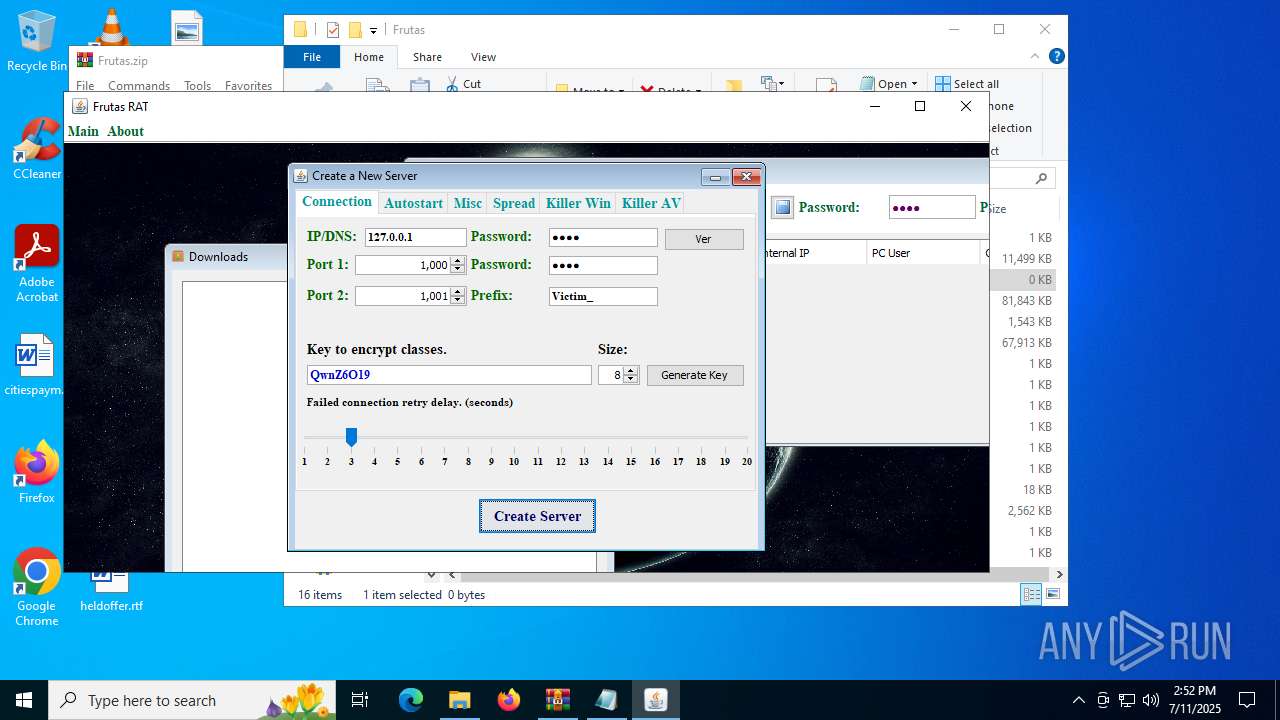
| URL: | http://depositfiles.com/files/04z41kwt8 |
| Full analysis: | https://app.any.run/tasks/a829f55f-981a-40c1-98fe-285c5c2dbf57 |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | July 11, 2025, 14:47:53 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 8A1FF2CBB7294956C3566B62EE6B8251 |
| SHA1: | 5EC74EDB04EBAD2F5F47B51275EB6CCADA59A06B |
| SHA256: | 85B106D1EEF0C30B7F2D13D07D831BD29D219E19A38D118C457C04D8576F81D3 |
| SSDEEP: | 3:N1KaAVDKY0KVG:CawKqG |
MALICIOUS
Create files in the Startup directory
- sass.exe (PID: 8664)
- clip.exe (PID: 2592)
Changes the autorun value in the registry
- svchost.exe (PID: 7636)
- update.exe (PID: 7980)
- svchost.exe (PID: 4832)
- pmx.exe (PID: 6948)
Vulnerable driver has been detected
- mine.exe (PID: 5620)
XMRig has been detected
- OmegaEngine.exe (PID: 7252)
PRYSMAX mutex has been found
- pmx.exe (PID: 6948)
Bypass User Account Control (Modify registry)
- pmx.exe (PID: 6948)
Actions looks like stealing of personal data
- svchost.exe (PID: 7636)
- svchost.exe (PID: 8580)
- svchost.exe (PID: 4832)
- vshost.exe (PID: 8724)
MINER has been detected (SURICATA)
- svchost.exe (PID: 2200)
- OmegaEngine.exe (PID: 7252)
Connects to the CnC server
- OmegaEngine.exe (PID: 7252)
Bypass User Account Control (ComputerDefaults)
- ComputerDefaults.exe (PID: 9180)
Steals credentials from Web Browsers
- svchost.exe (PID: 7636)
- svchost.exe (PID: 8580)
- svchost.exe (PID: 4832)
- vshost.exe (PID: 8724)
MILLENIUMRAT has been detected (YARA)
- svchost.exe (PID: 7636)
SUSPICIOUS
Reads security settings of Internet Explorer
- Frutas.exe (PID: 8968)
- update.exe (PID: 7980)
- mr.exe (PID: 984)
- dot.exe (PID: 8836)
- mine.exe (PID: 5620)
- javaw.exe (PID: 8212)
Reads Microsoft Outlook installation path
- Frutas.exe (PID: 8968)
Reads Internet Explorer settings
- Frutas.exe (PID: 8968)
The process creates files with name similar to system file names
- Frutas.exe (PID: 8968)
- svchost.exe (PID: 9204)
- powershell.exe (PID: 8448)
- mr.exe (PID: 8592)
- dot.exe (PID: 6940)
Process drops legitimate windows executable
- crack.exe (PID: 9004)
- rc.exe (PID: 9020)
Process drops python dynamic module
- crack.exe (PID: 9004)
- rc.exe (PID: 9020)
The process drops C-runtime libraries
- crack.exe (PID: 9004)
- rc.exe (PID: 9020)
The process executes VB scripts
- Frutas.exe (PID: 8968)
Executable content was dropped or overwritten
- svchost.exe (PID: 9204)
- crack.exe (PID: 9004)
- sass.exe (PID: 8664)
- Frutas.exe (PID: 8968)
- powershell.exe (PID: 8444)
- clip.exe (PID: 2592)
- powershell.exe (PID: 4828)
- update.exe (PID: 7980)
- rc.exe (PID: 9020)
- mine.exe (PID: 5620)
- mr.exe (PID: 8592)
- dot.exe (PID: 6940)
- powershell.exe (PID: 8448)
- pmx.exe (PID: 6948)
Starts itself from another location
- svchost.exe (PID: 9204)
- mr.exe (PID: 8592)
- dot.exe (PID: 6940)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 3976)
- wscript.exe (PID: 6840)
- wscript.exe (PID: 1588)
- wscript.exe (PID: 8216)
- mr.exe (PID: 984)
- dot.exe (PID: 8836)
- pmx.exe (PID: 6948)
- vshost.exe (PID: 8724)
Executing commands from a ".bat" file
- wscript.exe (PID: 3976)
- wscript.exe (PID: 6840)
- wscript.exe (PID: 1588)
- wscript.exe (PID: 8216)
Runs shell command (SCRIPT)
- wscript.exe (PID: 6840)
- wscript.exe (PID: 3976)
- wscript.exe (PID: 8216)
- wscript.exe (PID: 1588)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5288)
- cmd.exe (PID: 4788)
- cmd.exe (PID: 5284)
- cmd.exe (PID: 7276)
Downloads file from URI via Powershell
- powershell.exe (PID: 4828)
- powershell.exe (PID: 8444)
- powershell.exe (PID: 8448)
- powershell.exe (PID: 9092)
Checks for external IP
- svchost.exe (PID: 2200)
- svchost.exe (PID: 7636)
- svchost.exe (PID: 8580)
- svchost.exe (PID: 4832)
- vshost.exe (PID: 8724)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- svchost.exe (PID: 7636)
- svchost.exe (PID: 8580)
- vshost.exe (PID: 8724)
- svchost.exe (PID: 4832)
The executable file from the user directory is run by the CMD process
- clip.exe (PID: 2592)
- update.exe (PID: 7980)
- mr.exe (PID: 8592)
- dot.exe (PID: 6940)
- svchost.exe (PID: 4832)
Process requests binary or script from the Internet
- update.exe (PID: 7980)
Drops a system driver (possible attempt to evade defenses)
- mine.exe (PID: 5620)
Reads the date of Windows installation
- mine.exe (PID: 5620)
Changes default file association
- pmx.exe (PID: 6948)
Found regular expressions for crypto-addresses (YARA)
- sass.exe (PID: 8664)
Crypto Currency Mining Activity Detected
- svchost.exe (PID: 2200)
Potential Corporate Privacy Violation
- OmegaEngine.exe (PID: 7252)
Reads browser cookies
- svchost.exe (PID: 7636)
- svchost.exe (PID: 8580)
- svchost.exe (PID: 4832)
- vshost.exe (PID: 8724)
There is functionality for taking screenshot (YARA)
- crack.exe (PID: 9004)
Possible usage of Discord/Telegram API has been detected (YARA)
- svchost.exe (PID: 7636)
Multiple wallet extension IDs have been found
- svchost.exe (PID: 7636)
Uses ATTRIB.EXE to modify file attributes
- pmx.exe (PID: 6948)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 7668)
INFO
Reads the computer name
- identity_helper.exe (PID: 7892)
- identity_helper.exe (PID: 7828)
- Frutas.exe (PID: 8968)
- crack.exe (PID: 9004)
- sass.exe (PID: 8664)
- svchost.exe (PID: 7636)
- clip.exe (PID: 2592)
- update.exe (PID: 7980)
- clip.exe (PID: 6524)
- mine.exe (PID: 5620)
- dot.exe (PID: 8836)
- mr.exe (PID: 984)
- pmx.exe (PID: 6948)
- rc.exe (PID: 9020)
- javaw.exe (PID: 8212)
- OmegaEngine.exe (PID: 7252)
- vshost.exe (PID: 8724)
- svchost.exe (PID: 8580)
- svchost.exe (PID: 4832)
Application launched itself
- msedge.exe (PID: 5168)
- firefox.exe (PID: 7592)
- msedge.exe (PID: 8112)
- firefox.exe (PID: 7596)
- firefox.exe (PID: 8616)
- firefox.exe (PID: 8636)
- chrome.exe (PID: 7216)
- chrome.exe (PID: 6648)
Reads Environment values
- identity_helper.exe (PID: 7892)
- identity_helper.exe (PID: 7828)
Checks supported languages
- identity_helper.exe (PID: 7892)
- identity_helper.exe (PID: 7828)
- Frutas.exe (PID: 8968)
- sass.exe (PID: 8664)
- crack.exe (PID: 9004)
- svchost.exe (PID: 9204)
- svchost.exe (PID: 7636)
- clip.exe (PID: 2592)
- update.exe (PID: 7980)
- clip.exe (PID: 6524)
- javaw.exe (PID: 8212)
- mine.exe (PID: 5620)
- pmx.exe (PID: 6948)
- mr.exe (PID: 984)
- dot.exe (PID: 8836)
- rc.exe (PID: 9020)
- OmegaEngine.exe (PID: 7252)
- mr.exe (PID: 8592)
- dot.exe (PID: 6940)
- vshost.exe (PID: 8724)
- svchost.exe (PID: 8580)
- svchost.exe (PID: 4832)
Manual execution by a user
- firefox.exe (PID: 8636)
- firefox.exe (PID: 7596)
- WinRAR.exe (PID: 1868)
- notepad.exe (PID: 4048)
- Frutas.exe (PID: 8968)
- notepad.exe (PID: 1296)
Reads the software policy settings
- slui.exe (PID: 2952)
- update.exe (PID: 7980)
Reads Microsoft Office registry keys
- firefox.exe (PID: 8616)
- firefox.exe (PID: 7592)
- OpenWith.exe (PID: 4692)
Checks proxy server information
- slui.exe (PID: 2952)
- Frutas.exe (PID: 8968)
- powershell.exe (PID: 8444)
- powershell.exe (PID: 9092)
- powershell.exe (PID: 8448)
- powershell.exe (PID: 4828)
- update.exe (PID: 7980)
Reads security settings of Internet Explorer
- notepad.exe (PID: 4048)
- OpenWith.exe (PID: 4692)
- notepad.exe (PID: 1296)
- ComputerDefaults.exe (PID: 9180)
Process checks computer location settings
- Frutas.exe (PID: 8968)
- update.exe (PID: 7980)
- dot.exe (PID: 8836)
- mr.exe (PID: 984)
- mine.exe (PID: 5620)
Create files in a temporary directory
- crack.exe (PID: 9004)
- javaw.exe (PID: 8212)
- rc.exe (PID: 9020)
- dot.exe (PID: 6940)
The sample compiled with english language support
- crack.exe (PID: 9004)
- rc.exe (PID: 9020)
Creates files or folders in the user directory
- sass.exe (PID: 8664)
- svchost.exe (PID: 9204)
- clip.exe (PID: 2592)
- update.exe (PID: 7980)
- mine.exe (PID: 5620)
- mr.exe (PID: 8592)
- svchost.exe (PID: 7636)
- svchost.exe (PID: 8580)
- pmx.exe (PID: 6948)
- svchost.exe (PID: 4832)
- vshost.exe (PID: 8724)
Reads the machine GUID from the registry
- sass.exe (PID: 8664)
- clip.exe (PID: 2592)
- update.exe (PID: 7980)
Launching a file from the Startup directory
- sass.exe (PID: 8664)
- clip.exe (PID: 2592)
Attempting to use instant messaging service
- svchost.exe (PID: 2200)
- svchost.exe (PID: 7636)
- svchost.exe (PID: 8580)
- svchost.exe (PID: 4832)
Launching a file from a Registry key
- svchost.exe (PID: 7636)
- update.exe (PID: 7980)
- svchost.exe (PID: 4832)
- pmx.exe (PID: 6948)
Disables trace logs
- powershell.exe (PID: 8448)
- powershell.exe (PID: 4828)
- powershell.exe (PID: 9092)
- powershell.exe (PID: 8444)
Application based on Java
- javaw.exe (PID: 8212)
The sample compiled with japanese language support
- mine.exe (PID: 5620)
Creates files in the program directory
- javaw.exe (PID: 8212)
PyInstaller has been detected (YARA)
- crack.exe (PID: 9004)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(7636) svchost.exe
Telegram-Tokens (1)8022717075:AAFrvQGiTPbyXonzshWKfY-2hEJ-yjqbEBU
Telegram-Info-Links
8022717075:AAFrvQGiTPbyXonzshWKfY-2hEJ-yjqbEBU
Get info about bothttps://api.telegram.org/bot8022717075:AAFrvQGiTPbyXonzshWKfY-2hEJ-yjqbEBU/getMe
Get incoming updateshttps://api.telegram.org/bot8022717075:AAFrvQGiTPbyXonzshWKfY-2hEJ-yjqbEBU/getUpdates
Get webhookhttps://api.telegram.org/bot8022717075:AAFrvQGiTPbyXonzshWKfY-2hEJ-yjqbEBU/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot8022717075:AAFrvQGiTPbyXonzshWKfY-2hEJ-yjqbEBU/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot8022717075:AAFrvQGiTPbyXonzshWKfY-2hEJ-yjqbEBU/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token8022717075:AAFrvQGiTPbyXonzshWKfY-2hEJ-yjqbEBU
End-PointgetMe
Args
Telegram-Tokens (1)8022717075:AAFrvQGiTPbyXonzshWKfY-2hEJ-yjqbEBU
Telegram-Info-Links
8022717075:AAFrvQGiTPbyXonzshWKfY-2hEJ-yjqbEBU
Get info about bothttps://api.telegram.org/bot8022717075:AAFrvQGiTPbyXonzshWKfY-2hEJ-yjqbEBU/getMe
Get incoming updateshttps://api.telegram.org/bot8022717075:AAFrvQGiTPbyXonzshWKfY-2hEJ-yjqbEBU/getUpdates
Get webhookhttps://api.telegram.org/bot8022717075:AAFrvQGiTPbyXonzshWKfY-2hEJ-yjqbEBU/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot8022717075:AAFrvQGiTPbyXonzshWKfY-2hEJ-yjqbEBU/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot8022717075:AAFrvQGiTPbyXonzshWKfY-2hEJ-yjqbEBU/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token8022717075:AAFrvQGiTPbyXonzshWKfY-2hEJ-yjqbEBU
End-PointsendDocument
Args
chat_id (1)7848641603
Telegram-Tokens (1)8022717075:AAFrvQGiTPbyXonzshWKfY-2hEJ-yjqbEBU
Telegram-Info-Links
8022717075:AAFrvQGiTPbyXonzshWKfY-2hEJ-yjqbEBU
Get info about bothttps://api.telegram.org/bot8022717075:AAFrvQGiTPbyXonzshWKfY-2hEJ-yjqbEBU/getMe
Get incoming updateshttps://api.telegram.org/bot8022717075:AAFrvQGiTPbyXonzshWKfY-2hEJ-yjqbEBU/getUpdates
Get webhookhttps://api.telegram.org/bot8022717075:AAFrvQGiTPbyXonzshWKfY-2hEJ-yjqbEBU/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot8022717075:AAFrvQGiTPbyXonzshWKfY-2hEJ-yjqbEBU/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot8022717075:AAFrvQGiTPbyXonzshWKfY-2hEJ-yjqbEBU/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token8022717075:AAFrvQGiTPbyXonzshWKfY-2hEJ-yjqbEBU
End-PointsendDocument
Args
chat_id (1)7848641603
caption (1)📂 - Browser data
├── 📂 - cookies (2.24 kb)
Telegram-Tokens (1)8022717075:AAFrvQGiTPbyXonzshWKfY-2hEJ-yjqbEBU
Telegram-Info-Links
8022717075:AAFrvQGiTPbyXonzshWKfY-2hEJ-yjqbEBU
Get info about bothttps://api.telegram.org/bot8022717075:AAFrvQGiTPbyXonzshWKfY-2hEJ-yjqbEBU/getMe
Get incoming updateshttps://api.telegram.org/bot8022717075:AAFrvQGiTPbyXonzshWKfY-2hEJ-yjqbEBU/getUpdates
Get webhookhttps://api.telegram.org/bot8022717075:AAFrvQGiTPbyXonzshWKfY-2hEJ-yjqbEBU/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot8022717075:AAFrvQGiTPbyXonzshWKfY-2hEJ-yjqbEBU/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot8022717075:AAFrvQGiTPbyXonzshWKfY-2hEJ-yjqbEBU/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token8022717075:AAFrvQGiTPbyXonzshWKfY-2hEJ-yjqbEBU
End-PointsendDocument
Args
chat_id (1)7848641603
caption (1)📂 - Browser data
├── 📂 - cookies (2.24 kb)
Token8022717075:AAFrvQGiTPbyXonzshWKfY-2hEJ-yjqbEBU
End-PointsendDocument
Args
chat_id (1)7848641603
Telegram-Responses
oktrue
result
id8022717075
is_bottrue
first_namestormkitty2121
usernamestormkitty2121_bot
can_join_groupstrue
can_read_all_group_messagesfalse
supports_inline_queriesfalse
can_connect_to_businessfalse
has_main_web_appfalse
Total processes
296
Monitored processes
147
Malicious processes
23
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 320 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 952 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --noerrdialogs --user-data-dir="C:\Users\admin\AppData\Local\Google\Chrome\User Data" --extension-process --enable-dinosaur-easter-egg-alt-images --remote-debugging-port=9222 --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --field-trial-handle=2800,i,5154195214112468915,11749888681531461323,262144 --disable-features=PaintHolding --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=3672 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 984 | "C:\Users\admin\AppData\Roaming\mr.exe" | C:\Users\admin\AppData\Roaming\mr.exe | — | update.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1036 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc -parentBuildID 20250227124745 -prefsHandle 2200 -prefsLen 36520 -prefMapHandle 2204 -prefMapSize 272997 -ipcHandle 2212 -initialChannelId {e4775f1c-4b36-4932-9e61-264482373f22} -parentPid 7592 -crashReporter "\\.\pipe\gecko-crash-server-pipe.7592" -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - 2 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 136.0 Modules
| |||||||||||||||
| 1132 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --headless --string-annotations --noerrdialogs --user-data-dir="C:\Users\admin\AppData\Local\Google\Chrome\User Data" --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAAAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --use-gl=angle --use-angle=swiftshader-webgl --field-trial-handle=1916,i,15630820859543052971,14828992356390695820,262144 --disable-features=PaintHolding --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=1908 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1296 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=4832,i,17949965168126603563,7533932932748357996,262144 --variations-seed-version --mojo-platform-channel-handle=5072 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
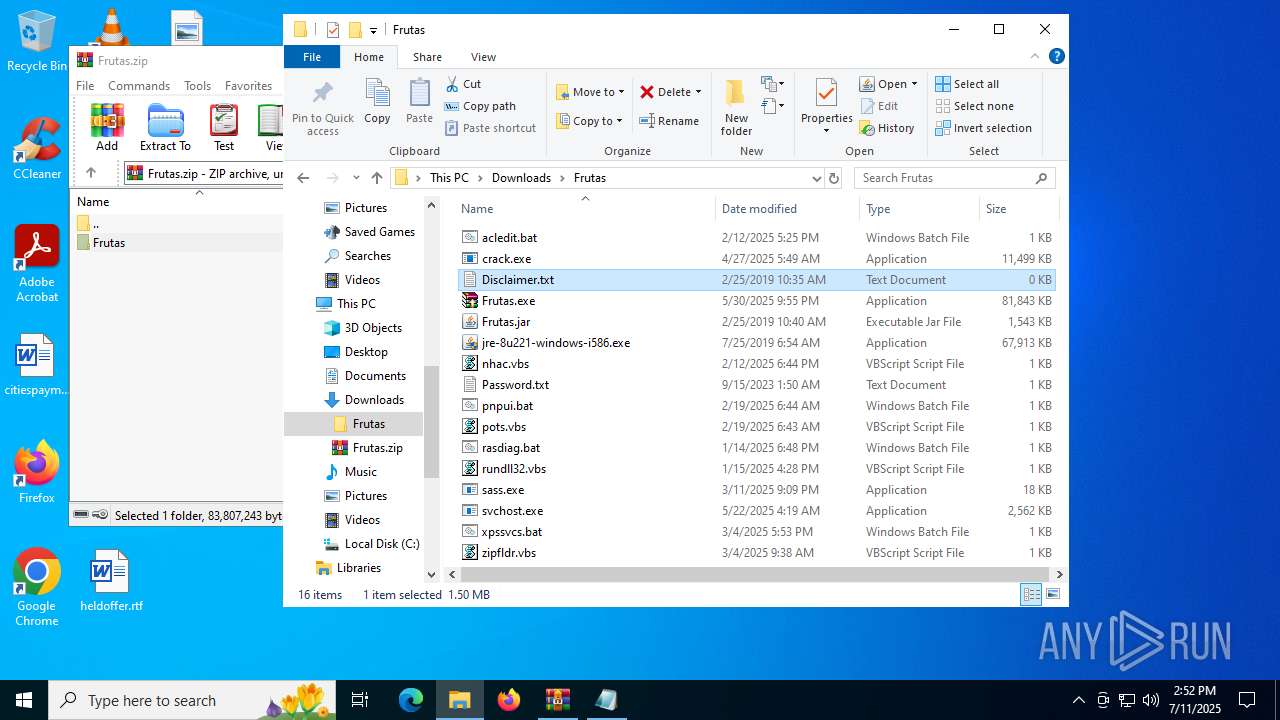
| 1296 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Downloads\Frutas\Disclaimer.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1332 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1520 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --noerrdialogs --user-data-dir="C:\Users\admin\AppData\Local\Google\Chrome\User Data" --enable-dinosaur-easter-egg-alt-images --remote-debugging-port=9222 --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --field-trial-handle=3132,i,5154195214112468915,11749888681531461323,262144 --disable-features=PaintHolding --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=3128 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1588 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\Downloads\Frutas\pots.vbs" | C:\Windows\SysWOW64\wscript.exe | — | Frutas.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
Total events
74 603
Read events
74 480
Write events
103
Delete events
20
Modification events
| (PID) Process: | (5168) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (5168) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (5168) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (5168) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (5168) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 971AFEAD3E982F00 | |||
| (PID) Process: | (5168) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\525124 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {F9A033EF-B8FE-40C2-8E11-08681F77787C} | |||
| (PID) Process: | (5168) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\525124 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {141A9767-67DA-4F70-A141-57AFBA0D9F81} | |||
| (PID) Process: | (5168) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\525124 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {AEB3171B-C6BD-48A3-A37F-2E772A1F32E2} | |||
| (PID) Process: | (5168) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\525124 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {5863287E-05BE-4EF2-8C80-1E5FA9972B39} | |||
| (PID) Process: | (5168) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\525124 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {676C83DD-AB7E-4EBF-BE27-7D8373BC67BF} | |||
Executable files
44
Suspicious files
455
Text files
1 861
Unknown types
270
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5168 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RF1754a8.TMP | — | |
MD5:— | SHA256:— | |||
| 5168 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5168 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF1754d6.TMP | — | |
MD5:— | SHA256:— | |||
| 5168 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5168 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF175553.TMP | — | |
MD5:— | SHA256:— | |||
| 5168 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5168 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF175553.TMP | — | |
MD5:— | SHA256:— | |||
| 5168 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5168 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF175553.TMP | — | |
MD5:— | SHA256:— | |||
| 5168 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
84
TCP/UDP connections
386
DNS requests
418
Threats
134
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4860 | msedge.exe | GET | 200 | 150.171.27.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:27hhgt97CVbj1WsdAvhBqXWZi9wBS4eeQQjE4mnjRfw&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7592 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
7592 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
7592 | firefox.exe | POST | 200 | 216.58.212.163:80 | http://o.pki.goog/s/wr3/azY | unknown | — | — | whitelisted |
7592 | firefox.exe | POST | 200 | 216.58.212.163:80 | http://o.pki.goog/s/wr3/k58 | unknown | — | — | whitelisted |
7592 | firefox.exe | POST | 200 | 216.58.212.163:80 | http://o.pki.goog/s/wr3/azY | unknown | — | — | whitelisted |
7592 | firefox.exe | POST | 200 | 216.58.212.163:80 | http://o.pki.goog/s/wr3/azY | unknown | — | — | whitelisted |
7592 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 52.191.219.104:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1268 | svchost.exe | 52.191.219.104:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4888 | RUXIMICS.exe | 52.191.219.104:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4860 | msedge.exe | 91.226.124.125:80 | depositfiles.com | Webzilla B.V. | CZ | whitelisted |
4860 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4860 | msedge.exe | 150.171.27.11:80 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4860 | msedge.exe | 150.171.27.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4860 | msedge.exe | 91.226.124.125:443 | depositfiles.com | Webzilla B.V. | CZ | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
depositfiles.com |
| whitelisted |
copilot.microsoft.com |
| whitelisted |
dfiles.com |
| unknown |
www.bing.com |
| whitelisted |
static.depositfiles.com |
| whitelisted |
www.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4860 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
4860 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
4860 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
4860 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
Process | Message |
|---|---|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Google\Chrome\User Data directory exists )
|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Google\Chrome\User Data directory exists )
|