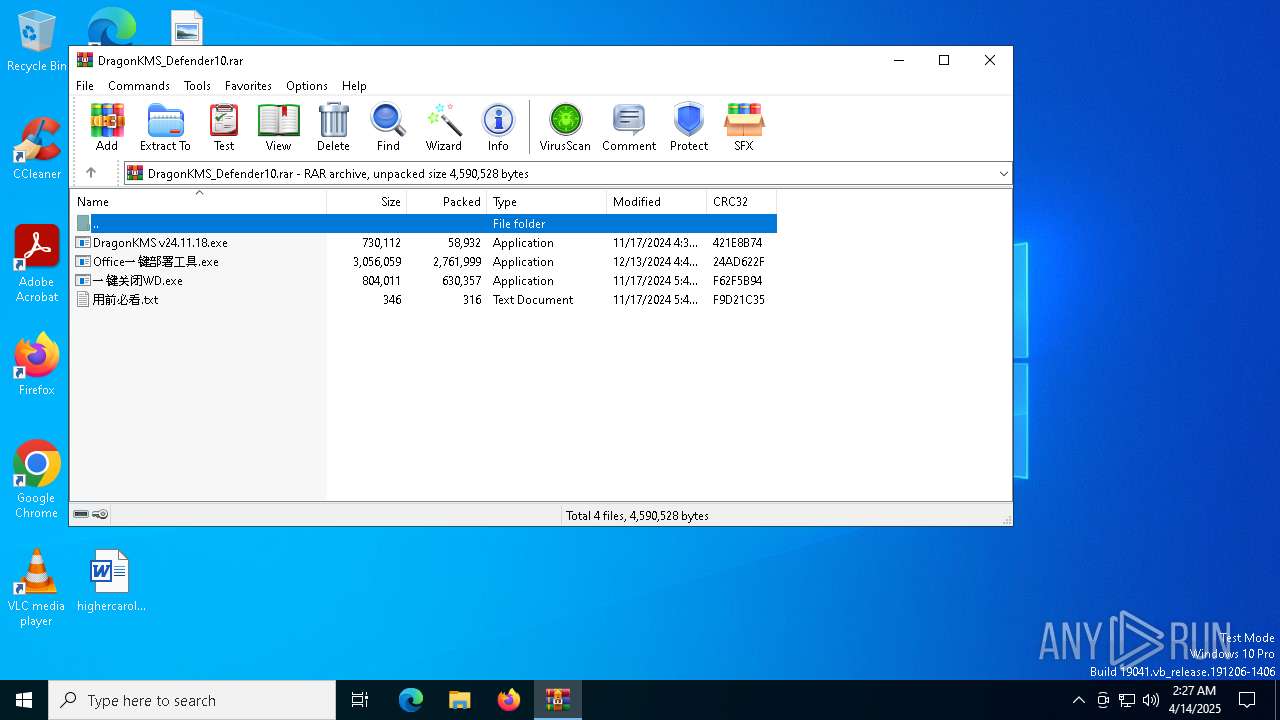
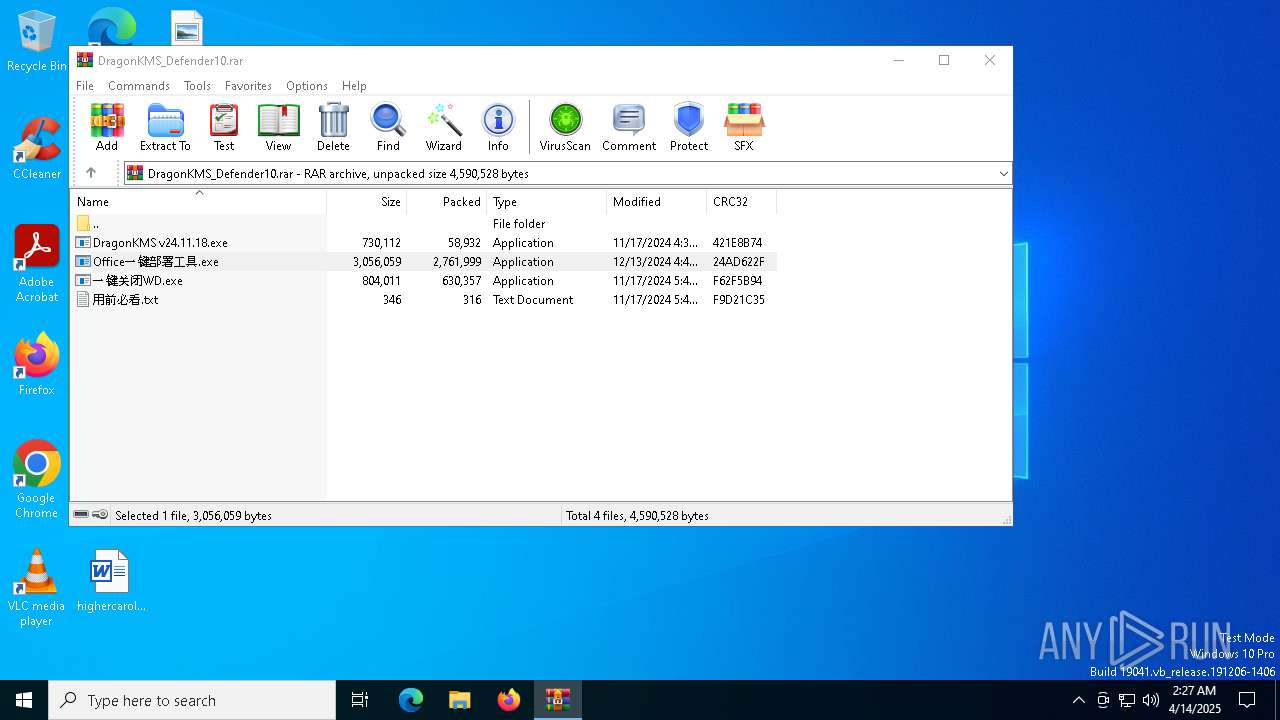
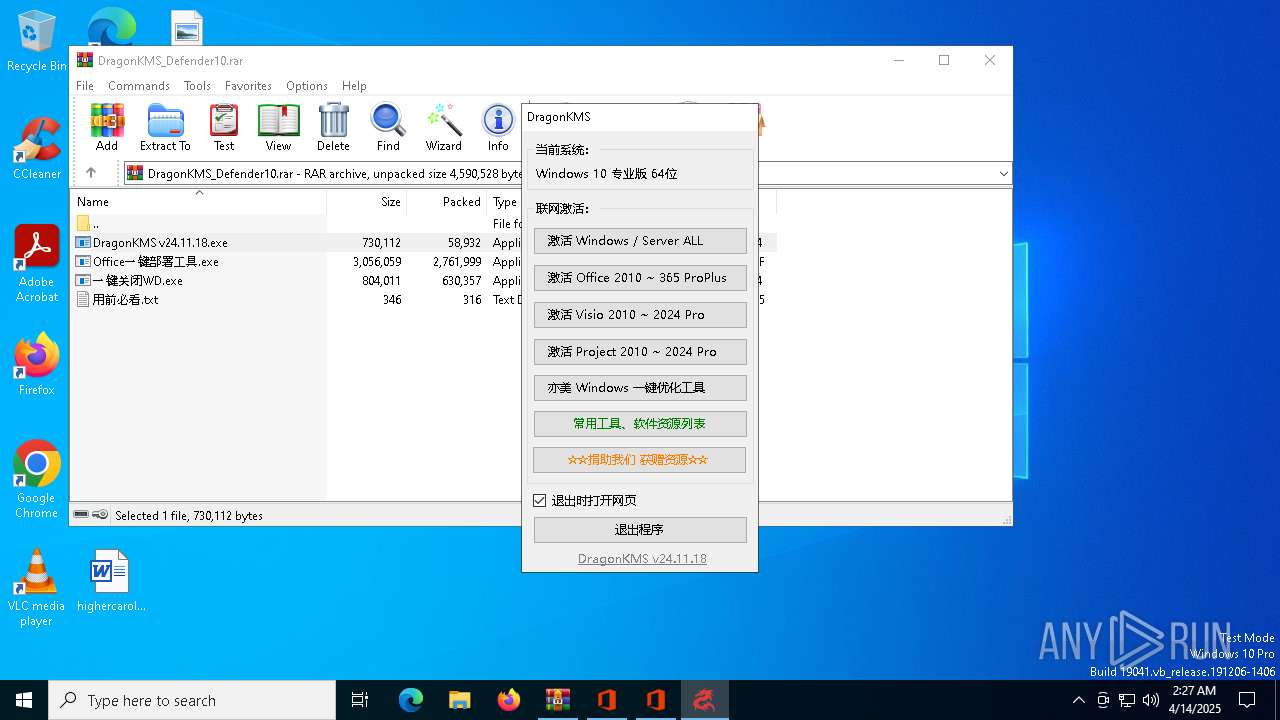
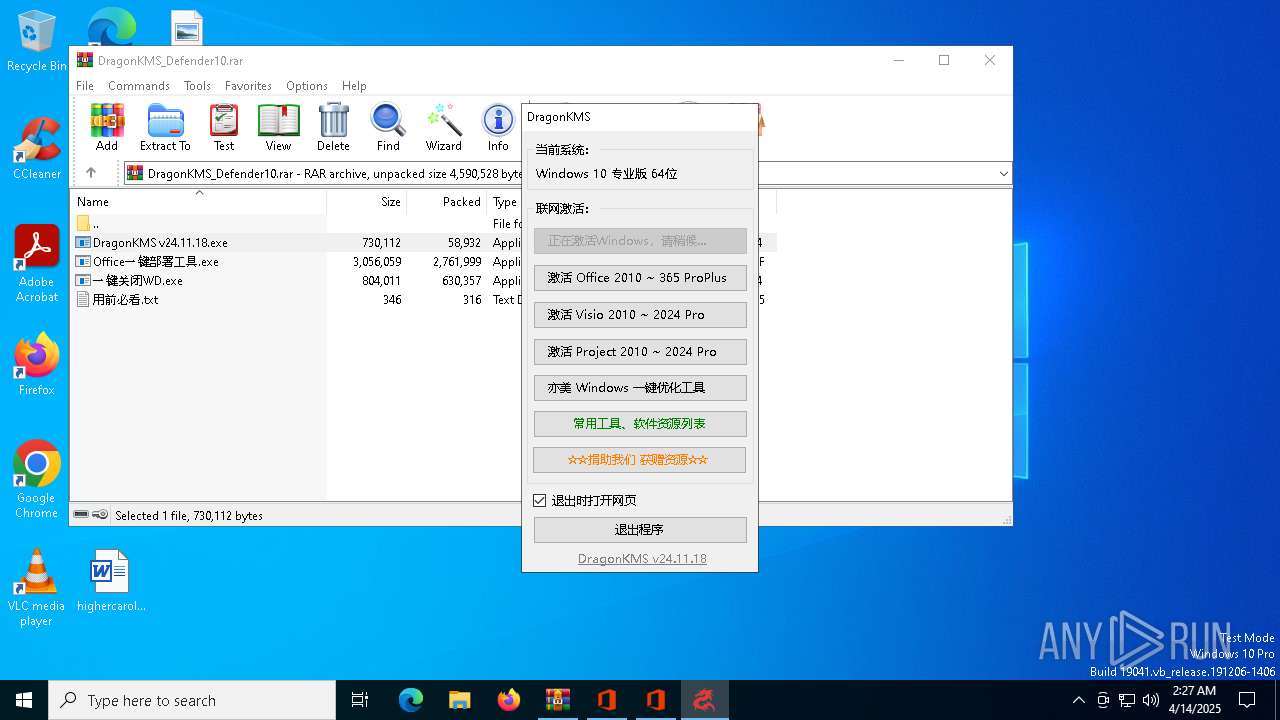
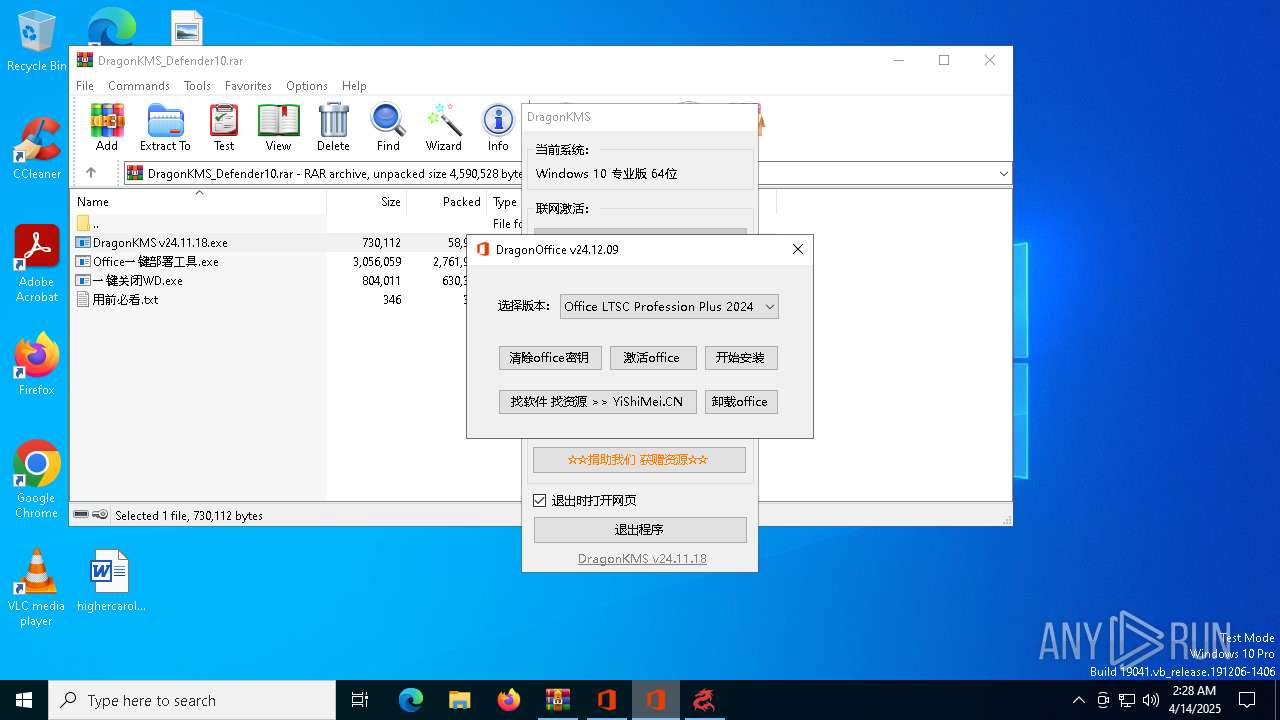
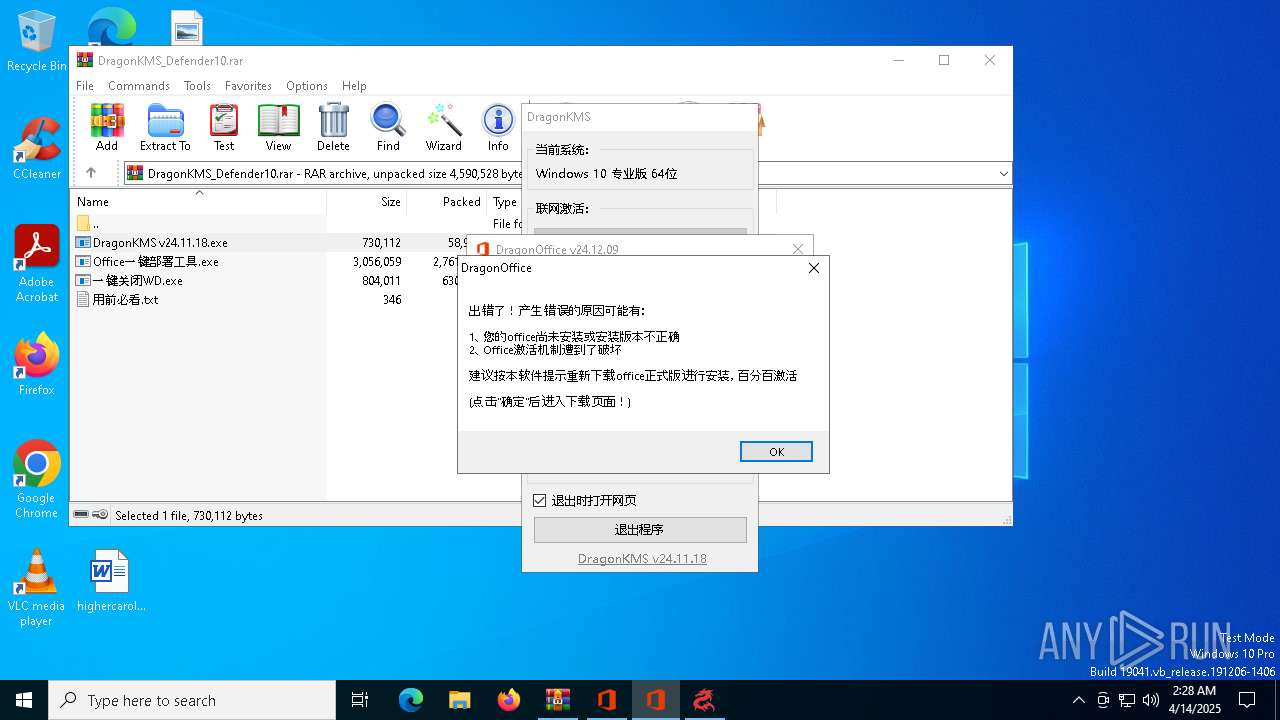
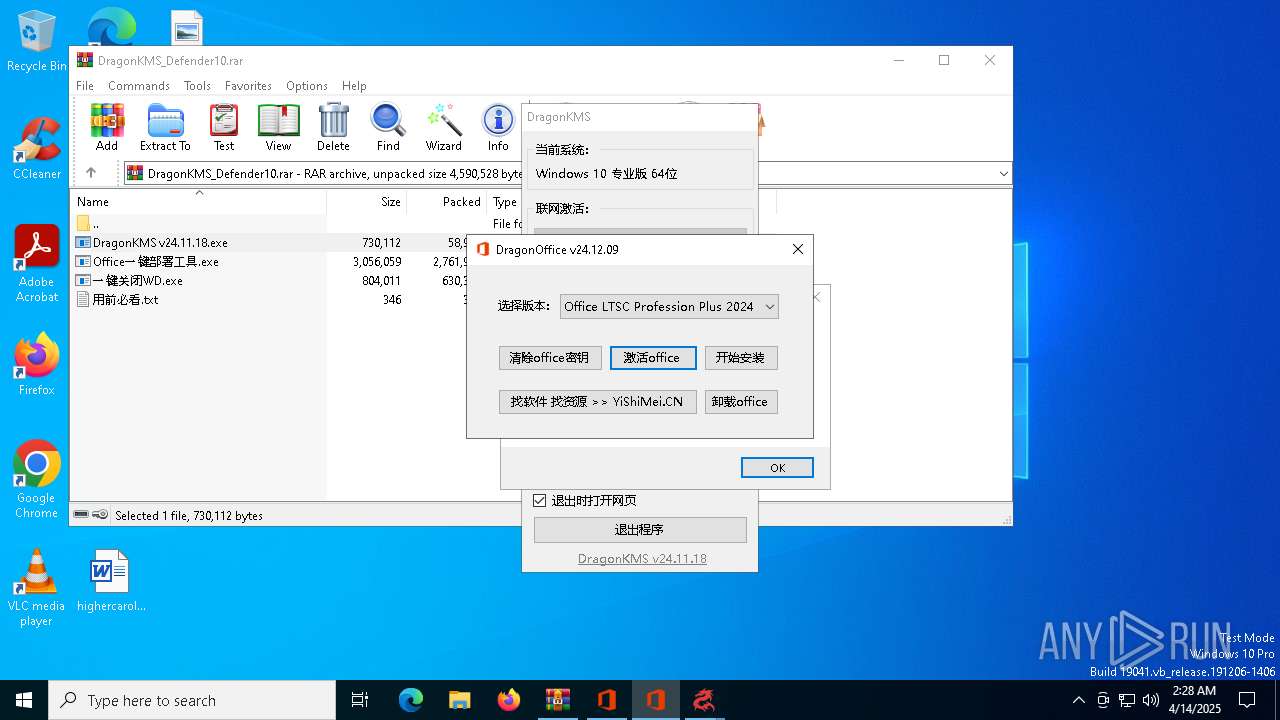
| File name: | DragonKMS_Defender10.rar |
| Full analysis: | https://app.any.run/tasks/c2ccfed9-461f-47d9-9467-2772232055a5 |
| Verdict: | Malicious activity |
| Analysis date: | April 14, 2025, 02:27:26 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 2F5154D910A1C969A80873EDF72B3355 |
| SHA1: | 4DF1F33BFB247BBE68C4C39BDB76114C3EA55437 |
| SHA256: | 8596F125C9AC117DB77B588561C0F14994A4FCE0F6E5C9662B9078B4450442AA |
| SSDEEP: | 98304:YWtisVSGZXimkv7J5JNrYP7mLOs1T65JWnClf36jNf9a86+KbDkKW5PDfBJMNDs6:Hq972lrLF |
MALICIOUS
Accesses name of the domain to which a computer belongs via WMI (SCRIPT)
- cscript.exe (PID: 3008)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4688)
- Office一键部署工具.exe (PID: 2108)
- Office一键部署工具.exe (PID: 5576)
- DragonOffice.exe (PID: 5164)
Executable content was dropped or overwritten
- Office一键部署工具.exe (PID: 2108)
- Office一键部署工具.exe (PID: 5576)
Process drops legitimate windows executable
- Office一键部署工具.exe (PID: 2108)
- Office一键部署工具.exe (PID: 5576)
Reads the date of Windows installation
- Office一键部署工具.exe (PID: 2108)
- Office一键部署工具.exe (PID: 5576)
Connects to unusual port
- DragonOffice.exe (PID: 5384)
- DragonOffice.exe (PID: 5164)
- DragonKMS v24.11.18.exe (PID: 5380)
- SppExtComObj.Exe (PID: 3676)
Starts CMD.EXE for commands execution
- DragonKMS v24.11.18.exe (PID: 5380)
The process executes VB scripts
- cmd.exe (PID: 2136)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 2908)
- cscript.exe (PID: 2800)
- cscript.exe (PID: 3008)
Reads data from a binary Stream object (SCRIPT)
- cscript.exe (PID: 2908)
- cscript.exe (PID: 3008)
- cscript.exe (PID: 2800)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 2908)
- cscript.exe (PID: 3008)
- cscript.exe (PID: 2800)
Creates file in the systems drive root
- cmd.exe (PID: 2136)
- DragonKMS v24.11.18.exe (PID: 5380)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4688)
Checks supported languages
- Office一键部署工具.exe (PID: 5576)
- Office一键部署工具.exe (PID: 2108)
- DragonOffice.exe (PID: 5164)
- DragonKMS v24.11.18.exe (PID: 5380)
- DragonOffice.exe (PID: 5384)
- identity_helper.exe (PID: 6248)
Create files in a temporary directory
- Office一键部署工具.exe (PID: 2108)
- Office一键部署工具.exe (PID: 5576)
Reads the computer name
- Office一键部署工具.exe (PID: 5576)
- Office一键部署工具.exe (PID: 2108)
- DragonOffice.exe (PID: 5164)
- DragonOffice.exe (PID: 5384)
- DragonKMS v24.11.18.exe (PID: 5380)
- identity_helper.exe (PID: 6248)
Process checks computer location settings
- Office一键部署工具.exe (PID: 2108)
- Office一键部署工具.exe (PID: 5576)
Reads the machine GUID from the registry
- DragonOffice.exe (PID: 5164)
- DragonOffice.exe (PID: 5384)
- DragonKMS v24.11.18.exe (PID: 5380)
Checks proxy server information
- DragonOffice.exe (PID: 5384)
- DragonOffice.exe (PID: 5164)
- DragonKMS v24.11.18.exe (PID: 5380)
Disables trace logs
- DragonOffice.exe (PID: 5164)
- DragonOffice.exe (PID: 5384)
- DragonKMS v24.11.18.exe (PID: 5380)
Reads Environment values
- DragonOffice.exe (PID: 5384)
- DragonOffice.exe (PID: 5164)
- DragonKMS v24.11.18.exe (PID: 5380)
- identity_helper.exe (PID: 6248)
Reads product name
- DragonKMS v24.11.18.exe (PID: 5380)
Reads security settings of Internet Explorer
- cscript.exe (PID: 2908)
- cscript.exe (PID: 3008)
- cscript.exe (PID: 2800)
Reads Microsoft Office registry keys
- DragonOffice.exe (PID: 5164)
Application launched itself
- msedge.exe (PID: 7392)
- msedge.exe (PID: 7660)
Manual execution by a user
- msedge.exe (PID: 7660)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 316 |
| UncompressedSize: | 346 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | 用前必看.txt |
Total processes
187
Monitored processes
52
Malicious processes
5
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 536 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --no-appcompat-clear --mojo-platform-channel-handle=5140 --field-trial-handle=2396,i,2307440225020223154,4086153420293679544,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 736 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4356 --field-trial-handle=2396,i,2307440225020223154,4086153420293679544,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2108 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa4688.47800\Office一键部署工具.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa4688.47800\Office一键部署工具.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 2136 | "cmd.exe" | C:\Windows\System32\cmd.exe | — | DragonKMS v24.11.18.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2148 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\DragonOffice.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\DragonOffice.exe | — | Office一键部署工具.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: DragonOffice Exit code: 3221226540 Version: 24.12.09.0 Modules
| |||||||||||||||
| 2800 | cscript C:\WINDOWS\System32\slmgr.vbs /ato | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 2908 | cscript C:\WINDOWS\System32\slmgr.vbs /ipk W269N-WFGWX-YVC9B-4J6C9-T83GX | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 3008 | cscript C:\WINDOWS\System32\slmgr.vbs /skms win.xdym11235.com | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 3240 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3268 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=4192 --field-trial-handle=2396,i,2307440225020223154,4086153420293679544,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
11 003
Read events
10 943
Write events
60
Delete events
0
Modification events
| (PID) Process: | (4688) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4688) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4688) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4688) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\DragonKMS_Defender10.rar | |||
| (PID) Process: | (4688) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4688) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4688) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4688) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5384) DragonOffice.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\DragonOffice_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5384) DragonOffice.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\DragonOffice_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
Executable files
20
Suspicious files
190
Text files
72
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4688 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4688.47800\用前必看.txt | text | |
MD5:511FE9AECE8FB432150763AEA7624738 | SHA256:A75BB8B2E556176725D6A5AF62B3ABBC6E51DB3358A575E7F6F6ADDCECD4BC75 | |||
| 4688 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4688.47836\用前必看.txt | text | |
MD5:511FE9AECE8FB432150763AEA7624738 | SHA256:A75BB8B2E556176725D6A5AF62B3ABBC6E51DB3358A575E7F6F6ADDCECD4BC75 | |||
| 2108 | Office一键部署工具.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\configuration\ProPlus2019Retail.xml | text | |
MD5:F13A9DEE2123DDADCF52800A6DD4CD6F | SHA256:E164ABA0CCE0F81B1A6815138947C1F8835F5875127BA126713C3A9BE3F9BCDC | |||
| 2108 | Office一键部署工具.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\configuration\OfficeSetup.exe | executable | |
MD5:2BA6246A85064DB4978F19EC71C347F7 | SHA256:335932E68D7A8BFA4FA00BBCDEA09256ED6ECAB2BEDD640E2580B0B43E3B7744 | |||
| 2108 | Office一键部署工具.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\configuration\ProjectPro2024Retail.xml | text | |
MD5:718A33530632B5E15396BCE88AA8E045 | SHA256:2A3D825EBAA82D5A8E9408CBE12DC32A84268DD905595F0C5584F2FBF8B8E0E2 | |||
| 2108 | Office一键部署工具.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\configuration\ProjectPro2016Retail.xml | text | |
MD5:AD37623BA9AFF40A7161B1D0B9B8B98B | SHA256:7AAAA2AD2C9E4A9657D07C9E3E0F12F60556F024A3F54B2534B784BF45D8E854 | |||
| 2108 | Office一键部署工具.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\configuration\ProPlus2016Retail.xml | text | |
MD5:FB7451F5D3086AF14DC06806C329774A | SHA256:CA74F0561F4E774E34DF9256E244797BA8E479AE5D20F5DF8471975DCECF06EC | |||
| 2108 | Office一键部署工具.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\configuration\ProPlus2024Retail.xml | text | |
MD5:F4977006A6F27222A0FD00CE2C1B0BE6 | SHA256:6F07C53299B99F83BC195583A12E553D354B88DEBE1A79E24D225ADA00444F8F | |||
| 2108 | Office一键部署工具.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\configuration\ProPlus2021Retail.xml | text | |
MD5:B9495D6EECE229EF966CE765EA50C7A5 | SHA256:725508B80BDAD250DD61CF9D1FE1C986C3C39ADC12952901838F916472D8267C | |||
| 2108 | Office一键部署工具.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\configuration\VisioPro2019Retail.xml | text | |
MD5:C8BB23416691D59B67200913B8EFF6DE | SHA256:4204FF1E84503F4631DEE30ED35E67A9BC25B3F946E37BF87B675B4F07808311 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
66
TCP/UDP connections
87
DNS requests
58
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
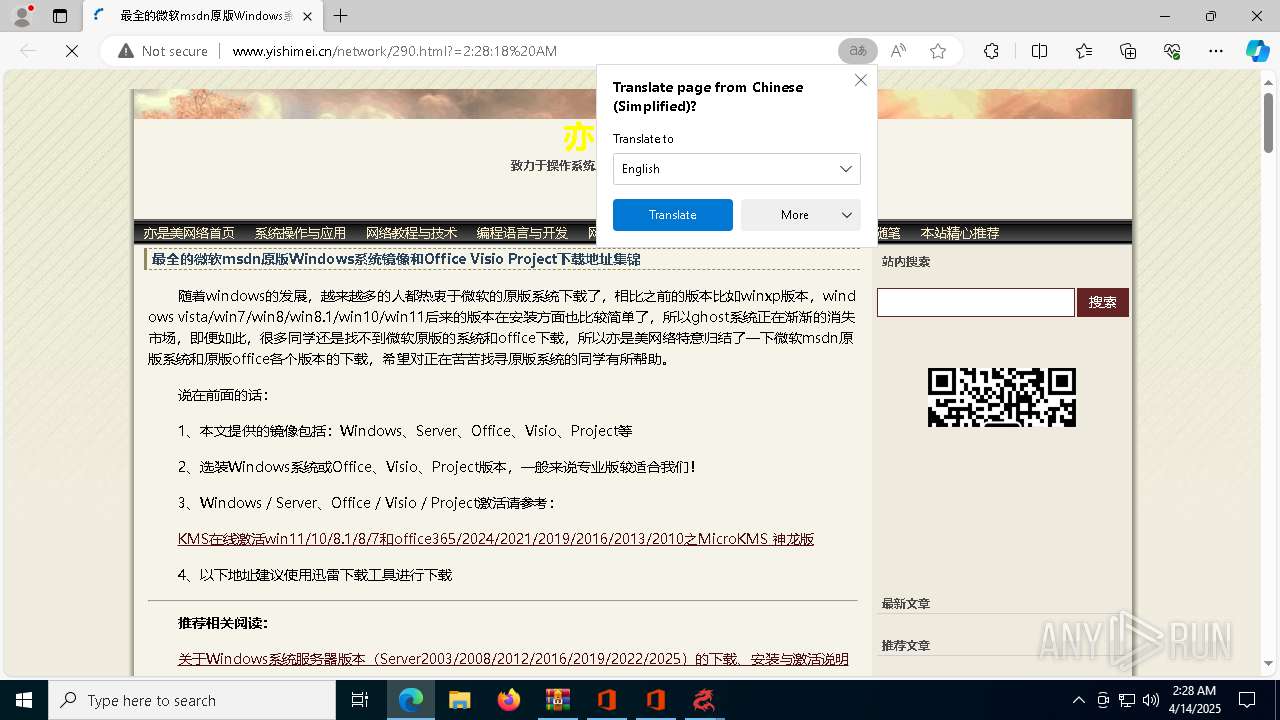
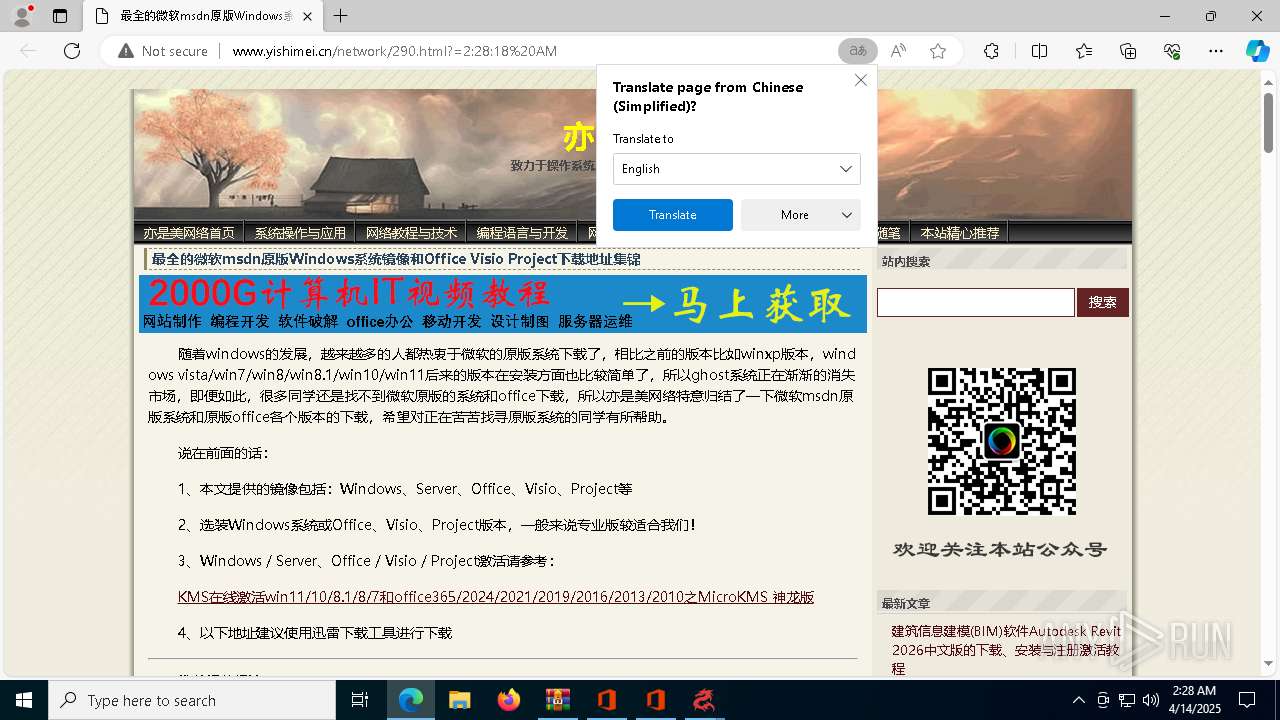
7972 | msedge.exe | GET | 200 | 116.255.154.157:80 | http://www.yishimei.cn/network/290.html?=2:28:18%20AM | unknown | — | — | unknown |
7972 | msedge.exe | GET | 200 | 116.255.154.157:80 | http://www.yishimei.cn/themes/j-spring/source/style.css.asp | unknown | — | — | unknown |
7972 | msedge.exe | GET | 200 | 116.255.154.157:80 | http://www.yishimei.cn/script/ad_daohang.js | unknown | — | — | unknown |
7972 | msedge.exe | GET | 200 | 116.255.154.157:80 | http://www.yishimei.cn/function/c_html_js_add.asp | unknown | — | — | unknown |
7972 | msedge.exe | GET | 200 | 116.255.154.157:80 | http://www.yishimei.cn/script/common.js | unknown | — | — | unknown |
7972 | msedge.exe | GET | 200 | 116.255.154.157:80 | http://www.yishimei.cn/themes/j-spring/style/j-spring.css | unknown | — | — | unknown |
7972 | msedge.exe | GET | 200 | 116.255.154.157:80 | http://www.yishimei.cn/script/ad_sidebar_down.js | unknown | — | — | unknown |
7972 | msedge.exe | GET | 200 | 116.255.154.157:80 | http://www.yishimei.cn/script/ad_banner.js | unknown | — | — | unknown |
7972 | msedge.exe | GET | 200 | 116.255.154.157:80 | http://www.yishimei.cn/script/ad_search.js | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.69:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5164 | DragonOffice.exe | 116.255.154.157:80 | www.yishimei.cn | CHINA UNICOM China169 Backbone | CN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.yishimei.cn |
| unknown |
win.xdym11235.com |
| unknown |
kms.kmzs123.cn |
| unknown |
kms.luody.info |
| unknown |