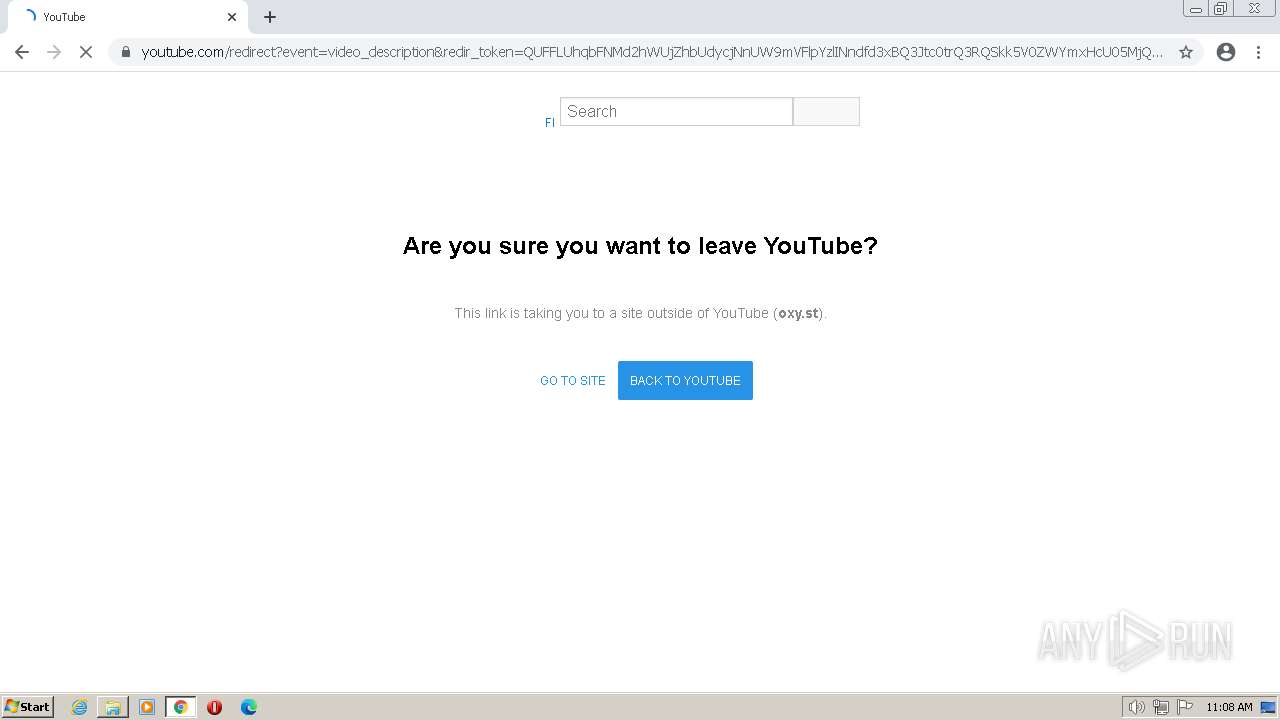
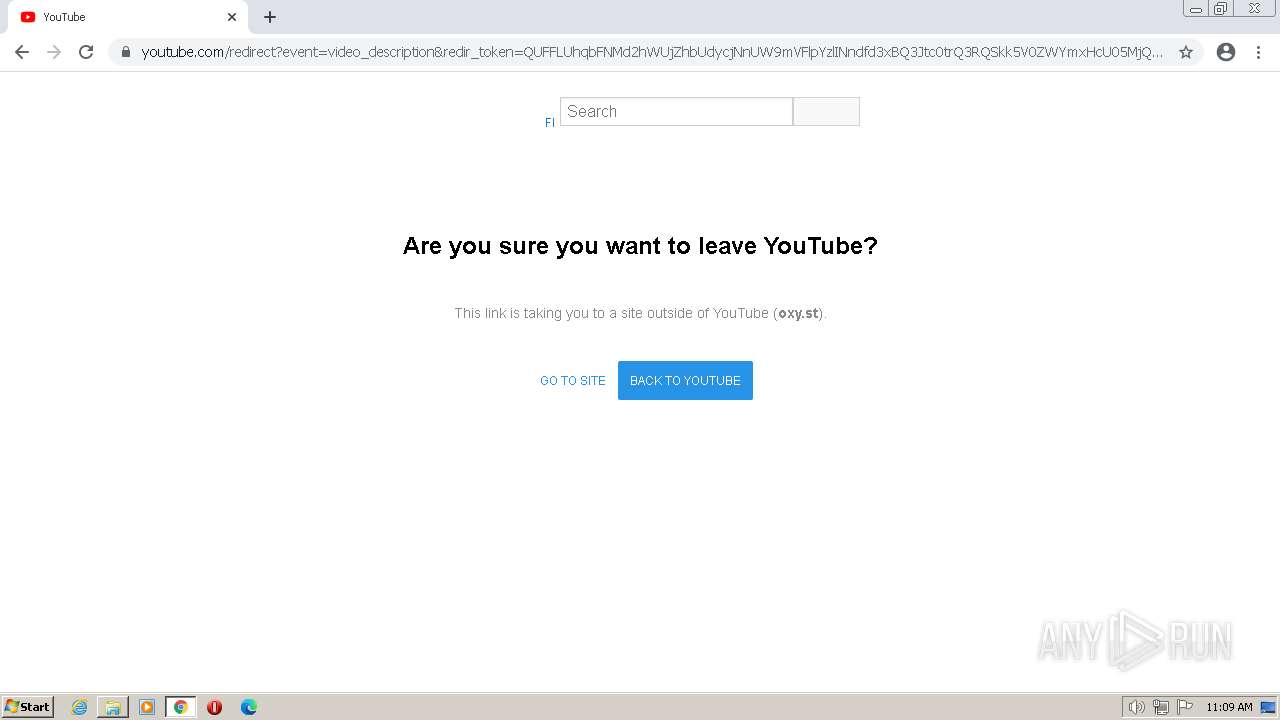
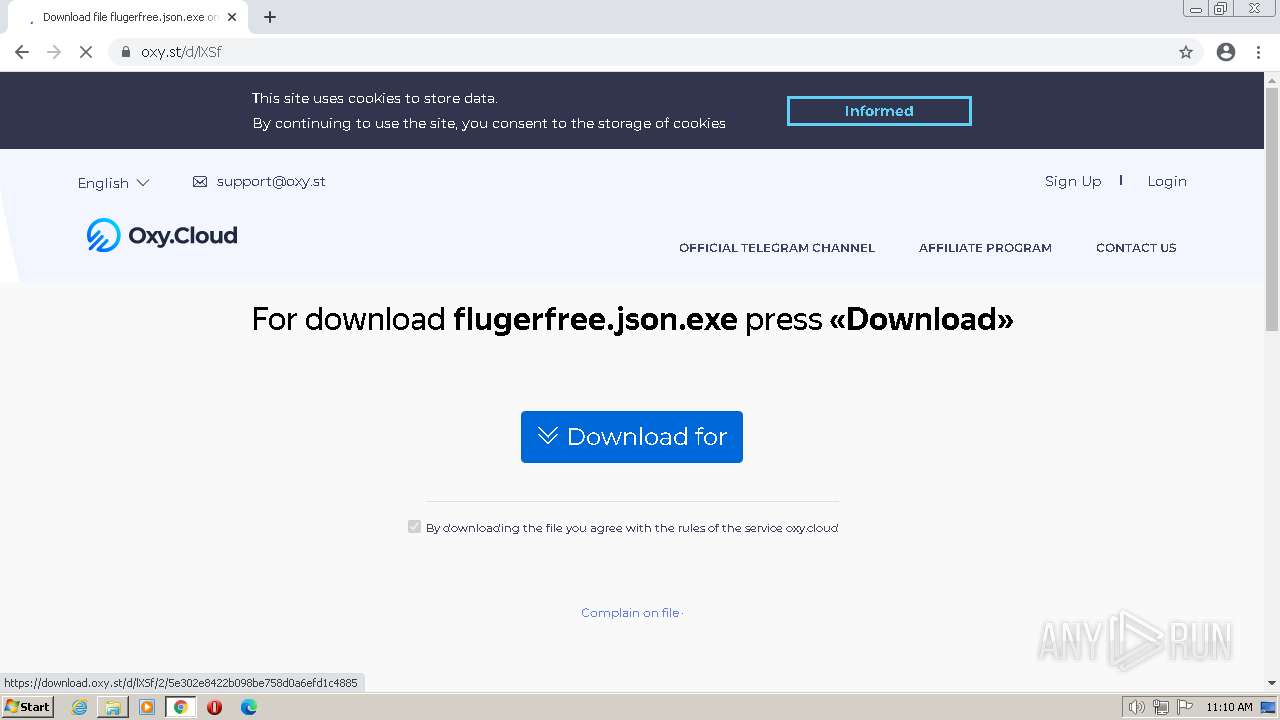
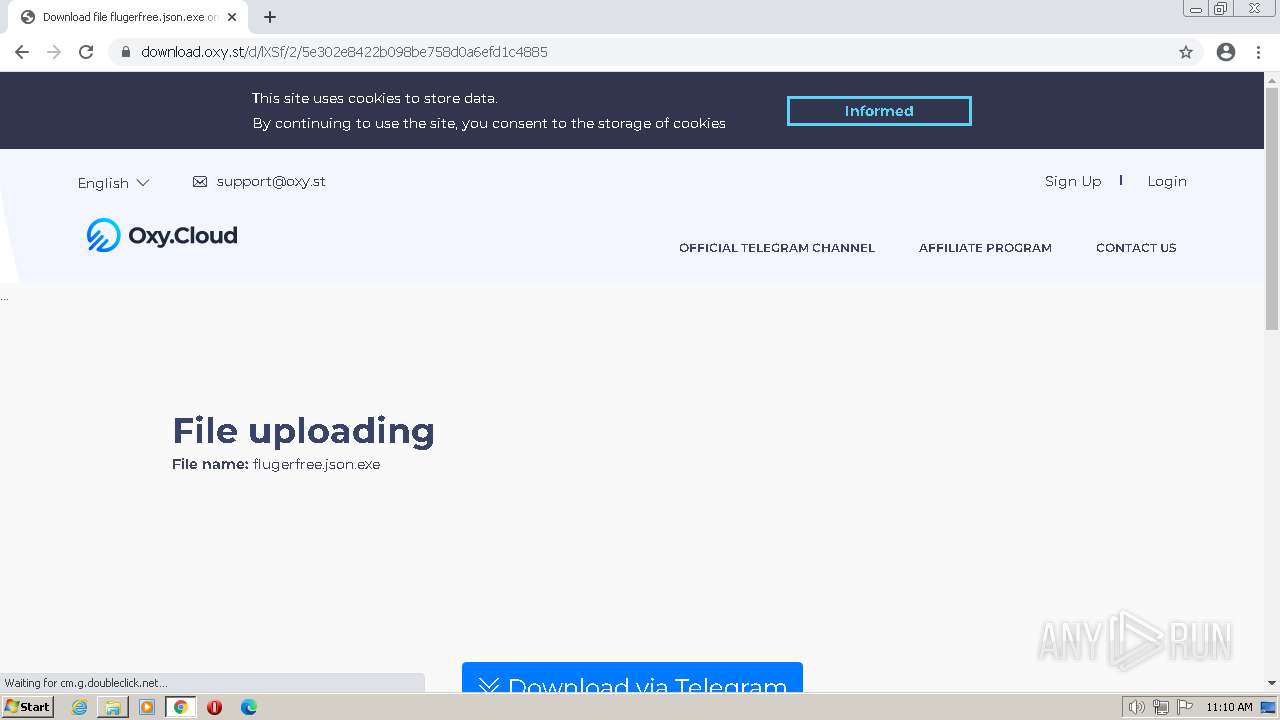
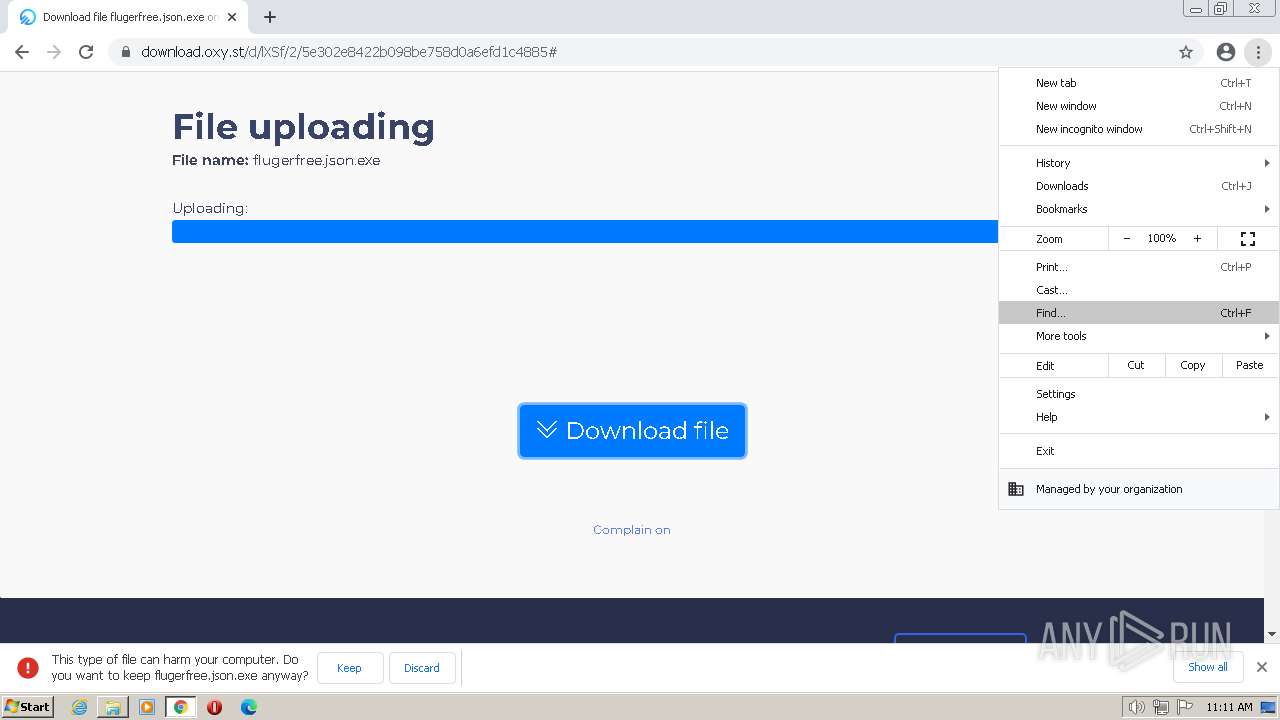
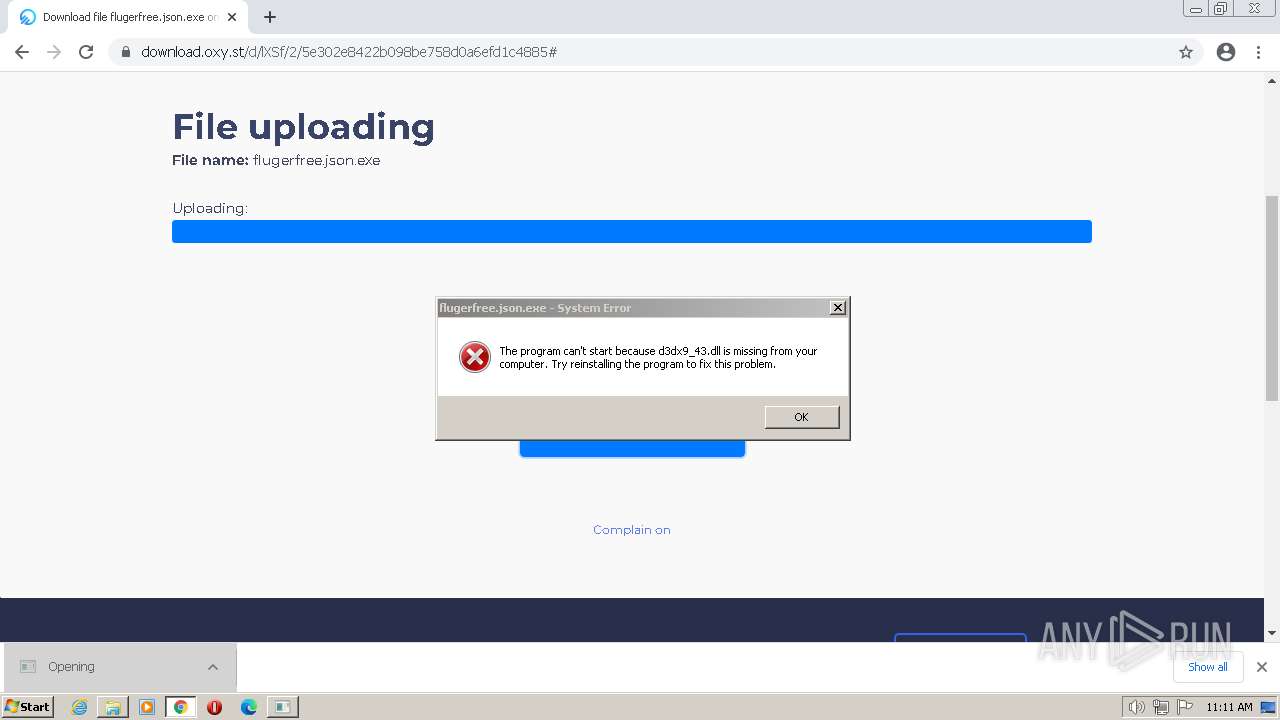
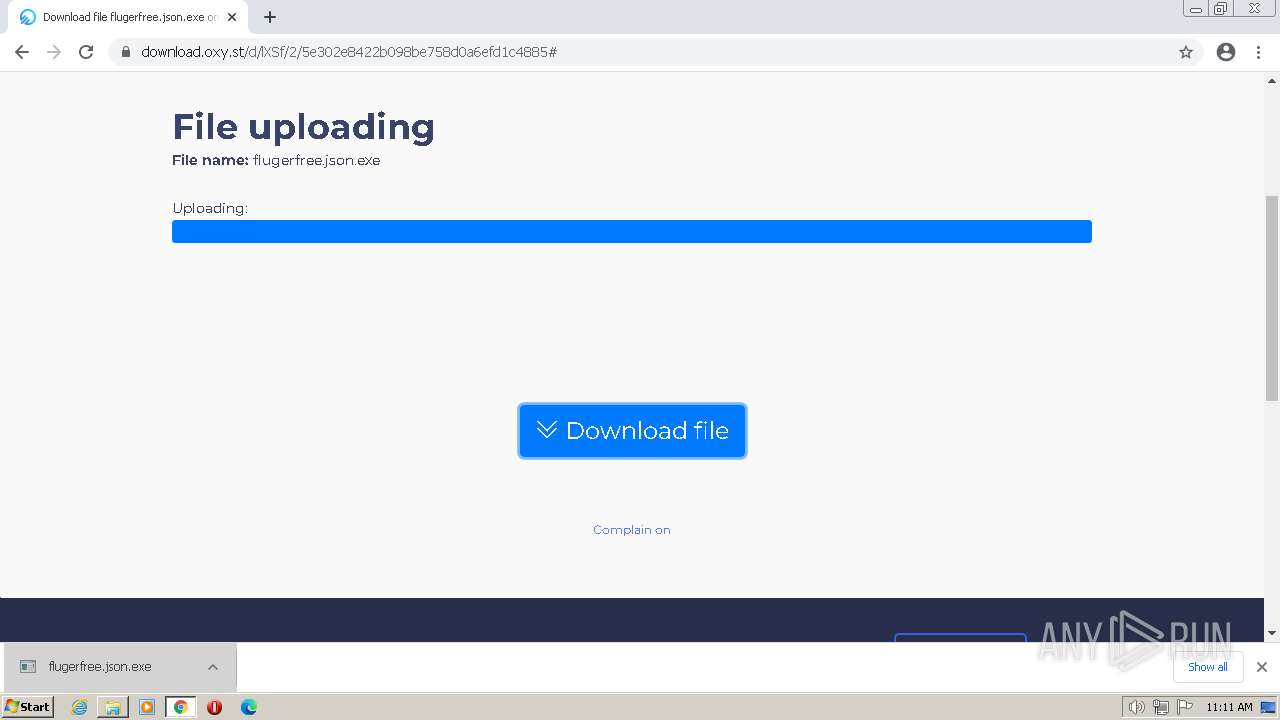
| URL: | https://www.youtube.com/redirect?event=video_description&redir_token=QUFFLUhqbFNMd2hWUjZhbUdycjNnUW9mVFlpYzlINndfd3xBQ3Jtc0trQ3RQSkk5V0ZWYmxHcU05MjQwTGRtVmg5Y2lMd2l4NkVVb194QThOWWhZX09vaEhPUE5mc2NUdjMzbzB4Uk1LV3VHczc1RDNXUmV4OUlpaGw5WFVjcUxDTFJEWjRmZkQ2UVJ0UEpNQTh1SHRLV202UQ&q=https%3A%2F%2Foxy.st%2Fd%2FlXSf&v=T5Z7USDEVlg |
| Full analysis: | https://app.any.run/tasks/42dc5e5d-25dd-480e-98c5-5c3fc1210061 |
| Verdict: | Malicious activity |
| Analysis date: | July 14, 2023, 10:07:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 66E02618DD9B88836C381653BE9B05AC |
| SHA1: | FA340CA4C7C915F110EC11DAD828F52298EB7070 |
| SHA256: | 854A3A86D87B4F287C86E31FC8FC109E59D378AD7DB26BBA5B66343FC73EFF0C |
| SSDEEP: | 6:2OLUxGKmKLqZYW6y35TR+QTZC4hJNcPfhqNkIGqKIr33kdD2t+w3H3zekP89N:2jGRfY63Ng8CONuMk+KIr3kdD2t+kZP2 |
MALICIOUS
Application was dropped or rewritten from another process
- flugerfree.json.exe (PID: 3312)
- flugerfree.json.exe (PID: 3496)
SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 3596)
- msedge.exe (PID: 2136)
- chrome.exe (PID: 3872)
Manual execution by a user
- chrome.exe (PID: 3872)
- explorer.exe (PID: 2288)
- wmpnscfg.exe (PID: 2804)
The process checks LSA protection
- explorer.exe (PID: 2288)
- wmpnscfg.exe (PID: 2804)
Reads the computer name
- wmpnscfg.exe (PID: 2804)
Checks supported languages
- wmpnscfg.exe (PID: 2804)
The process uses the downloaded file
- chrome.exe (PID: 1880)
- chrome.exe (PID: 3872)
Executable content was dropped or overwritten
- chrome.exe (PID: 3152)
- chrome.exe (PID: 3872)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 2804)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
86
Monitored processes
45
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 736 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1012,10529656361294815210,3065056292004890989,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3632 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 952 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1012,10529656361294815210,3065056292004890989,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1020 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 972 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1012,10529656361294815210,3065056292004890989,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3032 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1008 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --field-trial-handle=1012,10529656361294815210,3065056292004890989,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=icon_reader --mojo-platform-channel-handle=3328 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1564 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,10529656361294815210,3065056292004890989,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=20 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3456 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1760 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3596 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1880 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --field-trial-handle=1012,10529656361294815210,3065056292004890989,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=2184 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2136 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --from-ie-to-edge=3 --ie-frame-hwnd=500ce | C:\Program Files\Microsoft\Edge\Application\msedge.exe | ie_to_edge_stub.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2288 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2348 | "C:\Program Files\Microsoft\Edge\Application\109.0.1518.115\BHO\ie_to_edge_stub.exe" --from-ie-to-edge=3 --ie-frame-hwnd=500ce | C:\Program Files\Microsoft\Edge\Application\109.0.1518.115\BHO\ie_to_edge_stub.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: IEToEdge BHO Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
20 564
Read events
20 323
Write events
230
Delete events
11
Modification events
| (PID) Process: | (3596) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3596) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3596) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3596) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3596) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3596) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3596) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3596) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3596) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3596) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
5
Suspicious files
136
Text files
156
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2136 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2136 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF121c2b.TMP | — | |
MD5:— | SHA256:— | |||
| 2136 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2136 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF121c3b.TMP | — | |
MD5:— | SHA256:— | |||
| 2136 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad\settings.dat | binary | |
MD5:A2B913D3BC9B6344C76B056712064197 | SHA256:CC7E7F39A2B36FFD7D6EC45A4AA70BFB8DBEBC58EEB784D08218B0036D3AD564 | |||
| 1760 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:1C86851667ADB62DE38C1F6B7E29F23A | SHA256:F3DCCDF242C7E14F98A60D06EA21ECEF4FFC536A1E618999C7684B3747F24360 | |||
| 2136 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Vpn Tokens | binary | |
MD5:9BF00DCB858DEED5E4A1F2408E3C415D | SHA256:2DE69D17DE02A799F3015A68A2A036379059424F432167F519481BCD9519FF0D | |||
| 2136 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgeCoupons\coupons_data.db\LOG.old | text | |
MD5:52078B219C44C663CEBCA6616A8D5DCD | SHA256:A7D54C974840EDE60E5EE9200DBC06F9157076DC279C21695EA6138CF16253C7 | |||
| 1760 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 2996 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\CrashpadMetrics.pma | binary | |
MD5:886E82F2CA62ECCCE64601B30592078A | SHA256:E5E13D53601100FF3D6BB71514CBCCC4C73FE9B7EF5E930100E644187B42948E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
164
DNS requests
71
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1760 | iexplore.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCC9WDlwqYtEgkfLti89Qqj | US | binary | 472 b | whitelisted |
1096 | svchost.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?e13e53bb8acf1489 | US | compressed | 62.3 Kb | whitelisted |
3596 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://crl3.digicert.com/Omniroot2025.crl | US | binary | 7.78 Kb | whitelisted |
1760 | iexplore.exe | GET | 200 | 142.250.185.67:80 | http://crl.pki.goog/gsr1/gsr1.crl | US | binary | 1.70 Kb | whitelisted |
1760 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | US | binary | 471 b | whitelisted |
1760 | iexplore.exe | GET | 200 | 67.27.157.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?14517cca9e32d30d | US | compressed | 4.70 Kb | whitelisted |
1760 | iexplore.exe | GET | 200 | 67.27.157.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?67c23a11a398e078 | US | compressed | 4.70 Kb | whitelisted |
3596 | iexplore.exe | GET | 200 | 8.238.34.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e42dcc3752285f3b | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3388 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1760 | iexplore.exe | 172.217.18.110:443 | www.youtube.com | GOOGLE | US | whitelisted |
1760 | iexplore.exe | 88.221.179.76:443 | go.microsoft.com | AKAMAI-AS | GB | suspicious |
1760 | iexplore.exe | 67.27.157.126:80 | ctldl.windowsupdate.com | LEVEL3 | US | suspicious |
3596 | iexplore.exe | 2.16.153.222:443 | www.bing.com | Akamai International B.V. | NL | suspicious |
1760 | iexplore.exe | 172.217.18.3:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
3596 | iexplore.exe | 67.27.157.126:80 | ctldl.windowsupdate.com | LEVEL3 | US | suspicious |
2136 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
go.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
config.edge.skype.com |
| malicious |
edge.microsoft.com |
| whitelisted |
crl.pki.goog |
| whitelisted |
clients2.google.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1096 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .to TLD |
1096 | svchost.exe | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .icu Domain |
3152 | chrome.exe | Potentially Bad Traffic | ET INFO Suspicious Domain (*.icu) in TLS SNI |
1096 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .to TLD |