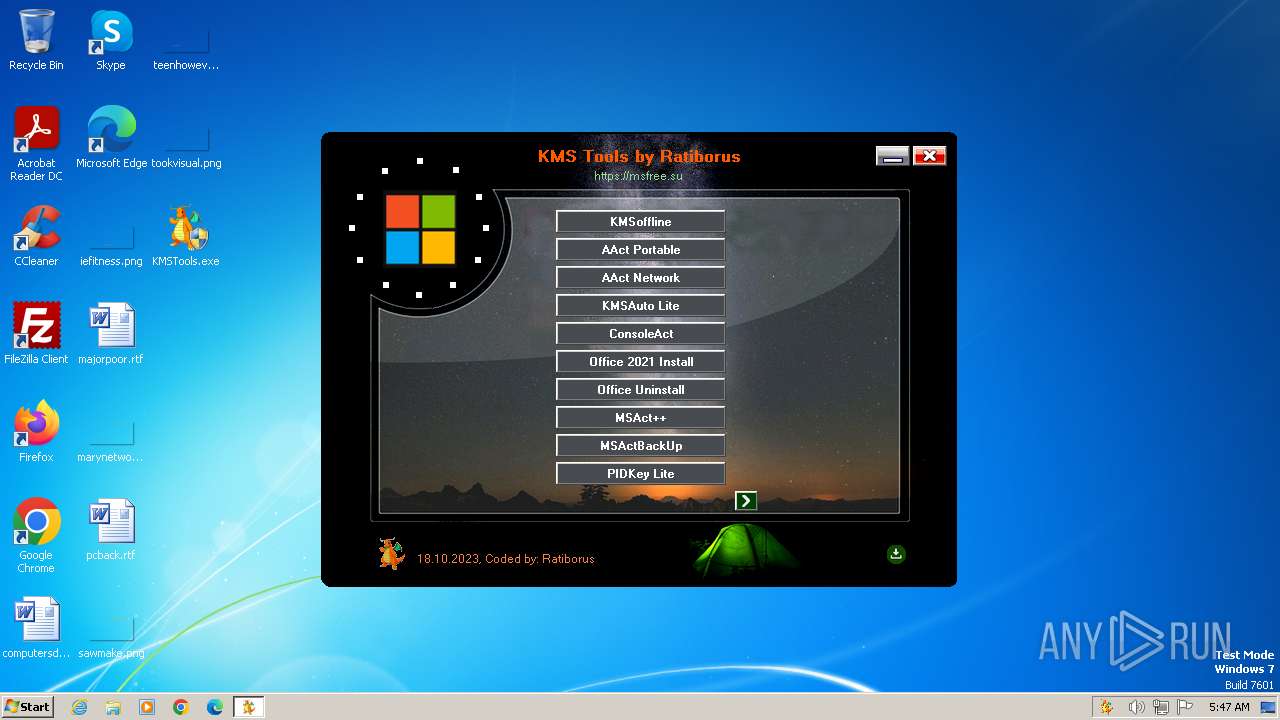
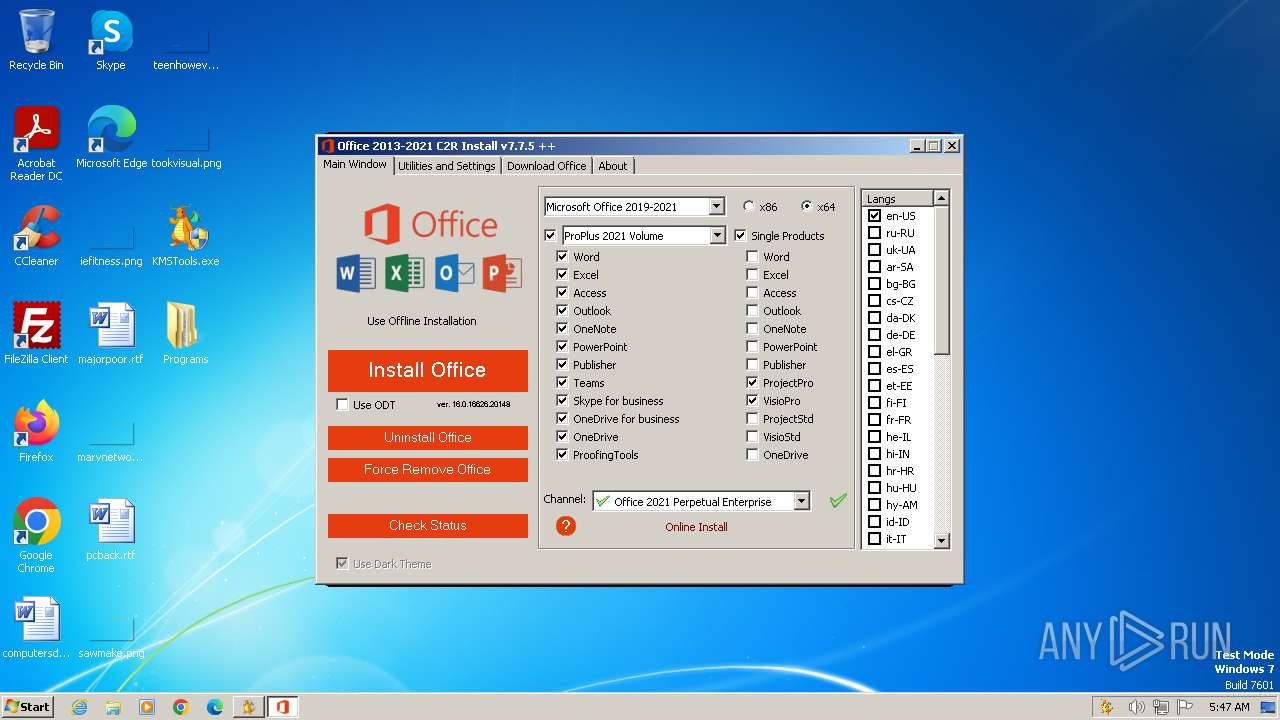
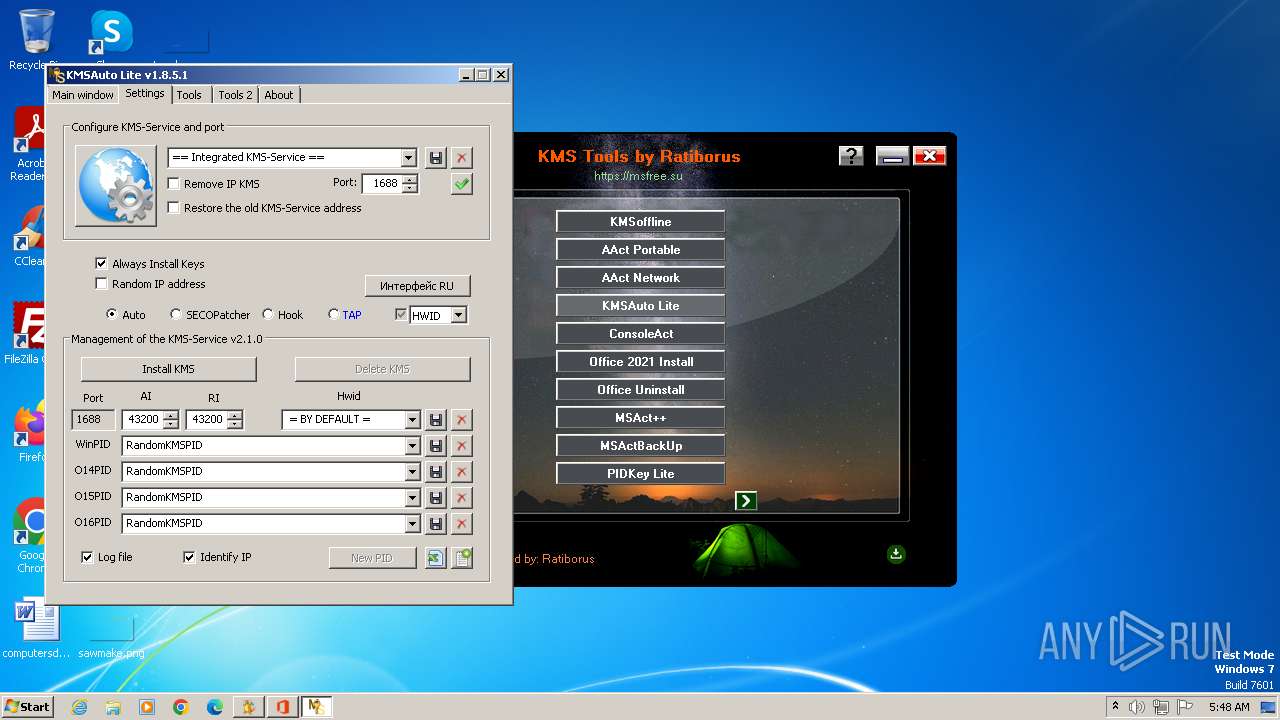
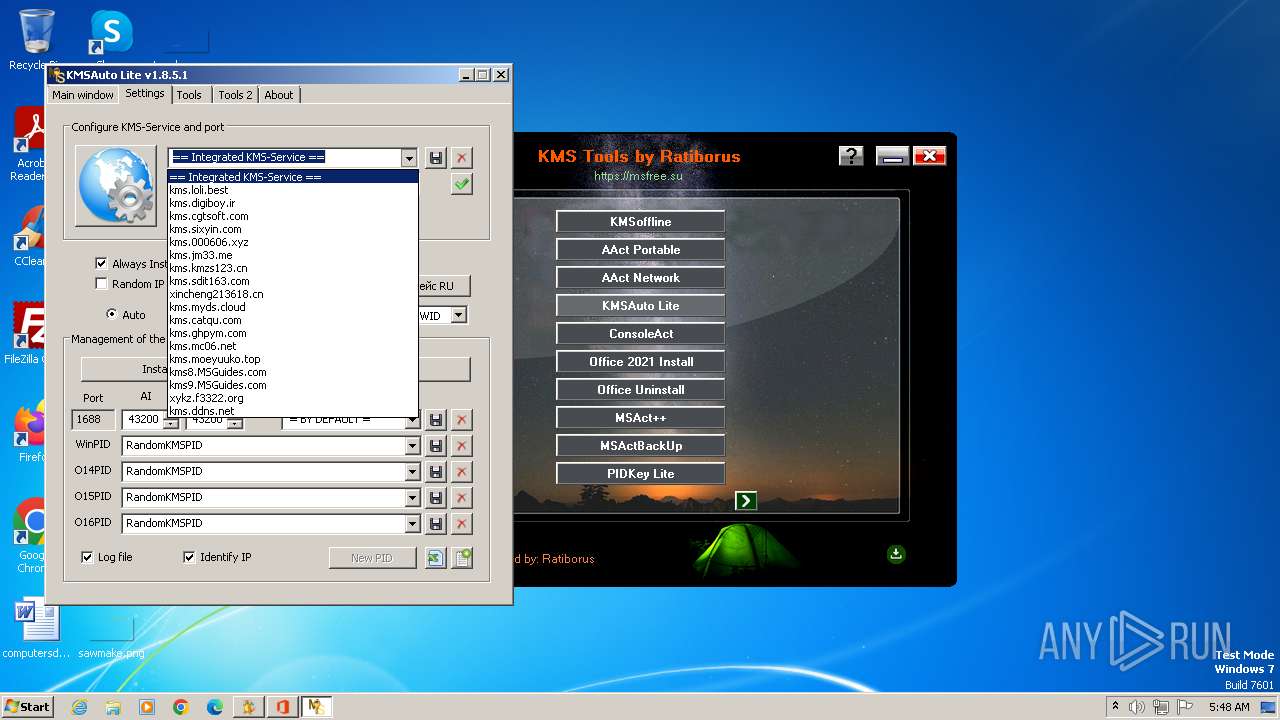
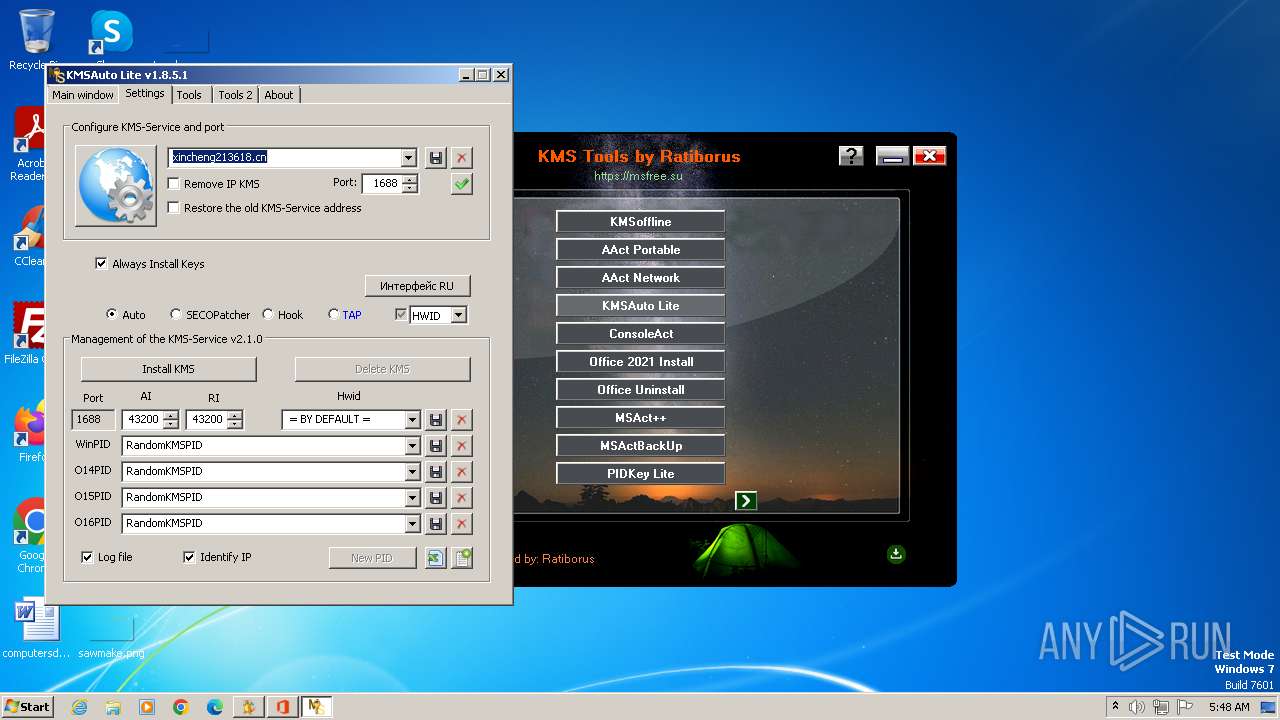
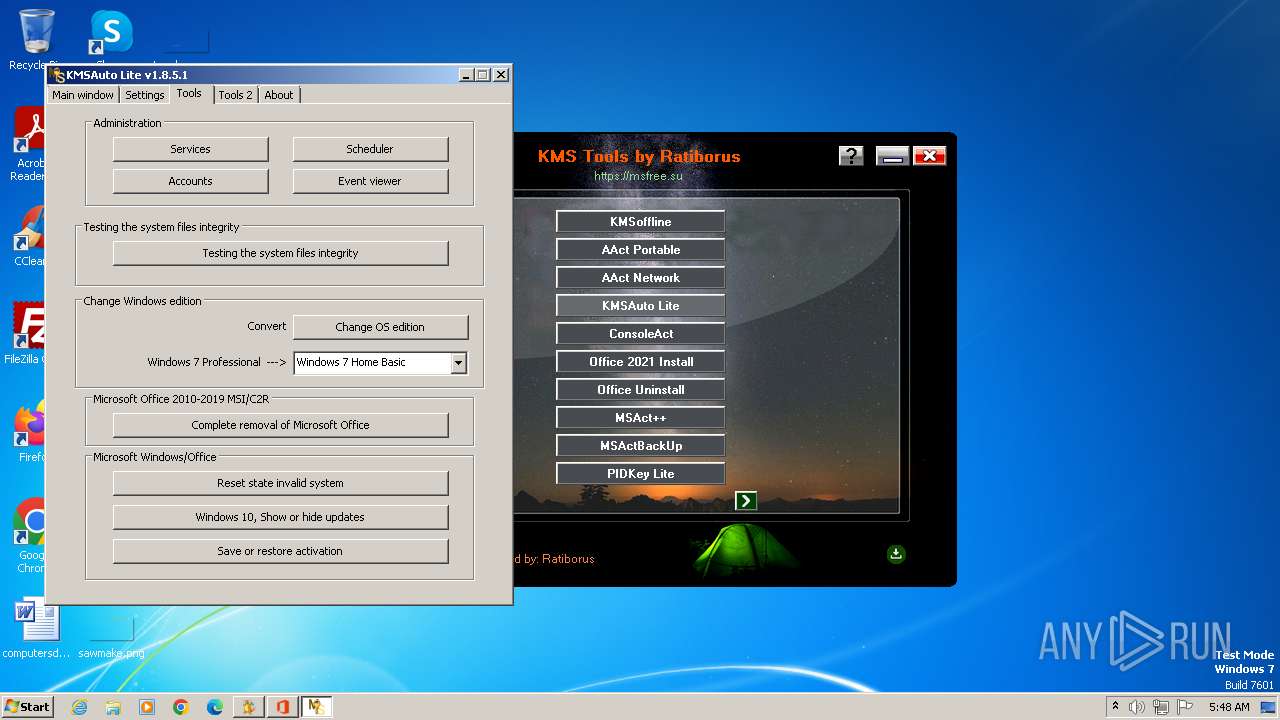
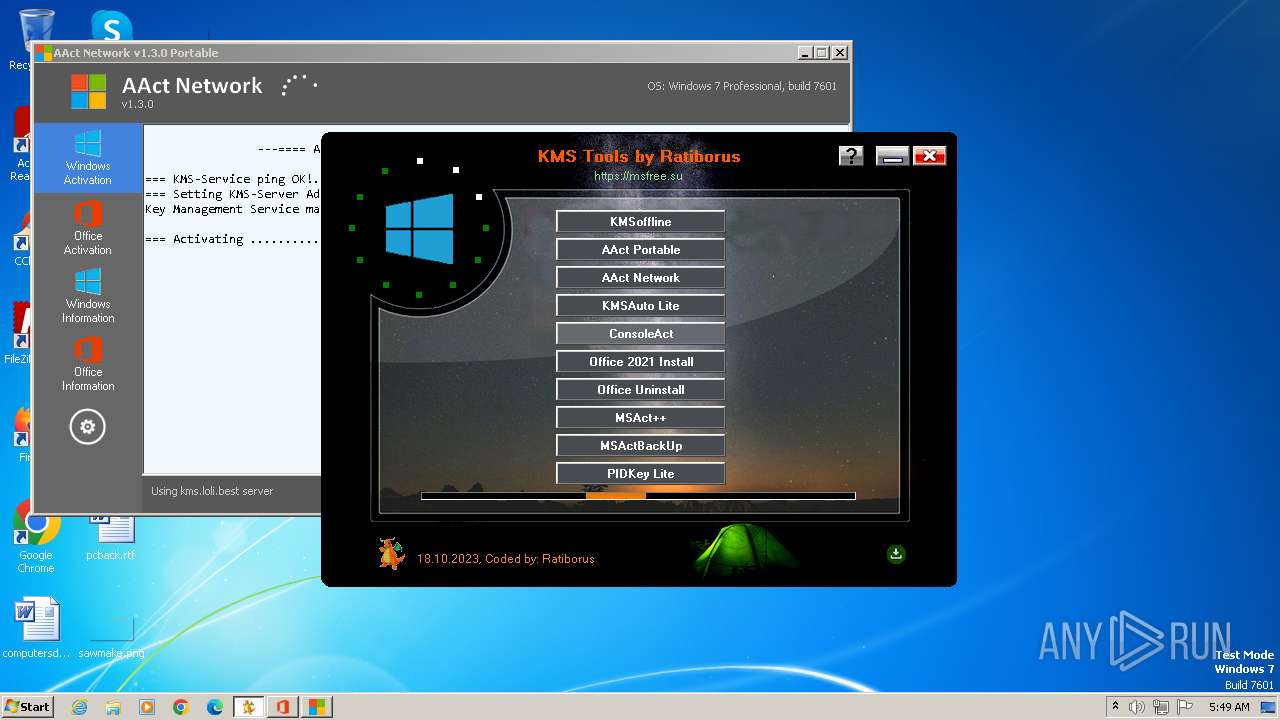
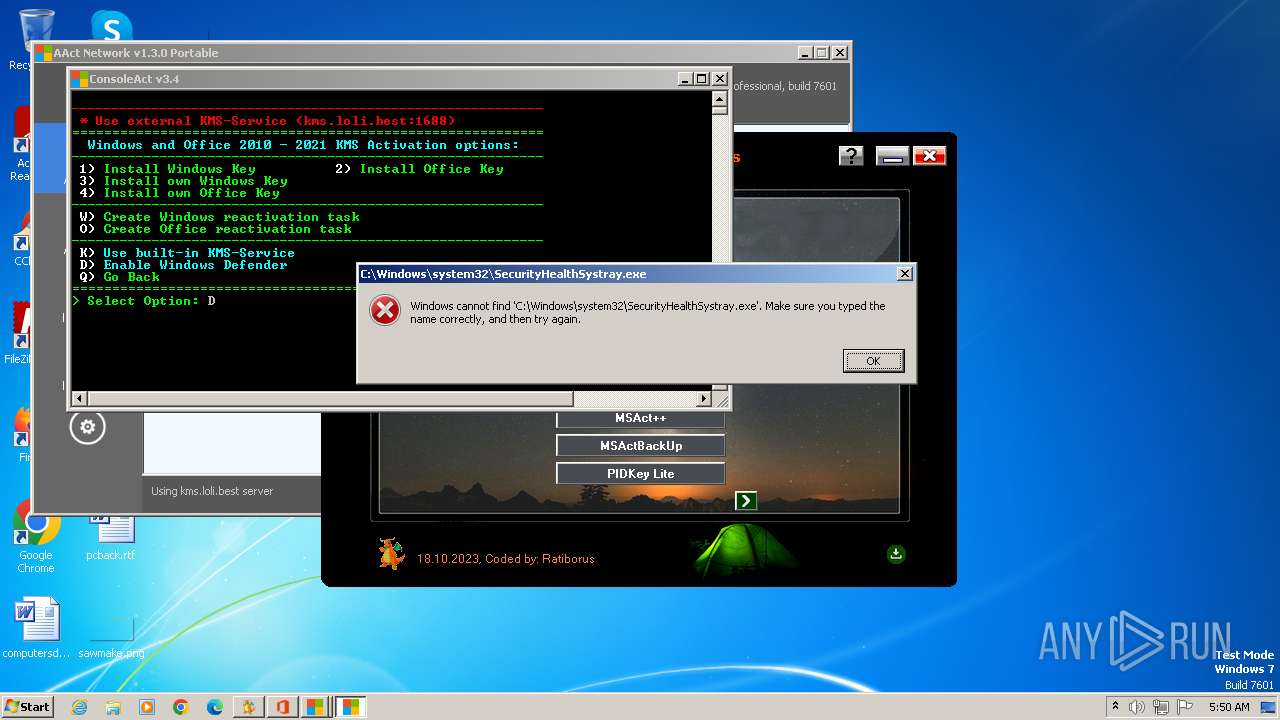
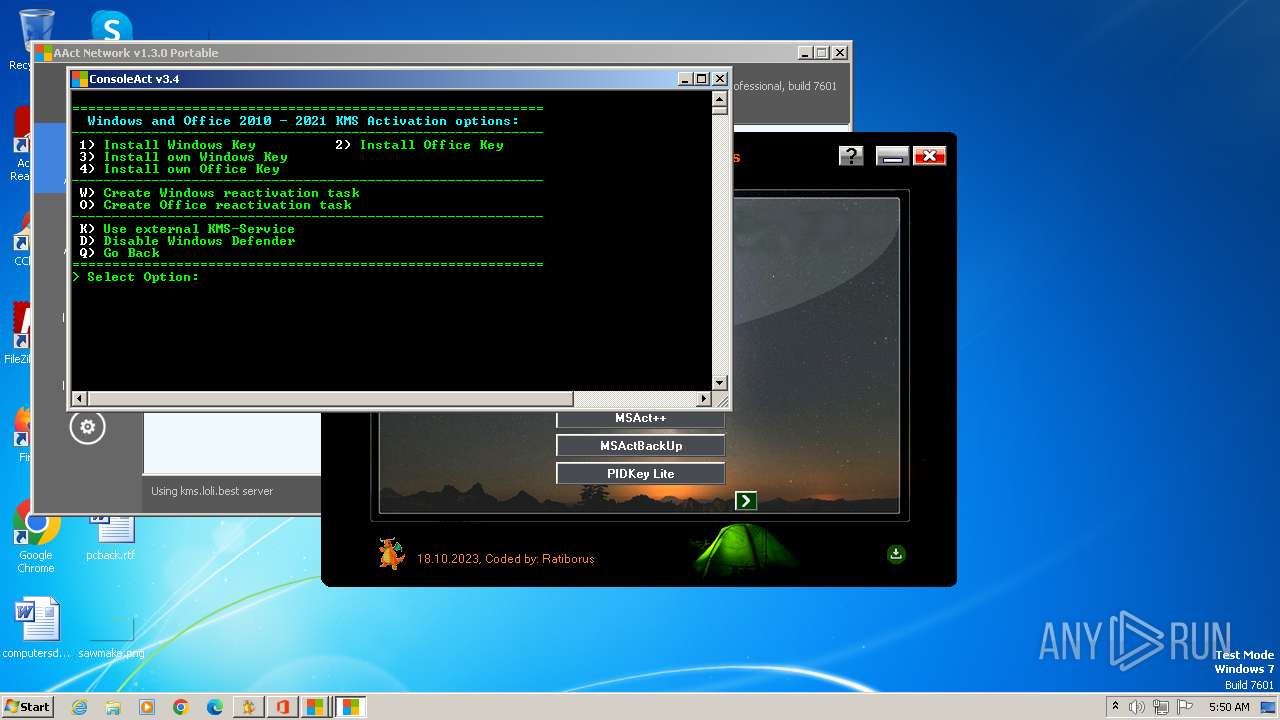
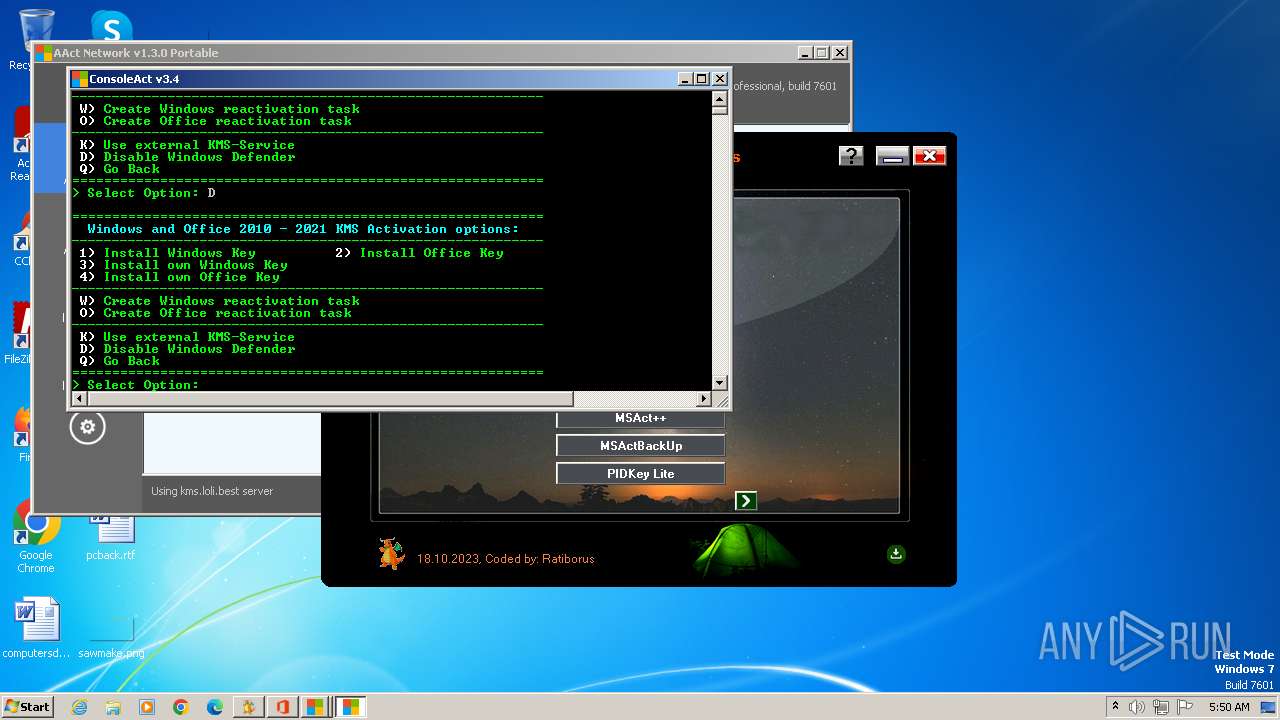
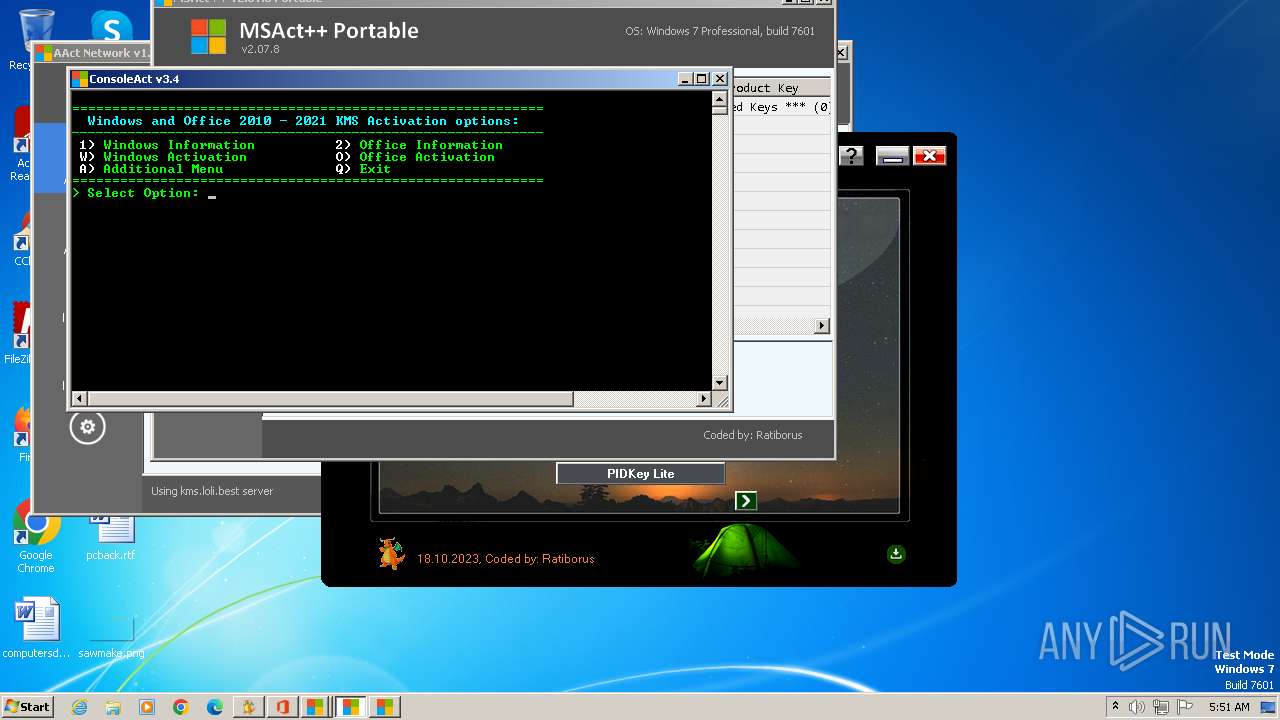
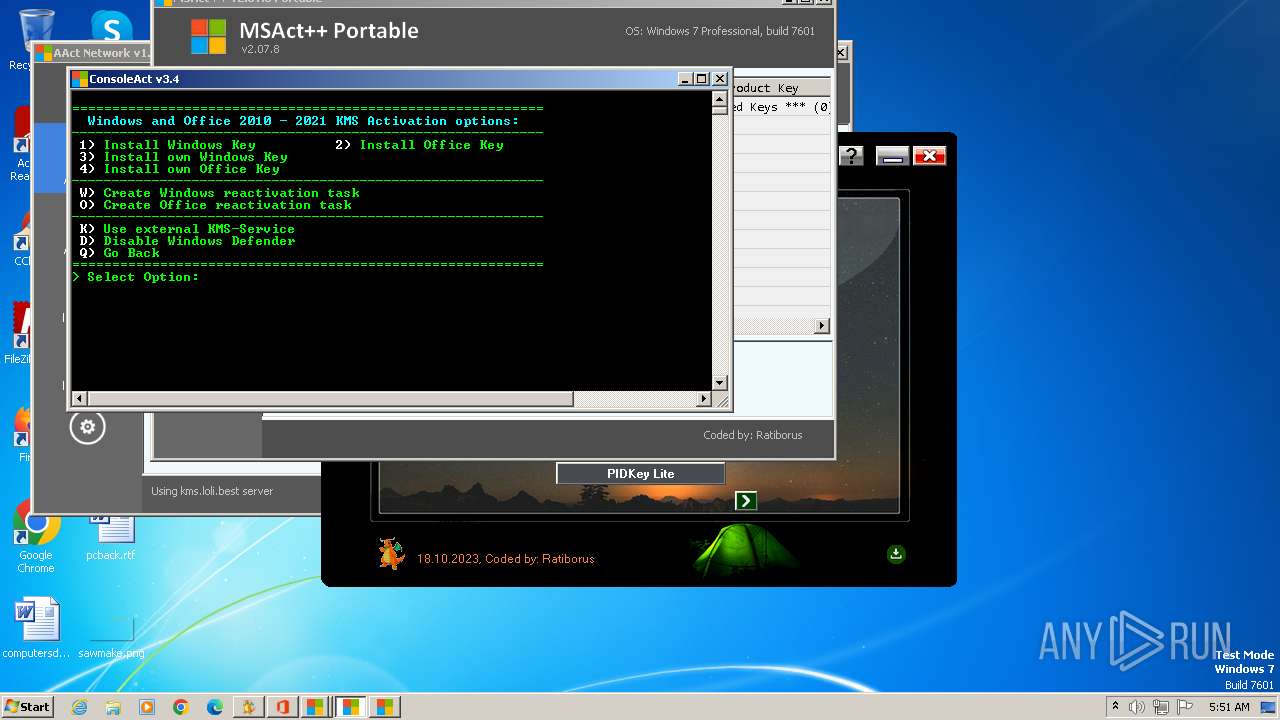
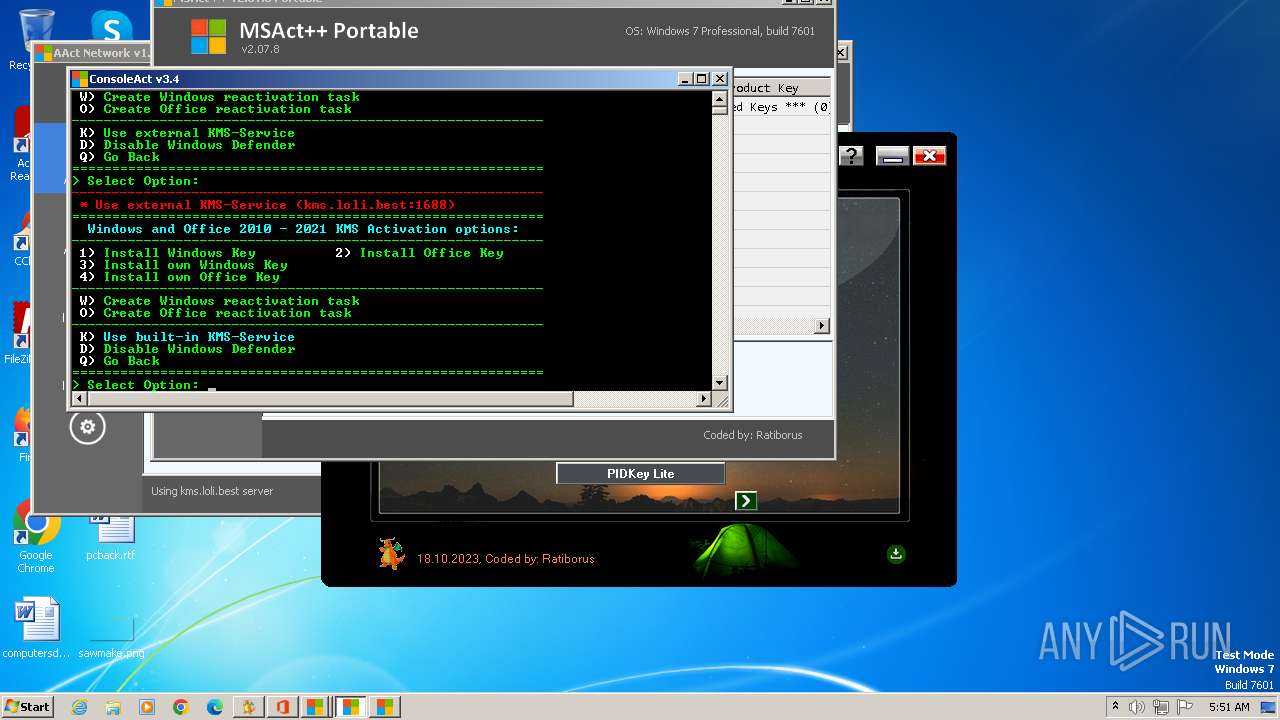
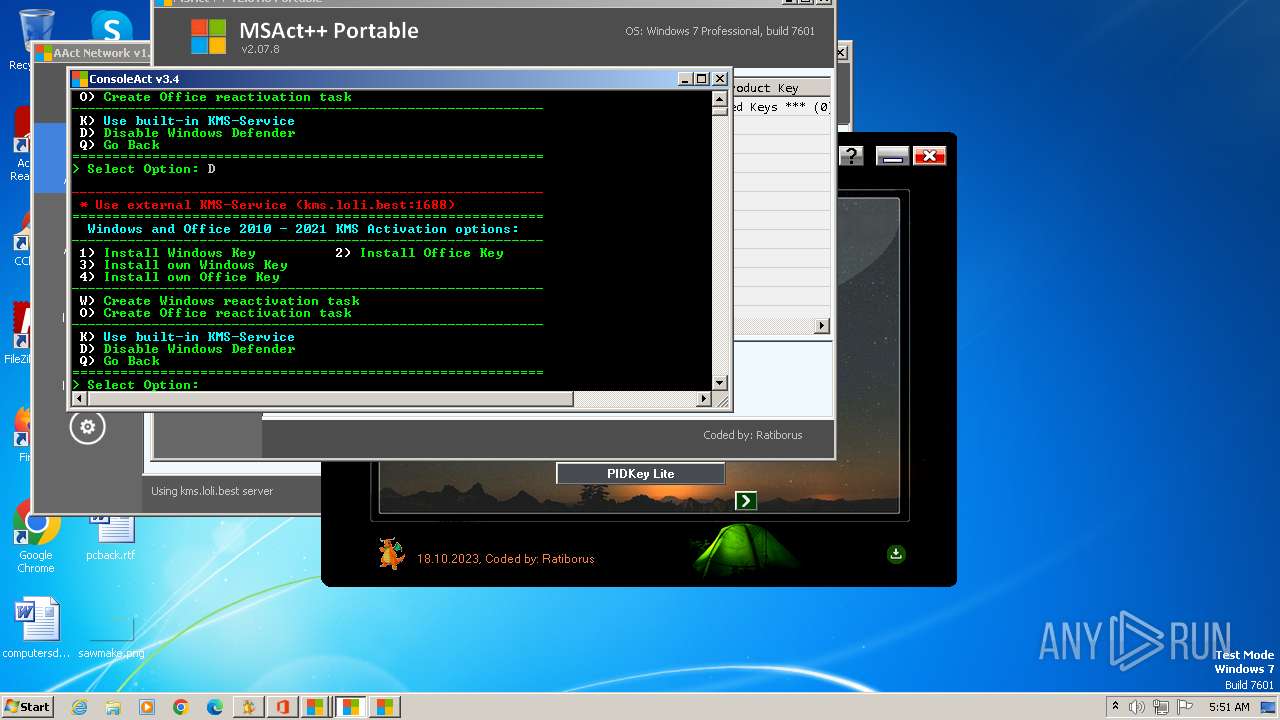
| File name: | KMS Tools Unpack.exe |
| Full analysis: | https://app.any.run/tasks/7d7aab0f-2db3-4643-90f4-7876eb68ff3b |
| Verdict: | Malicious activity |
| Analysis date: | February 06, 2024, 05:46:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 5EC4ACD95E3ABA210511D2807E068097 |
| SHA1: | E308D8F23EBFBC6FEA2FFD967770550DCFB13336 |
| SHA256: | 84B9AF42F0896ADA62D69276ACEC22256BBC984081916BA46605DE987A79BFF4 |
| SSDEEP: | 393216:gzZxuci3RAvov93NXVNUGg5u37XM3m1h7upDQdMD011:gzO1RAwVNn3Q3S0Qd1 |
MALICIOUS
Drops the executable file immediately after the start
- KMS Tools Unpack.exe (PID: 1072)
- KMSTools.exe (PID: 3596)
- OInstall.exe (PID: 3296)
- 7zaxxx.exe (PID: 3432)
- KMSAuto.exe (PID: 3336)
- 7zaxxx.exe (PID: 2752)
- 7zaxxx.exe (PID: 3964)
- 7zaxxx.exe (PID: 3876)
- AAct_Network.exe (PID: 3164)
- 7zaxxx.exe (PID: 1632)
- ConsoleAct.exe (PID: 3388)
- 7zaxxx.exe (PID: 3356)
Actions looks like stealing of personal data
- KMS Tools Unpack.exe (PID: 1072)
Opens a text file (SCRIPT)
- cscript.exe (PID: 3684)
- cscript.exe (PID: 2788)
- cscript.exe (PID: 3528)
- cscript.exe (PID: 1388)
- cscript.exe (PID: 3020)
- cscript.exe (PID: 1932)
- cscript.exe (PID: 2836)
Disables Windows Defender
- reg.exe (PID: 2896)
Antivirus name has been found in the command line (generic signature)
- find.exe (PID: 2244)
- find.exe (PID: 880)
- find.exe (PID: 3416)
- find.exe (PID: 552)
SUSPICIOUS
Starts CMD.EXE for commands execution
- KMSTools.exe (PID: 3596)
- OInstall.exe (PID: 3296)
- KMSAuto.exe (PID: 3336)
- AAct_Network.exe (PID: 3164)
- ConsoleAct.exe (PID: 3388)
- loader.exe (PID: 3688)
- loader.exe (PID: 3400)
- loader.exe (PID: 2588)
- loader.exe (PID: 896)
- loader.exe (PID: 2816)
Executable content was dropped or overwritten
- KMSTools.exe (PID: 3596)
- OInstall.exe (PID: 3296)
- expand.exe (PID: 1540)
- 7zaxxx.exe (PID: 3432)
- KMSAuto.exe (PID: 3336)
- 7zaxxx.exe (PID: 2752)
- 7zaxxx.exe (PID: 3876)
- 7zaxxx.exe (PID: 3964)
- AAct_Network.exe (PID: 3164)
- 7zaxxx.exe (PID: 1632)
- ConsoleAct.exe (PID: 3388)
- 7zaxxx.exe (PID: 3356)
Drops 7-zip archiver for unpacking
- KMSTools.exe (PID: 3596)
Starts POWERSHELL.EXE for commands execution
- OInstall.exe (PID: 3296)
Process drops legitimate windows executable
- OInstall.exe (PID: 3296)
- expand.exe (PID: 1540)
- KMSAuto.exe (PID: 3336)
- 7zaxxx.exe (PID: 3876)
Uses REG/REGEDIT.EXE to modify registry
- OInstall.exe (PID: 3296)
- cmd.exe (PID: 3156)
- cmd.exe (PID: 1820)
- cmd.exe (PID: 3416)
- cmd.exe (PID: 3020)
- cmd.exe (PID: 3592)
- AAct_Network.exe (PID: 3164)
- cmd.exe (PID: 1124)
Probably download files using WebClient
- OInstall.exe (PID: 3296)
Reads the Internet Settings
- powershell.exe (PID: 2472)
- powershell.exe (PID: 1112)
- powershell.exe (PID: 3392)
- powershell.exe (PID: 2348)
- WMIC.exe (PID: 4040)
- signtool.exe (PID: 4016)
- control.exe (PID: 3916)
The Powershell connects to the Internet
- powershell.exe (PID: 2472)
- powershell.exe (PID: 3392)
- powershell.exe (PID: 1112)
- powershell.exe (PID: 2348)
Unusual connection from system programs
- powershell.exe (PID: 1112)
- powershell.exe (PID: 3392)
- powershell.exe (PID: 2472)
- powershell.exe (PID: 2348)
The process drops C-runtime libraries
- expand.exe (PID: 1540)
- 7zaxxx.exe (PID: 3876)
Uses WMIC.EXE
- KMSAuto.exe (PID: 3336)
Starts a Microsoft application from unusual location
- signtool.exe (PID: 4016)
Reads security settings of Internet Explorer
- signtool.exe (PID: 4016)
Reads settings of System Certificates
- signtool.exe (PID: 4016)
Adds/modifies Windows certificates
- signtool.exe (PID: 4016)
Checks Windows Trust Settings
- signtool.exe (PID: 4016)
The process executes VB scripts
- cmd.exe (PID: 2292)
- cmd.exe (PID: 1236)
- cmd.exe (PID: 3744)
- cmd.exe (PID: 1844)
- cmd.exe (PID: 3316)
- cmd.exe (PID: 2300)
- cmd.exe (PID: 2316)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 3684)
- cscript.exe (PID: 2788)
- cscript.exe (PID: 3528)
- cscript.exe (PID: 1388)
- cscript.exe (PID: 3020)
- cscript.exe (PID: 1932)
- cscript.exe (PID: 2836)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 3684)
- cscript.exe (PID: 2788)
- cscript.exe (PID: 3528)
- cscript.exe (PID: 1388)
- cscript.exe (PID: 3020)
- cscript.exe (PID: 1932)
- cscript.exe (PID: 2836)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 3684)
- cscript.exe (PID: 2788)
- cscript.exe (PID: 3528)
- cscript.exe (PID: 1388)
- cscript.exe (PID: 3020)
- cscript.exe (PID: 1932)
- cscript.exe (PID: 2836)
Checks whether a specific file exists (SCRIPT)
- cscript.exe (PID: 3684)
- cscript.exe (PID: 2788)
- cscript.exe (PID: 3528)
- cscript.exe (PID: 1388)
- cscript.exe (PID: 3020)
- cscript.exe (PID: 1932)
- cscript.exe (PID: 2836)
Reads data from a binary Stream object (SCRIPT)
- cscript.exe (PID: 3684)
- cscript.exe (PID: 2788)
- cscript.exe (PID: 3528)
- cscript.exe (PID: 1388)
- cscript.exe (PID: 3020)
- cscript.exe (PID: 1932)
- cscript.exe (PID: 2836)
Executes WMI query (SCRIPT)
- cscript.exe (PID: 3684)
- cscript.exe (PID: 3528)
- cscript.exe (PID: 3020)
- cscript.exe (PID: 1932)
- cscript.exe (PID: 2836)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- cmd.exe (PID: 568)
- cmd.exe (PID: 3504)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 2760)
- cmd.exe (PID: 2560)
- cmd.exe (PID: 980)
The executable file from the user directory is run by the CMD process
- test.exe (PID: 1820)
- test.dat (PID: 2316)
Connects to unusual port
- test.exe (PID: 1820)
- test.dat (PID: 2316)
Starts application with an unusual extension
- cmd.exe (PID: 3272)
Executing commands from ".cmd" file
- loader.exe (PID: 3688)
- loader.exe (PID: 3400)
- loader.exe (PID: 2588)
- loader.exe (PID: 896)
- loader.exe (PID: 2816)
Starts SC.EXE for service management
- cmd.exe (PID: 1124)
Uses WMIC.EXE to obtain service application data
- cmd.exe (PID: 1124)
Get information on the list of running processes
- cmd.exe (PID: 4044)
- cmd.exe (PID: 2744)
- cmd.exe (PID: 1636)
- cmd.exe (PID: 3916)
INFO
Reads the computer name
- KMS Tools Unpack.exe (PID: 1072)
- KMSTools.exe (PID: 3596)
- OInstall.exe (PID: 3296)
- oinstrun.exe (PID: 124)
- 7zaxxx.exe (PID: 3432)
- signtool.exe (PID: 4016)
- 7zaxxx.exe (PID: 2752)
- 7zaxxx.exe (PID: 3876)
- 7zaxxx.exe (PID: 3964)
- test.exe (PID: 1820)
- 7zaxxx.exe (PID: 1632)
- loader.exe (PID: 3688)
- loader.exe (PID: 3400)
- test.dat (PID: 2316)
- loader.exe (PID: 2588)
- loader.exe (PID: 896)
- 7zaxxx.exe (PID: 3356)
- MSAct++.exe (PID: 3432)
- loader.exe (PID: 2816)
Checks supported languages
- KMS Tools Unpack.exe (PID: 1072)
- KMSTools.exe (PID: 3596)
- 7zaxxx.exe (PID: 3876)
- OInstall.exe (PID: 3296)
- oinstrun.exe (PID: 124)
- 7zaxxx.exe (PID: 3432)
- KMSAuto.exe (PID: 3336)
- signtool.exe (PID: 4016)
- 7zaxxx.exe (PID: 2752)
- AAct.exe (PID: 1692)
- 7zaxxx.exe (PID: 3964)
- AAct_Network.exe (PID: 3164)
- test.exe (PID: 1820)
- ConsoleAct.exe (PID: 3388)
- 7zaxxx.exe (PID: 1632)
- test.dat (PID: 2316)
- loader.exe (PID: 3688)
- loader.exe (PID: 3400)
- loader.exe (PID: 896)
- 7zaxxx.exe (PID: 3356)
- MSAct++.exe (PID: 3432)
- loader.exe (PID: 2588)
- loader.exe (PID: 2816)
Manual execution by a user
- KMSTools.exe (PID: 3596)
- KMSTools.exe (PID: 3020)
Reads Environment values
- KMSTools.exe (PID: 3596)
- OInstall.exe (PID: 3296)
- KMSAuto.exe (PID: 3336)
- AAct_Network.exe (PID: 3164)
- AAct.exe (PID: 1692)
- ConsoleAct.exe (PID: 3388)
- MSAct++.exe (PID: 3432)
Create files in a temporary directory
- KMSTools.exe (PID: 3596)
- OInstall.exe (PID: 3296)
- expand.exe (PID: 2852)
- expand.exe (PID: 3724)
- KMSAuto.exe (PID: 3336)
- signtool.exe (PID: 4016)
- AAct_Network.exe (PID: 3164)
- ConsoleAct.exe (PID: 3388)
Creates files in the program directory
- OInstall.exe (PID: 3296)
- expand.exe (PID: 1540)
- expand.exe (PID: 2052)
Drops the executable file immediately after the start
- expand.exe (PID: 1540)
Reads product name
- KMSAuto.exe (PID: 3336)
- AAct_Network.exe (PID: 3164)
- AAct.exe (PID: 1692)
- ConsoleAct.exe (PID: 3388)
- MSAct++.exe (PID: 3432)
Reads the machine GUID from the registry
- signtool.exe (PID: 4016)
- test.exe (PID: 1820)
- test.dat (PID: 2316)
- MSAct++.exe (PID: 3432)
Reads security settings of Internet Explorer
- cscript.exe (PID: 3684)
- cscript.exe (PID: 2788)
- cscript.exe (PID: 3528)
- cscript.exe (PID: 1388)
- cscript.exe (PID: 3020)
- cscript.exe (PID: 1932)
- cscript.exe (PID: 2836)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (72.3) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (11.7) |
| .exe | | | Win16/32 Executable Delphi generic (5.4) |
| .exe | | | Generic Win/DOS Executable (5.2) |
| .exe | | | DOS Executable Generic (5.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:10:17 13:07:32+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 376832 |
| InitializedDataSize: | 52602368 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
Total processes
277
Monitored processes
169
Malicious processes
23
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Users\admin\AppData\Local\Temp\oinstrun.exe" /w OfficeClickToRun.exe deliverymechanism=5030841d-c919-4594-8d2d-84ae4f96e58e platform=x64 productreleaseid=none culture=en-us defaultplatform=False lcid=1033 b= storeid= forceupgrade=True piniconstotaskbar=False pidkeys=KNH8D-FGHT4-T8RK3-CTDYJ-K2HT4,FTNWT-C6WBT-8HMGF-K9PRX-QV9H8,FXYTK-NJJ8C-GB6DW-3DYQT-6F7TH forceappshutdown=True autoactivate=1 productstoadd=ProPlus2021Volume.16_en-us_x-none|ProjectPro2021Volume.16_en-us_x-none|VisioPro2021Volume.16_en-us_x-none|ProofingTools.16_en-us_x-none scenario=unknown updatesenabled.16=True acceptalleulas.16=True cdnbaseurl.16=http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e version.16=16.0.14332.20624 mediatype.16=CDN baseurl.16=http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e sourcetype.16=CDN displaylevel=True uninstallpreviousversion=True ProPlus2021Volume.excludedapps.16=teams ProjectPro2021Volume.excludedapps.16=teams VisioPro2021Volume.excludedapps.16=teams ProofingTools.excludedapps.16=teams | C:\Users\admin\AppData\Local\Temp\oinstrun.exe | — | OInstall.exe | |||||||||||
User: admin Company: Awoo~ Integrity Level: HIGH Description: Run any process with TrustedInstaller privileges Exit code: 0 Version: 5.5.0.0 Modules
| |||||||||||||||
| 296 | "cmd.exe" /c cls | C:\Windows\System32\cmd.exe | — | ConsoleAct.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 324 | "cmd.exe" /c cls | C:\Windows\System32\cmd.exe | — | ConsoleAct.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 332 | Netsh.exe Advfirewall Firewall delete rule name=0pen_Port_KMS protocol=TCP | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 332 | "C:\Windows\System32\cmd.exe" /c copy C:\Windows\System32\Tasks\ConsoleAct "C:\Users\admin\AppData\Local\Temp\ConsoleAct.tmp" /Y 2>&1 | C:\Windows\System32\cmd.exe | — | ConsoleAct.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 532 | "C:\Windows\System32\reg.exe" query "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender" /v DisableAntiSpyware | C:\Windows\System32\reg.exe | — | ConsoleAct.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 552 | Find /I "MsMpEng.exe" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Find String (grep) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 568 | "C:\Windows\System32\cmd.exe" /c Netsh.exe Advfirewall Firewall delete rule name=AAct_Network protocol=TCP | C:\Windows\System32\cmd.exe | — | AAct_Network.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 568 | "C:\Windows\System32\reg.exe" query "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender" /v DisableAntiSpyware | C:\Windows\System32\reg.exe | — | ConsoleAct.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 668 | reg.exe add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Office\ClickToRun\Configuration" /f /v "UpdateChannel" /t REG_SZ /d http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
17 303
Read events
17 029
Write events
274
Delete events
0
Modification events
| (PID) Process: | (1072) KMS Tools Unpack.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1072) KMS Tools Unpack.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | Browse For Folder Width |
Value: 318 | |||
| (PID) Process: | (1072) KMS Tools Unpack.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | Browse For Folder Height |
Value: 288 | |||
| (PID) Process: | (3596) KMSTools.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\MediaResources\DirectSound\Speaker Configuration |
| Operation: | write | Name: | Speaker Configuration |
Value: 4 | |||
| (PID) Process: | (3296) OInstall.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\MediaResources\DirectSound\Speaker Configuration |
| Operation: | write | Name: | Speaker Configuration |
Value: 4 | |||
| (PID) Process: | (4016) signtool.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4016) signtool.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EnterpriseCertificates\Root\Certificates\9F6134C5FA75E4FDDE631B232BE961D6D4B97DB6 |
| Operation: | write | Name: | Blob |
Value: 0300000001000000140000009F6134C5FA75E4FDDE631B232BE961D6D4B97DB6200000000100000047030000308203433082022BA00302010202147327B7C17D5AE708EF73F1F45A79D78B4E99A29F300D06092A864886F70D01010B05003031310B3009060355040613025553310F300D06035504080C06426F73746F6E3111300F060355040A0C084469676943657274301E170D3233303932393130353030335A170D3339303530383130353030335A3031310B3009060355040613025553310F300D06035504080C06426F73746F6E3111300F060355040A0C08446967694365727430820122300D06092A864886F70D01010105000382010F003082010A0282010100D91B7A55548F44F3E97C493153B75B055695736B184640D7335A2E6218083B5A1BEE2695209350E57A3EB76FBC604CB3B250DF3D9D0C560D1FBDFE30108D233A3C555100BE1A3F8E543C0B253E06E91B6D5F9CB3A093009BC8B4D3A0EB19DB59E56DA7E3D637847970D6C2AEB4A1FCF3896A7C080FE68759BAA62E6AAA8B7C7CBDA176DDC72F8D259A16D3469E31F19D2959904611D730D7D26FCFED789A0C49698FDFABF3F6727D08C61A073BB11E85C96486D49B0E0D38364C008A5EB964F8813C5DF004F9E76D2F8DB90702D800032674959BF0DF823785419101CEA928A10ACBAE7E48FE19202F3CB7BCF416476D17CB64C5570FCED443BD75D9F2C632FF0203010001A3533051301D0603551D0E041604145D6CA352CEFC713CBBC5E21F663C3639FD19D4D7301F0603551D230418301680145D6CA352CEFC713CBBC5E21F663C3639FD19D4D7300F0603551D130101FF040530030101FF300D06092A864886F70D01010B05000382010100AF2218E4CA18144728FCC76EA14958061522FD4A018BED1A4BFCC5CCE70BC6AE9DF7D3795C9A010D53628E2B6E7C10D6B07E53546235A5EE480E5A434E312154BF1E39AAC27D2C18D4F41CBBECFE4538CEF93EF62C17D187A7F720F4A9478410D09620C9F8B293B5786A5440BC0743B7B7753CF66FBA498B7E083BC267597238DC031B9BB131F997D9B8164AAED0D6E328420E53E1969DA6CD035078179677A7177BB2BF9C87CF592910CD380E8501B92040A39469C782BA383BEAE498C060FCC7C429BC10B7B6B7A0659C9BE03DC13DB46C638CF5E3B22A303726906DC8DD91C64501EBFC282A3A497EC430CACC066EE4BF9C5C8F2F2A05D0C1921A9E3E85E3 | |||
| (PID) Process: | (4016) signtool.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EnterpriseCertificates\Root\Certificates\9F6134C5FA75E4FDDE631B232BE961D6D4B97DB6 |
| Operation: | write | Name: | Blob |
Value: 0F00000001000000200000009065F32AFC2CFEA7F452D2D6BE94D20C877EFC1C05433D9935696193FDCC05D80300000001000000140000009F6134C5FA75E4FDDE631B232BE961D6D4B97DB6200000000100000047030000308203433082022BA00302010202147327B7C17D5AE708EF73F1F45A79D78B4E99A29F300D06092A864886F70D01010B05003031310B3009060355040613025553310F300D06035504080C06426F73746F6E3111300F060355040A0C084469676943657274301E170D3233303932393130353030335A170D3339303530383130353030335A3031310B3009060355040613025553310F300D06035504080C06426F73746F6E3111300F060355040A0C08446967694365727430820122300D06092A864886F70D01010105000382010F003082010A0282010100D91B7A55548F44F3E97C493153B75B055695736B184640D7335A2E6218083B5A1BEE2695209350E57A3EB76FBC604CB3B250DF3D9D0C560D1FBDFE30108D233A3C555100BE1A3F8E543C0B253E06E91B6D5F9CB3A093009BC8B4D3A0EB19DB59E56DA7E3D637847970D6C2AEB4A1FCF3896A7C080FE68759BAA62E6AAA8B7C7CBDA176DDC72F8D259A16D3469E31F19D2959904611D730D7D26FCFED789A0C49698FDFABF3F6727D08C61A073BB11E85C96486D49B0E0D38364C008A5EB964F8813C5DF004F9E76D2F8DB90702D800032674959BF0DF823785419101CEA928A10ACBAE7E48FE19202F3CB7BCF416476D17CB64C5570FCED443BD75D9F2C632FF0203010001A3533051301D0603551D0E041604145D6CA352CEFC713CBBC5E21F663C3639FD19D4D7301F0603551D230418301680145D6CA352CEFC713CBBC5E21F663C3639FD19D4D7300F0603551D130101FF040530030101FF300D06092A864886F70D01010B05000382010100AF2218E4CA18144728FCC76EA14958061522FD4A018BED1A4BFCC5CCE70BC6AE9DF7D3795C9A010D53628E2B6E7C10D6B07E53546235A5EE480E5A434E312154BF1E39AAC27D2C18D4F41CBBECFE4538CEF93EF62C17D187A7F720F4A9478410D09620C9F8B293B5786A5440BC0743B7B7753CF66FBA498B7E083BC267597238DC031B9BB131F997D9B8164AAED0D6E328420E53E1969DA6CD035078179677A7177BB2BF9C87CF592910CD380E8501B92040A39469C782BA383BEAE498C060FCC7C429BC10B7B6B7A0659C9BE03DC13DB46C638CF5E3B22A303726906DC8DD91C64501EBFC282A3A497EC430CACC066EE4BF9C5C8F2F2A05D0C1921A9E3E85E3 | |||
| (PID) Process: | (4016) signtool.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\2B8F1B57330DBBA2D07A6C51F70EE90DDAB9AD8E |
| Operation: | write | Name: | Blob |
Value: 53000000010000004300000030413022060C2B06010401B231010201050130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C0190000000100000010000000EA6089055218053DD01E37E1D806EEDF620000000100000020000000E793C9B02FD8AA13E21C31228ACCB08119643B749C898964B1746D46C3D4CBD21400000001000000140000005379BF5AAA2B4ACF5480E1D89BC09DF2B20366CB1D0000000100000010000000885010358D29A38F059B028559C95F900B00000001000000100000005300650063007400690067006F0000000300000001000000140000002B8F1B57330DBBA2D07A6C51F70EE90DDAB9AD8E0F000000010000003000000066B764A96581128168CF208E374DDA479D54E311F32457F4AEE0DBD2A6C8D171D531289E1CD22BFDBBD4CFD979625483090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703082000000001000000E2050000308205DE308203C6A003020102021001FD6D30FCA3CA51A81BBC640E35032D300D06092A864886F70D01010C0500308188310B3009060355040613025553311330110603550408130A4E6577204A6572736579311430120603550407130B4A65727365792043697479311E301C060355040A131554686520555345525452555354204E6574776F726B312E302C06035504031325555345525472757374205253412043657274696669636174696F6E20417574686F72697479301E170D3130303230313030303030305A170D3338303131383233353935395A308188310B3009060355040613025553311330110603550408130A4E6577204A6572736579311430120603550407130B4A65727365792043697479311E301C060355040A131554686520555345525452555354204E6574776F726B312E302C06035504031325555345525472757374205253412043657274696669636174696F6E20417574686F7269747930820222300D06092A864886F70D01010105000382020F003082020A028202010080126517360EC3DB08B3D0AC570D76EDCD27D34CAD508361E2AA204D092D6409DCCE899FCC3DA9ECF6CFC1DCF1D3B1D67B3728112B47DA39C6BC3A19B45FA6BD7D9DA36342B676F2A93B2B91F8E26FD0EC162090093EE2E874C918B491D46264DB7FA306F188186A90223CBCFE13F087147BF6E41F8ED4E451C61167460851CB8614543FBC33FE7E6C9CFF169D18BD518E35A6A766C87267DB2166B1D49B7803C0503AE8CCF0DCBC9E4CFEAF0596351F575AB7FFCEF93DB72CB6F654DDC8E7123A4DAE4C8AB75C9AB4B7203DCA7F2234AE7E3B68660144E7014E46539B3360F794BE5337907343F332C353EFDBAAFE744E69C76B8C6093DEC4C70CDFE132AECC933B517895678BEE3D56FE0CD0690F1B0FF325266B336DF76E47FA7343E57E0EA566B1297C3284635589C40DC19354301913ACD37D37A7EB5D3A6C355CDB41D712DAA9490BDFD8808A0993628EB566CF2588CD84B8B13FA4390FD9029EEB124C957CF36B05A95E1683CCB867E2E8139DCC5B82D34CB3ED5BFFDEE573AC233B2D00BF3555740949D849581A7F9236E651920EF3267D1C4D17BCC9EC4326D0BF415F40A94444F499E757879E501F5754A83EFD74632FB1506509E658422E431A4CB4F0254759FA041E93D426464A5081B2DEBE78B7FC6715E1C957841E0F63D6E962BAD65F552EEA5CC62808042539B80E2BA9F24C971C073F0D52F5EDEF2F820F0203010001A3423040301D0603551D0E041604145379BF5AAA2B4ACF5480E1D89BC09DF2B20366CB300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF300D06092A864886F70D01010C050003820201005CD47C0DCFF7017D4199650C73C5529FCBF8CF99067F1BDA43159F9E0255579614F1523C27879428ED1F3A0137A276FC5350C0849BC66B4EBA8C214FA28E556291F36915D8BC88E3C4AA0BFDEFA8E94B552A06206D55782919EE5F305C4B241155FF249A6E5E2A2BEE0B4D9F7FF70138941495430709FB60A9EE1CAB128CA09A5EA7986A596D8B3F08FBC8D145AF18156490120F73282EC5E2244EFC58ECF0F445FE22B3EB2F8ED2D9456105C1976FA876728F8B8C36AFBF0D05CE718DE6A66F1F6CA67162C5D8D083720CF16711890C9C134C7234DFBCD571DFAA71DDE1B96C8C3C125D65DABD5712B6436BFFE5DE4D661151CF99AEEC17B6E871918CDE49FEDD3571A21527941CCF61E326BB6FA36725215DE6DD1D0B2E681B3B82AFEC836785D4985174B1B9998089FF7F78195C794A602E9240AE4C372A2CC9C762C80E5DF7365BCAE0252501B4DD1A079C77003FD0DCD5EC3DD4FABB3FCC85D66F7FA92DDFB902F7F5979AB535DAC367B0874AA9289E238EFF5C276BE1B04FF307EE002ED45987CB524195EAF447D7EE6441557C8D590295DD629DC2B9EE5A287484A59BB790C70C07DFF589367432D628C1B0B00BE09C4CC31CD6FCE369B54746812FA282ABD3634470C48DFF2D33BAAD8F7BB57088AE3E19CF4028D8FCC890BB5D9922F552E658C51F883143EE881DD7C68E3C436A1DA718DE7D3D16F162F9CA90A8FD | |||
| (PID) Process: | (4016) signtool.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\2B8F1B57330DBBA2D07A6C51F70EE90DDAB9AD8E |
| Operation: | write | Name: | Blob |
Value: 0400000001000000100000001BFE69D191B71933A372A80FE155E5B5090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703080F000000010000003000000066B764A96581128168CF208E374DDA479D54E311F32457F4AEE0DBD2A6C8D171D531289E1CD22BFDBBD4CFD9796254830300000001000000140000002B8F1B57330DBBA2D07A6C51F70EE90DDAB9AD8E0B00000001000000100000005300650063007400690067006F0000001D0000000100000010000000885010358D29A38F059B028559C95F901400000001000000140000005379BF5AAA2B4ACF5480E1D89BC09DF2B20366CB620000000100000020000000E793C9B02FD8AA13E21C31228ACCB08119643B749C898964B1746D46C3D4CBD2190000000100000010000000EA6089055218053DD01E37E1D806EEDF53000000010000004300000030413022060C2B06010401B231010201050130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C02000000001000000E2050000308205DE308203C6A003020102021001FD6D30FCA3CA51A81BBC640E35032D300D06092A864886F70D01010C0500308188310B3009060355040613025553311330110603550408130A4E6577204A6572736579311430120603550407130B4A65727365792043697479311E301C060355040A131554686520555345525452555354204E6574776F726B312E302C06035504031325555345525472757374205253412043657274696669636174696F6E20417574686F72697479301E170D3130303230313030303030305A170D3338303131383233353935395A308188310B3009060355040613025553311330110603550408130A4E6577204A6572736579311430120603550407130B4A65727365792043697479311E301C060355040A131554686520555345525452555354204E6574776F726B312E302C06035504031325555345525472757374205253412043657274696669636174696F6E20417574686F7269747930820222300D06092A864886F70D01010105000382020F003082020A028202010080126517360EC3DB08B3D0AC570D76EDCD27D34CAD508361E2AA204D092D6409DCCE899FCC3DA9ECF6CFC1DCF1D3B1D67B3728112B47DA39C6BC3A19B45FA6BD7D9DA36342B676F2A93B2B91F8E26FD0EC162090093EE2E874C918B491D46264DB7FA306F188186A90223CBCFE13F087147BF6E41F8ED4E451C61167460851CB8614543FBC33FE7E6C9CFF169D18BD518E35A6A766C87267DB2166B1D49B7803C0503AE8CCF0DCBC9E4CFEAF0596351F575AB7FFCEF93DB72CB6F654DDC8E7123A4DAE4C8AB75C9AB4B7203DCA7F2234AE7E3B68660144E7014E46539B3360F794BE5337907343F332C353EFDBAAFE744E69C76B8C6093DEC4C70CDFE132AECC933B517895678BEE3D56FE0CD0690F1B0FF325266B336DF76E47FA7343E57E0EA566B1297C3284635589C40DC19354301913ACD37D37A7EB5D3A6C355CDB41D712DAA9490BDFD8808A0993628EB566CF2588CD84B8B13FA4390FD9029EEB124C957CF36B05A95E1683CCB867E2E8139DCC5B82D34CB3ED5BFFDEE573AC233B2D00BF3555740949D849581A7F9236E651920EF3267D1C4D17BCC9EC4326D0BF415F40A94444F499E757879E501F5754A83EFD74632FB1506509E658422E431A4CB4F0254759FA041E93D426464A5081B2DEBE78B7FC6715E1C957841E0F63D6E962BAD65F552EEA5CC62808042539B80E2BA9F24C971C073F0D52F5EDEF2F820F0203010001A3423040301D0603551D0E041604145379BF5AAA2B4ACF5480E1D89BC09DF2B20366CB300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF300D06092A864886F70D01010C050003820201005CD47C0DCFF7017D4199650C73C5529FCBF8CF99067F1BDA43159F9E0255579614F1523C27879428ED1F3A0137A276FC5350C0849BC66B4EBA8C214FA28E556291F36915D8BC88E3C4AA0BFDEFA8E94B552A06206D55782919EE5F305C4B241155FF249A6E5E2A2BEE0B4D9F7FF70138941495430709FB60A9EE1CAB128CA09A5EA7986A596D8B3F08FBC8D145AF18156490120F73282EC5E2244EFC58ECF0F445FE22B3EB2F8ED2D9456105C1976FA876728F8B8C36AFBF0D05CE718DE6A66F1F6CA67162C5D8D083720CF16711890C9C134C7234DFBCD571DFAA71DDE1B96C8C3C125D65DABD5712B6436BFFE5DE4D661151CF99AEEC17B6E871918CDE49FEDD3571A21527941CCF61E326BB6FA36725215DE6DD1D0B2E681B3B82AFEC836785D4985174B1B9998089FF7F78195C794A602E9240AE4C372A2CC9C762C80E5DF7365BCAE0252501B4DD1A079C77003FD0DCD5EC3DD4FABB3FCC85D66F7FA92DDFB902F7F5979AB535DAC367B0874AA9289E238EFF5C276BE1B04FF307EE002ED45987CB524195EAF447D7EE6441557C8D590295DD629DC2B9EE5A287484A59BB790C70C07DFF589367432D628C1B0B00BE09C4CC31CD6FCE369B54746812FA282ABD3634470C48DFF2D33BAAD8F7BB57088AE3E19CF4028D8FCC890BB5D9922F552E658C51F883143EE881DD7C68E3C436A1DA718DE7D3D16F162F9CA90A8FD | |||
Executable files
235
Suspicious files
48
Text files
53
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1072 | KMS Tools Unpack.exe | C:\Users\admin\Desktop\KMSTools.exe | — | |
MD5:— | SHA256:— | |||
| 3596 | KMSTools.exe | C:\Users\admin\AppData\Local\Temp\data.pak | — | |
MD5:— | SHA256:— | |||
| 3596 | KMSTools.exe | C:\Users\admin\AppData\Local\Temp\7zaxxx.exe | executable | |
MD5:EC79CABD55A14379E4D676BB17D9E3DF | SHA256:44A55F5D9C31D0990DE47B9893E0C927478930CEF06FBE2D1F520A6D6CBA587D | |||
| 3876 | 7zaxxx.exe | C:\Users\admin\Desktop\Programs\Office 2013-2021 C2R Install\readme_ru.txt | text | |
MD5:D6CFF24C5745BD08F8DBC46DFEB7083B | SHA256:8C82C0E50D4F3D96F31069BE83F47860A5A0BC8CA4C24073090BE92AB60C9EEB | |||
| 3876 | 7zaxxx.exe | C:\Users\admin\Desktop\Programs\Office 2013-2021 C2R Install\readme_en.txt | text | |
MD5:909A3EB9EBD2F1D83CBEB9196CFB32C9 | SHA256:7F24E5339CCE72300C1AE1766BB6CC33B4812A490AA7D99F52701B9D6C818676 | |||
| 3876 | 7zaxxx.exe | C:\Users\admin\Desktop\Programs\Office 2013-2021 C2R Install\OInstall.exe | executable | |
MD5:50051288FAD11BC6F3EA622EB43CBB6C | SHA256:A29A6AC6ED24FFFC4D8B9D7B73006438637126908152C448ECB2FF21B4D48ABC | |||
| 3876 | 7zaxxx.exe | C:\Users\admin\Desktop\Programs\Office 2013-2021 C2R Install\files\Uninstall.xml | text | |
MD5:364F86F97324EA82FE0D142CD01CF6DD | SHA256:09D5B42140BAB13165BA97FBD0E77792304C3C93555BE02C3DCE21A7A69C66DD | |||
| 3296 | OInstall.exe | C:\Users\admin\Desktop\Programs\Office 2013-2021 C2R Install\files\Configure.xml | text | |
MD5:B8F2DDFACC0F036AE34E0802284CDC07 | SHA256:0A694E2C0022869A02F721CBEC2698CA9346D2C24561E098C7A819CF60C7FBB5 | |||
| 3876 | 7zaxxx.exe | C:\Users\admin\Desktop\Programs\Office 2013-2021 C2R Install\files\x64\msvcr100.dll | executable | |
MD5:DF3CA8D16BDED6A54977B30E66864D33 | SHA256:1D1A1AE540BA132F998D60D3622F0297B6E86AE399332C3B47462D7C0F560A36 | |||
| 3876 | 7zaxxx.exe | C:\Users\admin\Desktop\Programs\Office 2013-2021 C2R Install\files\Configure.xml | text | |
MD5:1053AEF0BBFAAA20F6F642D4FA8B2D5F | SHA256:83A770A54875F0C8025F13F8AAFE9F1C3EF5E0B7147705A3E0F2DED6327C9087 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
13
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2472 | powershell.exe | GET | 200 | 152.199.21.175:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/v32.cab | unknown | compressed | 10.9 Kb | unknown |
— | — | GET | 200 | 152.199.21.175:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/v32.cab | unknown | compressed | 10.9 Kb | unknown |
2348 | powershell.exe | GET | 200 | 152.199.21.175:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/16.0.14332.20624/i321033.cab | unknown | compressed | 9.86 Kb | unknown |
1112 | powershell.exe | GET | 200 | 152.199.21.175:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/16.0.14332.20624/i320.cab | unknown | compressed | 23.5 Mb | unknown |
4016 | signtool.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?68ea4eb7b6f45a30 | unknown | compressed | 65.2 Kb | unknown |
3112 | WmiPrvSE.exe | POST | 302 | 2.19.246.123:80 | http://go.microsoft.com/fwlink/?LinkID=88339 | unknown | — | — | unknown |
3112 | WmiPrvSE.exe | POST | 302 | 2.19.246.123:80 | http://go.microsoft.com/fwlink/?LinkID=88340 | unknown | — | — | unknown |
3112 | WmiPrvSE.exe | POST | 302 | 2.19.246.123:80 | http://go.microsoft.com/fwlink/?LinkID=88341 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2472 | powershell.exe | 152.199.21.175:80 | officecdn.microsoft.com | EDGECAST | DE | whitelisted |
3392 | powershell.exe | 152.199.21.175:80 | officecdn.microsoft.com | EDGECAST | DE | whitelisted |
1112 | powershell.exe | 152.199.21.175:80 | officecdn.microsoft.com | EDGECAST | DE | whitelisted |
2348 | powershell.exe | 152.199.21.175:80 | officecdn.microsoft.com | EDGECAST | DE | whitelisted |
4016 | signtool.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
1820 | test.exe | 106.55.134.25:1688 | kms.loli.best | Shenzhen Tencent Computer Systems Company Limited | CN | unknown |
3112 | WmiPrvSE.exe | 2.19.246.123:80 | go.microsoft.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
officecdn.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
kms.loli.best |
| unknown |
go.microsoft.com |
| whitelisted |
activation.sls.microsoft.com |
| whitelisted |