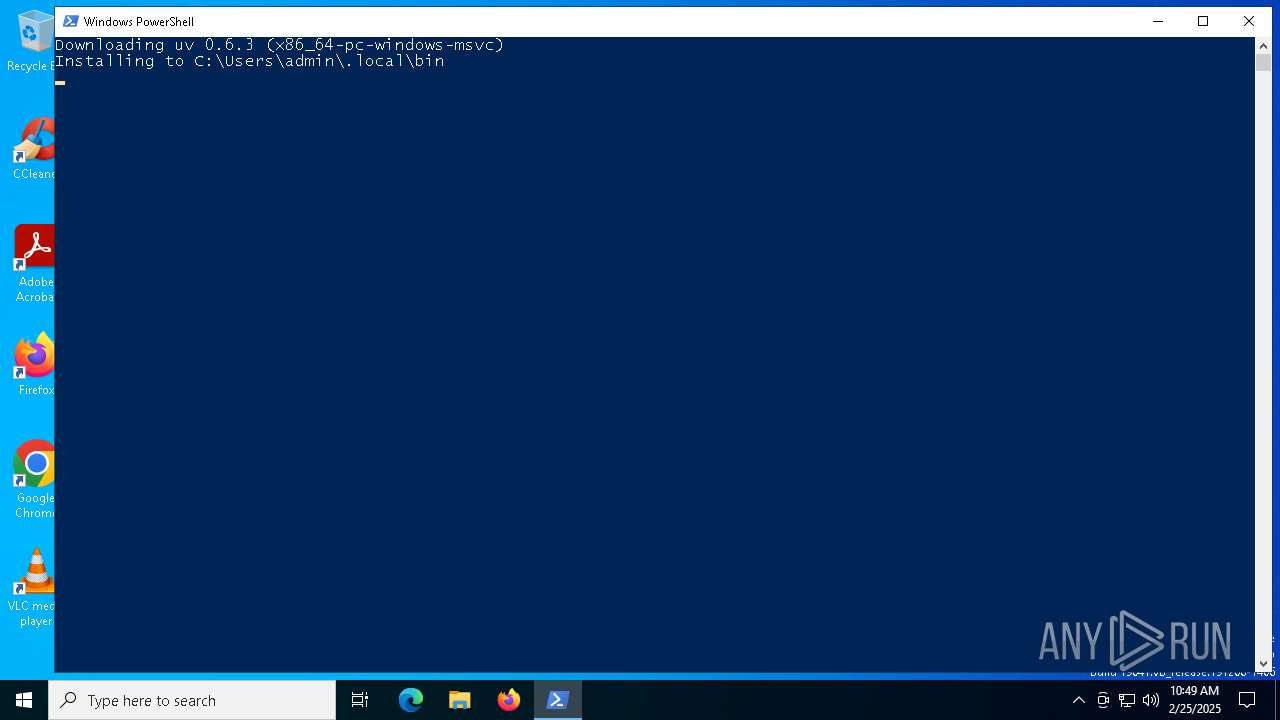
| download: | /uv/install.ps1 |
| Full analysis: | https://app.any.run/tasks/e89a56a3-f8c9-4e02-9dcc-f954136d4941 |
| Verdict: | Malicious activity |
| Analysis date: | February 25, 2025, 10:49:38 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines (367) |
| MD5: | 2C589C40DD560034124997E9656BCBCF |
| SHA1: | 550B15396226DE36972B8C5C7EDB4C911DD71C5A |
| SHA256: | 85818C4BD40FE1F06476232CE11C7F76E0223EB5D3BBB6575E6A836558EE85D4 |
| SSDEEP: | 384:xMManH74vczieoWPJdTRBfMdP4h/b9GiQY:xMMyH7icloGHVBfMdP4h/b9GiQY |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 6256)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 6256)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 6256)
SUSPICIOUS
Gets file extension (POWERSHELL)
- powershell.exe (PID: 6256)
Creates new GUID (POWERSHELL)
- powershell.exe (PID: 6256)
Executable content was dropped or overwritten
- powershell.exe (PID: 6256)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 6256)
INFO
Checks proxy server information
- powershell.exe (PID: 6256)
- BackgroundTransferHost.exe (PID: 6048)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 6048)
- BackgroundTransferHost.exe (PID: 5972)
- BackgroundTransferHost.exe (PID: 2124)
- BackgroundTransferHost.exe (PID: 6800)
- BackgroundTransferHost.exe (PID: 2148)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6256)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 6256)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 6048)
- uv.exe (PID: 872)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 6048)
- slui.exe (PID: 4464)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 6256)
Manual execution by a user
- uv.exe (PID: 1276)
- uvx.exe (PID: 6988)
- uv.exe (PID: 4304)
- uvx.exe (PID: 6048)
- uv.exe (PID: 6632)
- uvx.exe (PID: 5364)
Checks supported languages
- uv.exe (PID: 6632)
- uvx.exe (PID: 6988)
Disables trace logs
- powershell.exe (PID: 6256)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
163
Monitored processes
26
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
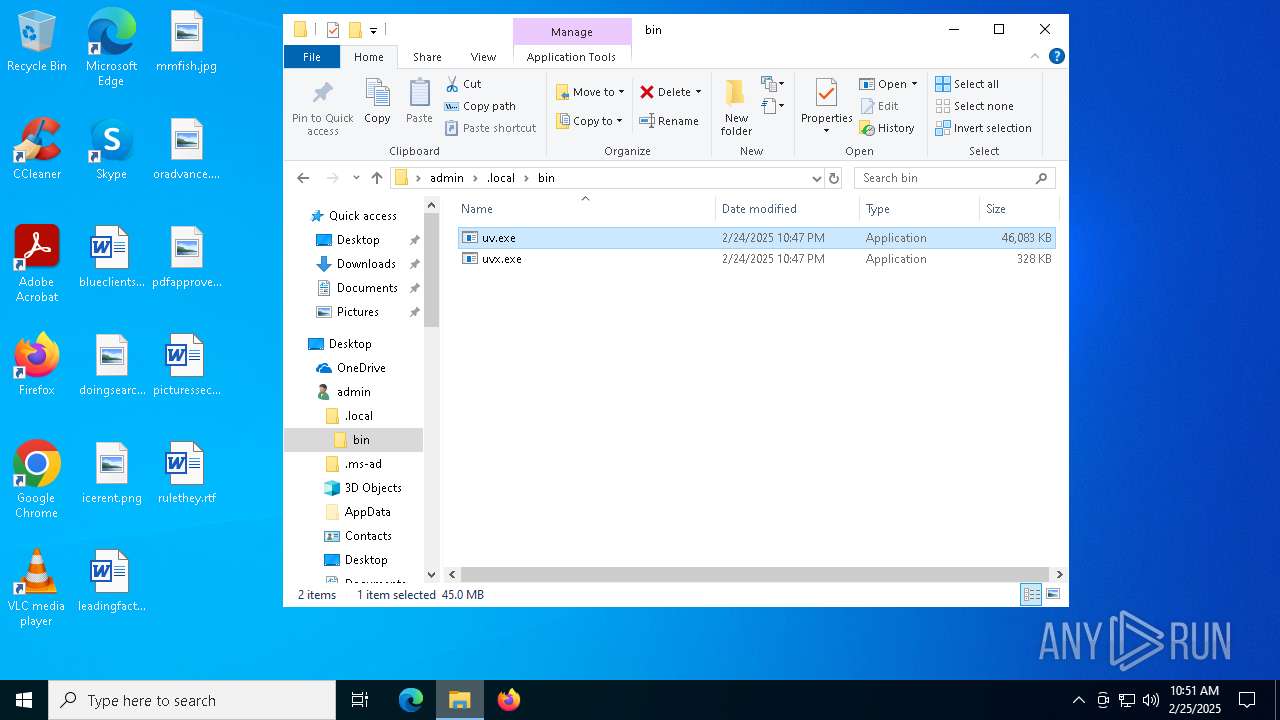
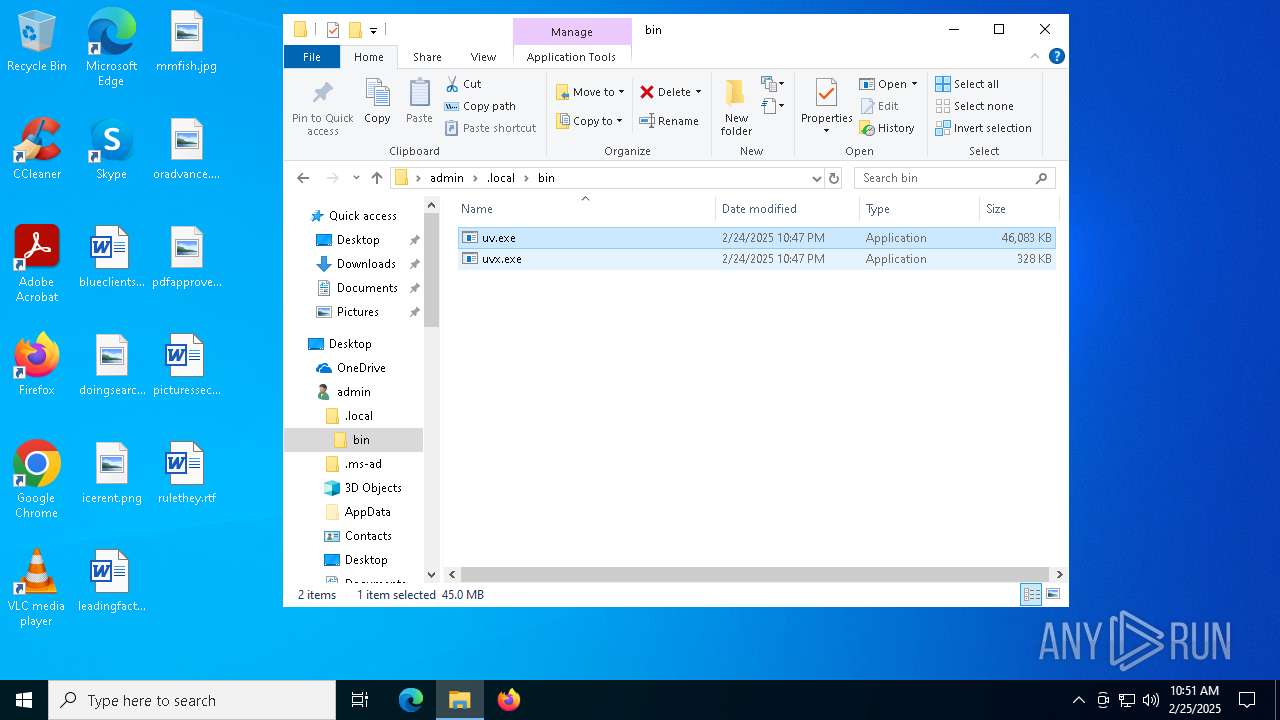
| 872 | "C:\Users\admin\.local\bin\uv.exe" tool uvx | C:\Users\admin\.local\bin\uv.exe | — | uvx.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 2 Modules
| |||||||||||||||
| 1276 | "C:\Users\admin\.local\bin\uv.exe" | C:\Users\admin\.local\bin\uv.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 2 Modules
| |||||||||||||||
| 2124 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2148 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4180 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4304 | "C:\Users\admin\.local\bin\uv.exe" | C:\Users\admin\.local\bin\uv.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 2 Modules
| |||||||||||||||
| 4444 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | uvx.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4464 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4880 | "C:\Users\admin\.local\bin\uv.exe" tool uvx | C:\Users\admin\.local\bin\uv.exe | — | uvx.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 2 Modules
| |||||||||||||||
| 4976 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | uv.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
9 816
Read events
9 798
Write events
17
Delete events
1
Modification events
| (PID) Process: | (2148) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2148) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2148) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6048) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6048) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6048) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6256) powershell.exe | Key: | HKEY_CURRENT_USER\Environment |
| Operation: | delete value | Name: | cargo-dist-01226a75-95c8-4ef8-a297-f340ab47ff8c |
Value: cargo-dist-dummy | |||
| (PID) Process: | (6256) powershell.exe | Key: | HKEY_CURRENT_USER\Environment |
| Operation: | write | Name: | Path |
Value: C:\Users\admin\.local\bin;%USERPROFILE%\AppData\Local\Microsoft\WindowsApps | |||
| (PID) Process: | (6256) powershell.exe | Key: | HKEY_CURRENT_USER\Environment |
| Operation: | write | Name: | cargo-dist-01226a75-95c8-4ef8-a297-f340ab47ff8c |
Value: cargo-dist-dummy | |||
| (PID) Process: | (5972) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
2
Suspicious files
12
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6256 | powershell.exe | C:\Users\admin\AppData\Local\Temp\2d03a4bd-2d6f-4e97-992e-91ed9d8a6e92\uv.exe | — | |
MD5:— | SHA256:— | |||
| 6048 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\8ae8478b-1da7-4c84-9306-aacfd395d842.down_data | — | |
MD5:— | SHA256:— | |||
| 6256 | powershell.exe | C:\Users\admin\.local\bin\uv.exe | — | |
MD5:— | SHA256:— | |||
| 6048 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:8DDD7C6D4A3AB775235E44297C251885 | SHA256:9AB98597EE66662FE13E1D1ABDFA73756608C345060DA9D7842C851EDE3D7992 | |||
| 6256 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\Y4JYH85Z1KM466N3LJ80.temp | binary | |
MD5:7D8C5B7CAA67FA8BEE4BED4B43FF5A66 | SHA256:4DB3ABCEFA1F40C17ECBA06C11E3D155B12B614F508186E06A770410B4C89781 | |||
| 6256 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_lpkp2glc.ekl.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6048 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\8ae8478b-1da7-4c84-9306-aacfd395d842.50c1fcb7-9c16-4fbd-ba44-04fa1e03a6f9.down_meta | binary | |
MD5:0540D4044F050B5E1782D56796D71C1F | SHA256:AD1930FC769107A89FC15A5A9F80D82645AEECBF317794D6A8CB20C15E179526 | |||
| 6256 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_idgd4iby.yzw.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6048 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:C480F7EE8D0EF449152C05F32CF1E55D | SHA256:CDDED1D495E52C3F6839882F44D5F121E4E561E15BFB5CA5257B7C05C11EE3A9 | |||
| 6256 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF127bef.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
39
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6388 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6388 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6048 | BackgroundTransferHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6080 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2088 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2740 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6256 | powershell.exe | 104.21.68.235:443 | astral.sh | CLOUDFLARENET | — | unknown |
6256 | powershell.exe | 140.82.121.4:443 | github.com | GITHUB | US | whitelisted |
6256 | powershell.exe | 185.199.108.133:443 | objects.githubusercontent.com | FASTLY | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
astral.sh |
| unknown |
github.com |
| whitelisted |
objects.githubusercontent.com |
| whitelisted |
login.live.com |
| whitelisted |
www.bing.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |