| File name: | SecuriteInfo.com.PUA.Themida.2211.28050 |
| Full analysis: | https://app.any.run/tasks/9fd64ac1-f822-4566-83cf-e535e4f1a9ce |
| Verdict: | Malicious activity |
| Analysis date: | August 26, 2024, 15:36:04 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | 8524557BB6995764972F0F1378551515 |
| SHA1: | 7404AB12472BD79092E39A124B5FD3346A43D0AF |
| SHA256: | 84F628F1D7842A26EC916A943805D1D1B274D709846E5414F17551230B2C2E9D |
| SSDEEP: | 98304:qQXj2APAucPFu417pQwof0VwBYqgxCiApiJK/F7a6SuHJEk2BTEt/sDEdoyk4UXb:XGiqibVGCwx6v1cQcIyr |
MALICIOUS
No malicious indicators.SUSPICIOUS
Drops the executable file immediately after the start
- SecuriteInfo.com.PUA.Themida.2211.28050.exe (PID: 5140)
Reads the BIOS version
- SecuriteInfo.com.PUA.Themida.2211.28050.exe (PID: 5140)
INFO
Process checks whether UAC notifications are on
- SecuriteInfo.com.PUA.Themida.2211.28050.exe (PID: 5140)
Checks supported languages
- SecuriteInfo.com.PUA.Themida.2211.28050.exe (PID: 5140)
Reads the computer name
- SecuriteInfo.com.PUA.Themida.2211.28050.exe (PID: 5140)
Create files in a temporary directory
- SecuriteInfo.com.PUA.Themida.2211.28050.exe (PID: 5140)
Reads the software policy settings
- SecuriteInfo.com.PUA.Themida.2211.28050.exe (PID: 5140)
Creates files in the program directory
- SecuriteInfo.com.PUA.Themida.2211.28050.exe (PID: 5140)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:08:23 07:16:05+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.38 |
| CodeSize: | 7492096 |
| InitializedDataSize: | 5683712 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x13c0058 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 10.0.1.0 |
| ProductVersionNumber: | 10.0.1.0 |
| FileFlagsMask: | 0x0017 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | NewSoftwares LLC |
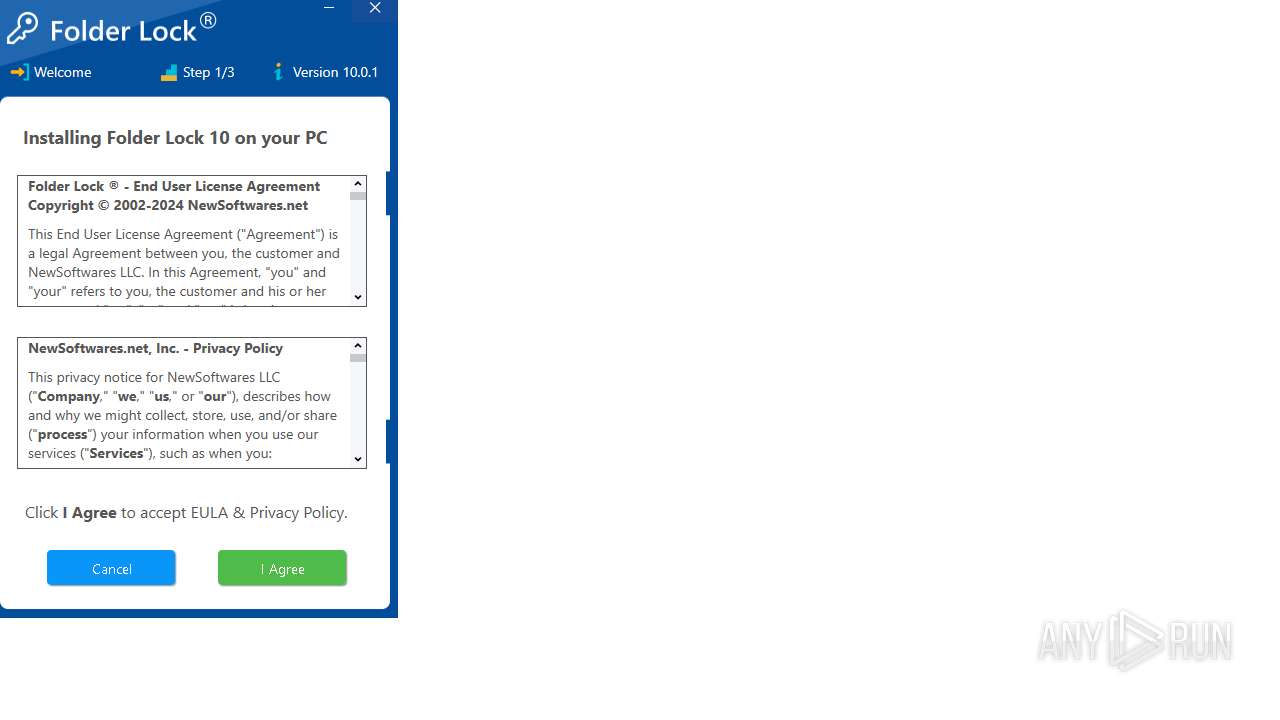
| FileDescription: | Folder Lock 10 Setup |
| FileVersion: | 10.0.1 |
| InternalName: | Folder Lock |
| LegalCopyright: | 2002-2024 © NewSoftwares LLC |
| LegalTrademarks: | Folder Lock ® is a registered trademark |
| OriginalFileName: | FolderLock10.exe |
| ProductName: | Folder Lock |
| ProductVersion: | 10.0.1 |
Total processes
128
Monitored processes
2
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2180 | "C:\Users\admin\AppData\Local\Temp\SecuriteInfo.com.PUA.Themida.2211.28050.exe" | C:\Users\admin\AppData\Local\Temp\SecuriteInfo.com.PUA.Themida.2211.28050.exe | — | explorer.exe | |||||||||||
User: admin Company: NewSoftwares LLC Integrity Level: MEDIUM Description: Folder Lock 10 Setup Exit code: 3221226540 Version: 10.0.1 Modules
| |||||||||||||||
| 5140 | "C:\Users\admin\AppData\Local\Temp\SecuriteInfo.com.PUA.Themida.2211.28050.exe" | C:\Users\admin\AppData\Local\Temp\SecuriteInfo.com.PUA.Themida.2211.28050.exe | explorer.exe | ||||||||||||
User: admin Company: NewSoftwares LLC Integrity Level: HIGH Description: Folder Lock 10 Setup Version: 10.0.1 Modules
| |||||||||||||||
Total events
856
Read events
837
Write events
1
Delete events
18
Modification events
| (PID) Process: | (5140) SecuriteInfo.com.PUA.Themida.2211.28050.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Spelling\Dictionaries |
| Operation: | delete value | Name: | en-us |
Value: | |||
| (PID) Process: | (5140) SecuriteInfo.com.PUA.Themida.2211.28050.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Spelling\Dictionaries |
| Operation: | delete value | Name: | en |
Value: | |||
| (PID) Process: | (5140) SecuriteInfo.com.PUA.Themida.2211.28050.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Spelling\Dictionaries |
| Operation: | delete value | Name: | _Global_ |
Value: | |||
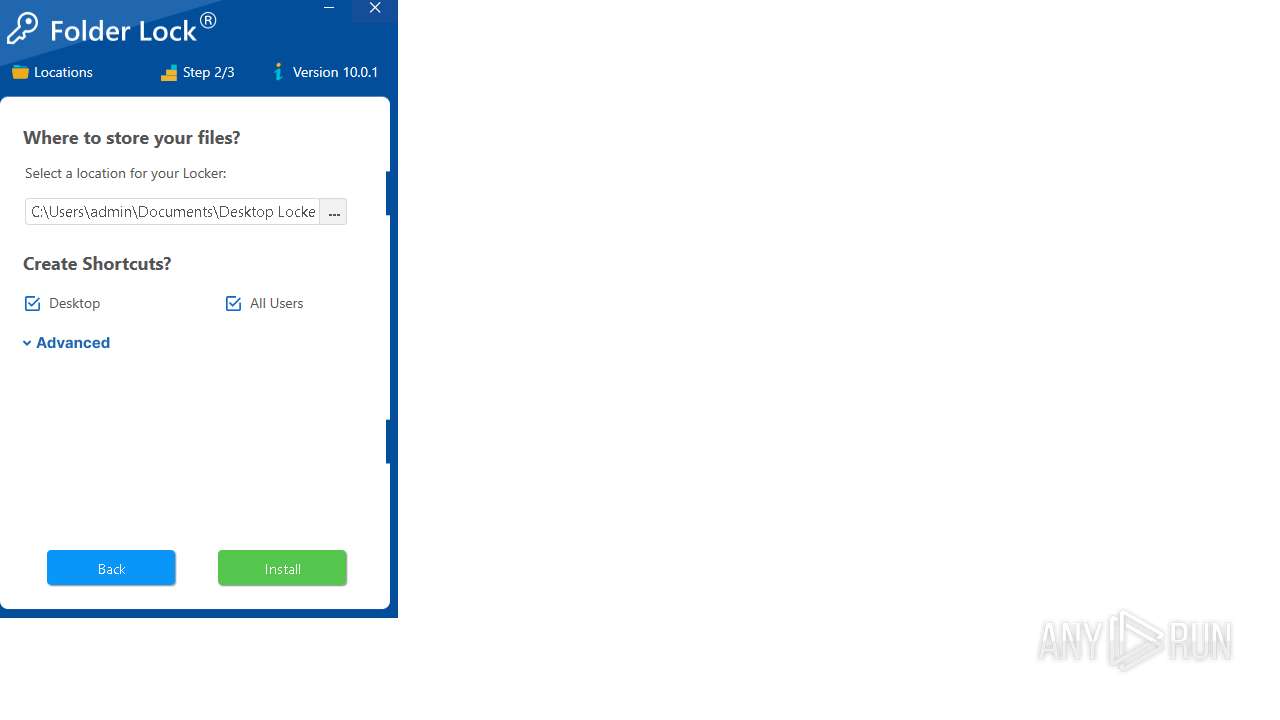
| (PID) Process: | (5140) SecuriteInfo.com.PUA.Themida.2211.28050.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\NewSoftware's\Folder Lock 10 |
| Operation: | write | Name: | SetupPath |
Value: C:\Users\admin\AppData\Local\Temp\SecuriteInfo.com.PUA.Themida.2211.28050.exe | |||
Executable files
0
Suspicious files
1
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5140 | SecuriteInfo.com.PUA.Themida.2211.28050.exe | C:\Users\admin\AppData\Roaming\Microsoft\Spelling\en-US\default.acl | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 5140 | SecuriteInfo.com.PUA.Themida.2211.28050.exe | C:\Users\admin\AppData\Roaming\Microsoft\Spelling\en-US\default.dic | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 5140 | SecuriteInfo.com.PUA.Themida.2211.28050.exe | C:\Users\admin\AppData\Roaming\Microsoft\Spelling\en-US\default.exc | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 5140 | SecuriteInfo.com.PUA.Themida.2211.28050.exe | C:\Users\admin\AppData\Local\Temp\WinFL10S.json | binary | |
MD5:8A343BD4B04B19BCDDCD6BC12FA9D5A1 | SHA256:C9E85F616CC52AA9F373109CF26D2D417BD1C6E04E6FDB63737A22584C7139D7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
23
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6580 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2820 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2820 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6252 | RUXIMICS.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7056 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
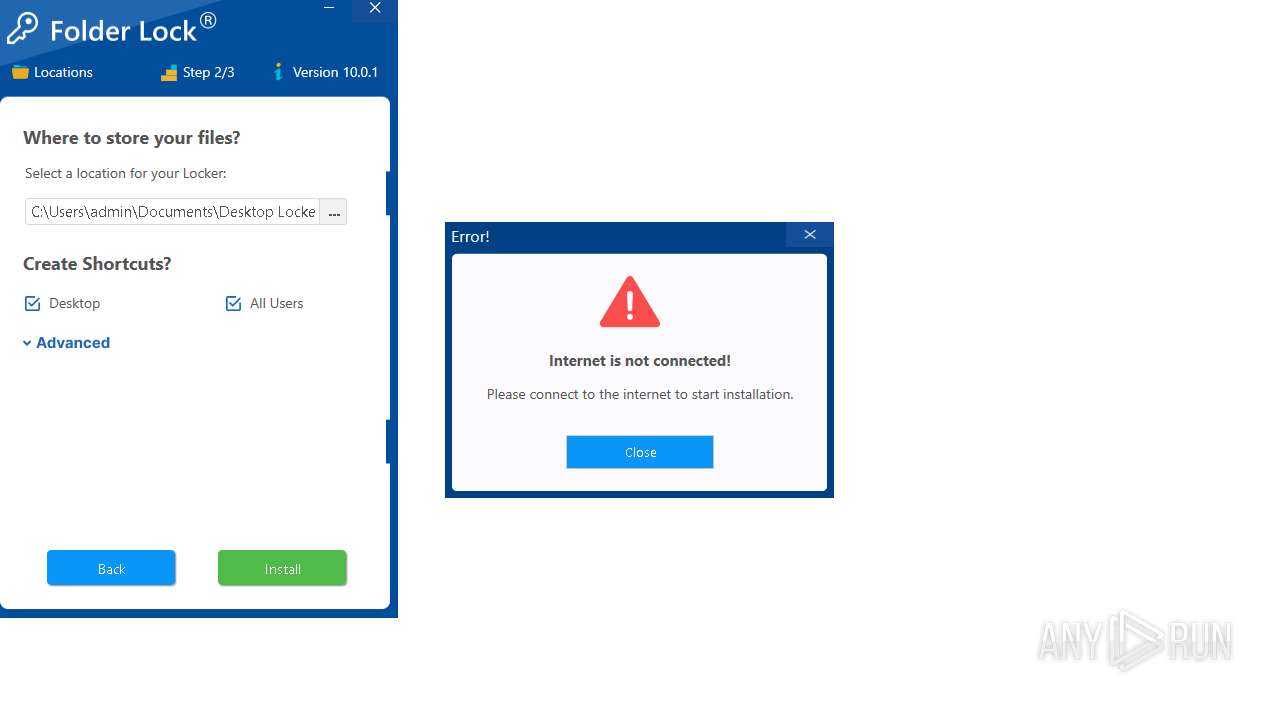
5140 | SecuriteInfo.com.PUA.Themida.2211.28050.exe | 69.16.221.160:443 | www.newsoftwares.net | LIQUIDWEB | US | malicious |
7056 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6580 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6580 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.newsoftwares.net |
| malicious |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
SecuriteInfo.com.PUA.Themida.2211.28050.exe | <ul> element is not allowed at ((968))
|
SecuriteInfo.com.PUA.Themida.2211.28050.exe | <ul> element is not allowed at ((1332))
|
SecuriteInfo.com.PUA.Themida.2211.28050.exe | <ul> element is not allowed at ((1419))
|
SecuriteInfo.com.PUA.Themida.2211.28050.exe | <ul> element is not allowed at ((1430))
|
SecuriteInfo.com.PUA.Themida.2211.28050.exe | <ul> element is not allowed at ((1445))
|
SecuriteInfo.com.PUA.Themida.2211.28050.exe | <ul> element is not allowed at ((1466))
|
SecuriteInfo.com.PUA.Themida.2211.28050.exe | <ul> element is not allowed at ((1494))
|
SecuriteInfo.com.PUA.Themida.2211.28050.exe | <ul> element is not allowed at ((1515))
|
SecuriteInfo.com.PUA.Themida.2211.28050.exe | <ul> element is not allowed at ((1534))
|
SecuriteInfo.com.PUA.Themida.2211.28050.exe | <ul> element is not allowed at ((1559))
|