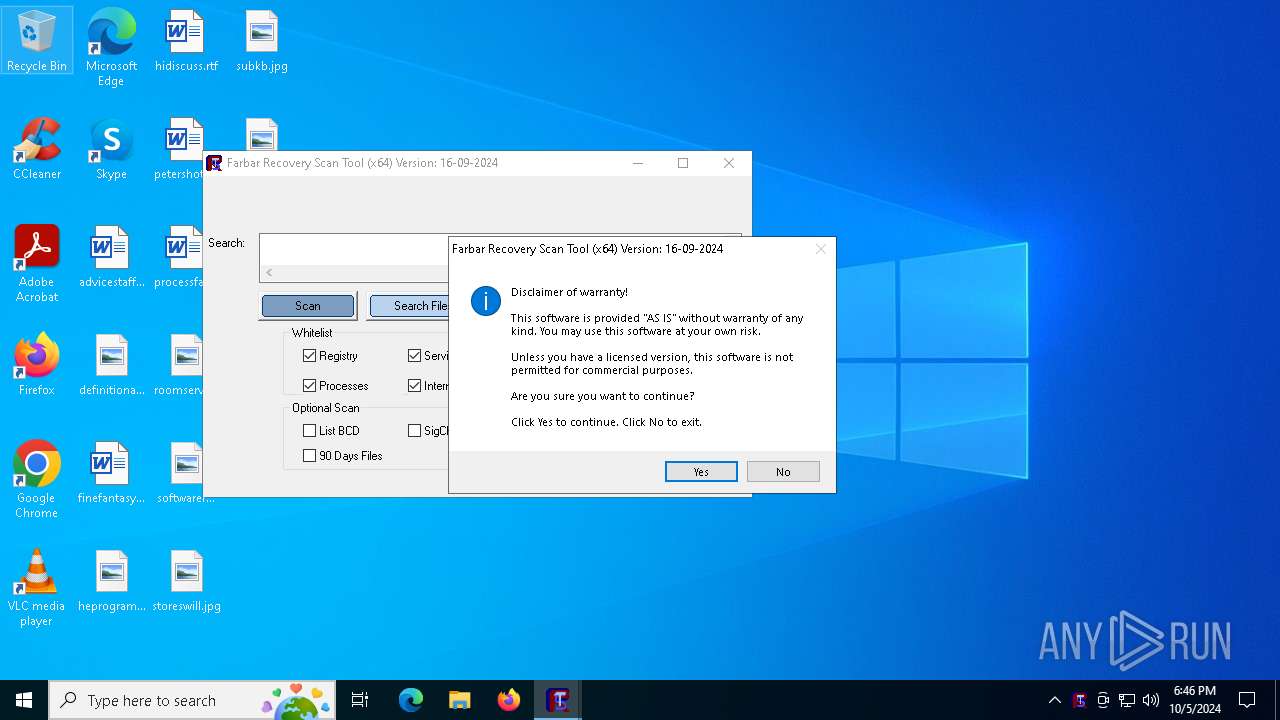
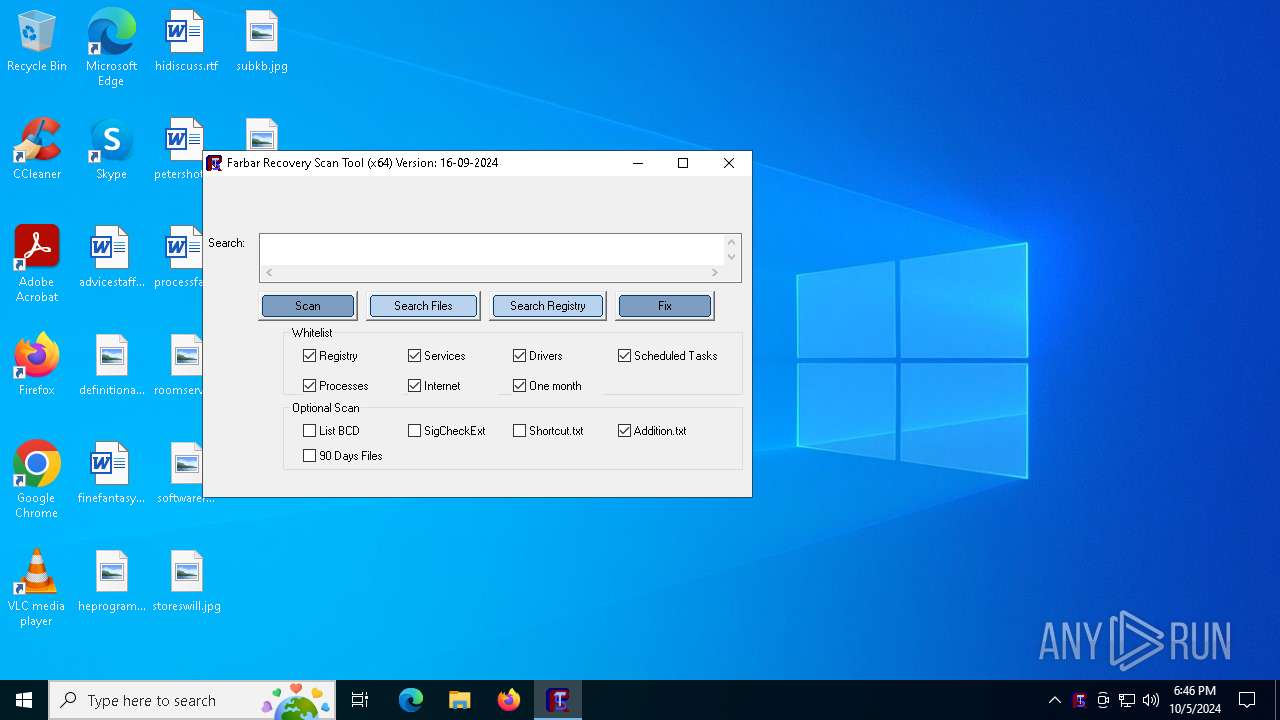
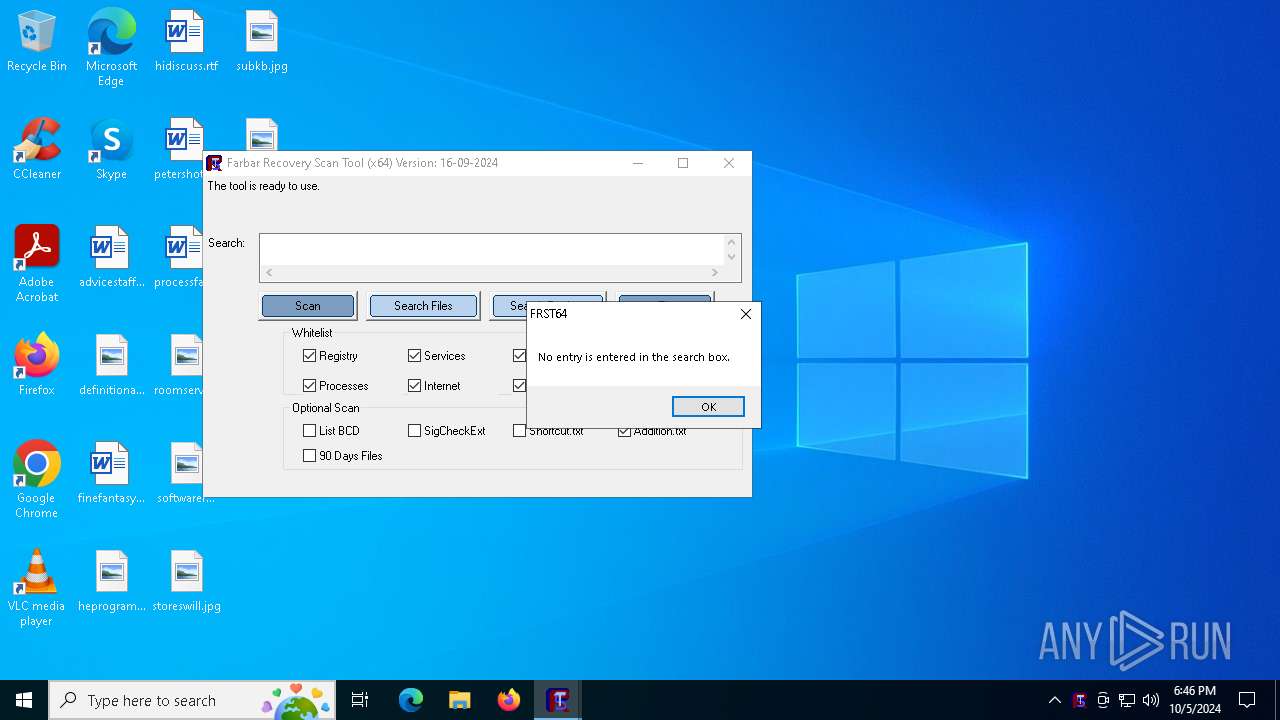
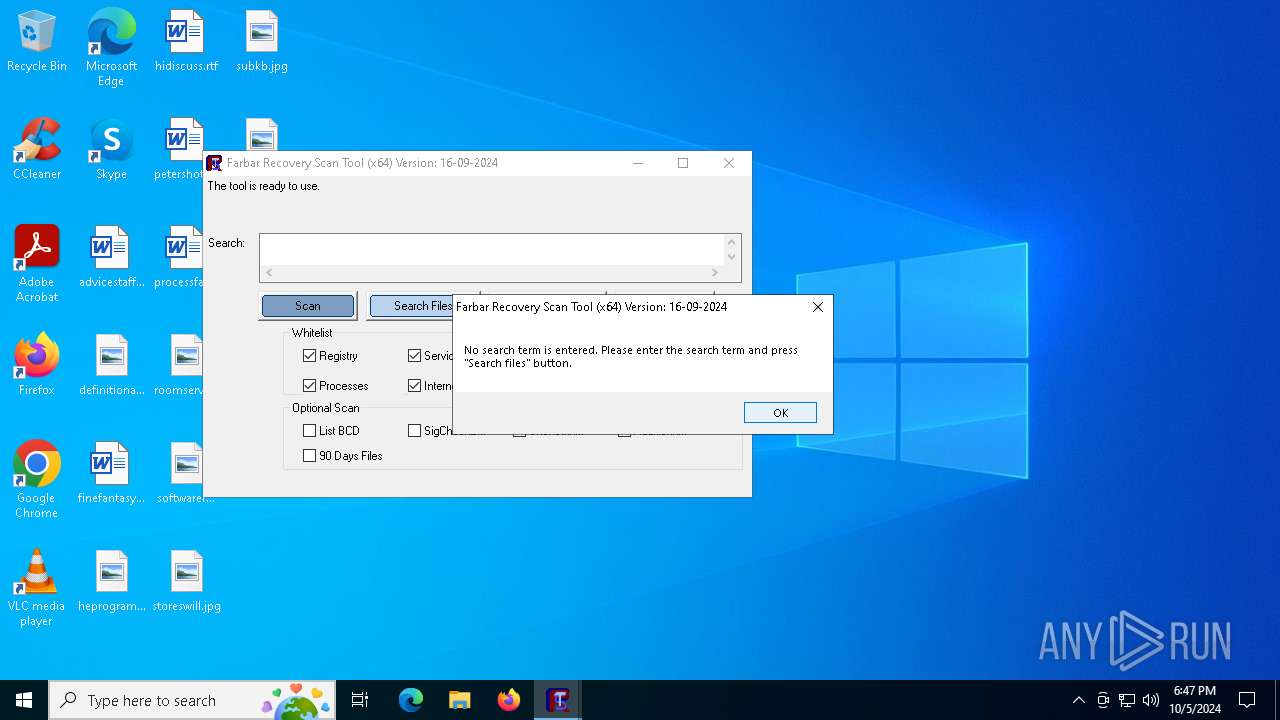
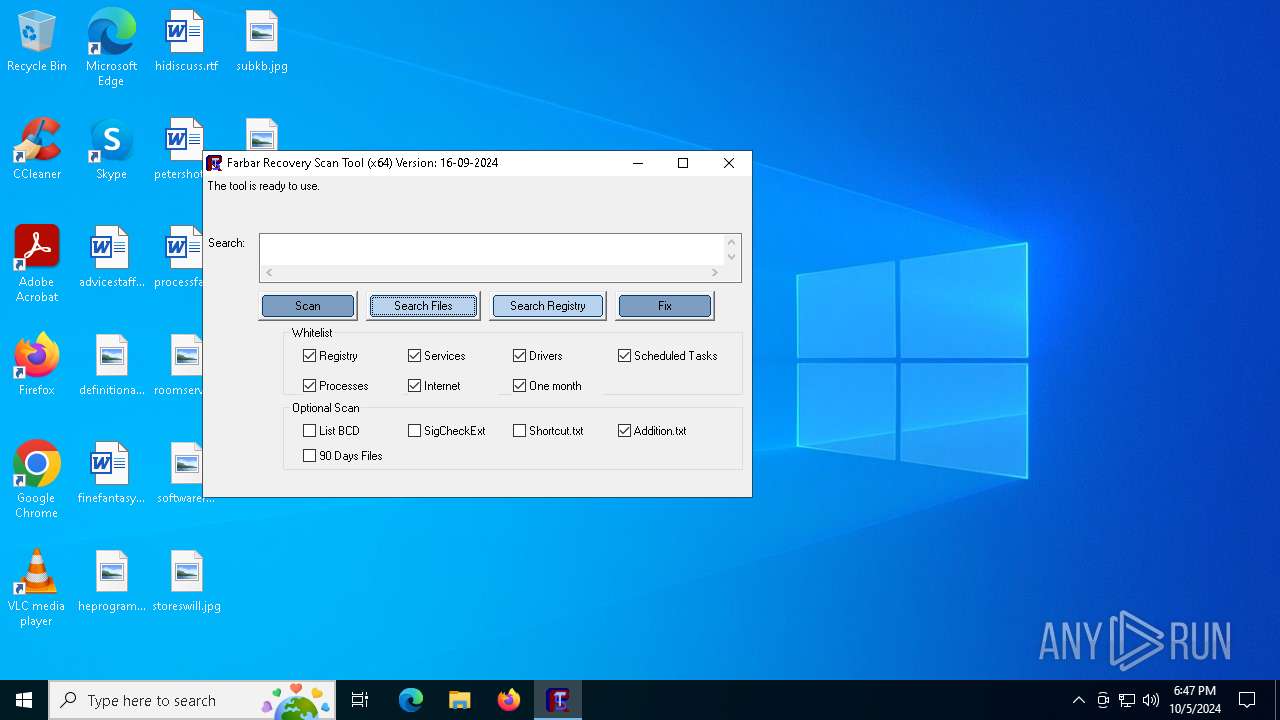
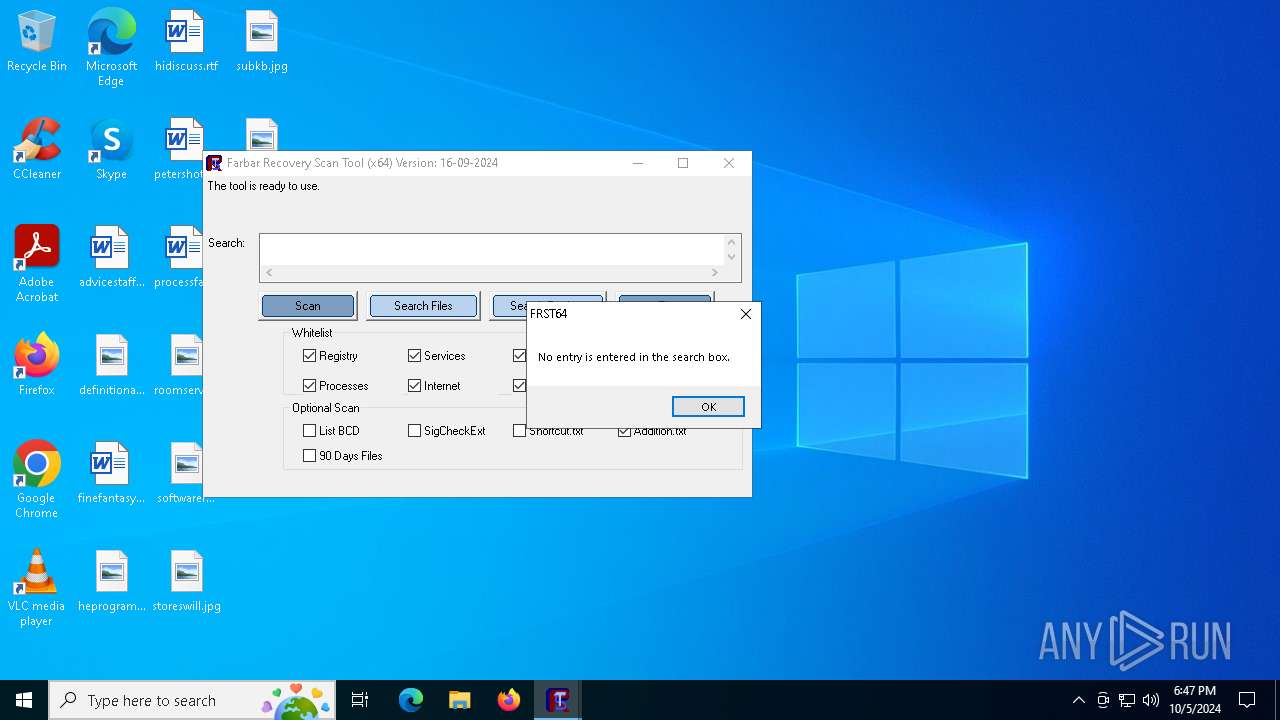
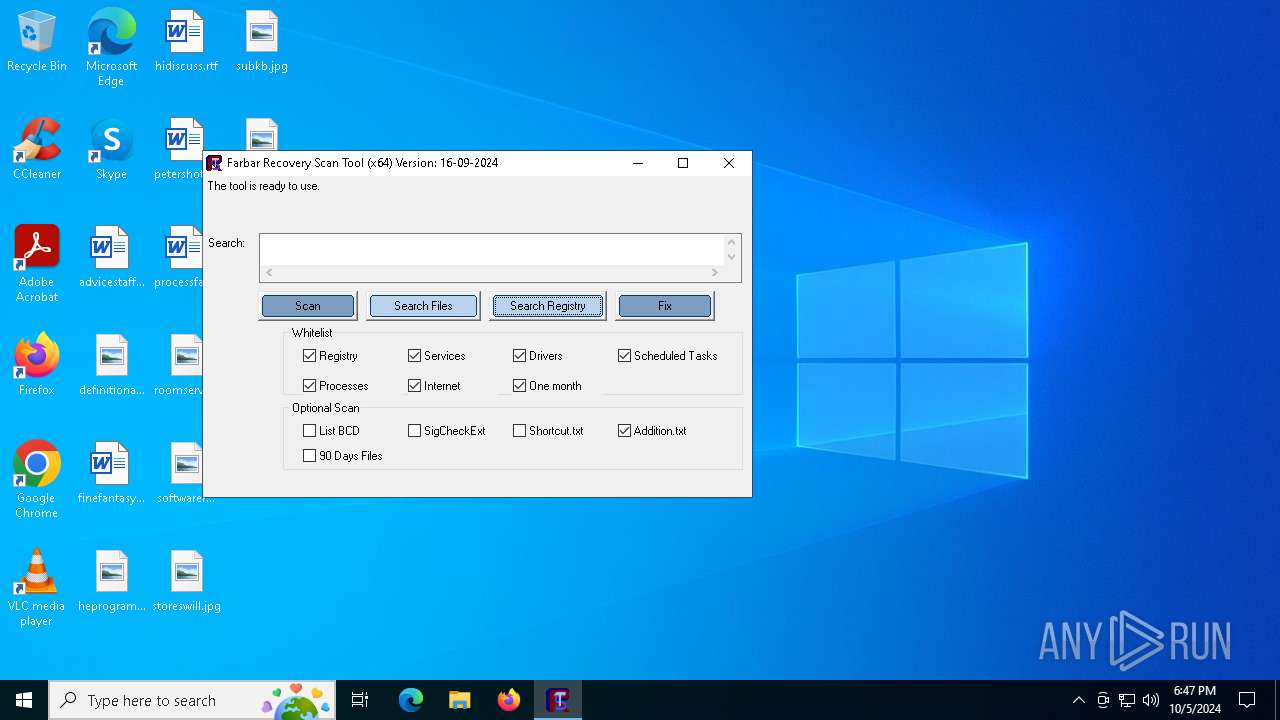
| File name: | FRST64.exe |
| Full analysis: | https://app.any.run/tasks/bdf8d07c-54c3-4af4-927c-db46a50fef1e |
| Verdict: | Malicious activity |
| Analysis date: | October 05, 2024, 18:46:26 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | C86E9ED57848DD2EF9A726789552558B |
| SHA1: | 2E5AAB2899742069496D17A6B55F765EE56E3078 |
| SHA256: | 84990004D772EE292B22225198713167906BAD574EEE8BA7463429674CA8A032 |
| SSDEEP: | 98304:q9rem5OidL7Xn/8MVtUeJUnhrynOIy5JEb8+RaRvuKHYT2471ZbX2FGJiY:s0N |
MALICIOUS
No malicious indicators.SUSPICIOUS
Detected use of alternative data streams (AltDS)
- FRST64.exe (PID: 5524)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2936)
- cmd.exe (PID: 5436)
- cmd.exe (PID: 5144)
- cmd.exe (PID: 2208)
- cmd.exe (PID: 5756)
- cmd.exe (PID: 1692)
- cmd.exe (PID: 6008)
- cmd.exe (PID: 5140)
Starts CMD.EXE for commands execution
- FRST64.exe (PID: 5524)
Executable content was dropped or overwritten
- FRST64.exe (PID: 5524)
Executes as Windows Service
- VSSVC.exe (PID: 3908)
Reads security settings of Internet Explorer
- FRST64.exe (PID: 5524)
Checks Windows Trust Settings
- FRST64.exe (PID: 5524)
Potential Corporate Privacy Violation
- FRST64.exe (PID: 5524)
INFO
Reads mouse settings
- FRST64.exe (PID: 5524)
Reads the software policy settings
- FRST64.exe (PID: 5524)
The process uses AutoIt
- FRST64.exe (PID: 5524)
Checks supported languages
- FRST64.exe (PID: 5524)
Create files in a temporary directory
- FRST64.exe (PID: 5524)
Reads the computer name
- FRST64.exe (PID: 5524)
Creates files or folders in the user directory
- FRST64.exe (PID: 5524)
Checks proxy server information
- FRST64.exe (PID: 5524)
Reads the machine GUID from the registry
- FRST64.exe (PID: 5524)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:09:16 09:58:14+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.16 |
| CodeSize: | 734208 |
| InitializedDataSize: | 1662464 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2549c |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 16.9.2024.0 |
| ProductVersionNumber: | 16.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Unicode |
| FileVersion: | 16.9.2024.0 |
| Comments: | http://www.autoitscript.com/autoit3/ |
| FileDescription: | Farbar Recovery Scan Tool |
| ProductName: | FRST64 |
| ProductVersion: | 16-09-2024 |
| CompanyName: | Farbar |
| LegalCopyright: | ©Farbar |
| OriginalFileName: | FRST64.exe |
| InternalName: | FRST64 |
Total processes
150
Monitored processes
32
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 832 | reg load hklm\b9Oz1Xv1Hz1 C:\FRST\v5Qr7Lg5Qx1W\DEFAULT | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1144 | reg load hklm\b9Oz1Xv1Hz1 C:\FRST\v5Qr7Lg5Qx1W\SECURITY | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1148 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1692 | C:\WINDOWS\system32\cmd.exe /c reg load hklm\b9Oz1Xv1Hz1 C:\FRST\v5Qr7Lg5Qx1W\COMPONENTS | C:\Windows\System32\cmd.exe | — | FRST64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1928 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2056 | C:\WINDOWS\system32\bcdedit /export C:\FRST\Hives\BCD | C:\Windows\System32\bcdedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2208 | C:\WINDOWS\system32\cmd.exe /c reg load hklm\b9Oz1Xv1Hz1 C:\FRST\v5Qr7Lg5Qx1W\DEFAULT | C:\Windows\System32\cmd.exe | — | FRST64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2356 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2776 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2820 | reg load hklm\b9Oz1Xv1Hz1 C:\FRST\v5Qr7Lg5Qx1W\NTUSER.DAT | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 585
Read events
6 346
Write events
228
Delete events
11
Modification events
| (PID) Process: | (2056) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2056) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | write | Name: | Element |
Value: 0000000000000000000000000000000006000000000000004800000000000000715E5C2FA985EB1190A89A9B763584210000000000000000745E5C2FA985EB1190A89A9B7635842100000000000000000000000000000000 | |||
| (PID) Process: | (2056) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\12000002 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2056) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\12000002 |
| Operation: | write | Name: | Element |
Value: \EFI\Microsoft\Boot\bootmgfw.efi | |||
| (PID) Process: | (2056) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{5b970157-8568-11eb-b45c-806e6f6e6963}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2056) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{5b970157-8568-11eb-b45c-806e6f6e6963}\Elements\11000001 |
| Operation: | write | Name: | Element |
Value: 0000000000000000000000000000000006000000000000004800000000000000715E5C2FA985EB1190A89A9B763584210000000000000000745E5C2FA985EB1190A89A9B7635842100000000000000000000000000000000 | |||
| (PID) Process: | (2056) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{5b970157-8568-11eb-b45c-806e6f6e6963}\Elements\12000002 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2056) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{5b970157-8568-11eb-b45c-806e6f6e6963}\Elements\12000002 |
| Operation: | write | Name: | Element |
Value: \EFI\Boot\Loader.efi | |||
| (PID) Process: | (2056) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{a5a30fa2-3d06-4e9f-b5f4-a01df9d1fcba}\Description |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2056) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{a5a30fa2-3d06-4e9f-b5f4-a01df9d1fcba}\Elements\24000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
1
Suspicious files
44
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5524 | FRST64.exe | C:\FRST\v5Qr7Lg5Qx1W\SOFTWARE | — | |
MD5:— | SHA256:— | |||
| 5524 | FRST64.exe | C:\FRST\v5Qr7Lg5Qx1W\SOFTWARE.LOG1 | — | |
MD5:— | SHA256:— | |||
| 5524 | FRST64.exe | C:\FRST\v5Qr7Lg5Qx1W\SOFTWARE.LOG2 | — | |
MD5:— | SHA256:— | |||
| 5524 | FRST64.exe | C:\FRST\Hives\SOFTWARE | — | |
MD5:— | SHA256:— | |||
| 5524 | FRST64.exe | C:\FRST\v5Qr7Lg5Qx1W\SYSTEM | — | |
MD5:— | SHA256:— | |||
| 5524 | FRST64.exe | C:\FRST\Hives\SYSTEM | — | |
MD5:— | SHA256:— | |||
| 5524 | FRST64.exe | C:\Users\admin\AppData\Local\Temp\aut776F.tmp | binary | |
MD5:C65D2BFEE6F33857980F95BBF647D5C0 | SHA256:90403EFC1FAC06E52D94B11473837C9C09D4F17F6892EA265B4A2E2968CCA49D | |||
| 5524 | FRST64.exe | C:\FRST\v5Qr7Lg5Qx1W\COMPONENTS | — | |
MD5:— | SHA256:— | |||
| 5524 | FRST64.exe | C:\FRST\v5Qr7Lg5Qx1W\COMPONENTS.LOG1 | — | |
MD5:— | SHA256:— | |||
| 5524 | FRST64.exe | C:\FRST\v5Qr7Lg5Qx1W\COMPONENTS.LOG2 | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
27
DNS requests
5
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6796 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5524 | FRST64.exe | GET | 301 | 172.67.2.229:80 | http://download.bleepingcomputer.com/farbar/up64 | unknown | — | — | whitelisted |
— | — | GET | 200 | 104.20.184.56:443 | https://download.bleepingcomputer.com/farbar/up64 | unknown | text | 11 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6796 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6796 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5524 | FRST64.exe | 172.67.2.229:80 | download.bleepingcomputer.com | CLOUDFLARENET | US | whitelisted |
5524 | FRST64.exe | 172.67.2.229:443 | download.bleepingcomputer.com | CLOUDFLARENET | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
download.bleepingcomputer.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5524 | FRST64.exe | Potential Corporate Privacy Violation | ET POLICY Autoit Windows Automation tool User-Agent in HTTP Request - Possibly Hostile |
— | — | Potential Corporate Privacy Violation | ET POLICY Autoit Windows Automation tool User-Agent in HTTP Request - Possibly Hostile |