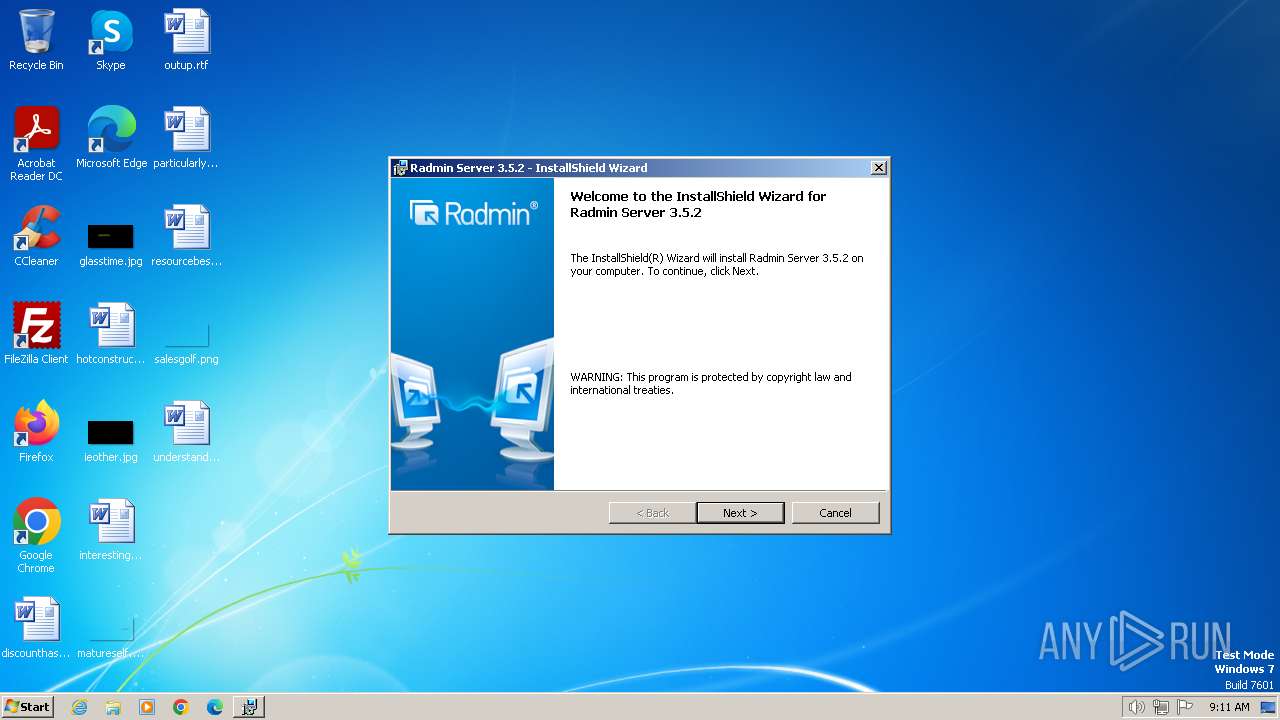
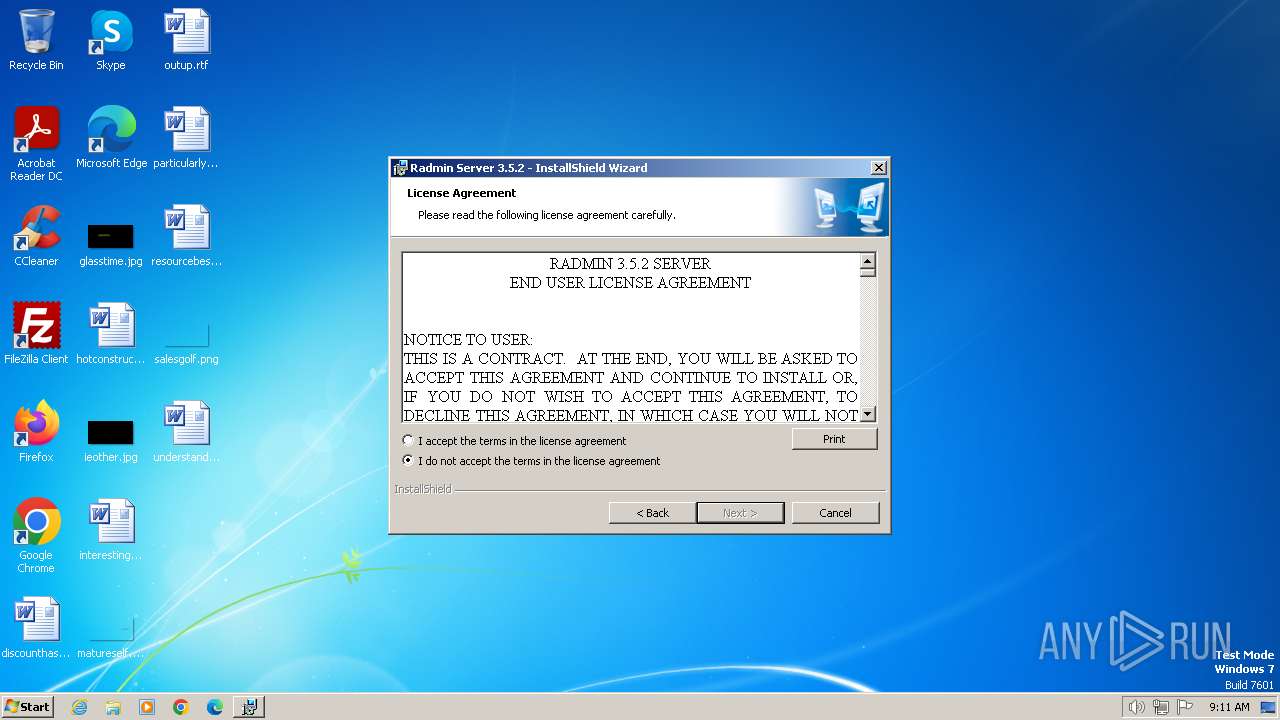
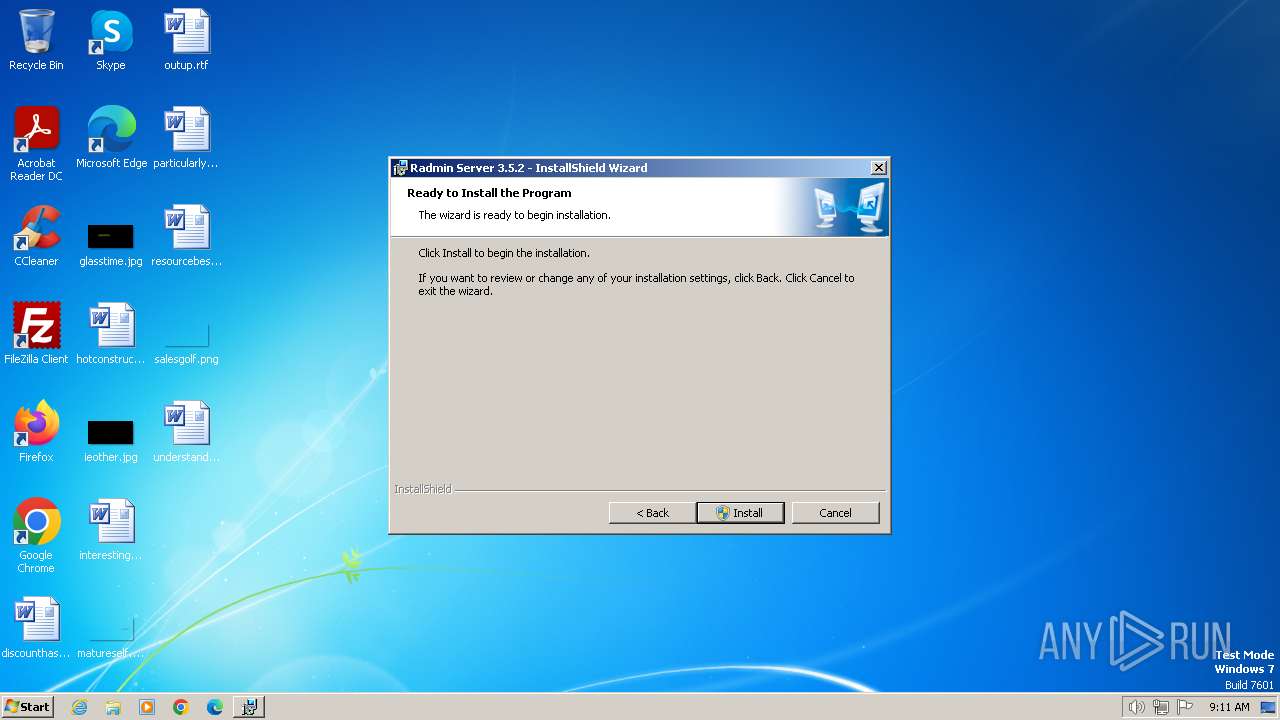
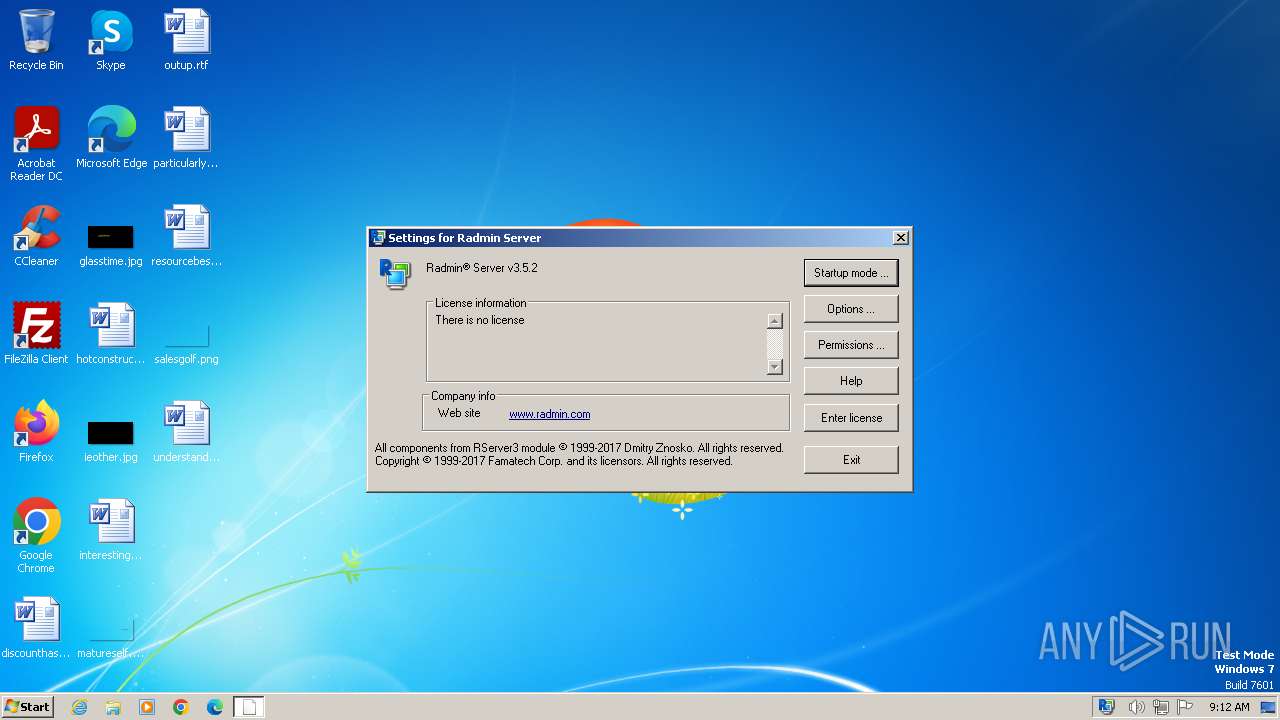
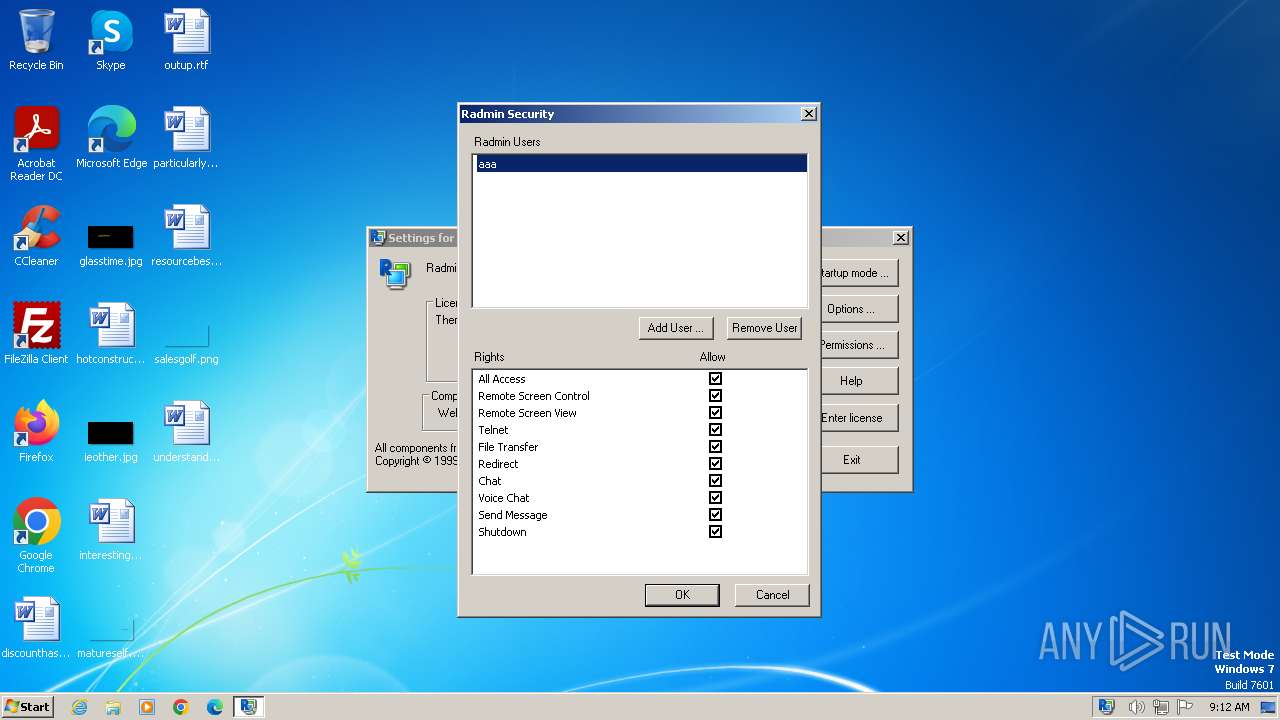
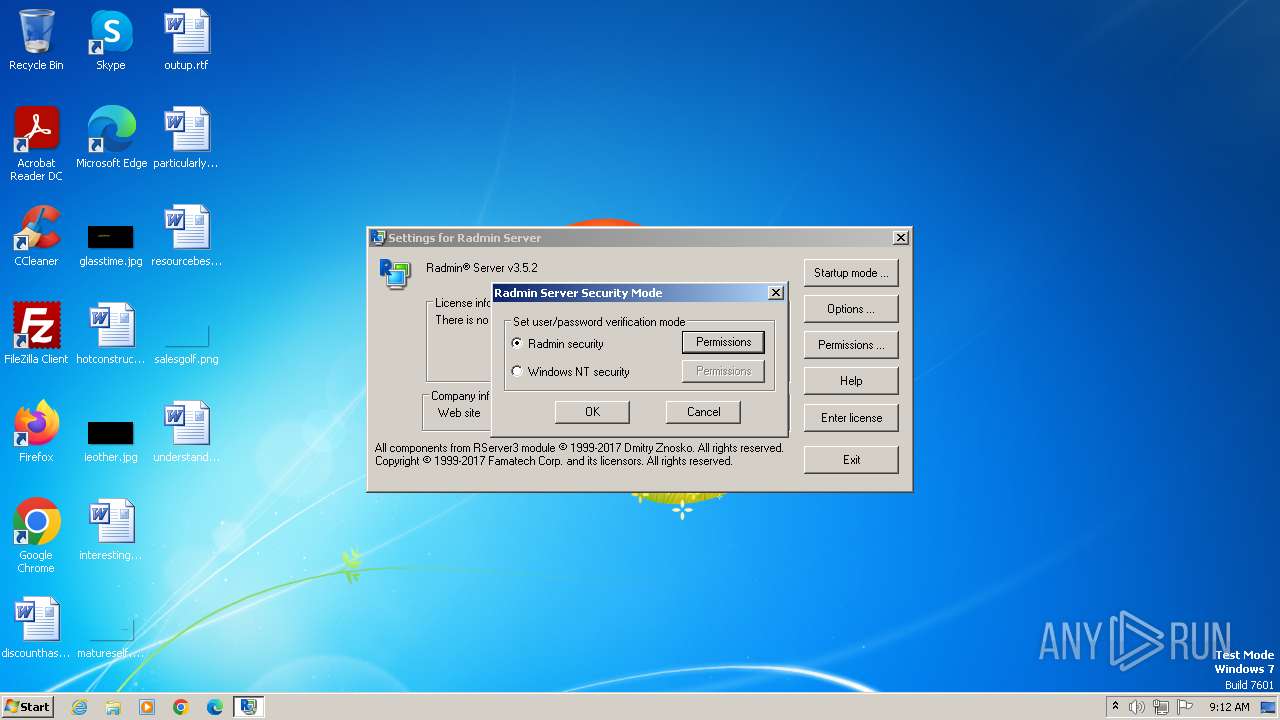
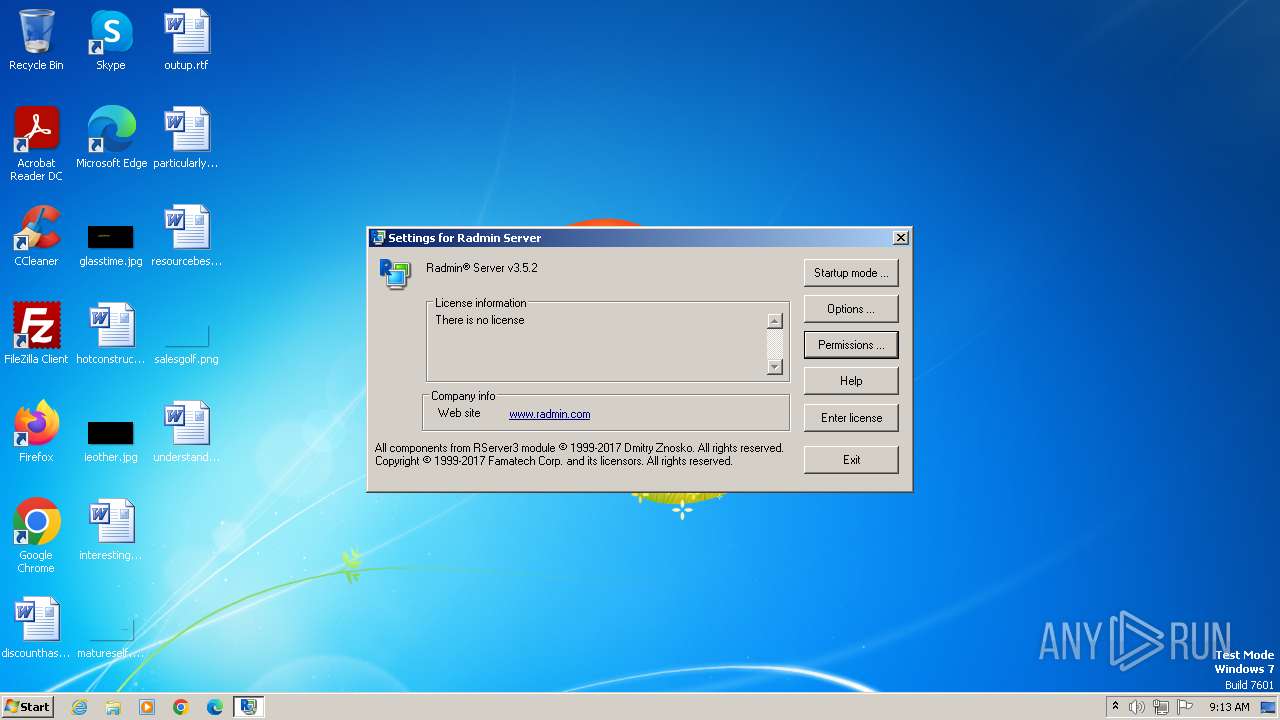
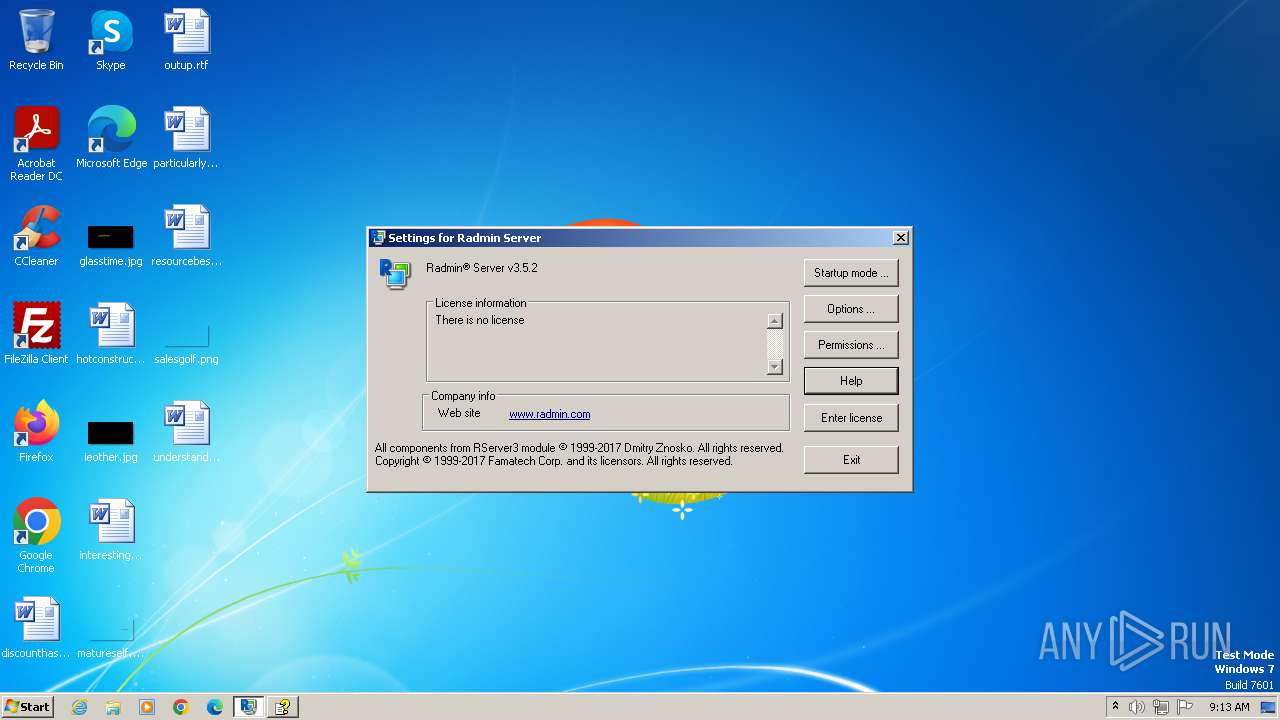
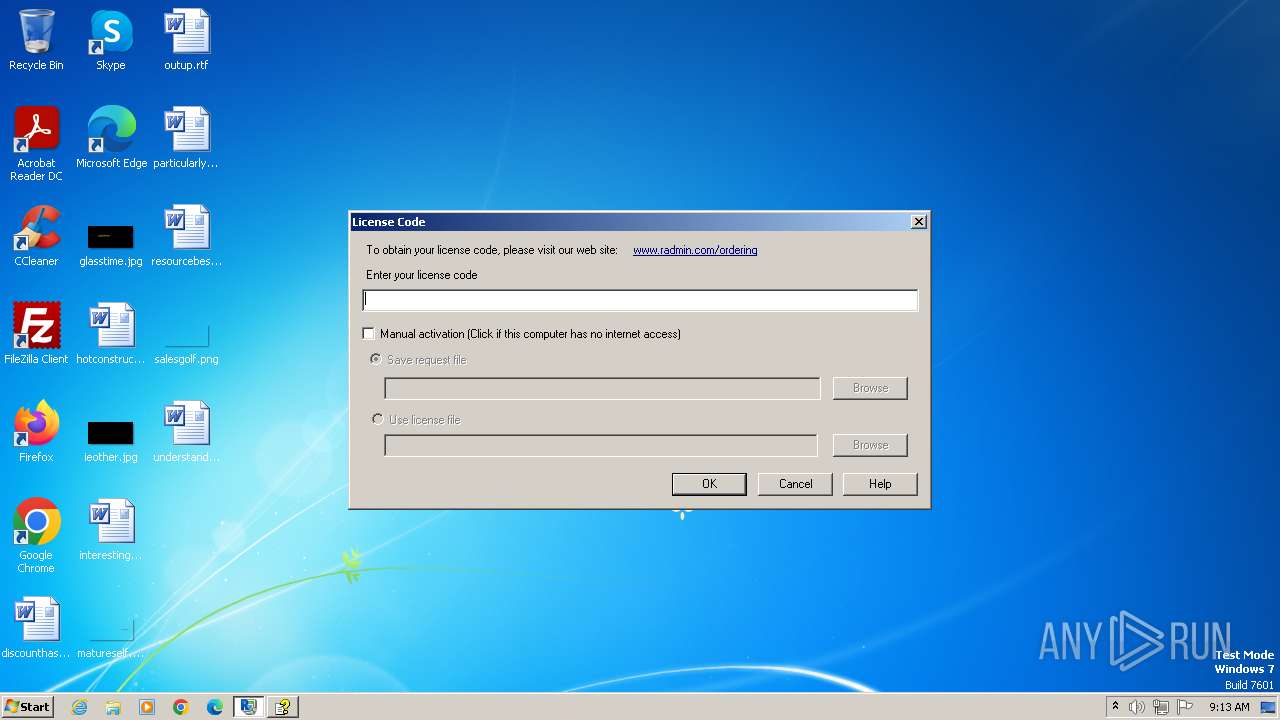
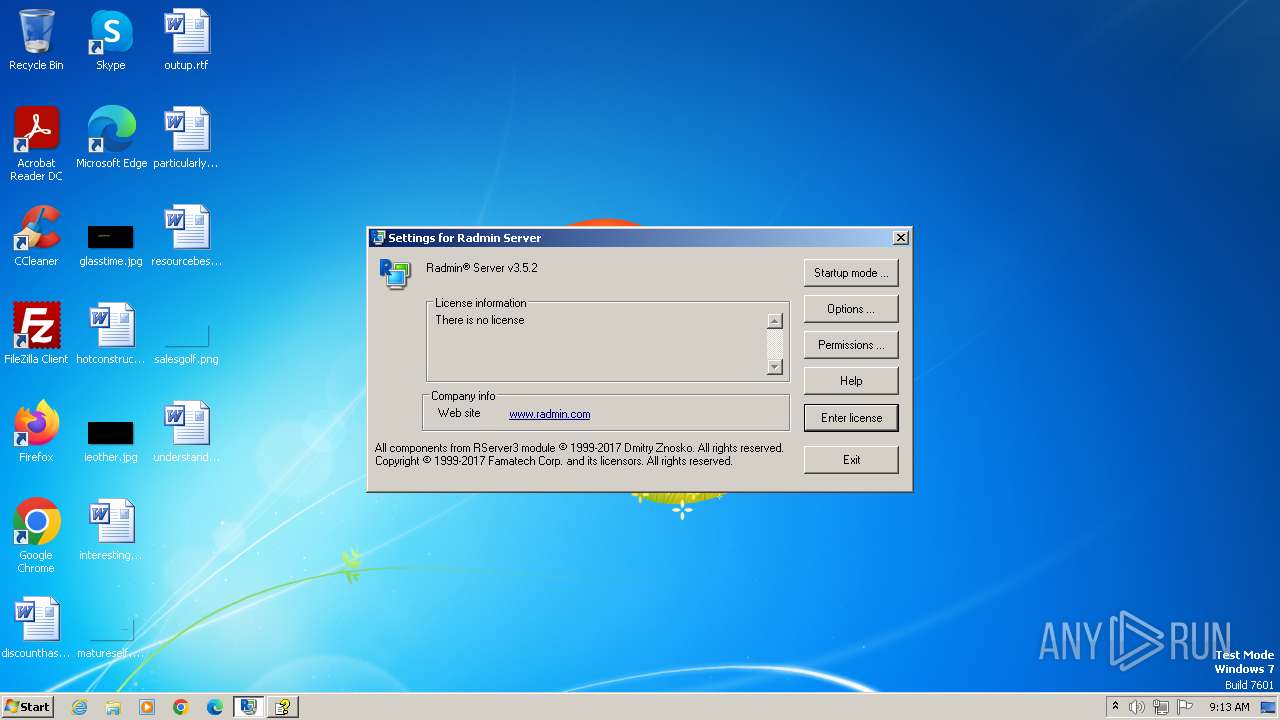
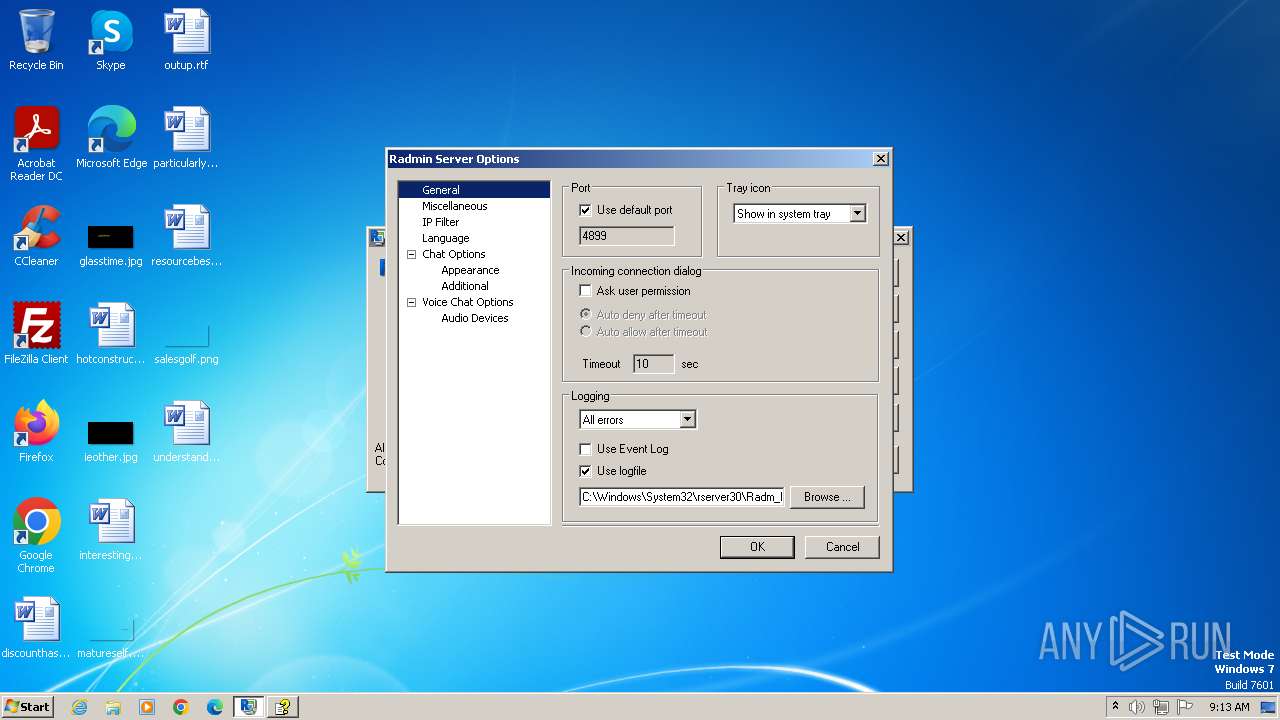
| File name: | Radmin_Server_3.5.2.1_EN.msi |
| Full analysis: | https://app.any.run/tasks/b7c8e7bd-b0d7-48a4-ba38-e44d2dea7e85 |
| Verdict: | Malicious activity |
| Analysis date: | March 15, 2024, 09:11:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 5.1, MSI Installer, Number of Characters: 0, Last Saved By: DavidHacker, Number of Words: 0, Title: Radmin Server 3.5.2 installation package, Comments: This installer contains the logic and data to install Radmin Server 3.5.2, Keywords: Installer,MSI,Database, Subject: Radmin Server 3.5.2, Author: Famatech, Security: 1, Number of Pages: 200, Name of Creating Application: InstallShield 12 - Professional Edition 12.0, Revision Number: {BBD285CD-D1FE-41B1-B6B4-7FF7C27F553B}, Last Saved Time/Date: Thu Dec 14 03:24:15 2017, Create Time/Date: Thu Dec 14 03:24:15 2017, Last Printed: Thu Dec 14 03:24:15 2017, Code page: 1252, Template: Intel;1033 |
| MD5: | A59832798A697BFE456B14F10E6ECCD4 |
| SHA1: | C81EFC67A52DDD207528AB4CE74C5D25B446B25E |
| SHA256: | 85844AE7394F2CF907B6378B415E77F7E29069C7E791598CF0985ADF4F53320E |
| SSDEEP: | 98304:ZISUrrdPPSbRNzlXrurlZJbEy61rS3ubYF0XUTchweB2OBCnMI2r7m2e0SZWw77B:ByOv7NBGcs |
MALICIOUS
Drops the executable file immediately after the start
- msiexec.exe (PID: 3500)
- drvinst.exe (PID: 1864)
- drvinst.exe (PID: 1892)
Creates a writable file in the system directory
- drvinst.exe (PID: 1864)
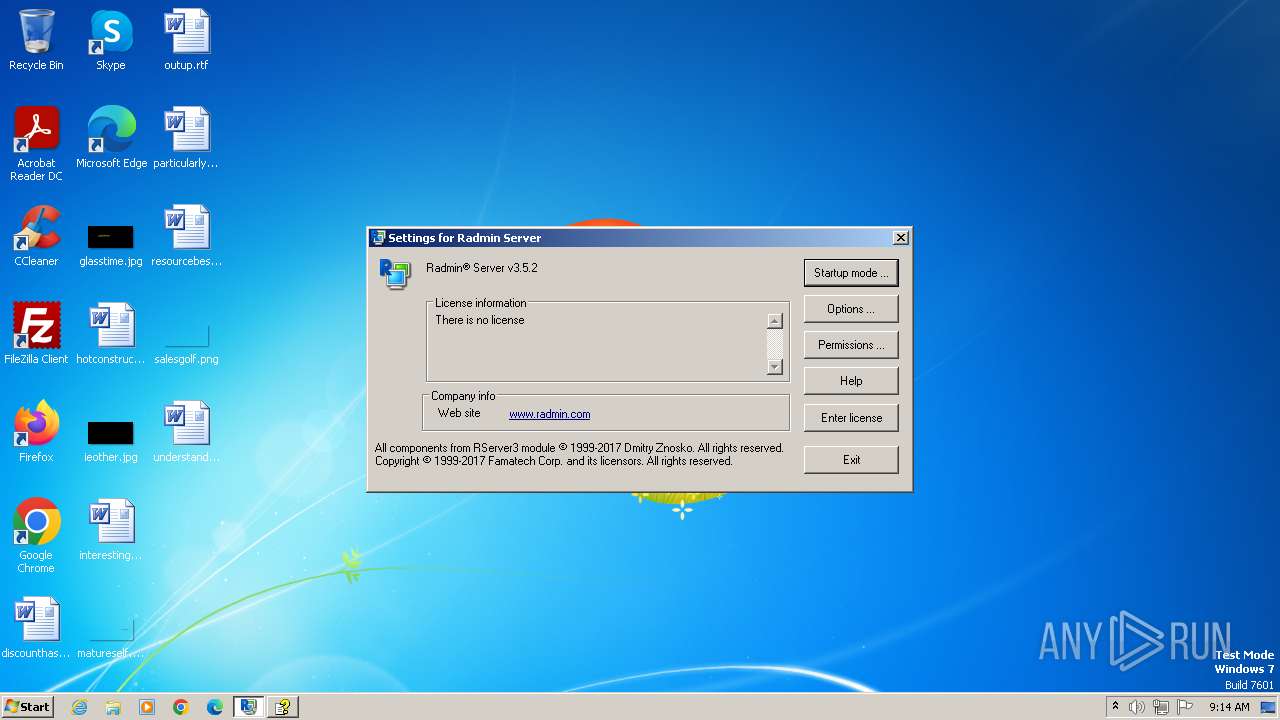
- rserver3.exe (PID: 2588)
- drvinst.exe (PID: 1892)
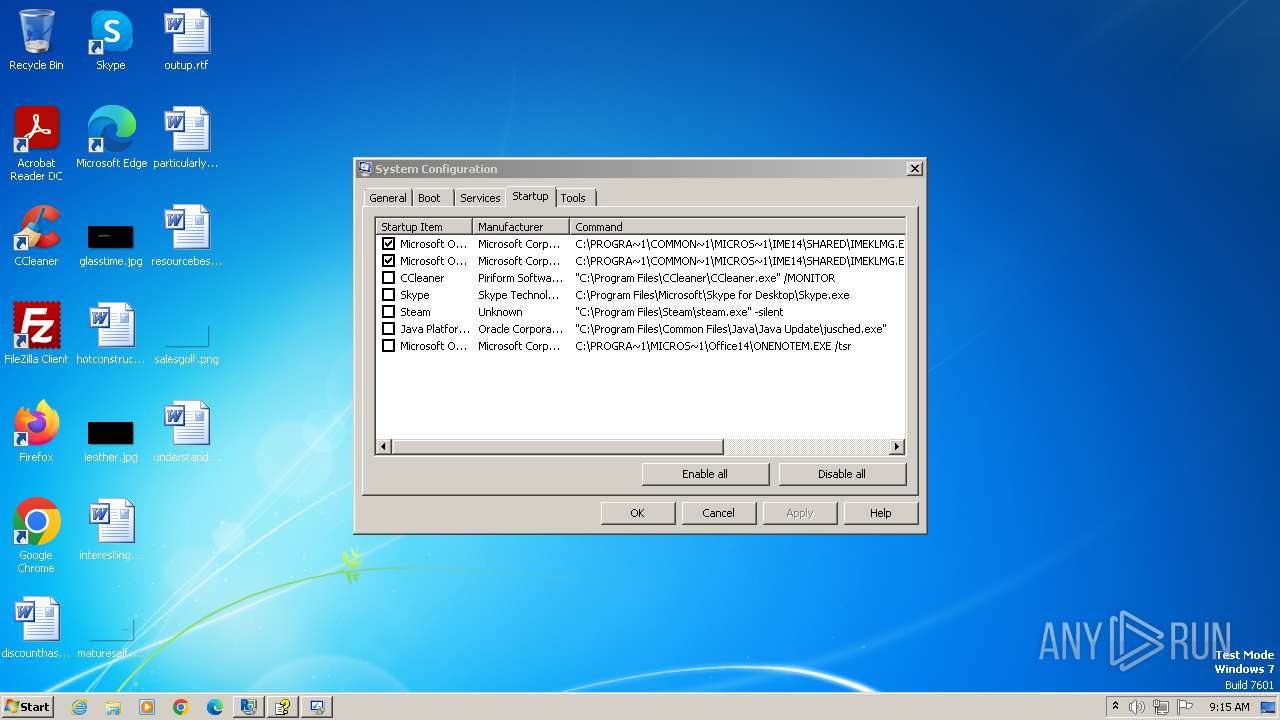
Changes the autorun value in the registry
- unregmp2.exe (PID: 3460)
- regsvr32.exe (PID: 3544)
Create files in the Startup directory
- regsvr32.exe (PID: 3544)
Steals credentials from Web Browsers
- setup.exe (PID: 3752)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- drvinst.exe (PID: 1864)
- drvinst.exe (PID: 1892)
Creates files in the driver directory
- drvinst.exe (PID: 1864)
- drvinst.exe (PID: 1892)
Checks Windows Trust Settings
- drvinst.exe (PID: 1864)
- drvinst.exe (PID: 1892)
Executable content was dropped or overwritten
- drvinst.exe (PID: 1864)
- drvinst.exe (PID: 1892)
Executes as Windows Service
- rserver3.exe (PID: 2588)
- VSSVC.exe (PID: 3996)
Application launched itself
- FamItrfc.Exe (PID: 920)
- FamItrfc.Exe (PID: 1644)
- FamItrfc.Exe (PID: 2420)
- ie4uinit.exe (PID: 3308)
- rundll32.exe (PID: 3352)
- setup.exe (PID: 3752)
- FamItrfc.Exe (PID: 1328)
Reads the Internet Settings
- rsl.exe (PID: 3272)
- rserver3.exe (PID: 1504)
- sipnotify.exe (PID: 1164)
- sipnotify.exe (PID: 3152)
- ie4uinit.exe (PID: 3308)
- hh.exe (PID: 3744)
- rundll32.exe (PID: 3352)
- rundll32.exe (PID: 3392)
- ie4uinit.exe (PID: 3448)
- ie4uinit.exe (PID: 3532)
Reads security settings of Internet Explorer
- rsl.exe (PID: 3272)
- rserver3.exe (PID: 1504)
Reads Microsoft Outlook installation path
- hh.exe (PID: 3744)
- ie4uinit.exe (PID: 3308)
Reads Internet Explorer settings
- hh.exe (PID: 3744)
- ie4uinit.exe (PID: 3308)
The process executes via Task Scheduler
- ctfmon.exe (PID: 1088)
- sipnotify.exe (PID: 1164)
- sipnotify.exe (PID: 3152)
Reads settings of System Certificates
- sipnotify.exe (PID: 1164)
- sipnotify.exe (PID: 3152)
Uses RUNDLL32.EXE to load library
- ie4uinit.exe (PID: 3308)
- rundll32.exe (PID: 3352)
Changes internet zones settings
- ie4uinit.exe (PID: 3308)
Write to the desktop.ini file (may be used to cloak folders)
- ie4uinit.exe (PID: 3308)
- unregmp2.exe (PID: 3460)
- regsvr32.exe (PID: 3544)
Changes default file association
- unregmp2.exe (PID: 3460)
INFO
Reads the software policy settings
- msiexec.exe (PID: 3500)
- drvinst.exe (PID: 1864)
- drvinst.exe (PID: 1892)
- sipnotify.exe (PID: 1164)
- sipnotify.exe (PID: 3152)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 3500)
- hh.exe (PID: 3744)
- sipnotify.exe (PID: 1164)
- ie4uinit.exe (PID: 3308)
- sipnotify.exe (PID: 3152)
Reads the machine GUID from the registry
- drvinst.exe (PID: 1864)
- drvinst.exe (PID: 1892)
- rserver3.exe (PID: 2588)
- rserver3.exe (PID: 1504)
- hh.exe (PID: 3744)
Reads the computer name
- drvinst.exe (PID: 1864)
- drvinst.exe (PID: 1892)
- rserver3.exe (PID: 2588)
- FamItrfc.Exe (PID: 920)
- rsl.exe (PID: 3272)
- FamItrfc.Exe (PID: 2748)
- rserver3.exe (PID: 1504)
- FamItrfc.Exe (PID: 1368)
- FamItrfc.Exe (PID: 1236)
- FamItrfc.Exe (PID: 1644)
- FamItrfc.Exe (PID: 1472)
- IMEKLMG.EXE (PID: 2260)
- IMEKLMG.EXE (PID: 2276)
- FamItrfc.Exe (PID: 2420)
- FamItrfc.Exe (PID: 2464)
- wmpnscfg.exe (PID: 2624)
- FamItrfc.Exe (PID: 2920)
- wmpnscfg.exe (PID: 2668)
- wmpnscfg.exe (PID: 3472)
- setup.exe (PID: 3760)
- setup.exe (PID: 3800)
- IMEKLMG.EXE (PID: 3924)
- IMEKLMG.EXE (PID: 3932)
- FamItrfc.Exe (PID: 1328)
- wmpnscfg.exe (PID: 2944)
- FamItrfc.Exe (PID: 1472)
- wmpnscfg.exe (PID: 188)
Checks supported languages
- drvinst.exe (PID: 1892)
- FamItrfc.Exe (PID: 920)
- rserver3.exe (PID: 2588)
- rsl.exe (PID: 3272)
- FamItrfc.Exe (PID: 2748)
- rserver3.exe (PID: 1504)
- drvinst.exe (PID: 1864)
- FamItrfc.Exe (PID: 3684)
- FamItrfc.Exe (PID: 3068)
- FamItrfc.Exe (PID: 1492)
- FamItrfc.Exe (PID: 2148)
- FamItrfc.Exe (PID: 1644)
- FamItrfc.Exe (PID: 1740)
- FamItrfc.Exe (PID: 1368)
- FamItrfc.Exe (PID: 1236)
- FamItrfc.Exe (PID: 1472)
- IMEKLMG.EXE (PID: 2260)
- IMEKLMG.EXE (PID: 2276)
- FamItrfc.Exe (PID: 2420)
- FamItrfc.Exe (PID: 2464)
- wmpnscfg.exe (PID: 2668)
- wmpnscfg.exe (PID: 2624)
- FamItrfc.Exe (PID: 2920)
- wmpnscfg.exe (PID: 3472)
- setup.exe (PID: 3752)
- setup.exe (PID: 3760)
- setup.exe (PID: 3800)
- IMEKLMG.EXE (PID: 3924)
- IMEKLMG.EXE (PID: 3932)
- IMKRMIG.EXE (PID: 3964)
- FamItrfc.Exe (PID: 1328)
- FamItrfc.Exe (PID: 1472)
- wmpnscfg.exe (PID: 2944)
- wmpnscfg.exe (PID: 188)
Creates files in the program directory
- hh.exe (PID: 3744)
- chrmstp.exe (PID: 3600)
- setup.exe (PID: 3752)
- setup.exe (PID: 3760)
- setup.exe (PID: 3800)
- ie4uinit.exe (PID: 3308)
- chrmstp.exe (PID: 3648)
Create files in a temporary directory
- hh.exe (PID: 3744)
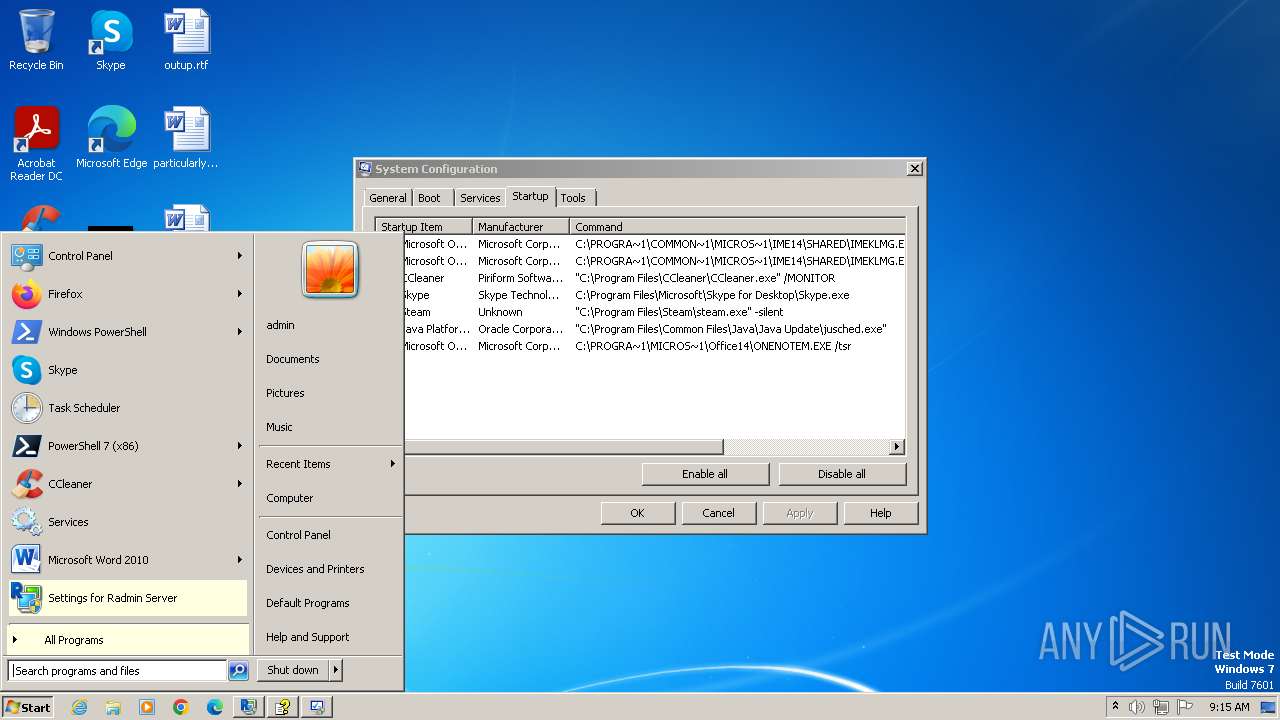
Manual execution by a user
- msconfig.exe (PID: 4020)
- msconfig.exe (PID: 392)
- IMEKLMG.EXE (PID: 2260)
- IMEKLMG.EXE (PID: 2276)
- wmpnscfg.exe (PID: 2624)
- wmpnscfg.exe (PID: 2668)
- ie4uinit.exe (PID: 3308)
- ie4uinit.exe (PID: 3448)
- unregmp2.exe (PID: 3460)
- wmpnscfg.exe (PID: 3472)
- ie4uinit.exe (PID: 3532)
- regsvr32.exe (PID: 3544)
- chrmstp.exe (PID: 3600)
- setup.exe (PID: 3752)
- IMEKLMG.EXE (PID: 3924)
- IMEKLMG.EXE (PID: 3932)
- wmpnscfg.exe (PID: 2944)
- wmpnscfg.exe (PID: 188)
Executable content was dropped or overwritten
- msiexec.exe (PID: 3500)
Checks proxy server information
- hh.exe (PID: 3744)
Creates files or folders in the user directory
- hh.exe (PID: 3744)
Process checks whether UAC notifications are on
- IMEKLMG.EXE (PID: 2260)
- IMEKLMG.EXE (PID: 2276)
- IMEKLMG.EXE (PID: 3924)
- IMEKLMG.EXE (PID: 3932)
Application launched itself
- chrmstp.exe (PID: 3600)
- chrmstp.exe (PID: 3648)
- msedge.exe (PID: 3824)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (88.6) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (10) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| Characters: | - |
|---|---|
| LastModifiedBy: | DavidHacker |
| Words: | - |
| Title: | Radmin Server 3.5.2 installation package |
| Comments: | This installer contains the logic and data to install Radmin Server 3.5.2 |
| Keywords: | Installer,MSI,Database |
| Subject: | Radmin Server 3.5.2 |
| Author: | Famatech |
| Security: | Password protected |
| Pages: | 200 |
| Software: | InstallShield? 12 - Professional Edition 12.0 |
| RevisionNumber: | {BBD285CD-D1FE-41B1-B6B4-7FF7C27F553B} |
| ModifyDate: | 2017:12:14 03:24:15 |
| CreateDate: | 2017:12:14 03:24:15 |
| LastPrinted: | 2017:12:14 03:24:15 |
| CodePage: | Windows Latin 1 (Western European) |
| Template: | Intel;1033 |
Total processes
174
Monitored processes
62
Malicious processes
7
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 392 | "C:\Windows\system32\msconfig.exe" | C:\Windows\System32\msconfig.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: System Configuration Utility Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 920 | "C:\Windows\system32\rserver30\FamItrfc.Exe" | C:\Windows\System32\rserver30\FamItrfc.Exe | — | rserver3.exe | |||||||||||
User: SYSTEM Company: Famatech Corp. Integrity Level: SYSTEM Description: Radmin component Exit code: 1073807364 Version: 3,5,2,1205 Modules
| |||||||||||||||
| 1080 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1468 --field-trial-handle=908,i,14760849931976874505,6484823416367338163,131072 /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1084 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1272 --field-trial-handle=908,i,14760849931976874505,6484823416367338163,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1088 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1164 | C:\Windows\system32\sipnotify.exe -LogonOrUnlock | C:\Windows\System32\sipnotify.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: sipnotify Exit code: 0 Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) Modules
| |||||||||||||||
| 1236 | "C:\Windows\system32\rserver30\FamItrfc.Exe" | C:\Windows\System32\rserver30\FamItrfc.Exe | — | rserver3.exe | |||||||||||
User: SYSTEM Company: Famatech Corp. Integrity Level: SYSTEM Description: Radmin component Exit code: 0 Version: 3,5,2,1205 Modules
| |||||||||||||||
| 1328 | "C:\Windows\system32\rserver30\FamItrfc.Exe" | C:\Windows\System32\rserver30\FamItrfc.Exe | — | rserver3.exe | |||||||||||
User: SYSTEM Company: Famatech Corp. Integrity Level: SYSTEM Description: Radmin component Exit code: 0 Version: 3,5,2,1205 Modules
| |||||||||||||||
| 1368 | "C:\Windows\system32\rserver30\FamItrfc.Exe" | C:\Windows\System32\rserver30\FamItrfc.Exe | — | FamItrfc.Exe | |||||||||||
User: admin Company: Famatech Corp. Integrity Level: MEDIUM Description: Radmin component Exit code: 0 Version: 3,5,2,1205 Modules
| |||||||||||||||
Total events
36 910
Read events
35 282
Write events
1 421
Delete events
207
Modification events
| (PID) Process: | (3500) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3996) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000DE7A7AD0B876DA019C0F0000E80A0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3996) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000DE7A7AD0B876DA019C0F00004C0B0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3996) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000DE7A7AD0B876DA019C0F0000D0080000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3996) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000DE7A7AD0B876DA019C0F000068090000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3996) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 400000000000000038DD7CD0B876DA019C0F000068090000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3996) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 400000000000000038DD7CD0B876DA019C0F0000D0080000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3996) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 4000000000000000923F7FD0B876DA019C0F0000E80A0000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3996) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 4000000000000000923F7FD0B876DA019C0F00004C0B0000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3996) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SwProvider_{b5946137-7b9f-4925-af80-51abd60b20d5} |
| Operation: | write | Name: | PROVIDER_BEGINPREPARE (Enter) |
Value: 400000000000000072DD22D2B876DA019C0F00004C0B00000104000001000000000000000000000019F0D9A5CE7BF74A82A08D4CBAAEB3780000000000000000 | |||
Executable files
17
Suspicious files
53
Text files
91
Unknown types
22
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1864 | drvinst.exe | C:\Windows\System32\DriverStore\Temp\{1363f27e-3f27-7435-ec6b-13033933163b}\SET64C1.tmp | cat | |
MD5:ADC6697619202B12AFE849297733AD35 | SHA256:127272F97A2C62977151FC80F10017BABFBFB190640287CBF70C6118B556040C | |||
| 1864 | drvinst.exe | C:\Windows\System32\DriverStore\Temp\{1363f27e-3f27-7435-ec6b-13033933163b}\mirrorv3.dll | executable | |
MD5:B14024B1D0CC7B53717A565BCA51C40D | SHA256:608153CDE7D5CF9B867D316DFD2265207CD7907260976780F59A807A82CF8199 | |||
| 1864 | drvinst.exe | C:\Windows\System32\DriverStore\Temp\{1363f27e-3f27-7435-ec6b-13033933163b}\rminiv3.sys | executable | |
MD5:D96EA49AB9A9174331BC023FD0CADC18 | SHA256:E9A46BE19DB6BBF2CC7D049F275434242A58E77EEB55DEE6A0E25F39258CEFBD | |||
| 1864 | drvinst.exe | C:\Windows\System32\DriverStore\INFCACHE.2 | binary | |
MD5:ABB638661D737D9457D78D28C4145066 | SHA256:7602F549ABBAC7DE5CD8125329869D02A0C82AA8C9AAF78011162175AA319261 | |||
| 1864 | drvinst.exe | C:\Windows\System32\DriverStore\Temp\{1363f27e-3f27-7435-ec6b-13033933163b}\SET64E2.tmp | binary | |
MD5:52345B1A54E39791BB75B68305D3B47A | SHA256:8437BFBA6F39A70299120BCEB26CE7D2A565626A1548ED2FC3DF70847B39D538 | |||
| 1864 | drvinst.exe | C:\Windows\System32\DriverStore\Temp\{1363f27e-3f27-7435-ec6b-13033933163b}\SET64D1.tmp | executable | |
MD5:B14024B1D0CC7B53717A565BCA51C40D | SHA256:608153CDE7D5CF9B867D316DFD2265207CD7907260976780F59A807A82CF8199 | |||
| 3500 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI28D0.tmp | executable | |
MD5:4A908EE9C6F2F4AAD63382CCCEE731E4 | SHA256:459F503FB8B4FC4A600261430AC77BF70118D41FA19F7B2620D43BA6E9C8FA5E | |||
| 1864 | drvinst.exe | C:\Windows\System32\DriverStore\infpub.dat | binary | |
MD5:BB235CEEC30C639BBA255C20CE9C7CBC | SHA256:DDD5B8FA2DBA93E89540276D95B2D5B444EC2ECC15811D369B3808B915ECC6E7 | |||
| 1892 | drvinst.exe | C:\Windows\INF\setupapi.ev1 | binary | |
MD5:C85C4D65C8827DC0BF8FC2F71F175FE6 | SHA256:31D21863F3EC6E9027C6B783F3E6626DECC99442AAE61BEDB5B796DBB1636B83 | |||
| 1864 | drvinst.exe | C:\Windows\System32\DriverStore\infstor.dat | binary | |
MD5:E3A1F96C7F8B2348B3F4E4942F04DA2E | SHA256:F22AEF797AD3F4B645AEE647424B6C7395E6B3F1EA395015653E9550AB4DE7BD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
13
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1164 | sipnotify.exe | HEAD | 200 | 88.221.61.151:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133549677509370000 | unknown | — | — | unknown |
3152 | sipnotify.exe | HEAD | 200 | 23.192.244.236:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133549677755750000 | unknown | — | — | unknown |
3152 | sipnotify.exe | GET | 200 | 23.192.244.236:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133549677755750000 | unknown | compressed | 78.4 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1124 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1164 | sipnotify.exe | 88.221.61.151:80 | query.prod.cms.rt.microsoft.com | AKAMAI-AS | DE | unknown |
3152 | sipnotify.exe | 23.192.244.236:80 | query.prod.cms.rt.microsoft.com | AKAMAI-AS | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
query.prod.cms.rt.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
rserver3.exe | %n%n%n%n%n%n%n%n%n |
rserver3.exe | %n%n%n%n%n%n%n%n%n |