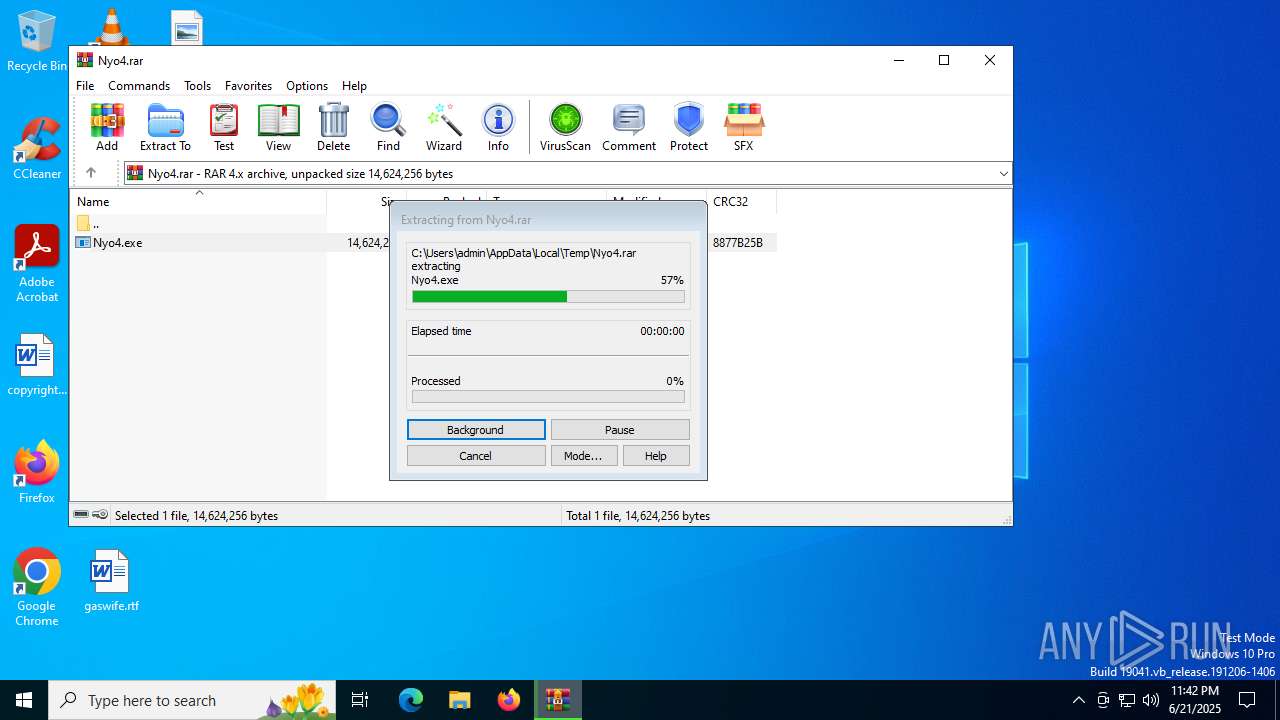
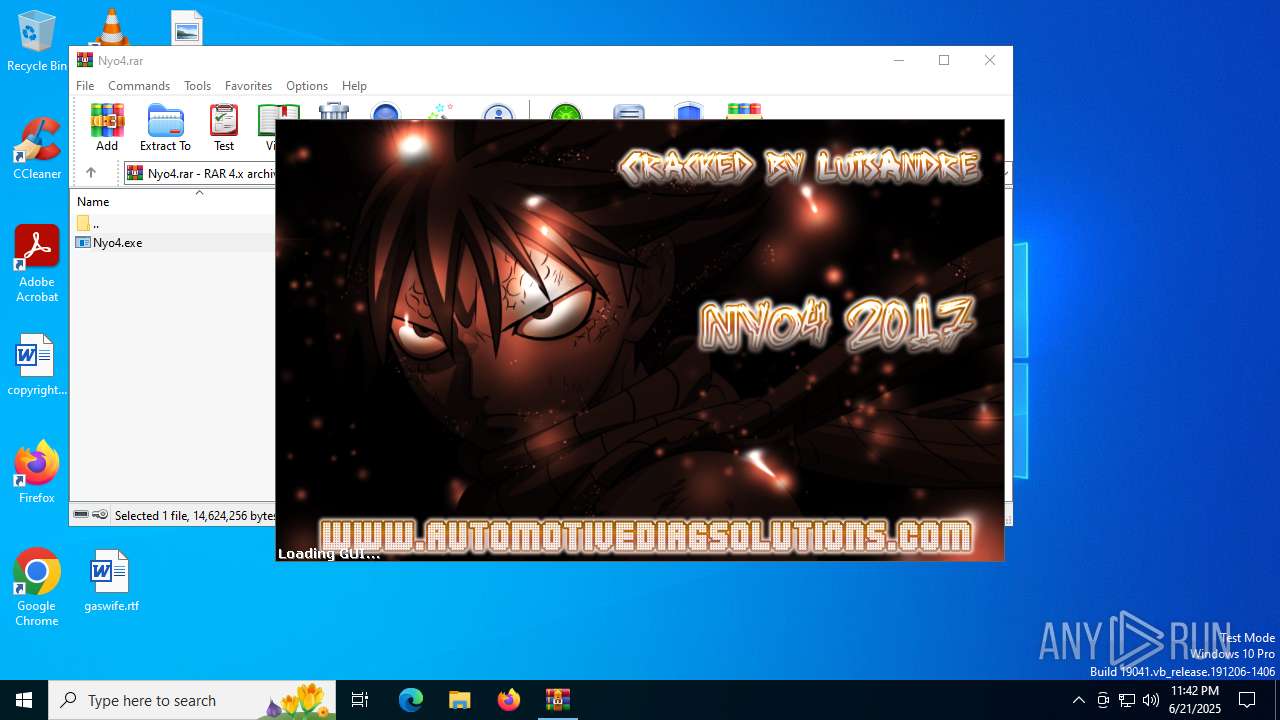
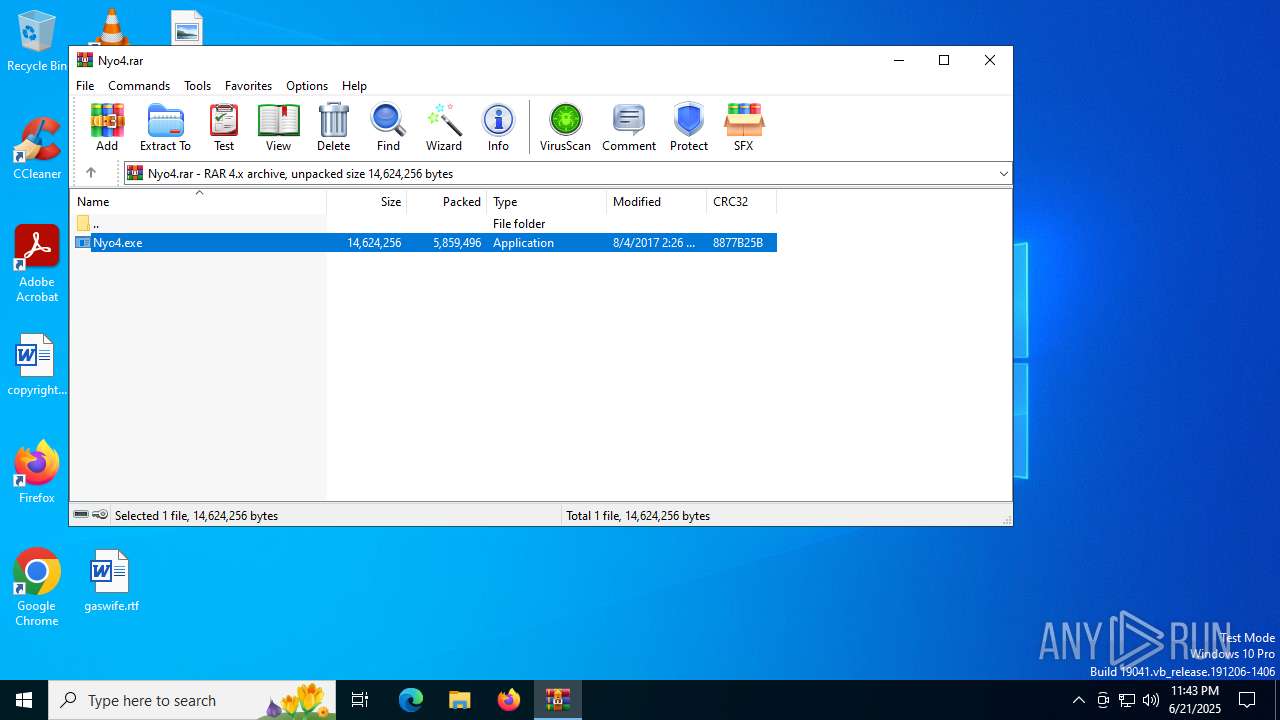
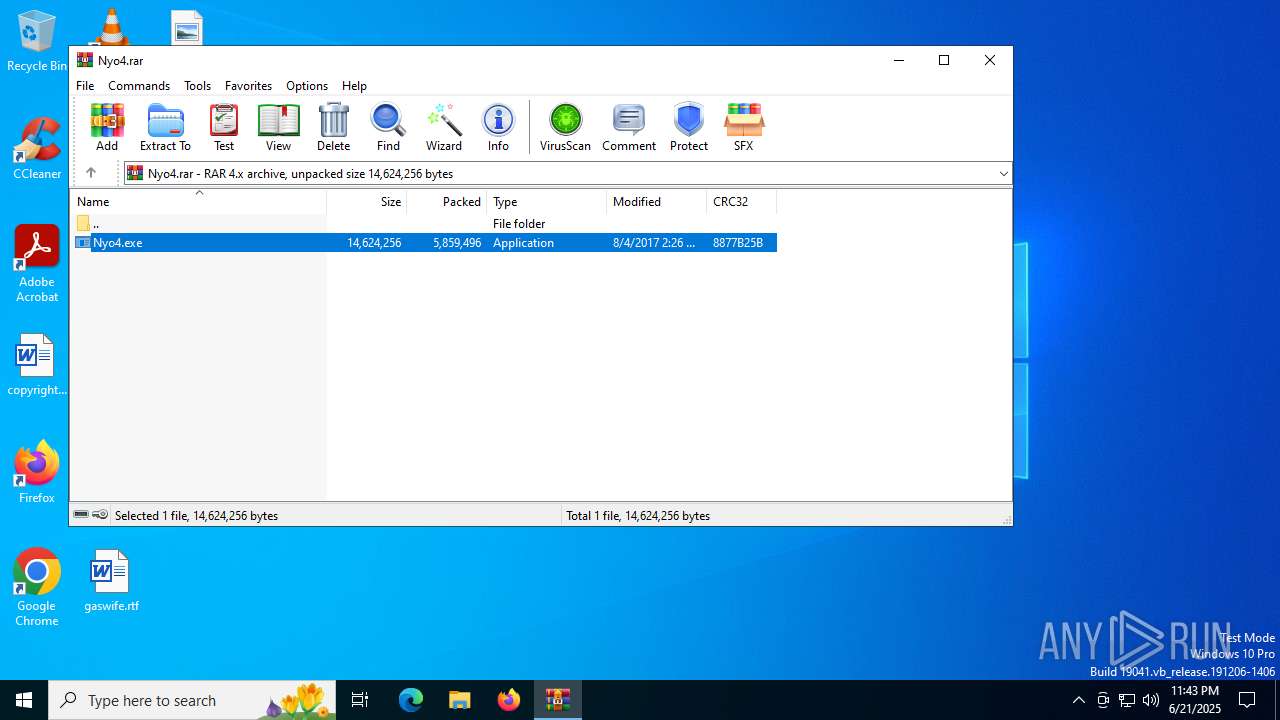
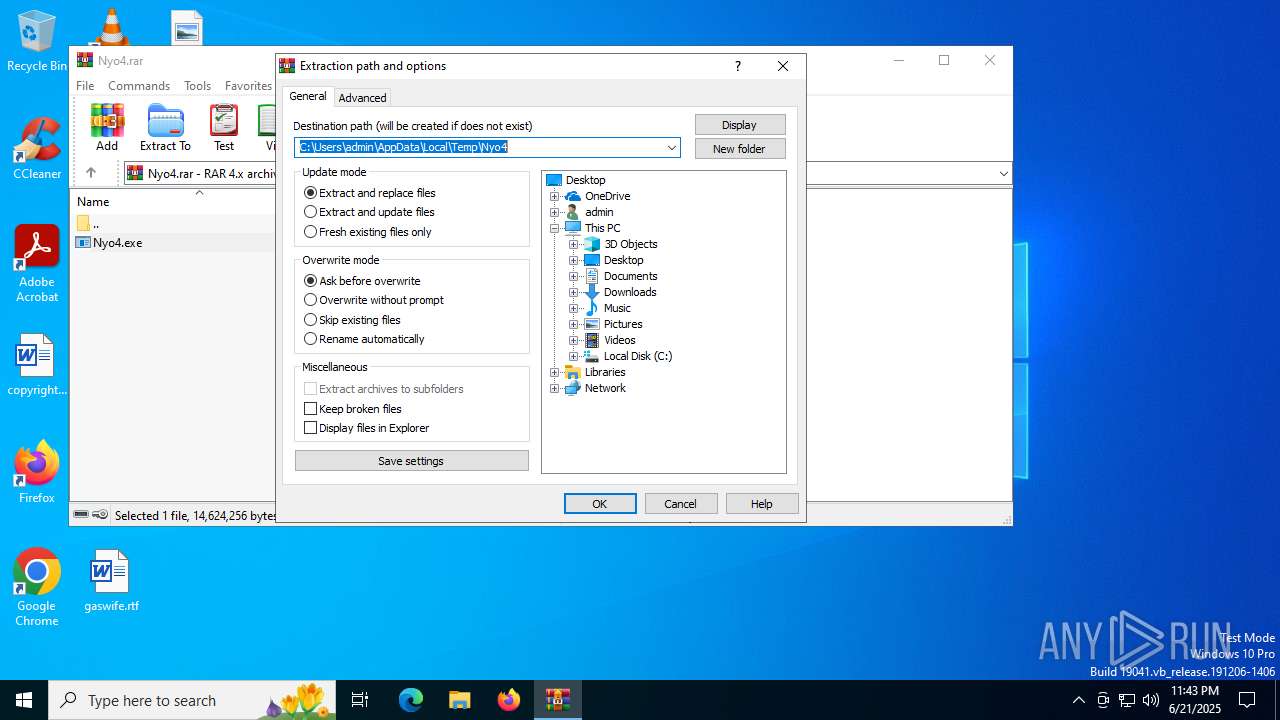
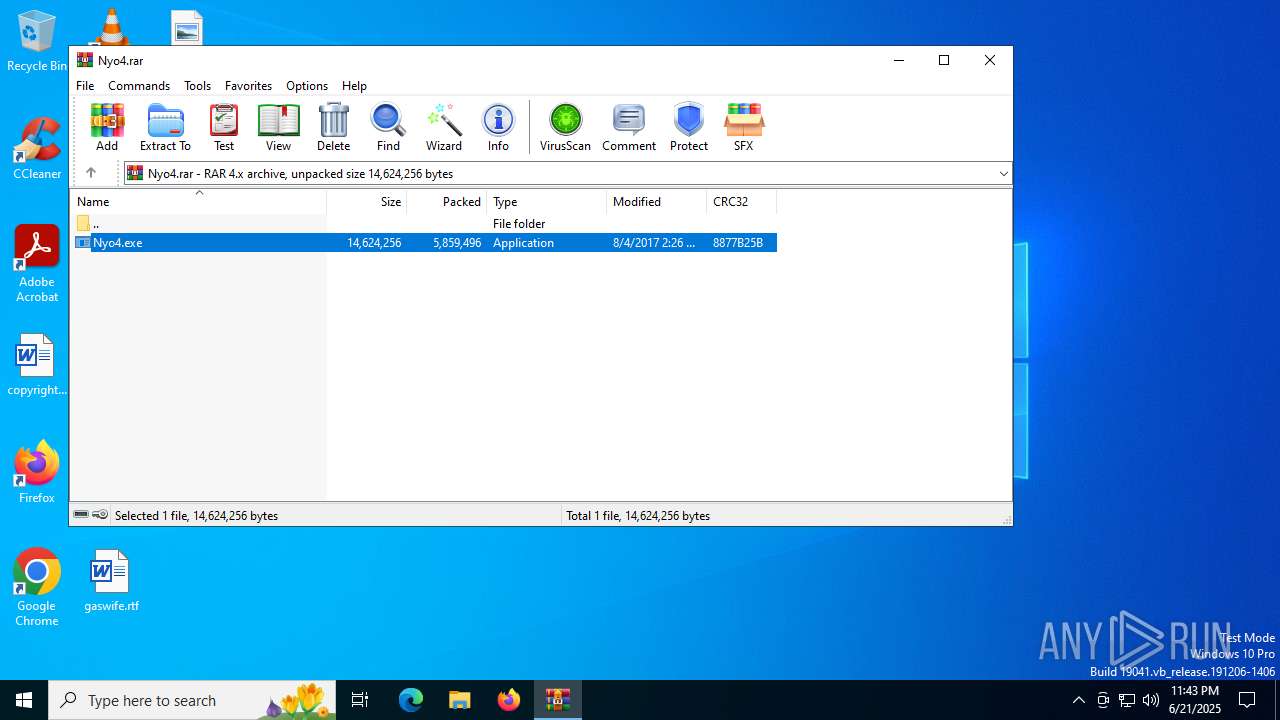
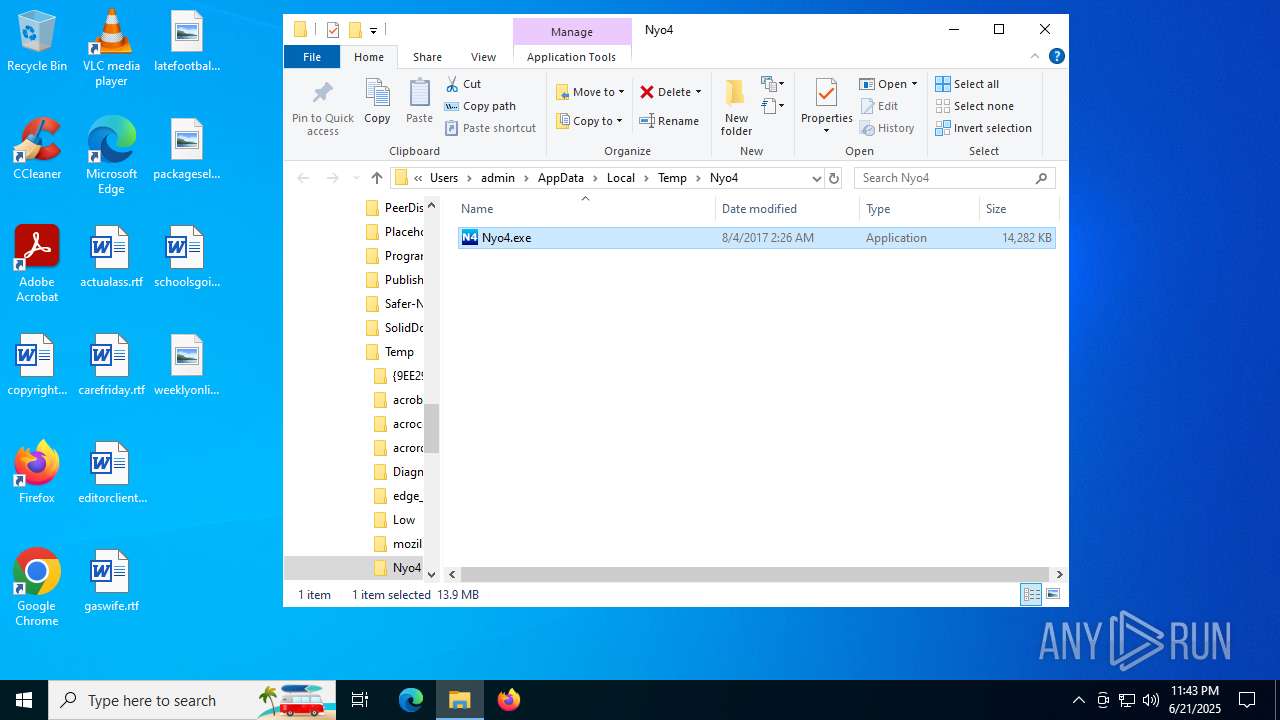
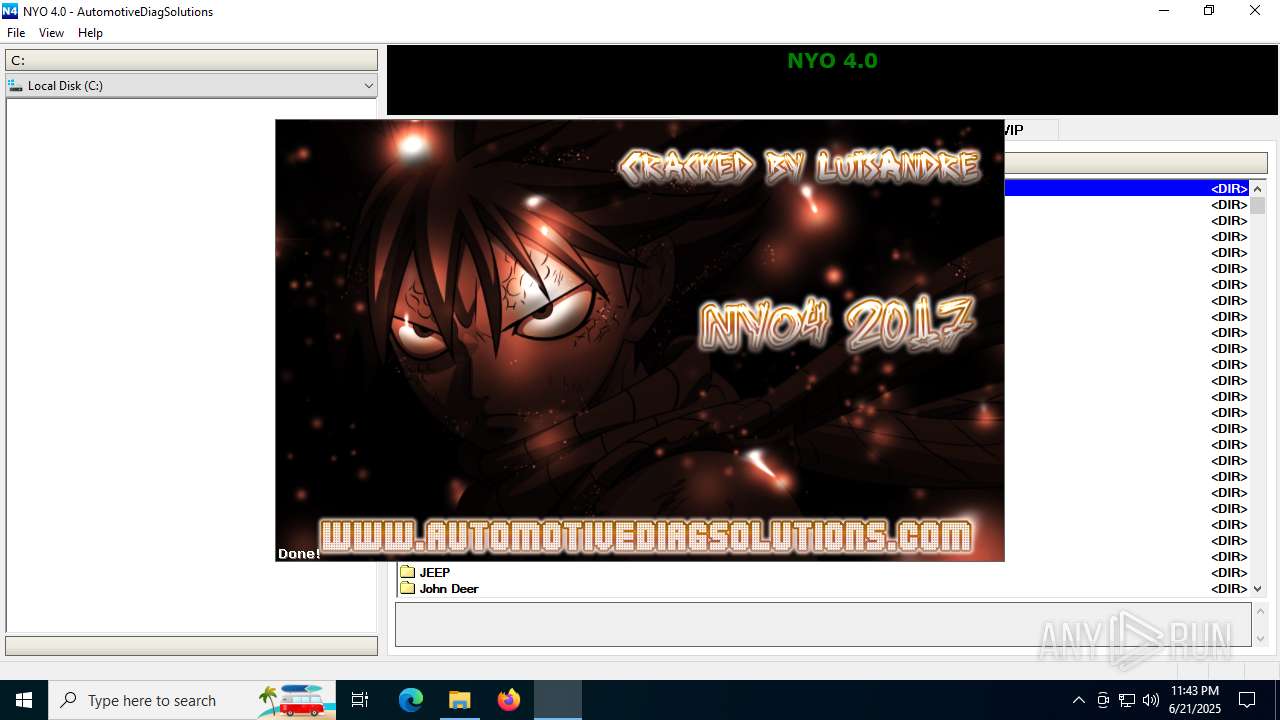
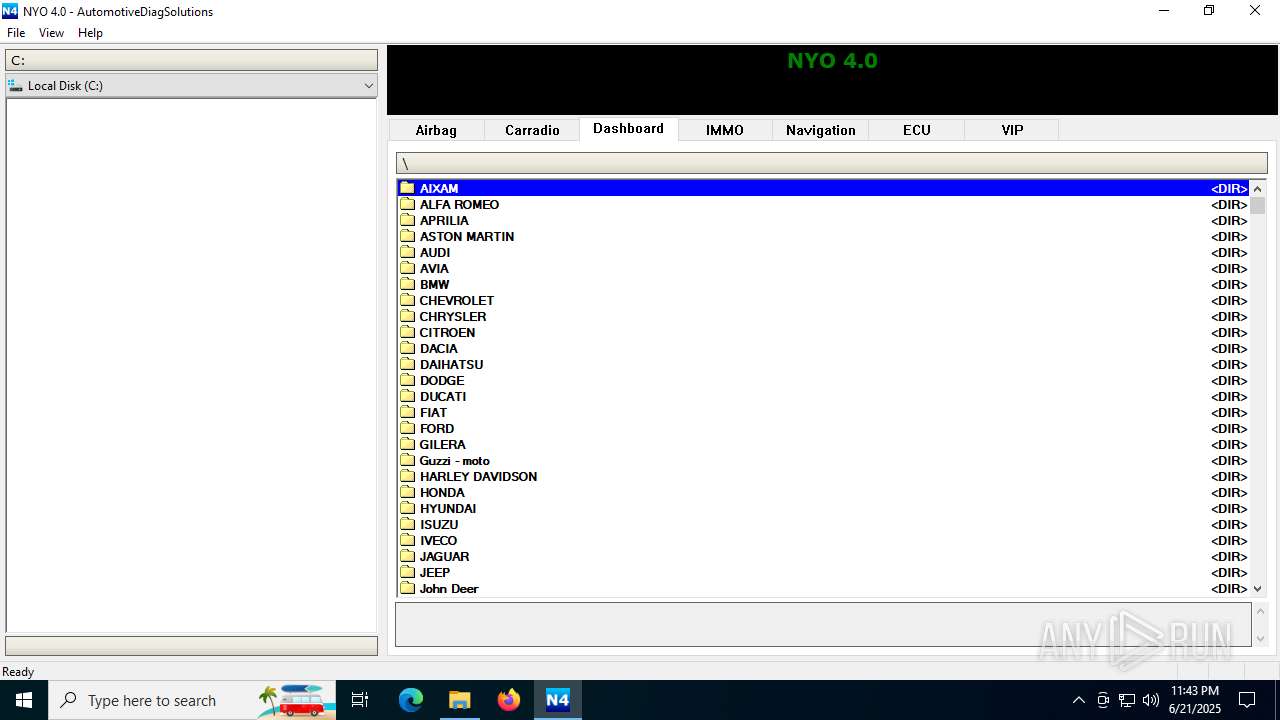
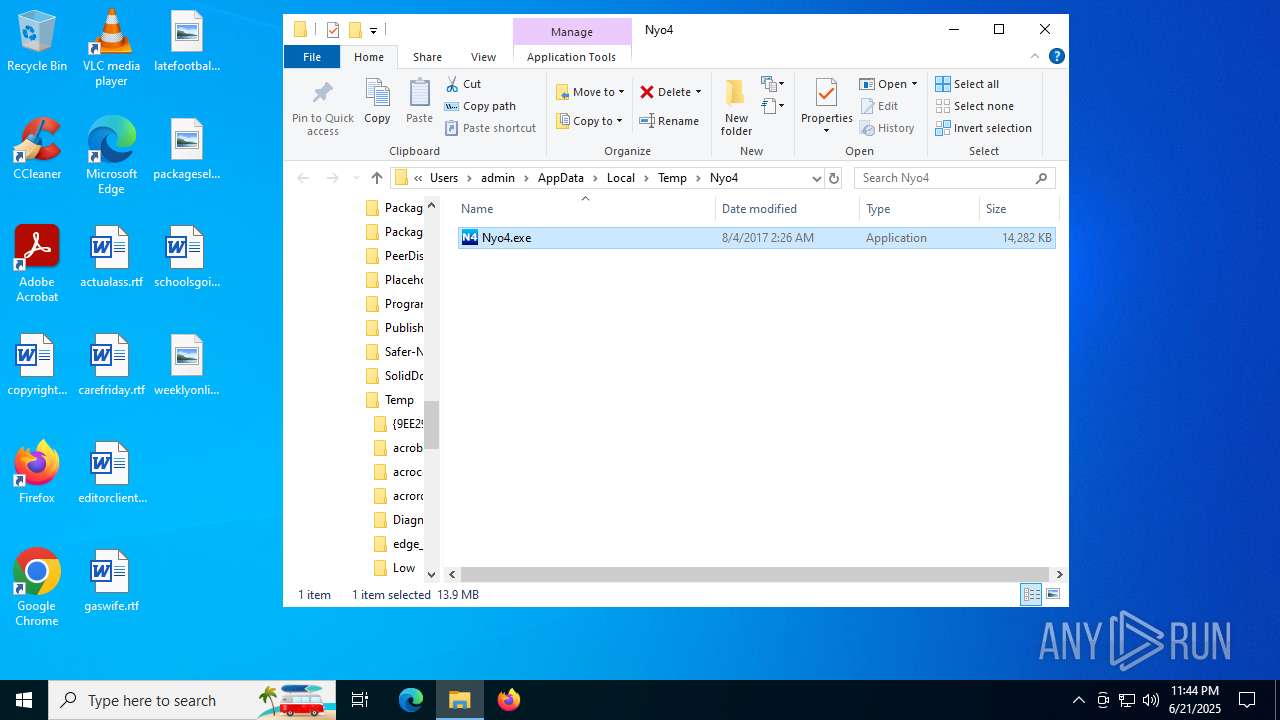
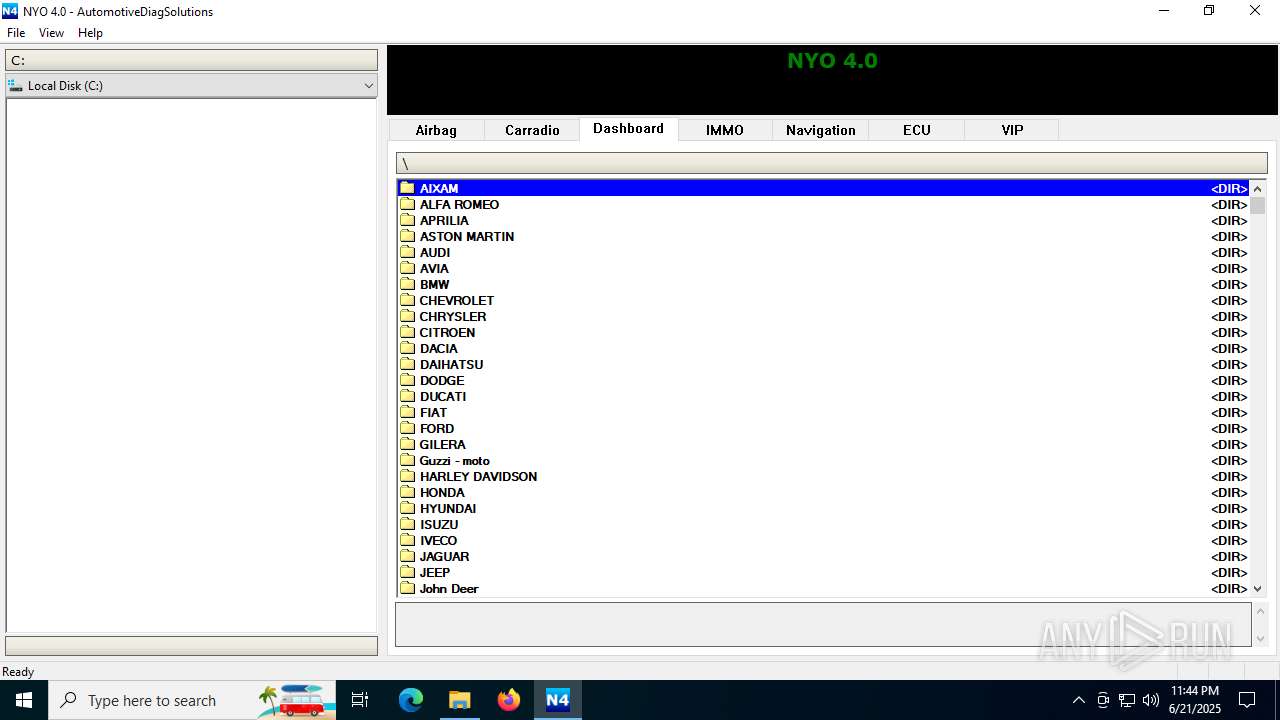
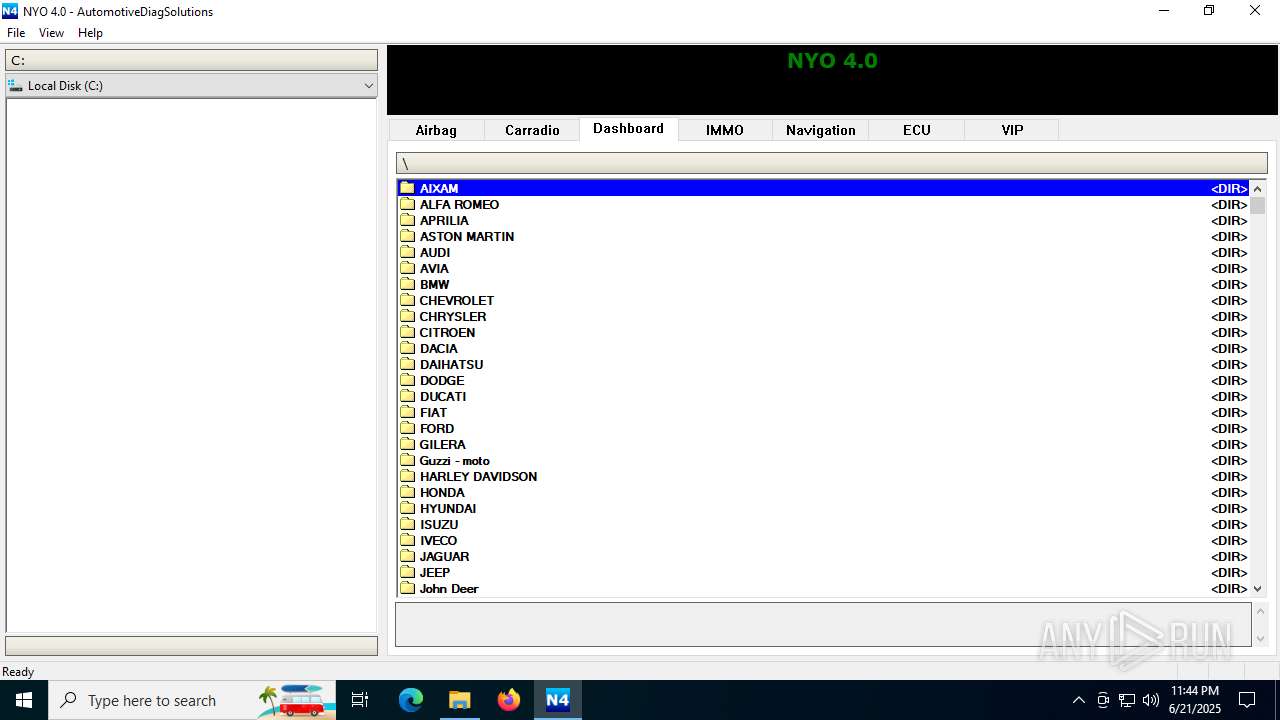
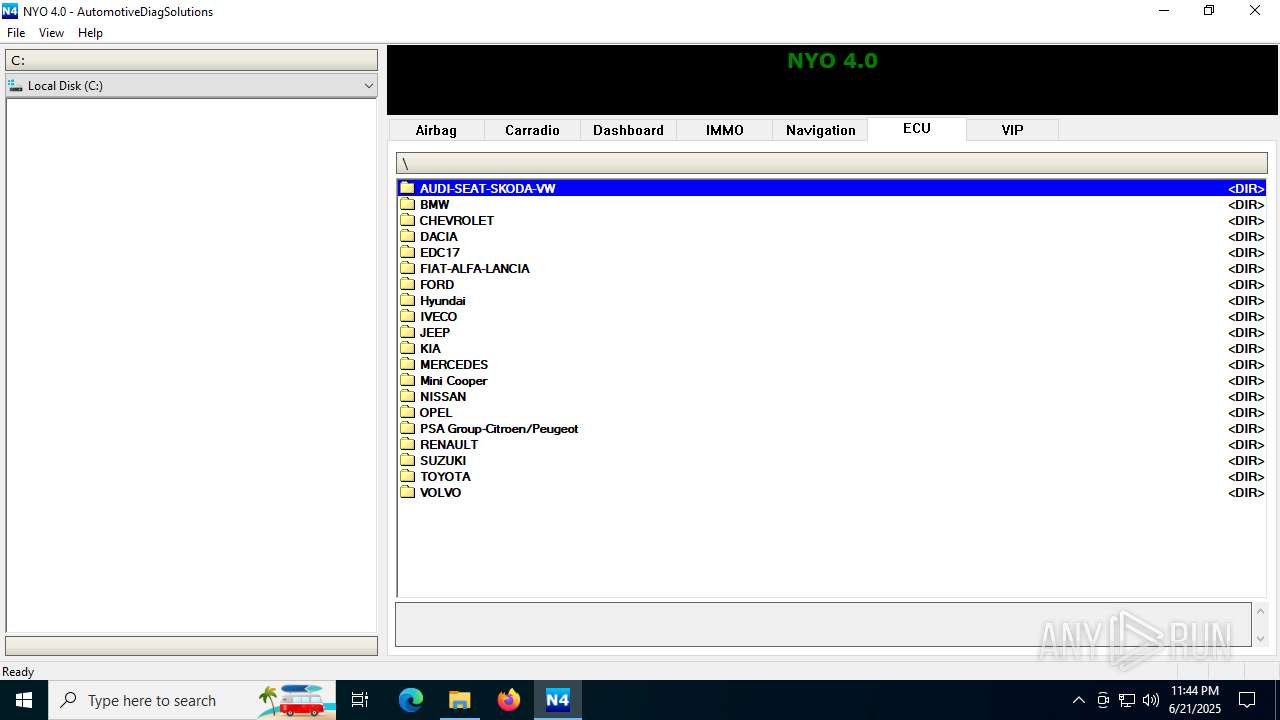
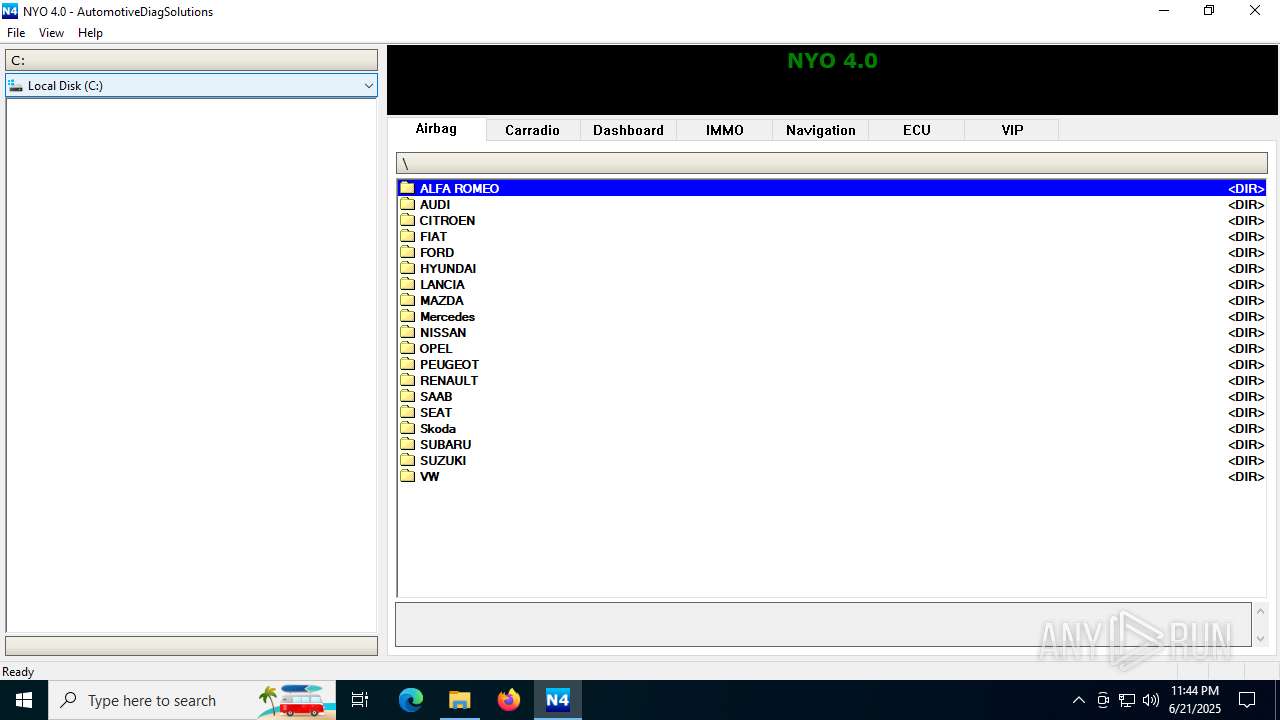
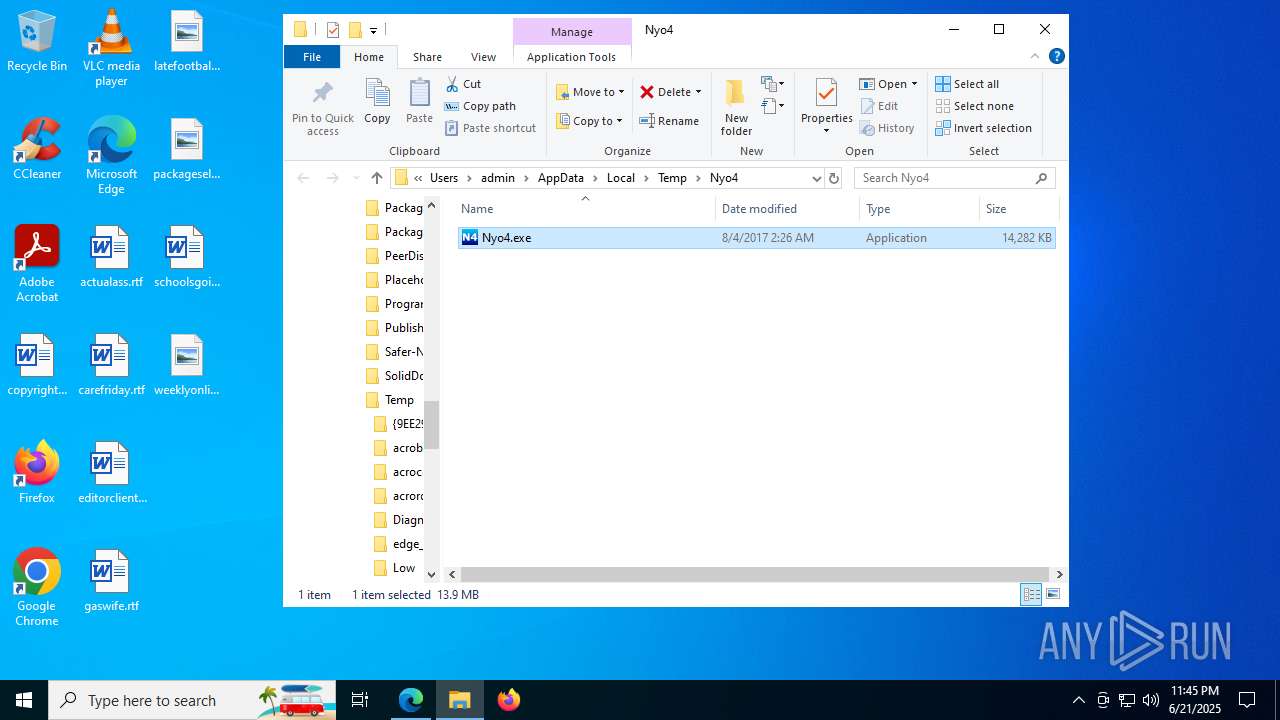
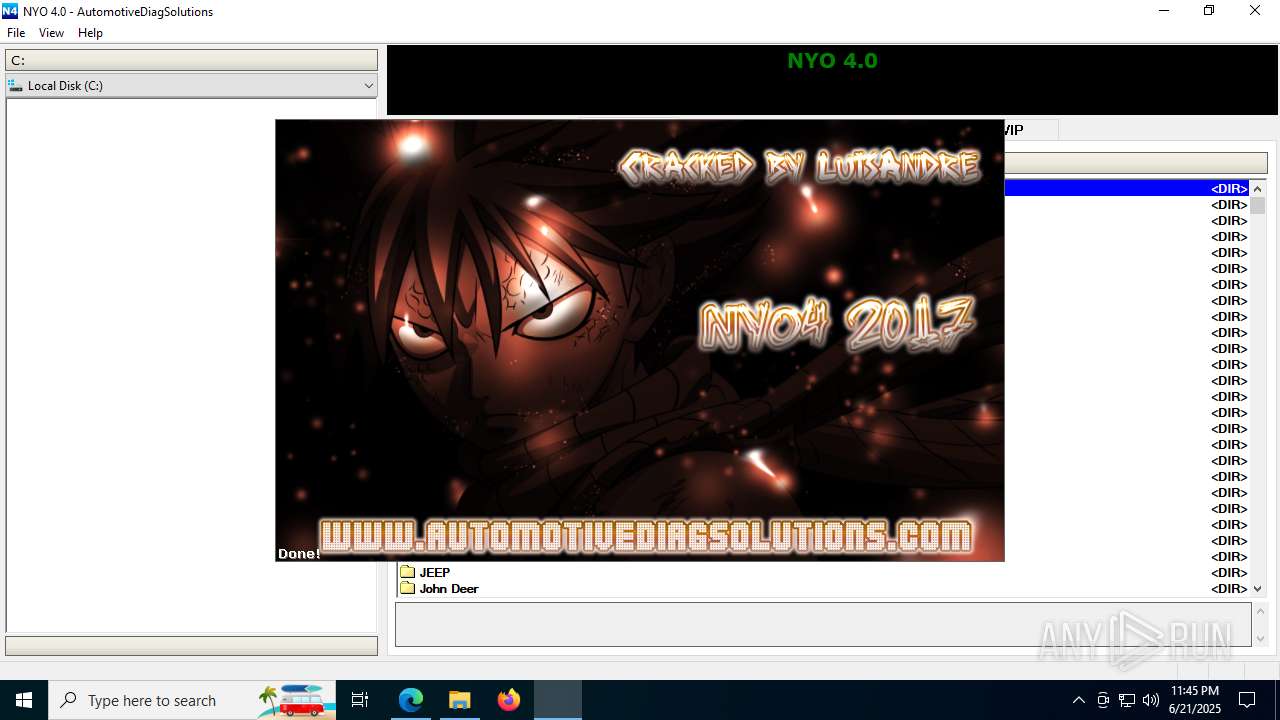
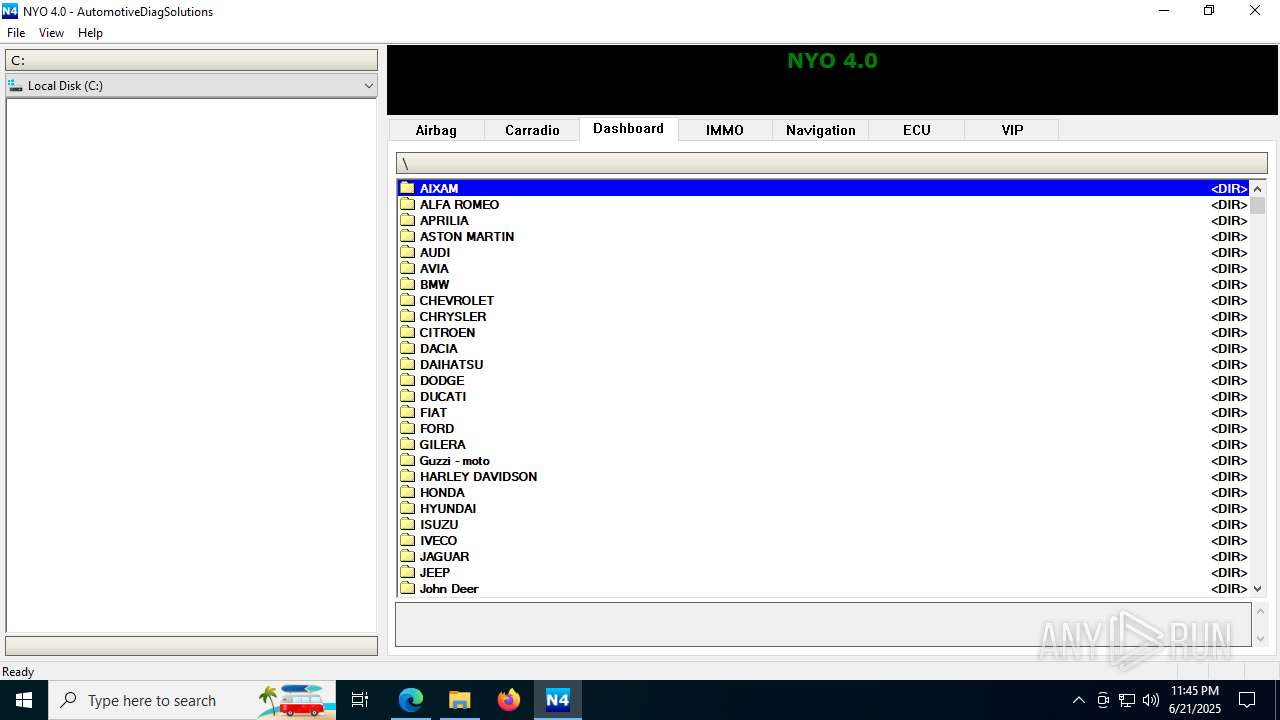
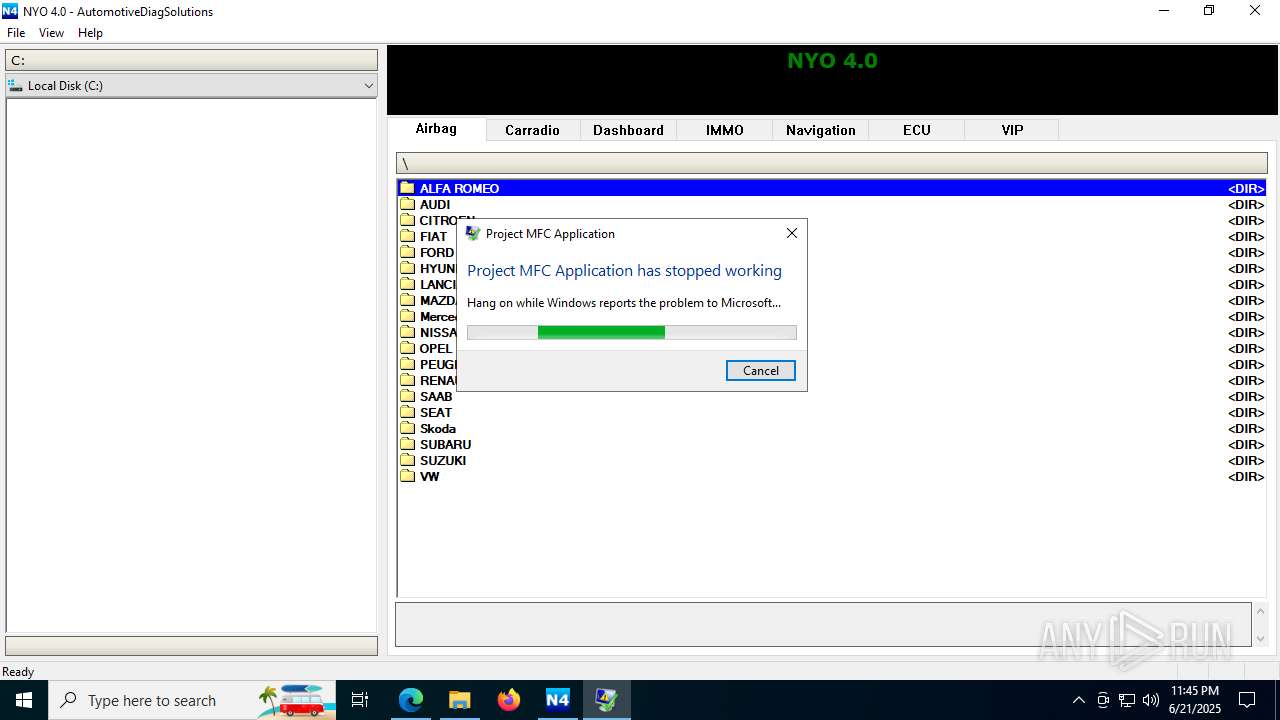
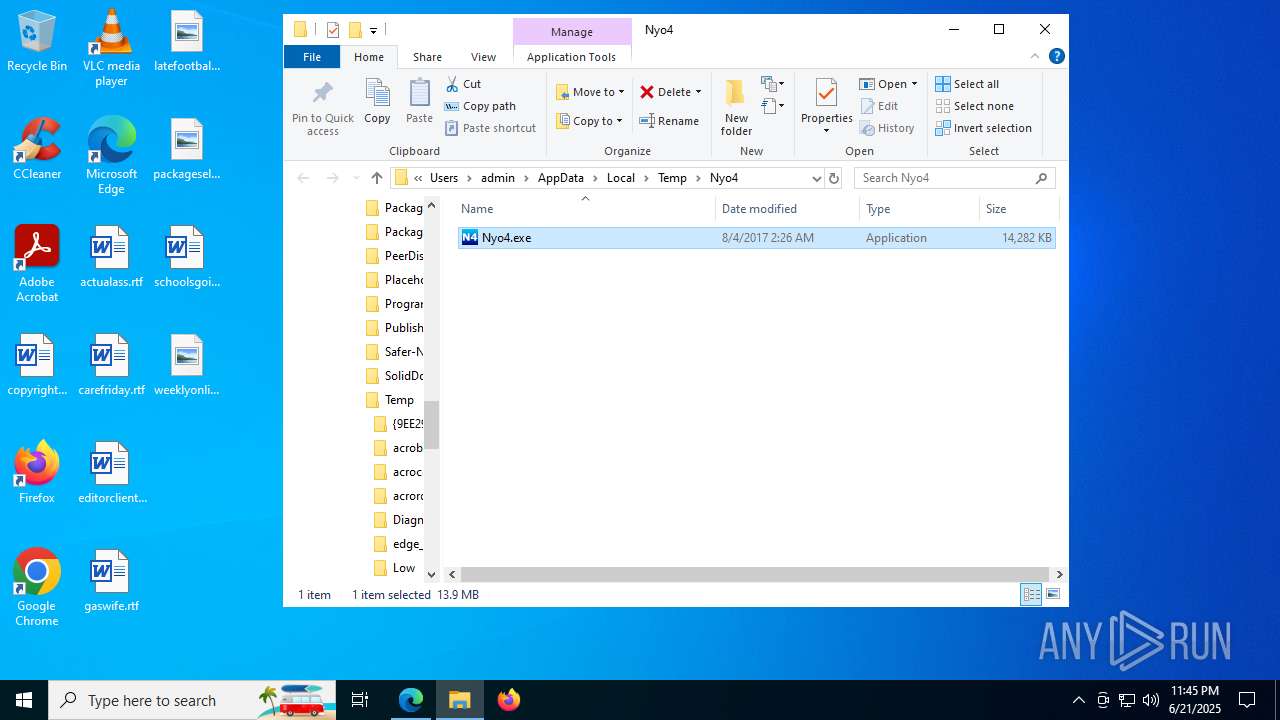
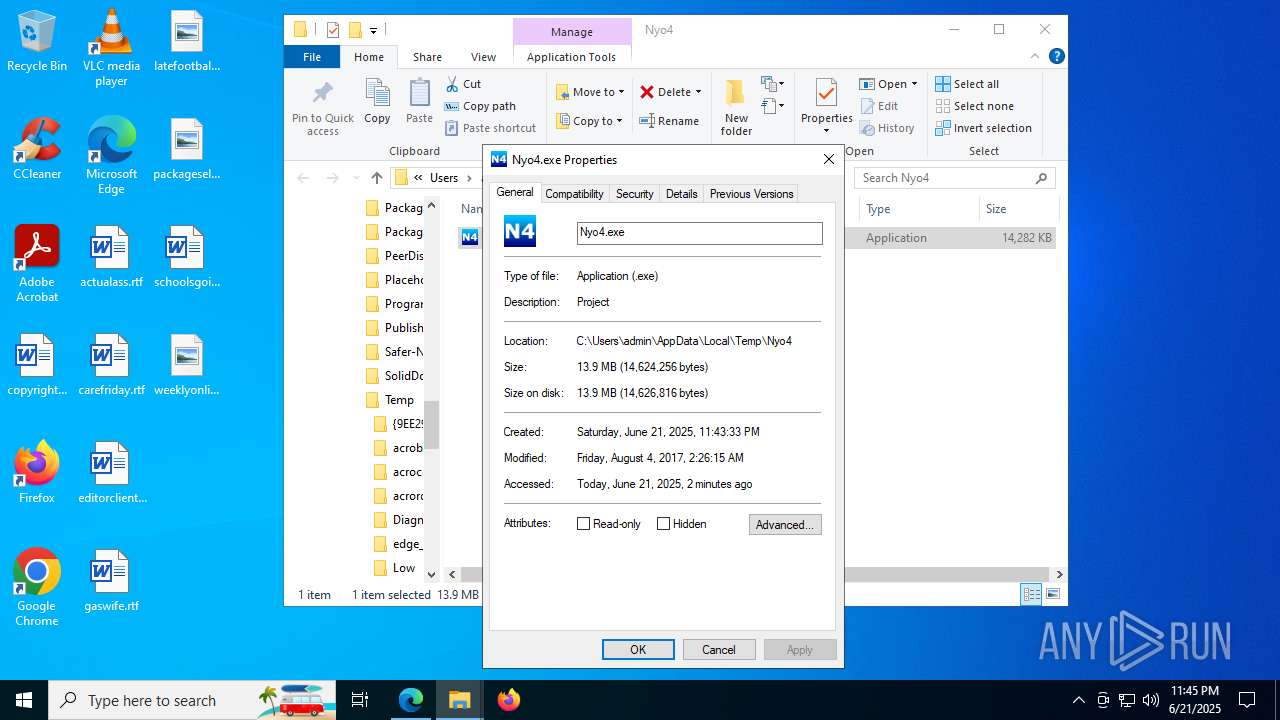
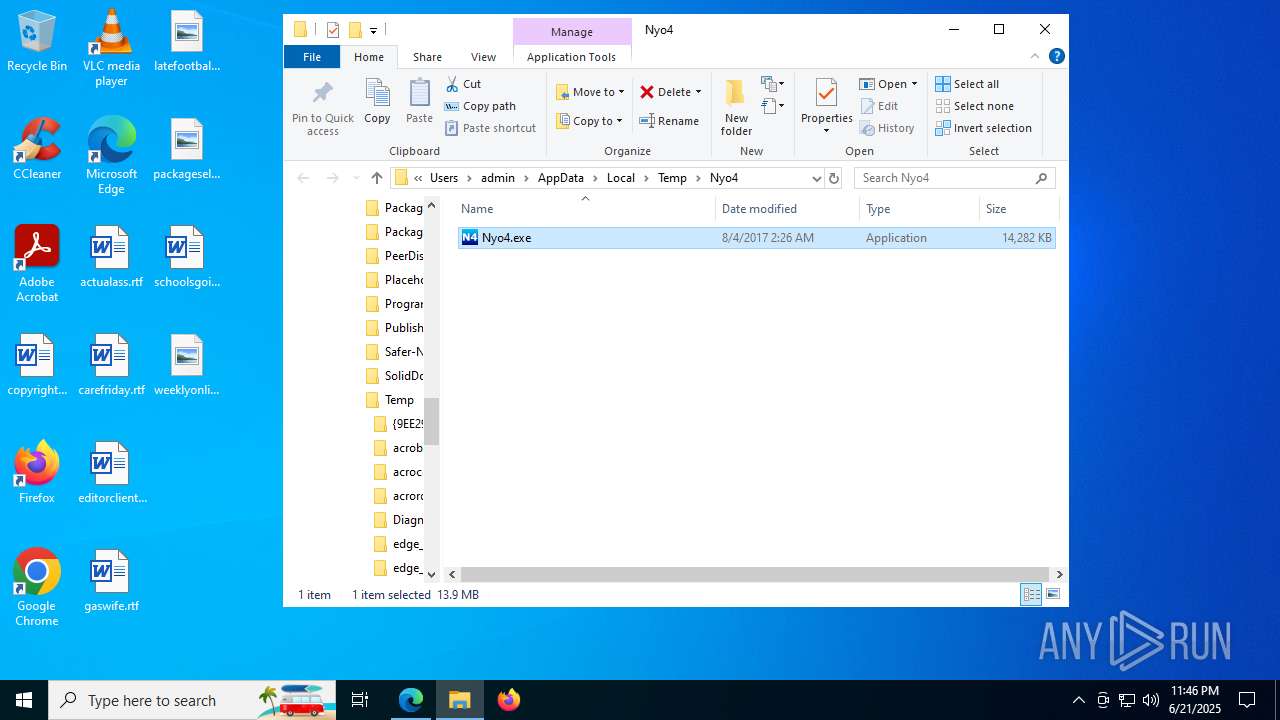
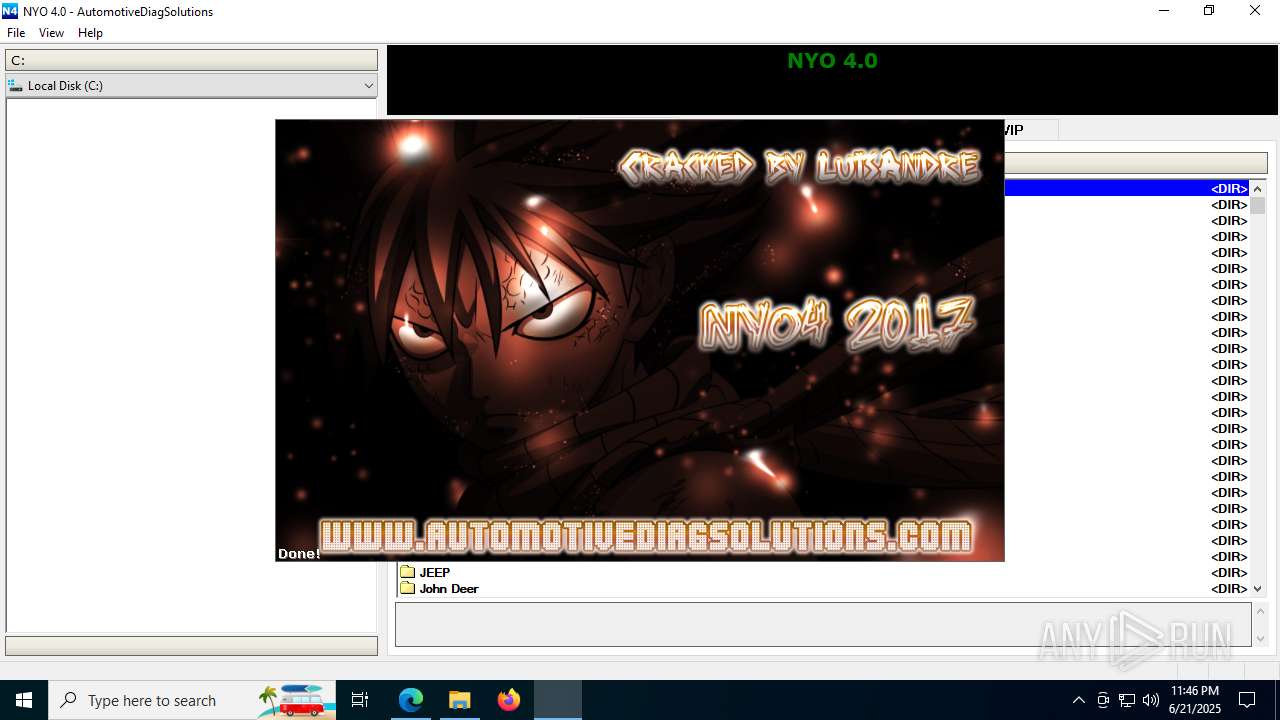
| File name: | Nyo4.rar |
| Full analysis: | https://app.any.run/tasks/950b0904-aca3-43a2-90e4-6eb101a17a98 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 23:42:17 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 7856F3A0DCBF3508E272E92E025ABFB7 |
| SHA1: | 1793E635DFBBB80C2C409642D7F341812A1DAF94 |
| SHA256: | 854DED07401A492FAFA1EB32212DC2D8C9DDF7F5AB71A1692AE022C3AFA32C6E |
| SSDEEP: | 98304:X+5ZZ39AEDvgQss6csTeEFM2cEvnCnad9Ox7qD92gHiBFA8dcURfmDqTndpZrlJ4:YH6IJ6mPHw |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6652)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6652)
- Nyo4.exe (PID: 6540)
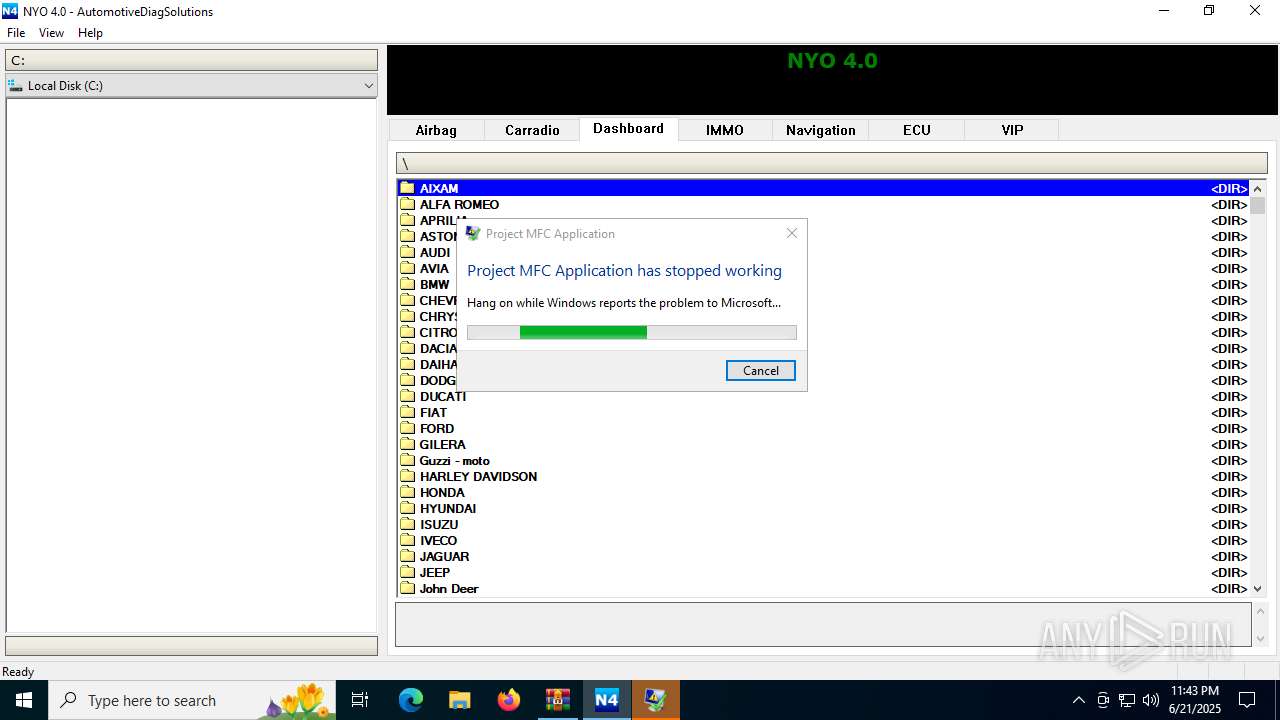
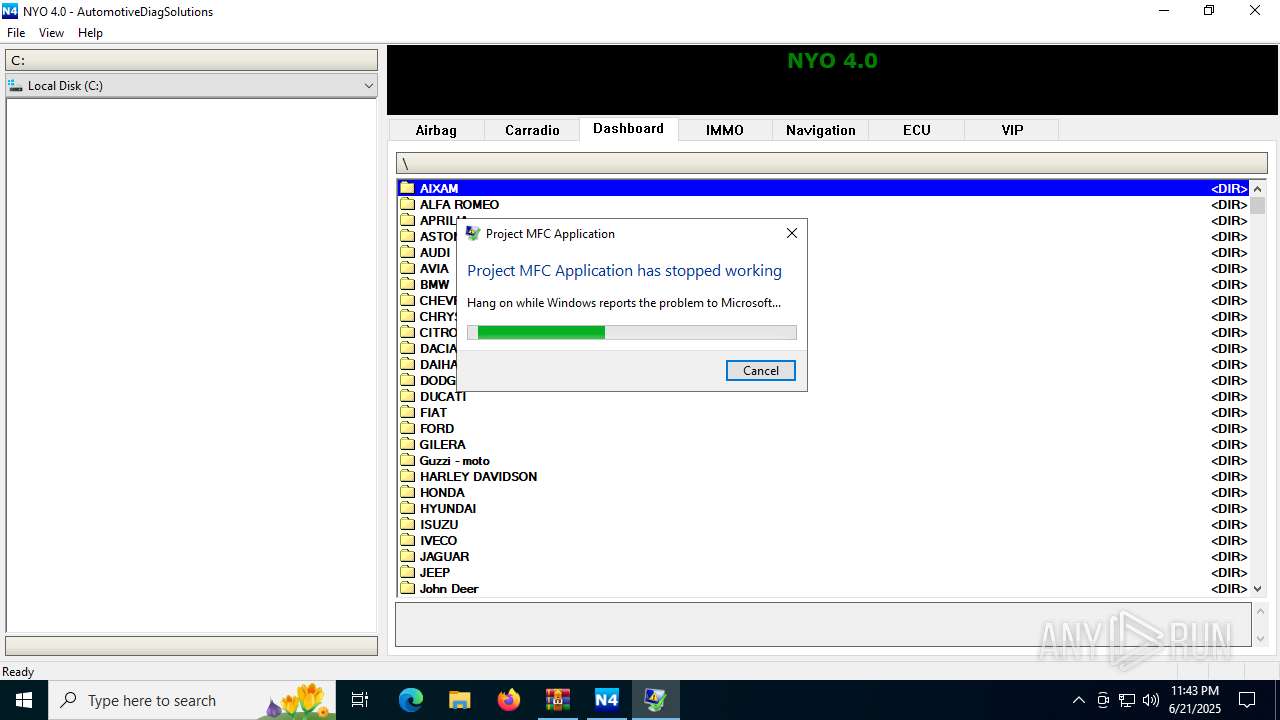
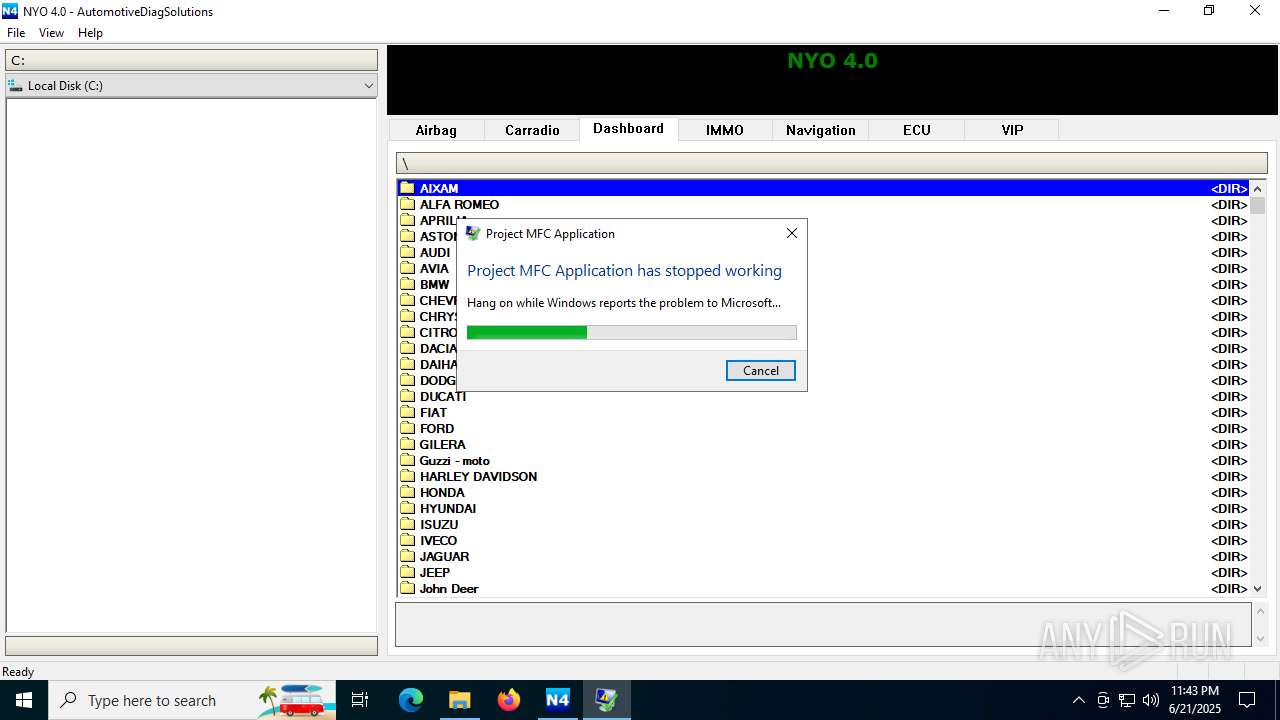
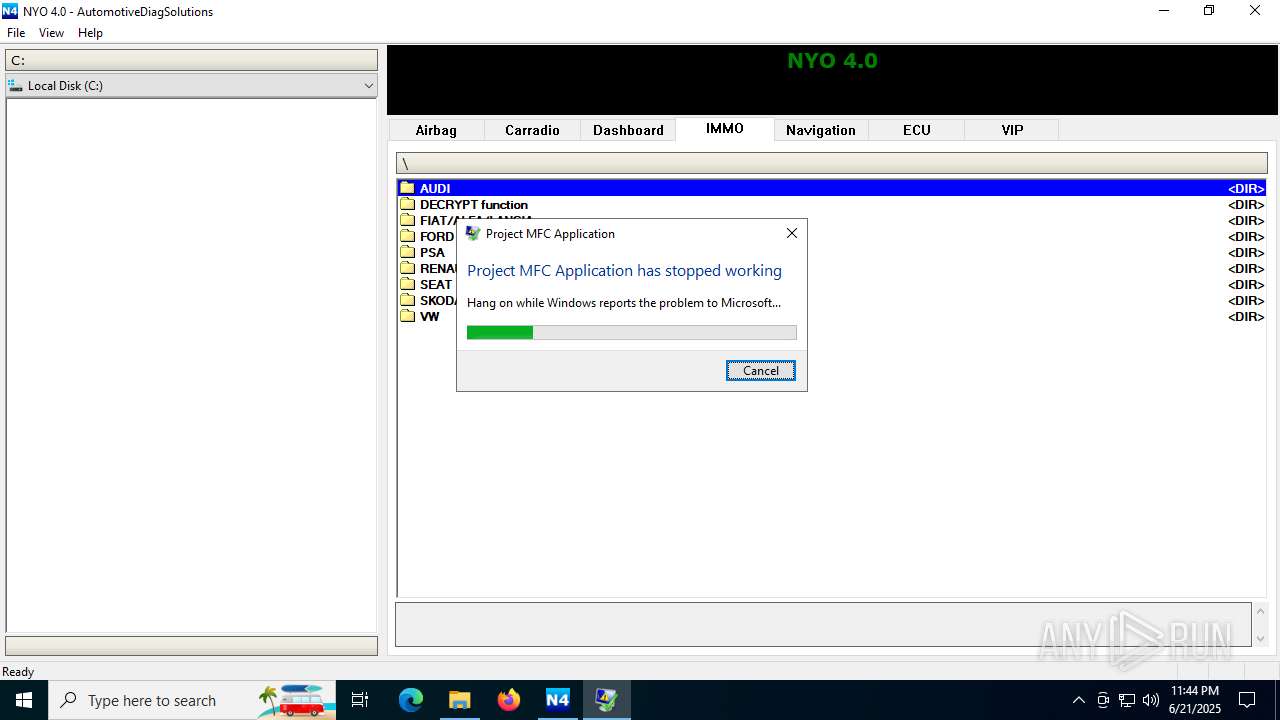
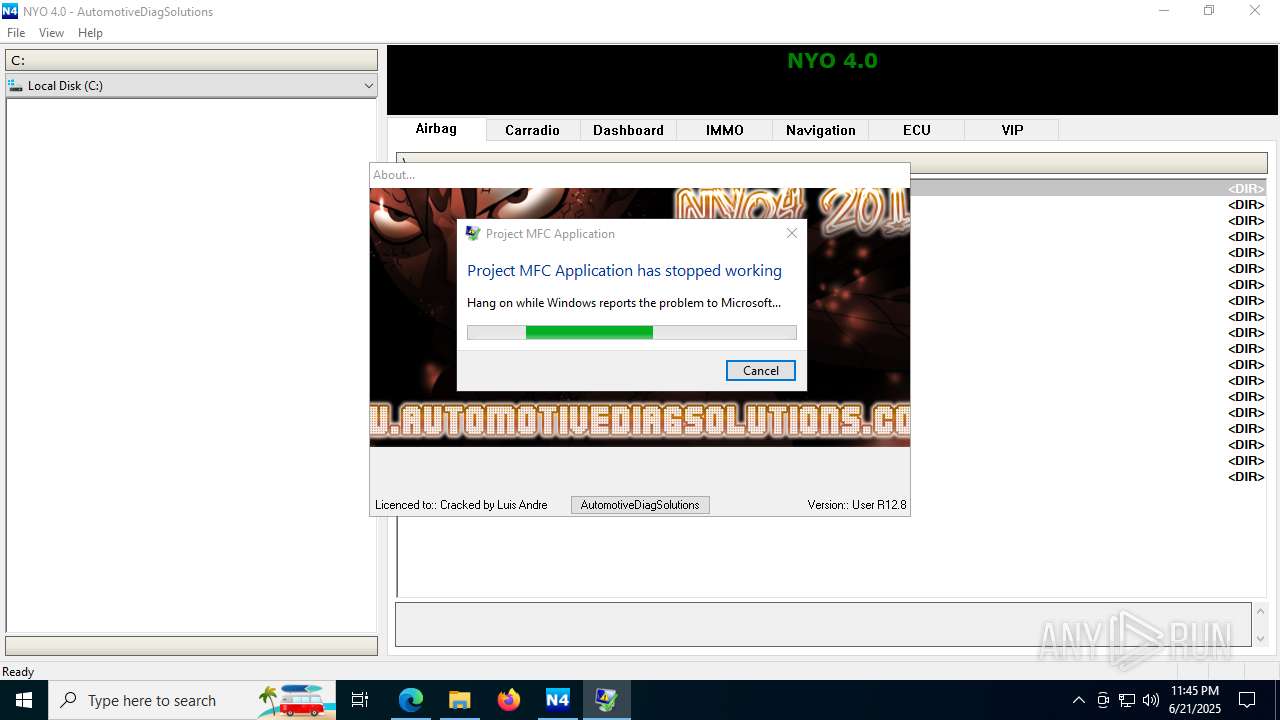
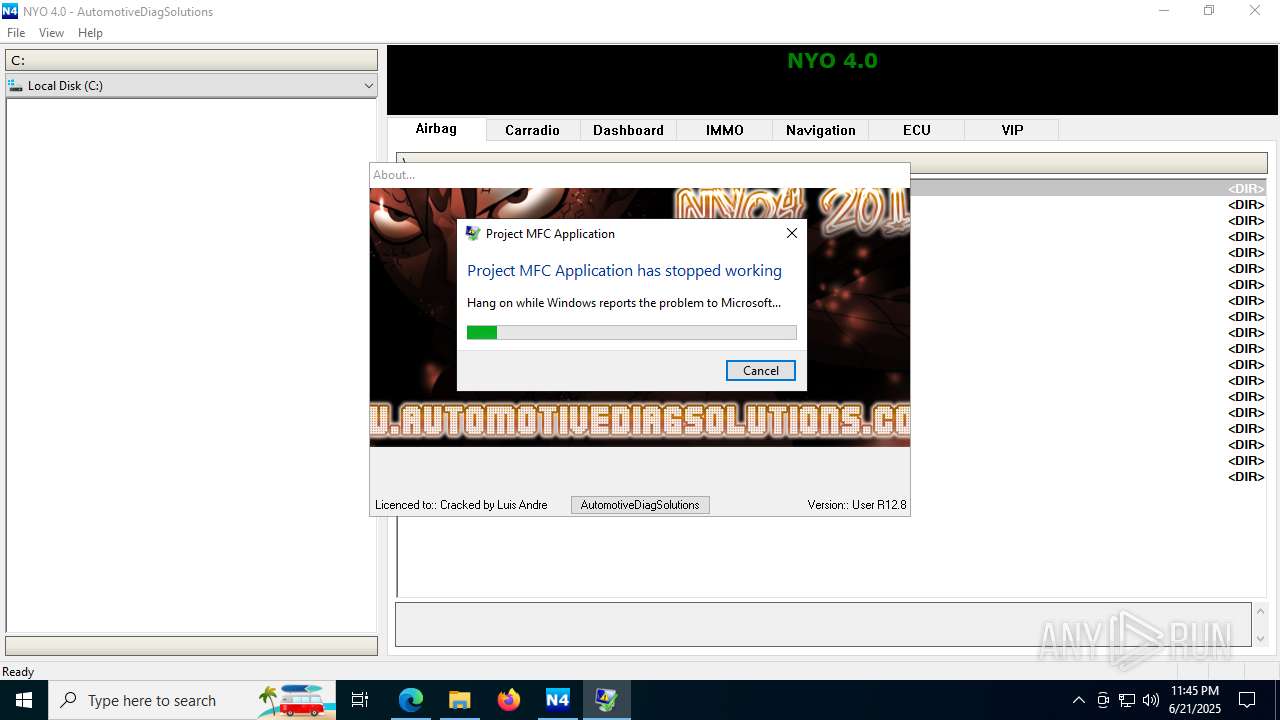
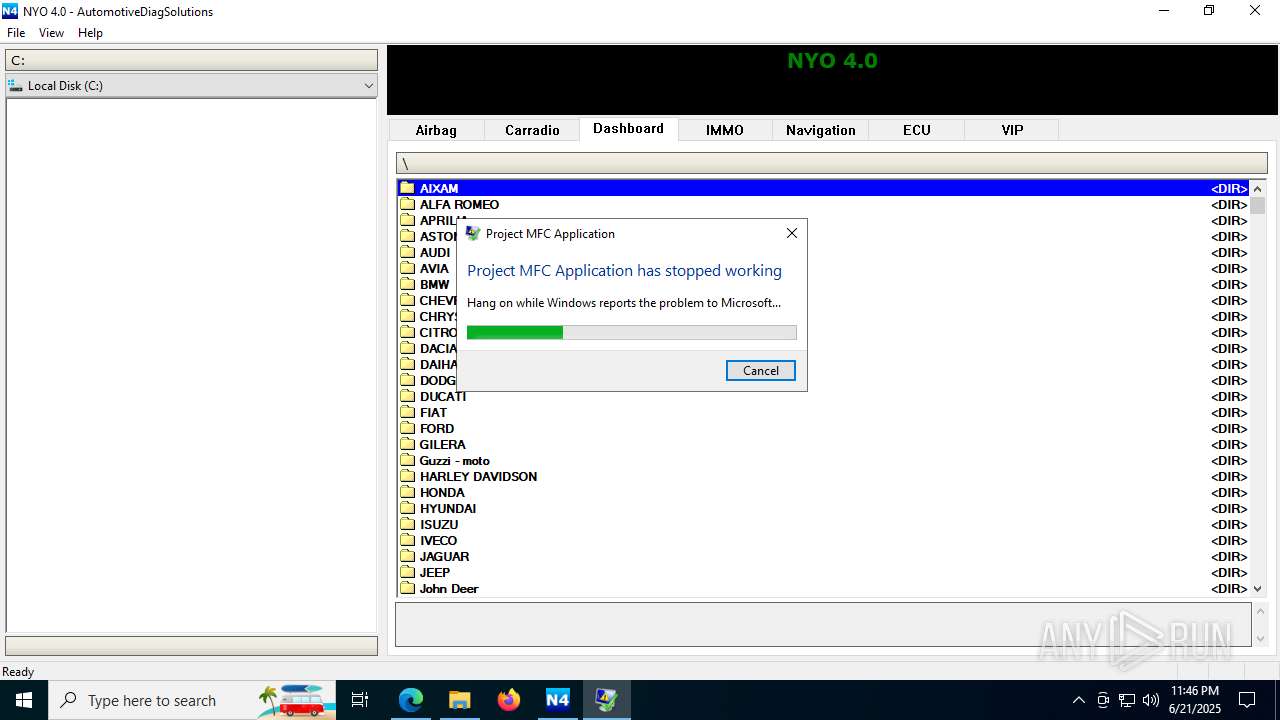
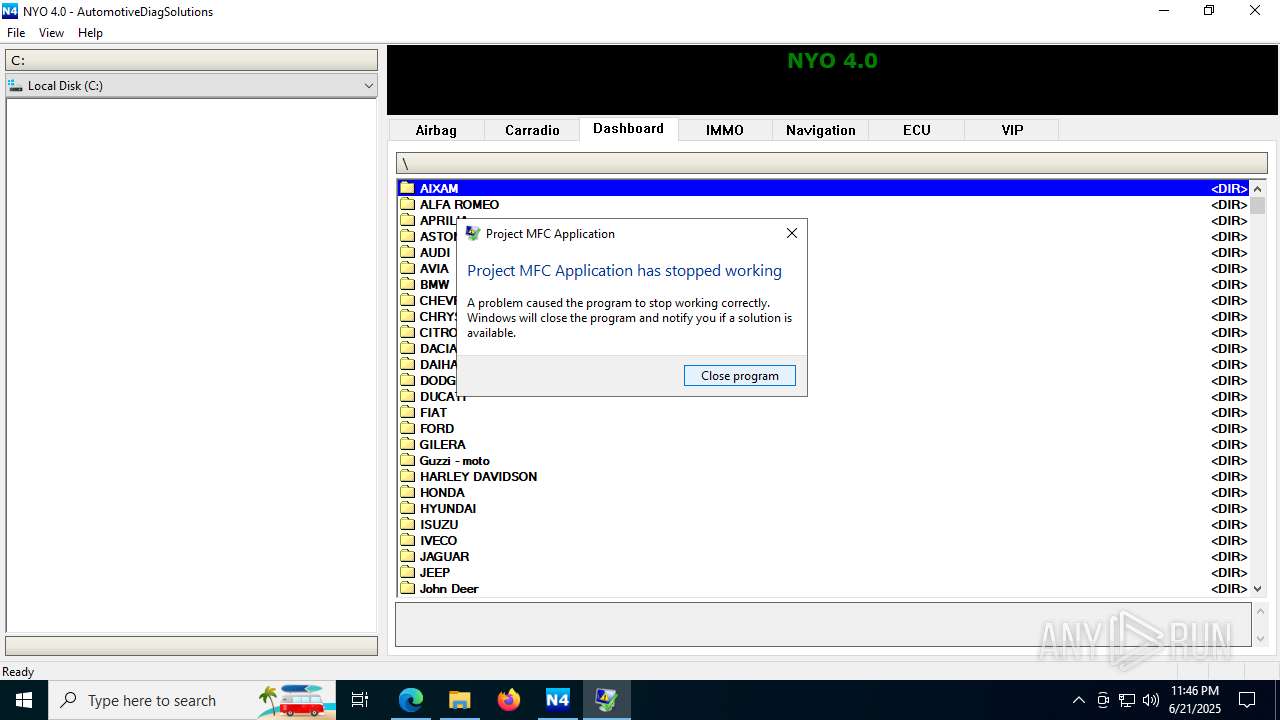
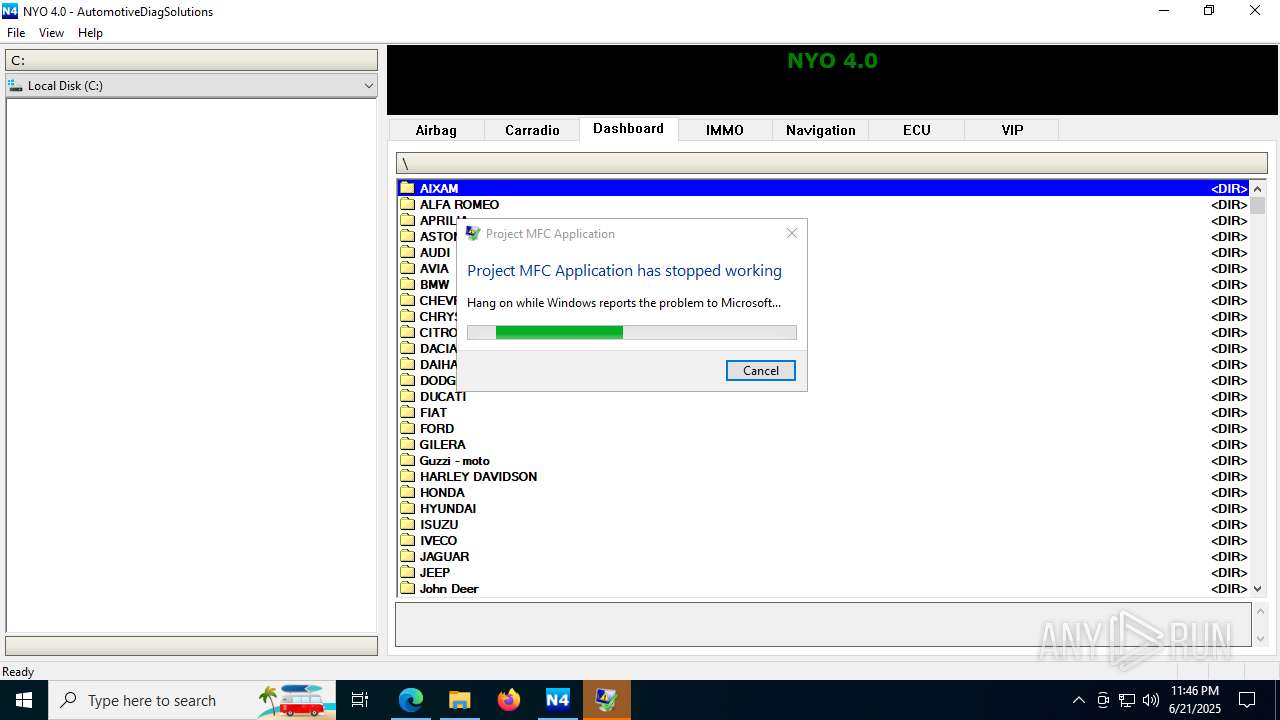
Executes application which crashes
- Nyo4.exe (PID: 6940)
- Nyo4.exe (PID: 6124)
- Nyo4.exe (PID: 6732)
- Nyo4.exe (PID: 6304)
- Nyo4.exe (PID: 6540)
- Nyo4.exe (PID: 1512)
- Nyo4.exe (PID: 6200)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 6652)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6652)
Create files in a temporary directory
- Nyo4.exe (PID: 6940)
- Nyo4.exe (PID: 6124)
- Nyo4.exe (PID: 6732)
- Nyo4.exe (PID: 6540)
- Nyo4.exe (PID: 6304)
- Nyo4.exe (PID: 1512)
- Nyo4.exe (PID: 6200)
- Nyo4.exe (PID: 4372)
Checks supported languages
- Nyo4.exe (PID: 6940)
- Nyo4.exe (PID: 6124)
- Nyo4.exe (PID: 6732)
- Nyo4.exe (PID: 6540)
- Nyo4.exe (PID: 6304)
- identity_helper.exe (PID: 1056)
- Nyo4.exe (PID: 1512)
- Nyo4.exe (PID: 6200)
- Nyo4.exe (PID: 4372)
Reads the computer name
- Nyo4.exe (PID: 6940)
- Nyo4.exe (PID: 6732)
- Nyo4.exe (PID: 6124)
- Nyo4.exe (PID: 6540)
- Nyo4.exe (PID: 6304)
- identity_helper.exe (PID: 1056)
- Nyo4.exe (PID: 1512)
- Nyo4.exe (PID: 6200)
- Nyo4.exe (PID: 4372)
VMProtect protector has been detected
- Nyo4.exe (PID: 6940)
- Nyo4.exe (PID: 6124)
- Nyo4.exe (PID: 6304)
- Nyo4.exe (PID: 6540)
- Nyo4.exe (PID: 1512)
- Nyo4.exe (PID: 6200)
- Nyo4.exe (PID: 4372)
Compiled with Borland Delphi (YARA)
- Nyo4.exe (PID: 6940)
- Nyo4.exe (PID: 6124)
- Nyo4.exe (PID: 6304)
- Nyo4.exe (PID: 1512)
- Nyo4.exe (PID: 6540)
- Nyo4.exe (PID: 6200)
- Nyo4.exe (PID: 4372)
Creates files or folders in the user directory
- WerFault.exe (PID: 5620)
- WerFault.exe (PID: 1700)
- WerFault.exe (PID: 3624)
- WerFault.exe (PID: 6384)
- WerFault.exe (PID: 1644)
- WerFault.exe (PID: 6340)
- WerFault.exe (PID: 3752)
- WerFault.exe (PID: 2116)
- WerFault.exe (PID: 4984)
Manual execution by a user
- Nyo4.exe (PID: 6732)
- Nyo4.exe (PID: 6540)
- Nyo4.exe (PID: 6304)
- Nyo4.exe (PID: 1512)
- Nyo4.exe (PID: 6200)
- Nyo4.exe (PID: 4372)
- Nyo4.exe (PID: 1808)
Reads the software policy settings
- WerFault.exe (PID: 6384)
- WerFault.exe (PID: 1700)
- WerFault.exe (PID: 3624)
- slui.exe (PID: 2512)
- WerFault.exe (PID: 1644)
- WerFault.exe (PID: 6340)
- WerFault.exe (PID: 3752)
- WerFault.exe (PID: 2116)
- WerFault.exe (PID: 4984)
Checks proxy server information
- WerFault.exe (PID: 6384)
- WerFault.exe (PID: 1700)
- slui.exe (PID: 2512)
- WerFault.exe (PID: 3624)
- WerFault.exe (PID: 1644)
- WerFault.exe (PID: 6340)
- WerFault.exe (PID: 3752)
- WerFault.exe (PID: 4984)
- WerFault.exe (PID: 2116)
Application launched itself
- msedge.exe (PID: 5556)
Reads Environment values
- identity_helper.exe (PID: 1056)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| FileVersion: | RAR v4 |
|---|---|
| CompressedSize: | 5859527 |
| UncompressedSize: | 14624256 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2017:08:04 02:26:14 |
| PackingMethod: | Normal |
| ArchivedFileName: | Nyo4.exe |
Total processes
208
Monitored processes
50
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 316 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=6940,i,7667650087338164688,3727906836943878398,262144 --variations-seed-version --mojo-platform-channel-handle=6920 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1056 | "C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=5968,i,7667650087338164688,3727906836943878398,262144 --variations-seed-version --mojo-platform-channel-handle=5984 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1296 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_xpay_wallet.mojom.EdgeXPayWalletService --lang=en-US --service-sandbox-type=utility --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=3708,i,7667650087338164688,3727906836943878398,262144 --variations-seed-version --mojo-platform-channel-handle=3936 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
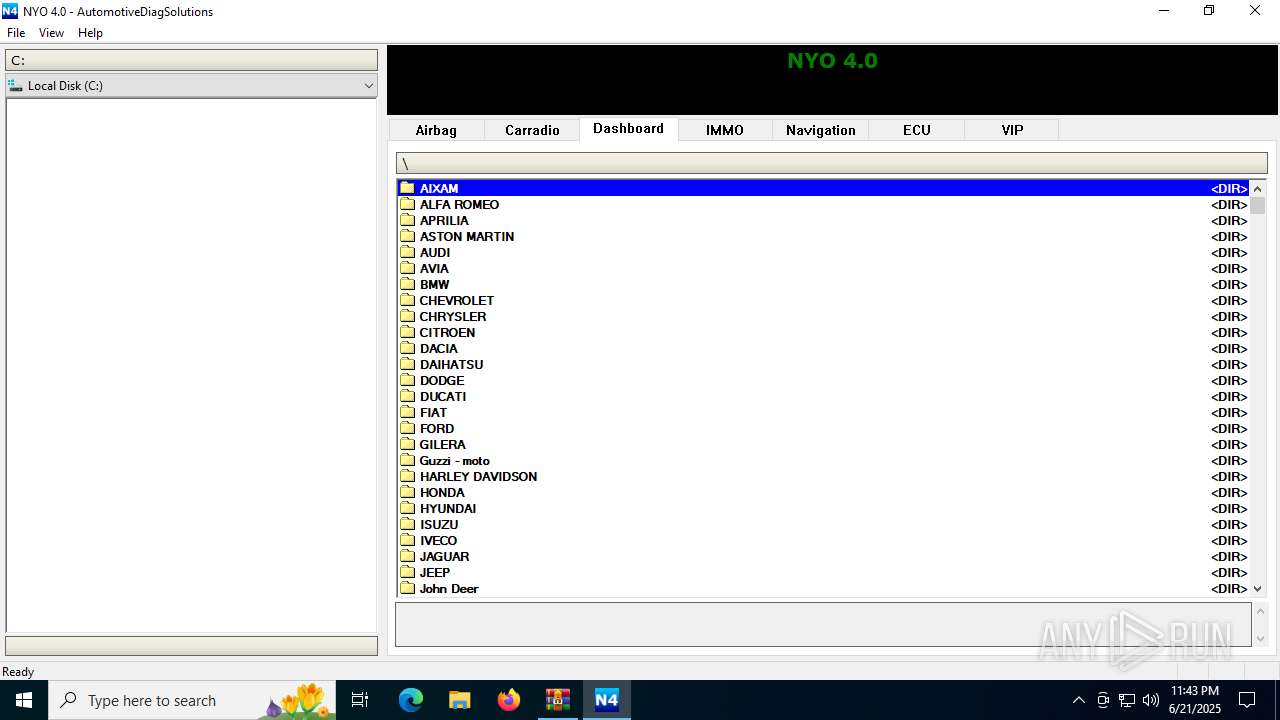
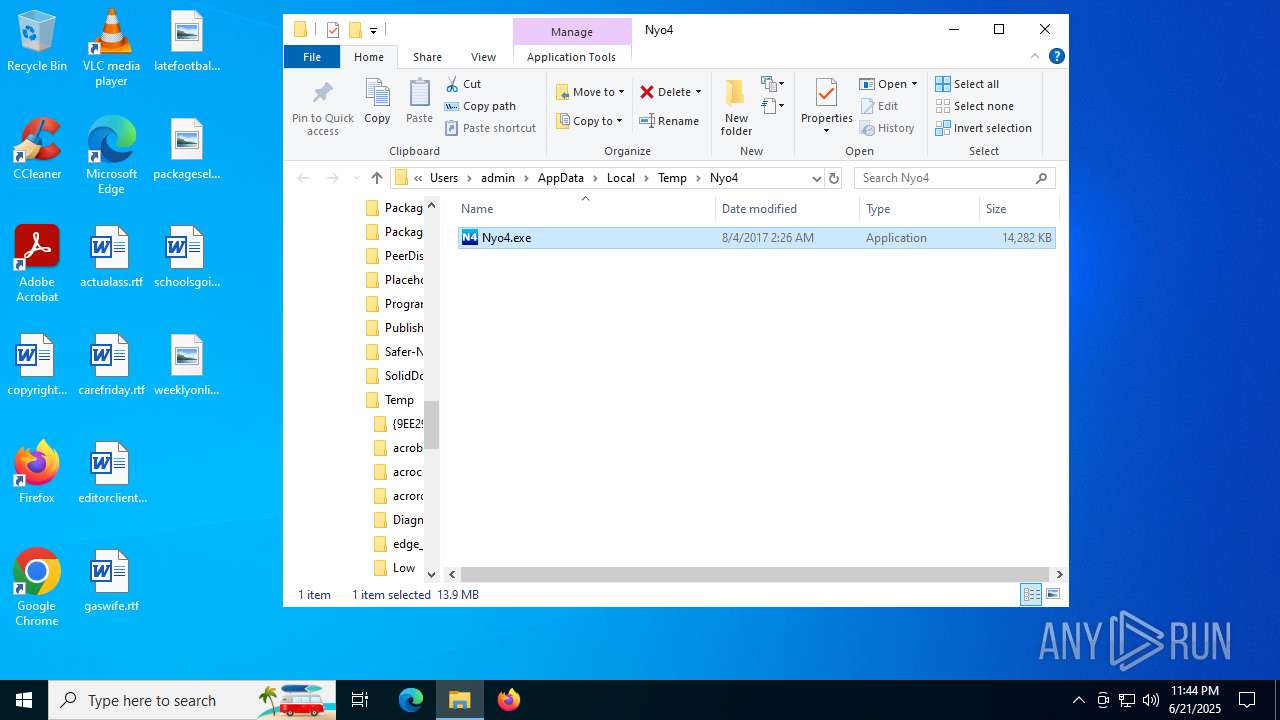
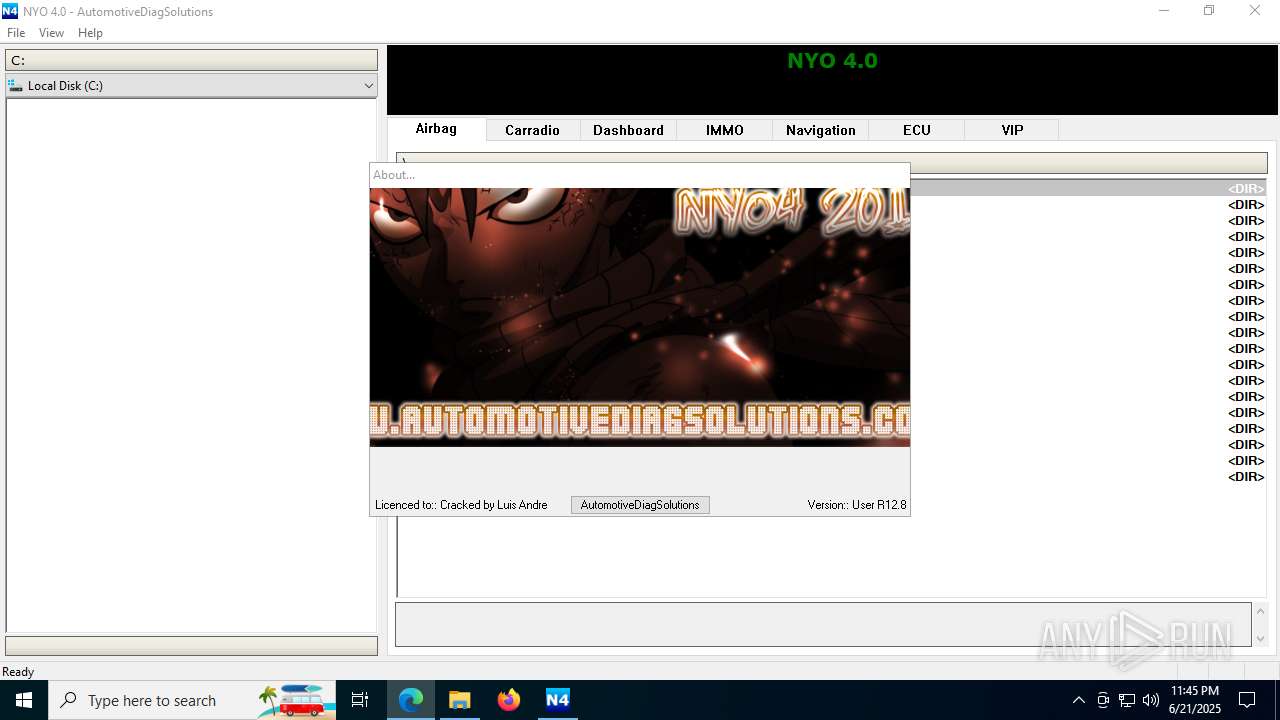
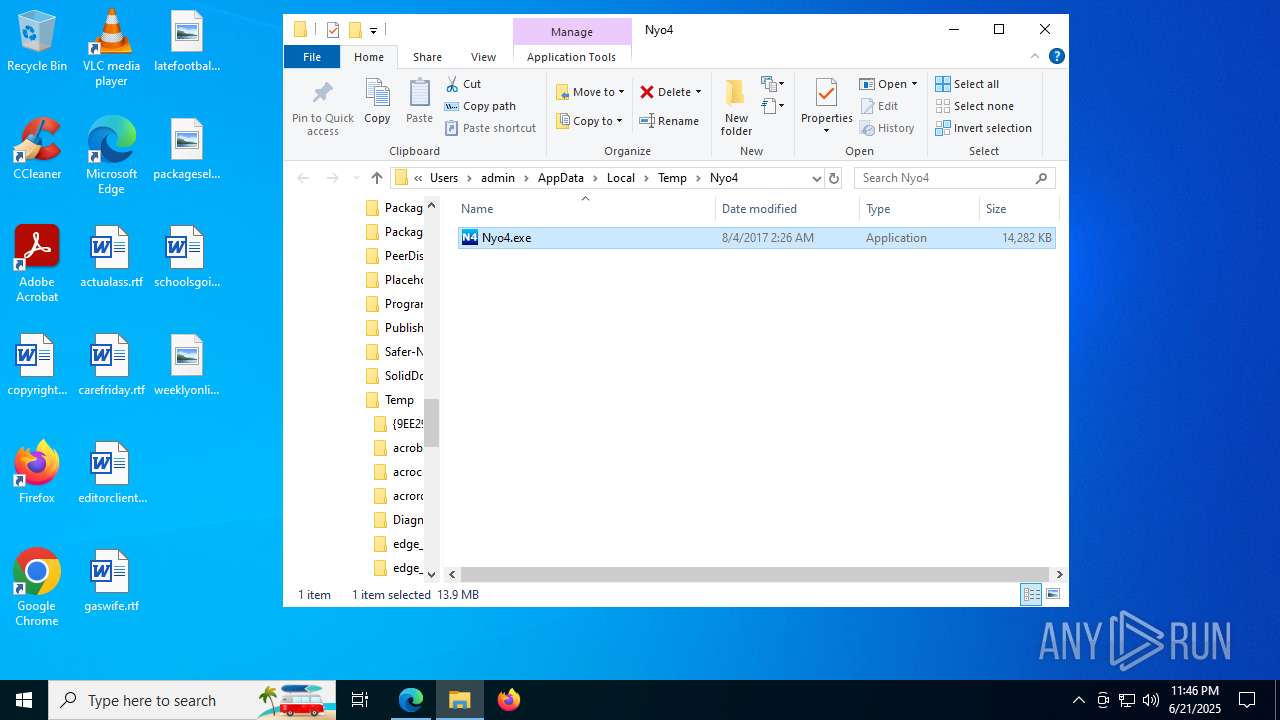
| 1512 | "C:\Users\admin\AppData\Local\Temp\Nyo4\Nyo4.exe" | C:\Users\admin\AppData\Local\Temp\Nyo4\Nyo4.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Project MFC Application Exit code: 3221225477 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 1568 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=6952,i,7667650087338164688,3727906836943878398,262144 --variations-seed-version --mojo-platform-channel-handle=7012 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1576 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=4924,i,7667650087338164688,3727906836943878398,262144 --variations-seed-version --mojo-platform-channel-handle=7120 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1604 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --always-read-main-dll --field-trial-handle=3624,i,7667650087338164688,3727906836943878398,262144 --variations-seed-version --mojo-platform-channel-handle=3564 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1644 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 6540 -s 1776 | C:\Windows\SysWOW64\WerFault.exe | Nyo4.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1700 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 6124 -s 1376 | C:\Windows\SysWOW64\WerFault.exe | Nyo4.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1808 | "C:\Users\admin\AppData\Local\Temp\Nyo4\Nyo4.exe" | C:\Users\admin\AppData\Local\Temp\Nyo4\Nyo4.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Project MFC Application Exit code: 3221226540 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
Total events
49 561
Read events
49 446
Write events
95
Delete events
20
Modification events
| (PID) Process: | (6652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Nyo4.rar | |||
| (PID) Process: | (6652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6652) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
Executable files
13
Suspicious files
143
Text files
59
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5620 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_Nyo4.exe_be8feac129fcbc1d339dd030f4a2165fe70f981_8016037e_a2c18ba9-7f5c-4bab-94cf-0420c1732dca\Report.wer | — | |
MD5:— | SHA256:— | |||
| 1700 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_Nyo4.exe_be8feac129fcbc1d339dd030f4a2165fe70f981_8016037e_6c40c194-3ef1-49ea-8b8a-3cb4af50b7ad\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6384 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_Nyo4.exe_be8feac129fcbc1d339dd030f4a2165fe70f981_8016037e_73b7c194-799a-4df2-ae15-04c5cf9bc776\Report.wer | — | |
MD5:— | SHA256:— | |||
| 5620 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER80B.tmp.xml | xml | |
MD5:3B7B151CD2478368863AE5D85DFF9C2F | SHA256:6E6C5EF19576B2D6B601847907A3C241E99D9430079395402DCEE4E41F430830 | |||
| 5620 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER7EB.tmp.WERInternalMetadata.xml | xml | |
MD5:AAEBB372F8200D8C4CF9B43859EC65A0 | SHA256:9CAC08B0A68F58BAD11CECA5C26706F86A870BF5517DB00C6D5FCCC8ACCDEAB4 | |||
| 6652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6652.18349\Nyo4.exe | executable | |
MD5:9A1D26CD273D7E555228FA754D045AC9 | SHA256:F85EFF603C72CCFBC8EC2DD8CA62AC47FBF41F327494080C30B43382C1393BB6 | |||
| 3624 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_Nyo4.exe_be8feac129fcbc1d339dd030f4a2165fe70f981_8016037e_a1a38a62-e468-4d06-95a6-c4e274269b86\Report.wer | — | |
MD5:— | SHA256:— | |||
| 1700 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER46F7.tmp.dmp | binary | |
MD5:696161D243E5AC4CBBAAB75ECBF51D49 | SHA256:7F2296AB136E0546182D62011D564513DEFB72AADE486FDD90A1ACC571FDD6DF | |||
| 5620 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\Nyo4.exe.6940.dmp | binary | |
MD5:DAED9E13DE6906644C98D31FBF3A3984 | SHA256:24696644D0CD9F71D1F95F86E737571C736B561E69F3E9536459C32031F760CE | |||
| 1700 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER4766.tmp.xml | xml | |
MD5:5A10487FC8D0D9D31E316C517623D7DD | SHA256:309244FACD689A2FB8CC947B24F65120B165E298432041D90097B2EF46D7FCF1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
152
DNS requests
85
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3476 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2764 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3476 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1700 | WerFault.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1700 | WerFault.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
6892 | msedge.exe | GET | 200 | 150.171.27.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:sBr6CtWrRCLt45w6gTR5bNT0Mutq_4a20-7tR4EgVZY&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6012 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3476 | SIHClient.exe | 4.245.163.56:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3476 | SIHClient.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3476 | SIHClient.exe | 40.69.42.241:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Nyo4.exe | FTH: (6200): *** Fault tolerant heap shim applied to current process. This is usually due to previous crashes. ***
|
Nyo4.exe | FTH: (4372): *** Fault tolerant heap shim applied to current process. This is usually due to previous crashes. ***
|