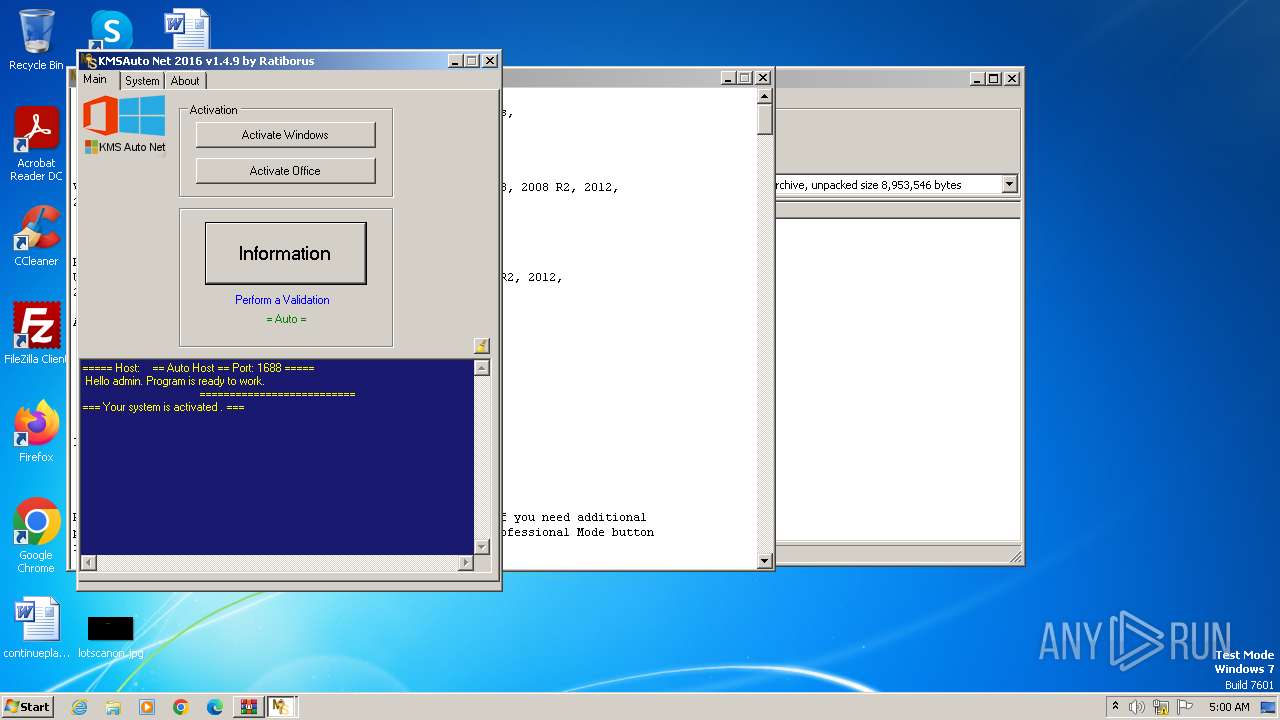
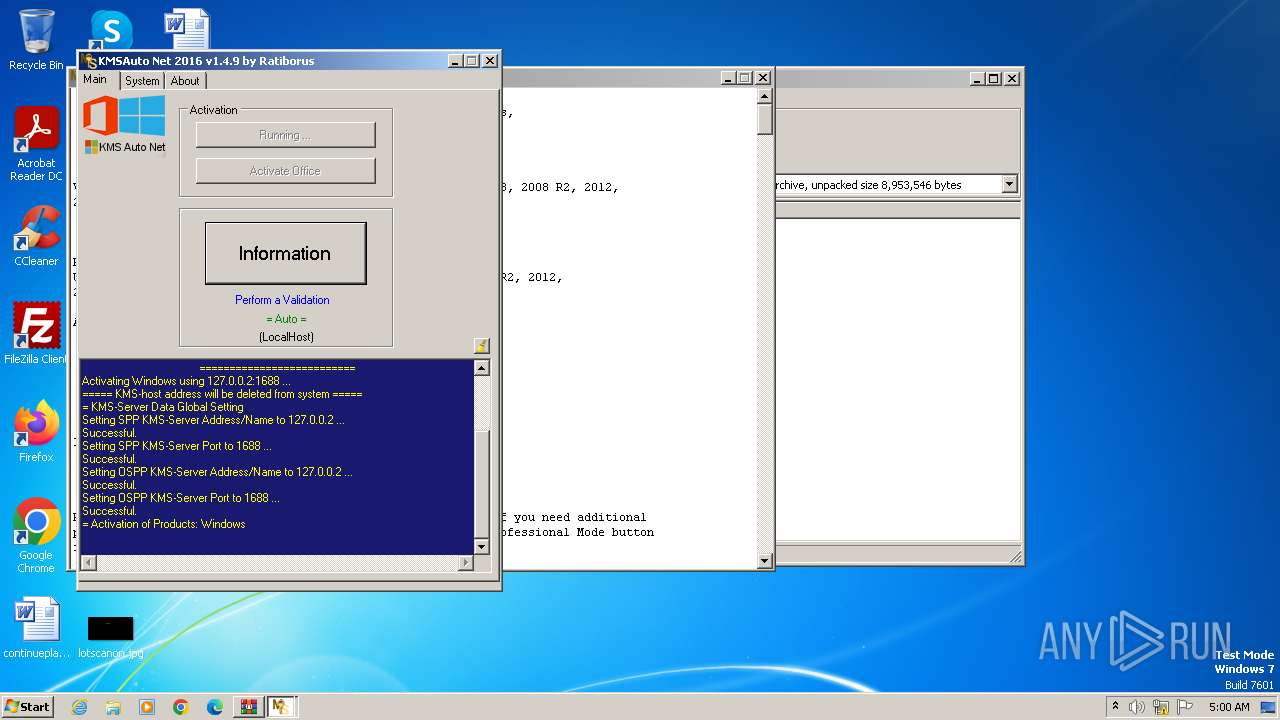
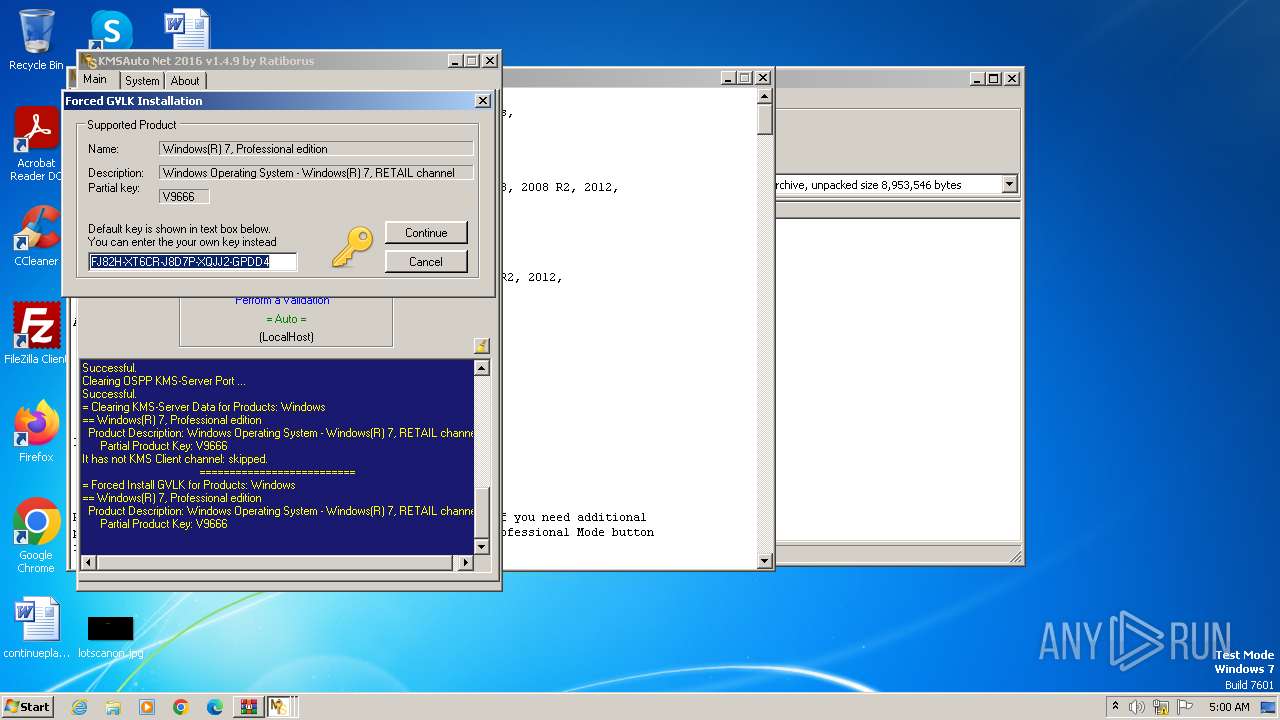
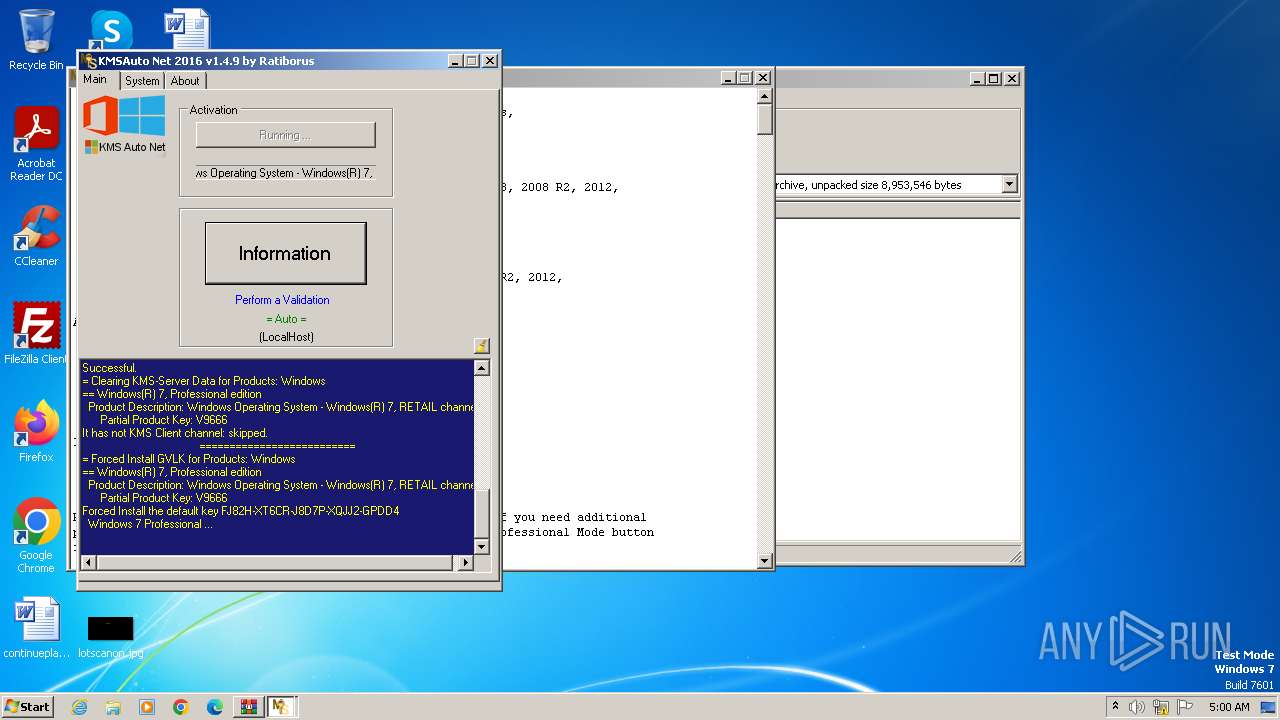
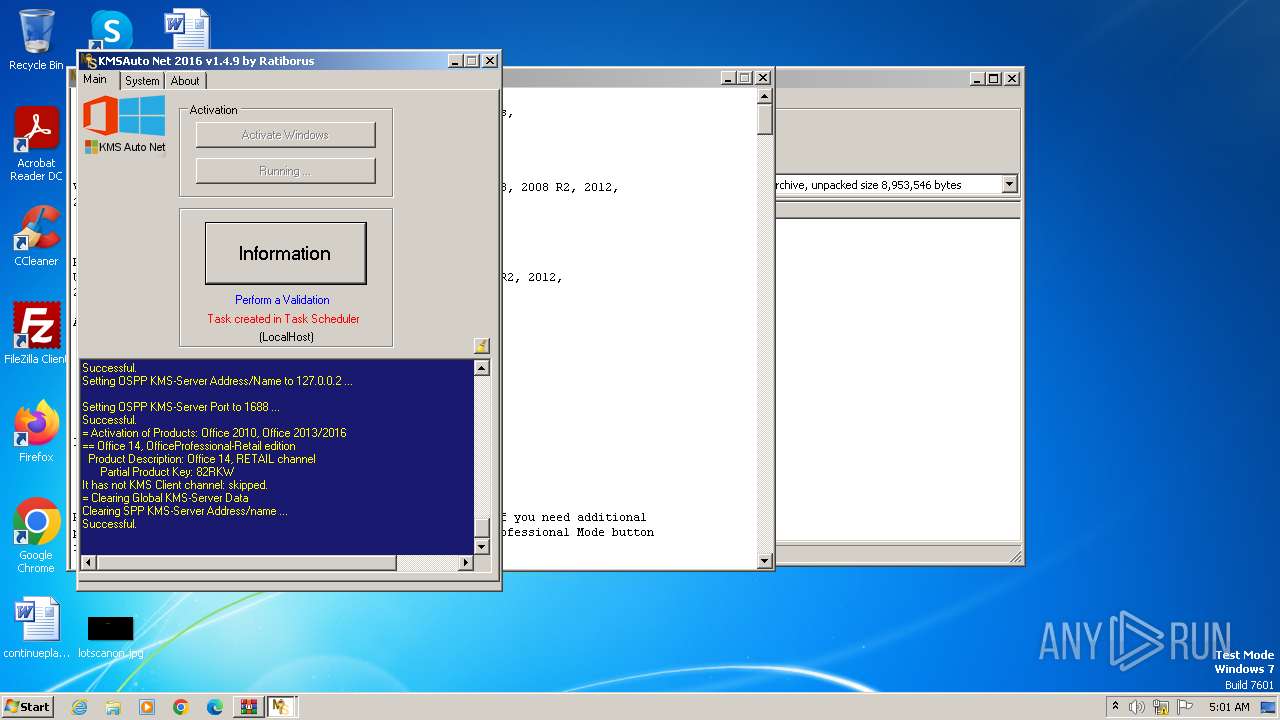
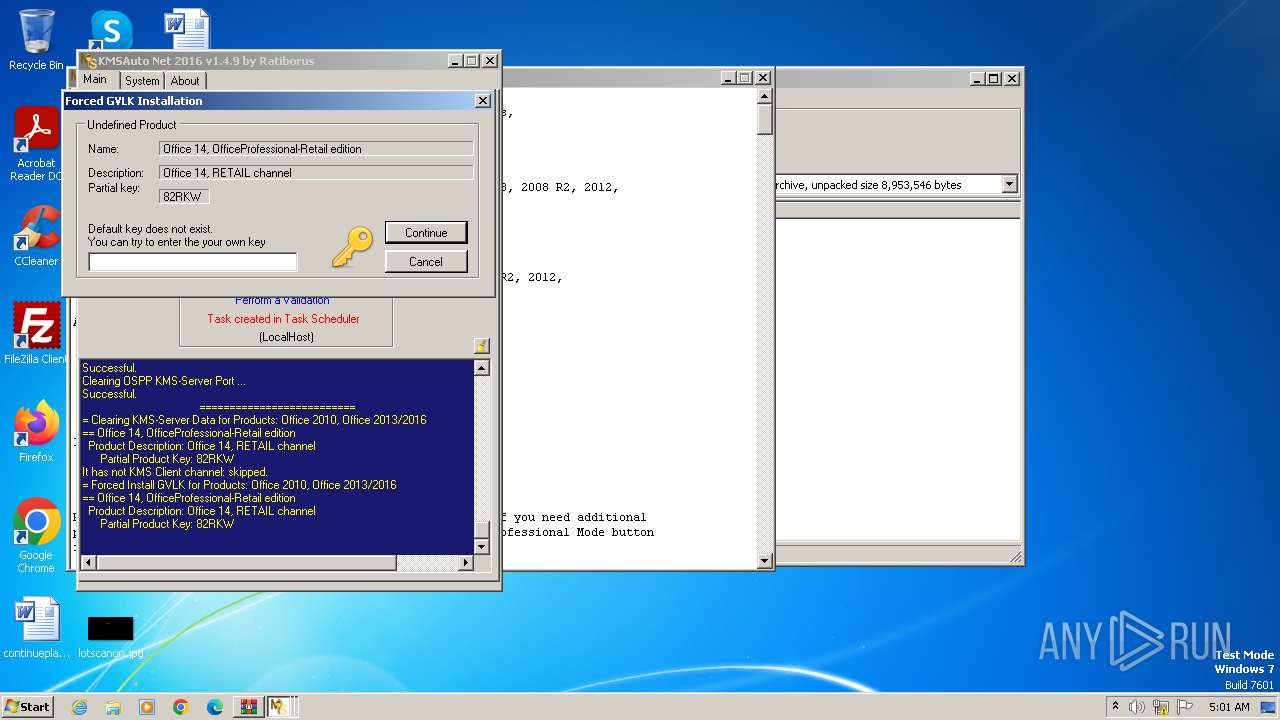
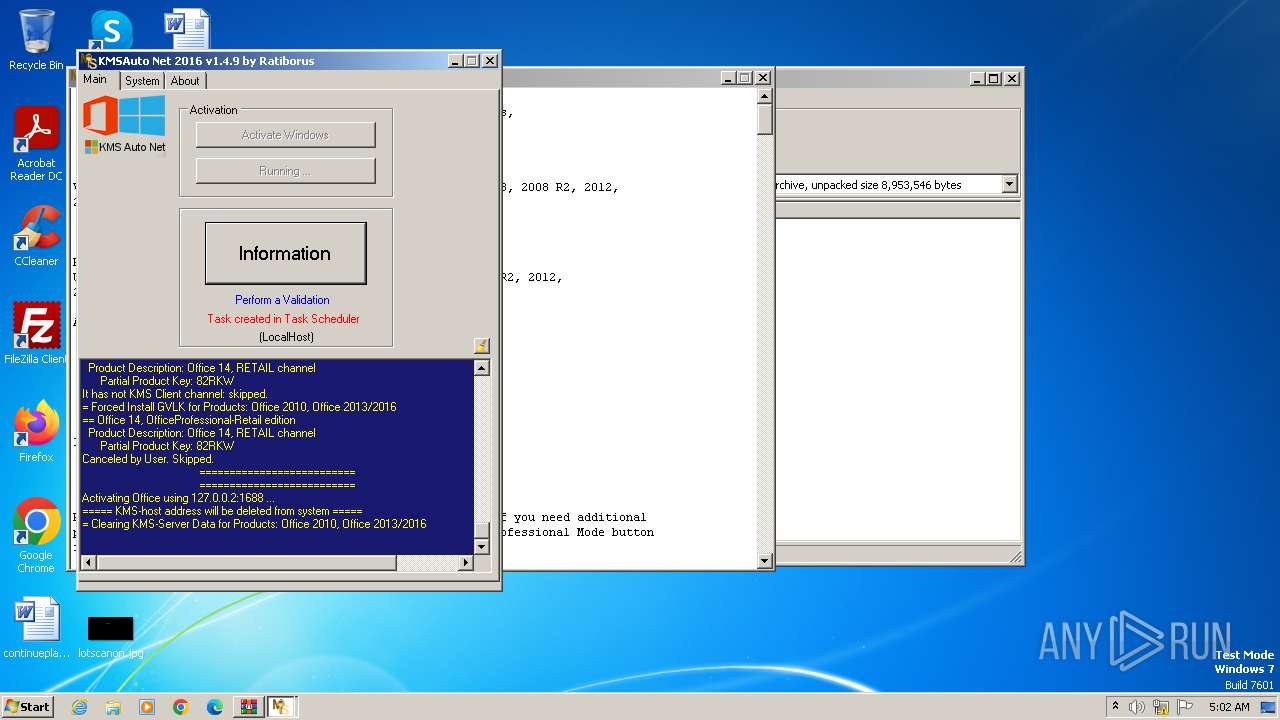
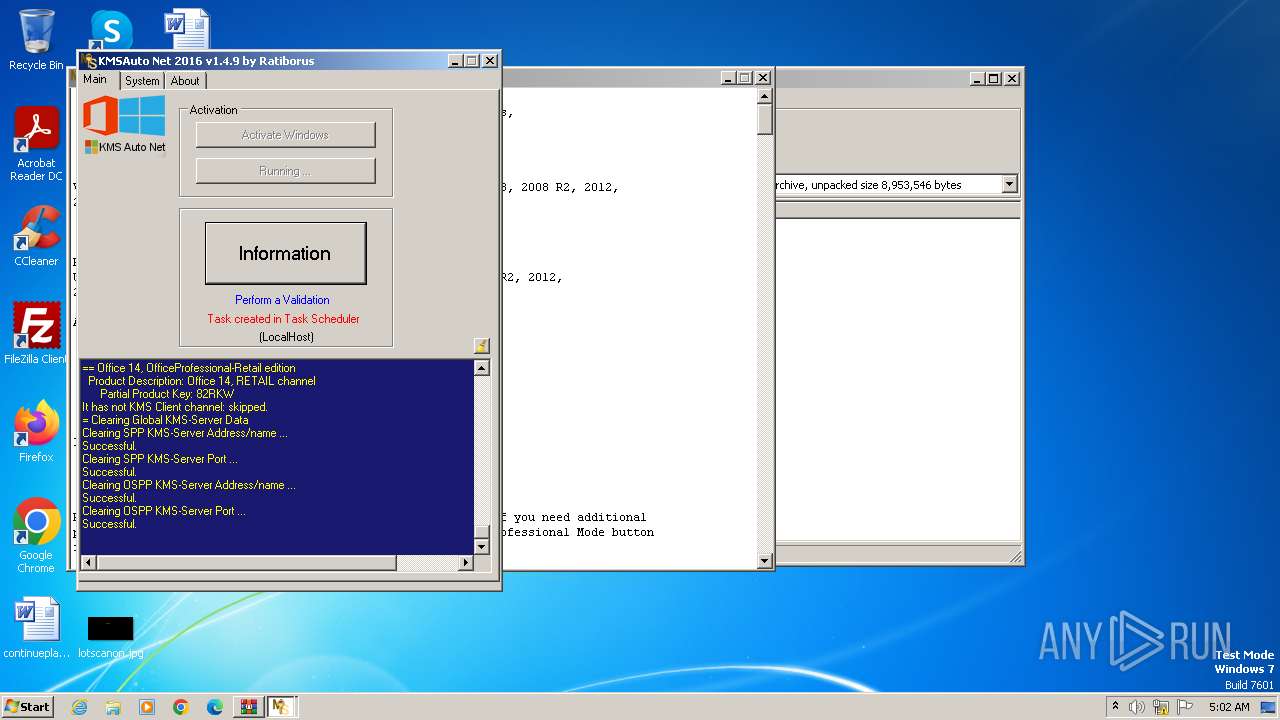
| File name: | KMSAuto Net 2016 - Windows 10 & Office 2016 Activator.rar |
| Full analysis: | https://app.any.run/tasks/8f678e1d-6011-4bea-8a03-c67379b7091e |
| Verdict: | Malicious activity |
| Analysis date: | June 05, 2024, 03:59:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 2C7FCCA70042645146B6EBEC873518A8 |
| SHA1: | A97C78645ADD9080EF28E151AF53DF992F904281 |
| SHA256: | 8593634EE71DE8E18CAEE16540AA3E8C4FA16C4A63D17ACDADC0959962EE8AA4 |
| SSDEEP: | 98304:s8Bfpv5cZmE83dzOEJEIMgOCINo+wEe9+B5gOUx7Nu3tMxhn5dprr3mnJC2z9rzj:YWAnZdwI |
MALICIOUS
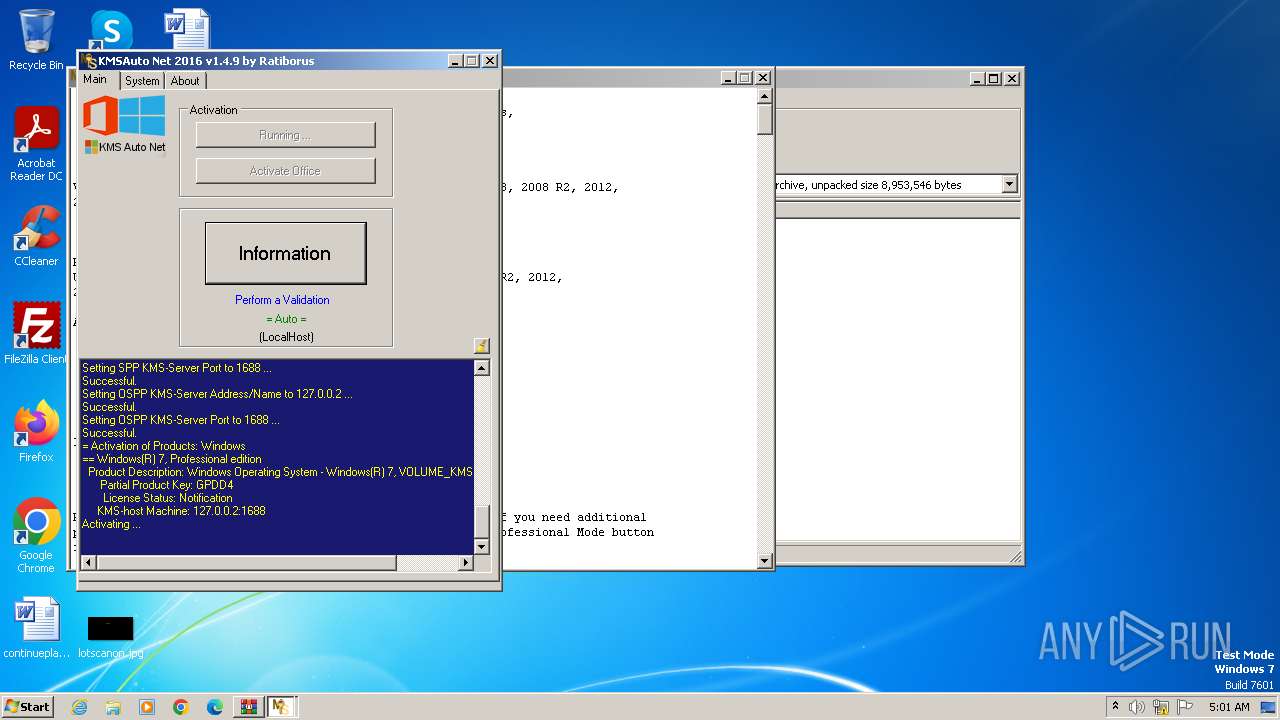
Drops the executable file immediately after the start
- KMSAuto Net.exe (PID: 2116)
- bin.dat (PID: 1600)
- bin_x86.dat (PID: 2456)
- AESDecoder.exe (PID: 2624)
- bin.dat (PID: 3724)
- AESDecoder.exe (PID: 752)
- bin.dat (PID: 2612)
- bin_x86.dat (PID: 2424)
- AESDecoder.exe (PID: 1880)
- bin_x86.dat (PID: 588)
- bin.dat (PID: 1768)
- AESDecoder.exe (PID: 3024)
- bin_x86.dat (PID: 1036)
- AESDecoder.exe (PID: 3696)
- bin.dat (PID: 3596)
- bin_x86.dat (PID: 3632)
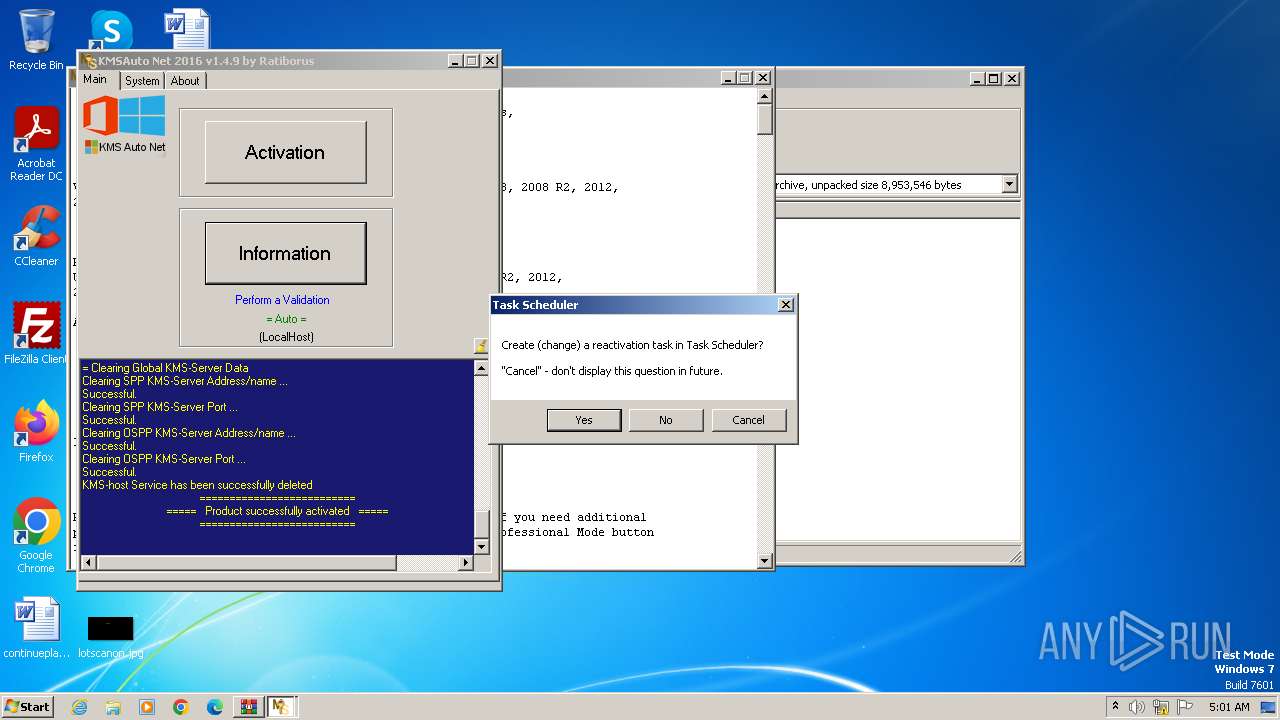
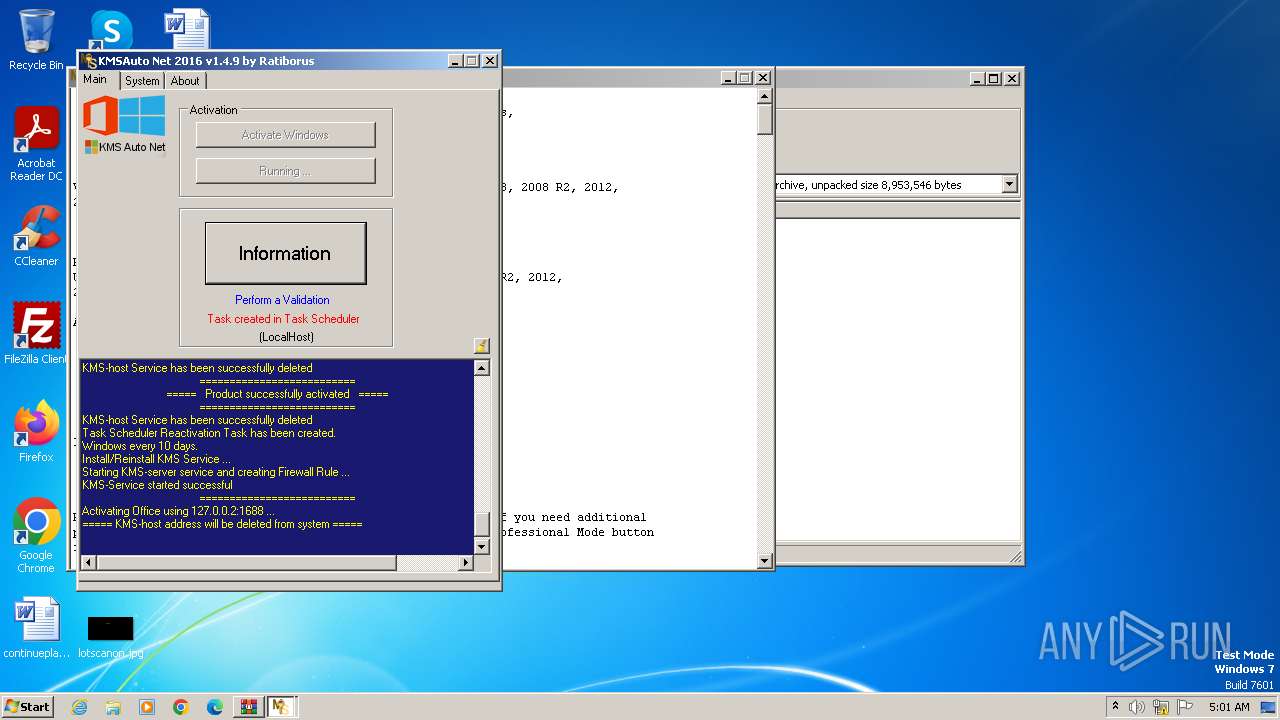
Uses Task Scheduler to run other applications
- cmd.exe (PID: 2348)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3972)
Executable content was dropped or overwritten
- bin.dat (PID: 1600)
- KMSAuto Net.exe (PID: 2116)
- bin_x86.dat (PID: 2456)
- AESDecoder.exe (PID: 2624)
- bin.dat (PID: 3724)
- AESDecoder.exe (PID: 752)
- bin_x86.dat (PID: 588)
- bin.dat (PID: 2612)
- AESDecoder.exe (PID: 1880)
- bin_x86.dat (PID: 2424)
- bin.dat (PID: 1768)
- AESDecoder.exe (PID: 3024)
- bin_x86.dat (PID: 1036)
- bin.dat (PID: 3596)
- AESDecoder.exe (PID: 3696)
- bin_x86.dat (PID: 3632)
Reads Internet Explorer settings
- KMSAuto Net.exe (PID: 2116)
Drops 7-zip archiver for unpacking
- KMSAuto Net.exe (PID: 2116)
Starts application with an unusual extension
- cmd.exe (PID: 736)
- cmd.exe (PID: 2344)
- cmd.exe (PID: 3784)
- cmd.exe (PID: 2012)
- cmd.exe (PID: 856)
- cmd.exe (PID: 2432)
- cmd.exe (PID: 1680)
- cmd.exe (PID: 728)
- cmd.exe (PID: 3064)
- cmd.exe (PID: 3628)
Starts CMD.EXE for commands execution
- KMSAuto Net.exe (PID: 2116)
- cmd.exe (PID: 1868)
- cmd.exe (PID: 2944)
- cmd.exe (PID: 1604)
Application launched itself
- cmd.exe (PID: 1868)
- cmd.exe (PID: 2944)
- cmd.exe (PID: 1604)
Drops a system driver (possible attempt to evade defenses)
- bin_x86.dat (PID: 2456)
- bin_x86.dat (PID: 588)
- bin_x86.dat (PID: 2424)
- bin_x86.dat (PID: 1036)
- bin_x86.dat (PID: 3632)
Process drops legitimate windows executable
- bin_x86.dat (PID: 2456)
- bin_x86.dat (PID: 588)
- bin_x86.dat (PID: 2424)
- bin_x86.dat (PID: 1036)
- bin_x86.dat (PID: 3632)
Uses NETSH.EXE to add a firewall rule or allowed programs
- KMSAuto Net.exe (PID: 2116)
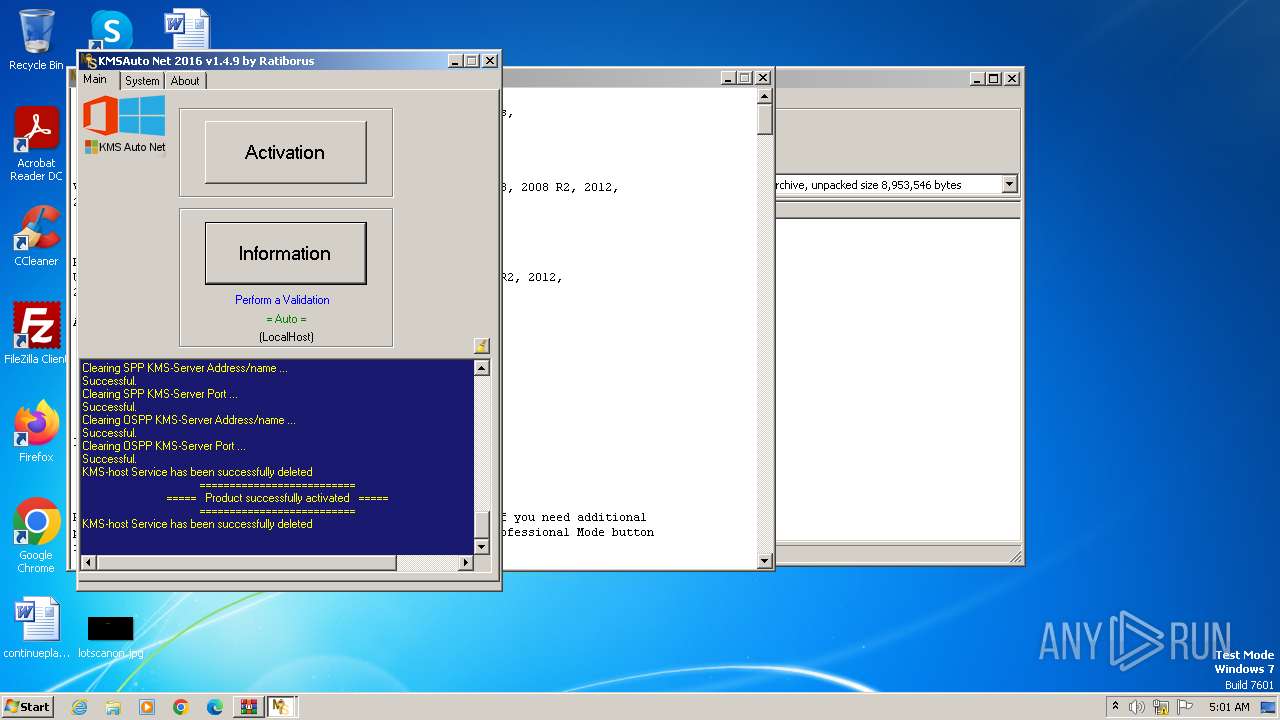
Creates or modifies Windows services
- KMSAuto Net.exe (PID: 2116)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- KMSAuto Net.exe (PID: 2116)
Starts SC.EXE for service management
- KMSAuto Net.exe (PID: 2116)
Executes as Windows Service
- KMSSS.exe (PID: 904)
- KMSSS.exe (PID: 3112)
- KMSSS.exe (PID: 2196)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 3516)
- KMSAuto Net.exe (PID: 2116)
- cmd.exe (PID: 4020)
- cmd.exe (PID: 2996)
Uses ROUTE.EXE to modify routing table
- cmd.exe (PID: 3680)
Uses ROUTE.EXE to obtain the routing table information
- cmd.exe (PID: 2616)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 1480)
Uses WMIC.EXE
- cmd.exe (PID: 3536)
- cmd.exe (PID: 3380)
Reads the Internet Settings
- WMIC.exe (PID: 3516)
- WMIC.exe (PID: 3928)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3972)
Reads the computer name
- KMSAuto Net.exe (PID: 2116)
- KMSSS.exe (PID: 904)
- KMSSS.exe (PID: 3112)
- KMSSS.exe (PID: 2196)
- FakeClient.exe (PID: 2592)
Reads Environment values
- KMSAuto Net.exe (PID: 2116)
Reads product name
- KMSAuto Net.exe (PID: 2116)
Creates files in the program directory
- cmd.exe (PID: 2240)
- bin.dat (PID: 1600)
- KMSAuto Net.exe (PID: 2116)
- bin_x86.dat (PID: 2456)
- AESDecoder.exe (PID: 2624)
- KMSSS.exe (PID: 904)
- cmd.exe (PID: 1768)
- bin.dat (PID: 3724)
- AESDecoder.exe (PID: 752)
- bin_x86.dat (PID: 588)
- cmd.exe (PID: 2448)
- bin.dat (PID: 2612)
- AESDecoder.exe (PID: 1880)
- bin_x86.dat (PID: 2424)
- KMSSS.exe (PID: 3112)
- cmd.exe (PID: 1440)
- bin.dat (PID: 1768)
- AESDecoder.exe (PID: 3024)
- bin_x86.dat (PID: 1036)
- KMSSS.exe (PID: 2196)
- cmd.exe (PID: 3180)
- bin.dat (PID: 3596)
- AESDecoder.exe (PID: 3696)
- bin_x86.dat (PID: 3632)
Checks supported languages
- AESDecoder.exe (PID: 2624)
- KMSAuto Net.exe (PID: 2116)
- bin.dat (PID: 1600)
- KMSSS.exe (PID: 904)
- bin_x86.dat (PID: 2456)
- bin.dat (PID: 3724)
- AESDecoder.exe (PID: 752)
- bin_x86.dat (PID: 588)
- bin.dat (PID: 2612)
- AESDecoder.exe (PID: 1880)
- bin_x86.dat (PID: 2424)
- KMSSS.exe (PID: 3112)
- bin.dat (PID: 1768)
- AESDecoder.exe (PID: 3024)
- bin_x86.dat (PID: 1036)
- KMSSS.exe (PID: 2196)
- FakeClient.exe (PID: 2592)
- bin.dat (PID: 3596)
- AESDecoder.exe (PID: 3696)
- bin_x86.dat (PID: 3632)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3972)
Reads the machine GUID from the registry
- KMSAuto Net.exe (PID: 2116)
- KMSSS.exe (PID: 904)
- KMSSS.exe (PID: 3112)
- KMSSS.exe (PID: 2196)
Creates files or folders in the user directory
- KMSAuto Net.exe (PID: 2116)
Reads Microsoft Office registry keys
- KMSAuto Net.exe (PID: 2116)
Create files in a temporary directory
- KMSAuto Net.exe (PID: 2116)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 3473127 |
|---|---|
| UncompressedSize: | 8767160 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2016:12:18 01:21:14 |
| PackingMethod: | Normal |
| ArchivedFileName: | KMSAuto Net 2016 - Windows 10 & Office 2016 Activator\KMSAuto Net.exe |
Total processes
312
Monitored processes
158
Malicious processes
17
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 112 | schtasks.exe /end /TN KMSAutoNet | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 116 | "C:\Windows\System32\cmd.exe" /c rd "C:\ProgramData\KMSAuto" /S /Q | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 324 | C:\Windows\System32\reg delete "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform\0FF1CE15-A989-479D-AF46-F275C6370663" /f | C:\Windows\System32\reg.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 328 | schtasks.exe /delete /TN KMSAutoNet /F | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 368 | C:\Windows\System32\reg delete "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform\55C92734-D682-4D71-983E-D6EC3F16059F" /f | C:\Windows\System32\reg.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 560 | C:\Windows\system32\cmd.exe /c netstat -ano | find ":1688 " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 560 | C:\Windows\System32\reg delete "HKEY_USERS\S-1-5-20\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform\55c92734-d682-4d71-983e-d6ec3f16059f" /f | C:\Windows\System32\reg.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 580 | schtasks.exe /create /TN KMSAutoNet /XML xmlfile.xml | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 588 | bin_x86.dat -y -pkmsauto | C:\ProgramData\KMSAutoS\bin_x86.dat | cmd.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7z Console SFX Exit code: 0 Version: 9.20 Modules
| |||||||||||||||
| 660 | C:\Windows\System32\cmd.exe /D /c del /F /Q "AESDecoder.exe" | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
15 980
Read events
15 431
Write events
529
Delete events
20
Modification events
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\KMSAuto Net 2016 - Windows 10 & Office 2016 Activator.rar | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
67
Suspicious files
44
Text files
25
Unknown types
15
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3972.29501\KMSAuto Net 2016 - Windows 10 & Office 2016 Activator\KMSAuto Net.exe | — | |
MD5:— | SHA256:— | |||
| 3972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3972.29501\KMSAuto Net 2016 - Windows 10 & Office 2016 Activator\readme\readme_ua.txt | binary | |
MD5:7198D578994C94E03EC59A9A77C2CE5C | SHA256:03E016497148A25841D24DDE4F25706286CE863B658B6EA4DA176C08E73619FB | |||
| 3972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3972.29501\KMSAuto Net 2016 - Windows 10 & Office 2016 Activator\readme\readme_es.txt | binary | |
MD5:02B8AA34903532195267C877A00A057F | SHA256:058EEDD688A03145980BC474EEC19F37AC038E7C22BF0D7993DB2DDF97B8C848 | |||
| 3972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3972.29501\KMSAuto Net 2016 - Windows 10 & Office 2016 Activator\readme\readme_cn.txt | binary | |
MD5:8EF01C32F661F98604A8088520532F90 | SHA256:14A3AEAEAD3BE7450E8707357CCA35F5920A4E7406D4127FAD6B5462CDDD7AF9 | |||
| 3972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3972.29501\KMSAuto Net 2016 - Windows 10 & Office 2016 Activator\readme\readme_ru.txt | binary | |
MD5:8D5153463AD43F43271CB43A68BE415F | SHA256:3679E149DE2D9CE5F28CF0EB17638A2EC4572FE1AD8FDA9A74879C33D0430CB8 | |||
| 3972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3972.29501\KMSAuto Net 2016 - Windows 10 & Office 2016 Activator\readme\readme_en.txt | binary | |
MD5:52D9AEC19C8A160C604B5392C61457B9 | SHA256:76DCE296C07DD9609E338F6966BA38D027C29AAFC546DB47A26A534B80AB7C6D | |||
| 3972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3972.29501\KMSAuto Net 2016 - Windows 10 & Office 2016 Activator\readme\readme_fr.txt | binary | |
MD5:BC4F643037CD440523BDB5F7DC53128D | SHA256:6740373EE8C6CA547FCB3D6A955B36E27174A0E01B32337E000C38AFF3714F2C | |||
| 3972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3972.29501\KMSAuto Net 2016 - Windows 10 & Office 2016 Activator\readme\readme_kms.txt | binary | |
MD5:1008CB833203D9EDD3065F5D42ACDD62 | SHA256:60FF6EEA01FE0C421A25CF9503C93B0939C882A3213F49FF8CBC1FB860EFBD3A | |||
| 3972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3972.32965\KMSAuto Net 2016 - Windows 10 & Office 2016 Activator\readme\readme_fr.txt | text | |
MD5:474FB9BCC634EA9BC1F2B77382A0D03B | SHA256:D0B8BBE89016B3E05FF1C376C9A3CCE7CA2E4070BFFC11BFD9A91808B6DC060C | |||
| 3972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3972.29501\KMSAuto Net 2016 - Windows 10 & Office 2016 Activator\readme\readme_vi.txt | binary | |
MD5:6DEC6BE4586672843C551B90A047FE32 | SHA256:CDF472422A10C4A6AFF827B20DBCCC66FF1A31128400E116E4F40E1458242110 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
DNS requests
Threats
Process | Message |
|---|---|
FakeClient.exe | WdfCoInstaller: [06/05/2024 05:02.06.781] ReadComponents: WdfSection for Driver Service windivert using KMDF lib version Major 0x1, minor 0x9
|
FakeClient.exe | WdfCoInstaller: [06/05/2024 05:02.06.812] BootApplication: GetStartType error error(87) The parameter is incorrect.
Driver Service name windivert
|
FakeClient.exe | WdfCoInstaller: [06/05/2024 05:02.06.812] BootApplication: could not open service windivert, error error(1060) The specified service does not exist as an installed service.
|