| download: | Brothers_Dead_Sexy_Girlfriend_Tease_me_for_a_Long_Time.html |
| Full analysis: | https://app.any.run/tasks/66ea790e-47d0-4fc6-8e78-3eb37811b6e2 |
| Verdict: | Malicious activity |
| Analysis date: | July 04, 2018, 12:33:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, ASCII text, with very long lines, with CRLF, LF line terminators |
| MD5: | DB9262ADCA5EE2A4584F99F3BD3B1AF1 |
| SHA1: | D213B4B7636B5045580F86ED8803858F9772B85B |
| SHA256: | 856AD54053D1FBCCCF0EF71BB0D53DFBA786328E2078F9D8F23FEFC1EEE9A2E9 |
| SSDEEP: | 1536:TYWw9+OUMxR9Vxl9Sxr9wxy99xi99xZ9rxc9Qxh93x19qx69Lx09qxM93xgte9GR:TYWw9dUyv |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
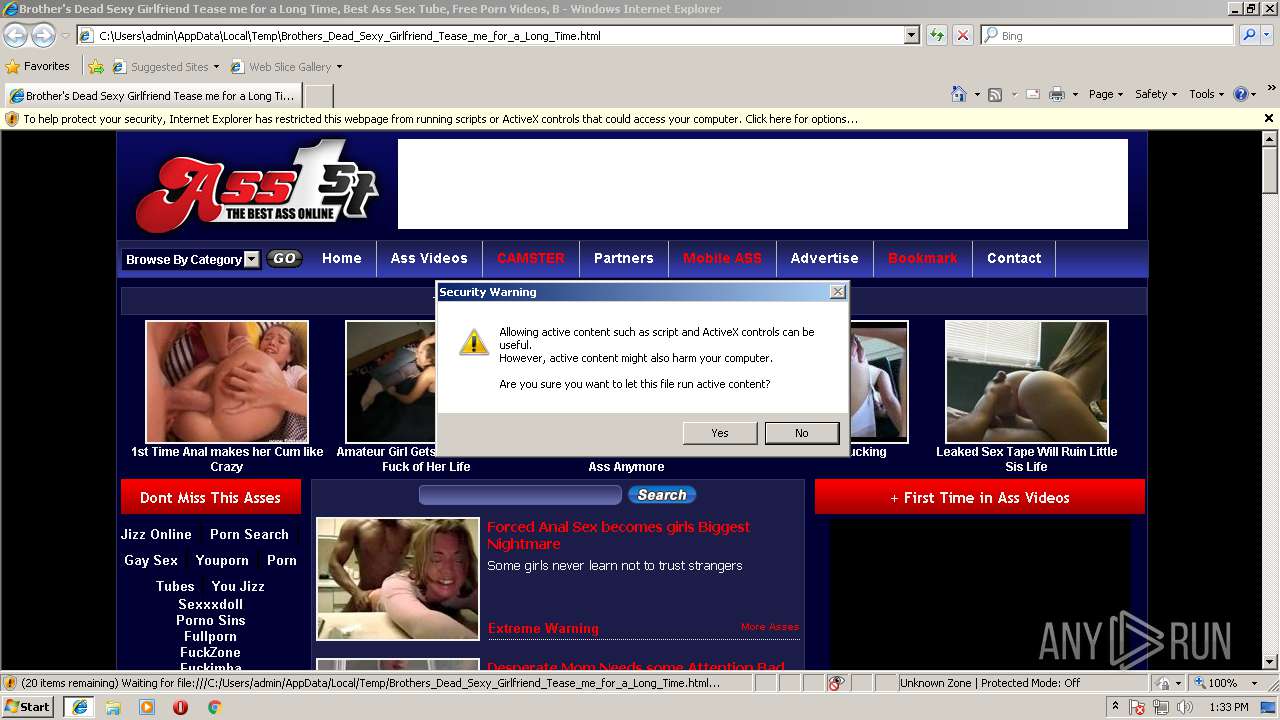
Application launched itself
- iexplore.exe (PID: 1360)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2480)
Changes settings of System certificates
- iexplore.exe (PID: 2480)
Creates files in the user directory
- iexplore.exe (PID: 2480)
Changes internet zones settings
- iexplore.exe (PID: 1360)
Reads internet explorer settings
- iexplore.exe (PID: 2480)
Dropped object may contain URL's
- iexplore.exe (PID: 2480)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .htm/html | | | HyperText Markup Language with DOCTYPE (80.6) |
|---|---|---|
| .html | | | HyperText Markup Language (19.3) |
EXIF
HTML
| ContentType: | text/html; charset=iso-8859-1 |
|---|---|
| Title: | Brother's Dead Sexy Girlfriend Tease me for a Long Time, Best Ass Sex Tube, Free Porn Videos, Big Black Hot Ass |
| Description: | Free Porn Videos, Brother's Dead Sexy Girlfriend Tease me for a Long Time, She entered naked in my room and fuck my brain out that I didn't know where I am, Free Teen Asses, Ass Sex Tube, Black Nice Ass Fucking, Hot Ass Video, Best Porn Asses, Big Black ASS, Free Tube Ass, Teen Hot Ass, First time Ass at Ass1st |
| Rating: | RTA-5042-1996-1400-1577-RTA |
| Keywords: | big,boobs,brother,dead,fuck,girlfriend,hot,long,sexy,tease, ass, asses, big ass, hot ass, black ass, best ass, nice ass, teen ass big hot ass, ass porn, ass tube, ass sex |
| RevisitAfter: | 1 days |
| Robots: | all |
| googleSiteVerification: | QdwCNonoqDDT8PakNOuIheaIIg_2pNnnBiT1eFeEP4Y |
Total processes
34
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1360 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\AppData\Local\Temp\Brothers_Dead_Sexy_Girlfriend_Tease_me_for_a_Long_Time.html | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2480 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1360 CREDAT:79873 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
401
Read events
313
Write events
86
Delete events
2
Modification events
| (PID) Process: | (1360) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1360) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1360) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (1360) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (1360) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (1360) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000070000000010000000000000000000000000000000000000000000000400C35B347C7D301000000000000000000000000020000001700000000000000FE80000000000000D45917EAB3ED3D860B000000000000001700000000000000FE80000000000000D45917EAB3ED3D860B000000000000001C00000000000000000000000000000000000000000000000000000000000000170000000000000000000000000000000000FFFFC0A8640B000000000000000002000000C0A801640000000000000000000000000000000000000000000000000C00000C37D0000010A73800D8703600000000000000000000000000000000000000000000000000000000000000000000000000000000000000000081F800009000230090002300380023000000000000702C000A00000000000000F8412C00 | |||
| (PID) Process: | (1360) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {77A5753F-7F86-11E8-B27F-5254004AAD21} |
Value: 0 | |||
| (PID) Process: | (1360) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (1360) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 5 | |||
| (PID) Process: | (1360) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E2070700030004000C0021002300D902 | |||
Executable files
0
Suspicious files
0
Text files
77
Unknown types
43
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1360 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2LKO8ICX\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 1360 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2480 | iexplore.exe | C:\Users\admin\AppData\Roaming\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\settings.sxx | — | |
MD5:— | SHA256:— | |||
| 2480 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LM4BD81N\pro728[1].php | — | |
MD5:— | SHA256:— | |||
| 2480 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\admin@statcounter[1].txt | — | |
MD5:— | SHA256:— | |||
| 2480 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2LKO8ICX\21i7p6g[1].jpg | image | |
MD5:— | SHA256:— | |||
| 2480 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\BCPS3ZPQ\floater[1].js | html | |
MD5:— | SHA256:— | |||
| 2480 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\OP5DQHUV\cr647rz[1].jpg | image | |
MD5:— | SHA256:— | |||
| 2480 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LM4BD81N\prxcno2[1].jpg | image | |
MD5:— | SHA256:— | |||
| 2480 | iexplore.exe | C:\Users\admin\AppData\Roaming\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\settings.sol | sol | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
138
TCP/UDP connections
30
DNS requests
14
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2480 | iexplore.exe | GET | — | 66.254.100.195:80 | http://ads.mofos.com/ads/mofos_inserts/index472.php?nats=NDAwMDg3OC4xLjIxLjc3LjUuNzE2MC4wLjAuMA | US | — | — | unknown |
2480 | iexplore.exe | GET | — | 172.217.22.110:80 | http://www.google-analytics.com/urchin.js | US | — | — | whitelisted |
2480 | iexplore.exe | GET | 200 | 107.191.33.74:80 | http://www.ass1st.com/webmasters/mootools.svn.js | US | text | 179 Kb | suspicious |
2480 | iexplore.exe | GET | 200 | 107.191.33.74:80 | http://www.ass1st.com/floater.js | US | html | 5.30 Kb | suspicious |
2480 | iexplore.exe | GET | 200 | 107.191.33.74:80 | http://www.ass1st.com/thumbs/21i7p6g.jpg | US | image | 12.3 Kb | suspicious |
2480 | iexplore.exe | GET | 200 | 107.191.33.74:80 | http://www.ass1st.com/thumbs/cr647rz.jpg | US | image | 3.96 Kb | suspicious |
2480 | iexplore.exe | GET | 200 | 107.191.33.74:80 | http://www.ass1st.com/thumbs/xe8pll5.jpg | US | image | 13.2 Kb | suspicious |
2480 | iexplore.exe | GET | 200 | 107.191.33.74:80 | http://www.ass1st.com/styles/a1st-theme.css | US | text | 3.62 Kb | suspicious |
2480 | iexplore.exe | GET | 200 | 107.191.33.74:80 | http://www.ass1st.com/thumbs/2014/01/prxcno2.jpg | US | image | 4.14 Kb | suspicious |
2480 | iexplore.exe | GET | 200 | 107.191.33.74:80 | http://www.ass1st.com/thumbs/5ypwplp.jpg | US | image | 5.46 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2480 | iexplore.exe | 107.191.33.74:80 | www.ass1st.com | Choopa, LLC | US | suspicious |
1360 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2480 | iexplore.exe | 104.20.208.59:443 | coinhive.com | Cloudflare Inc | US | shared |
2480 | iexplore.exe | 66.254.100.195:80 | ads.mofos.com | Reflected Networks, Inc. | US | unknown |
2480 | iexplore.exe | 54.208.99.166:80 | adcode.adengage.com | Amazon.com, Inc. | US | unknown |
2480 | iexplore.exe | 2.18.235.69:443 | fpdownload.macromedia.com | Akamai International B.V. | — | whitelisted |
2480 | iexplore.exe | 205.185.208.78:443 | hw-cdn.contentabc.com | Highwinds Network Group, Inc. | US | suspicious |
2480 | iexplore.exe | 172.217.22.110:80 | www.google-analytics.com | Google Inc. | US | whitelisted |
2480 | iexplore.exe | 104.20.2.47:80 | www.statcounter.com | Cloudflare Inc | US | shared |
2480 | iexplore.exe | 192.229.221.214:443 | vz-cdn.contentabc.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.ass1st.com |
| suspicious |
coinhive.com |
| whitelisted |
www.bing.com |
| whitelisted |
ads.mofos.com |
| unknown |
www.statcounter.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
ads2.contentabc.com |
| whitelisted |
c.statcounter.com |
| whitelisted |
vz-cdn.contentabc.com |
| unknown |
cdn1.ads.brazzers.com |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2480 | iexplore.exe | Potential Corporate Privacy Violation | ET POLICY Outdated Flash Version M1 |