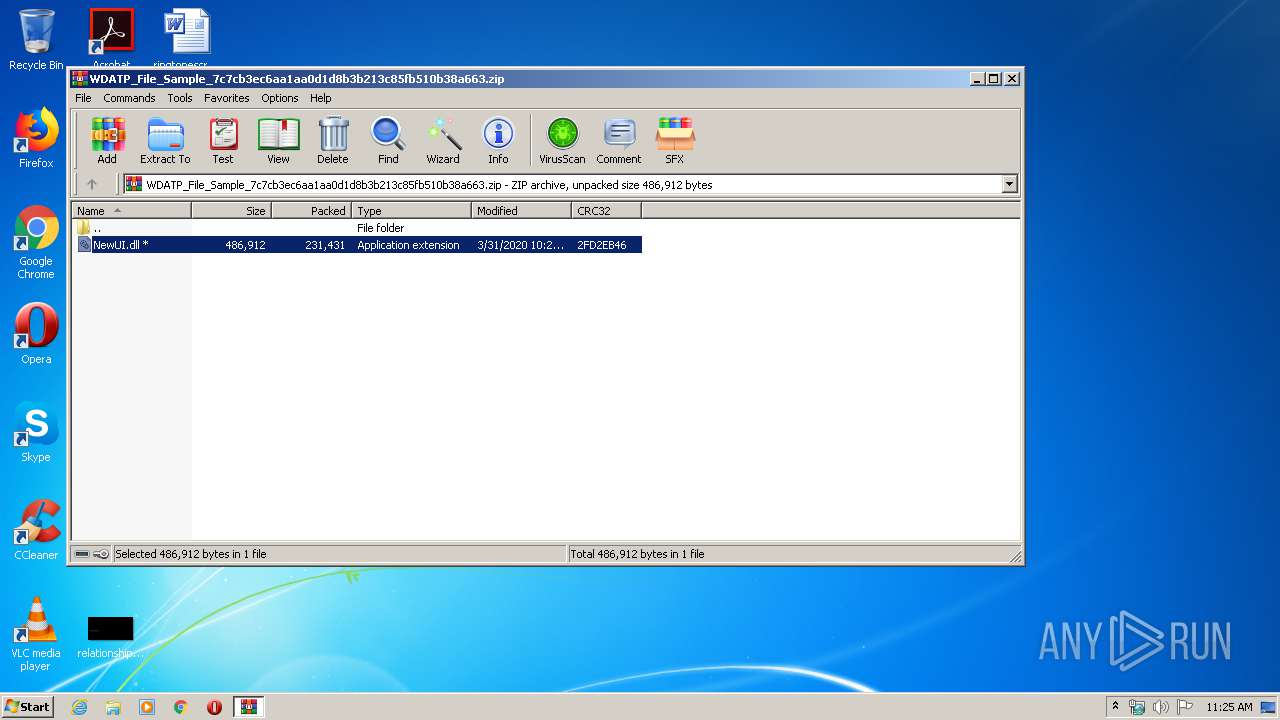
| File name: | WDATP_File_Sample_7c7cb3ec6aa1aa0d1d8b3b213c85fb510b38a663.zip |
| Full analysis: | https://app.any.run/tasks/ca933157-0899-4fbd-a4db-768442f89bc8 |
| Verdict: | Malicious activity |
| Analysis date: | March 31, 2020, 10:24:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 771E0A62B5D445CAD0225C083EDA309E |
| SHA1: | 096ED9ECBF2709C7147DEF1FCC7D9BCF3EBFDC7B |
| SHA256: | 853A35447811EFF437188F987B50136643B9A12D38E9062B8E20FD6D093C0C5E |
| SSDEEP: | 3072:MKJbgAqvV39dL8nqsmGIR9ssSrXmFVZ997Db3GXorsGtmXR5NwSOvJ0pZM4:MycNNl8nyWrWVZb7nG4rivNLBI4 |
MALICIOUS
Loads dropped or rewritten executable
- regsvr32.exe (PID: 3516)
- explorer.exe (PID: 372)
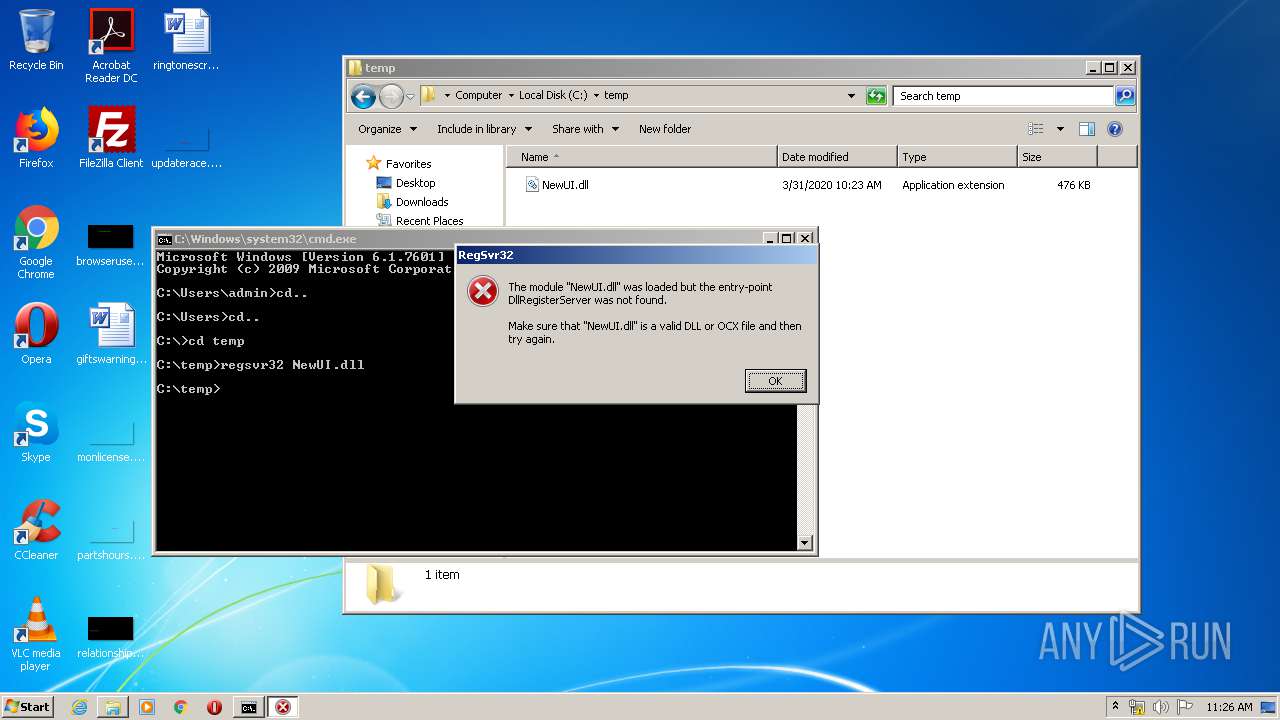
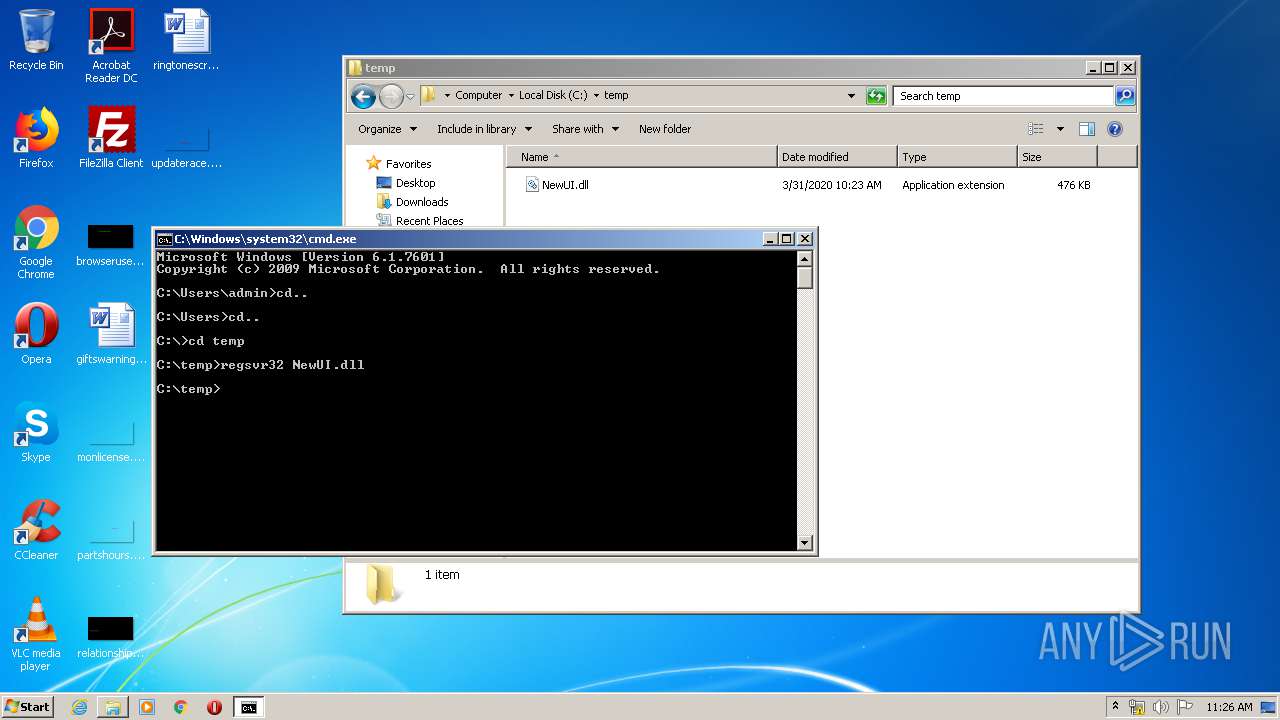
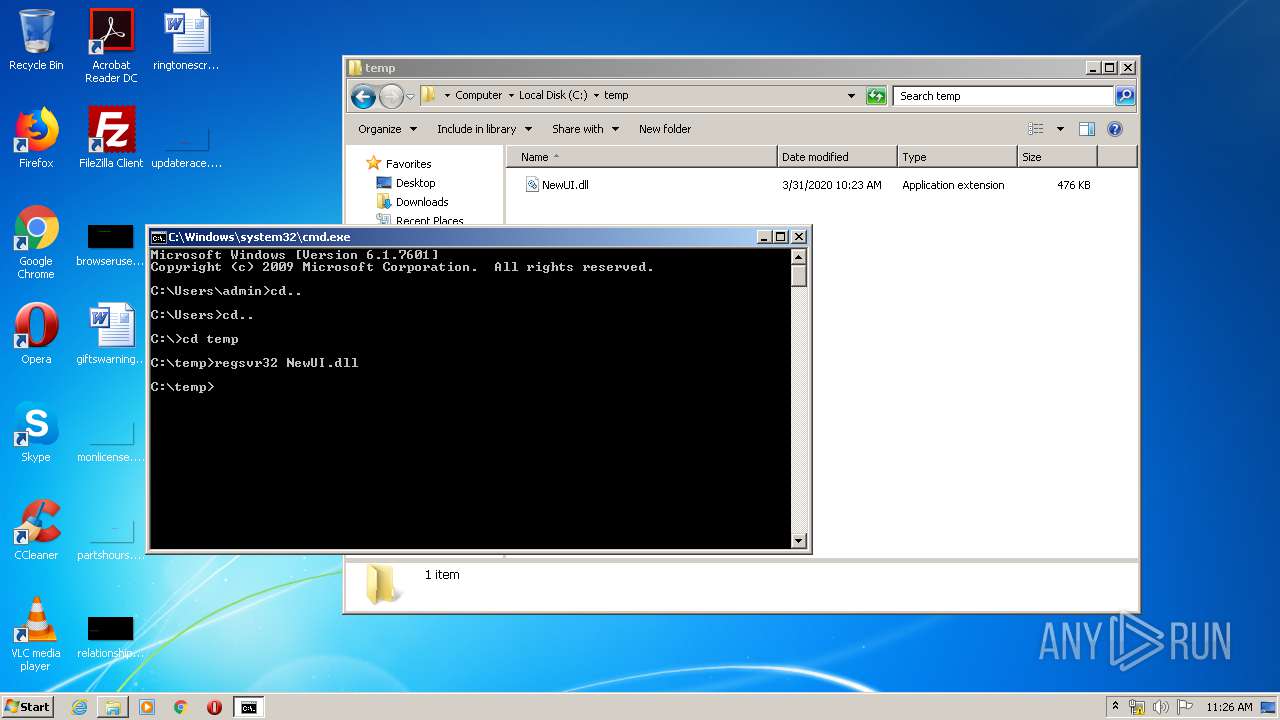
Registers / Runs the DLL via REGSVR32.EXE
- cmd.exe (PID: 440)
Runs app for hidden code execution
- explorer.exe (PID: 372)
SUSPICIOUS
Starts CMD.EXE for commands execution
- explorer.exe (PID: 372)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1232)
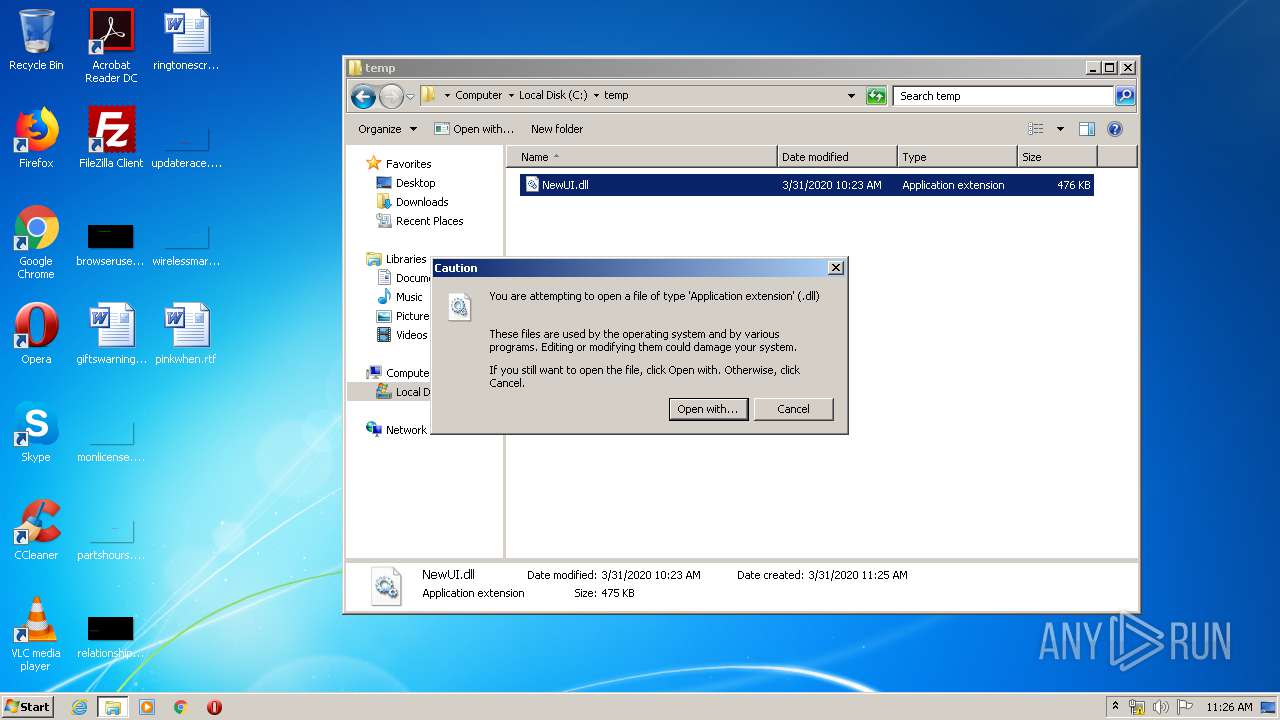
Uses RUNDLL32.EXE to load library
- explorer.exe (PID: 372)
Creates files in the user directory
- explorer.exe (PID: 372)
INFO
Manual execution by user
- cmd.exe (PID: 440)
- rundll32.exe (PID: 2908)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:03:31 10:23:27 |
| ZipCRC: | 0x2fd2eb46 |
| ZipCompressedSize: | 231431 |
| ZipUncompressedSize: | 486912 |
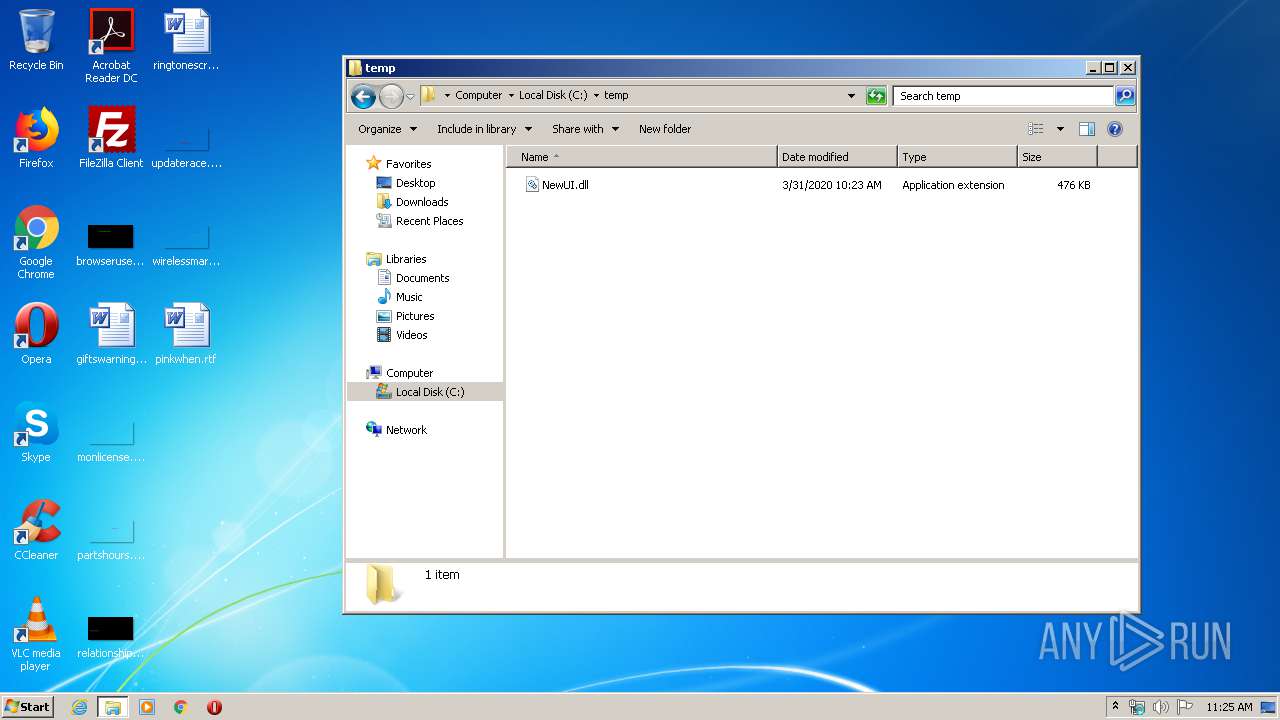
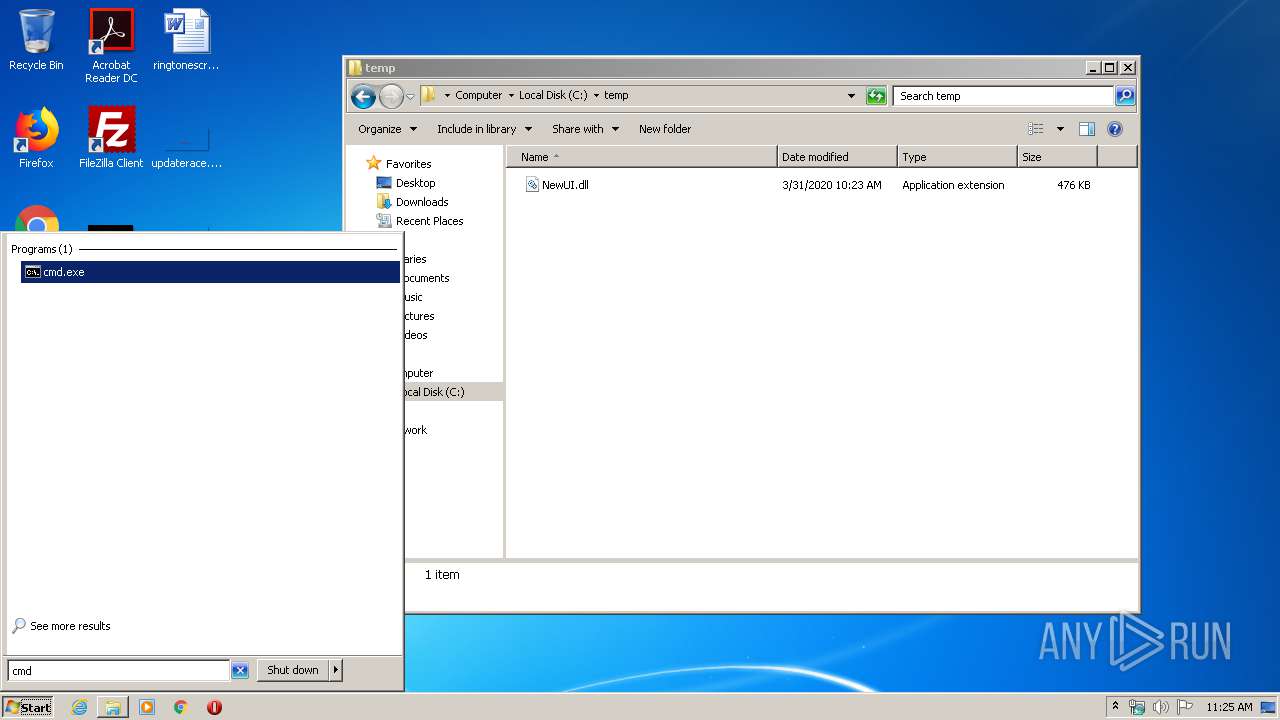
| ZipFileName: | NewUI.dll |
Total processes
41
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 372 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 440 | "C:\Windows\system32\cmd.exe" | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1232 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\WDATP_File_Sample_7c7cb3ec6aa1aa0d1d8b3b213c85fb510b38a663.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2908 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\temp\NewUI.dll | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
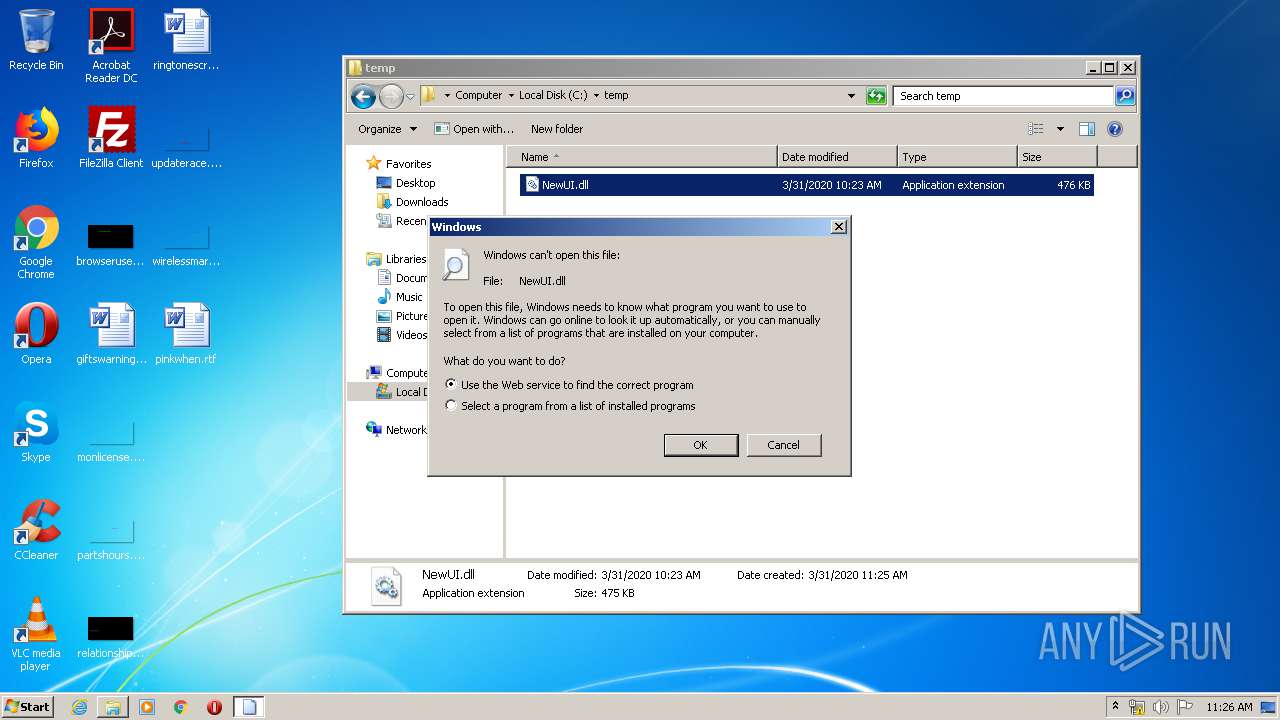
| 3516 | regsvr32 NewUI.dll | C:\Windows\system32\regsvr32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 4 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
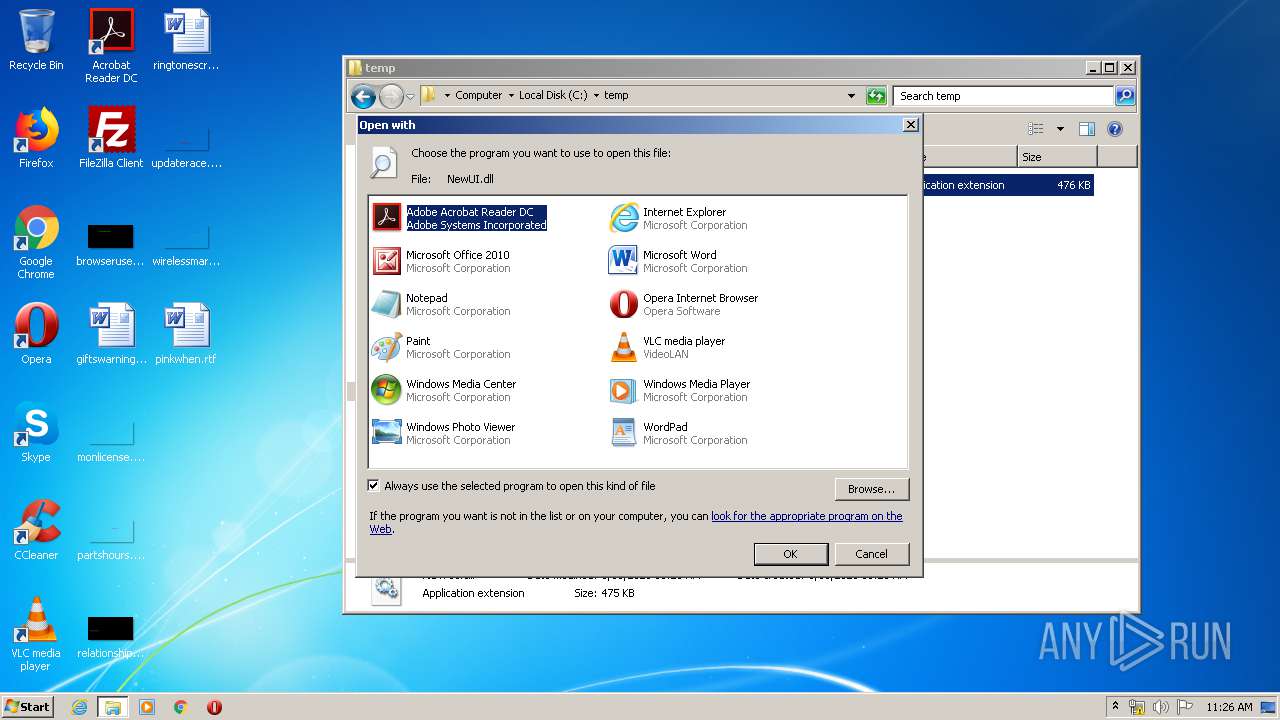
| 3832 | "C:\Windows\system32\NOTEPAD.EXE" C:\temp\NewUI.dll | C:\Windows\system32\NOTEPAD.EXE | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 322
Read events
900
Write events
422
Delete events
0
Modification events
| (PID) Process: | (1232) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1232) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1232) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1232) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\WDATP_File_Sample_7c7cb3ec6aa1aa0d1d8b3b213c85fb510b38a663.zip | |||
| (PID) Process: | (1232) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1232) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1232) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1232) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (372) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
| (PID) Process: | (372) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
Executable files
1
Suspicious files
0
Text files
0
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1232 | WinRAR.exe | C:\temp | — | |
MD5:— | SHA256:— | |||
| 372 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\temp.lnk | lnk | |
MD5:— | SHA256:— | |||
| 372 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\918e0ecb43d17e23.automaticDestinations-ms | automaticdestinations-ms | |
MD5:— | SHA256:— | |||
| 372 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\1b4dd67f29cb1962.automaticDestinations-ms | automaticdestinations-ms | |
MD5:— | SHA256:— | |||
| 372 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\NewUI.dll.lnk | lnk | |
MD5:— | SHA256:— | |||
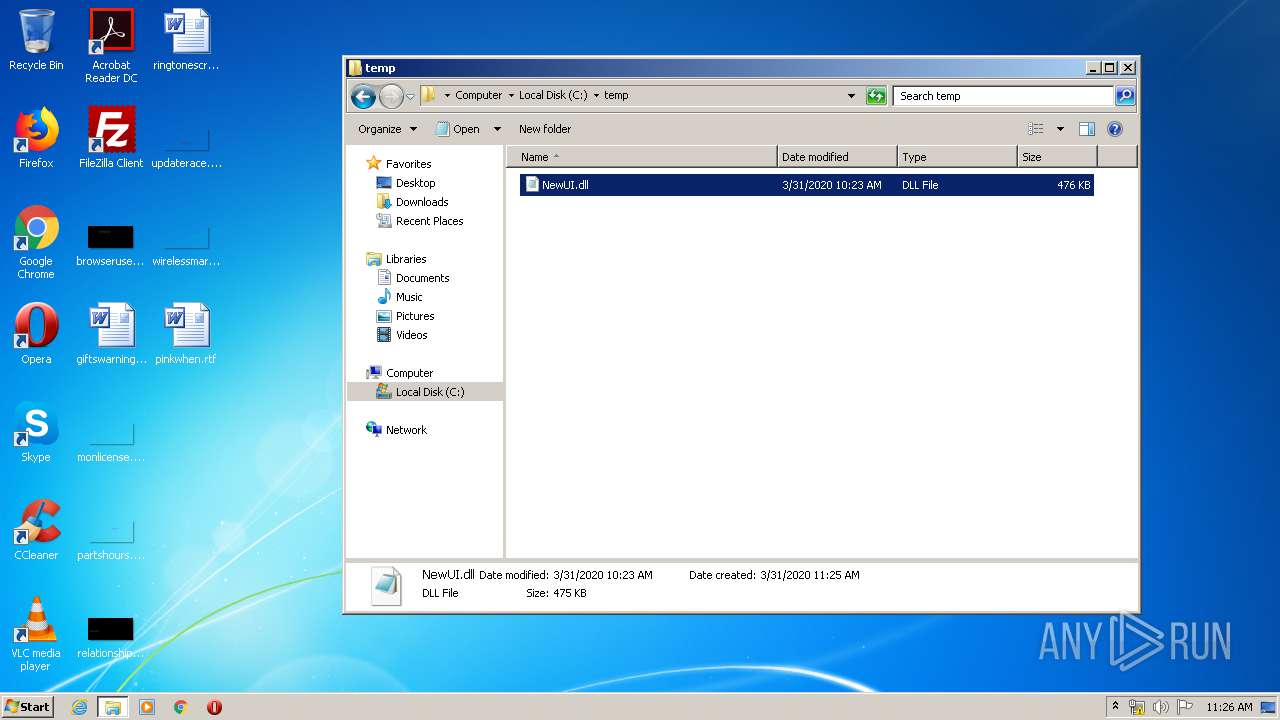
| 1232 | WinRAR.exe | C:\temp\NewUI.dll | executable | |
MD5:69AE2C900632AF2437786C7D65504667 | SHA256:05F85FF76F8BB96424C0DF7378661C3C1349F0DE393AC7FF9C87B2779366C1D6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report