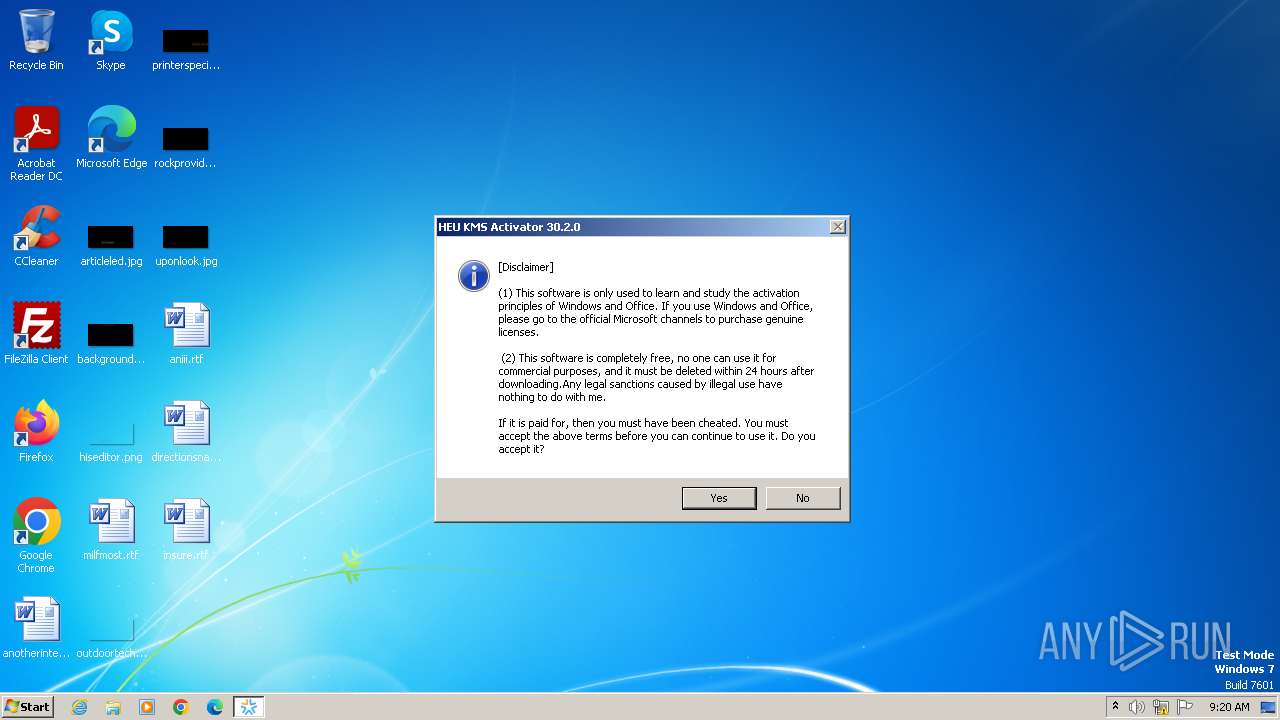
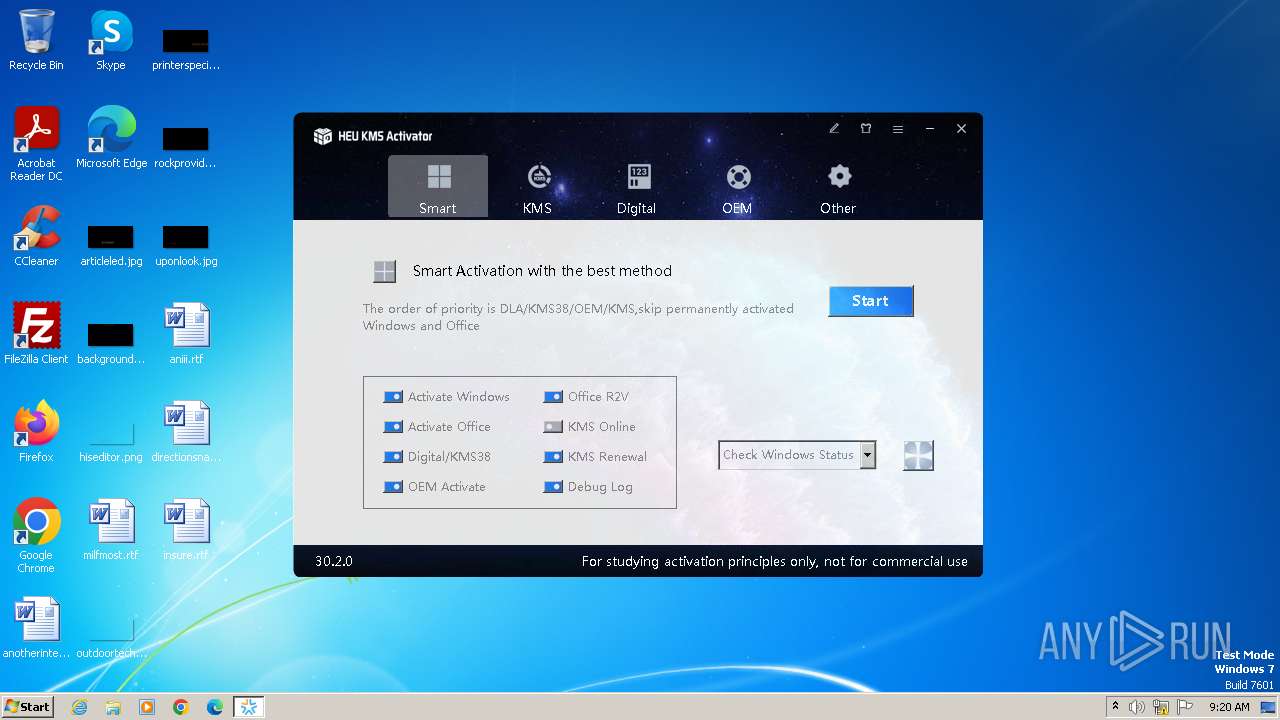
| File name: | HEU_KMS_Activator_30.2.0.exe |
| Full analysis: | https://app.any.run/tasks/999ff76f-763b-44dc-a3aa-ca93a1ab56e6 |
| Verdict: | Malicious activity |
| Analysis date: | November 23, 2023, 09:19:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | F18506AFEB56FCDE4A4F0AE9ED3B1134 |
| SHA1: | B909944EBFD258A9401802EDC743AD759801949F |
| SHA256: | 84FF818A54F8D74AC9F108F4EB59548C30E1187A55F9C979235E12B11310C174 |
| SSDEEP: | 98304:j+S9bgsTaFGQ0+mra19Dr7AoVMRuT7mGfVmH68TeOq8+:CMc6YGQ021tr71VLnmKVma8KP8+ |
MALICIOUS
Accesses system services(Win32_Service) via WMI (SCRIPT)
- cscript.exe (PID: 1364)
- cscript.exe (PID: 2300)
- cscript.exe (PID: 1640)
- cscript.exe (PID: 1696)
- cscript.exe (PID: 2560)
- cscript.exe (PID: 3780)
- cscript.exe (PID: 280)
- cscript.exe (PID: 1992)
- cscript.exe (PID: 2764)
- cscript.exe (PID: 888)
- cscript.exe (PID: 2512)
- cscript.exe (PID: 3436)
- cscript.exe (PID: 3212)
- cscript.exe (PID: 3504)
- cscript.exe (PID: 4024)
- cscript.exe (PID: 3860)
- cscript.exe (PID: 4048)
- cscript.exe (PID: 3820)
Drops the executable file immediately after the start
- 7Z.EXE (PID: 3496)
- HEU_KMS_Activator_30.2.0.exe (PID: 3164)
- kms.exe (PID: 3420)
Creates a writable file in the system directory
- kms.exe (PID: 3420)
SUSPICIOUS
Reads the Internet Settings
- cscript.exe (PID: 3444)
- cscript.exe (PID: 3940)
Drops 7-zip archiver for unpacking
- HEU_KMS_Activator_30.2.0.exe (PID: 3164)
Starts CMD.EXE for commands execution
- kms.exe (PID: 3420)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 3444)
- cscript.exe (PID: 3940)
Accesses ComputerSystem(Win32_ComputerSystem) via WMI (SCRIPT)
- cscript.exe (PID: 3444)
Executes WMI query (SCRIPT)
- cscript.exe (PID: 3444)
- cscript.exe (PID: 3940)
- cscript.exe (PID: 1364)
- cscript.exe (PID: 1640)
- cscript.exe (PID: 2300)
- cscript.exe (PID: 1696)
- cscript.exe (PID: 2560)
- cscript.exe (PID: 3780)
- cscript.exe (PID: 280)
- cscript.exe (PID: 1992)
- cscript.exe (PID: 2764)
- cscript.exe (PID: 888)
- cscript.exe (PID: 2512)
- cscript.exe (PID: 3436)
- cscript.exe (PID: 3212)
- cscript.exe (PID: 3504)
- cscript.exe (PID: 4024)
- cscript.exe (PID: 3860)
- cscript.exe (PID: 4048)
- cscript.exe (PID: 3820)
Starts SC.EXE for service management
- cmd.exe (PID: 4028)
- cmd.exe (PID: 4020)
- cmd.exe (PID: 4056)
- cmd.exe (PID: 3740)
- cmd.exe (PID: 3700)
- cmd.exe (PID: 2100)
- cmd.exe (PID: 856)
- cmd.exe (PID: 3320)
- cmd.exe (PID: 1984)
- cmd.exe (PID: 2088)
- cmd.exe (PID: 2164)
- cmd.exe (PID: 924)
- cmd.exe (PID: 2984)
The process executes VB scripts
- cmd.exe (PID: 1656)
- cmd.exe (PID: 2092)
- cmd.exe (PID: 1988)
- cmd.exe (PID: 2136)
- cmd.exe (PID: 2108)
- cmd.exe (PID: 2784)
- cmd.exe (PID: 2408)
- cmd.exe (PID: 2112)
- cmd.exe (PID: 2708)
- cmd.exe (PID: 3096)
- cmd.exe (PID: 2476)
- cmd.exe (PID: 2852)
- cmd.exe (PID: 3216)
- cmd.exe (PID: 3228)
- cmd.exe (PID: 3380)
- cmd.exe (PID: 3932)
- cmd.exe (PID: 3536)
- cmd.exe (PID: 3696)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 1364)
- cscript.exe (PID: 1640)
- cscript.exe (PID: 2300)
- cscript.exe (PID: 1696)
- cscript.exe (PID: 2560)
- cscript.exe (PID: 3780)
- cscript.exe (PID: 280)
- cscript.exe (PID: 1992)
- cscript.exe (PID: 2764)
- cscript.exe (PID: 888)
- cscript.exe (PID: 2512)
- cscript.exe (PID: 3436)
- cscript.exe (PID: 3212)
- cscript.exe (PID: 3504)
- cscript.exe (PID: 3860)
- cscript.exe (PID: 4024)
- cscript.exe (PID: 4048)
- cscript.exe (PID: 3820)
Accesses computer name via WMI (SCRIPT)
- cscript.exe (PID: 1364)
- cscript.exe (PID: 1640)
- cscript.exe (PID: 2300)
- cscript.exe (PID: 1696)
- cscript.exe (PID: 2560)
- cscript.exe (PID: 3780)
- cscript.exe (PID: 1992)
- cscript.exe (PID: 280)
- cscript.exe (PID: 2764)
- cscript.exe (PID: 888)
- cscript.exe (PID: 2512)
- cscript.exe (PID: 3436)
- cscript.exe (PID: 3212)
- cscript.exe (PID: 3504)
- cscript.exe (PID: 3860)
- cscript.exe (PID: 4024)
- cscript.exe (PID: 4048)
- cscript.exe (PID: 3820)
Gets a collection of all available drive names (SCRIPT)
- cscript.exe (PID: 1364)
- cscript.exe (PID: 1640)
- cscript.exe (PID: 2300)
- cscript.exe (PID: 1696)
- cscript.exe (PID: 2560)
- cscript.exe (PID: 3780)
- cscript.exe (PID: 1992)
- cscript.exe (PID: 280)
- cscript.exe (PID: 2764)
- cscript.exe (PID: 888)
- cscript.exe (PID: 2512)
- cscript.exe (PID: 3436)
- cscript.exe (PID: 3212)
- cscript.exe (PID: 3504)
- cscript.exe (PID: 3860)
- cscript.exe (PID: 4024)
- cscript.exe (PID: 4048)
- cscript.exe (PID: 3820)
Gets the drive type (SCRIPT)
- cscript.exe (PID: 1364)
- cscript.exe (PID: 1640)
- cscript.exe (PID: 2300)
- cscript.exe (PID: 1696)
- cscript.exe (PID: 2560)
- cscript.exe (PID: 3780)
- cscript.exe (PID: 280)
- cscript.exe (PID: 1992)
- cscript.exe (PID: 888)
- cscript.exe (PID: 2512)
- cscript.exe (PID: 3436)
- cscript.exe (PID: 3212)
- cscript.exe (PID: 3860)
- cscript.exe (PID: 3504)
- cscript.exe (PID: 4024)
- cscript.exe (PID: 4048)
- cscript.exe (PID: 2764)
- cscript.exe (PID: 3820)
Accesses WMI object, sets custom ImpersonationLevel (SCRIPT)
- cscript.exe (PID: 1364)
- cscript.exe (PID: 1640)
- cscript.exe (PID: 2300)
- cscript.exe (PID: 1696)
- cscript.exe (PID: 2560)
- cscript.exe (PID: 3780)
- cscript.exe (PID: 280)
- cscript.exe (PID: 1992)
- cscript.exe (PID: 2764)
- cscript.exe (PID: 888)
- cscript.exe (PID: 2512)
- cscript.exe (PID: 3436)
- cscript.exe (PID: 3212)
- cscript.exe (PID: 3504)
- cscript.exe (PID: 3860)
- cscript.exe (PID: 4024)
- cscript.exe (PID: 4048)
- cscript.exe (PID: 3820)
Reads data from a binary Stream object (SCRIPT)
- cscript.exe (PID: 1364)
- cscript.exe (PID: 1640)
- cscript.exe (PID: 2300)
- cscript.exe (PID: 1696)
- cscript.exe (PID: 2560)
- cscript.exe (PID: 3780)
- cscript.exe (PID: 280)
- cscript.exe (PID: 1992)
- cscript.exe (PID: 2764)
- cscript.exe (PID: 2512)
- cscript.exe (PID: 888)
- cscript.exe (PID: 3436)
- cscript.exe (PID: 3212)
- cscript.exe (PID: 3504)
- cscript.exe (PID: 3860)
- cscript.exe (PID: 4024)
- cscript.exe (PID: 3820)
- cscript.exe (PID: 4048)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- cscript.exe (PID: 1364)
- cscript.exe (PID: 1640)
- cscript.exe (PID: 2300)
- cscript.exe (PID: 1696)
- cscript.exe (PID: 2560)
- cscript.exe (PID: 3780)
- cscript.exe (PID: 280)
- cscript.exe (PID: 1992)
- cscript.exe (PID: 2764)
- cscript.exe (PID: 888)
- cscript.exe (PID: 2512)
- cscript.exe (PID: 3436)
- cscript.exe (PID: 3212)
- cscript.exe (PID: 3504)
- cscript.exe (PID: 3860)
- cscript.exe (PID: 4048)
- cscript.exe (PID: 4024)
- cscript.exe (PID: 3820)
Changes charset (SCRIPT)
- cscript.exe (PID: 1364)
- cscript.exe (PID: 1640)
- cscript.exe (PID: 2300)
- cscript.exe (PID: 1696)
- cscript.exe (PID: 2560)
- cscript.exe (PID: 3780)
- cscript.exe (PID: 280)
- cscript.exe (PID: 1992)
- cscript.exe (PID: 2764)
- cscript.exe (PID: 888)
- cscript.exe (PID: 2512)
- cscript.exe (PID: 3436)
- cscript.exe (PID: 3212)
- cscript.exe (PID: 3504)
- cscript.exe (PID: 3860)
- cscript.exe (PID: 4024)
- cscript.exe (PID: 4048)
- cscript.exe (PID: 3820)
Checks whether a specific file exists (SCRIPT)
- cscript.exe (PID: 1364)
- cscript.exe (PID: 1640)
- cscript.exe (PID: 2300)
- cscript.exe (PID: 2560)
- cscript.exe (PID: 3780)
- cscript.exe (PID: 1696)
- cscript.exe (PID: 280)
- cscript.exe (PID: 1992)
- cscript.exe (PID: 2764)
- cscript.exe (PID: 888)
- cscript.exe (PID: 2512)
- cscript.exe (PID: 3436)
- cscript.exe (PID: 3504)
- cscript.exe (PID: 3212)
- cscript.exe (PID: 3860)
- cscript.exe (PID: 4024)
- cscript.exe (PID: 4048)
- cscript.exe (PID: 3820)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 1364)
- cscript.exe (PID: 1640)
- cscript.exe (PID: 2300)
- cscript.exe (PID: 1696)
- cscript.exe (PID: 2560)
- cscript.exe (PID: 3780)
- cscript.exe (PID: 1992)
- cscript.exe (PID: 280)
- cscript.exe (PID: 2764)
- cscript.exe (PID: 888)
- cscript.exe (PID: 2512)
- cscript.exe (PID: 3436)
- cscript.exe (PID: 3504)
- cscript.exe (PID: 3212)
- cscript.exe (PID: 3860)
- cscript.exe (PID: 4024)
- cscript.exe (PID: 4048)
- cscript.exe (PID: 3820)
Reads data from a file (SCRIPT)
- cscript.exe (PID: 1364)
- cscript.exe (PID: 1640)
- cscript.exe (PID: 2300)
- cscript.exe (PID: 2560)
- cscript.exe (PID: 3780)
- cscript.exe (PID: 280)
- cscript.exe (PID: 1992)
- cscript.exe (PID: 1696)
- cscript.exe (PID: 888)
- cscript.exe (PID: 2764)
- cscript.exe (PID: 2512)
- cscript.exe (PID: 3436)
- cscript.exe (PID: 3212)
- cscript.exe (PID: 3504)
- cscript.exe (PID: 3860)
- cscript.exe (PID: 4024)
- cscript.exe (PID: 3820)
- cscript.exe (PID: 4048)
Detected use of alternative data streams (AltDS)
- kms.exe (PID: 3420)
Accesses system date via WMI (SCRIPT)
- cscript.exe (PID: 1696)
- cscript.exe (PID: 2560)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2988)
- cmd.exe (PID: 2376)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- cmd.exe (PID: 1236)
- cmd.exe (PID: 3476)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 2620)
Executes as Windows Service
- kms-server.exe (PID: 956)
INFO
Reads mouse settings
- HEU_KMS_Activator_30.2.0.exe (PID: 3164)
- kms.exe (PID: 3420)
Checks supported languages
- HEU_KMS_Activator_30.2.0.exe (PID: 3164)
- 7Z.EXE (PID: 3496)
- kms.exe (PID: 3420)
- 7Z.EXE (PID: 1508)
- kms-server.exe (PID: 1836)
- kms-server.exe (PID: 956)
- kms-server.exe (PID: 2076)
Create files in a temporary directory
- kms.exe (PID: 3420)
- HEU_KMS_Activator_30.2.0.exe (PID: 3164)
Checks Windows language
- kms.exe (PID: 3420)
- HEU_KMS_Activator_30.2.0.exe (PID: 3164)
Reads security settings of Internet Explorer
- cscript.exe (PID: 3444)
- cscript.exe (PID: 3940)
- cscript.exe (PID: 1364)
- cscript.exe (PID: 1640)
- cscript.exe (PID: 2300)
- cscript.exe (PID: 1696)
- cscript.exe (PID: 2560)
- cscript.exe (PID: 3780)
- cscript.exe (PID: 280)
- cscript.exe (PID: 1992)
- cscript.exe (PID: 2764)
- cscript.exe (PID: 888)
- cscript.exe (PID: 2512)
- cscript.exe (PID: 3436)
- cscript.exe (PID: 3212)
- cscript.exe (PID: 3504)
- cscript.exe (PID: 3860)
- cscript.exe (PID: 4024)
- cscript.exe (PID: 4048)
- cscript.exe (PID: 3820)
Reads the machine GUID from the registry
- HEU_KMS_Activator_30.2.0.exe (PID: 3164)
- kms.exe (PID: 3420)
Reads the computer name
- 7Z.EXE (PID: 3496)
- 7Z.EXE (PID: 1508)
- kms.exe (PID: 3420)
- kms-server.exe (PID: 1836)
- kms-server.exe (PID: 2076)
- kms-server.exe (PID: 956)
Reads product name
- kms.exe (PID: 3420)
Reads Environment values
- kms.exe (PID: 3420)
Reads Microsoft Office registry keys
- kms.exe (PID: 3420)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (43.5) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (42.7) |
| .exe | | | Win32 Executable (generic) (7.2) |
| .exe | | | Generic Win/DOS Executable (3.2) |
| .exe | | | DOS Executable Generic (3.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:04:02 18:08:20+02:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 385024 |
| InitializedDataSize: | 4358144 |
| UninitializedDataSize: | 4911104 |
| EntryPoint: | 0x50cd70 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 30.2.0.0 |
| ProductVersionNumber: | 30.2.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | Chinese (Simplified) |
| CharacterSet: | Unicode |
| FileVersion: | 30.2.0.0 |
| Comments: | KMS/数字权利/KMS38/OEM激活 |
| FileDescription: | HEU KMS Activator™ |
| ProductVersion: | 30.2.0.0 |
| LegalCopyright: | 知彼而知己 |
| Productname: | HEU KMS Activator |
| CompanyName: | 知彼而知己 |
| OriginalFileName: | HEU_KMS_Activator_v30.2.0 |
| InternalName: | HEU_KMS_Activator_v30.2.0 |
Total processes
170
Monitored processes
87
Malicious processes
40
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 280 | cscript "C:\Program Files\Microsoft Office\Office14\\ospp.vbs" /inslic:"C:\Windows\_temp_heu168yyds\Licenses\Office2010\OneNote\OneNote_MAK_PHN.xrm-ms" | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 856 | C:\Windows\system32\cmd.exe /c sc query vlmcsd | C:\Windows\System32\cmd.exe | — | kms.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 888 | cscript "C:\Program Files\Microsoft Office\Office14\\ospp.vbs" /inslic:"C:\Windows\_temp_heu168yyds\Licenses\Office2010\Word\Word_KMS_Client_OOB.xrm-ms" | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 924 | C:\Windows\system32\cmd.exe /c sc query WinMgmt | C:\Windows\System32\cmd.exe | — | kms.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 956 | "C:\Windows\System32\kms-server.exe" -P 1688 -R 10080 -A 120 | C:\Windows\System32\kms-server.exe | — | services.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Modules
| |||||||||||||||
| 1236 | C:\Windows\system32\cmd.exe /c set "Path=%SystemRoot%;%SystemRoot%\system32;%SystemRoot%\System32\Wbem;%SystemRoot\System32\WindowsPowerShell\v1.0\" & netsh advfirewall firewall delete rule name="heu-kms-mini" | C:\Windows\System32\cmd.exe | — | kms.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1364 | cscript "C:\Program Files\Microsoft Office\Office14\\ospp.vbs" /inslic:"C:\Windows\_temp_heu168yyds\Licenses\Office2010\OneNote\OneNote_KMS_Client_OOB.xrm-ms" | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1416 | netsh advfirewall firewall add rule name="heu-kms-mini" dir=in action=allow profile=any program="C:\Windows\System32\kms-server.exe" | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1436 | sc query OfficeSvc | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1508 | C:\Windows\_temp_heu168yyds\7Z.EXE x "C:\Windows\_temp_heu168yyds\files.7z" -y -o"C:\Windows\_temp_heu168yyds" Licenses\Office2010 | C:\Windows\_temp_heu168yyds\7Z.EXE | — | kms.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Standalone Console Exit code: 0 Version: 19.00 Modules
| |||||||||||||||
Total events
4 743
Read events
4 591
Write events
152
Delete events
0
Modification events
| (PID) Process: | (3444) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3444) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3444) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3444) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3940) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3940) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3940) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3940) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1824) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2428) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
12
Suspicious files
6
Text files
294
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3164 | HEU_KMS_Activator_30.2.0.exe | C:\Users\admin\AppData\Local\Temp\ScriptTemp.ini | text | |
MD5:73B988A2A2092F8796C3A8A17A7B0283 | SHA256:A35BB11E7DAD4493E1D72E1C8780D5A8939B164A6A62F963A5DA03C295102ED0 | |||
| 3164 | HEU_KMS_Activator_30.2.0.exe | C:\Users\admin\AppData\Local\Temp\aut85C0.tmp | compressed | |
MD5:A6DD14E413F468A0A858C65A6A91ACA0 | SHA256:8C9F9E572F4B31D842D8E5852852590CB82B95E594E29E7714FF958752717231 | |||
| 3164 | HEU_KMS_Activator_30.2.0.exe | C:\Users\admin\AppData\Local\Temp\aut868C.tmp | compressed | |
MD5:C7926C9B1DFE047575916F8016F36555 | SHA256:C02C302C2F9861B4120664AD32B74280A5F13DAE54735AD858691837AA496888 | |||
| 3164 | HEU_KMS_Activator_30.2.0.exe | C:\Windows\_temp_heu168yyds\KMSmini.7z | compressed | |
MD5:A6DD14E413F468A0A858C65A6A91ACA0 | SHA256:8C9F9E572F4B31D842D8E5852852590CB82B95E594E29E7714FF958752717231 | |||
| 3164 | HEU_KMS_Activator_30.2.0.exe | C:\Users\admin\AppData\Local\Temp\aut8571.tmp | binary | |
MD5:B14108CB199F86AA15351D2E9219412B | SHA256:9BCB98ECEF86ABEE7356CCC4038EDB370BC0CAD07AC15AD6FF73DAB6F90045F5 | |||
| 3164 | HEU_KMS_Activator_30.2.0.exe | C:\Users\admin\AppData\Local\Temp\splashlogo.jpg | image | |
MD5:2BC3F059E8A844879F91D900FFA6EFFB | SHA256:A222634FD0145551CFBDAAEB101421CDE0037E77A9A33DA407219B99CF0985E1 | |||
| 3496 | 7Z.EXE | C:\Windows\_temp_heu168yyds\OtherOfficeOSPP\slerror.xml | text | |
MD5:36F7DADFE84E62DA00292D0569C3F523 | SHA256:B3378A3178F3E52094DB20E8A828011CD8882017919522A544BAEF3057BD11D3 | |||
| 3496 | 7Z.EXE | C:\Windows\_temp_heu168yyds\OtherOfficeOSPP\OSPP.VBS | text | |
MD5:885B4DAE3623B427B8F04A7BC88780B9 | SHA256:6BC8E3991DA8C6527B3588E8F95068665918B685299CBB16BA6CC0C484BFE072 | |||
| 3164 | HEU_KMS_Activator_30.2.0.exe | C:\Users\admin\AppData\Local\Temp\aut8729.tmp | binary | |
MD5:E25E09DF3DB990F98A165990B2F48B02 | SHA256:52F64C84948068514240283D6C7FA1204E81CA0549CF0159FCACC556A950CD94 | |||
| 3164 | HEU_KMS_Activator_30.2.0.exe | C:\Windows\_temp_heu168yyds\files.7z | compressed | |
MD5:C7926C9B1DFE047575916F8016F36555 | SHA256:C02C302C2F9861B4120664AD32B74280A5F13DAE54735AD858691837AA496888 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |