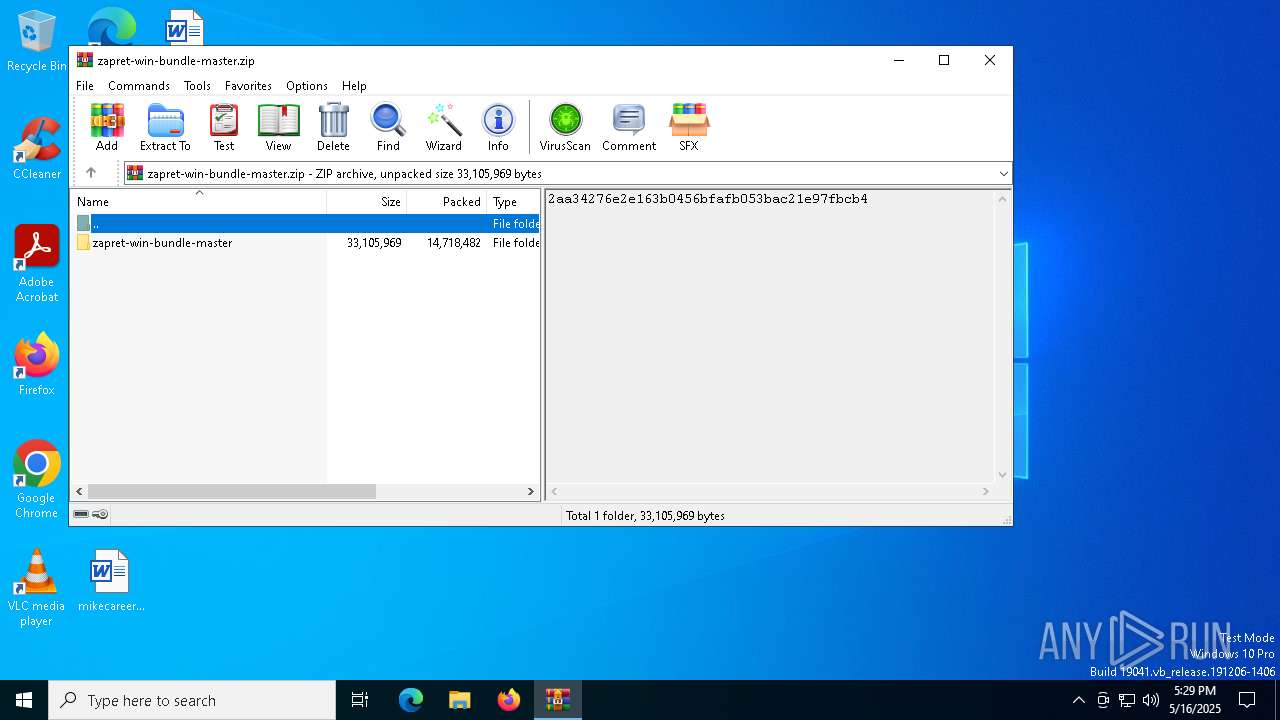
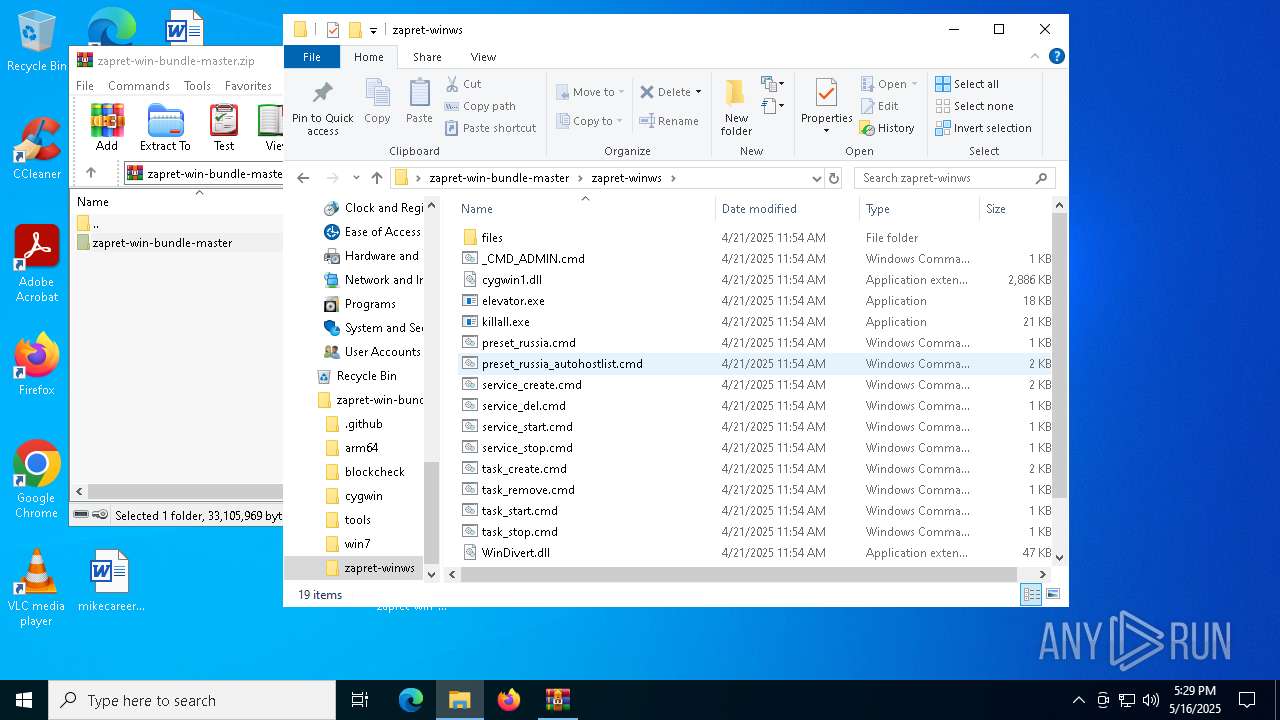
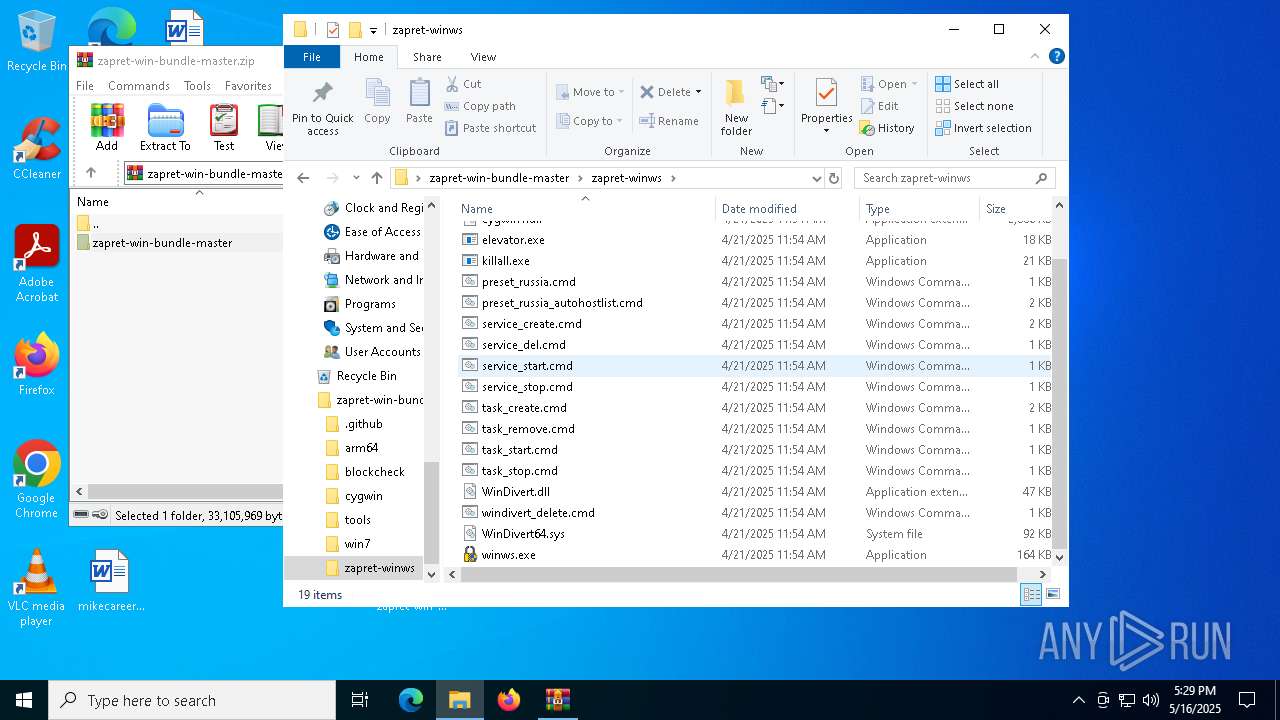
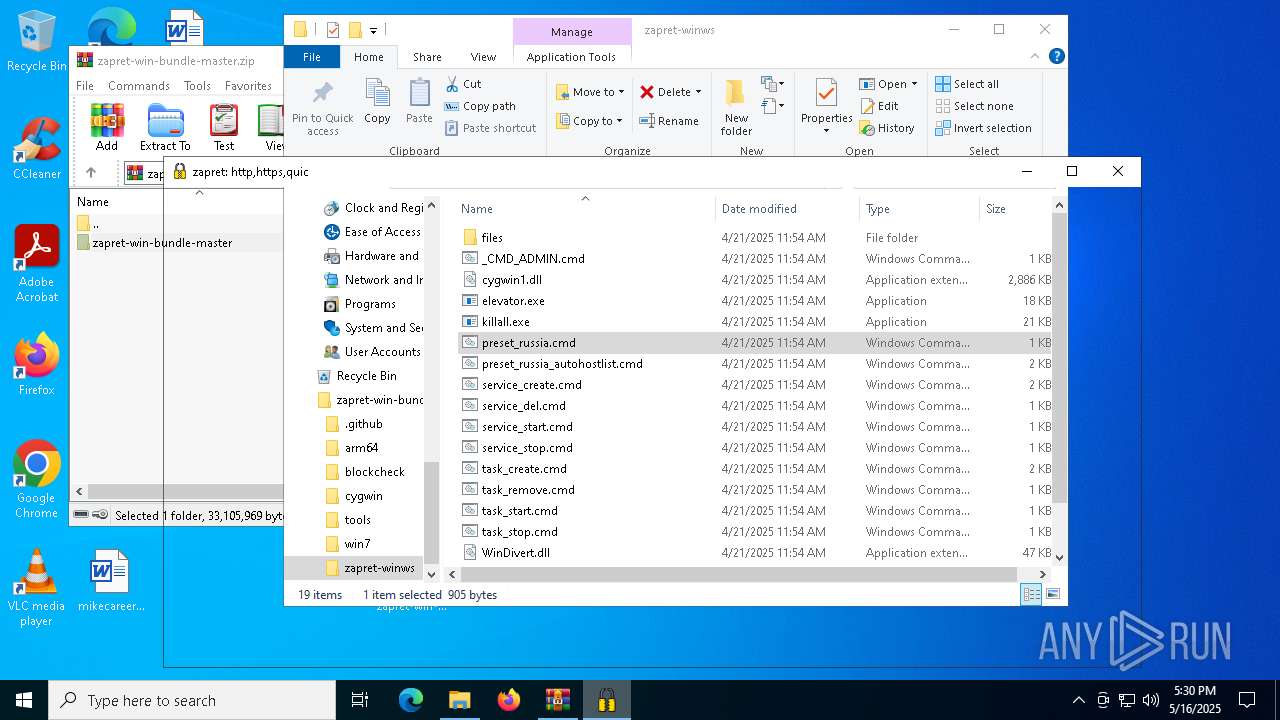
| File name: | zapret-win-bundle-master.zip |
| Full analysis: | https://app.any.run/tasks/2c320781-e239-496f-a651-2134e36953b7 |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 17:29:10 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 2D129FDAC5DD5E12350ED83A5A40CA82 |
| SHA1: | 68703CD91BF1FADEED2C88E8D0034F6AC00B8E23 |
| SHA256: | 849BC52B4682E57F86313DB3BF79EECDDB423DBF88548D0640180C18DEA64E58 |
| SSDEEP: | 98304:LDEcZZlTxE/KIwPB7SMwlsgecngos5qdkcjYcZ4v3rxblQT0U5sghW8n9poYTo3s:MSRTct1ifqnmSFnmaClHdk |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7308)
Malicious driver has been detected
- WinRAR.exe (PID: 7308)
Detects Cygwin installation
- WinRAR.exe (PID: 7308)
SUSPICIOUS
Starts SC.EXE for service management
- cmd.exe (PID: 7680)
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 7308)
Windows service management via SC.EXE
- sc.exe (PID: 7744)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7308)
Manual execution by a user
- cmd.exe (PID: 7680)
- cmd.exe (PID: 7988)
Reads the computer name
- winws.exe (PID: 8132)
The sample compiled with english language support
- WinRAR.exe (PID: 7308)
Checks supported languages
- winws.exe (PID: 8132)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:04:21 04:54:18 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | zapret-win-bundle-master/ |
Total processes
135
Monitored processes
13
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 7308 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\zapret-win-bundle-master.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7436 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7468 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7580 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7680 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\zapret-win-bundle-master\zapret-winws\service_start.cmd" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7688 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7744 | sc start winws1 | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7988 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\zapret-win-bundle-master\zapret-winws\preset_russia.cmd" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7996 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
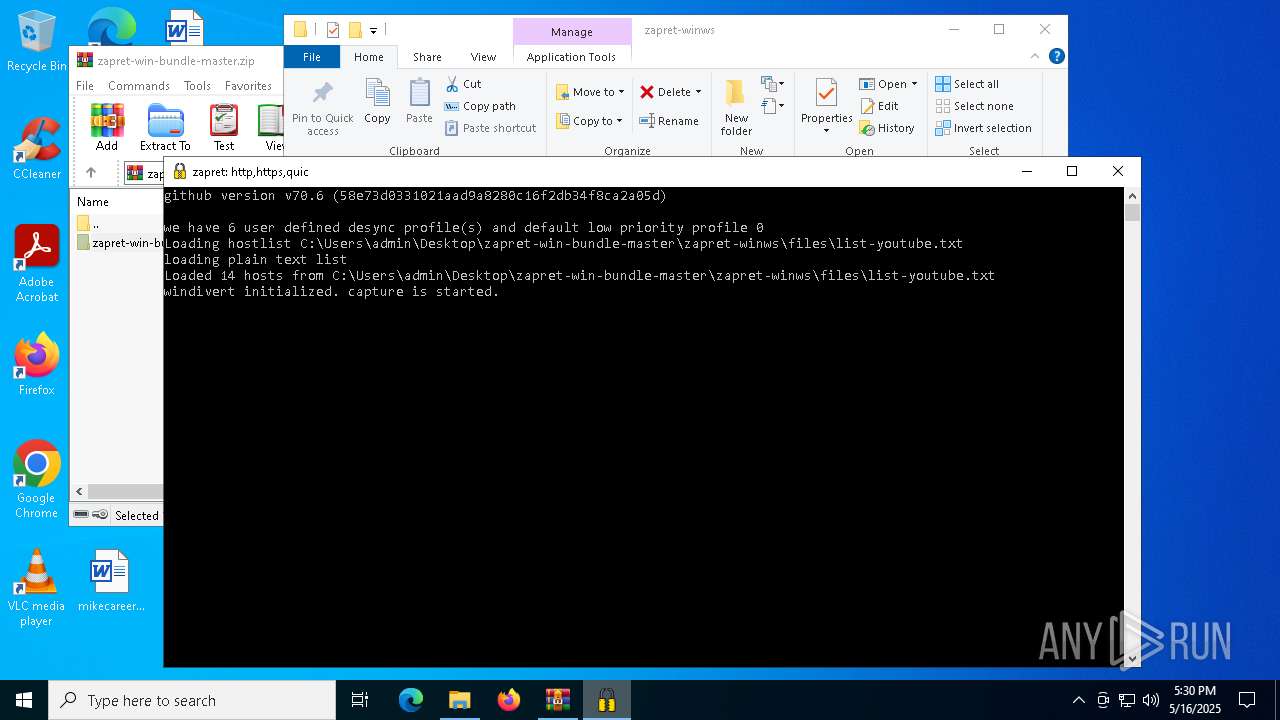
| 8048 | "C:\Users\admin\Desktop\zapret-win-bundle-master\zapret-winws\winws.exe" --wf-tcp=80,443 --wf-udp=443,50000-50099 --filter-tcp=80 --dpi-desync=fake,fakedsplit --dpi-desync-autottl=2 --dpi-desync-fooling=md5sig --new --filter-tcp=443 --hostlist="C:\Users\admin\Desktop\zapret-win-bundle-master\zapret-winws\files\list-youtube.txt" --dpi-desync=fake,multidisorder --dpi-desync-split-pos=1,midsld --dpi-desync-repeats=11 --dpi-desync-fooling=md5sig --dpi-desync-fake-tls-mod=rnd,dupsid,sni=www.google.com --new --filter-tcp=443 --dpi-desync=fake,multidisorder --dpi-desync-split-pos=midsld --dpi-desync-repeats=6 --dpi-desync-fooling=badseq,md5sig --new --filter-udp=443 --hostlist="C:\Users\admin\Desktop\zapret-win-bundle-master\zapret-winws\files\list-youtube.txt" --dpi-desync=fake --dpi-desync-repeats=11 --dpi-desync-fake-quic="C:\Users\admin\Desktop\zapret-win-bundle-master\zapret-winws\files\quic_initial_www_google_com.bin" --new --filter-udp=443 --dpi-desync=fake --dpi-desync-repeats=11 --new --filter-udp=50000-50099 --filter-l7=discord,stun --dpi-desync=fake | C:\Users\admin\Desktop\zapret-win-bundle-master\zapret-winws\winws.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
Total events
2 143
Read events
2 132
Write events
11
Delete events
0
Modification events
| (PID) Process: | (7308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\zapret-win-bundle-master.zip | |||
| (PID) Process: | (7308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (8132) winws.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Cygwin\Installations |
| Operation: | write | Name: | 84c188ee655393d2 |
Value: \??\C:\Users\admin\Desktop\zapret-win-bundle-master | |||
| (PID) Process: | (8132) winws.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\EventLog\System\WinDivert |
| Operation: | write | Name: | EventMessageFile |
Value: C:\Users\admin\Desktop\zapret-win-bundle-master\zapret-winws\WinDivert64.sys | |||
Executable files
153
Suspicious files
190
Text files
76
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7308.37288\zapret-win-bundle-master\.github\lockdown.yml | text | |
MD5:45C803FE878A7E445B25AAC584F5C3A3 | SHA256:1F4E0432B510CDA65C31855C9937D6924F90485FD1B969C195366DDC7A396C8E | |||
| 7308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7308.37288\zapret-win-bundle-master\.gitattributes | text | |
MD5:2A64C1195F8A6102DBABDCC1C1DF1304 | SHA256:F5A08A5102DFEE6955ABBB07B2A435537F126F1509D855B96A837E4BBA793F4F | |||
| 7308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7308.37288\zapret-win-bundle-master\arm64\install_arm64.cmd | text | |
MD5:541DED7120E3CEE2FAD8447EAAFE47AC | SHA256:3B5B8617A5A35EDD33574D291AC631E99B7386FC2D1DAF7A2D814C512F17D7B7 | |||
| 7308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7308.37288\zapret-win-bundle-master\arm64\WinDivert64.sys | executable | |
MD5:DEB29A3F3A032B99A8B95D70087C1840 | SHA256:55CD5C827A28FC91448F2AD1AE629E3FC951F07726819AEB035969DFBF3712C9 | |||
| 7308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7308.37288\zapret-win-bundle-master\blockcheck\blockcheck.cmd | text | |
MD5:5763CB58E6D9B26D626DC860EDF2D964 | SHA256:5A2DE13B097B1EE482F02052C72C5ED29D1541E139464A98697388F4E90CD998 | |||
| 7308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7308.37288\zapret-win-bundle-master\blockcheck\zapret\common\dialog.sh | text | |
MD5:6FD5B6525DFDD5FDFF0A4919FD1A5105 | SHA256:CCAF7F160B50060CA3A4044F43C30018C156636C3F4A8AD2E00E60518905A5E9 | |||
| 7308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7308.37288\zapret-win-bundle-master\arm64\ip2net.exe | executable | |
MD5:D3C67EC6E4EBEDBB52C4A5560298DB94 | SHA256:6AFEF4C74821F9D6F843BF031A0B9A0F3CBBEE22EB34B38E68F9C50EB5303AC0 | |||
| 7308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7308.37288\zapret-win-bundle-master\arm64\mdig.exe | executable | |
MD5:2C9AE45944AC7213D8F25043A8718940 | SHA256:9634736F4627A5F8DDA140B694CE729C020B59D2159BF588141E3B78F3DE6C7A | |||
| 7308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7308.37288\zapret-win-bundle-master\blockcheck\zapret\files\fake\dtls_clienthello_w3_org.bin | binary | |
MD5:E091D8E448CB76D8842CA22643E12B82 | SHA256:5BACD8CB6BD451F2374E55BC066B632E3C88FB852E3A44F19E6246C04D127BE5 | |||
| 7308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7308.37288\zapret-win-bundle-master\blockcheck\zapret\blog.sh | text | |
MD5:47FCC2F9D199486B64E3F5C37E0B3920 | SHA256:66F32FA4470CD63A4014DA8FA10AF11A25862F564E53016D1B790F82C2D83760 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
16
DNS requests
11
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7840 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7840 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7840 | SIHClient.exe | 4.245.163.56:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7840 | SIHClient.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
7840 | SIHClient.exe | 52.165.164.15:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |