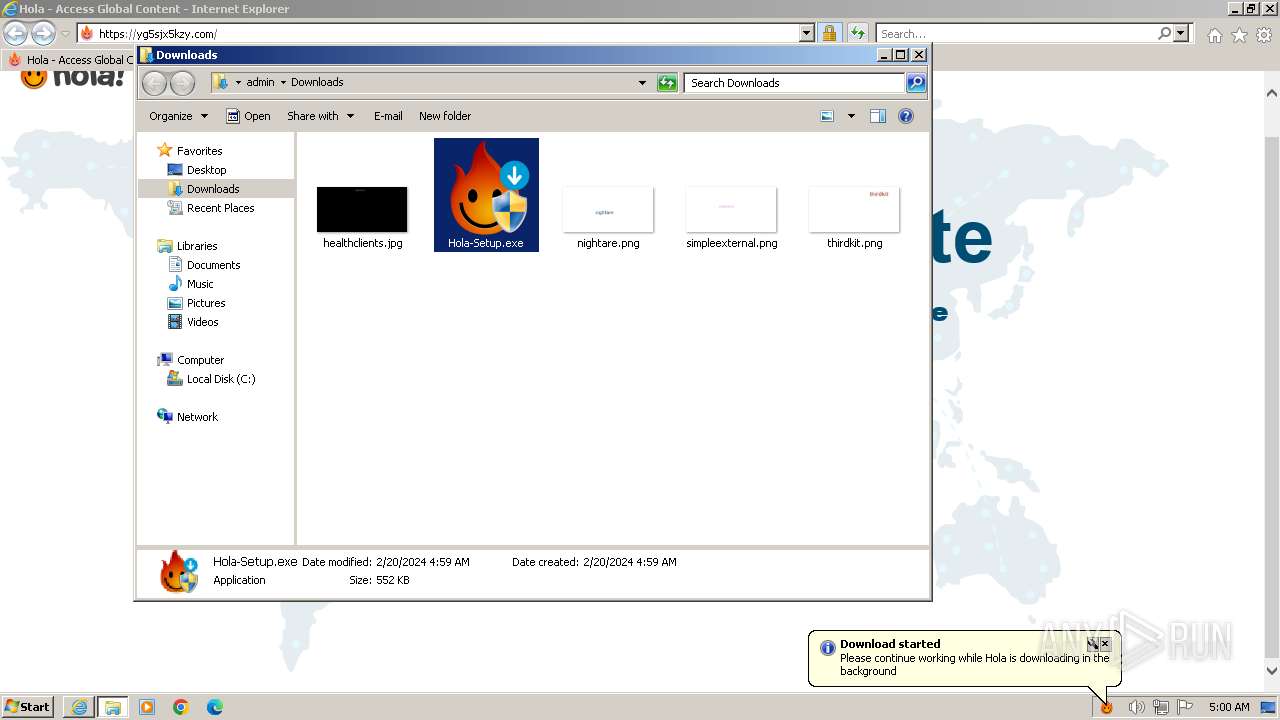
| URL: | yg5sjx5kzy.com |
| Full analysis: | https://app.any.run/tasks/600ed557-7d71-4ca7-b794-8865a1207e70 |
| Verdict: | Malicious activity |
| Analysis date: | February 20, 2024, 04:59:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 623592D45FED9C2A94B31570B4B70753 |
| SHA1: | 11578C6D0AC262EBE9C410B52D94D84D402A70DF |
| SHA256: | 8507CB6E18B9232D11DAB1BB024A7A12AC4EB1B6D29A6CB4E5B4CA4763088384 |
| SSDEEP: | 3:z2Mn:qM |
MALICIOUS
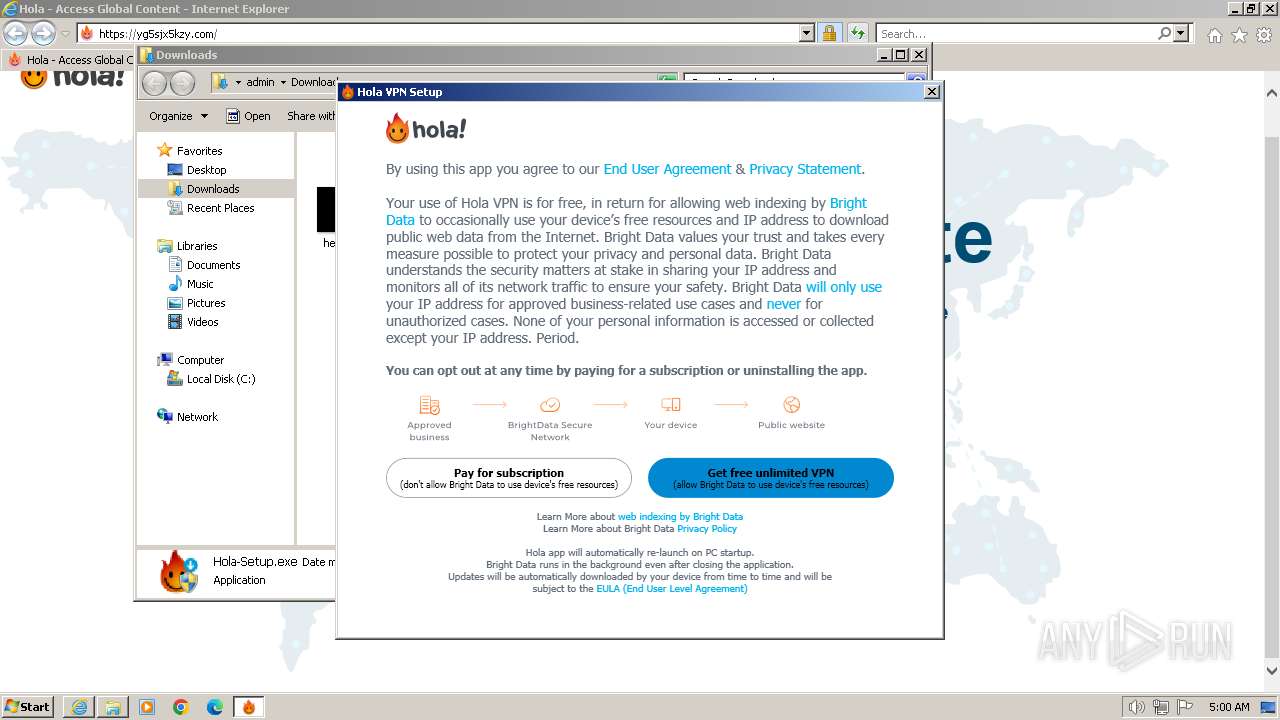
Drops the executable file immediately after the start
- Hola-Setup.exe (PID: 2888)
SUSPICIOUS
Checks Windows Trust Settings
- Hola-Setup-Core.exe (PID: 1556)
- Hola-Setup-Core.exe (PID: 2972)
Executable content was dropped or overwritten
- Hola-Setup.exe (PID: 2888)
Reads security settings of Internet Explorer
- Hola-Setup-Core.exe (PID: 1556)
- Hola-Setup-Core.exe (PID: 2972)
Reads settings of System Certificates
- Hola-Setup-Core.exe (PID: 1556)
- Hola-Setup-Core.exe (PID: 2972)
Adds/modifies Windows certificates
- Hola-Setup-Core.exe (PID: 1556)
Application launched itself
- Hola-Setup-Core.exe (PID: 1556)
Reads the Internet Settings
- Hola-Setup-Core.exe (PID: 1556)
- Hola-Setup-Core.exe (PID: 2972)
Executes as Windows Service
- PresentationFontCache.exe (PID: 1792)
INFO
Executable content was dropped or overwritten
- iexplore.exe (PID: 3664)
- iexplore.exe (PID: 3656)
Checks supported languages
- Hola-Setup.exe (PID: 2888)
- Hola-Setup-Core.exe (PID: 1556)
- Hola-Setup-Core.exe (PID: 2972)
- PresentationFontCache.exe (PID: 1792)
Application launched itself
- iexplore.exe (PID: 3656)
Drops the executable file immediately after the start
- iexplore.exe (PID: 3664)
- iexplore.exe (PID: 3656)
Reads the computer name
- Hola-Setup-Core.exe (PID: 1556)
- Hola-Setup-Core.exe (PID: 2972)
- PresentationFontCache.exe (PID: 1792)
Create files in a temporary directory
- Hola-Setup.exe (PID: 2888)
- Hola-Setup-Core.exe (PID: 1556)
- Hola-Setup-Core.exe (PID: 2972)
Reads the software policy settings
- Hola-Setup-Core.exe (PID: 1556)
- Hola-Setup-Core.exe (PID: 2972)
Reads the machine GUID from the registry
- Hola-Setup-Core.exe (PID: 1556)
- Hola-Setup-Core.exe (PID: 2972)
- PresentationFontCache.exe (PID: 1792)
Reads Environment values
- Hola-Setup-Core.exe (PID: 1556)
- Hola-Setup-Core.exe (PID: 2972)
Manual execution by a user
- Hola-Setup.exe (PID: 2888)
- Hola-Setup.exe (PID: 3072)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3656)
The process uses the downloaded file
- iexplore.exe (PID: 3656)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
47
Monitored processes
7
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1556 | .\Hola-Setup-Core.exe | C:\Users\admin\AppData\Local\Temp\7zSA081.tmp\Hola-Setup-Core.exe | Hola-Setup.exe | ||||||||||||
User: admin Company: Hola Networks Ltd. Integrity Level: HIGH Description: Hola VPN Setup Exit code: 0 Version: 1.0.8678.23934 Modules
| |||||||||||||||
| 1792 | C:\Windows\Microsoft.Net\Framework\v3.0\WPF\PresentationFontCache.exe | C:\Windows\Microsoft.Net\Framework\v3.0\WPF\PresentationFontCache.exe | — | services.exe | |||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: PresentationFontCache.exe Exit code: 0 Version: 3.0.6920.4902 built by: NetFXw7 Modules
| |||||||||||||||
| 2888 | "C:\Users\admin\Downloads\Hola-Setup.exe" | C:\Users\admin\Downloads\Hola-Setup.exe | explorer.exe | ||||||||||||
User: admin Company: Hola Networks Ltd. Integrity Level: HIGH Description: Hola Setup Exit code: 0 Version: 1.0.8678.23934 Modules
| |||||||||||||||
| 2972 | ".\Hola-Setup-Core.exe" --monitor 1540 | C:\Users\admin\AppData\Local\Temp\7zSA081.tmp\Hola-Setup-Core.exe | Hola-Setup-Core.exe | ||||||||||||
User: admin Company: Hola Networks Ltd. Integrity Level: HIGH Description: Hola VPN Setup Exit code: 0 Version: 1.0.8678.23934 Modules
| |||||||||||||||
| 3072 | "C:\Users\admin\Downloads\Hola-Setup.exe" | C:\Users\admin\Downloads\Hola-Setup.exe | — | explorer.exe | |||||||||||
User: admin Company: Hola Networks Ltd. Integrity Level: MEDIUM Description: Hola Setup Exit code: 3221226540 Version: 1.0.8678.23934 Modules
| |||||||||||||||
| 3656 | "C:\Program Files\Internet Explorer\iexplore.exe" "yg5sjx5kzy.com" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3664 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3656 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
33 285
Read events
33 057
Write events
159
Delete events
69
Modification events
| (PID) Process: | (3656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31089593 | |||
| (PID) Process: | (3656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31089593 | |||
| (PID) Process: | (3656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
7
Suspicious files
14
Text files
23
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3664 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:FB91282DC5831423662AA292CD50B11D | SHA256:2D0446B084643851B51B16C2EEE1D986C0F06ED76DDF056C170B544A53944B03 | |||
| 3664 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | der | |
MD5:2CDEA405E4DBE5D0B8C7C223AC2A1F22 | SHA256:457E0EBB2CDFBE5CE12B9C9679E522883CA7EBA355DECA0BE73985C4BEBB7F26 | |||
| 3664 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:B0C6EB8045E7554860FF37775BD03C6B | SHA256:3018A97408B800B105EDB0C5452813C6741ECA66BC128E1AD4312CD98CAD5A7A | |||
| 3664 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | binary | |
MD5:FB587A90A5798798CFB8745D29EE5557 | SHA256:D8FAFDA794D6F7B69CE43BD123547D18E136AED87C01CFDCD14C99B6A1166383 | |||
| 3664 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\FDCC27A142E421CAE33B19B381FB4D2D | binary | |
MD5:F2971BAF0DD40E57DBE2C03DDF346C35 | SHA256:8B38C93C4BA7433420F7ACCD749B892D4341C7BC464696E5BD4072B9229D8AC7 | |||
| 3656 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\imagestore\f7ruq93\imagestore.dat | binary | |
MD5:201F4AFC61E6BA7E7470F283C168AA90 | SHA256:23F63E5C41502A9BEF8CBE5CF050A3B011CD56D4E5ED685F9B3B129B6CF208BE | |||
| 3664 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\unsupported_ie[1].png | image | |
MD5:38DE96BE11EECF385B84CDD43D0A814B | SHA256:1CFCD41E309324FB458FCF4415D2594D1F57D82AB4C4616F9C464E2F5260AFBA | |||
| 3664 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\map[1].png | image | |
MD5:7122E8CD8DD40D0F9540DF0E394D032B | SHA256:09002156F6765153613086EFA9082601505BF2B8784B023361264B6C73367F41 | |||
| 3664 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\YKEZUMG5.htm | html | |
MD5:6E1E6142413667DE627BD1E6089770CC | SHA256:7748EC9758B70C24B75FB04BEFACFB67B3DD93D93D7549E17C31D2864F080DDE | |||
| 3664 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\FDCC27A142E421CAE33B19B381FB4D2D | binary | |
MD5:F1D2C6BF7AD343D214B18538E22A7086 | SHA256:EC4C7EF9E4152C12FFA17C7A84BF98DE782DFE23735F236198D91666E5B2AEFF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
45
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3664 | iexplore.exe | GET | 304 | 23.32.238.219:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?148aa66c17cd606b | unknown | — | — | unknown |
3656 | iexplore.exe | GET | 304 | 23.32.238.219:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?70d85e3b0e586cab | unknown | — | — | unknown |
3664 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEQCkPYbZy1zGfVhAfBmc5PBx | unknown | binary | 472 b | unknown |
3656 | iexplore.exe | GET | 304 | 23.32.238.219:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b23edf5cfbe16fd7 | unknown | — | — | unknown |
3656 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 312 b | unknown |
1080 | svchost.exe | GET | 200 | 23.32.238.232:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?e2ddf83a2417bb20 | unknown | compressed | 65.2 Kb | unknown |
3656 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://crl3.digicert.com/DigiCertGlobalRootG2.crl | unknown | binary | 1.14 Kb | unknown |
3656 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
3656 | iexplore.exe | GET | — | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAxq6XzO1ZmDhpCgCp6lMhQ%3D | unknown | — | — | unknown |
3664 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | binary | 2.18 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3664 | iexplore.exe | 107.22.193.119:80 | yg5sjx5kzy.com | AMAZON-AES | US | unknown |
3664 | iexplore.exe | 107.22.193.119:443 | yg5sjx5kzy.com | AMAZON-AES | US | unknown |
3664 | iexplore.exe | 23.32.238.219:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3664 | iexplore.exe | 172.64.149.23:80 | ocsp.comodoca.com | CLOUDFLARENET | US | unknown |
3664 | iexplore.exe | 104.18.38.233:80 | ocsp.comodoca.com | CLOUDFLARENET | — | shared |
3664 | iexplore.exe | 169.150.247.38:443 | cdn4.yg5sjx5kzy.com | — | GB | unknown |
3656 | iexplore.exe | 107.22.193.119:443 | yg5sjx5kzy.com | AMAZON-AES | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
yg5sjx5kzy.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
cdn4.yg5sjx5kzy.com |
| unknown |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Hola-Setup-Core.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
Hola-Setup-Core.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
Hola-Setup-Core.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
Hola-Setup-Core.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
Hola-Setup-Core.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
Hola-Setup-Core.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
Hola-Setup-Core.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
Hola-Setup-Core.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
Hola-Setup-Core.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
Hola-Setup-Core.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|