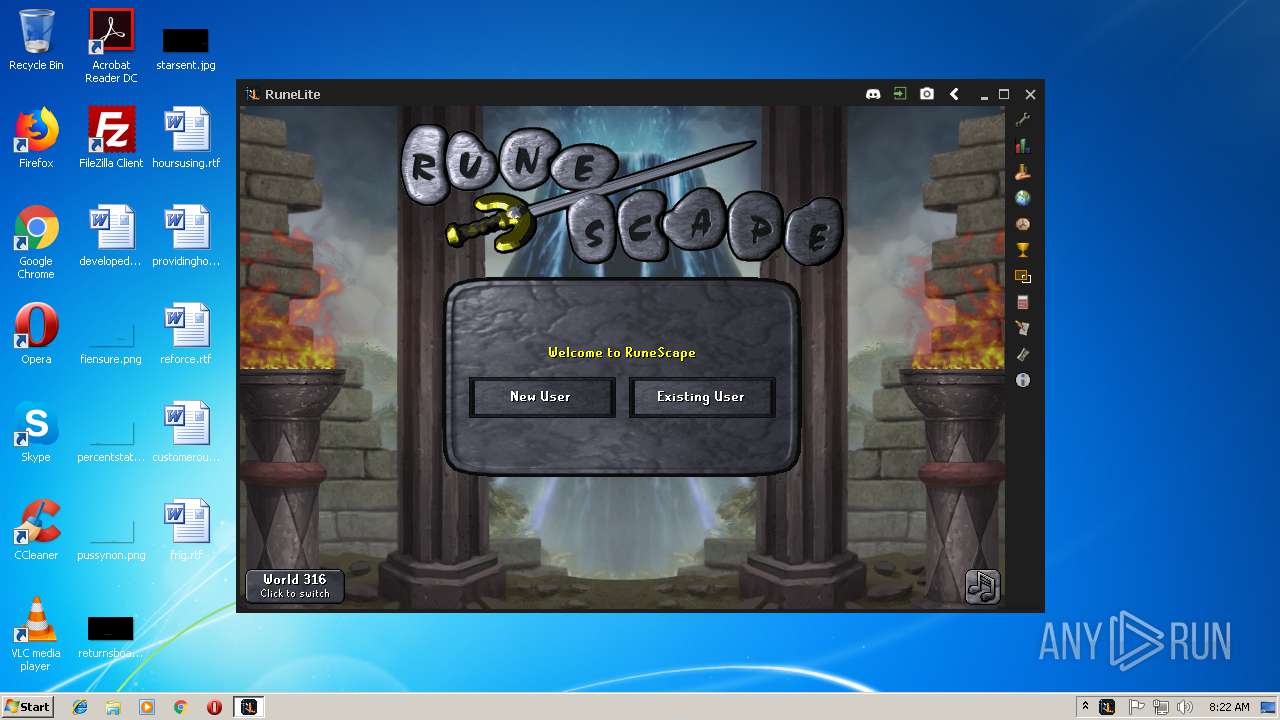
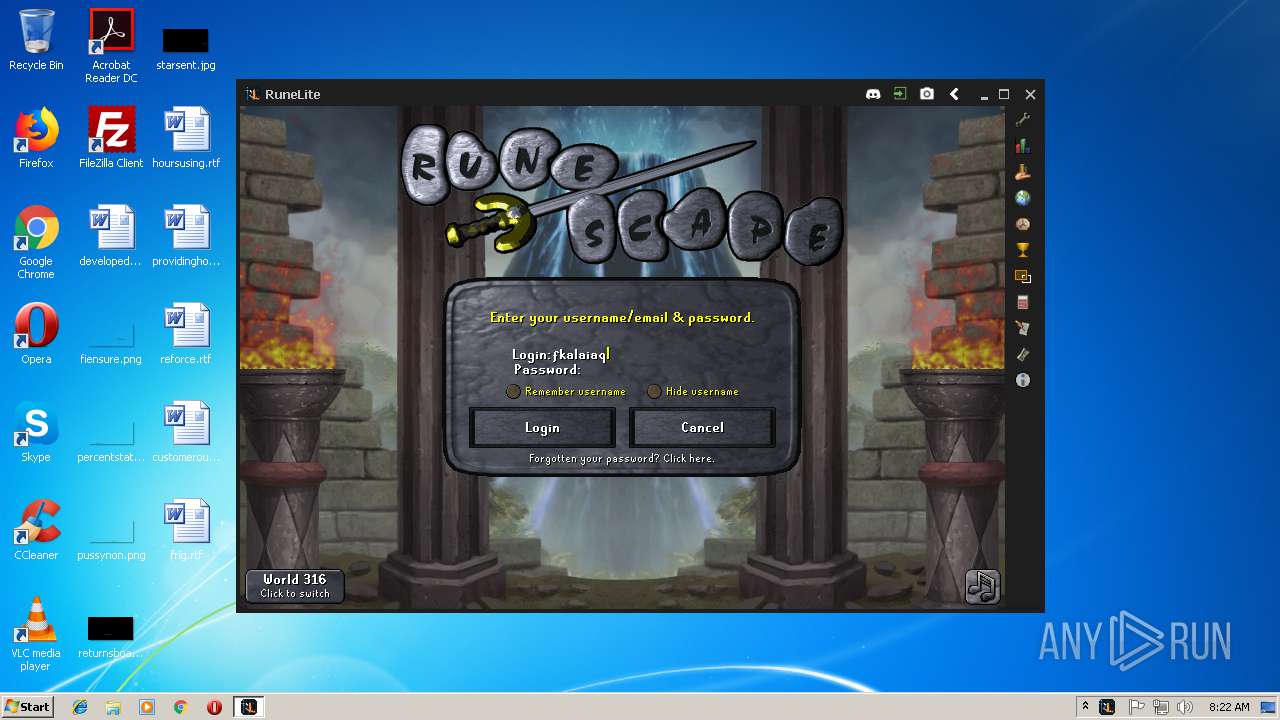
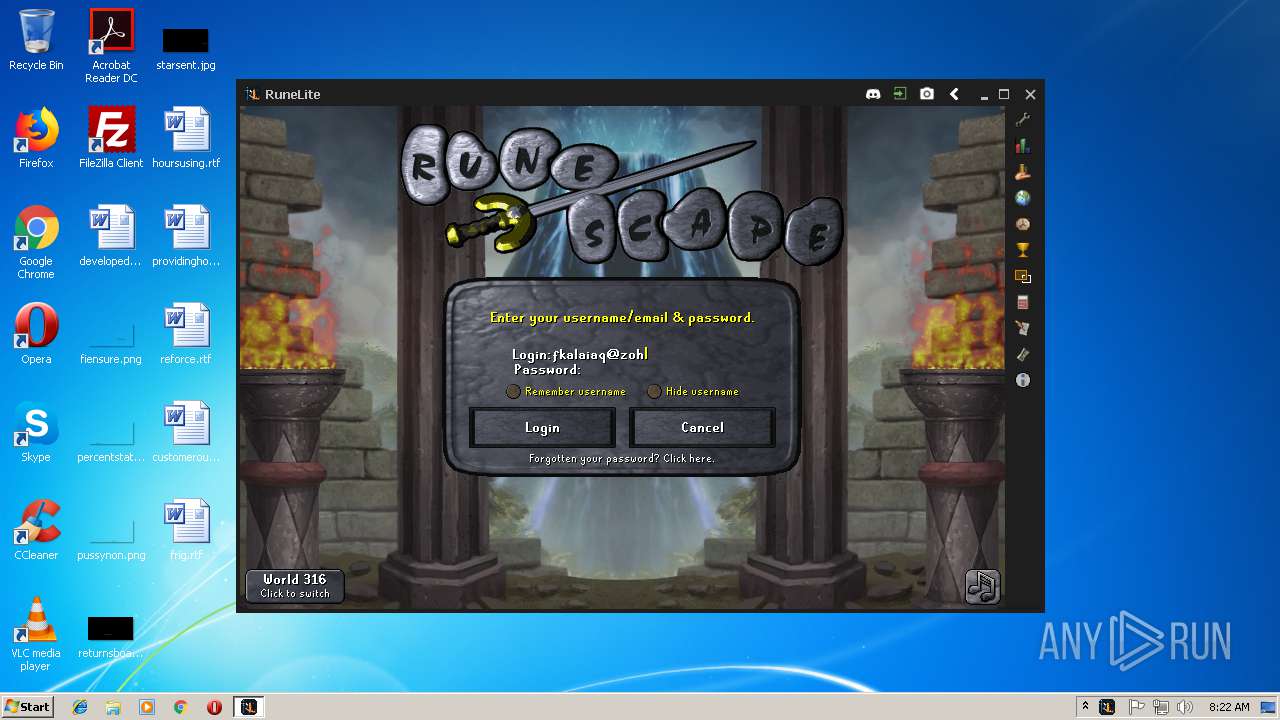
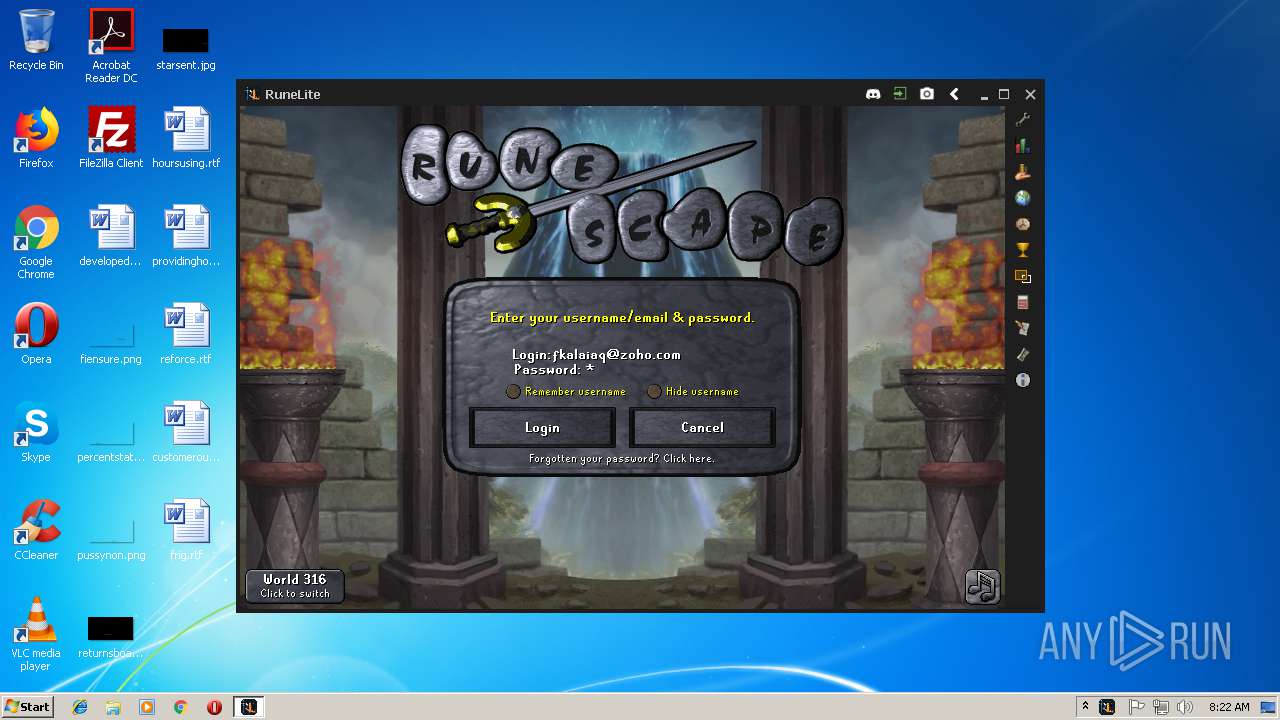
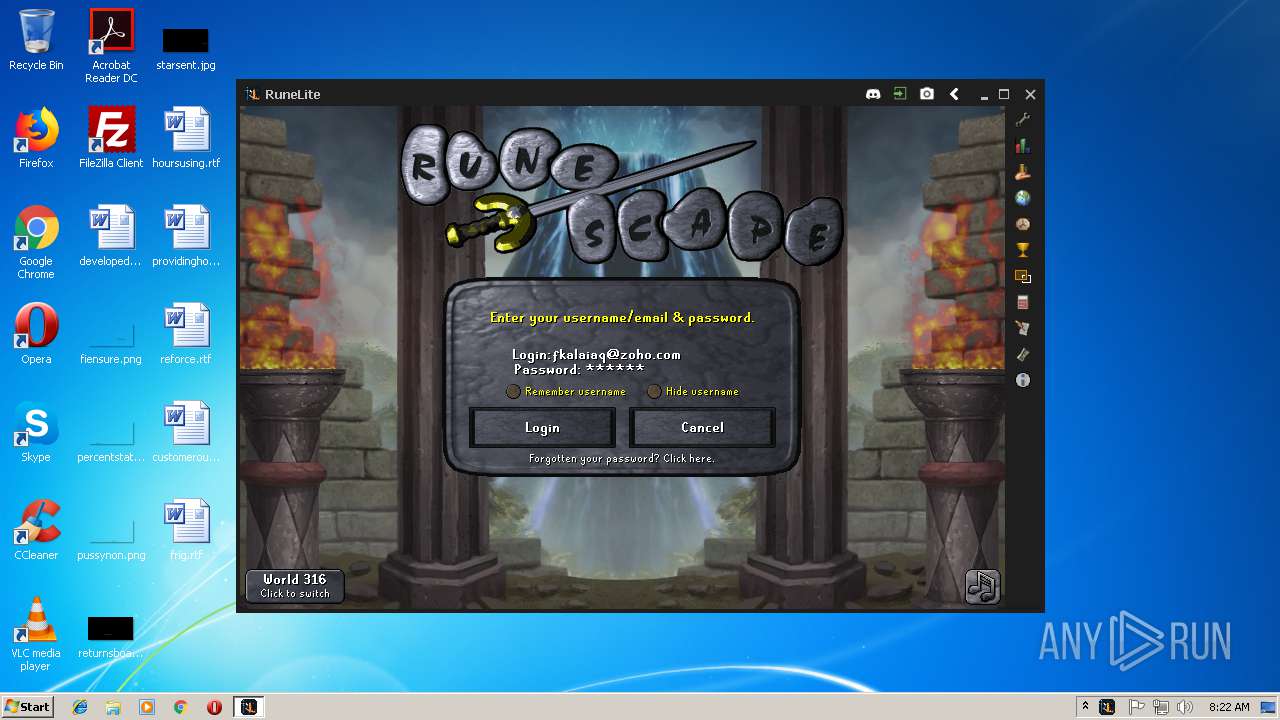
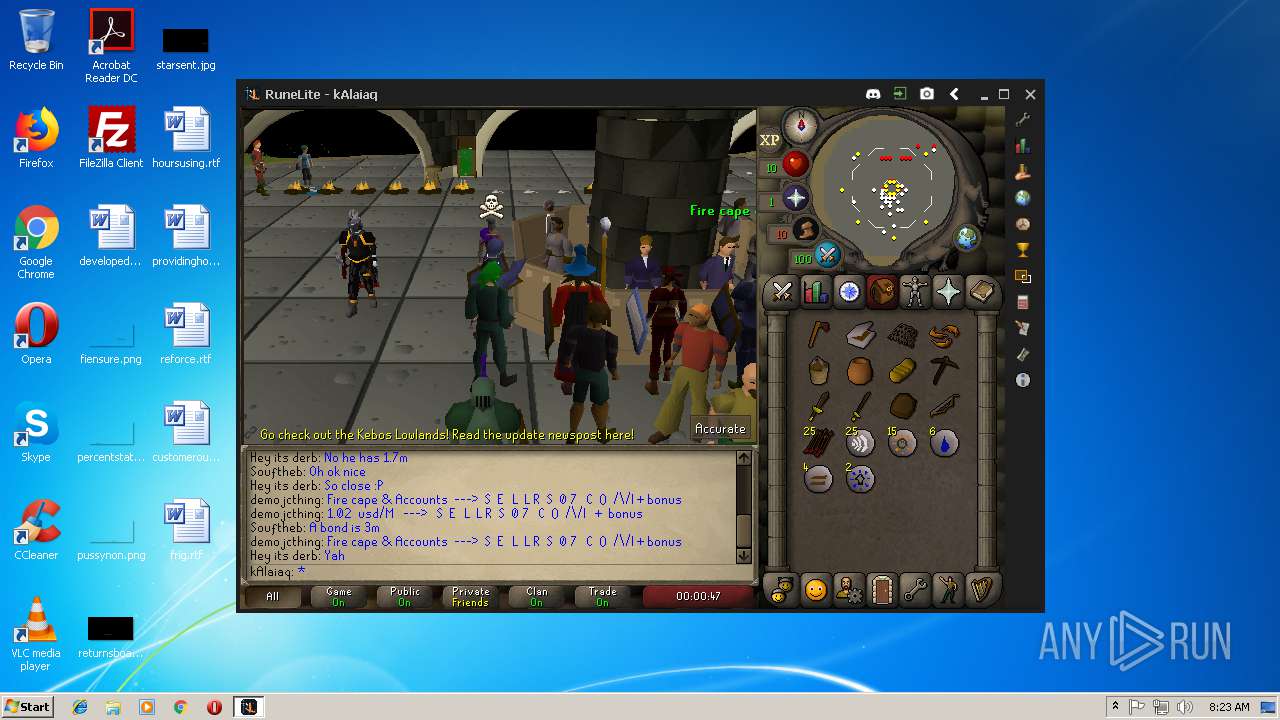
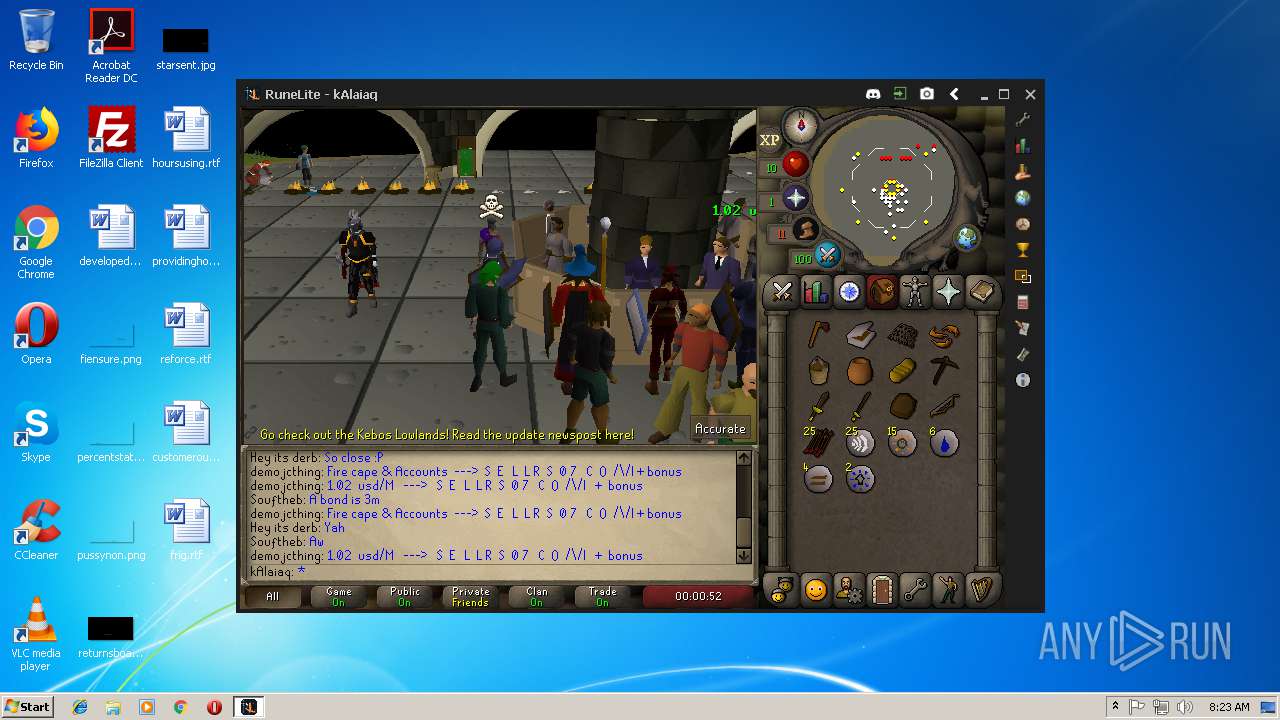
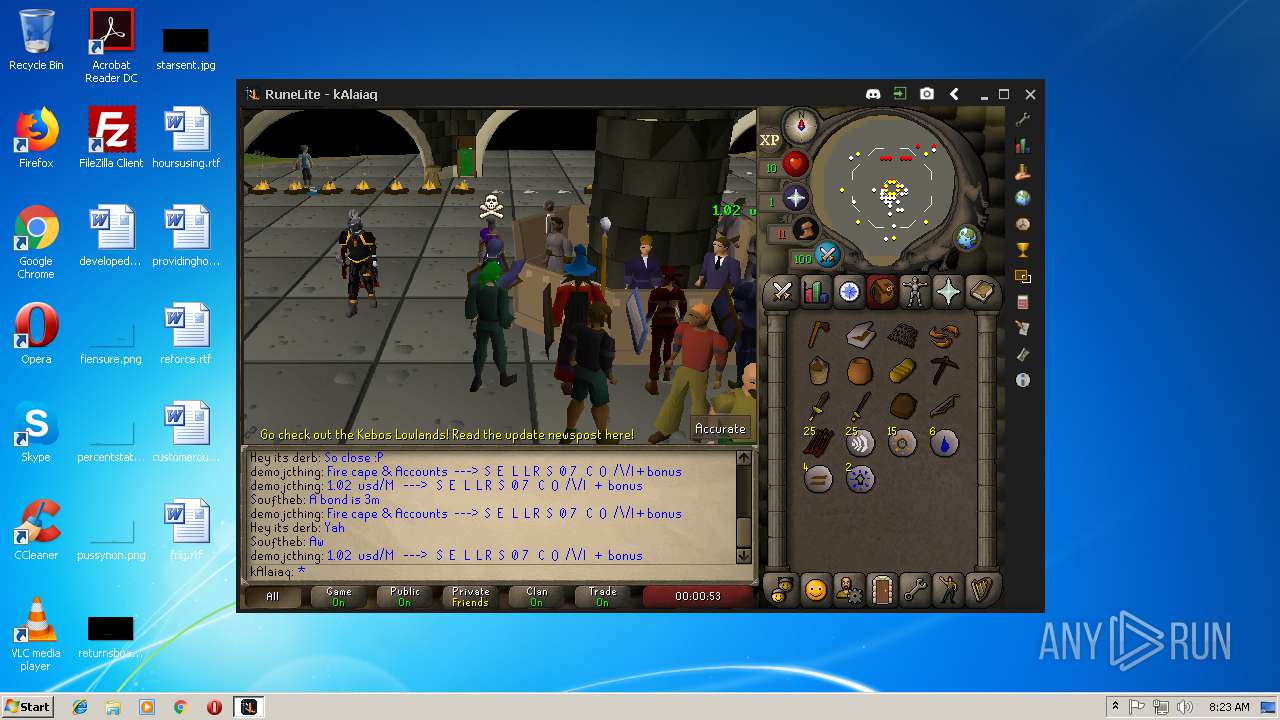
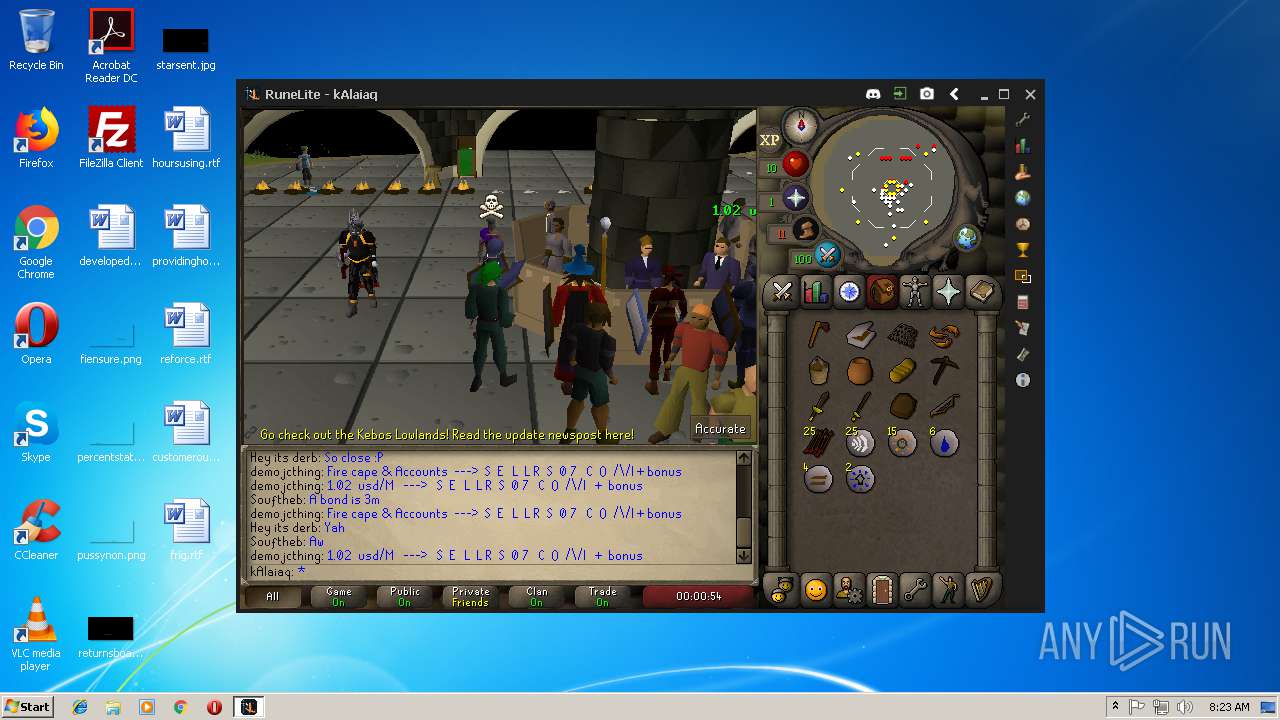
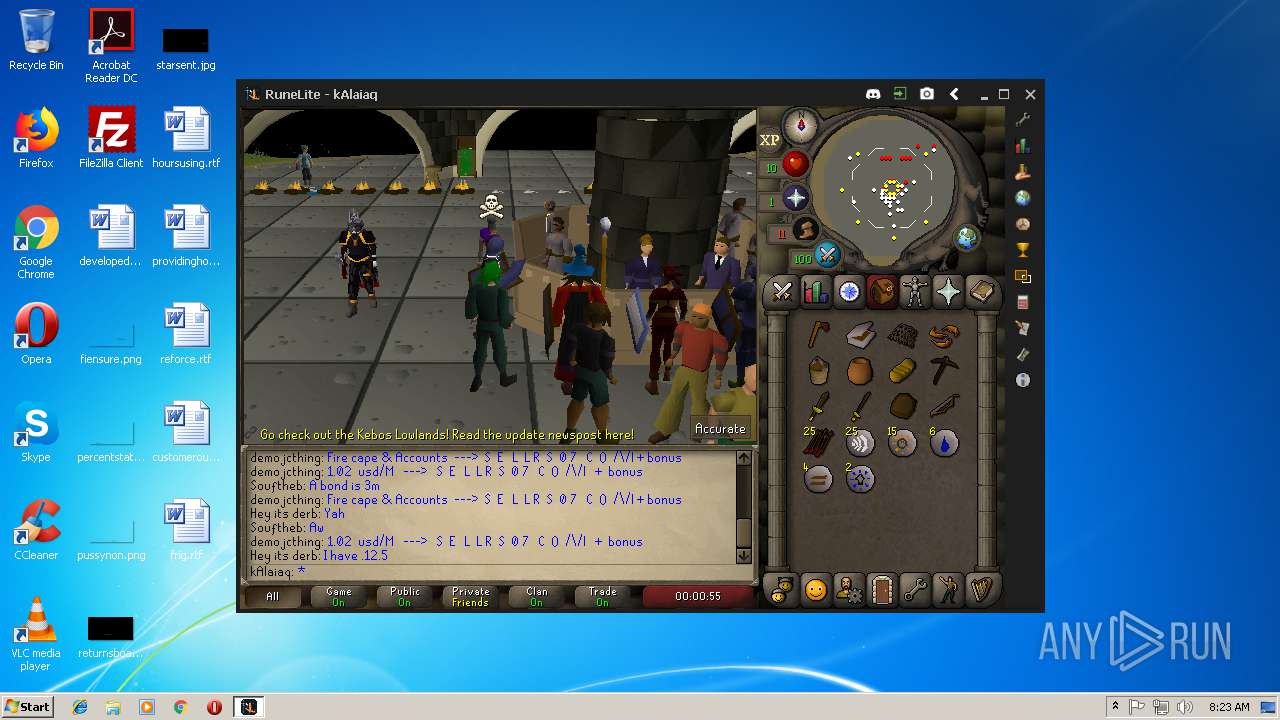
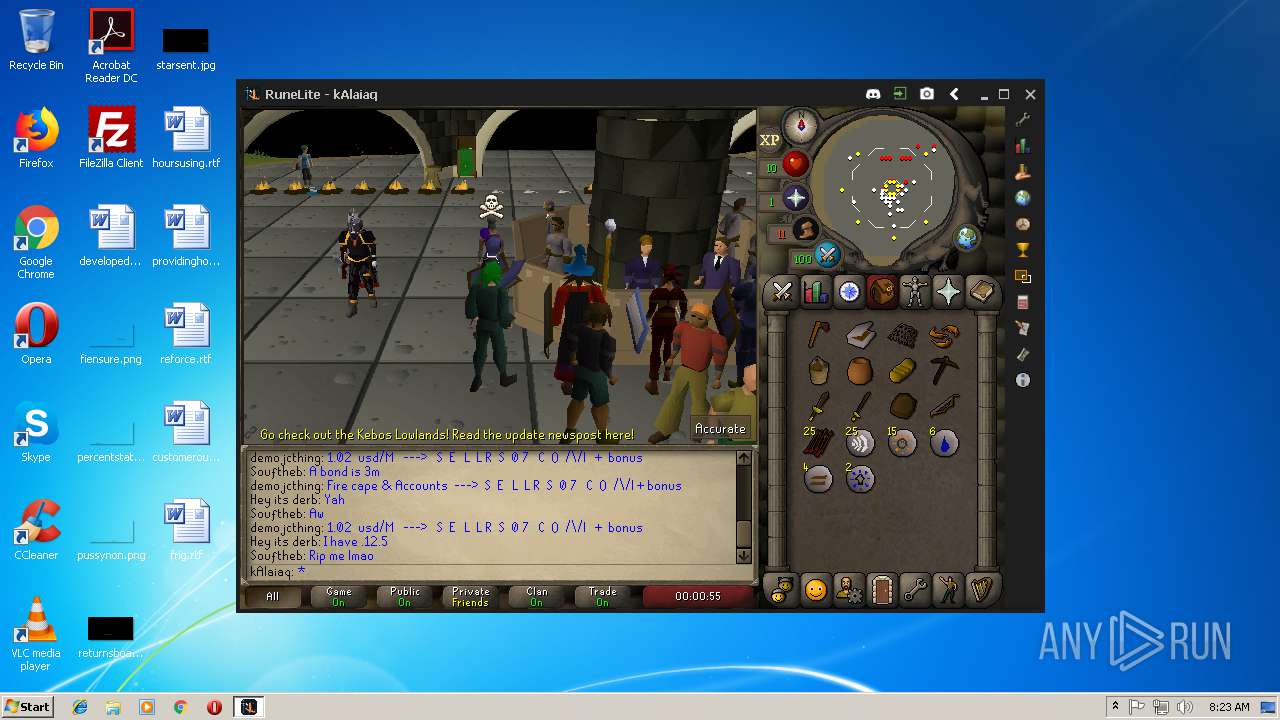
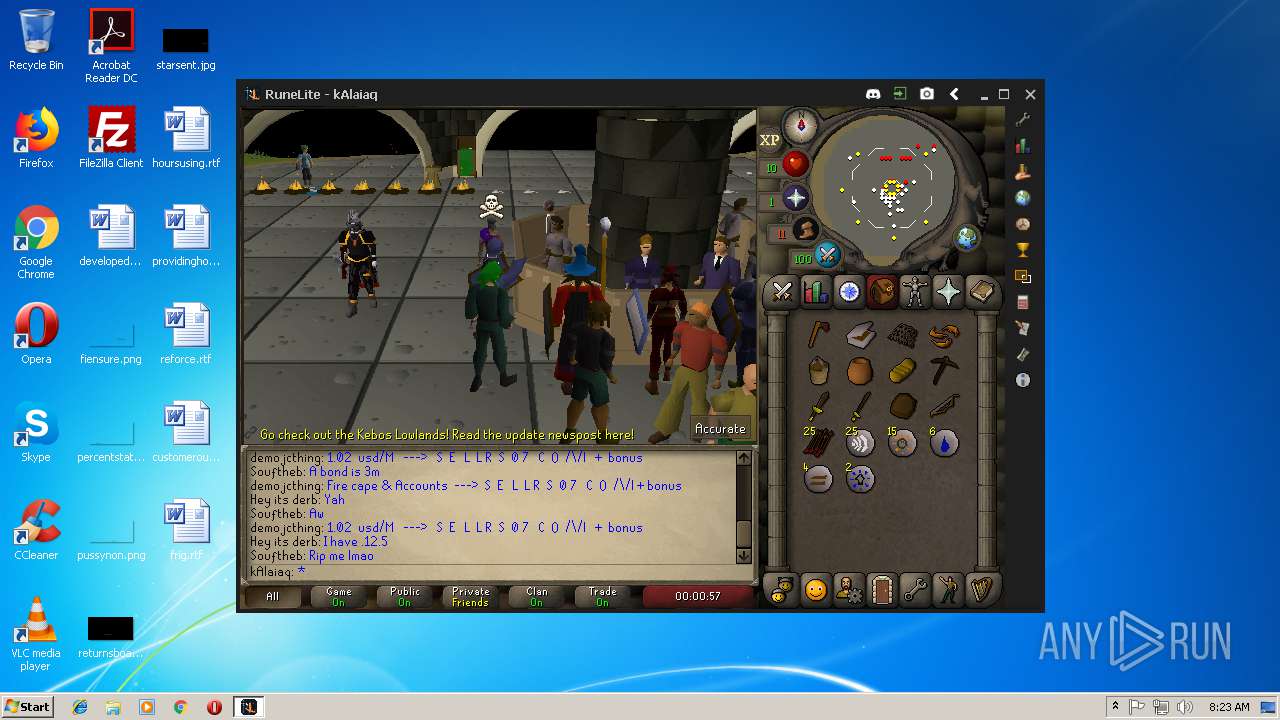
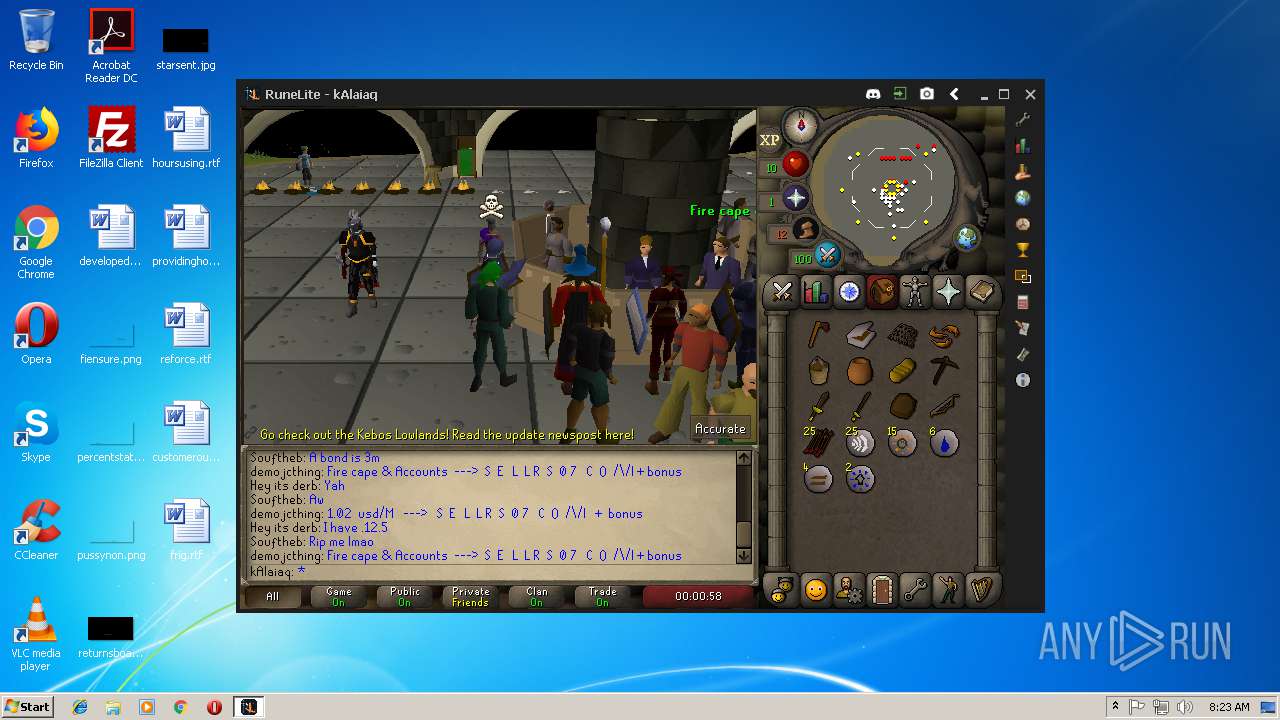
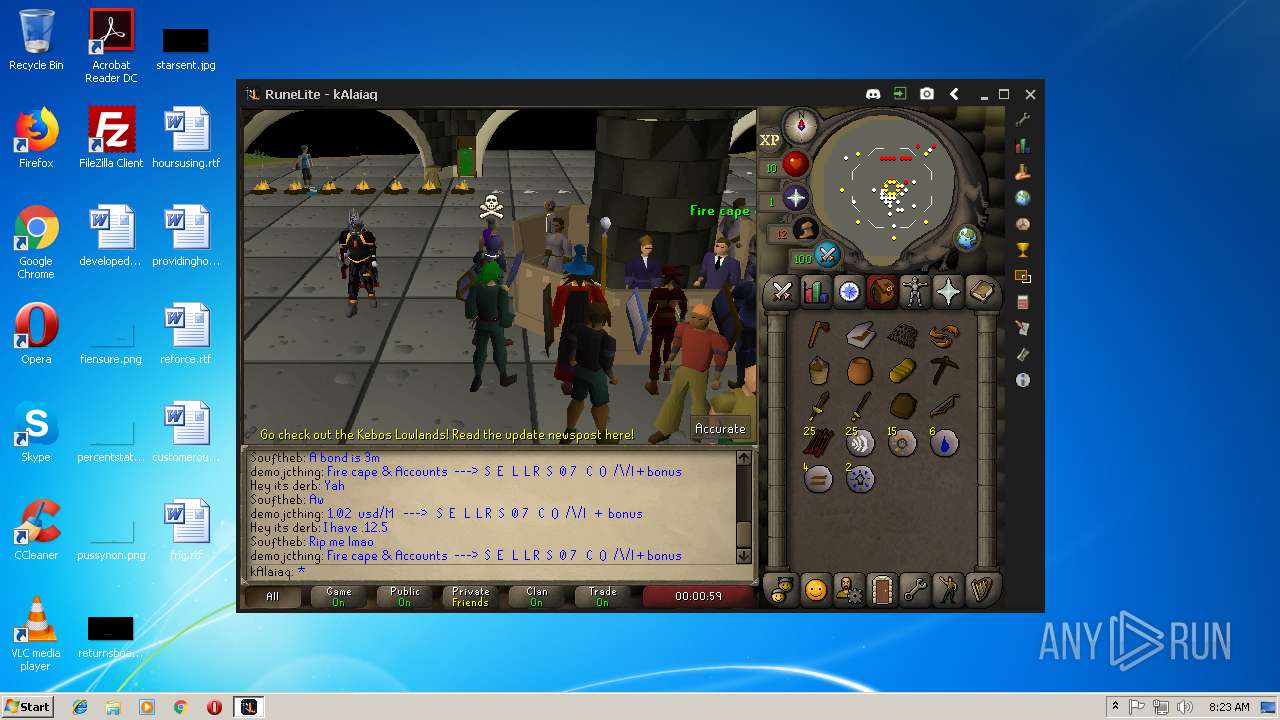
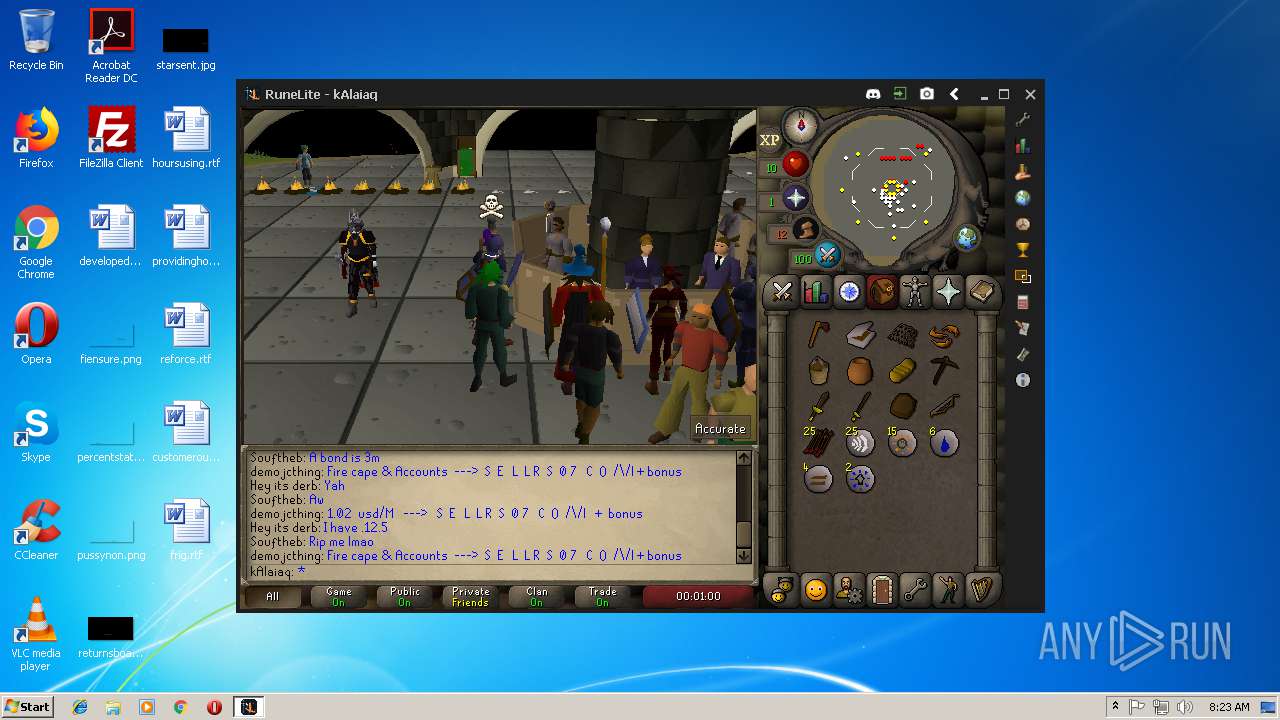
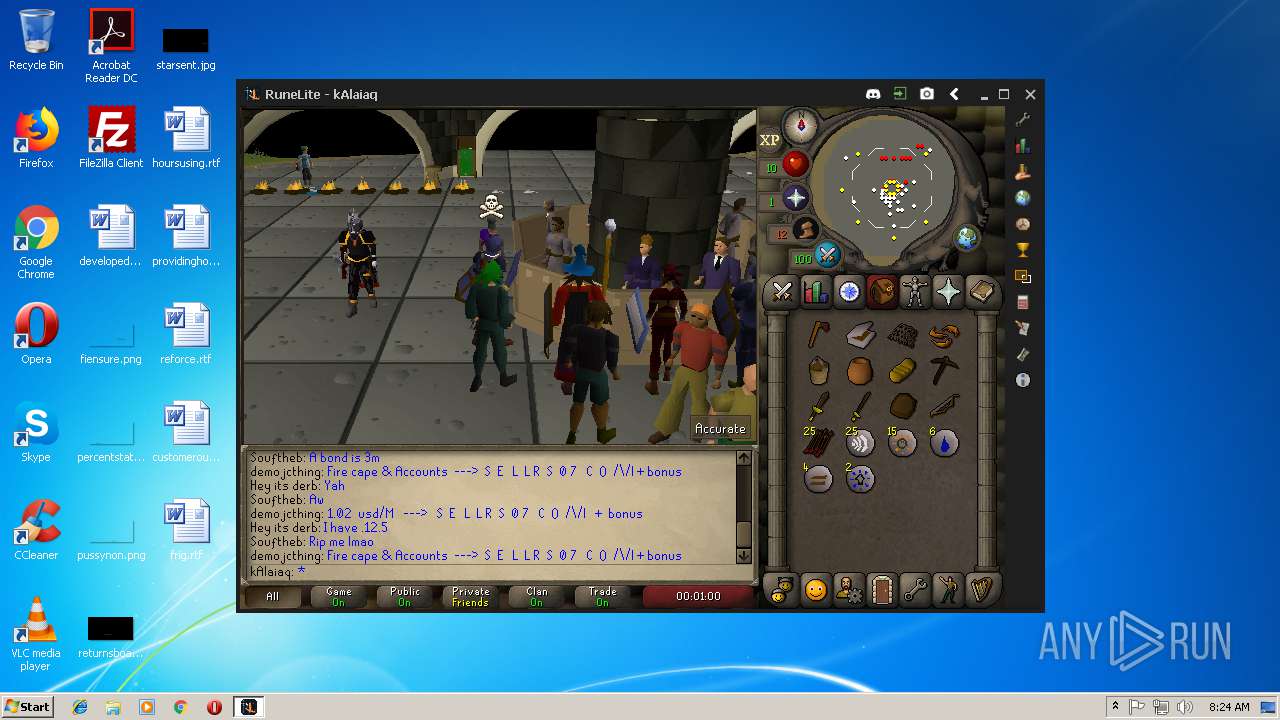
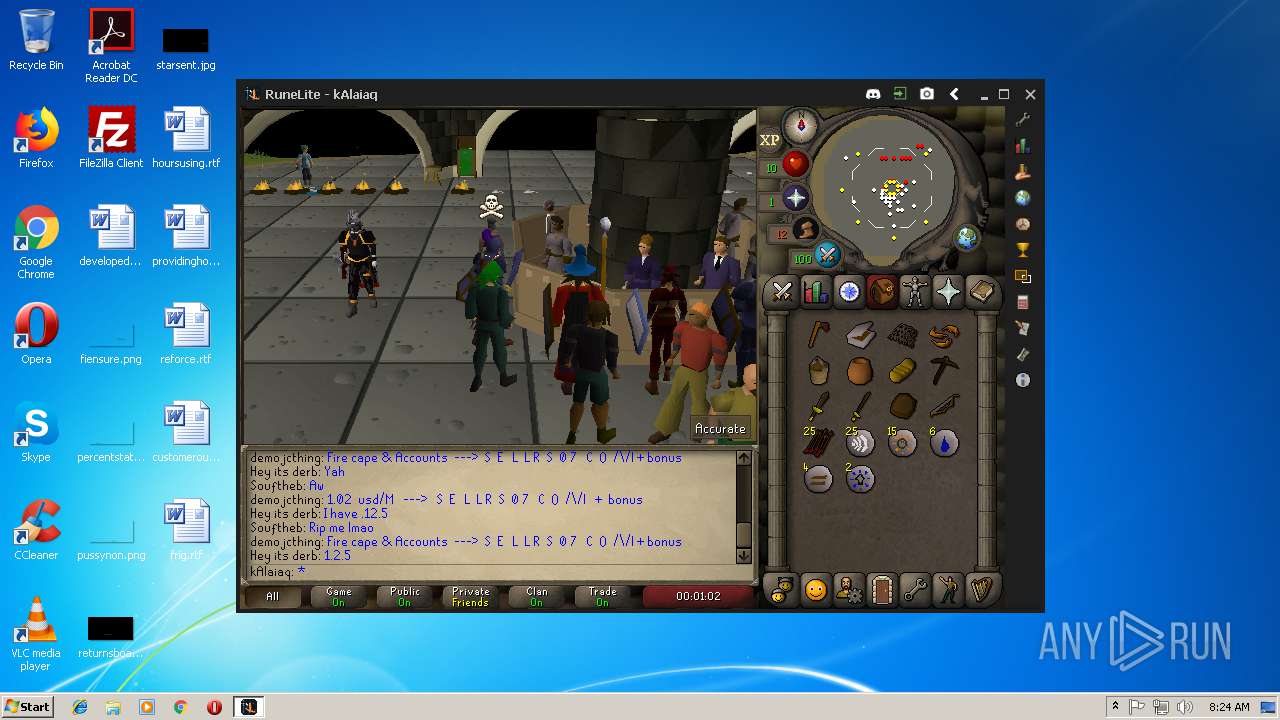
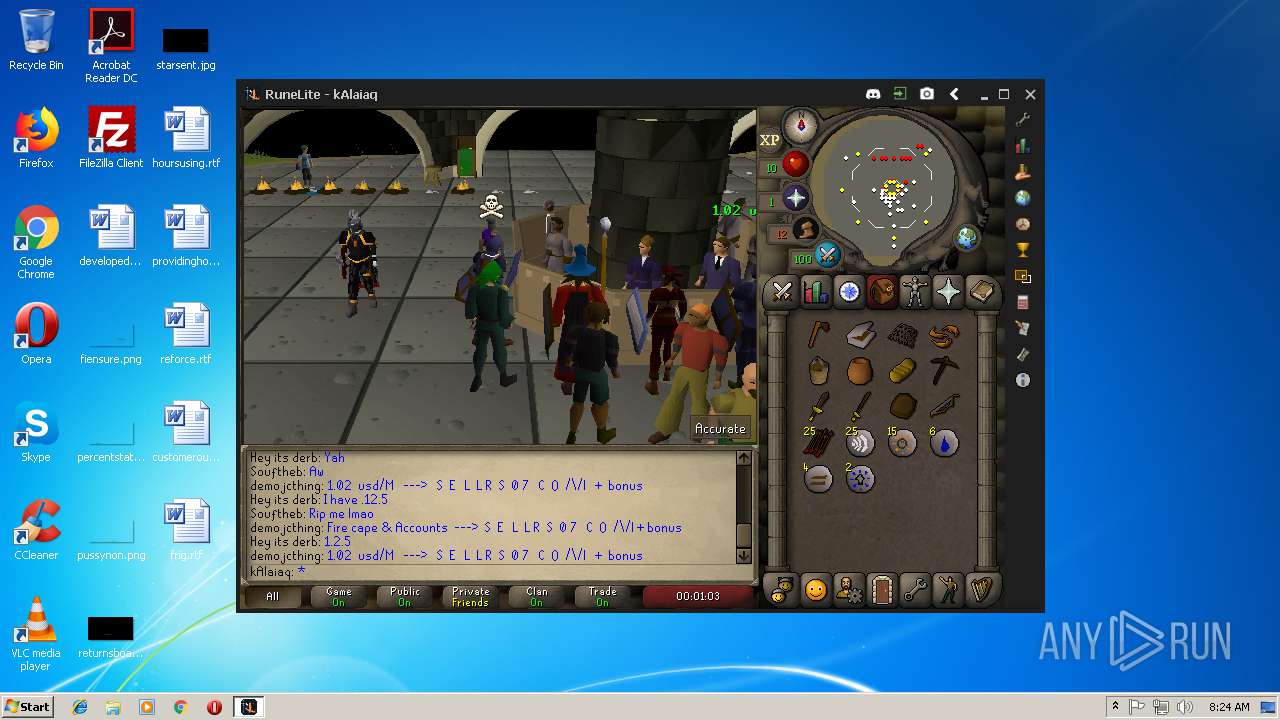
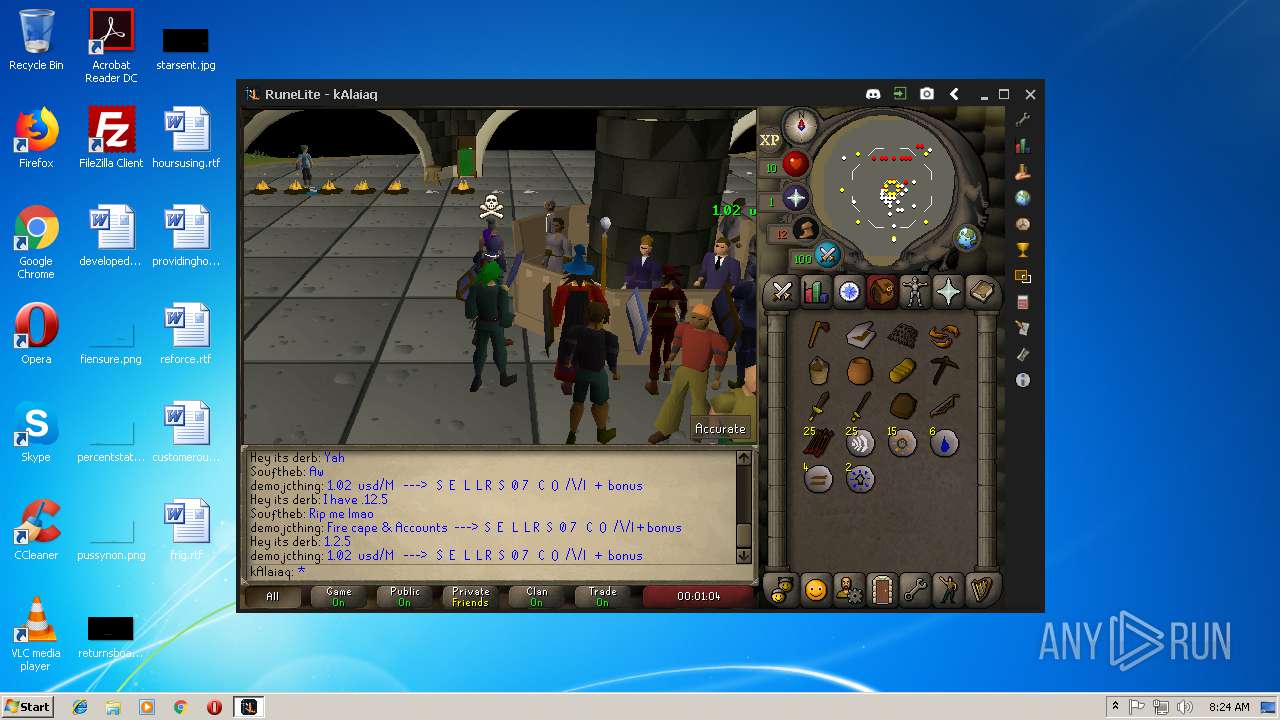
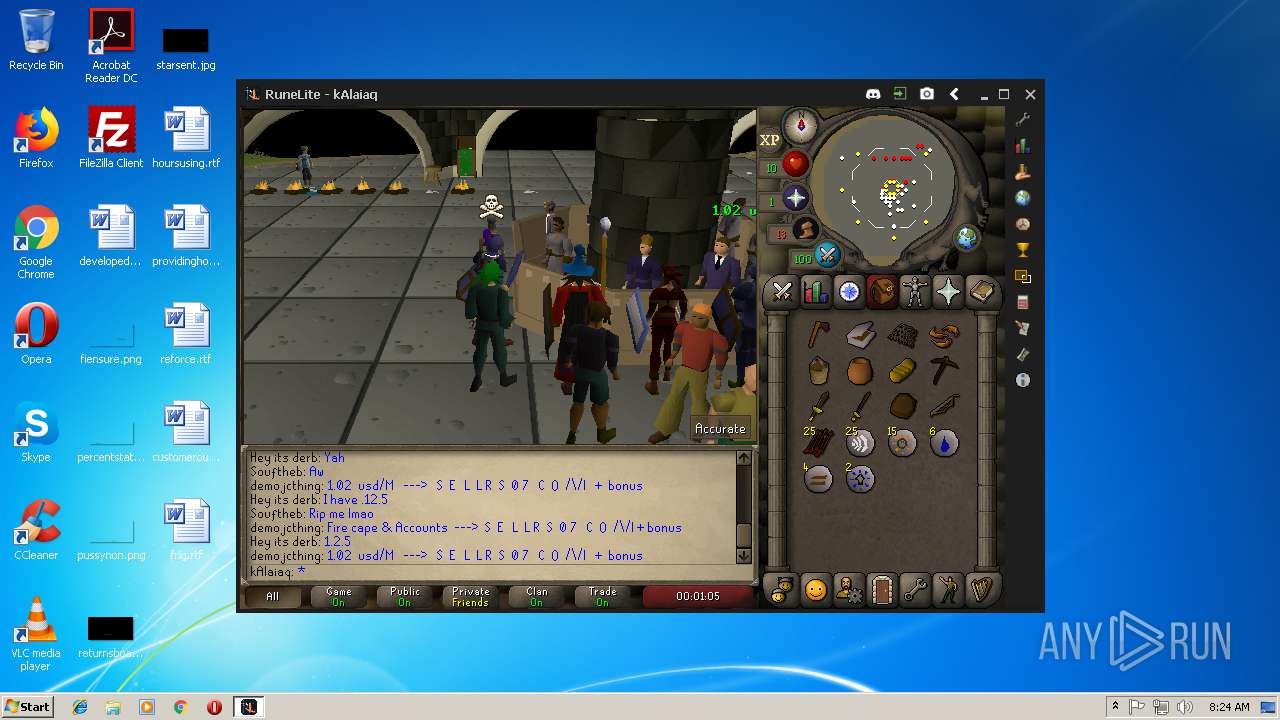
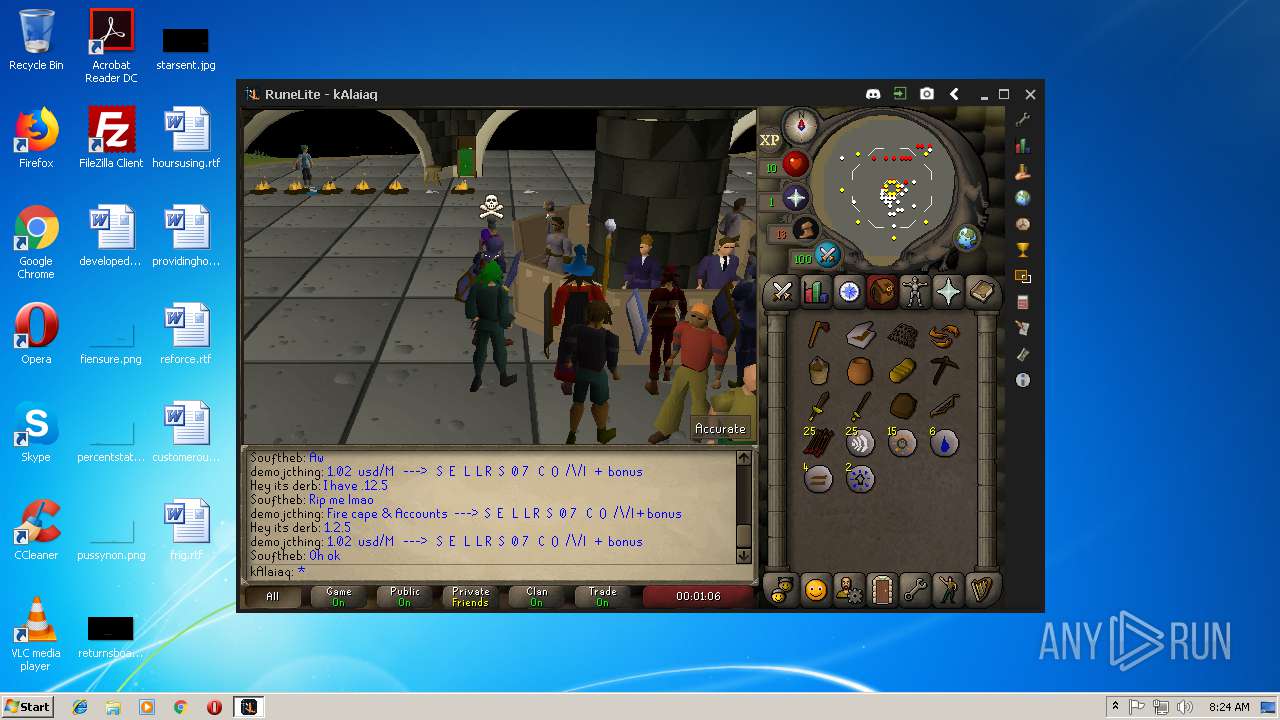
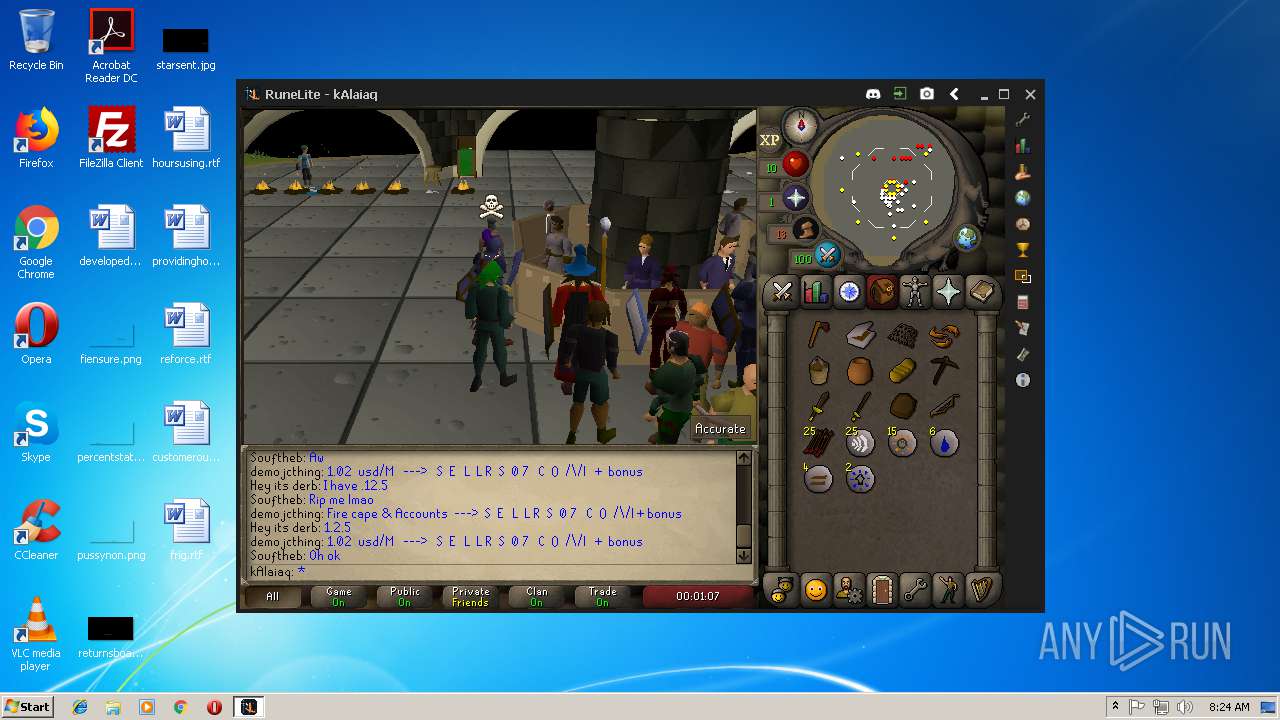
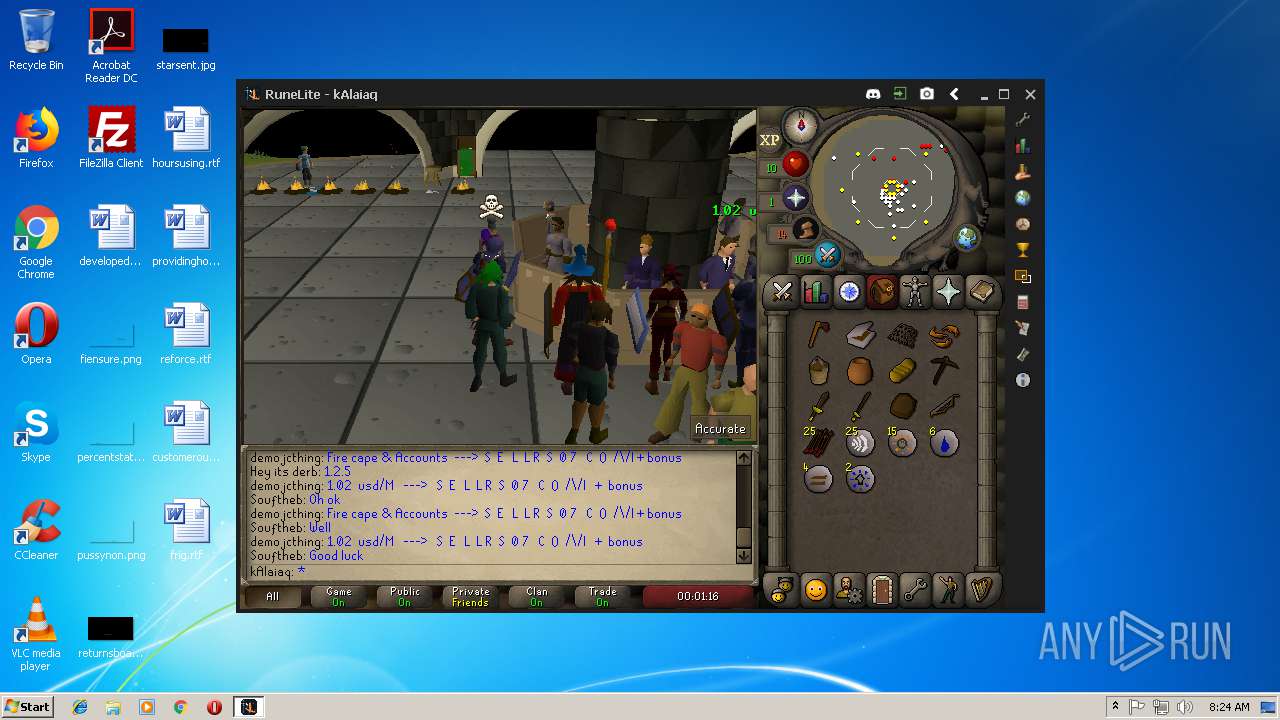
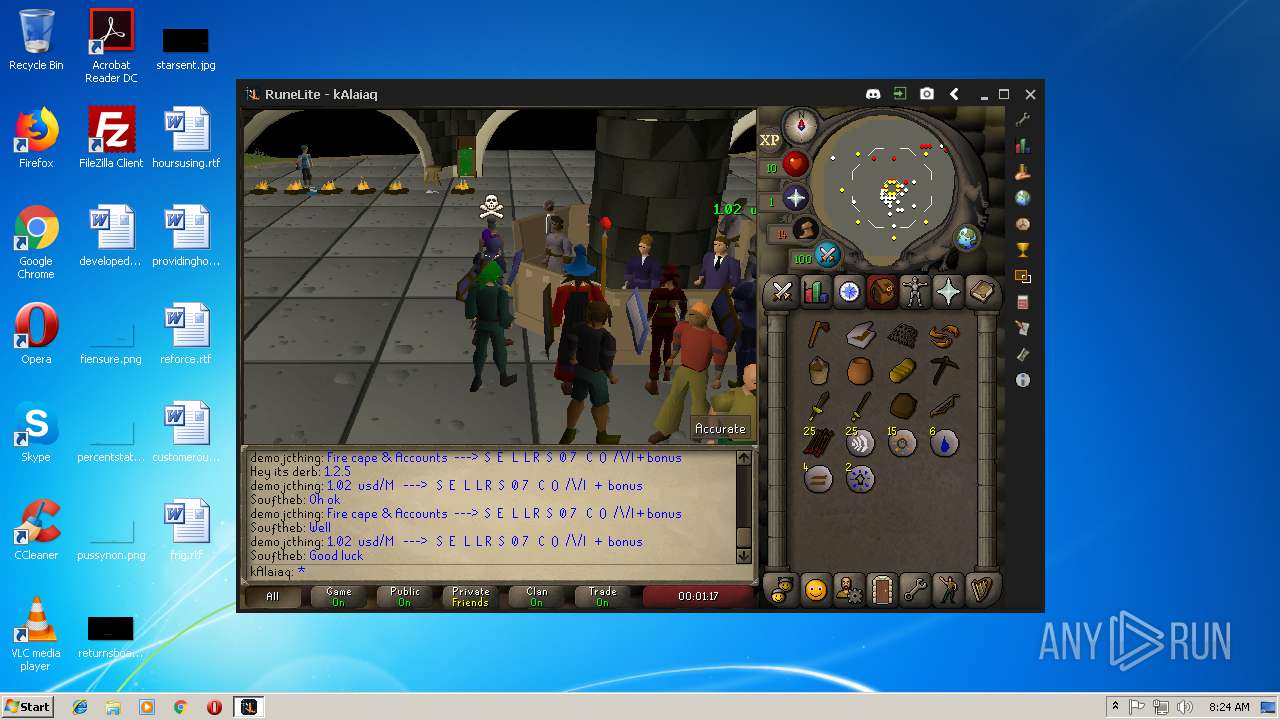
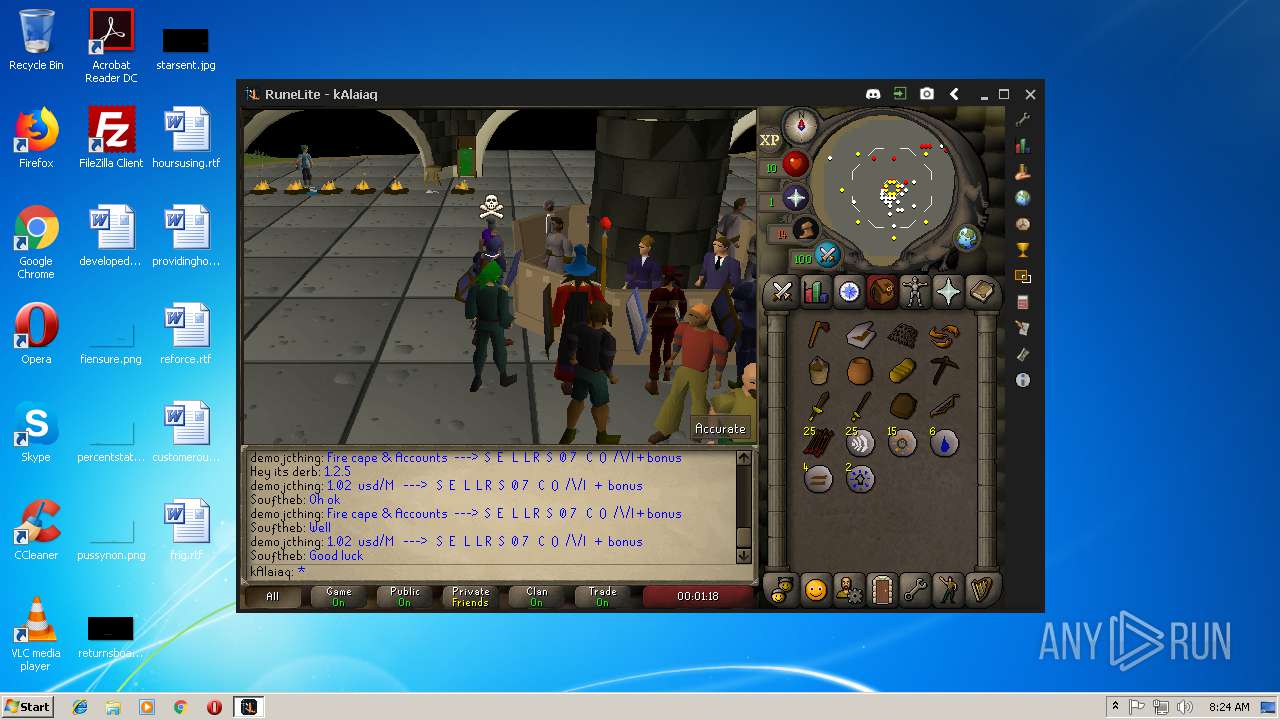
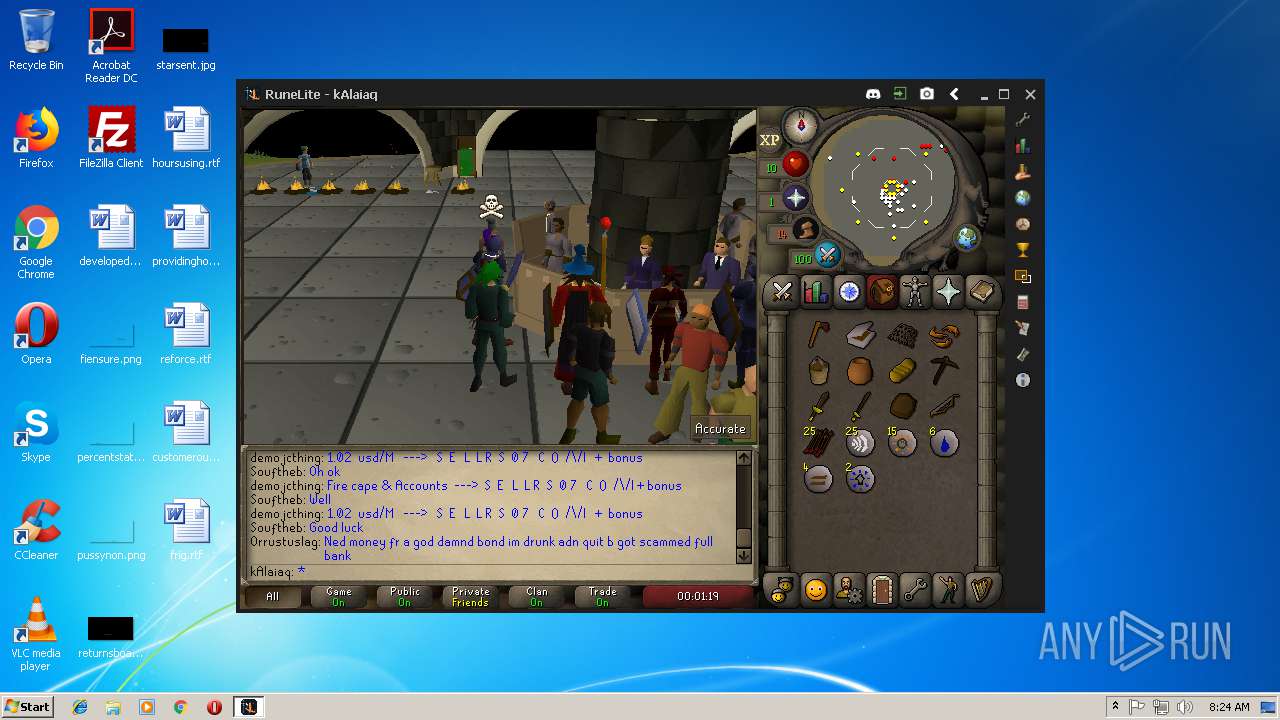
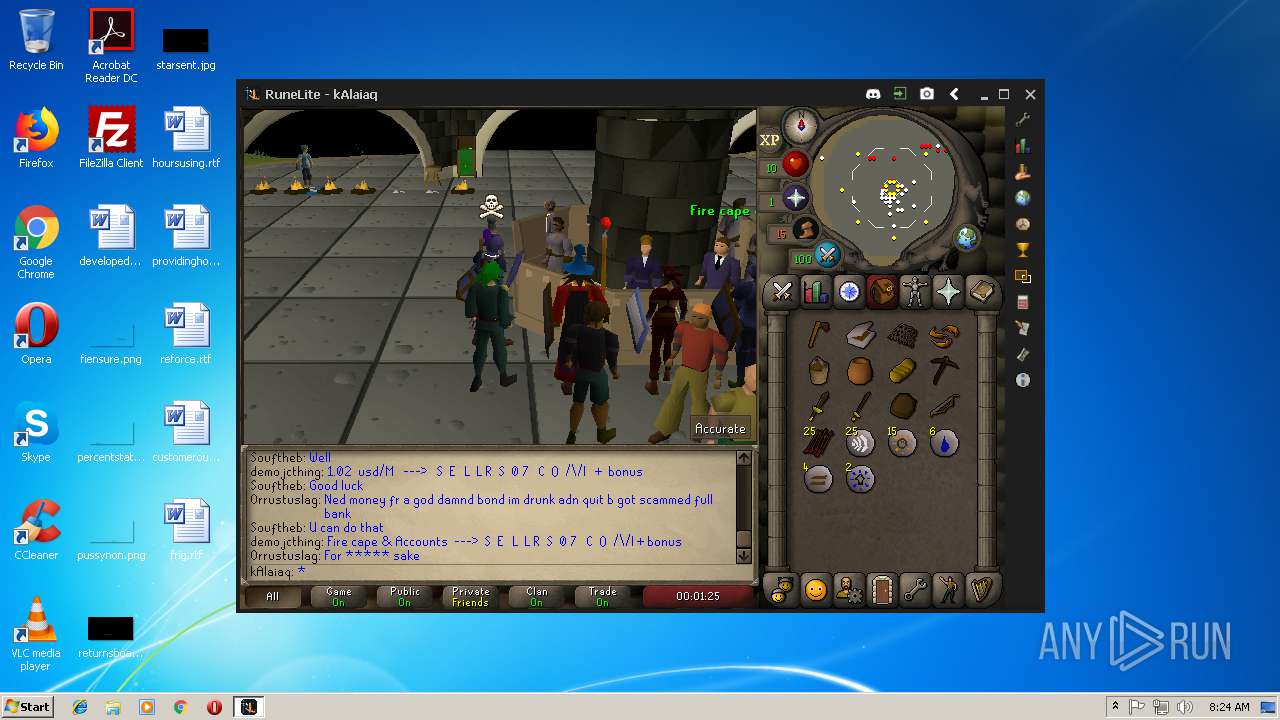
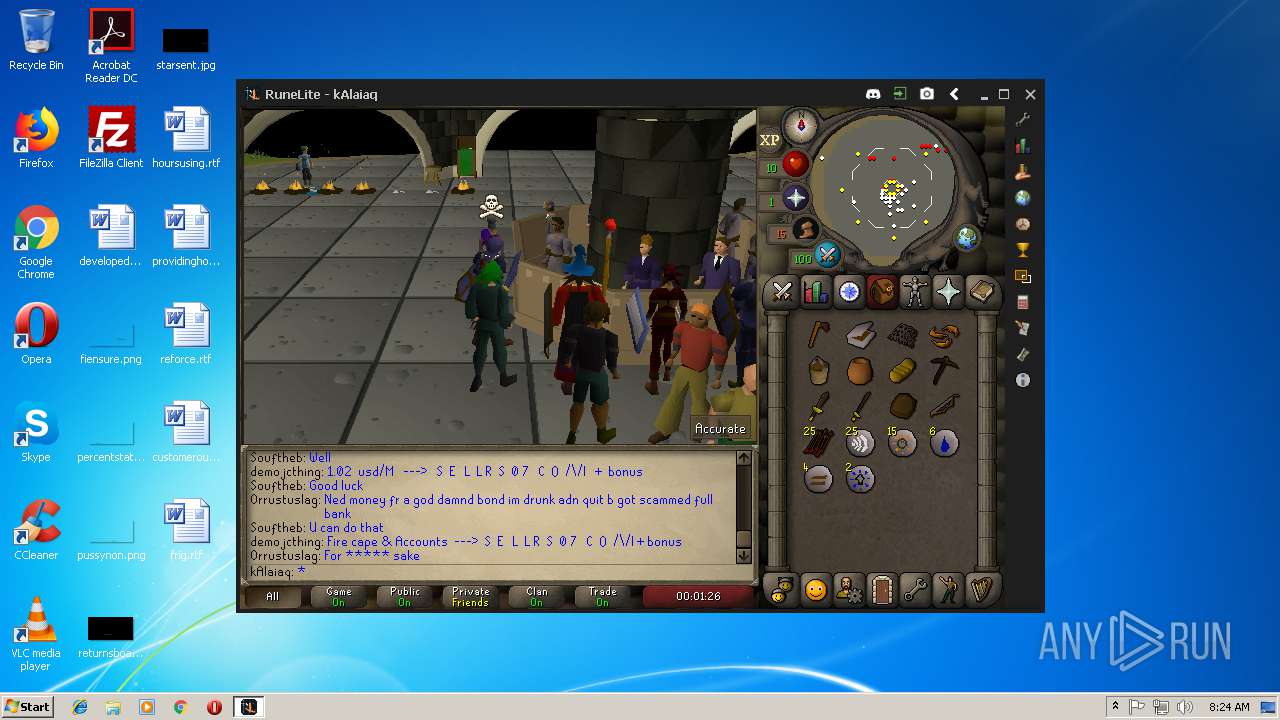
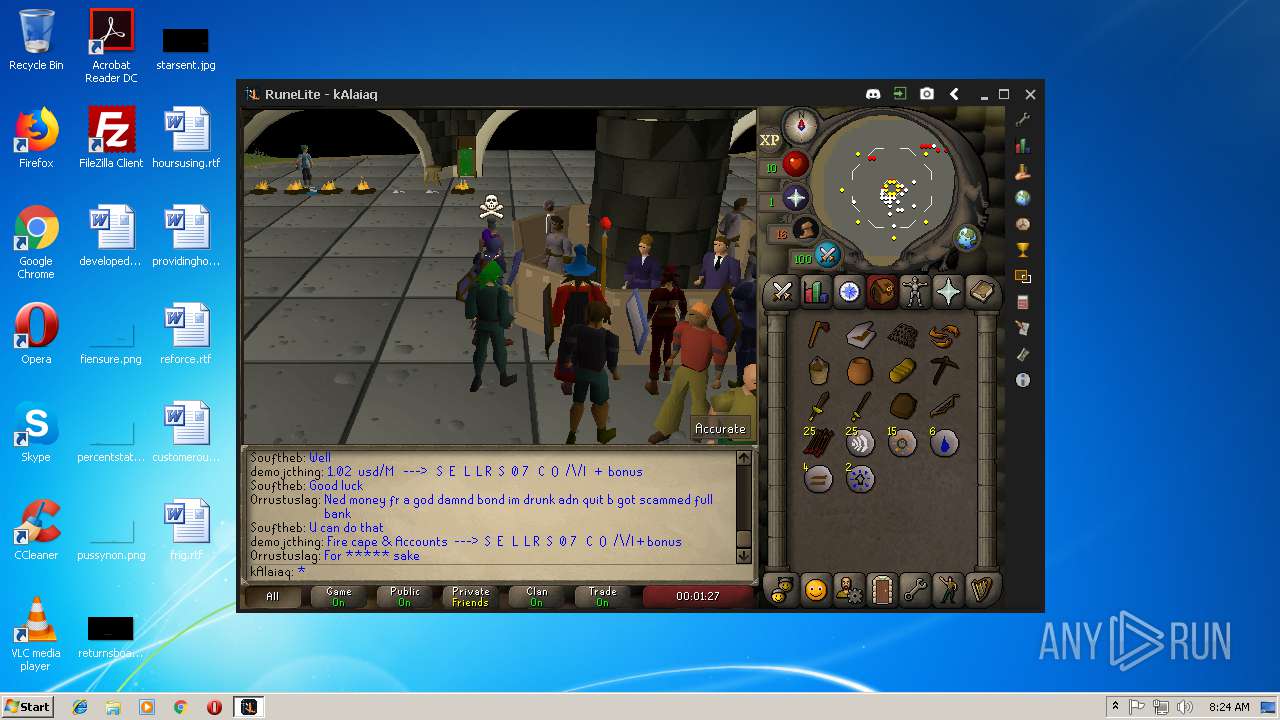
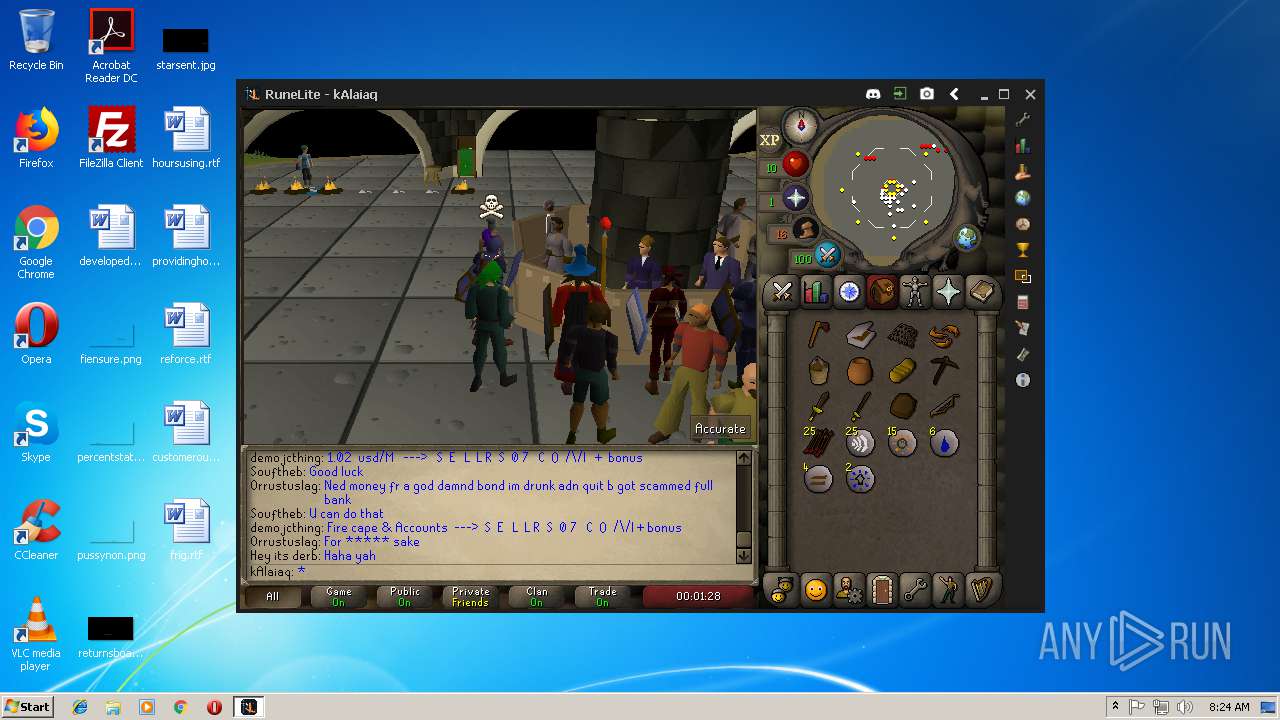
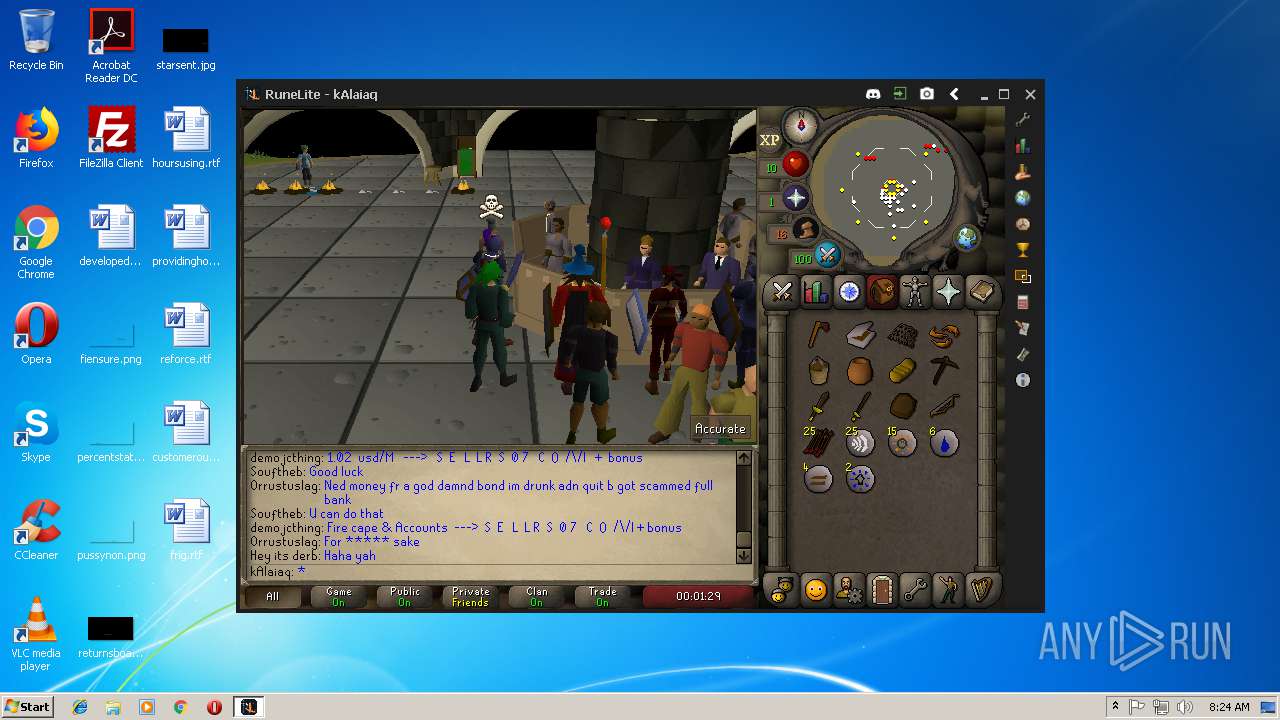
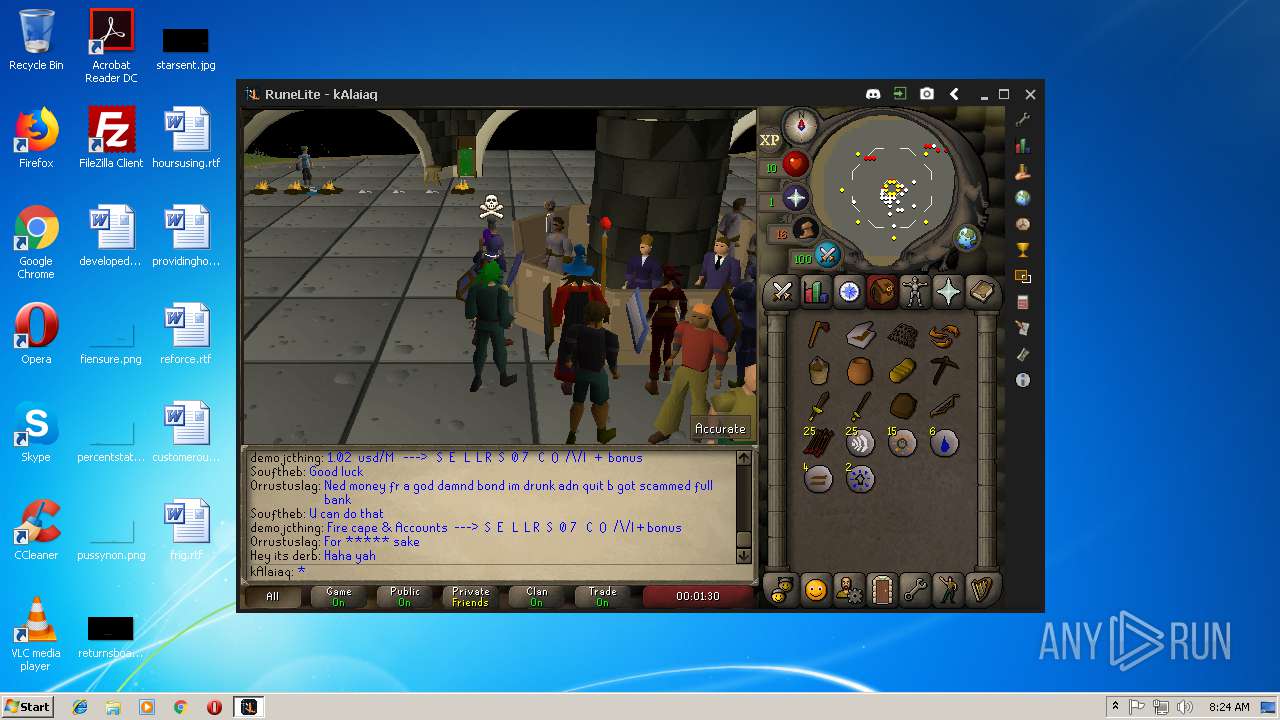
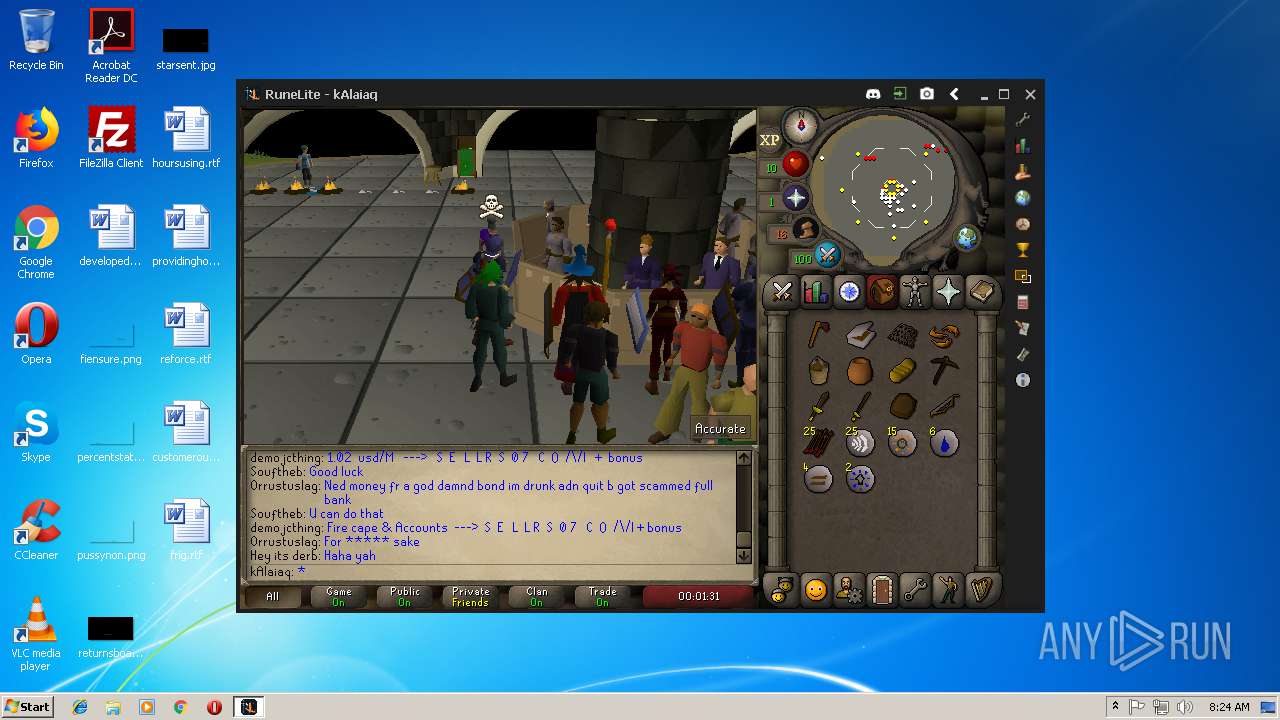
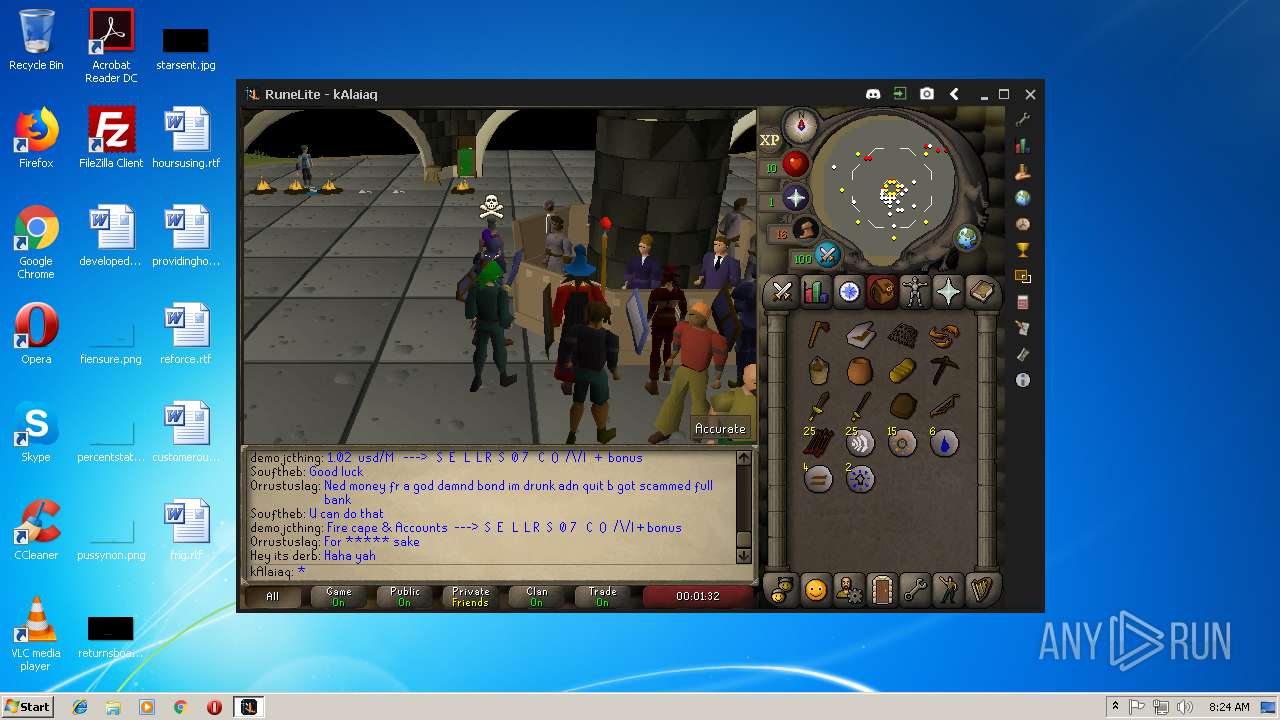
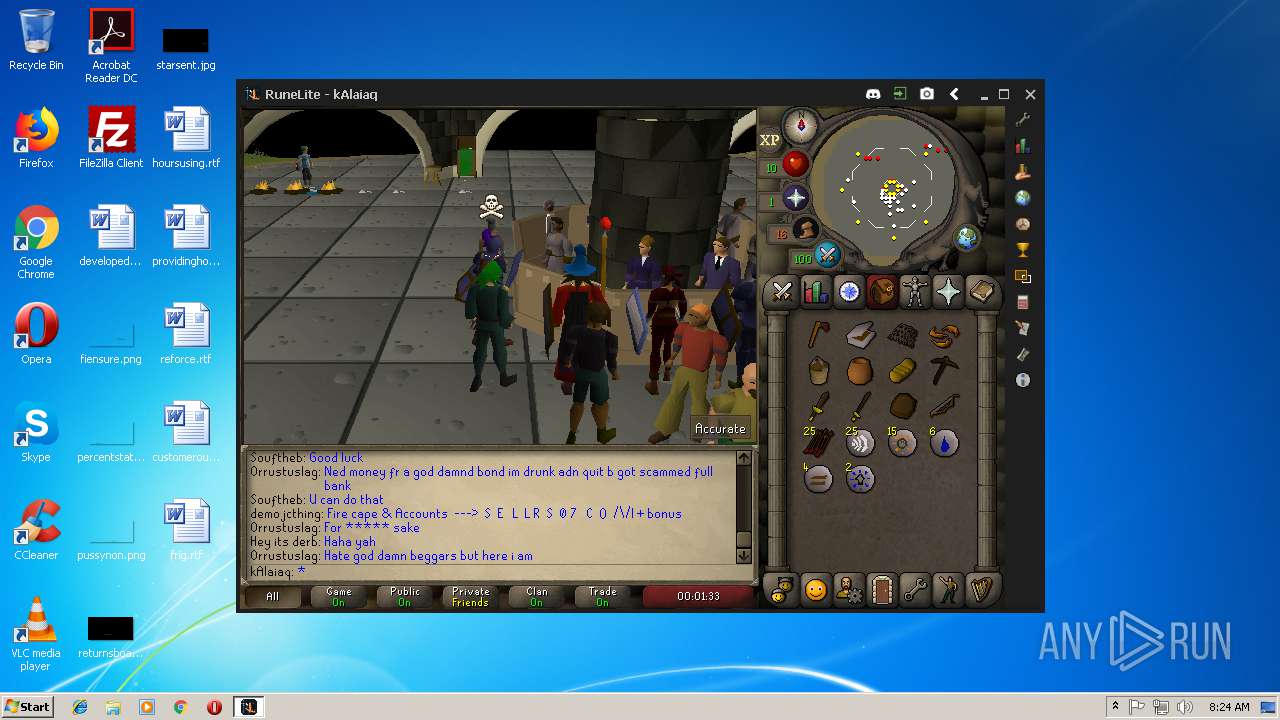
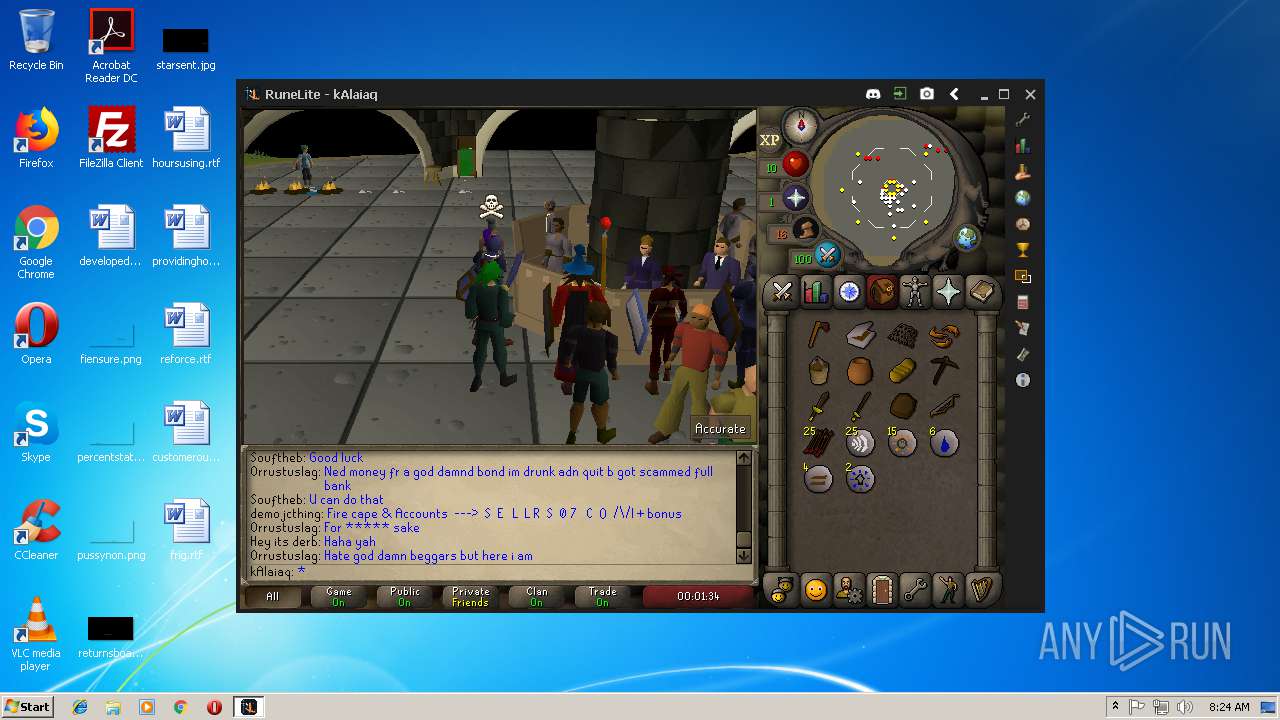
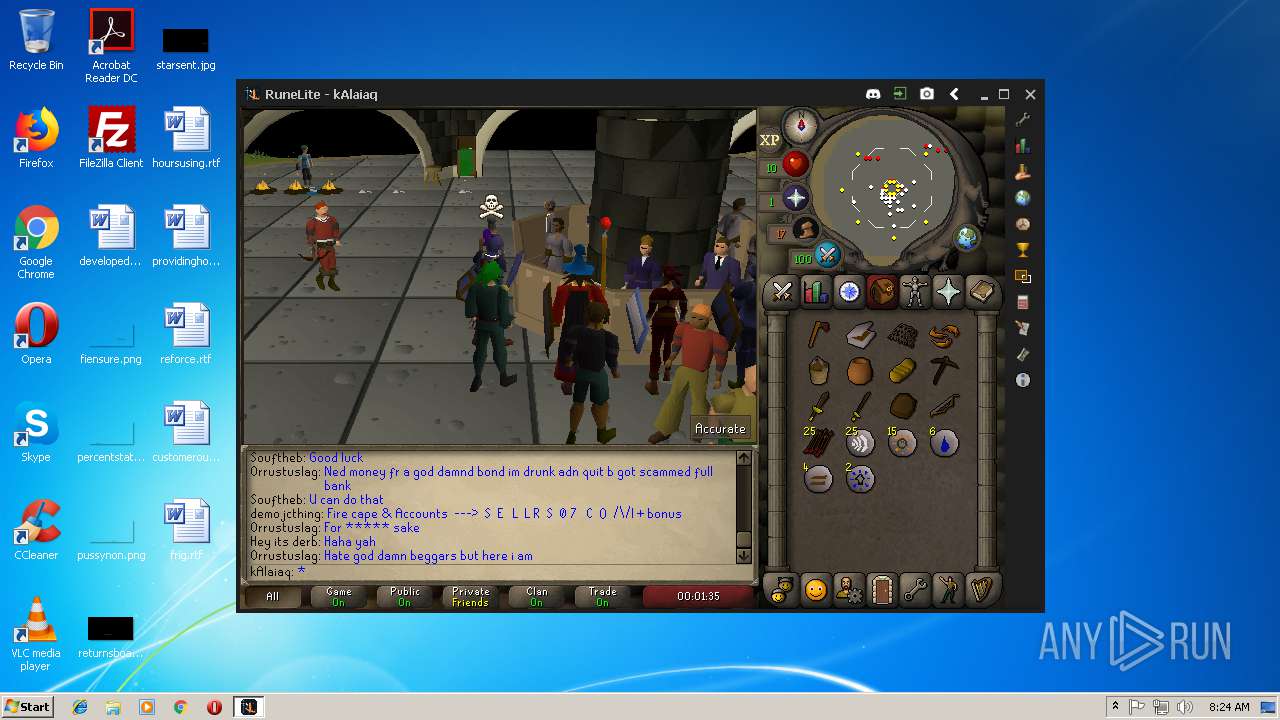
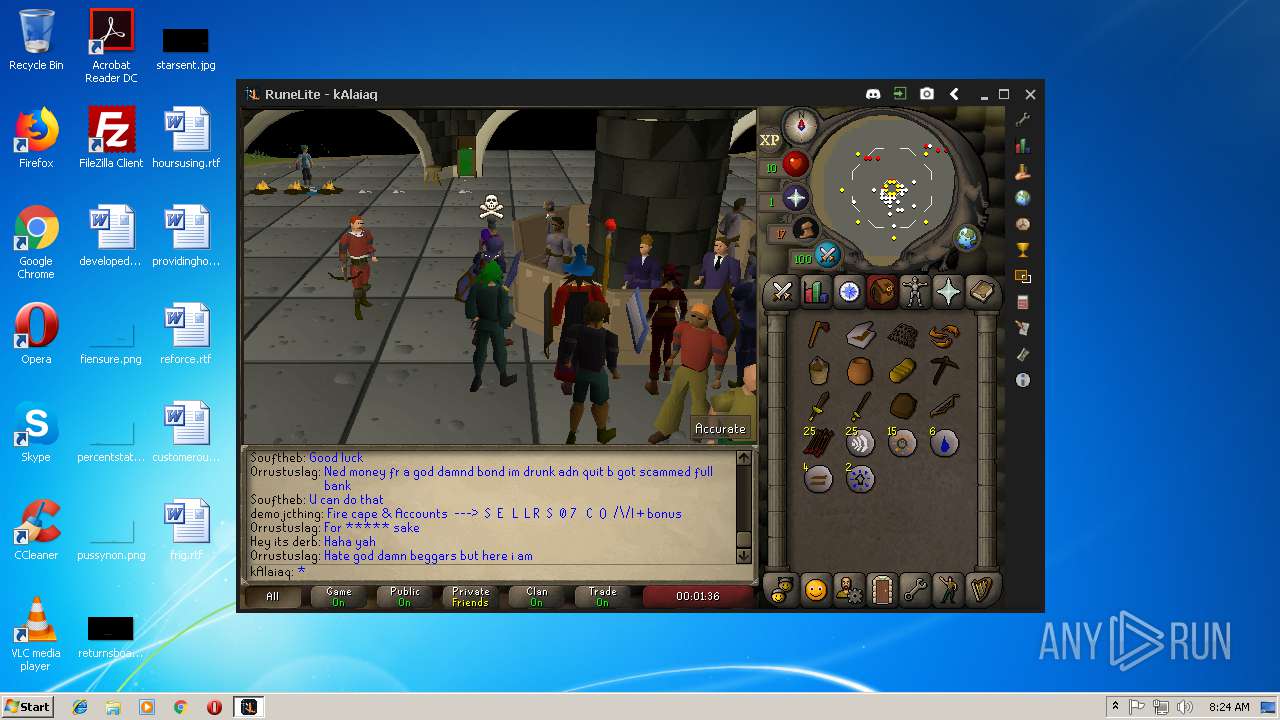
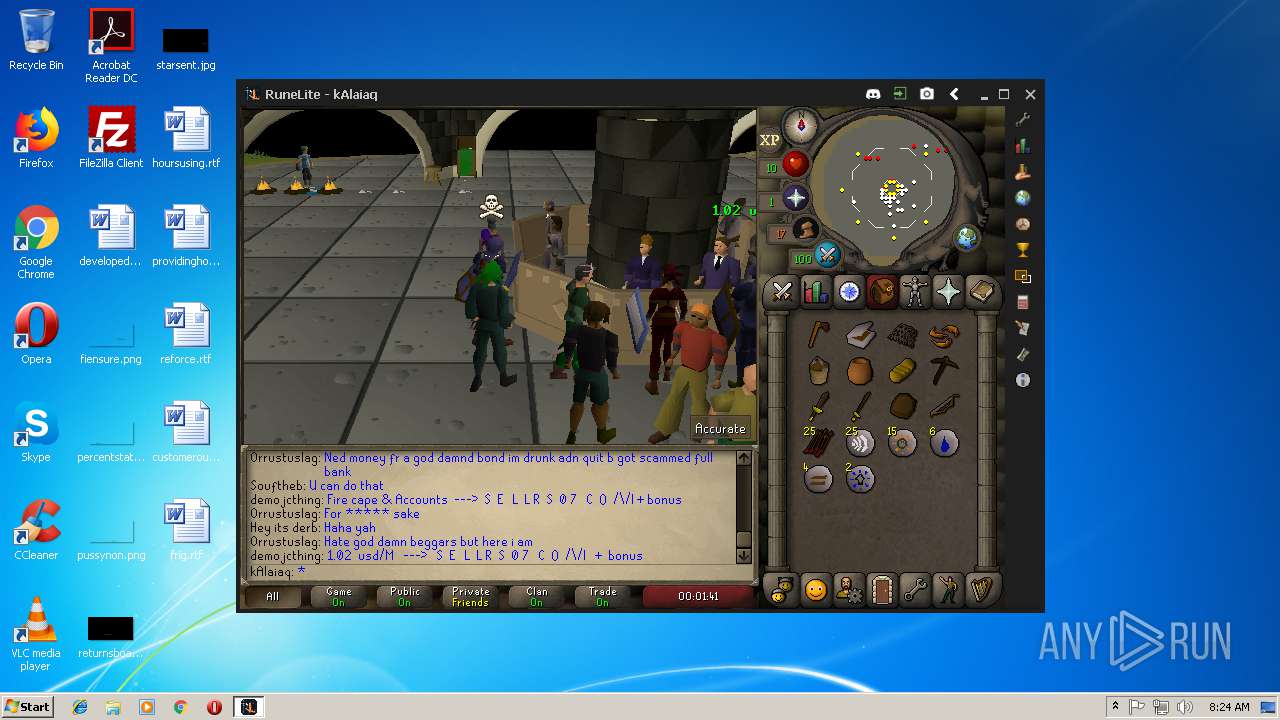
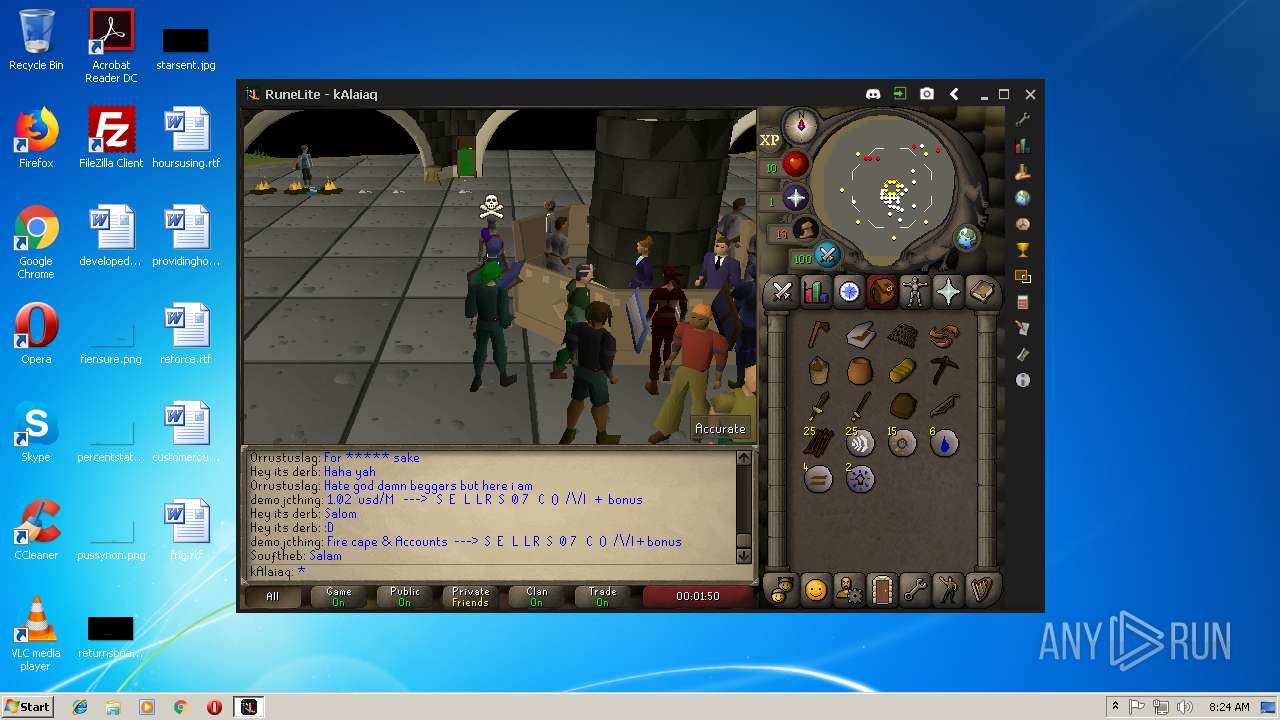
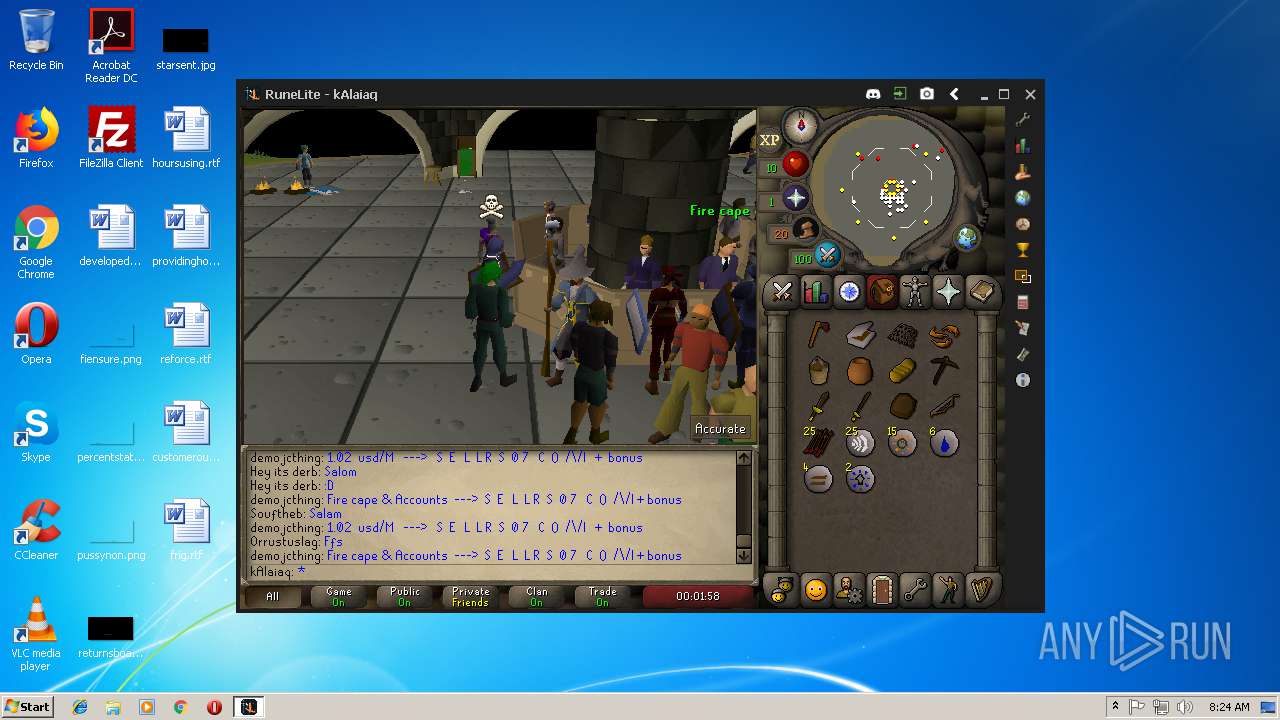
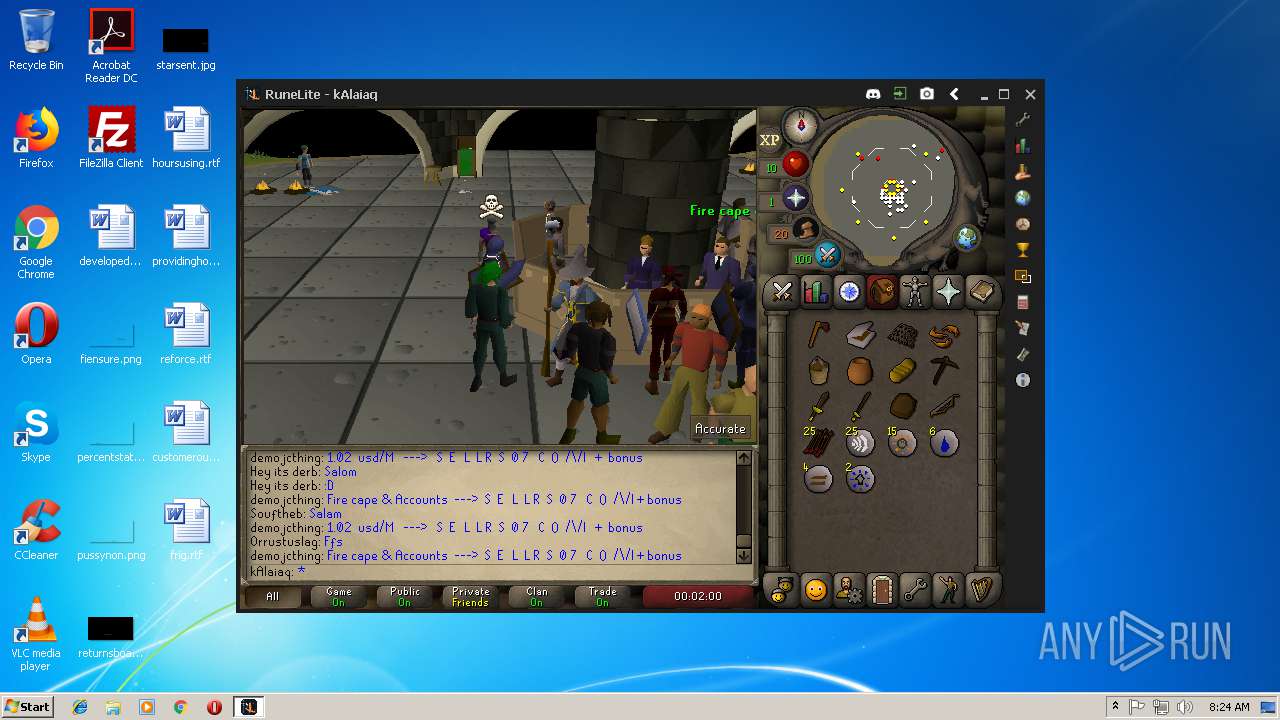
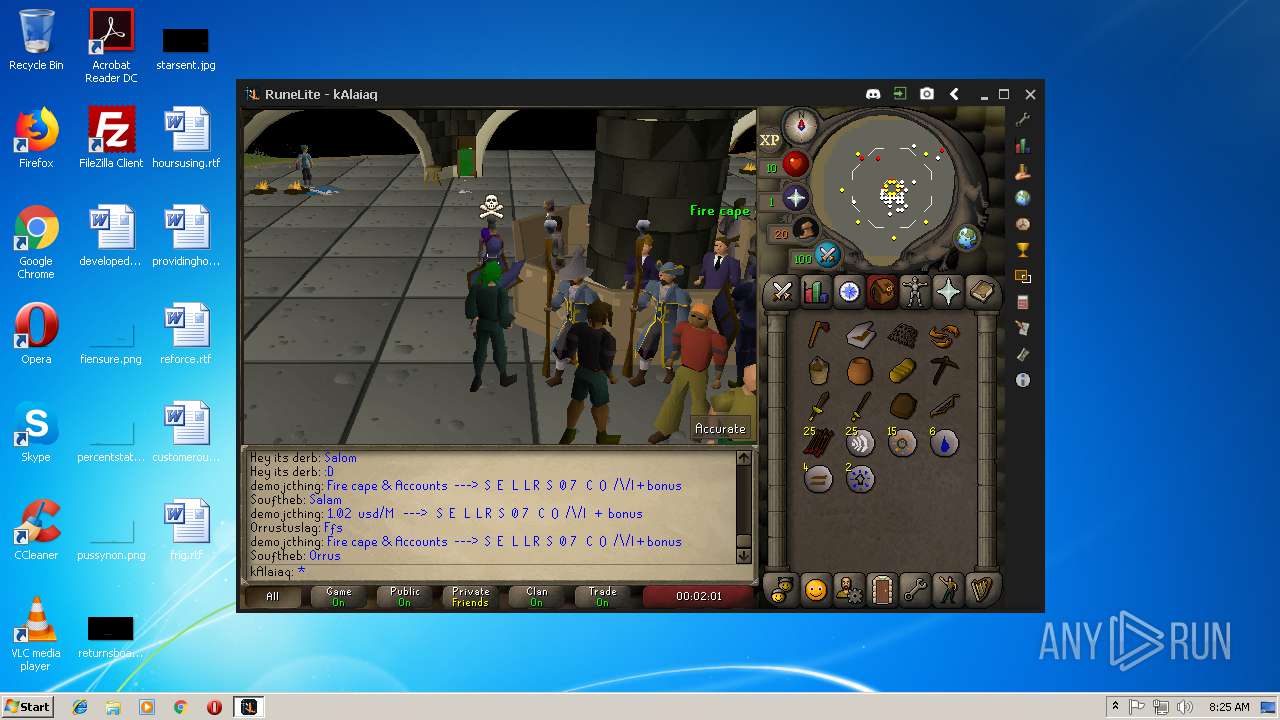
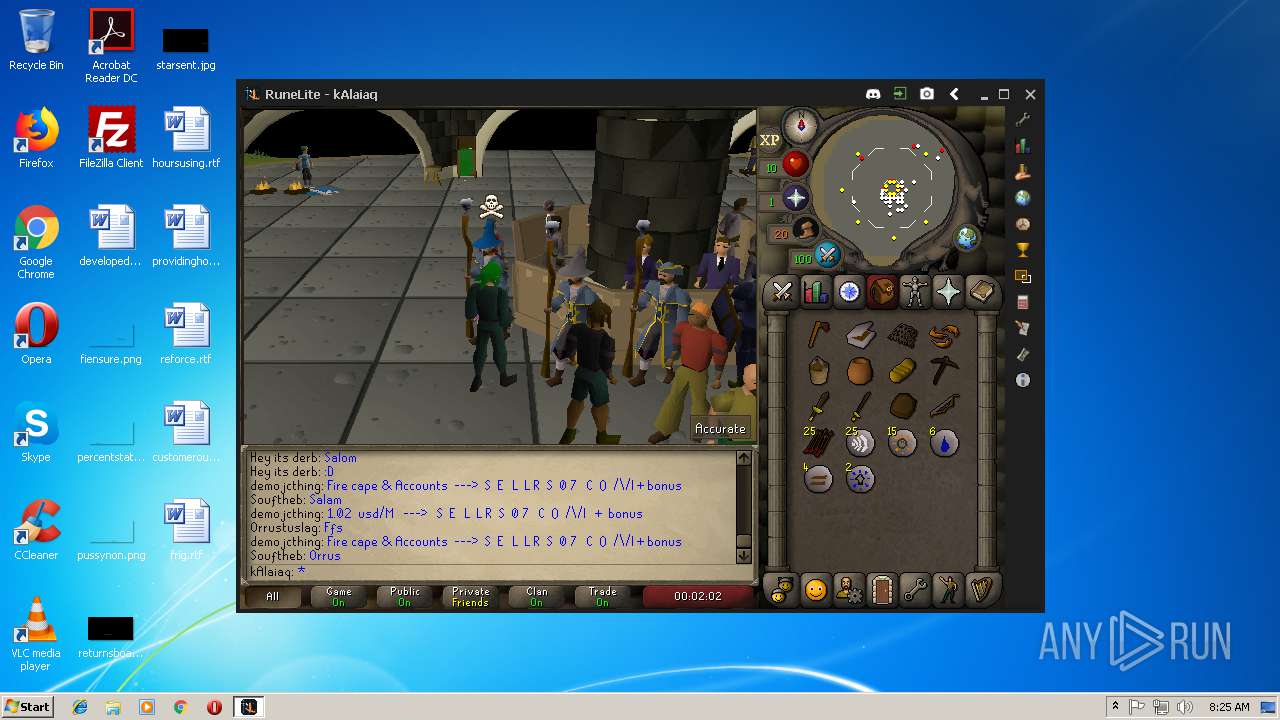
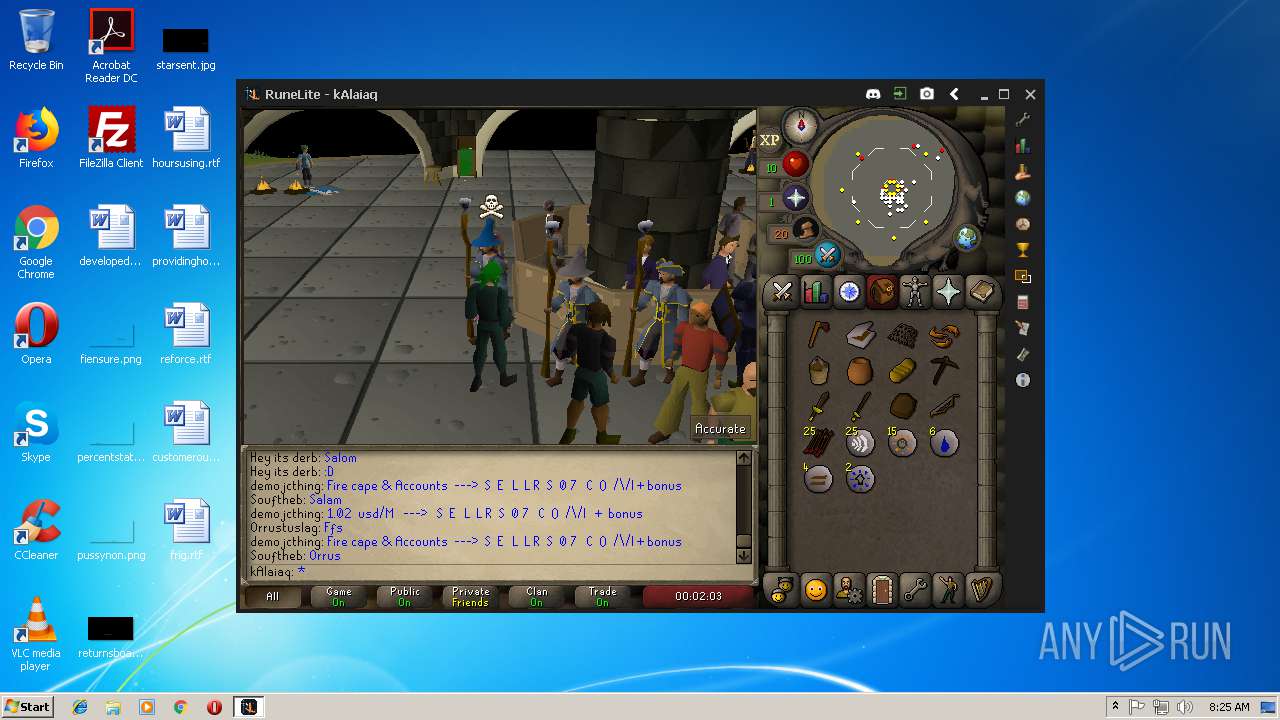
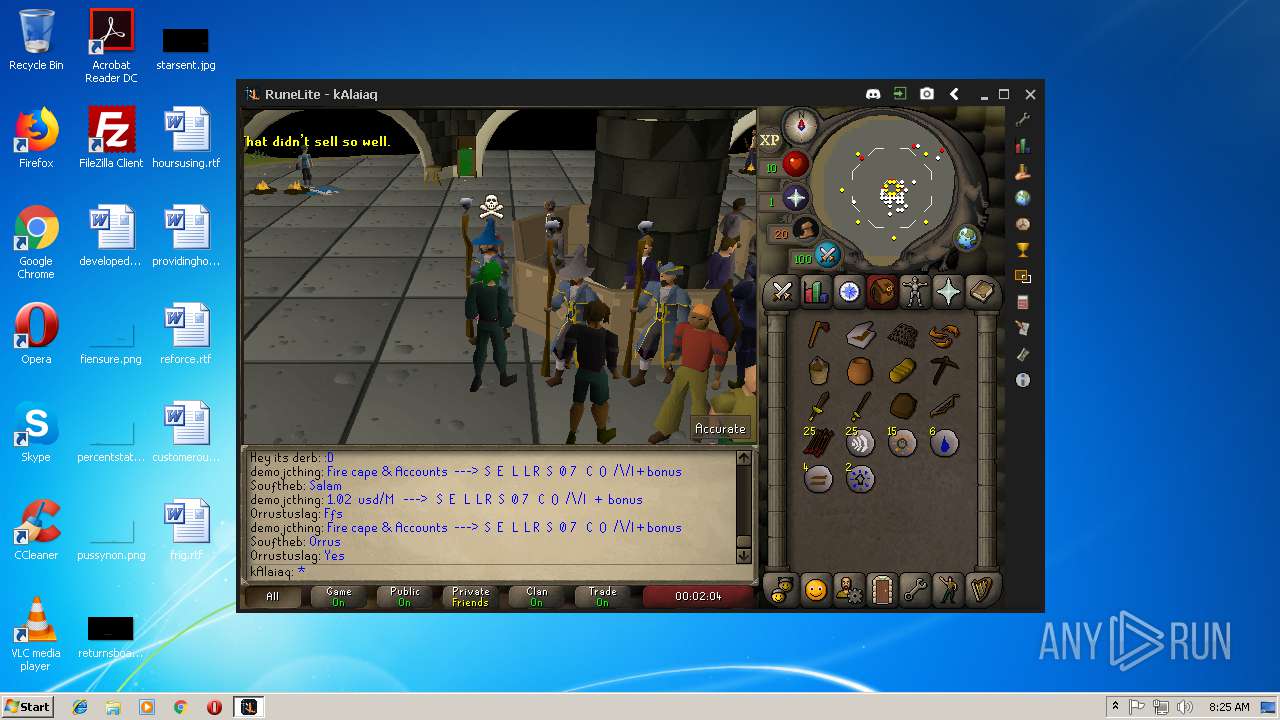
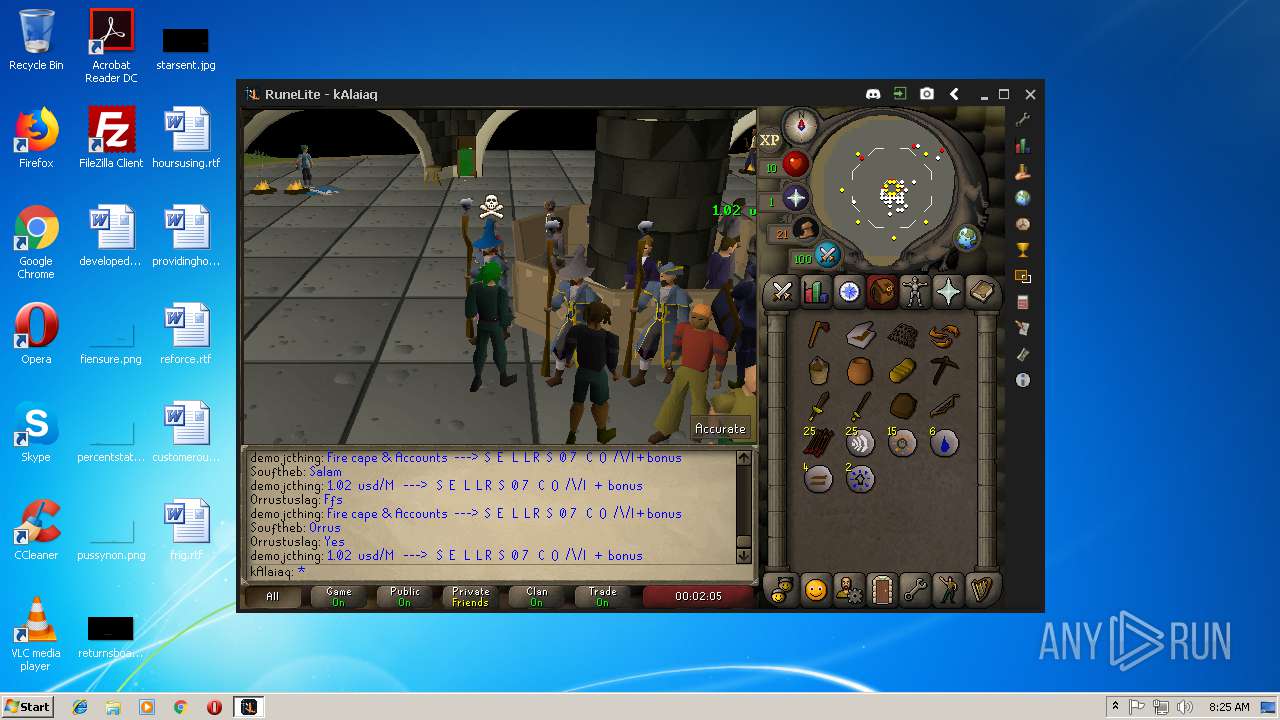
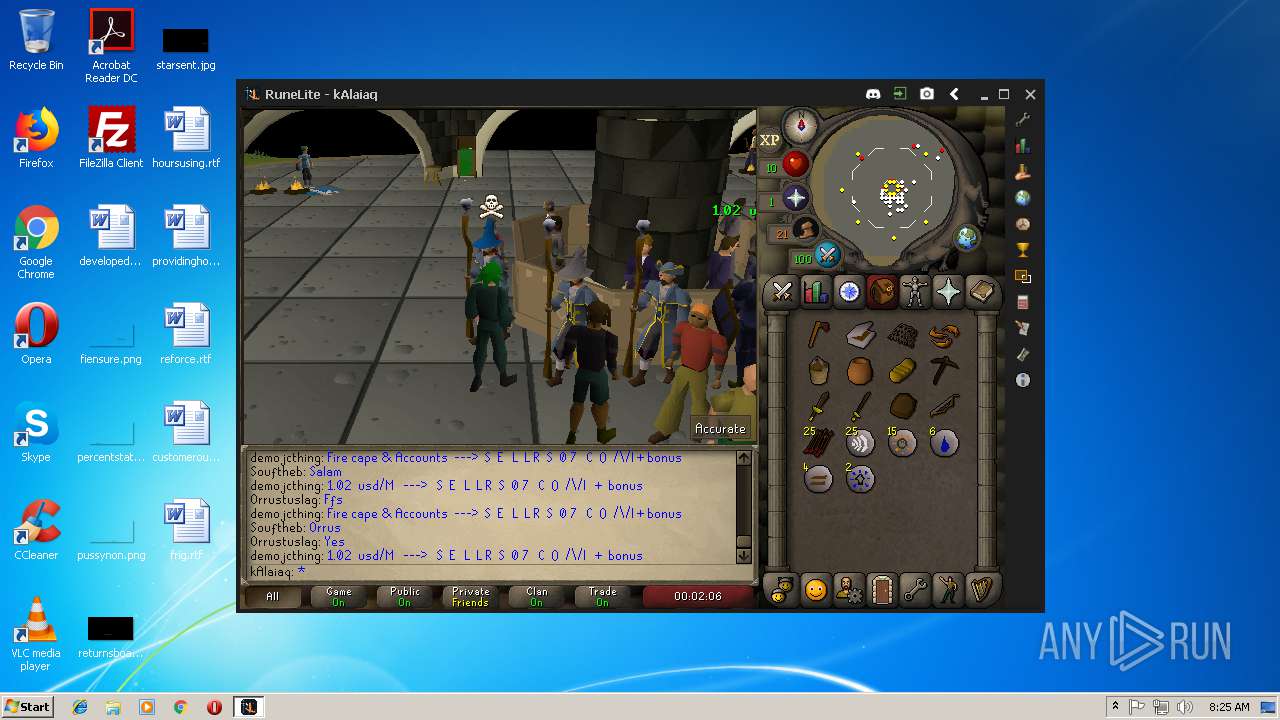
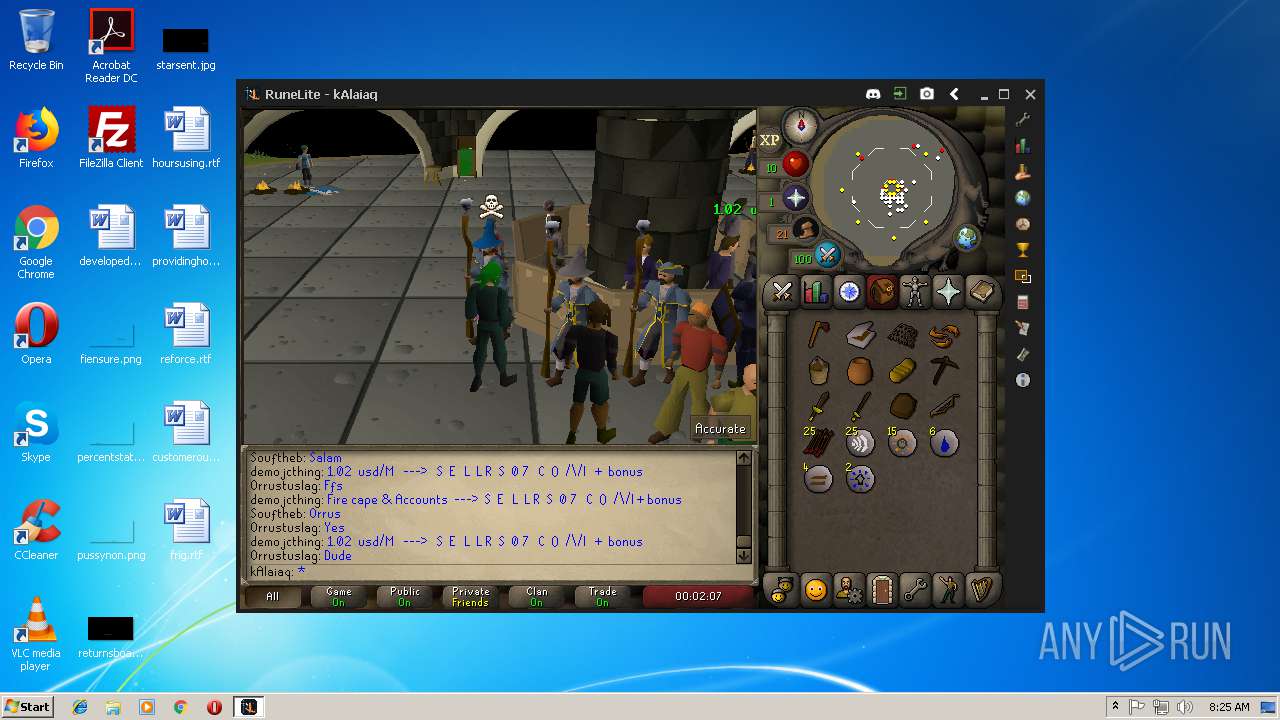
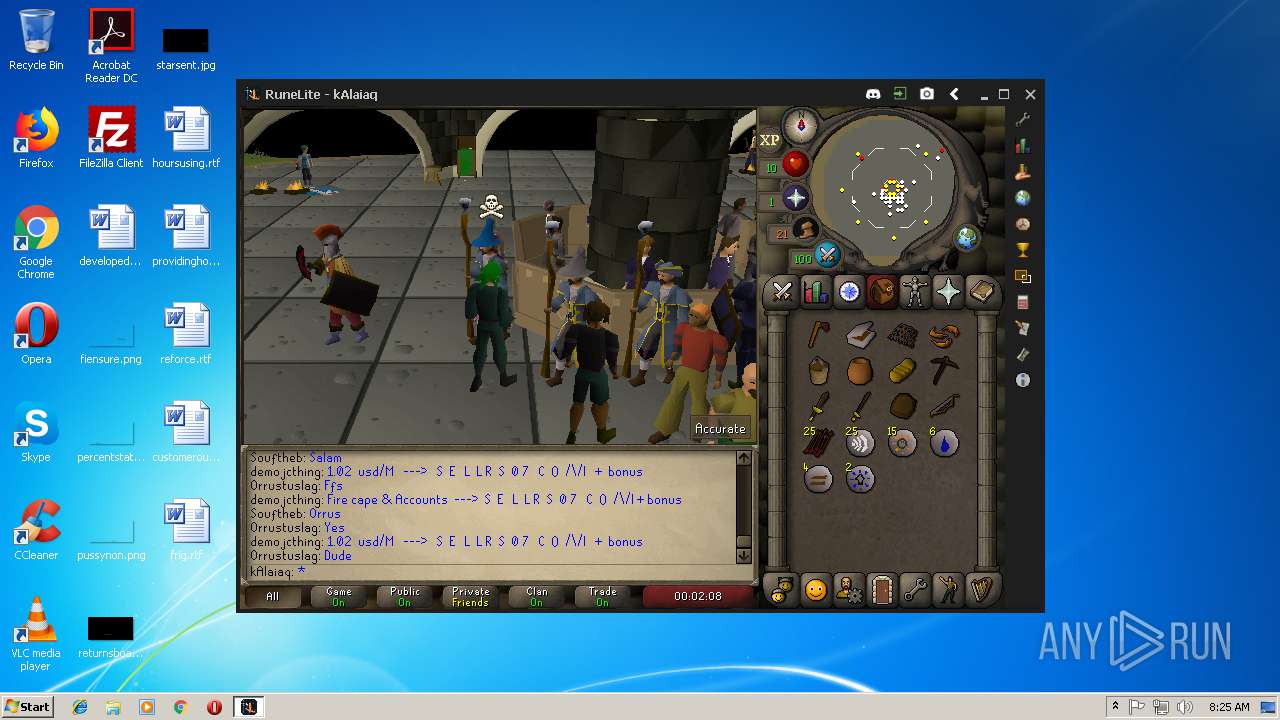
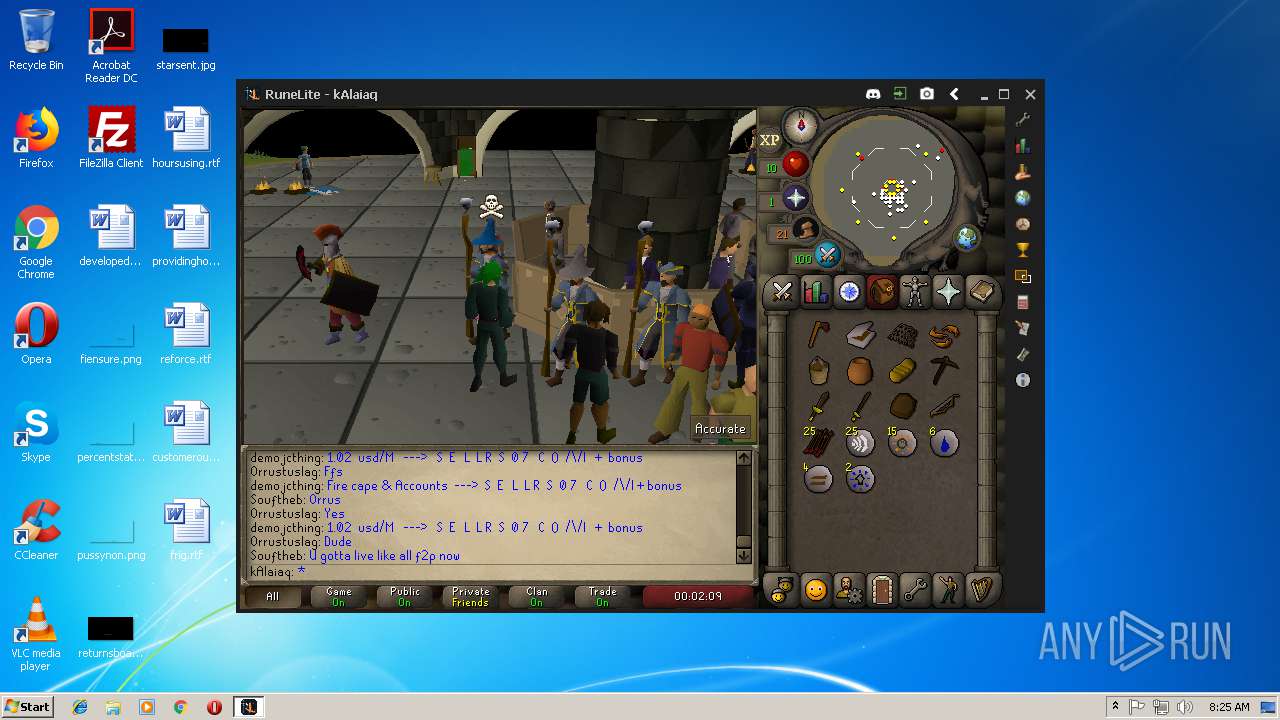
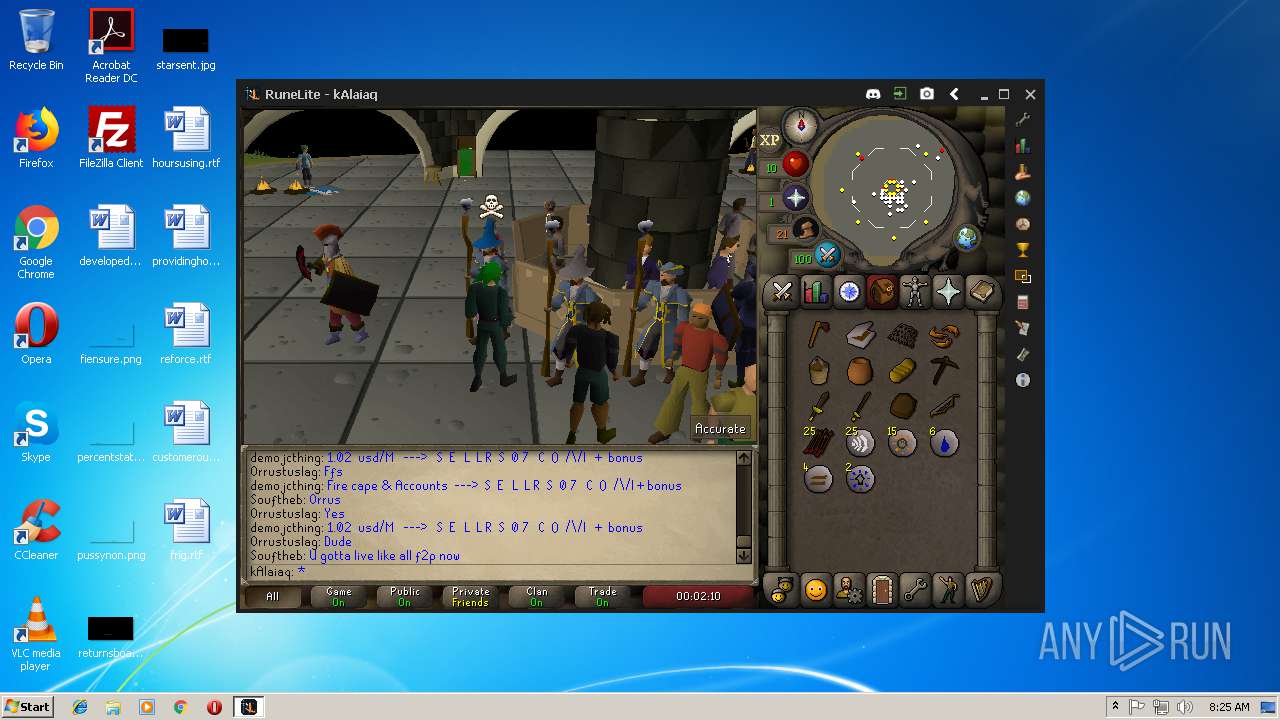
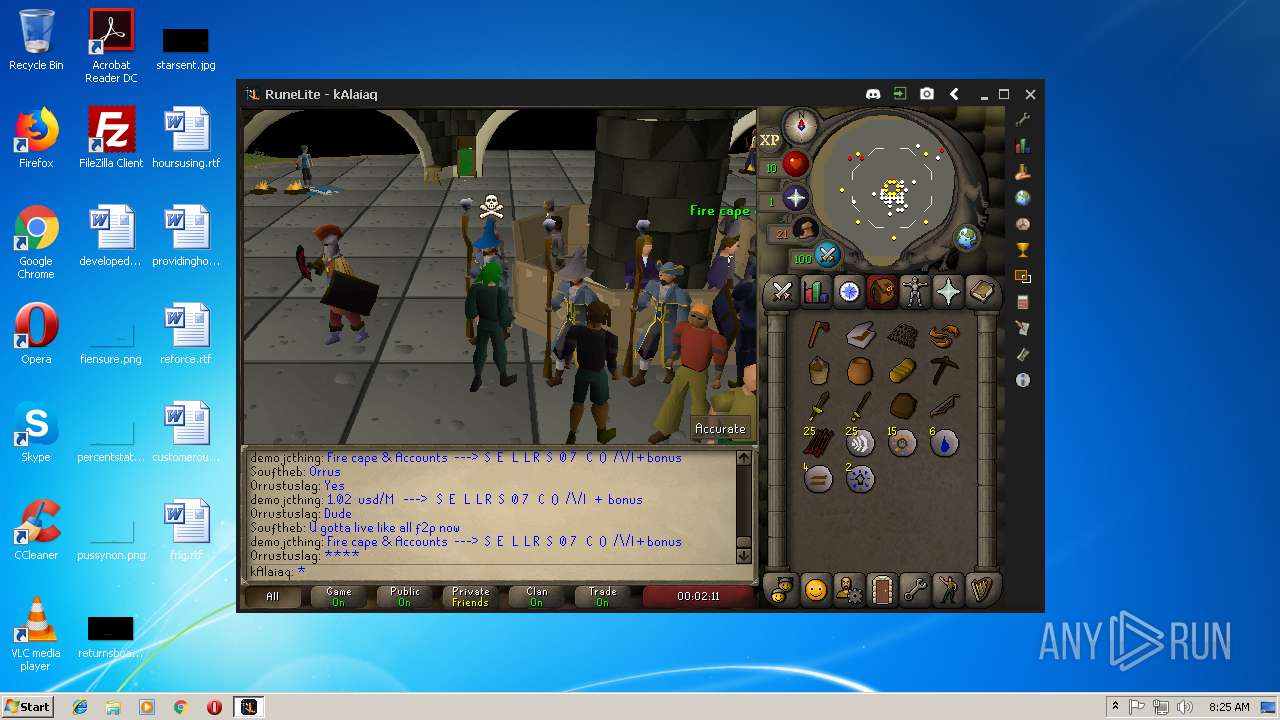
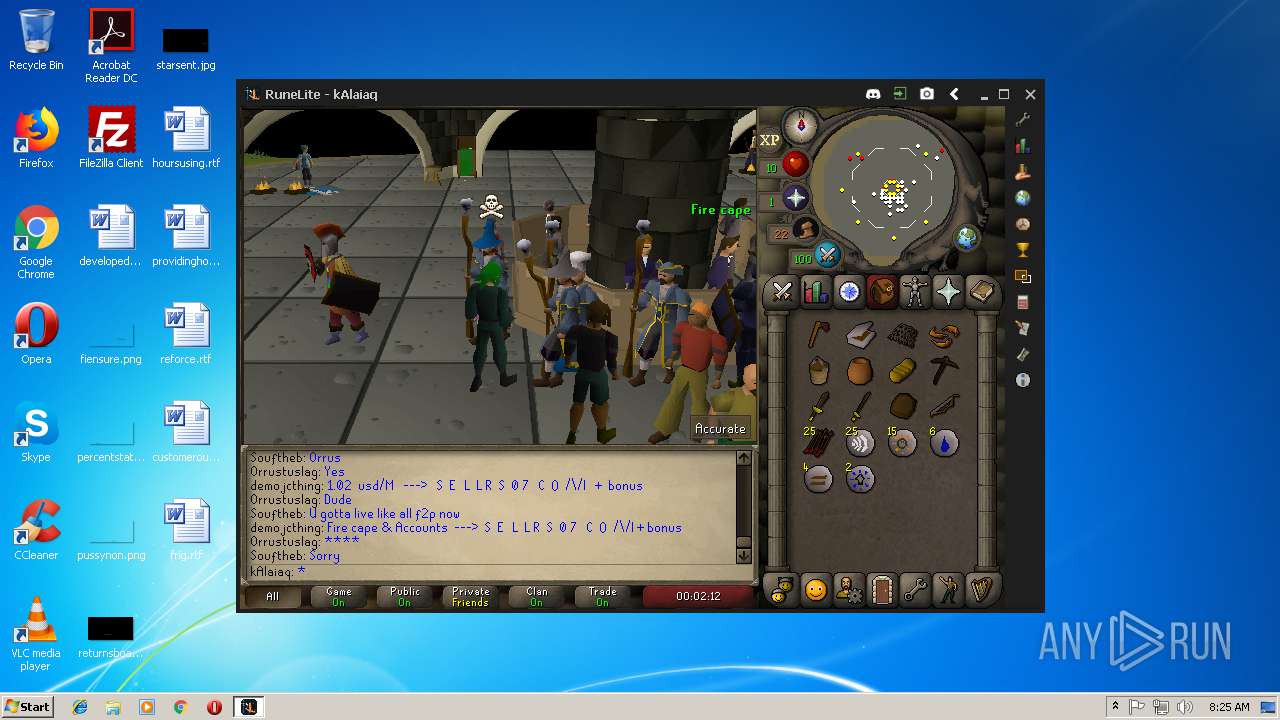
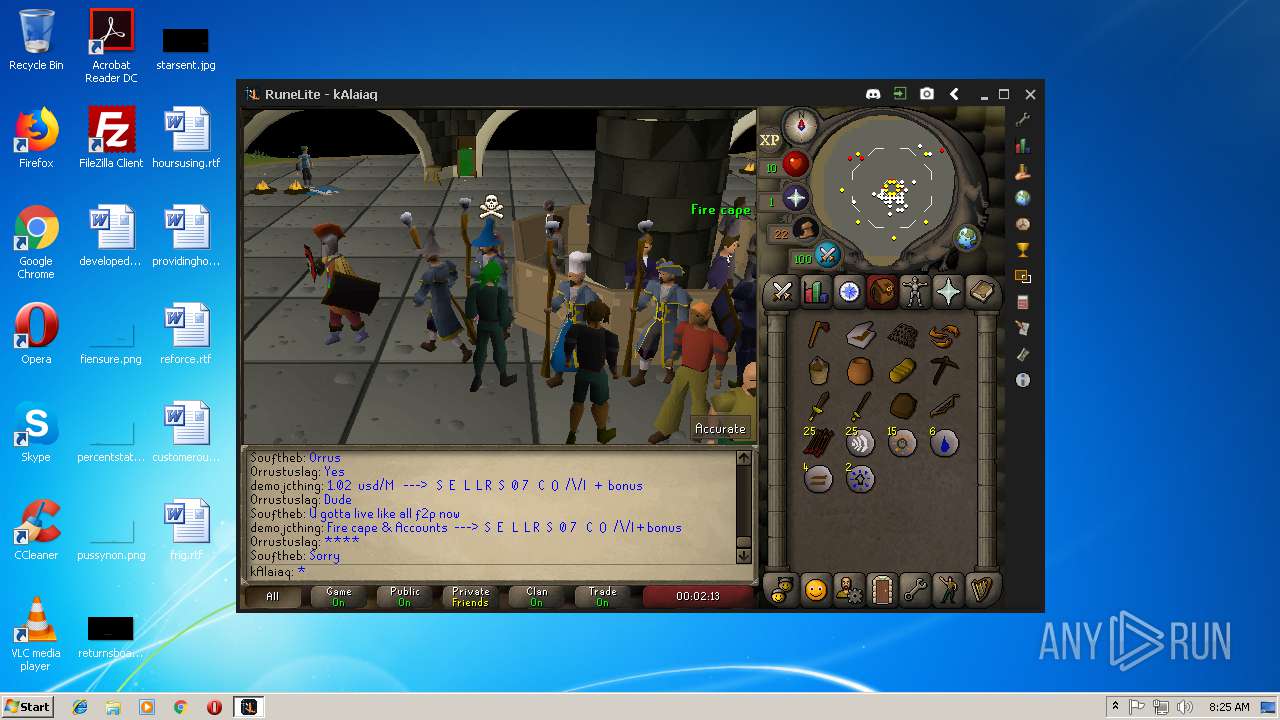
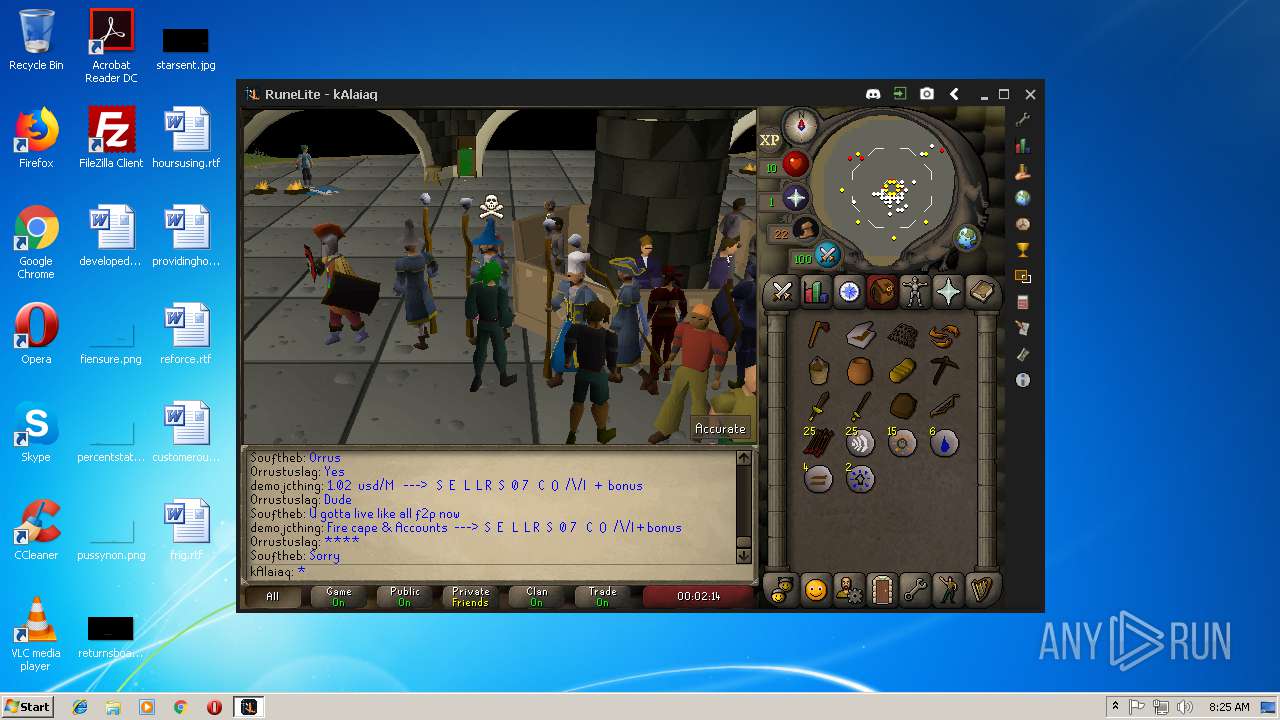
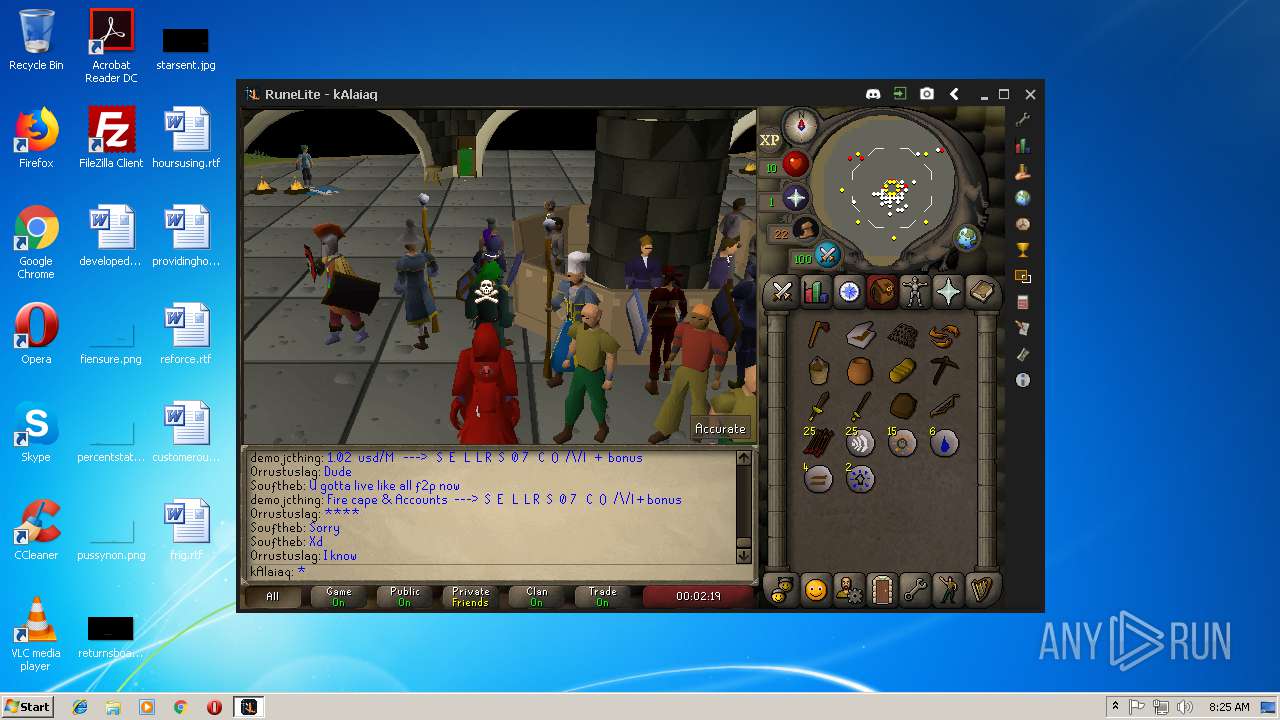
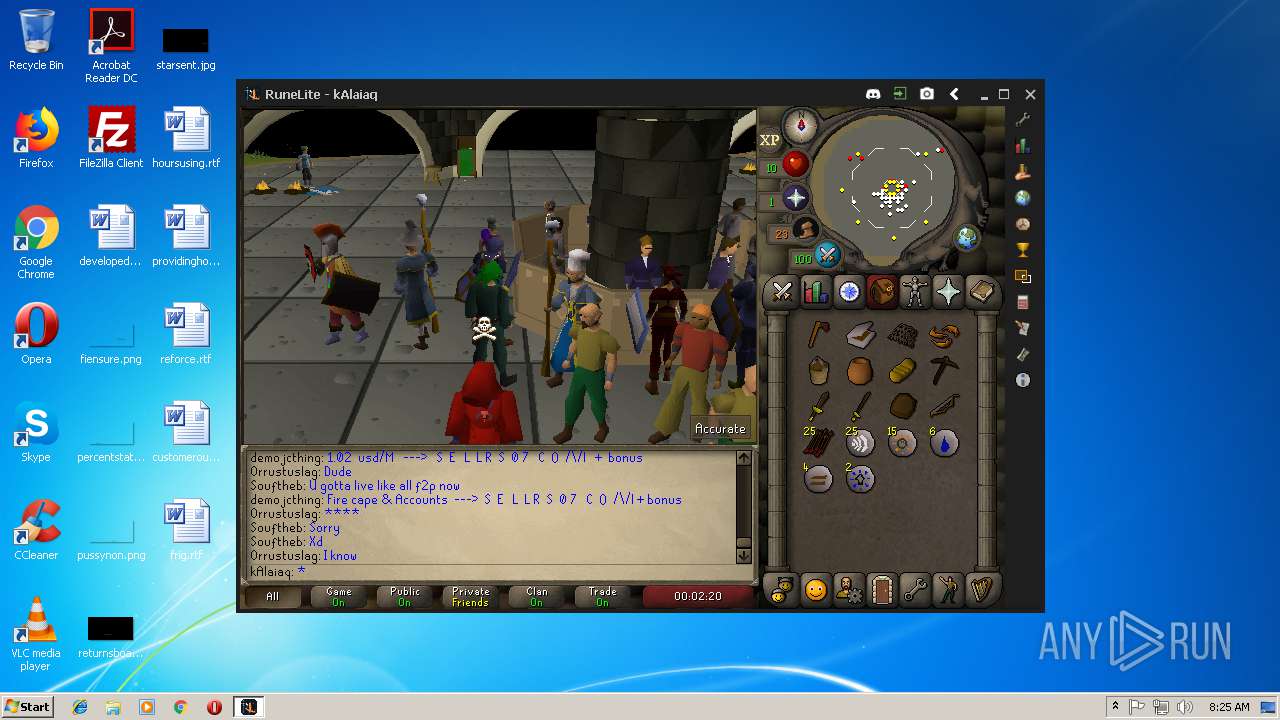
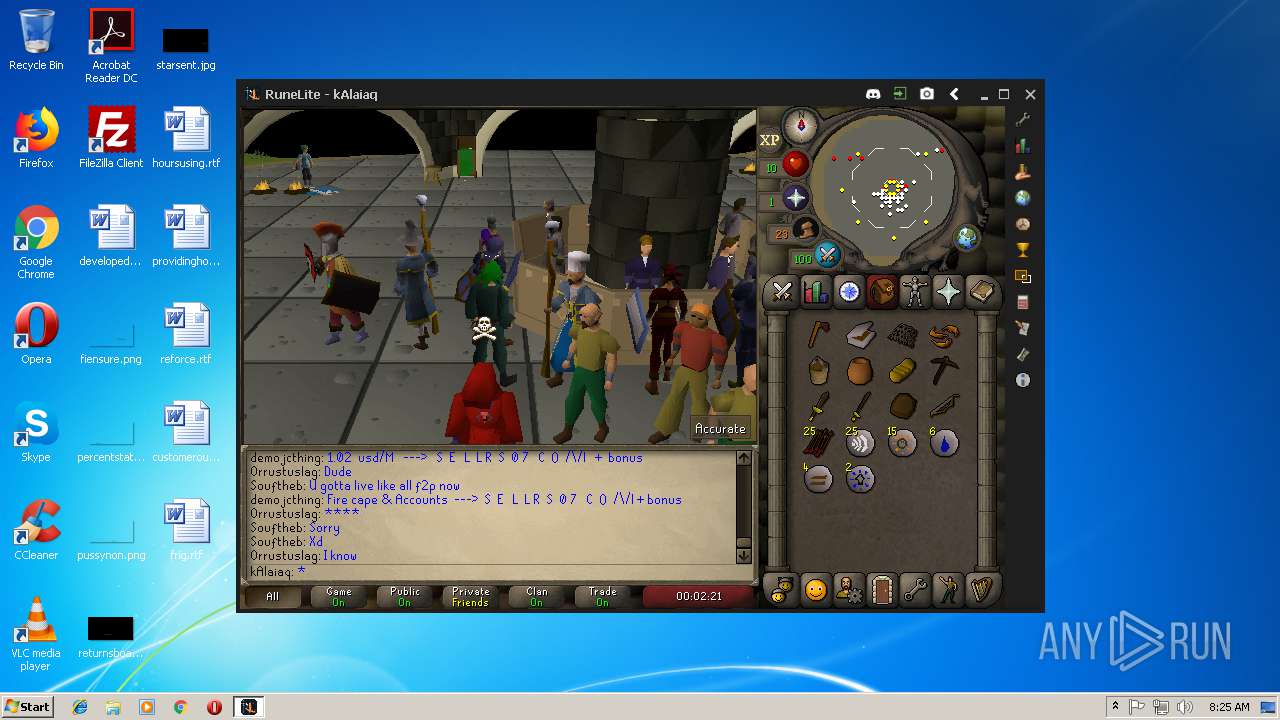
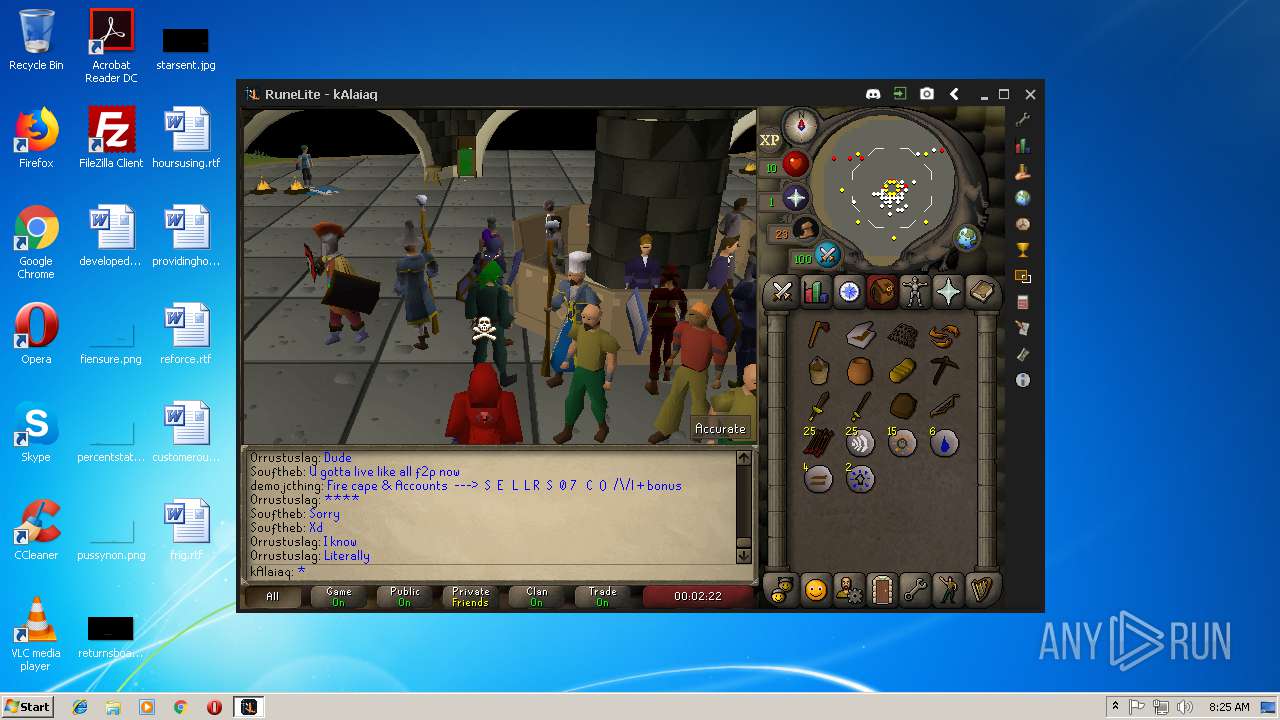
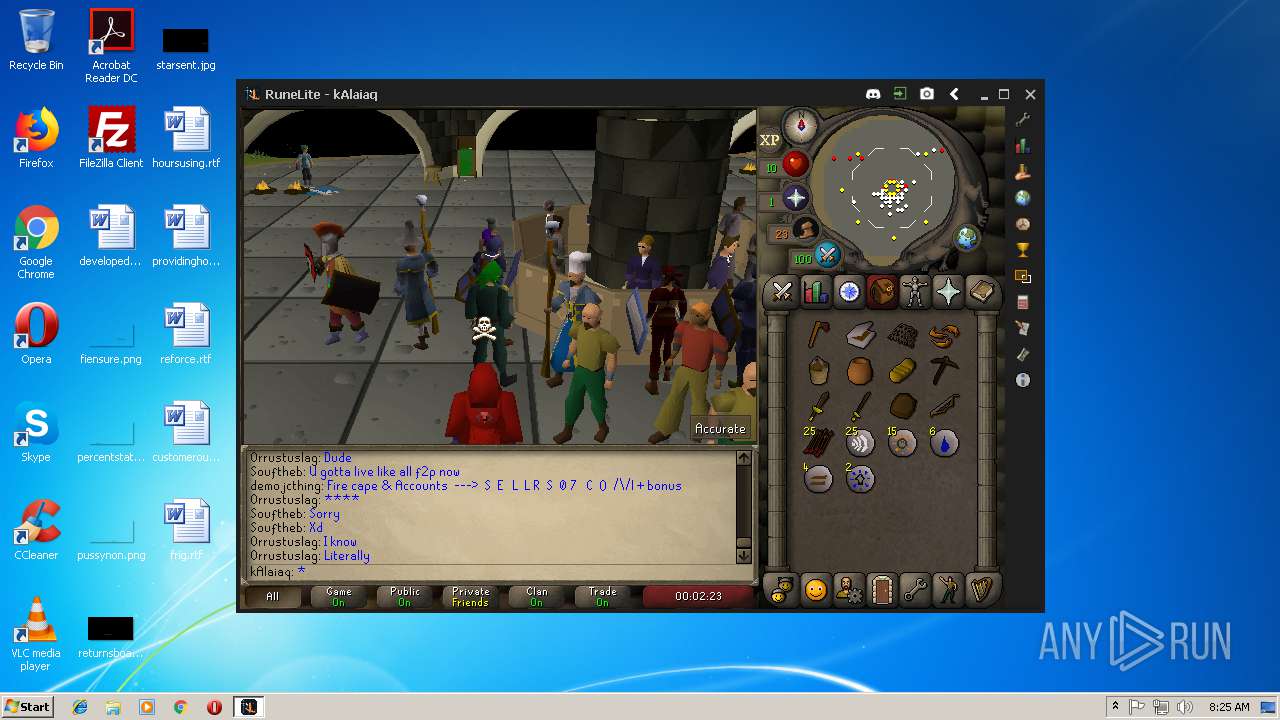
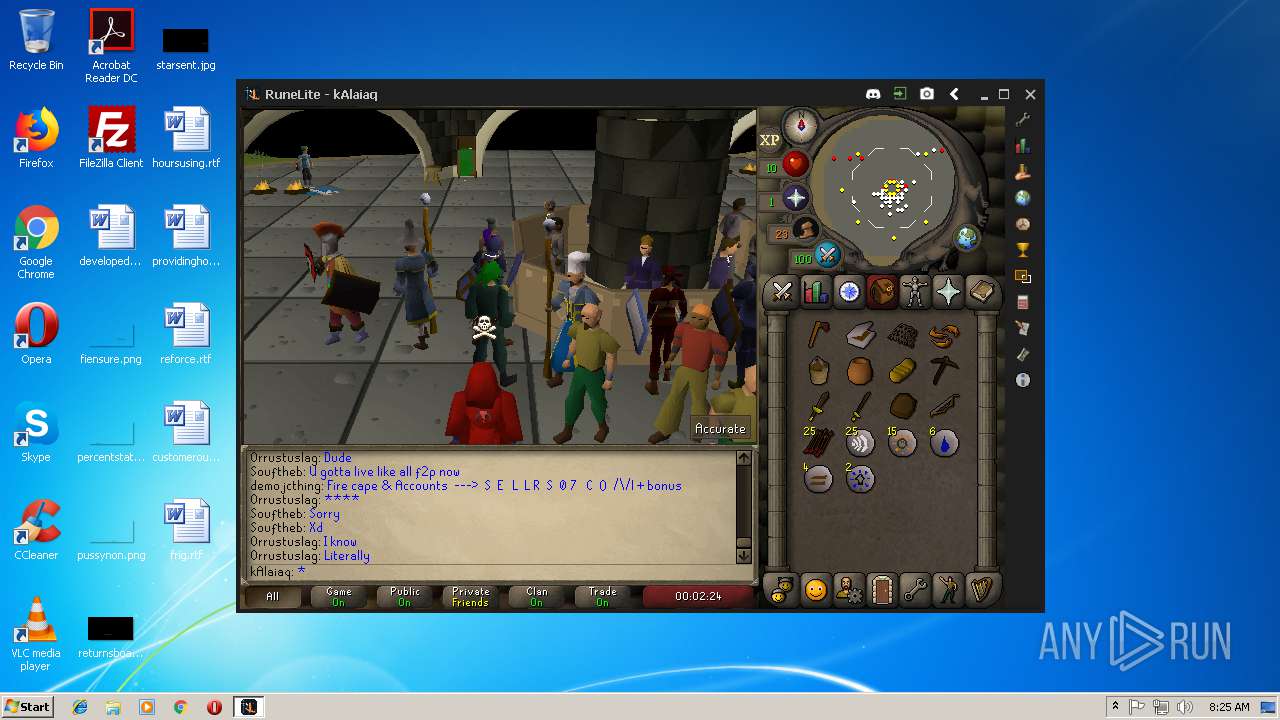
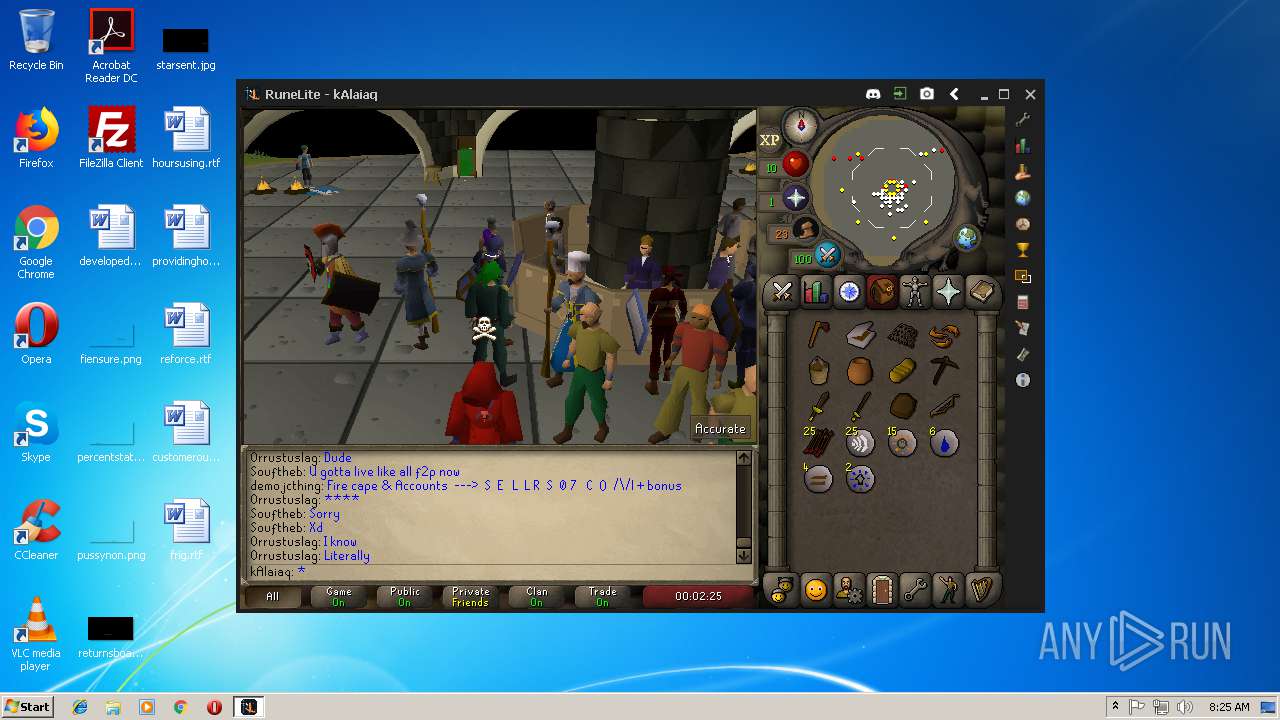
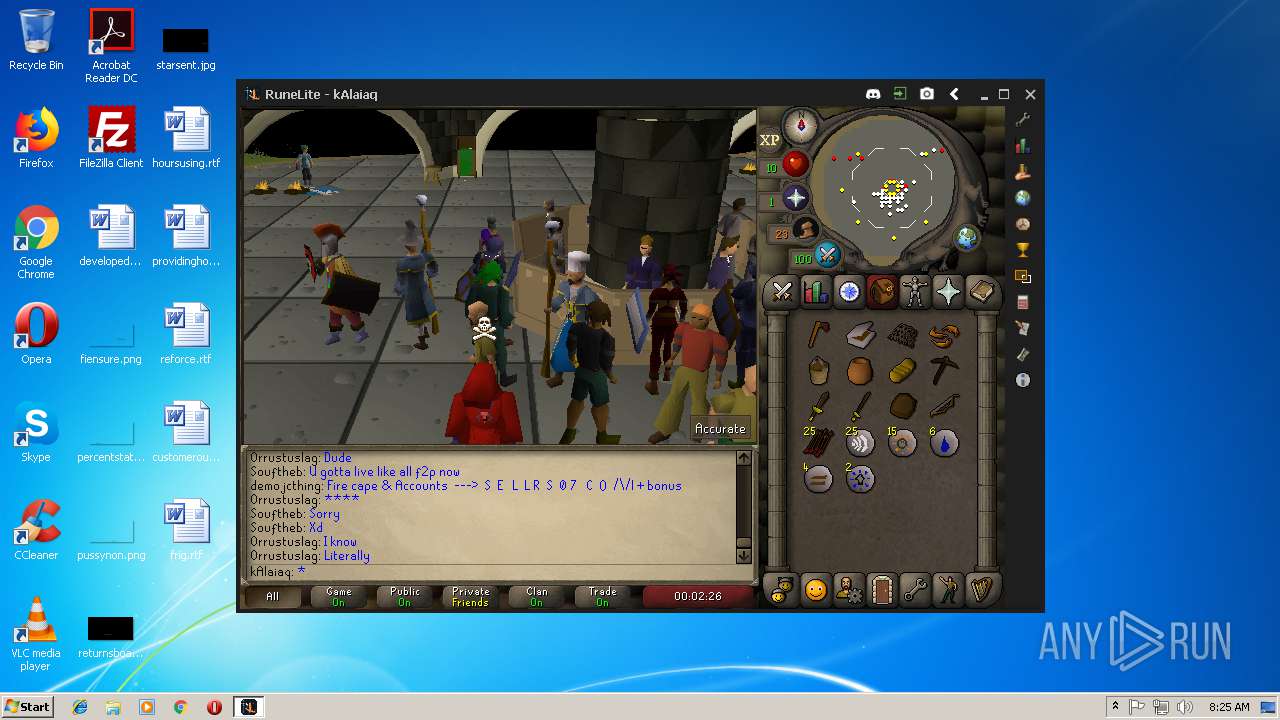
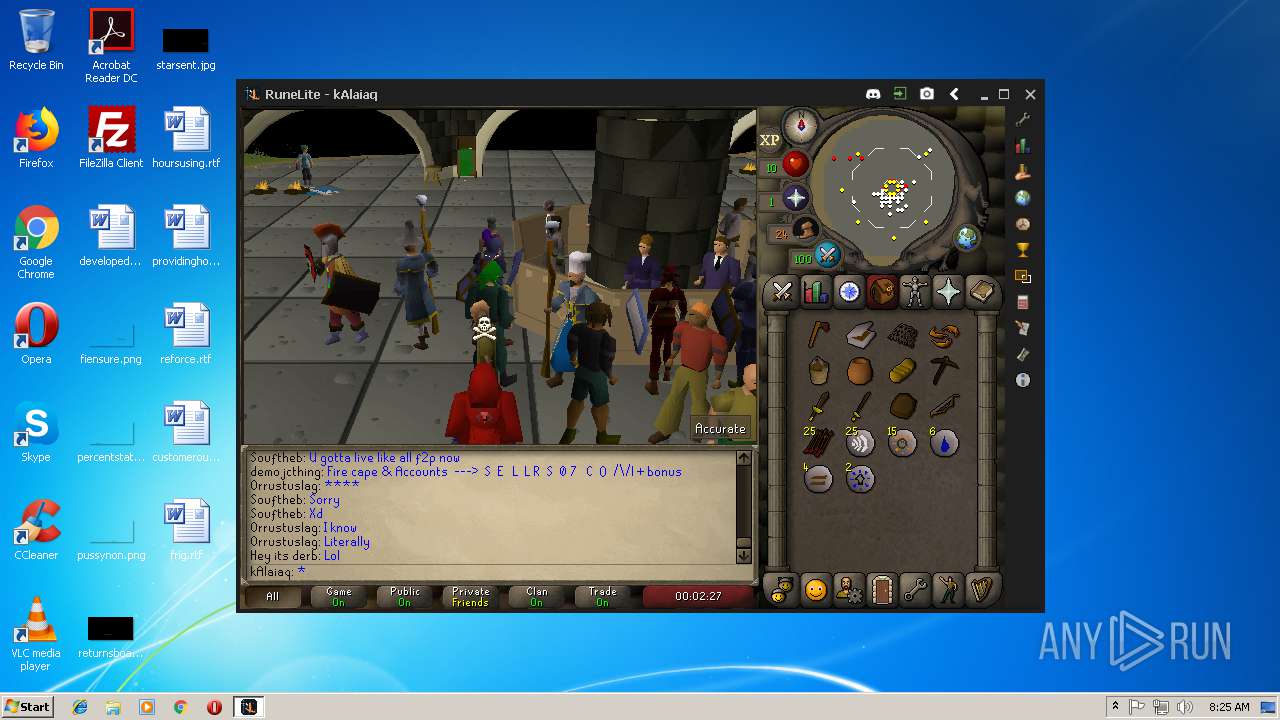
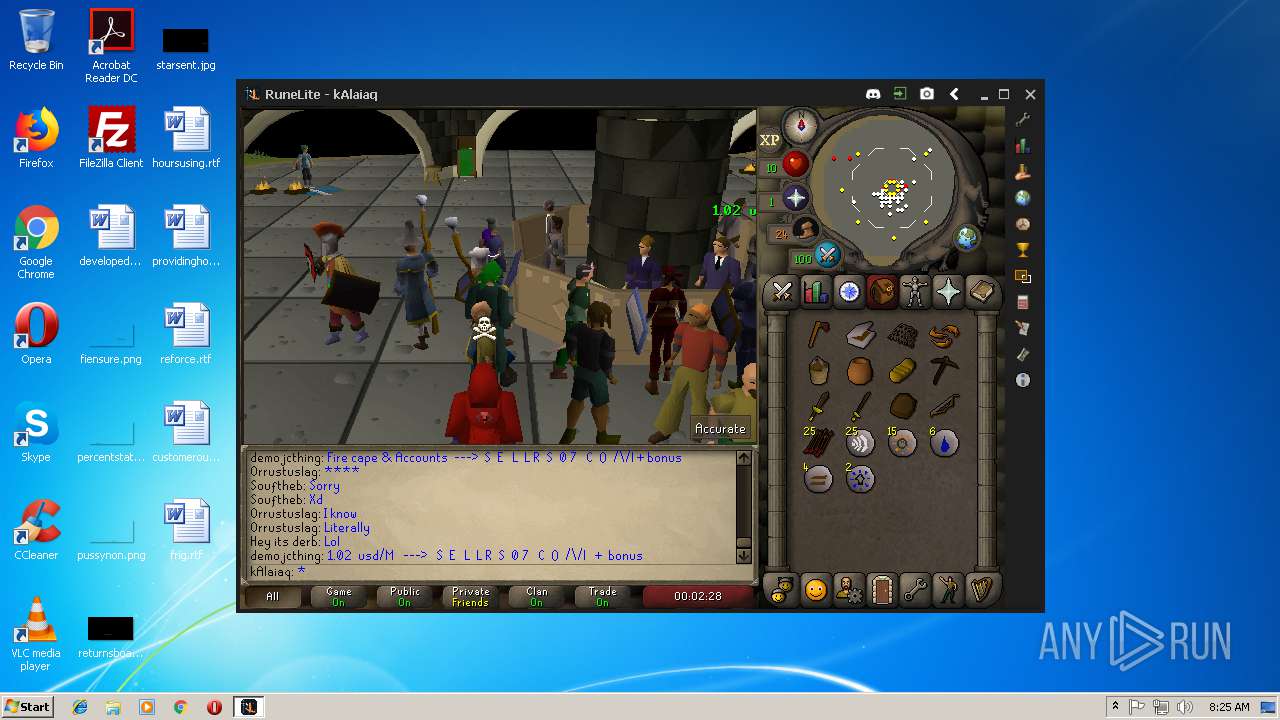
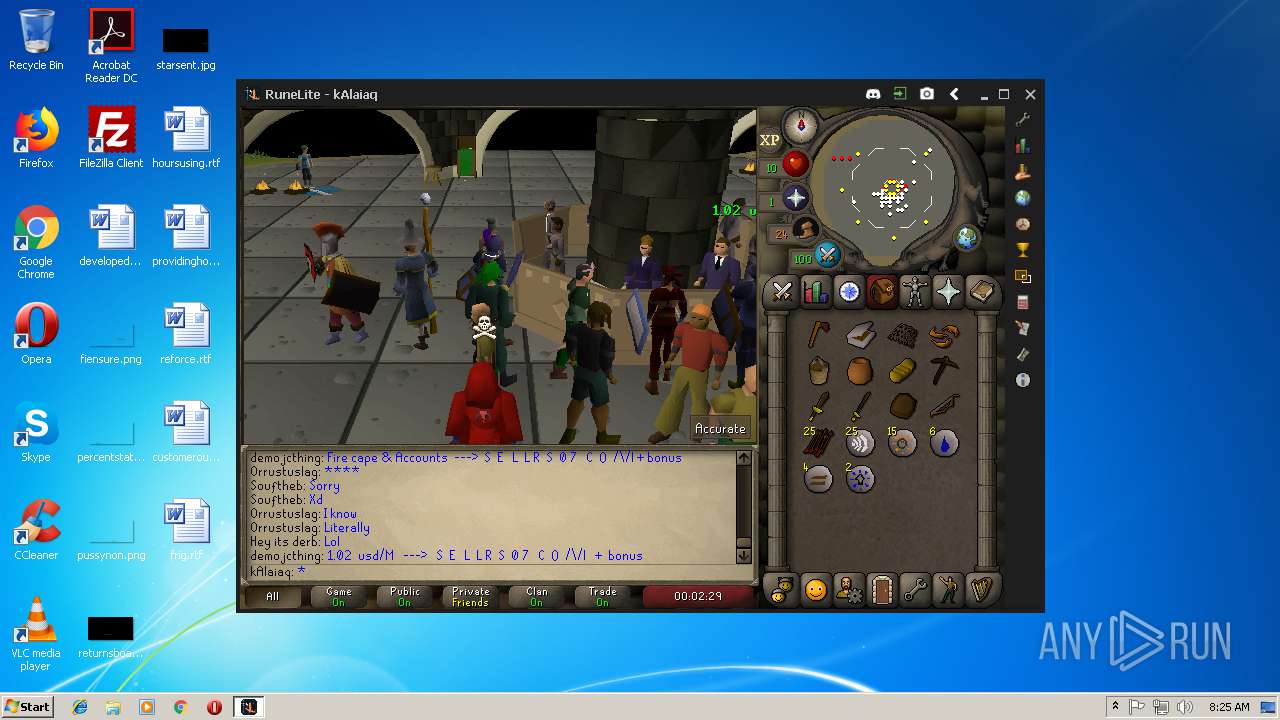
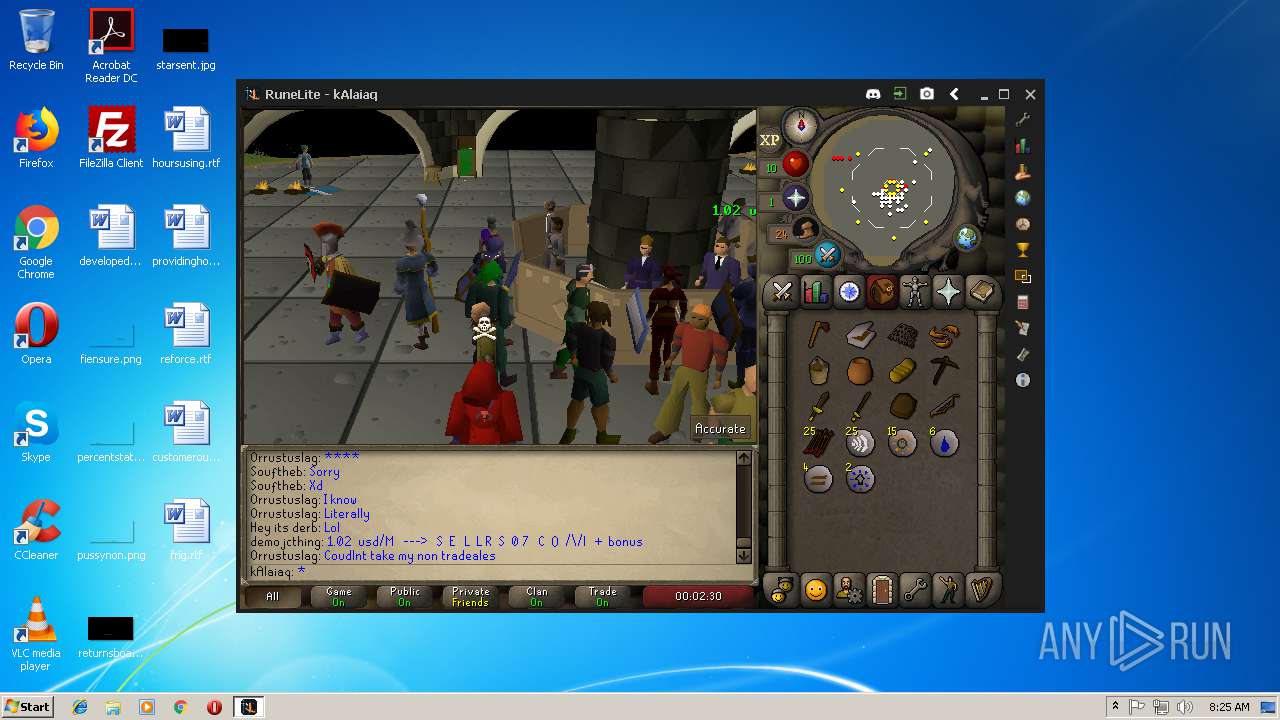
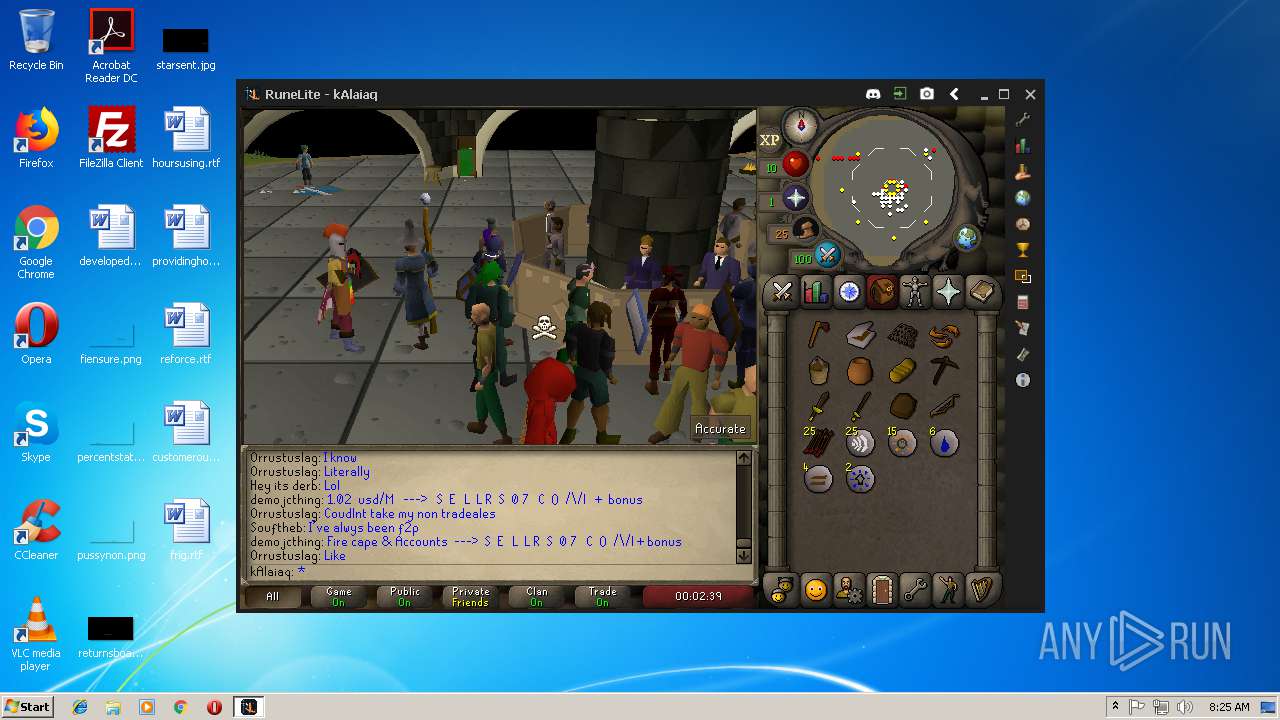
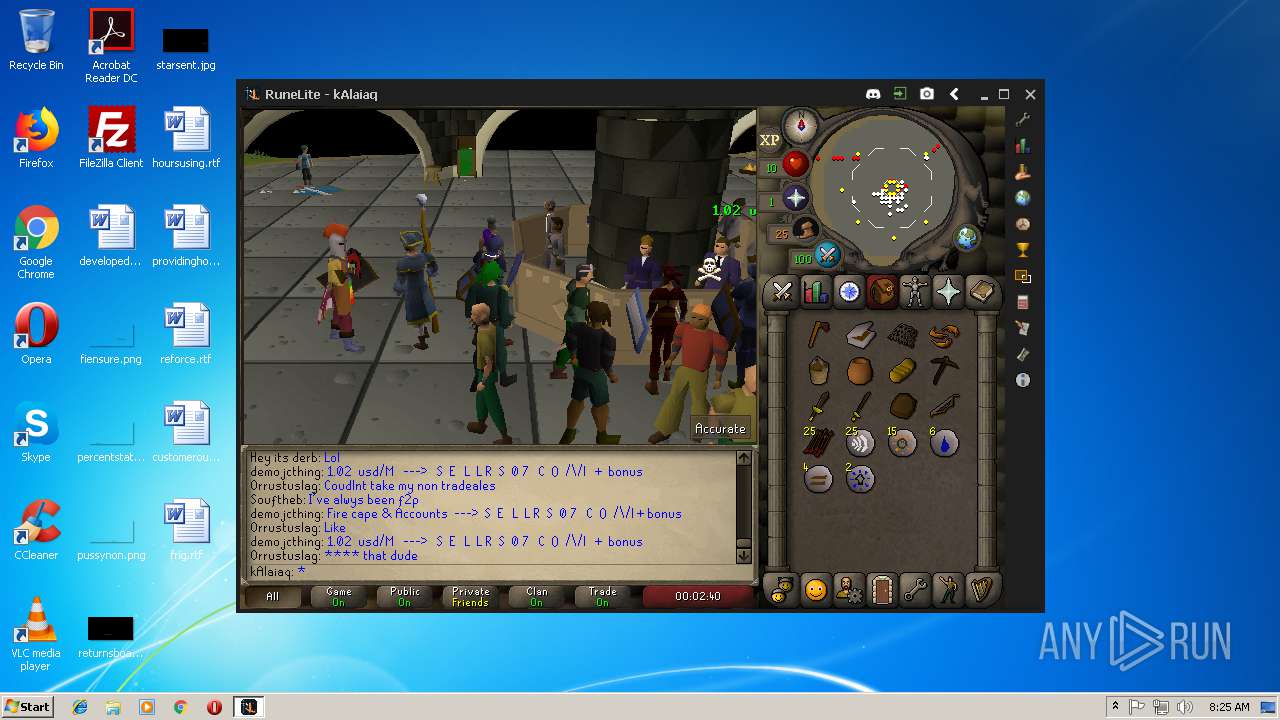
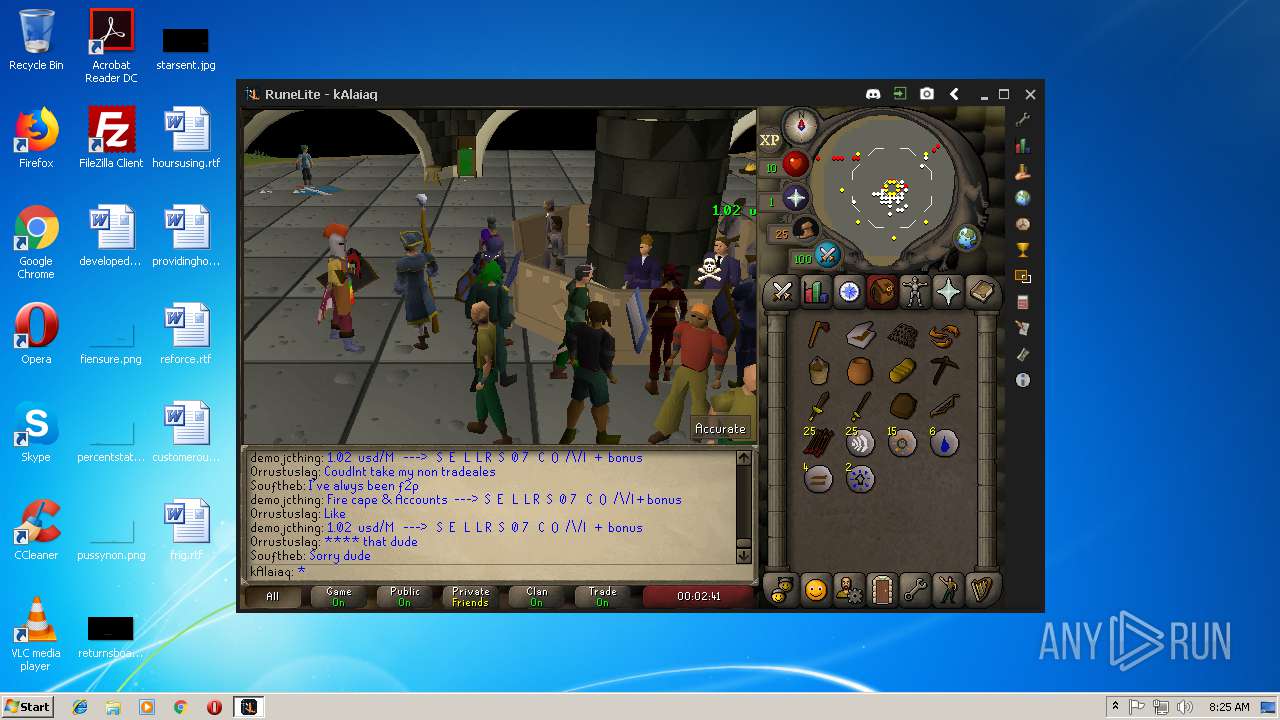
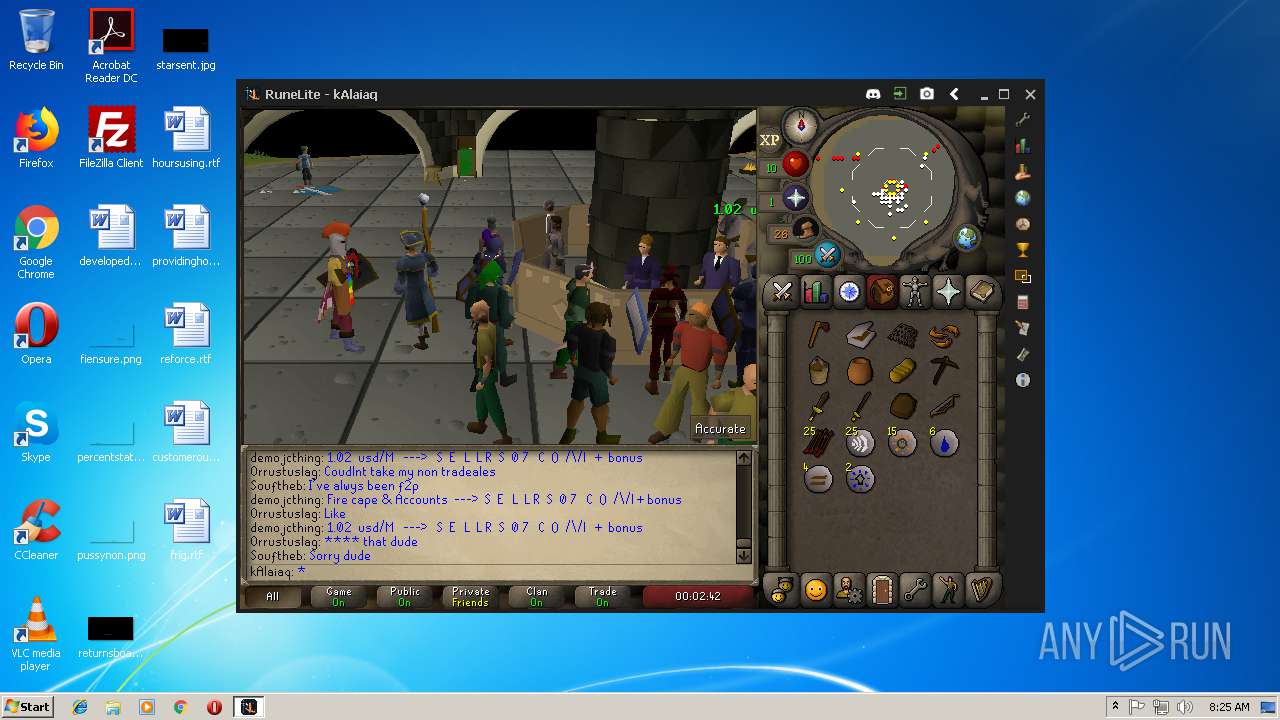
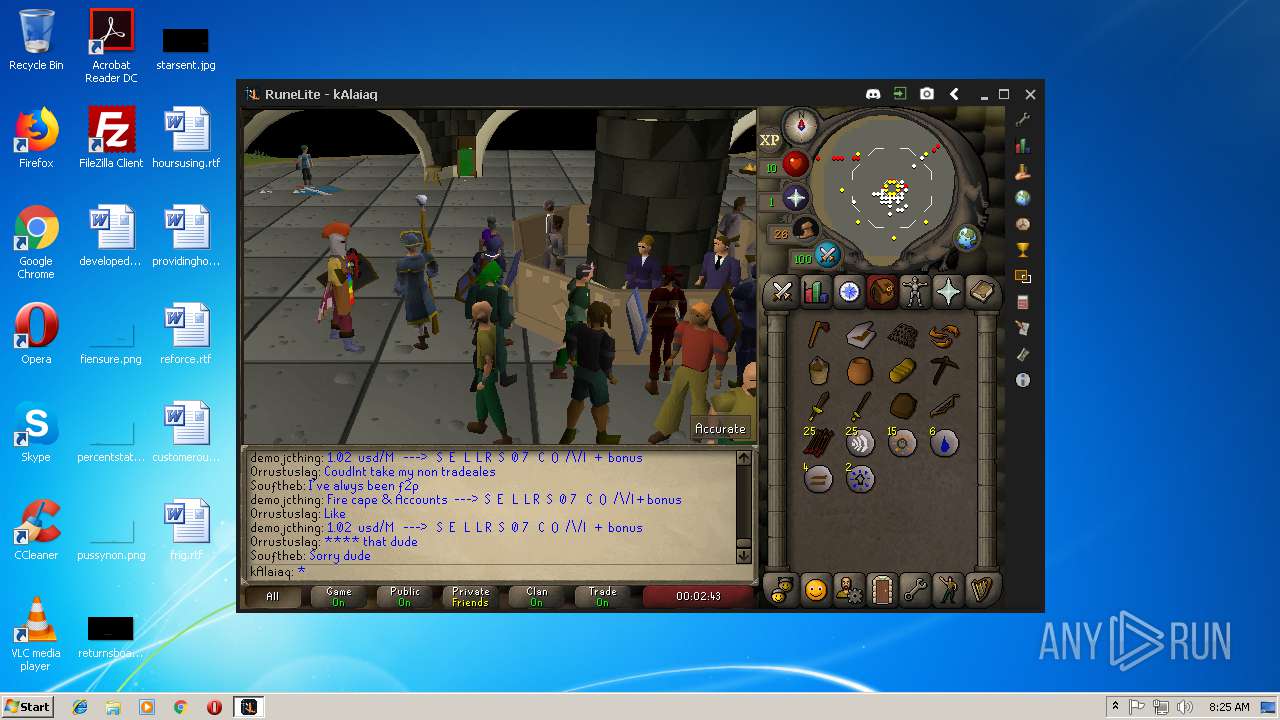
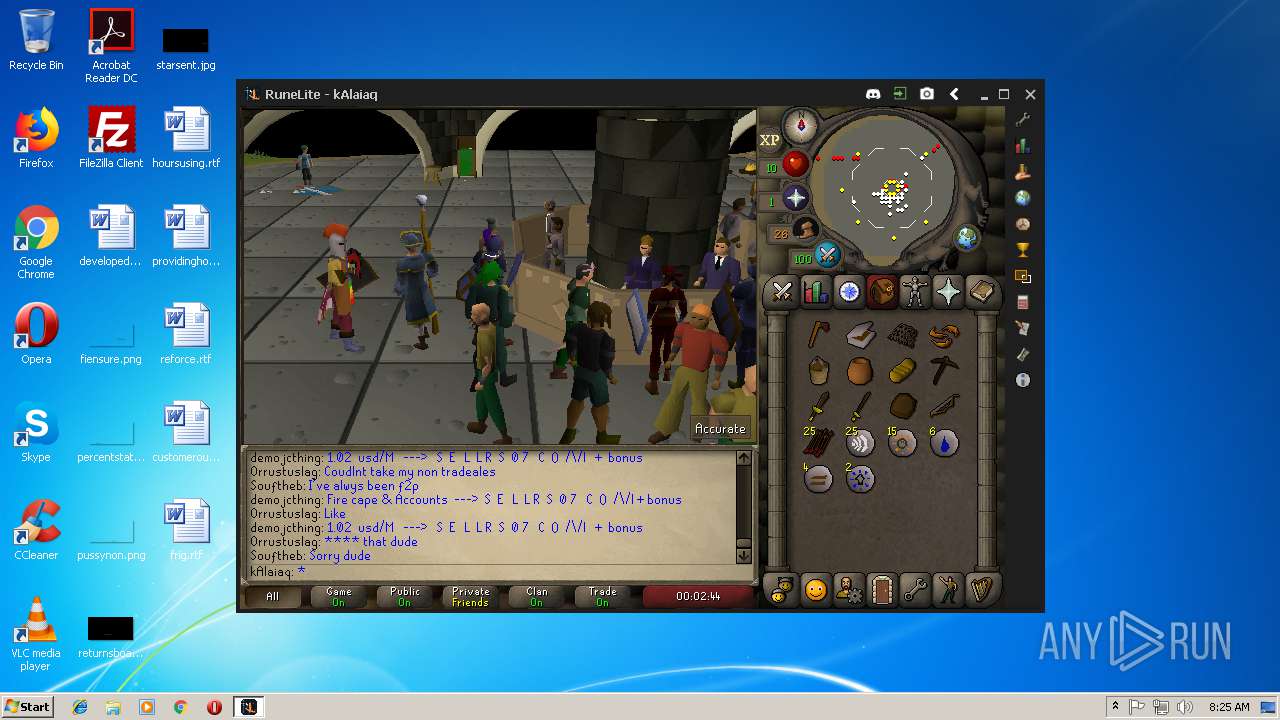
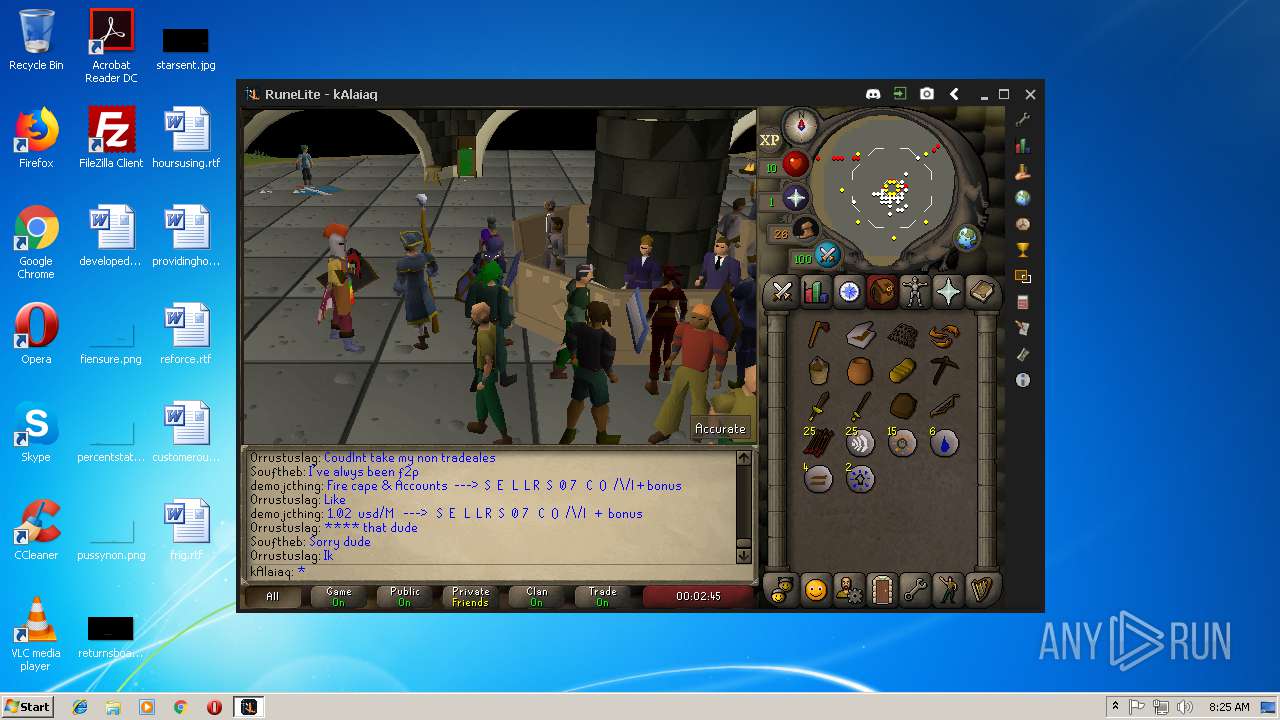
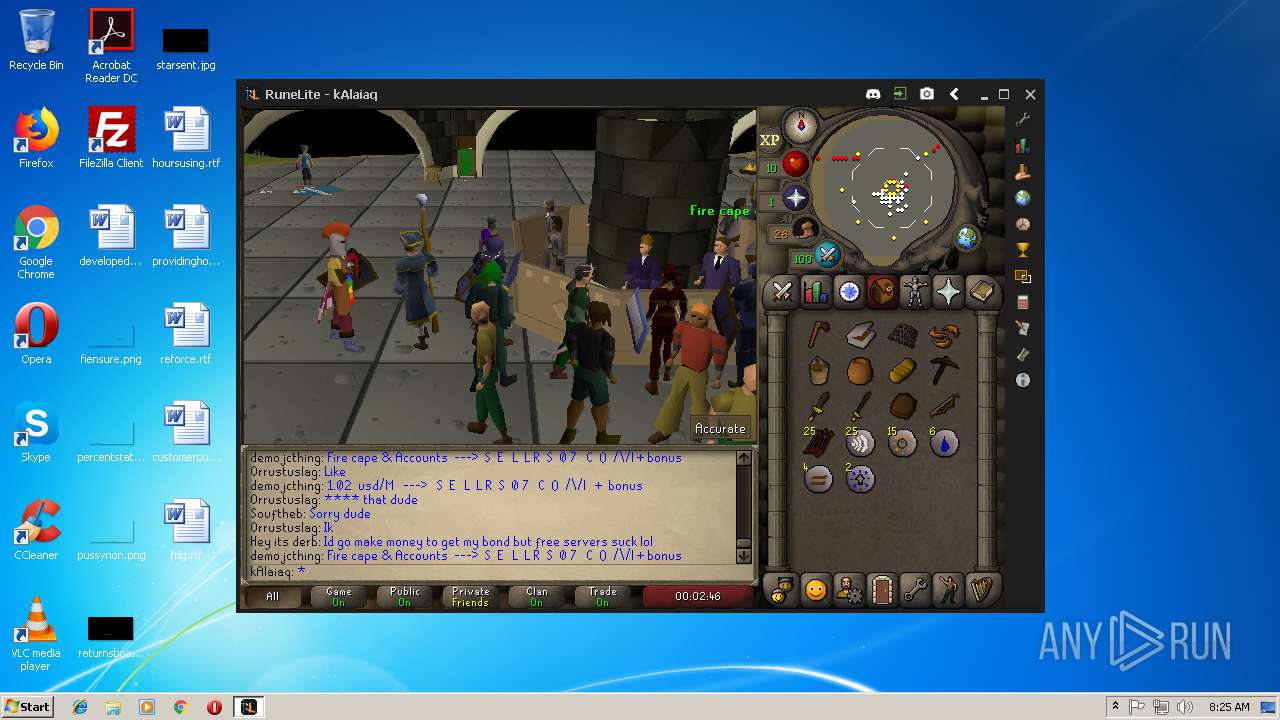
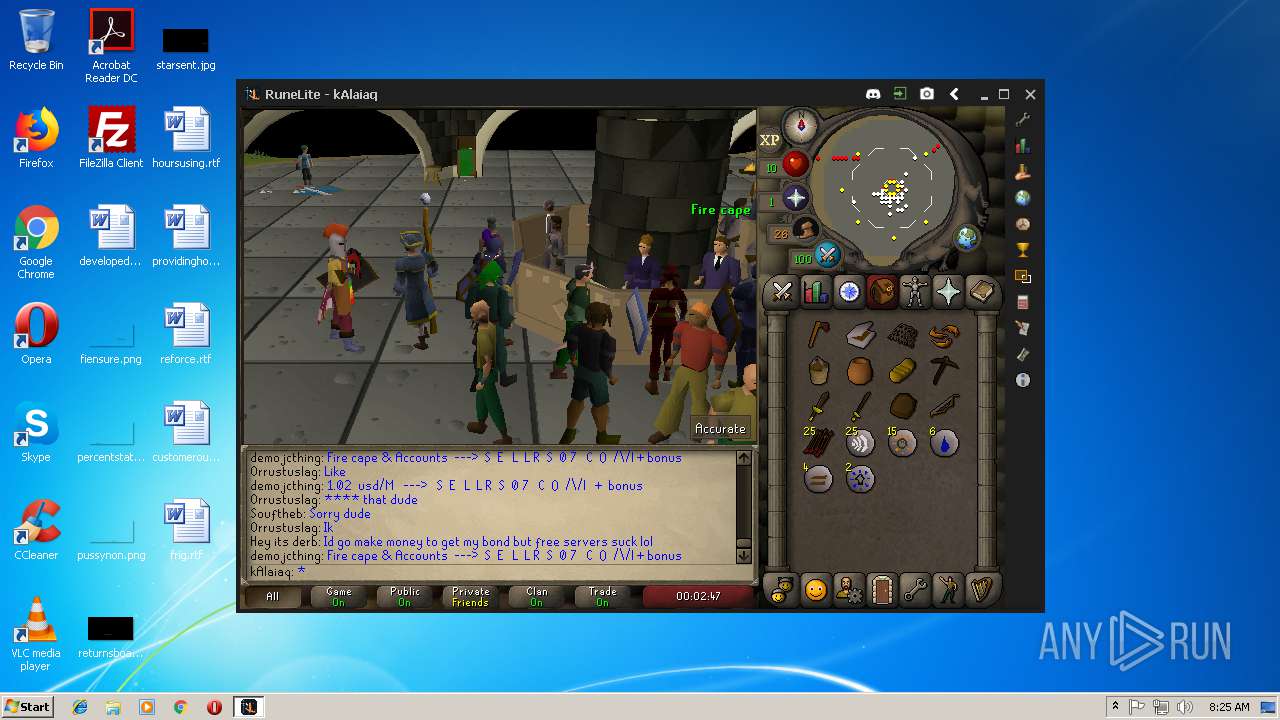
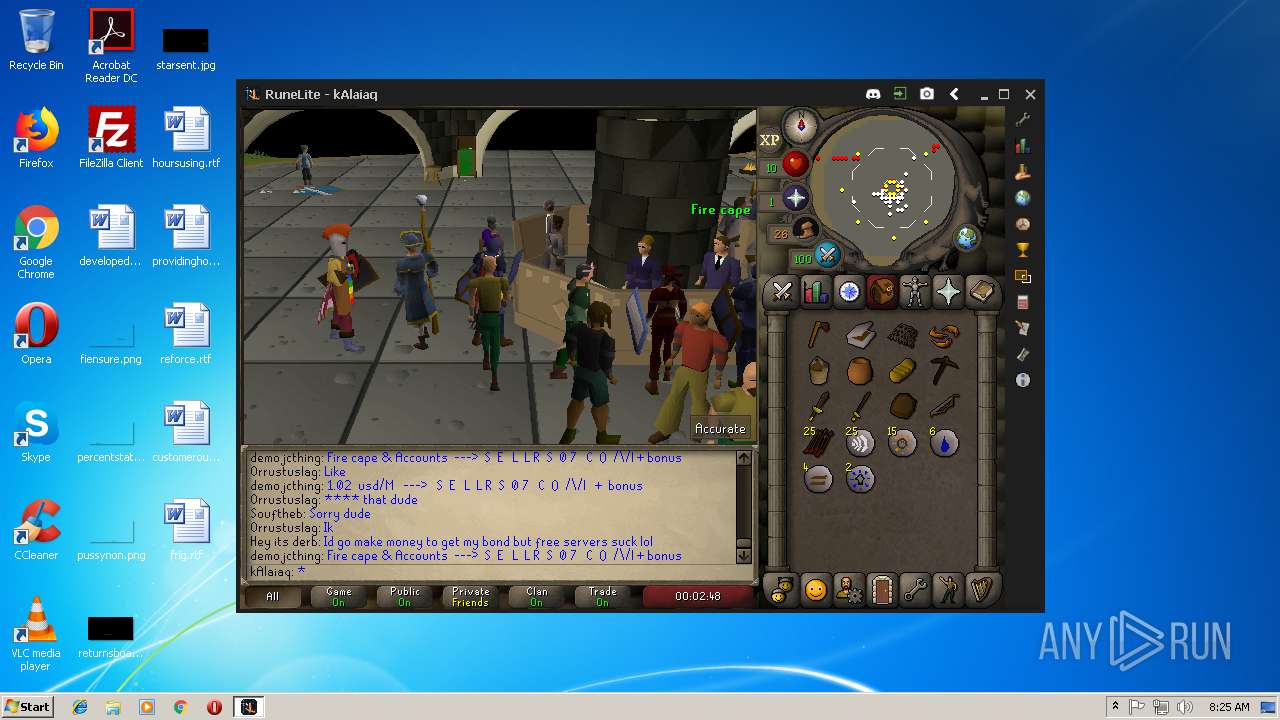
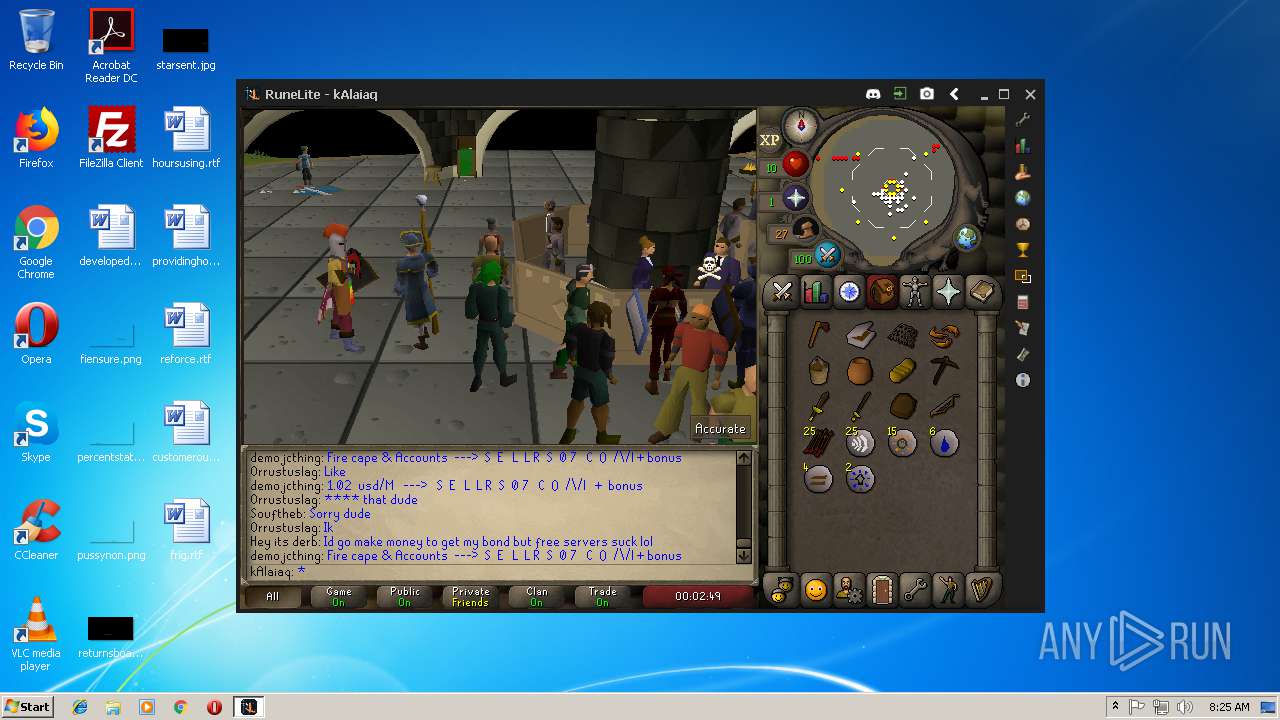
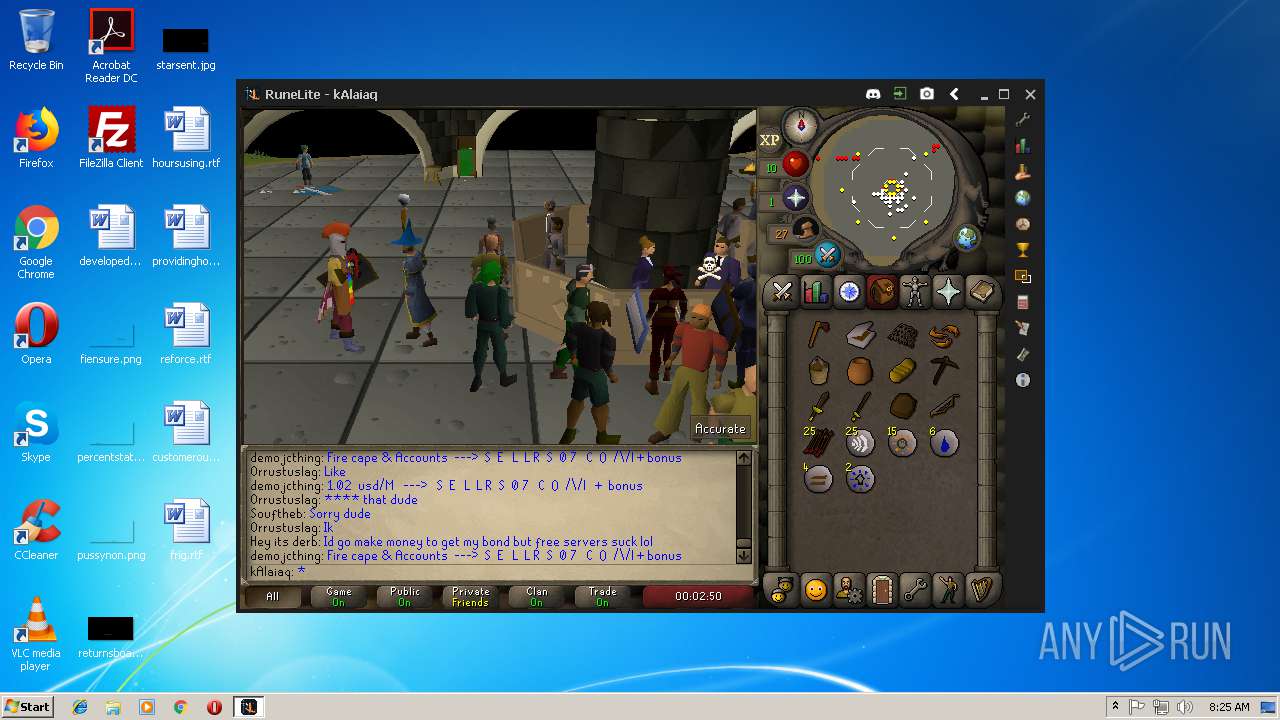
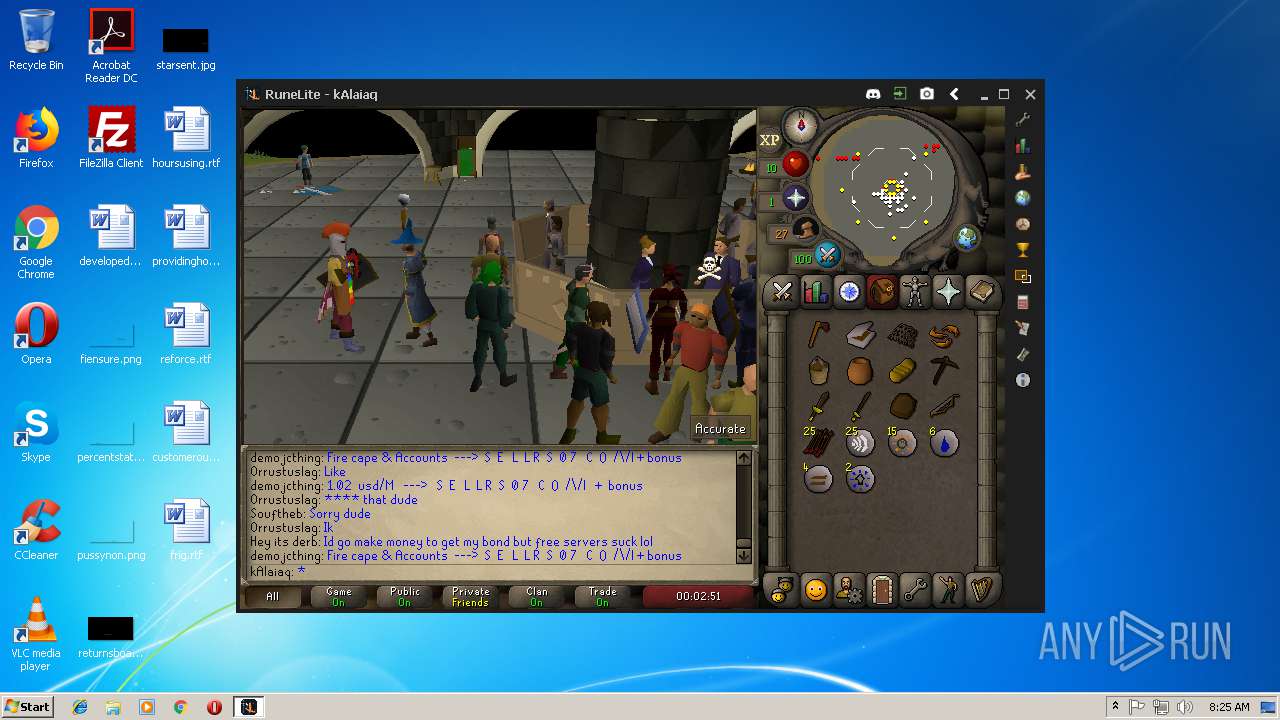
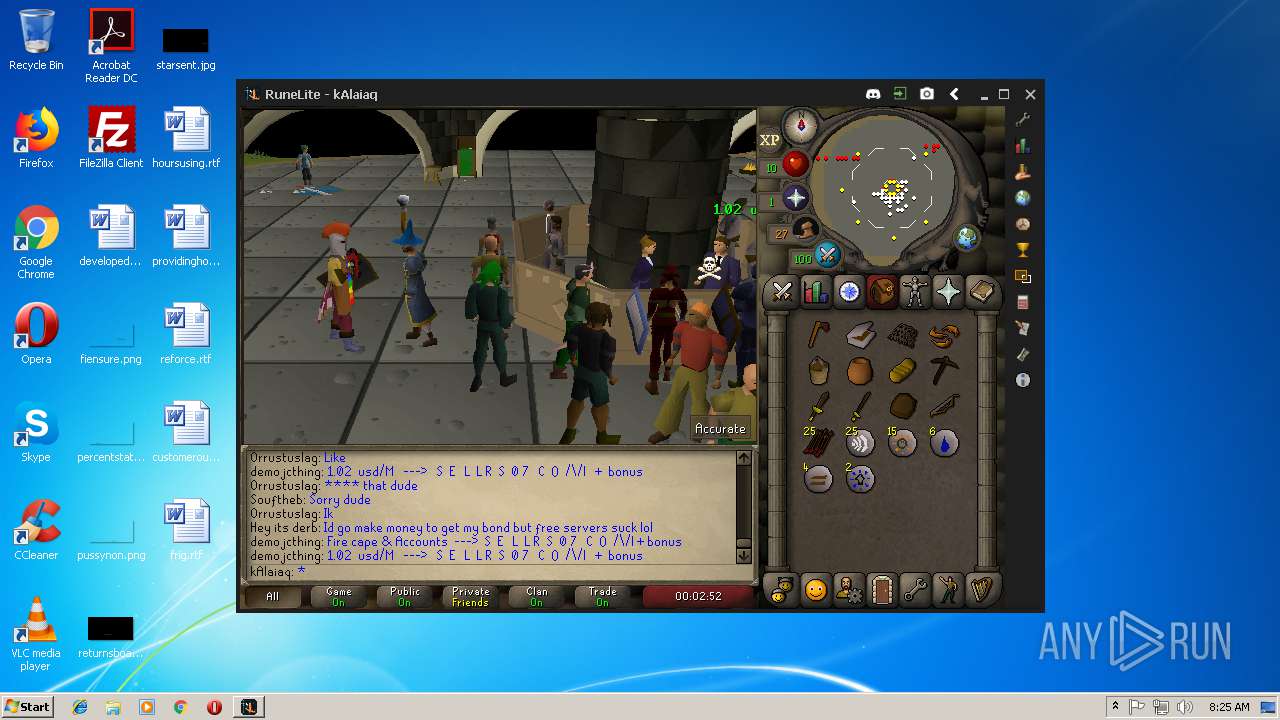
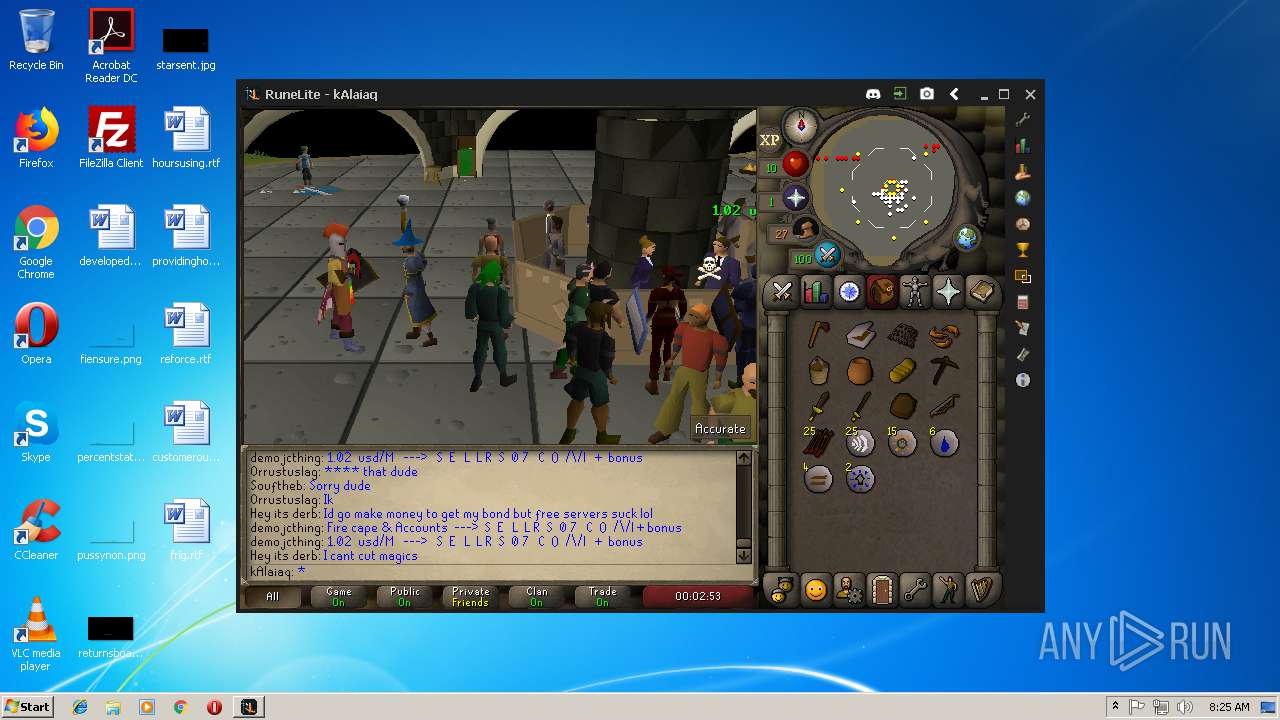
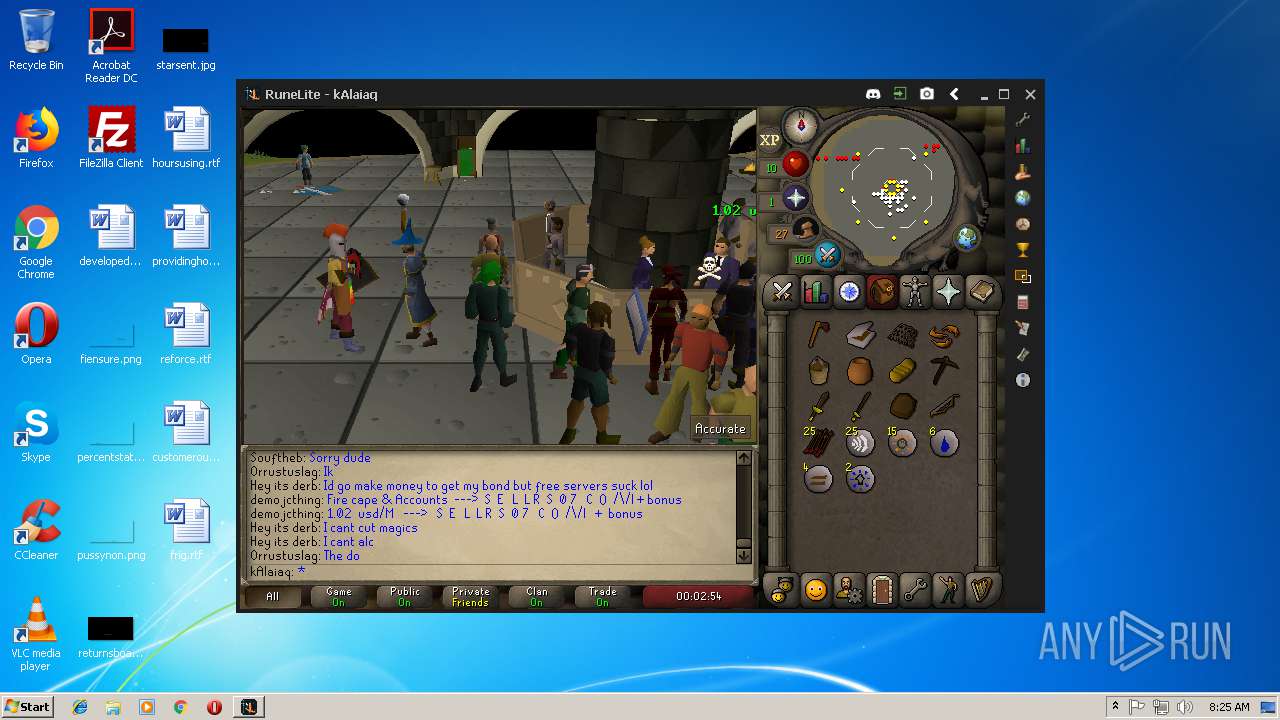
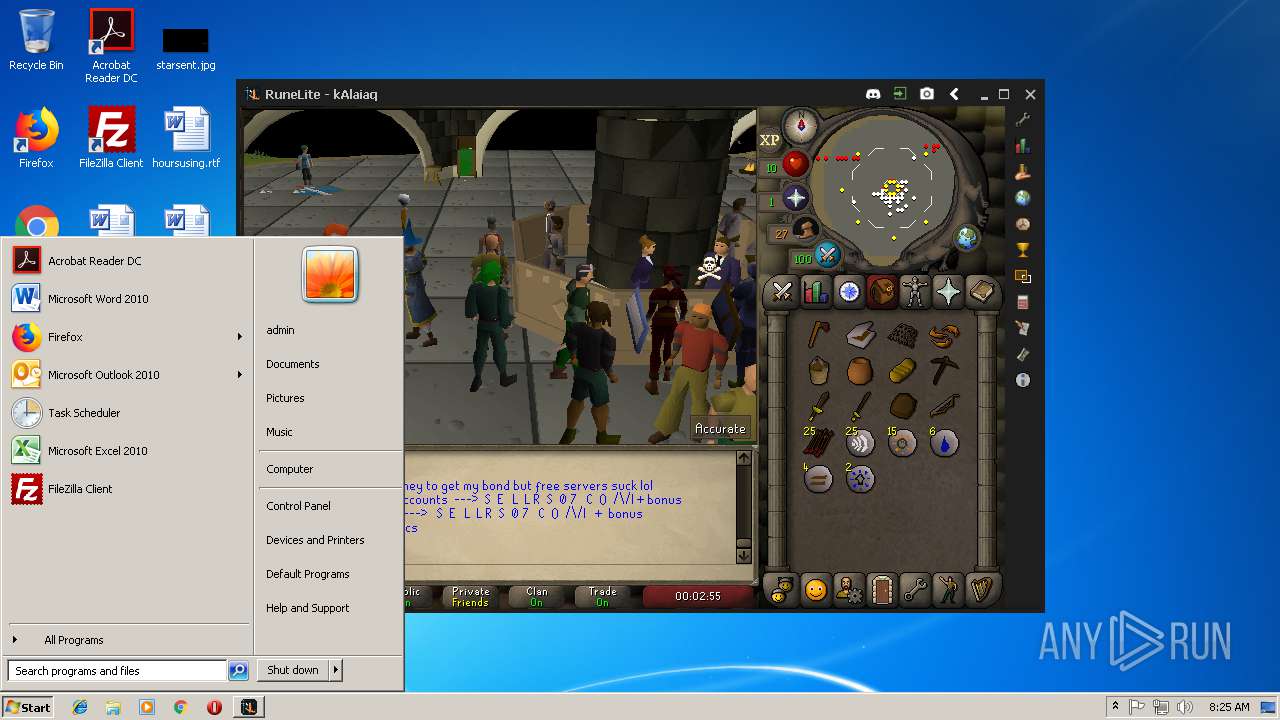
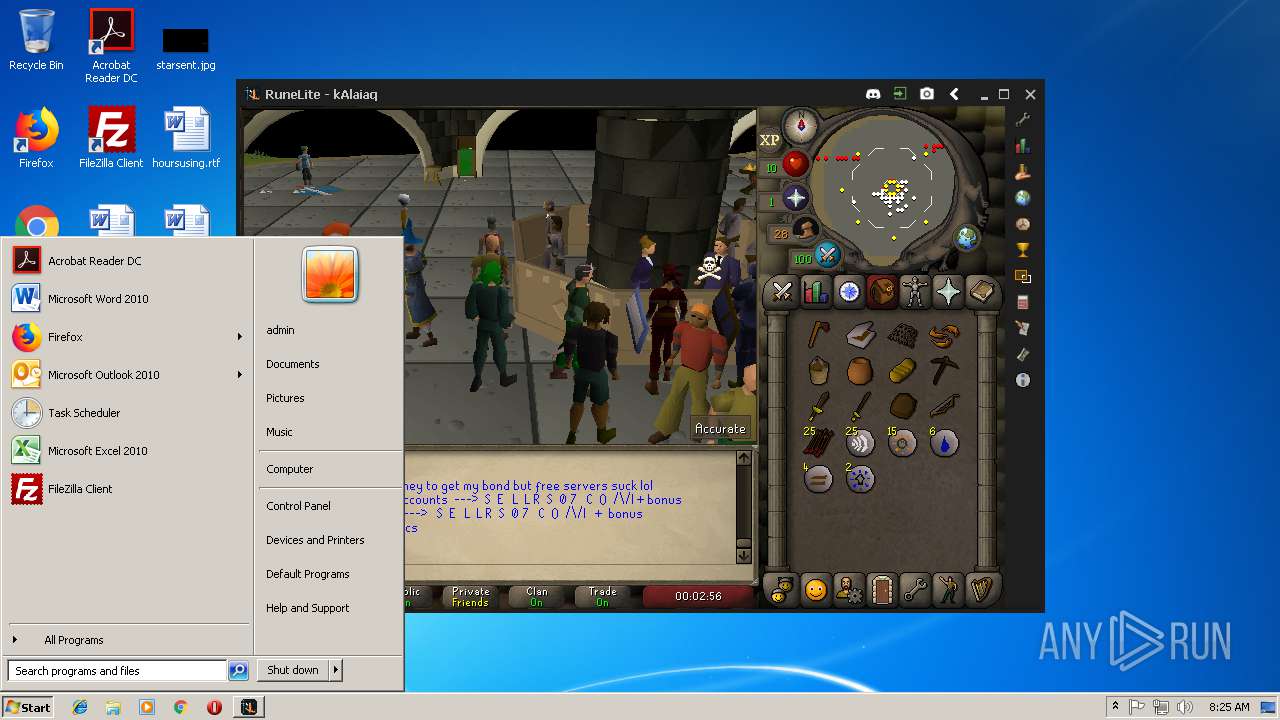
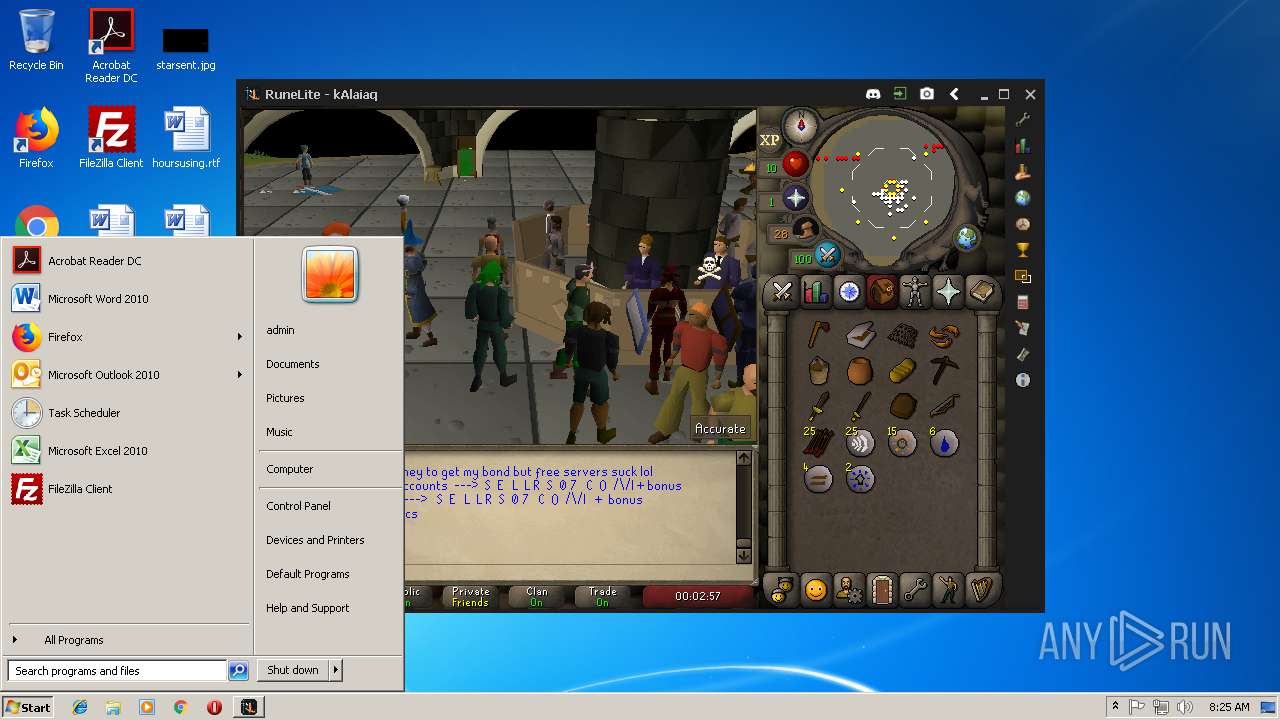
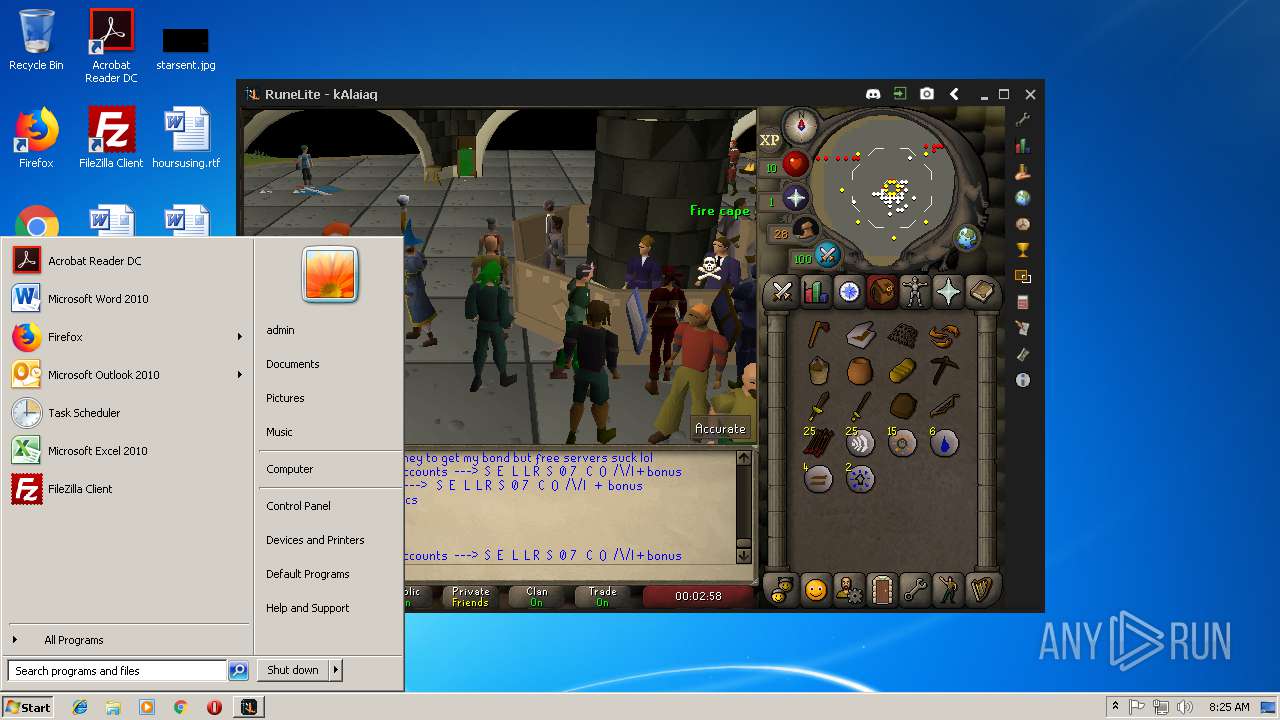
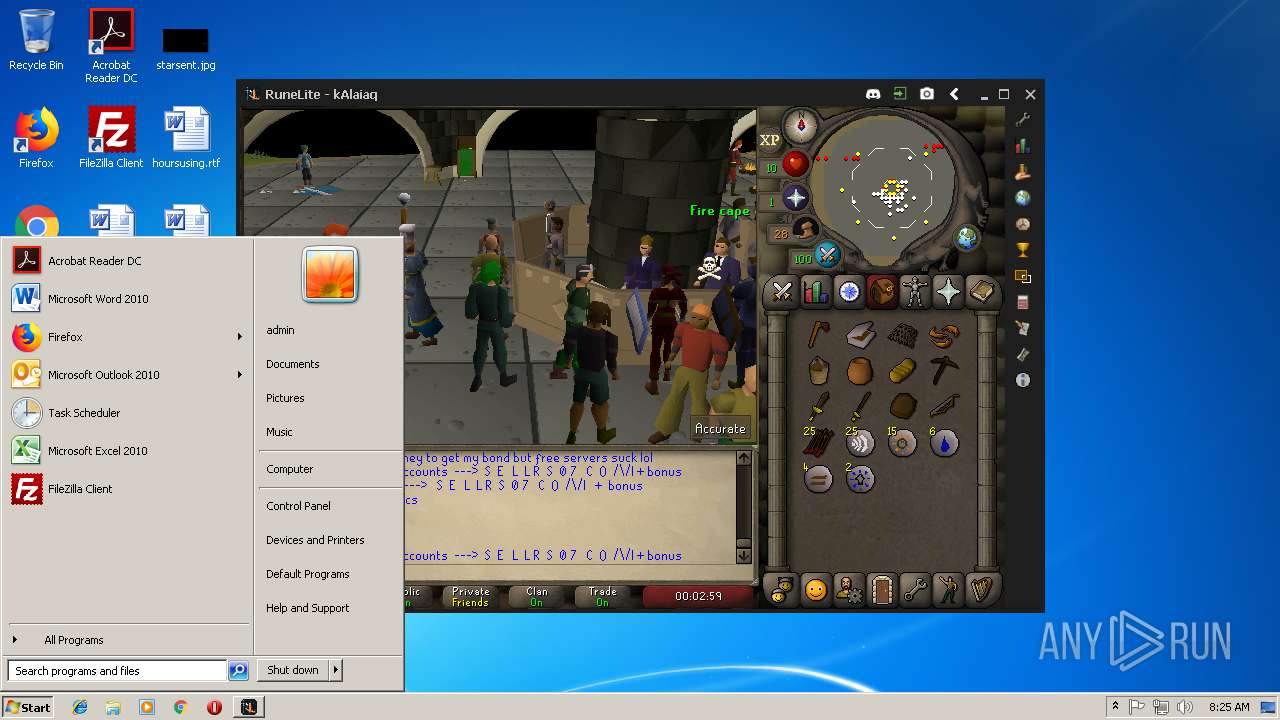
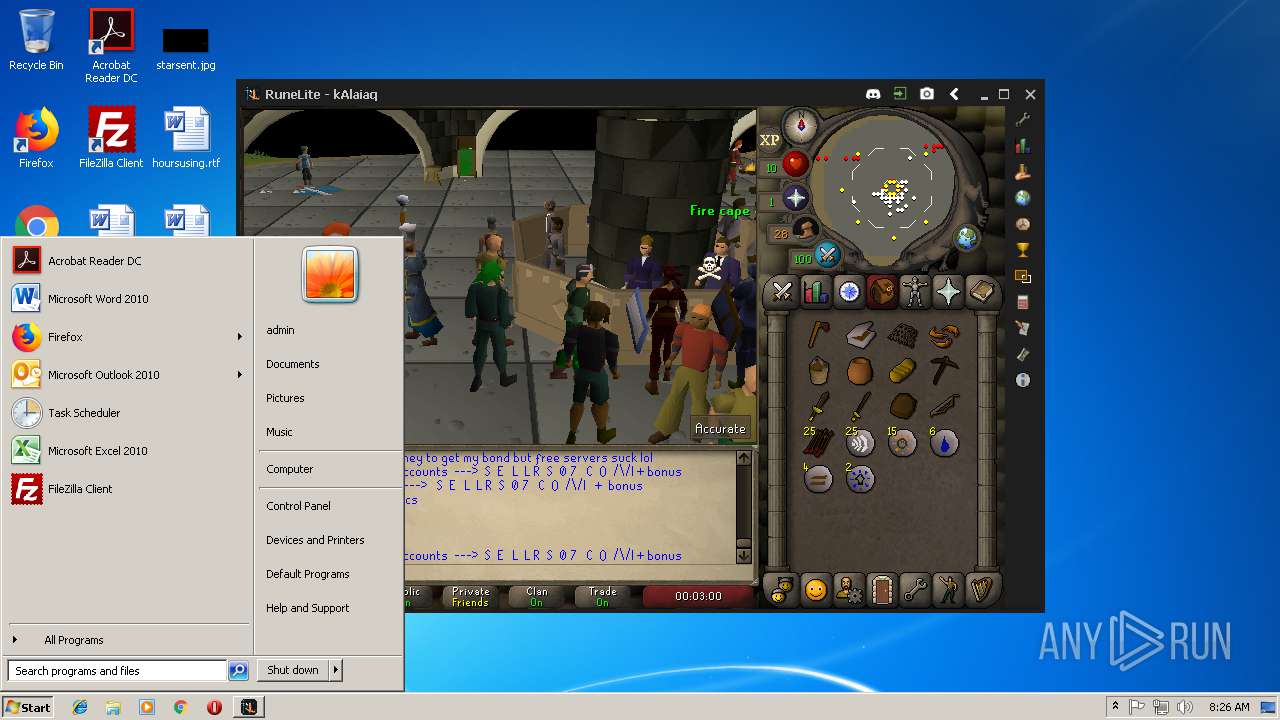
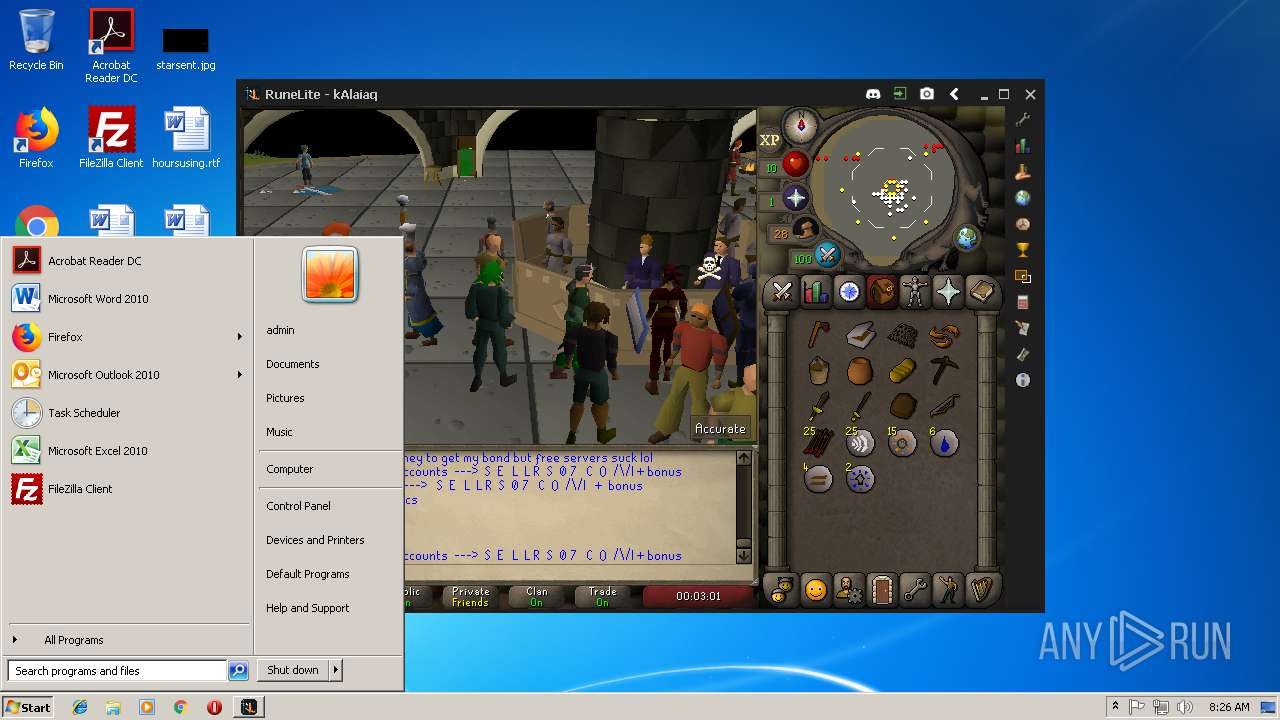
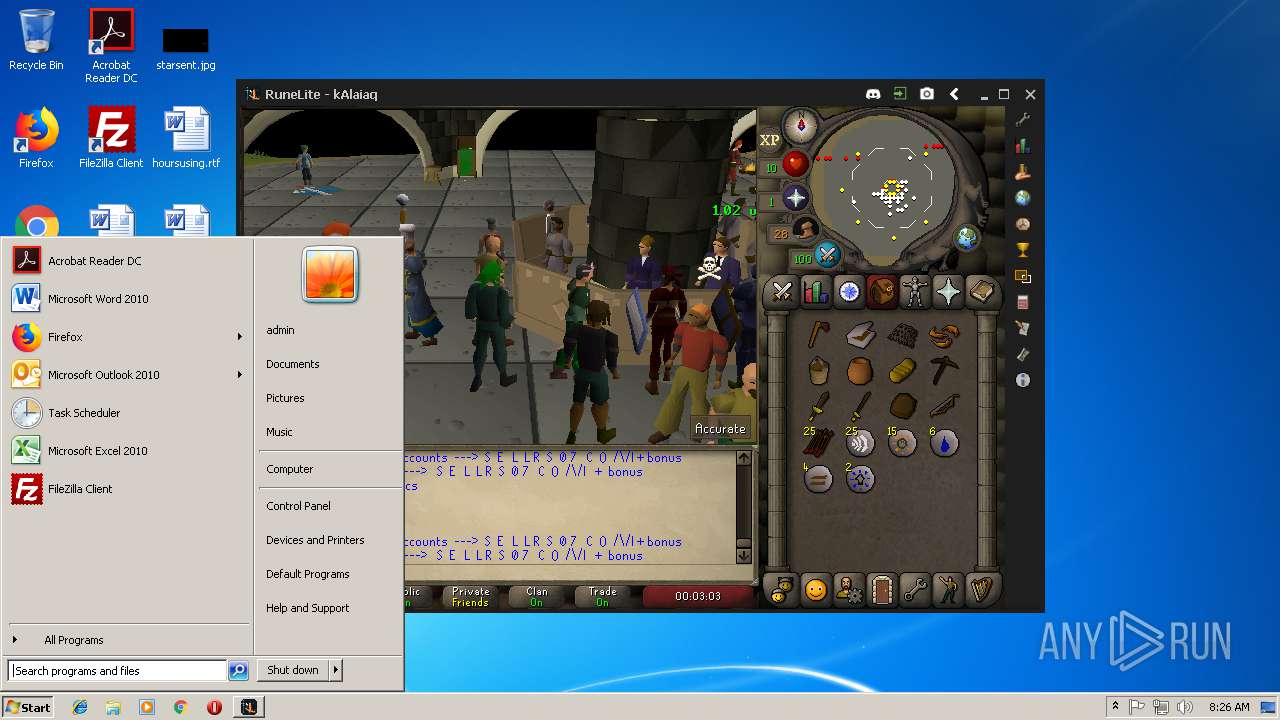
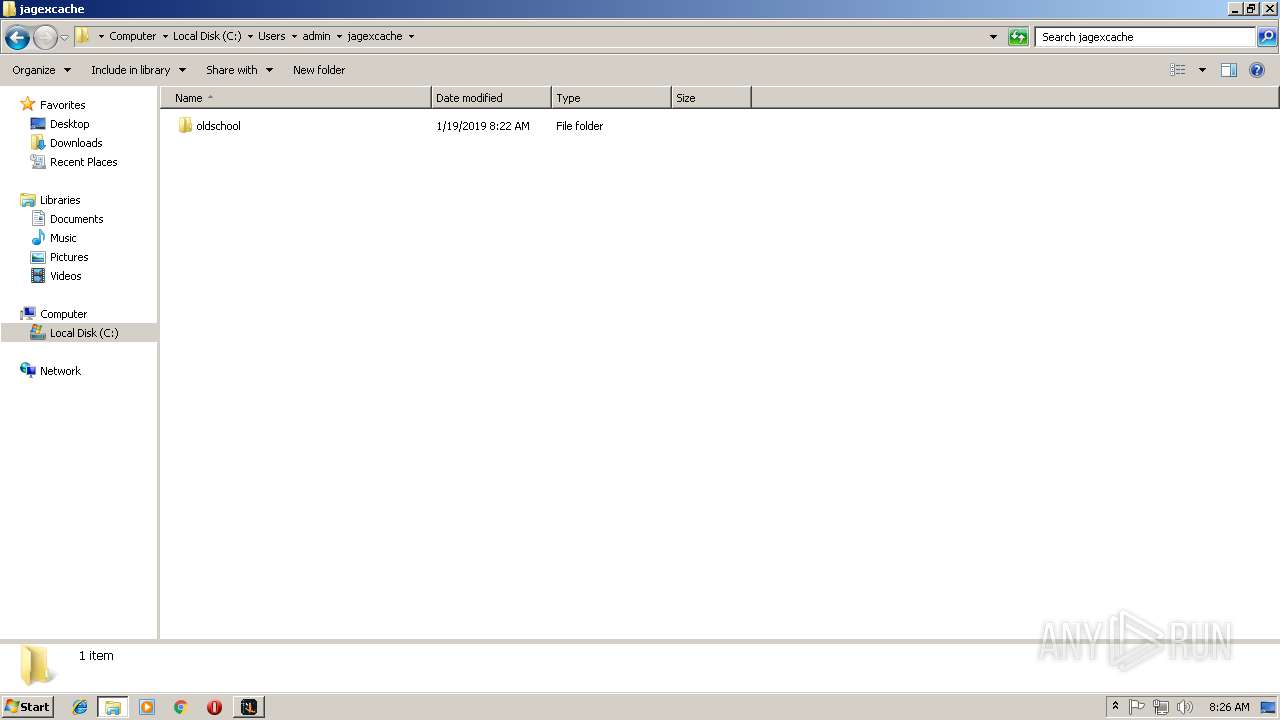
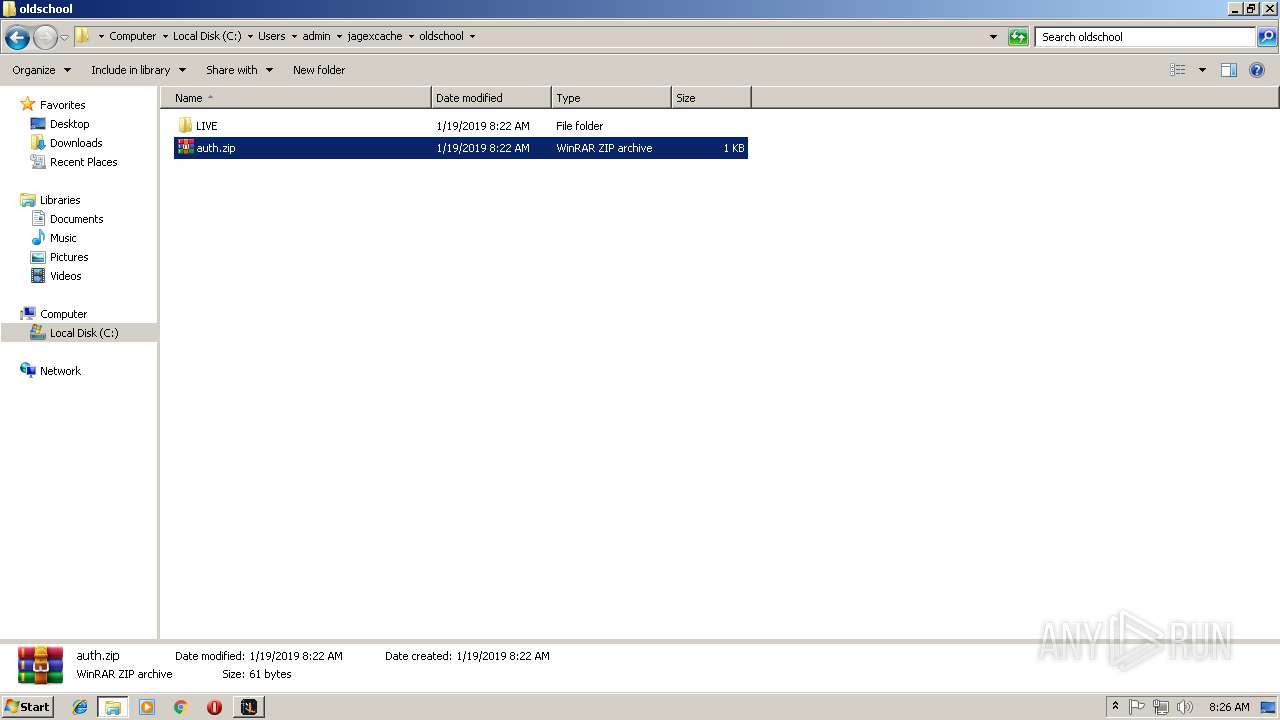
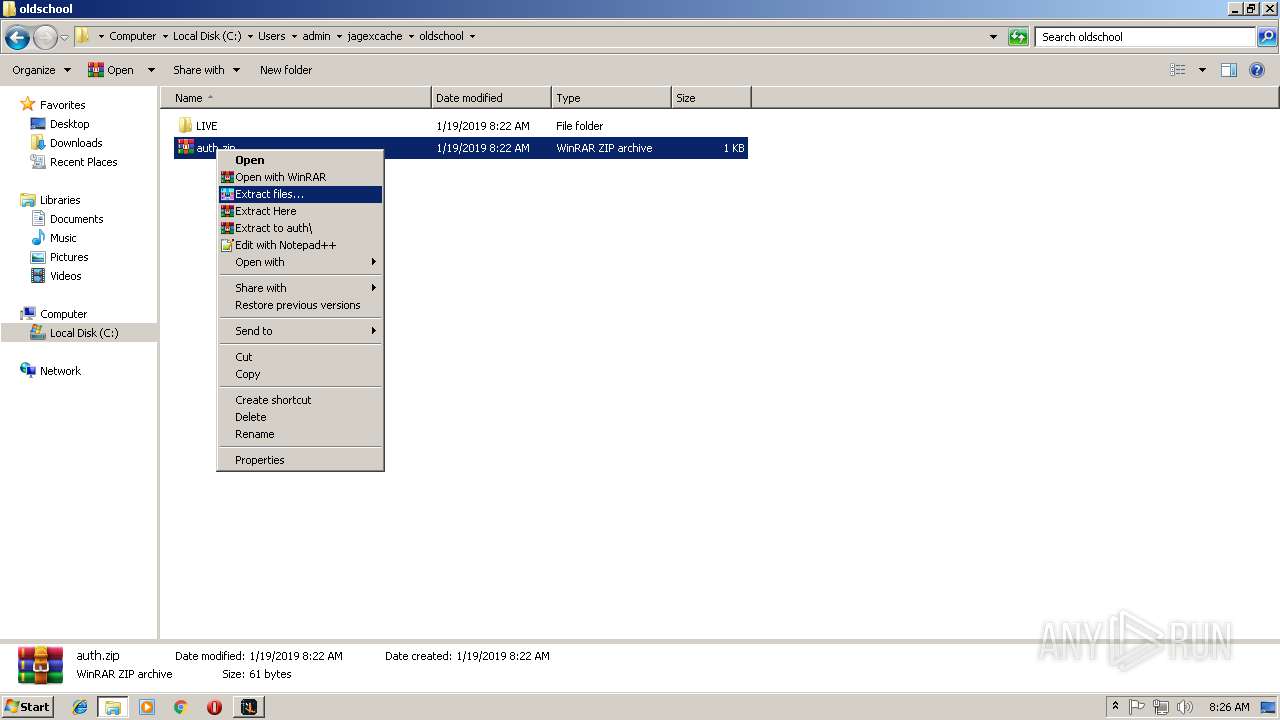
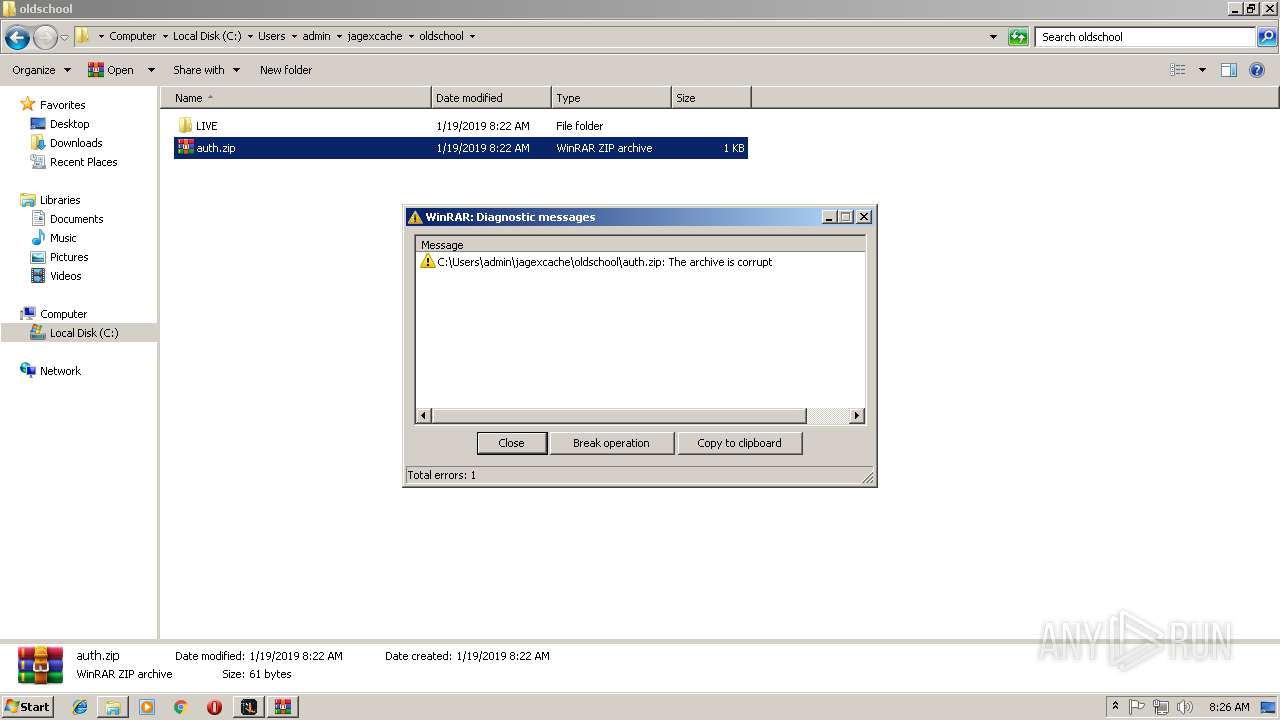
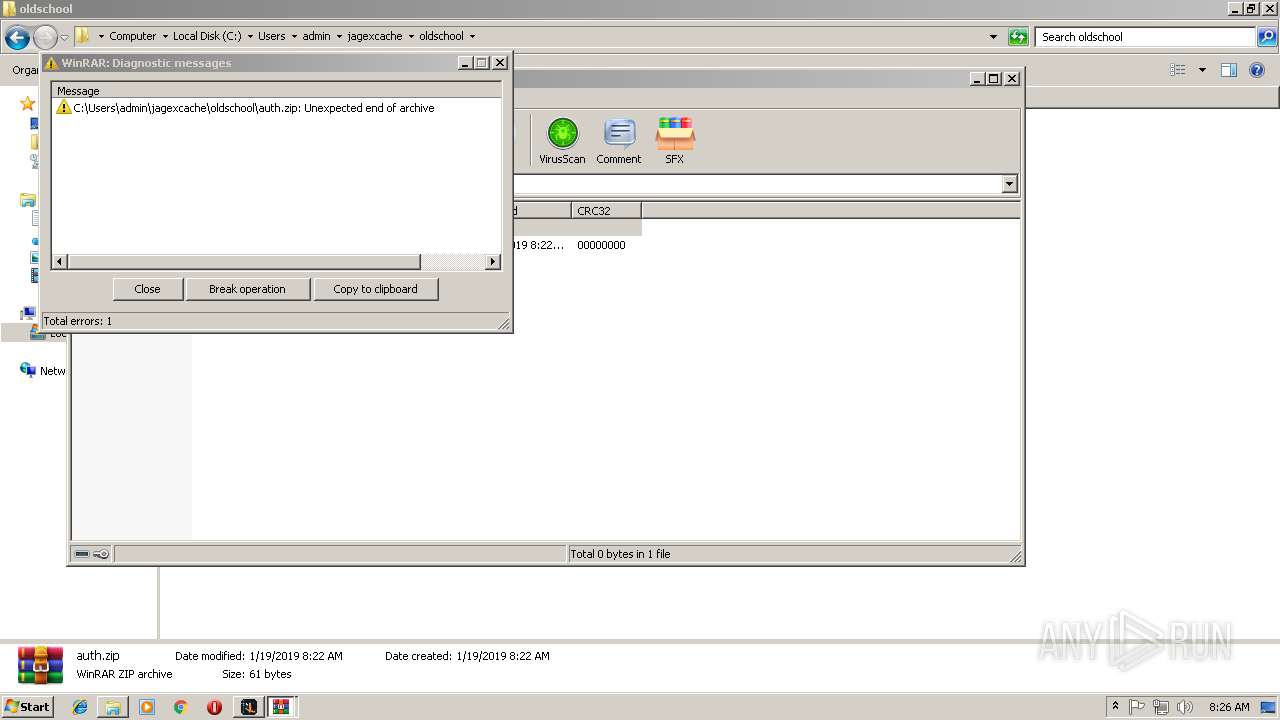
| File name: | RuneLite (2).jar |
| Full analysis: | https://app.any.run/tasks/15856cfa-039a-4a4c-b5e5-77f90193af55 |
| Verdict: | Suspicious activity |
| Analysis date: | January 19, 2019, 08:21:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/java-archive |
| File info: | Java archive data (JAR) |
| MD5: | C8CA478304067D62E8EAAAF40EB332D6 |
| SHA1: | 6F6B2AFD7B8CB9E11A854D35977C9ABB7A7A7891 |
| SHA256: | 84942A229379BCEF07AE9866453ABA20D9A0A7C481BF390FE810F809E2996D4A |
| SSDEEP: | 49152:/RrBhtvwa1jIlTvVZOg4D5ABA9YdQcr6knmm26Xifq:/PhhjoTdZO9i7BjHDyi |
MALICIOUS
Loads dropped or rewritten executable
- java.exe (PID: 3192)
SUSPICIOUS
Executes JAVA applets
- javaw.exe (PID: 3028)
Uses TASKLIST.EXE to query information about running processes
- java.exe (PID: 3192)
Creates files in the user directory
- java.exe (PID: 3192)
Modifies the open verb of a shell class
- java.exe (PID: 3192)
Starts CMD.EXE for commands execution
- java.exe (PID: 3192)
Executable content was dropped or overwritten
- java.exe (PID: 3192)
Connects to unusual port
- java.exe (PID: 3192)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .maff | | | Mozilla Archive Format (gen) (63.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (36.3) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0808 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2018:12:13 18:02:03 |
| ZipCRC: | 0xaf77355c |
| ZipCompressedSize: | 120 |
| ZipUncompressedSize: | 139 |
| ZipFileName: | META-INF/MANIFEST.MF |
Total processes
47
Monitored processes
8
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2092 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\jagexcache\oldschool\auth.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2140 | C:\Windows\system32\cmd.exe /c WMIC COMPUTERSYSTEM GET MODEL | C:\Windows\system32\cmd.exe | — | java.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2272 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\jagexcache\oldschool\auth.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2572 | WMIC COMPUTERSYSTEM GET MODEL | C:\Windows\System32\Wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2836 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\jagexcache\oldschool\auth.zip" C:\Users\admin\jagexcache\oldschool\auth\ | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 3 Version: 5.60.0 Modules
| |||||||||||||||
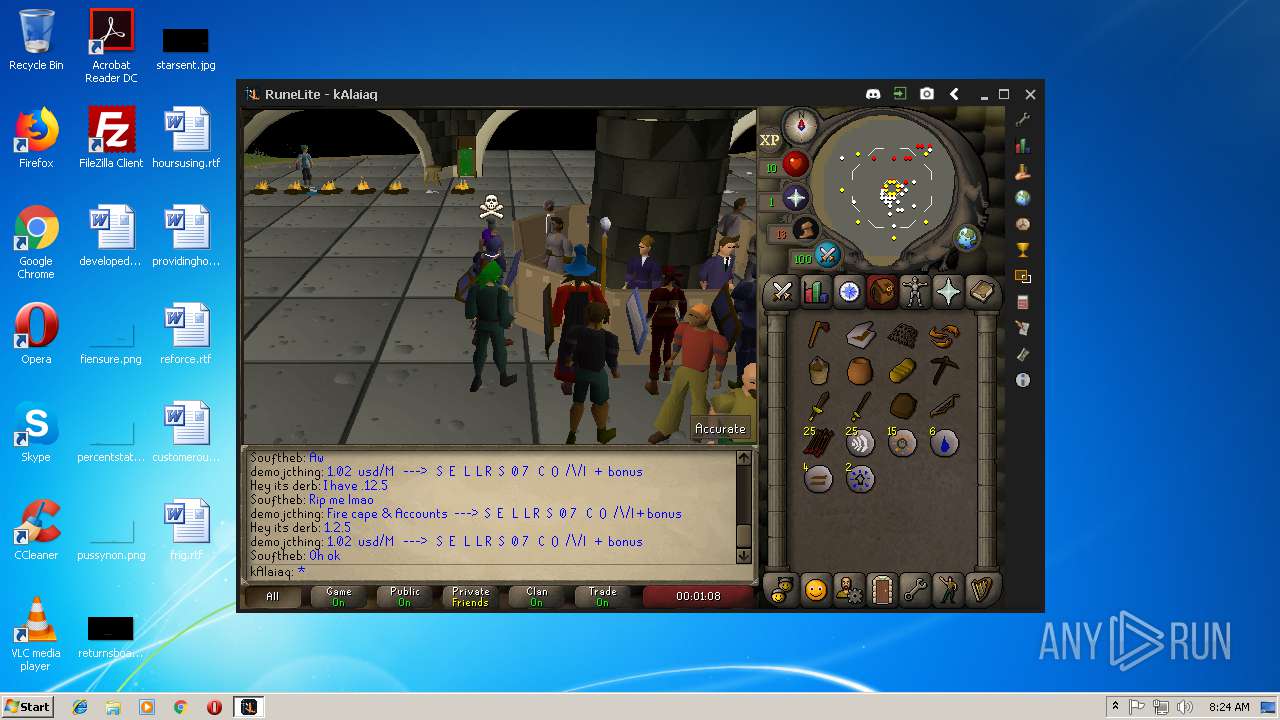
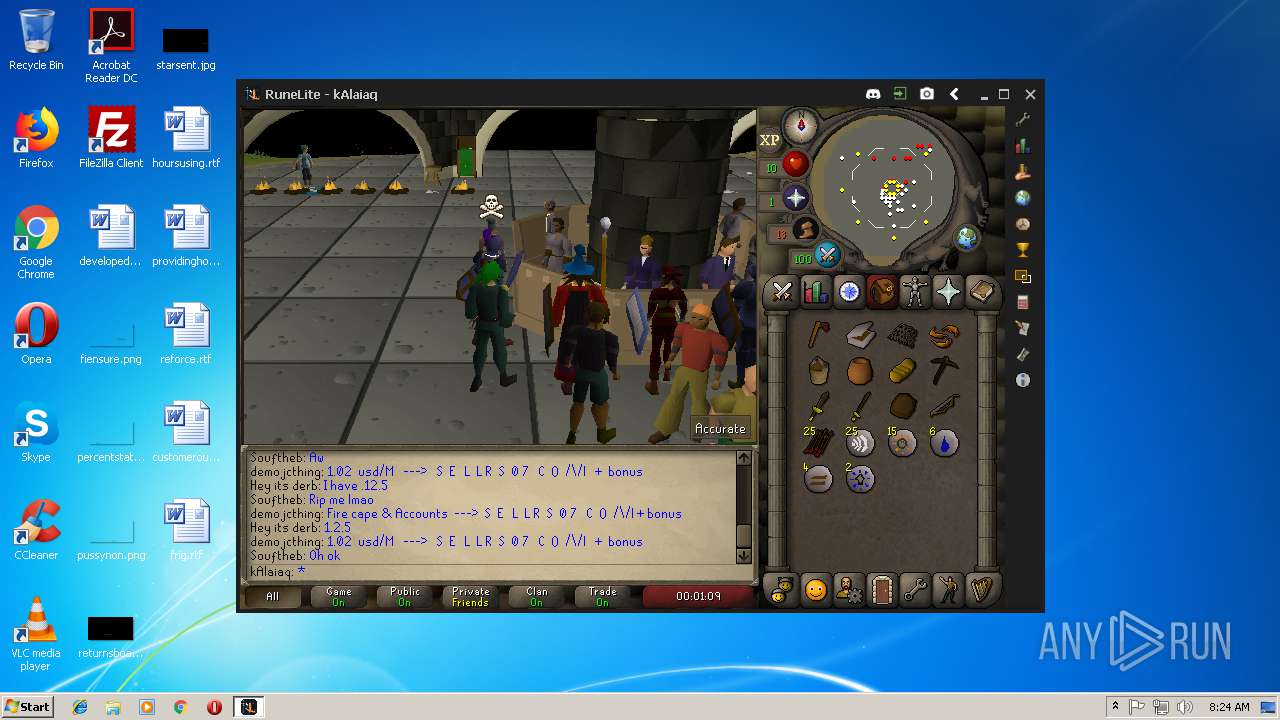
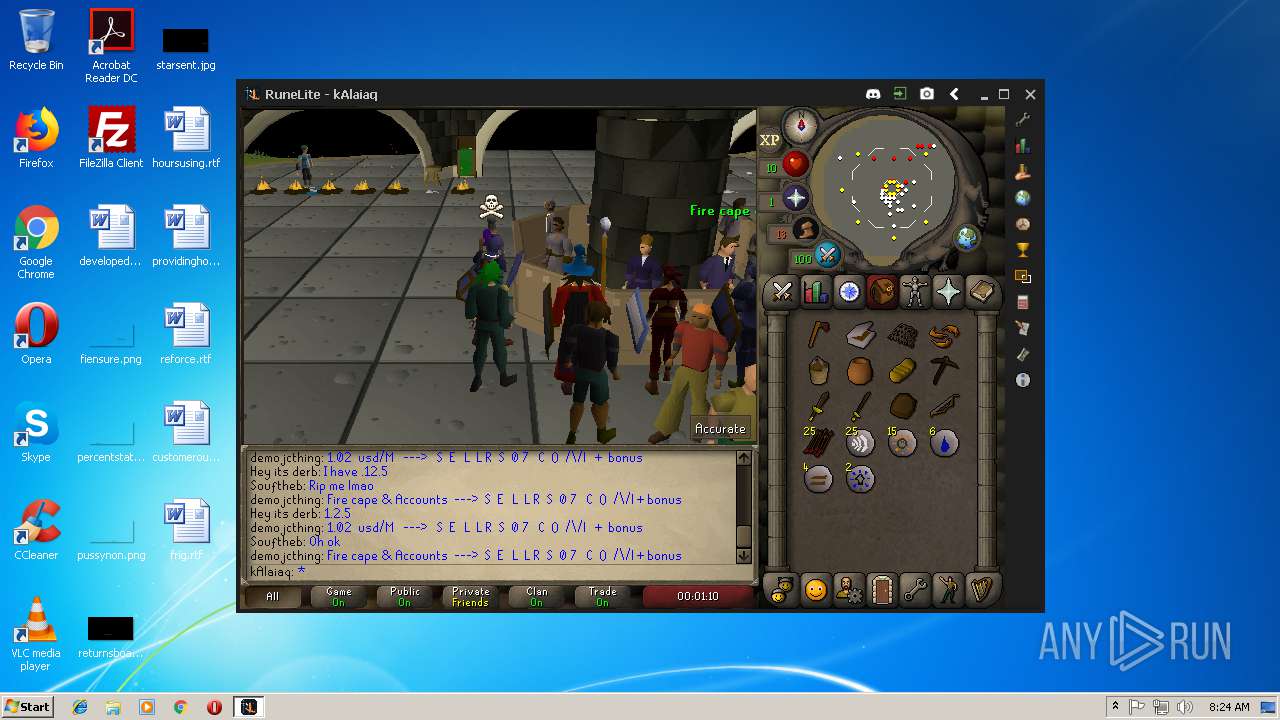
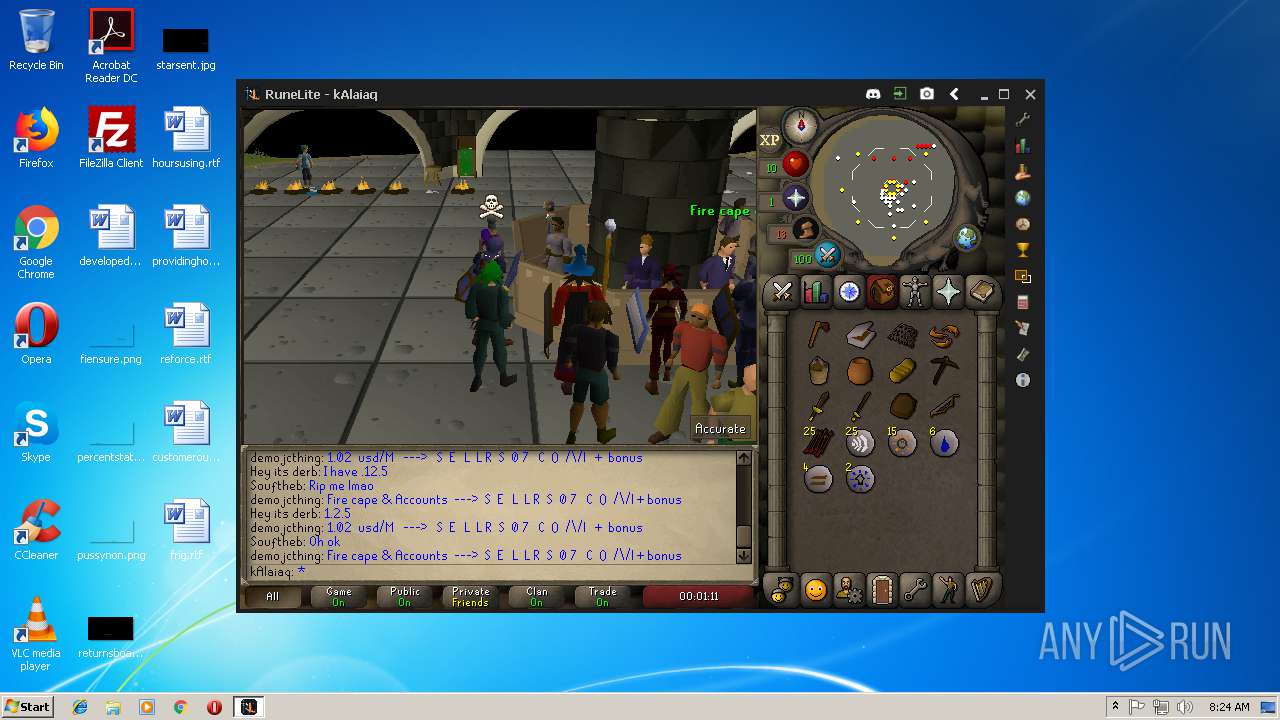
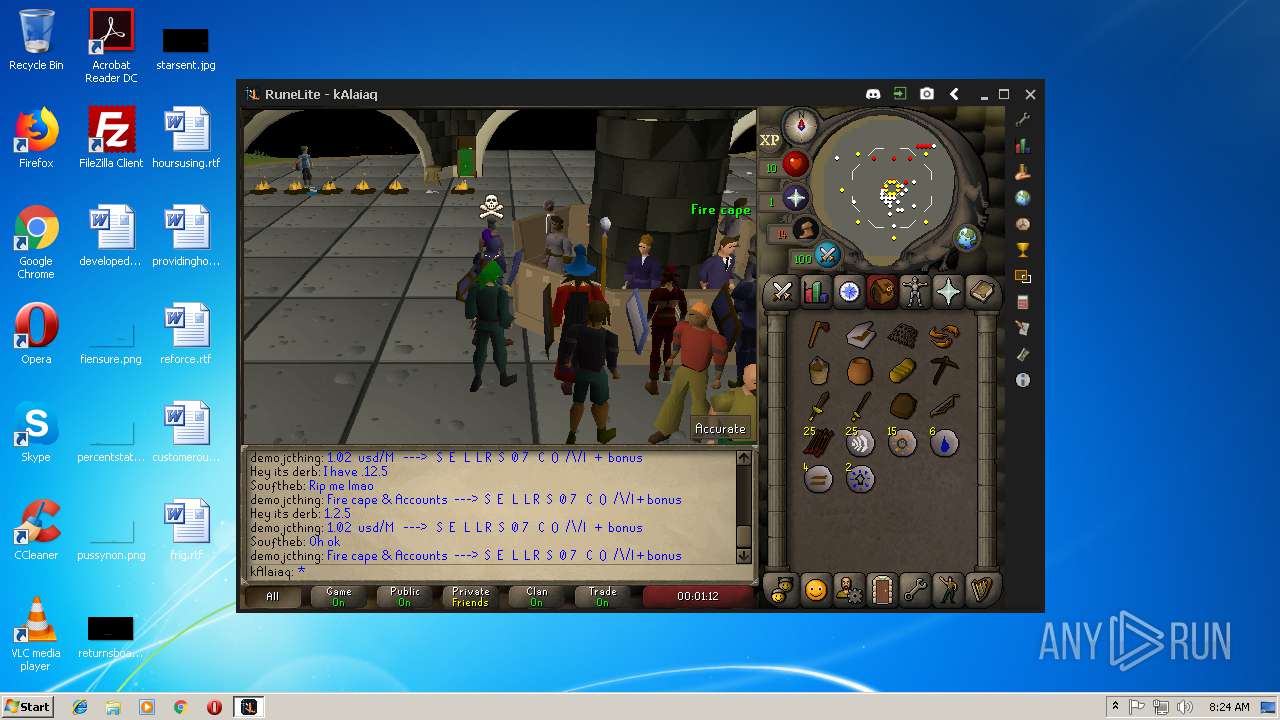
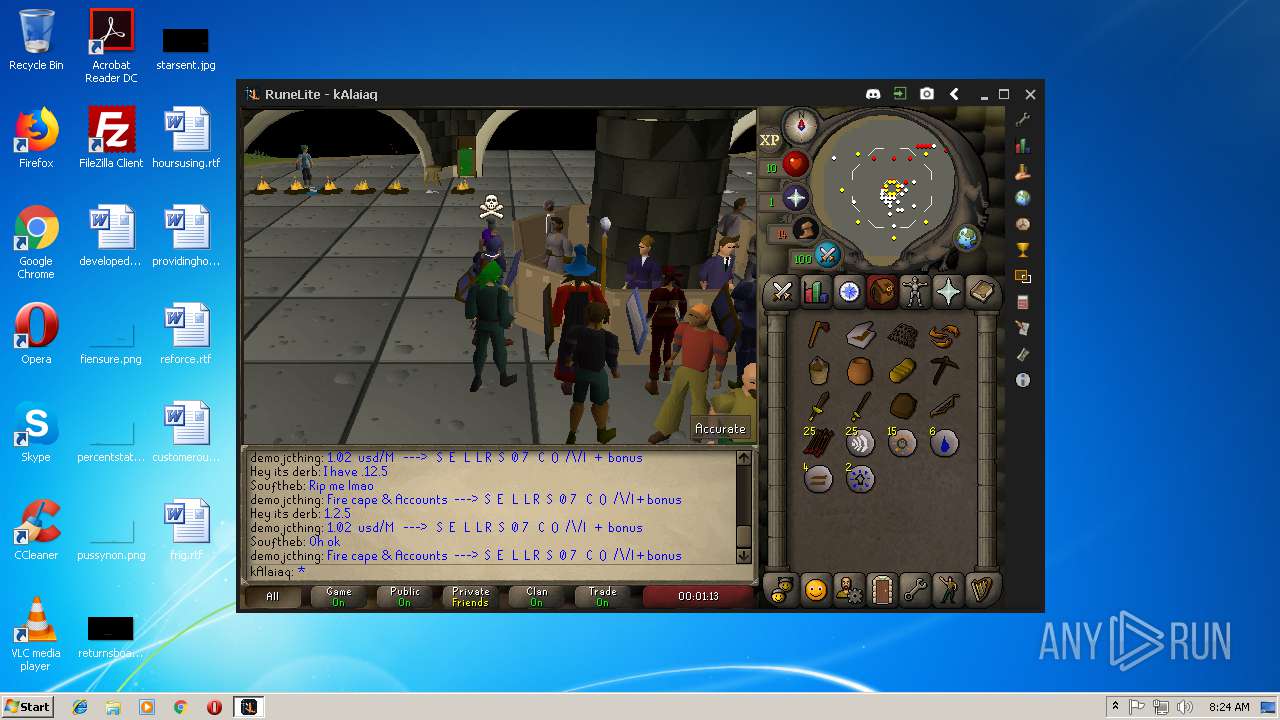
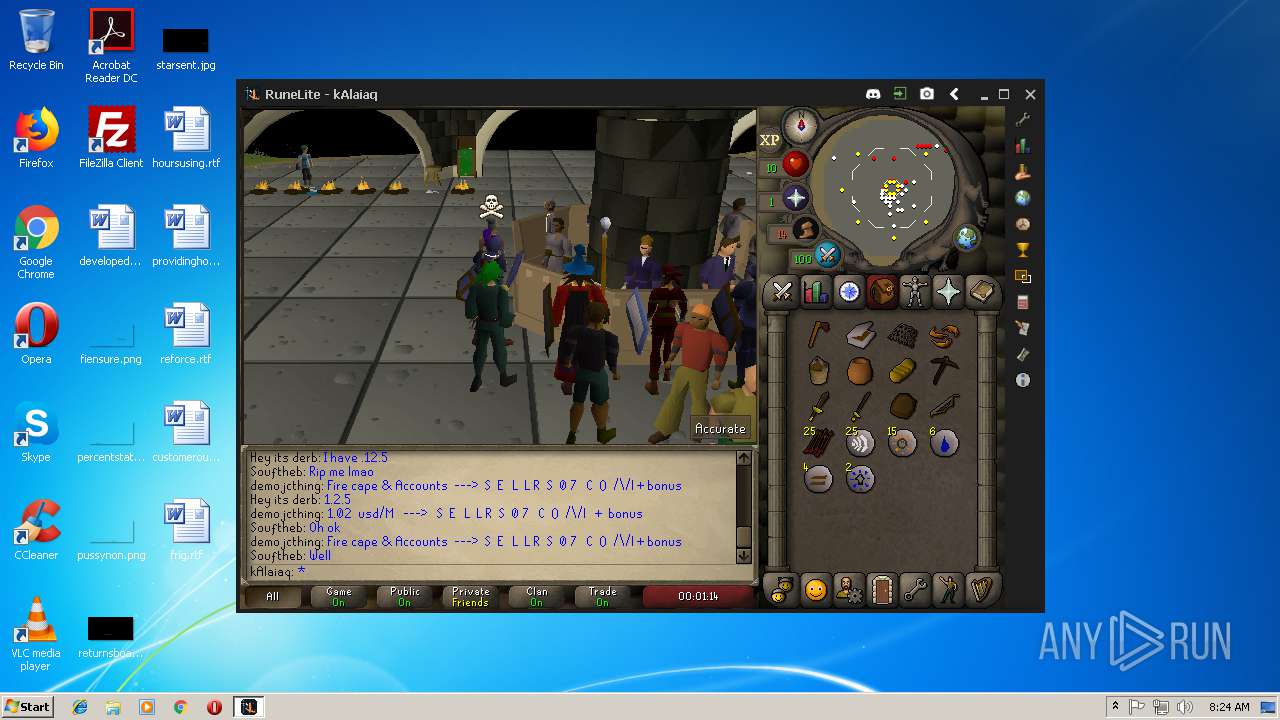
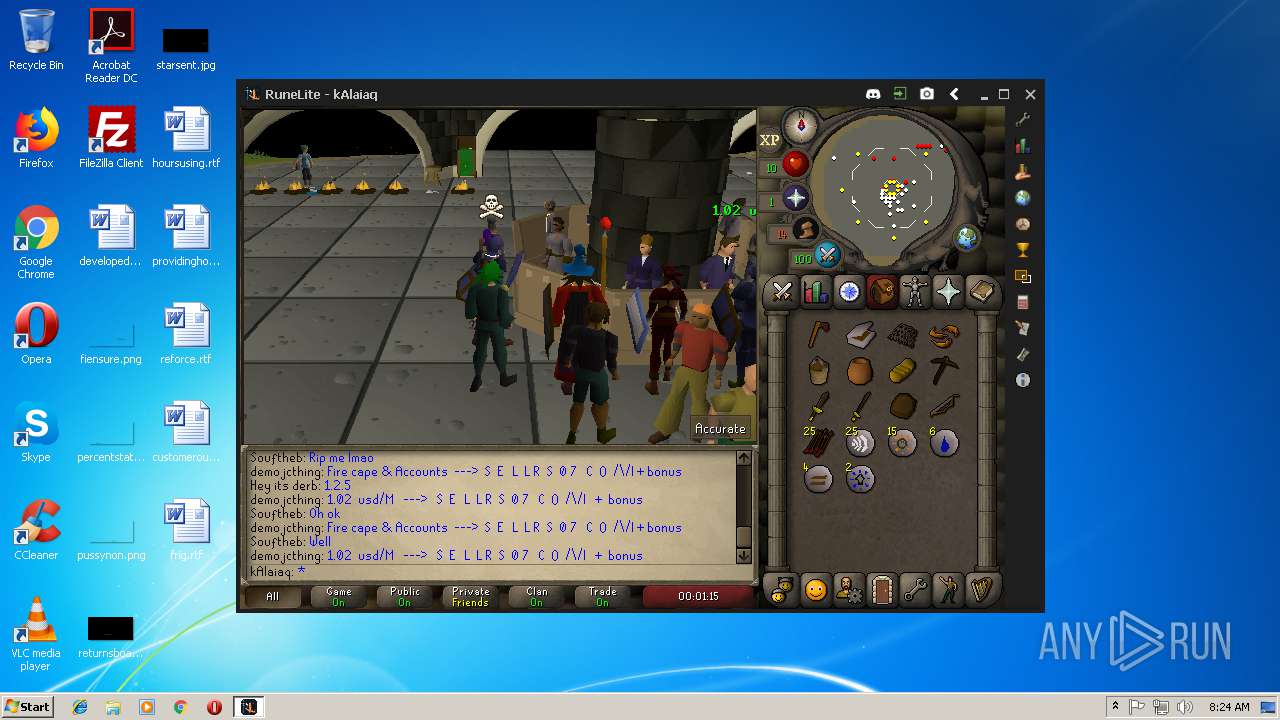
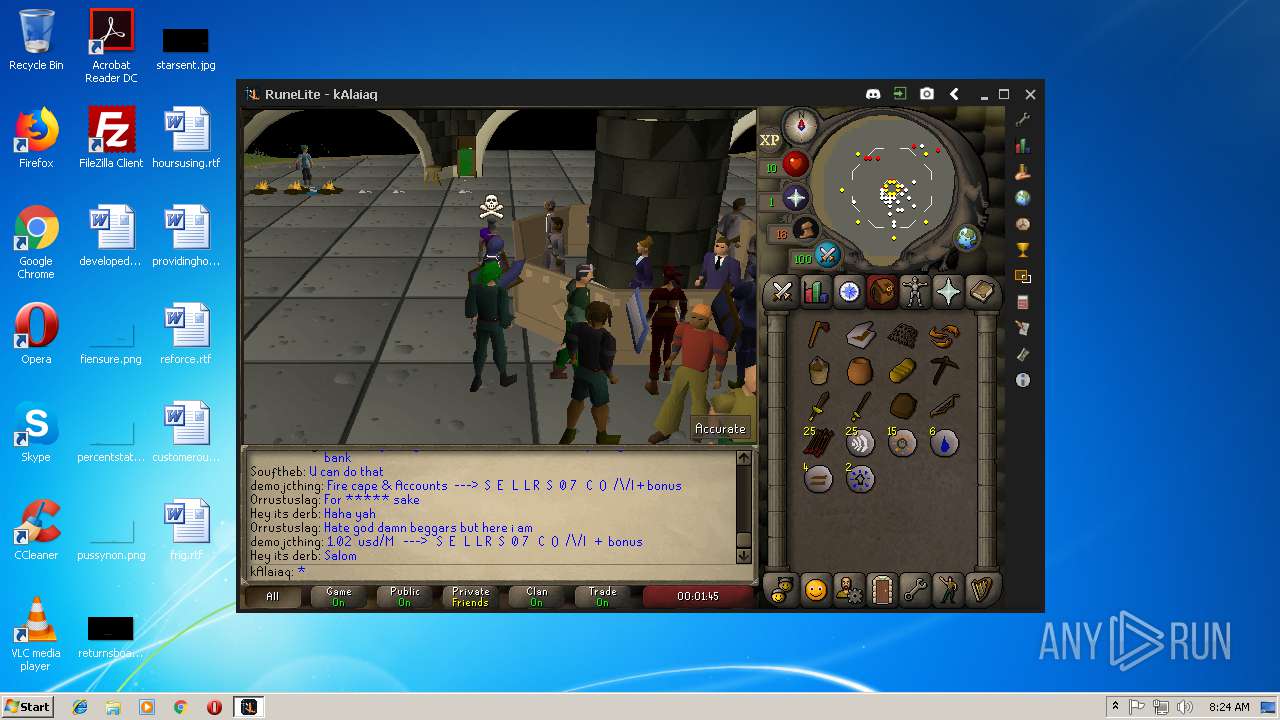
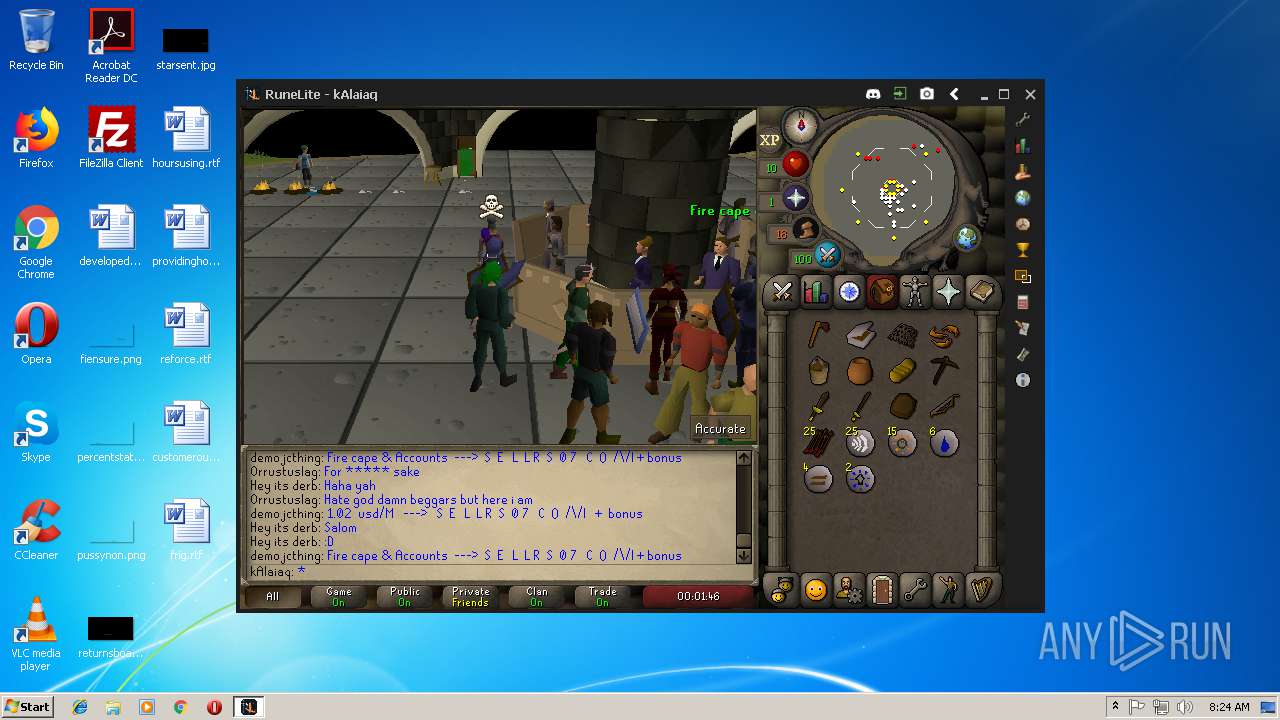
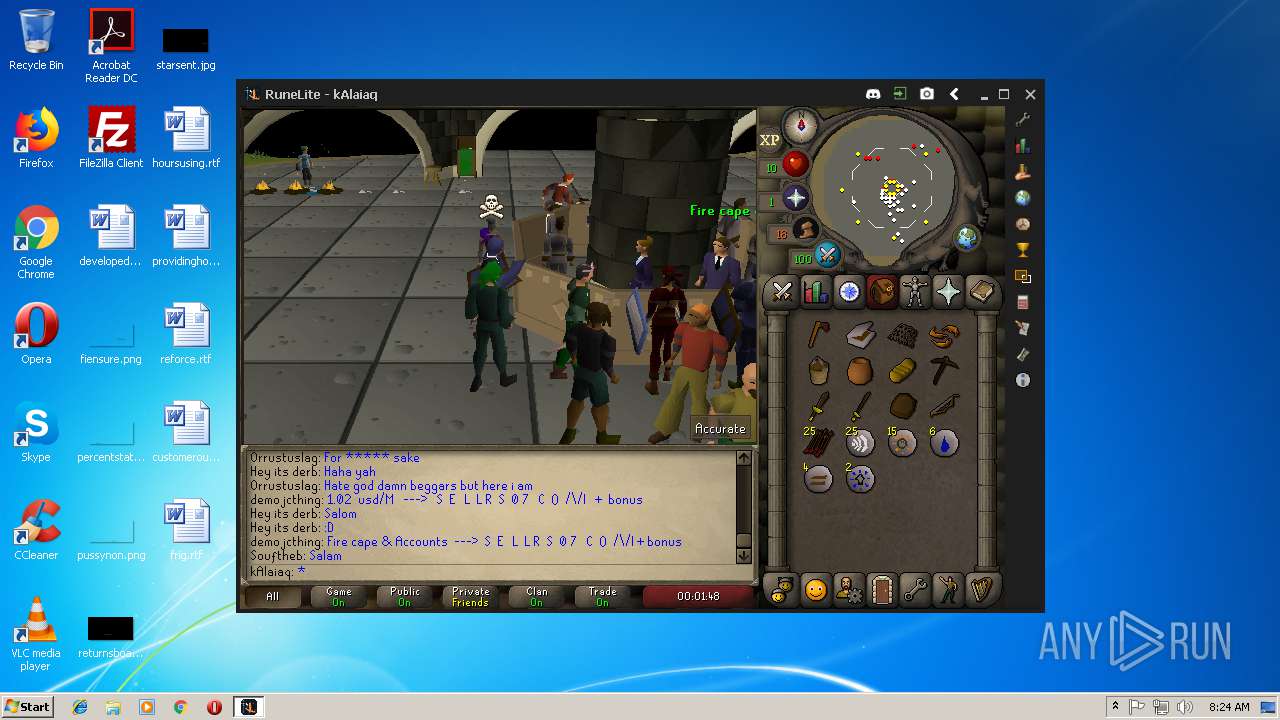
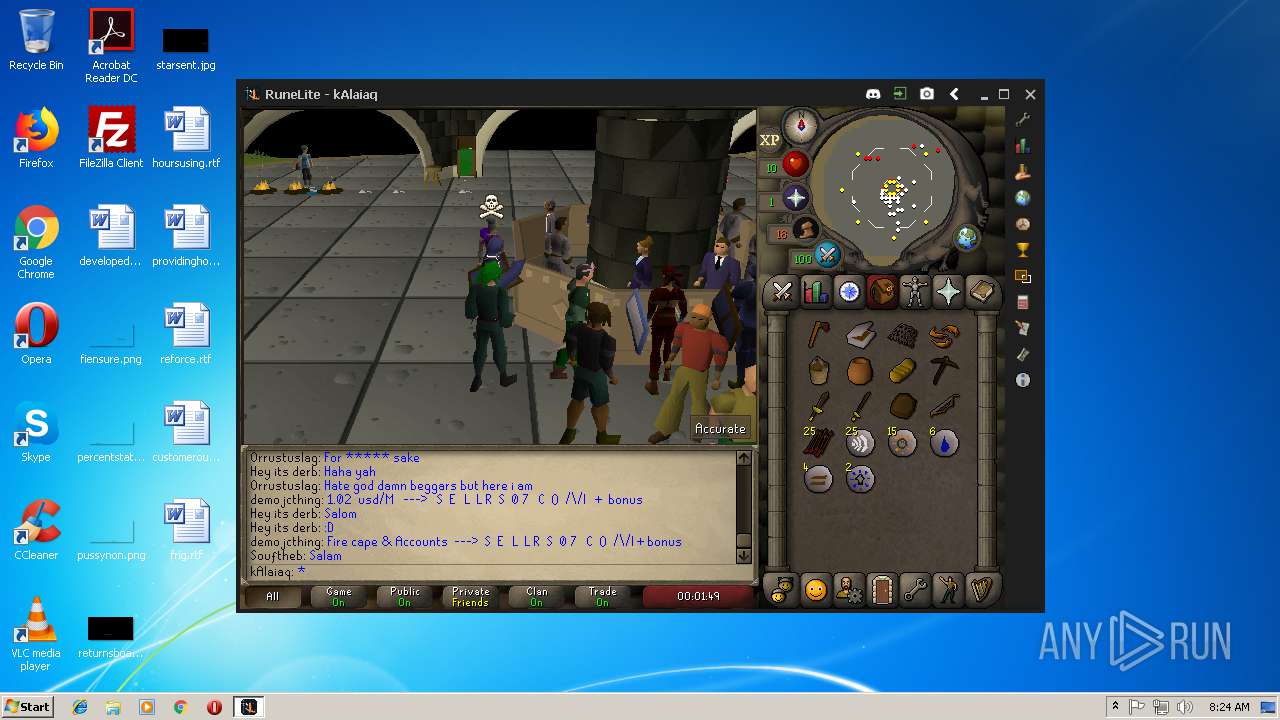
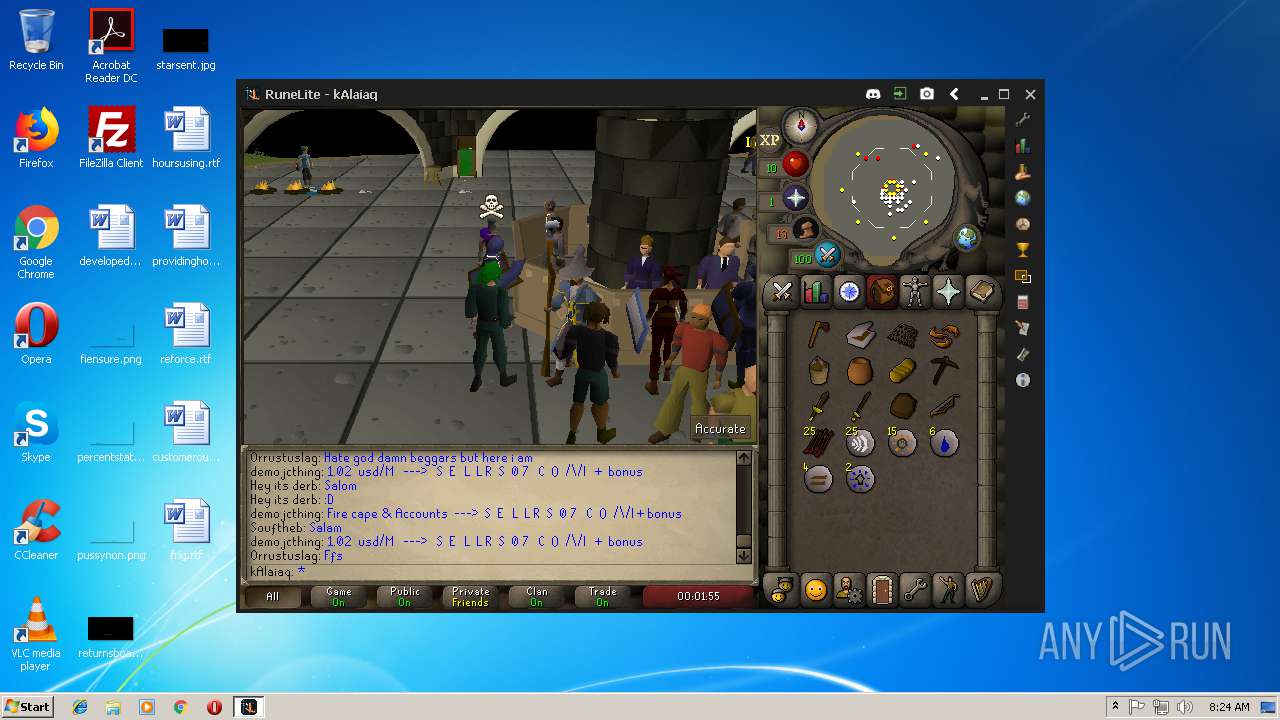
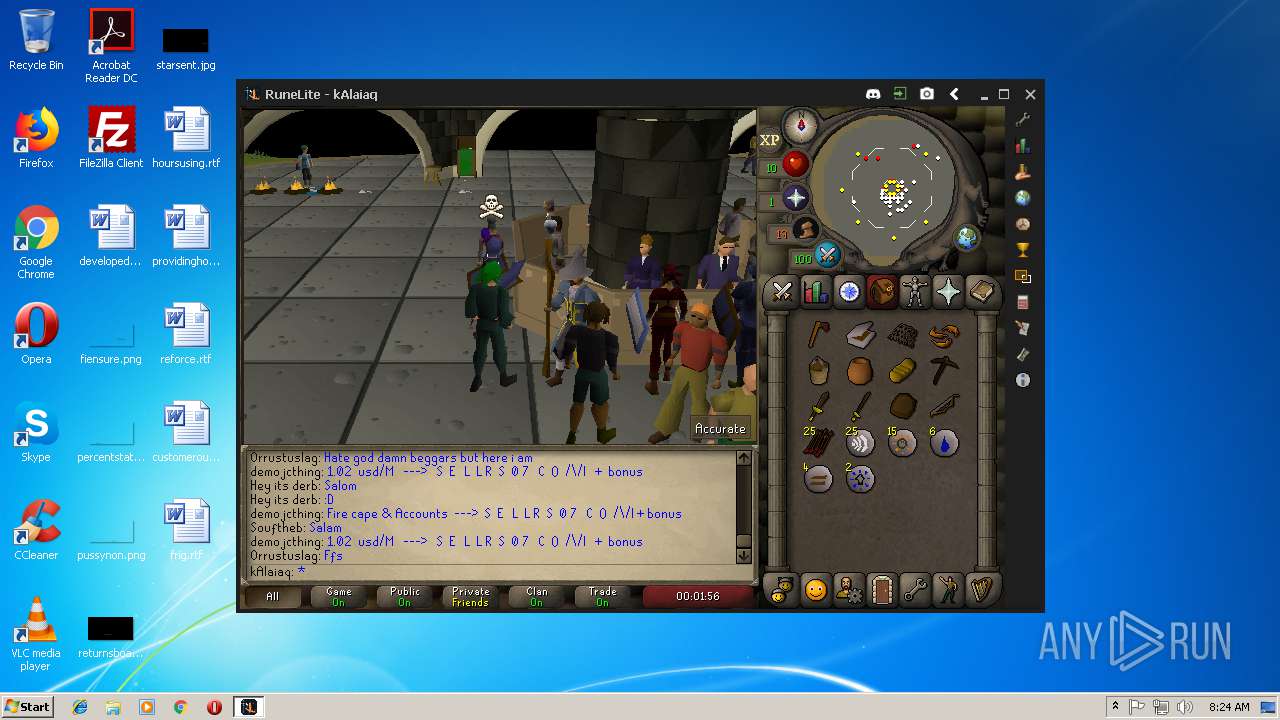
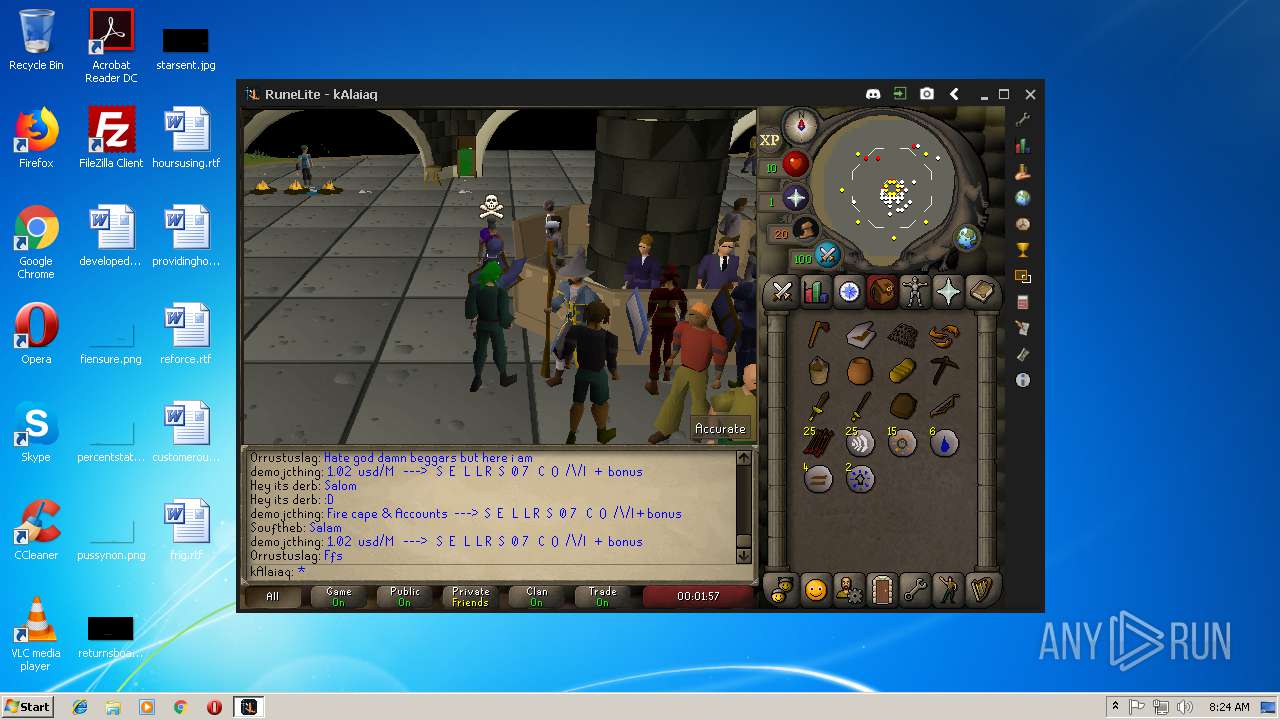
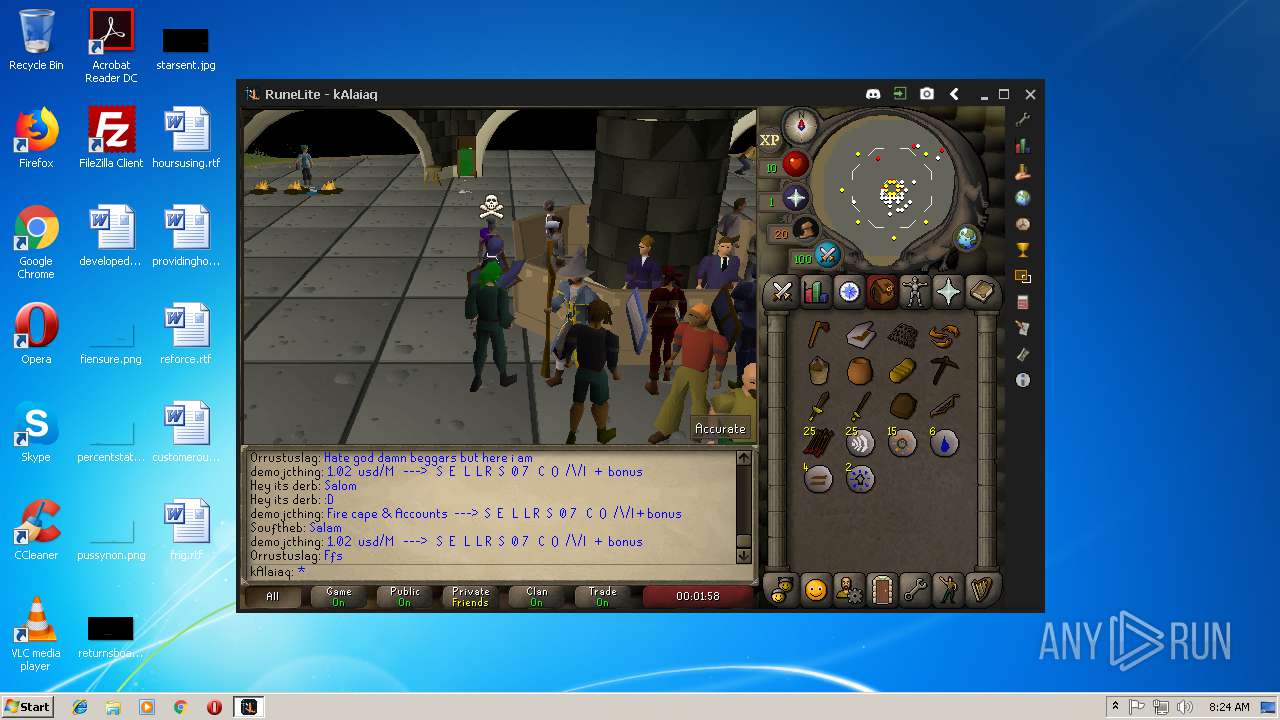
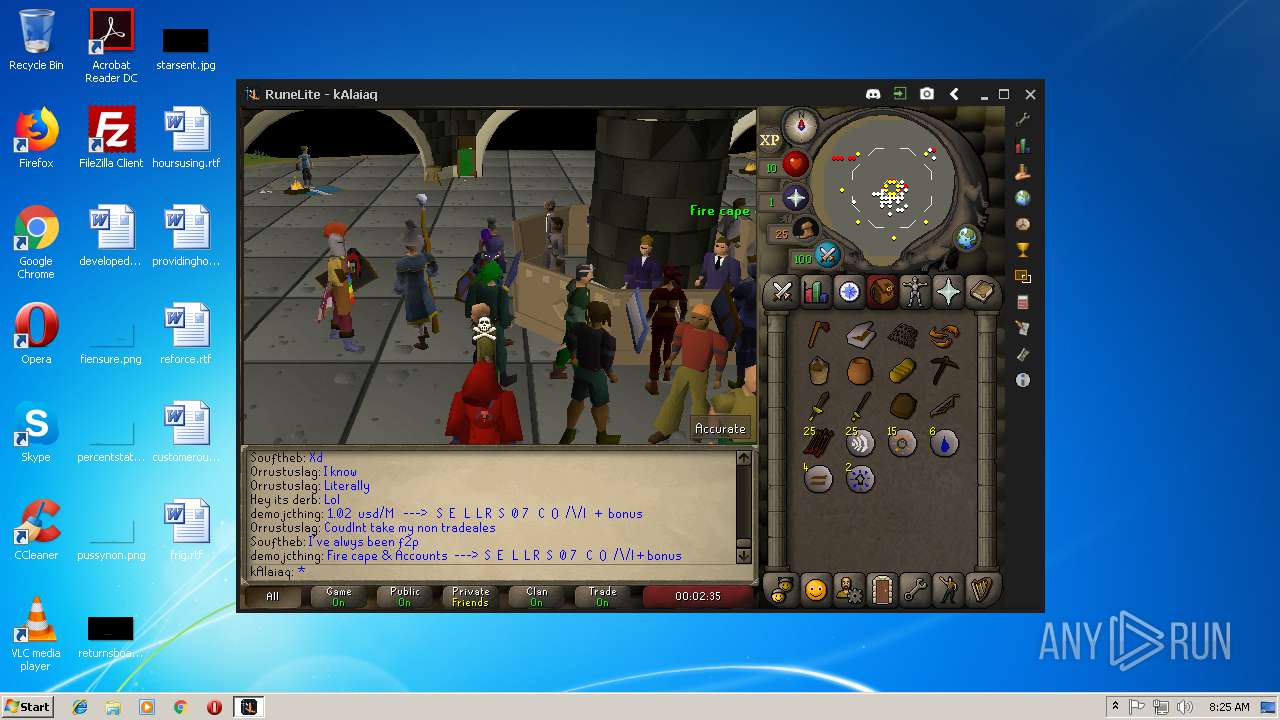
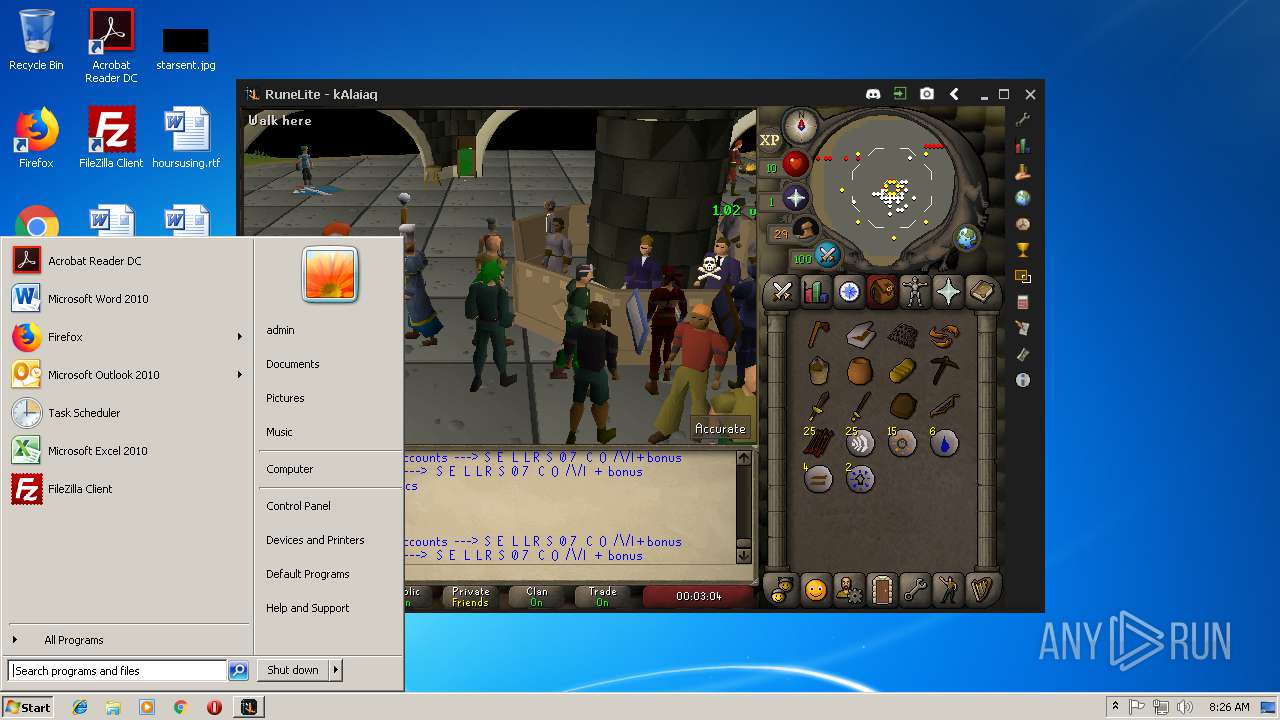
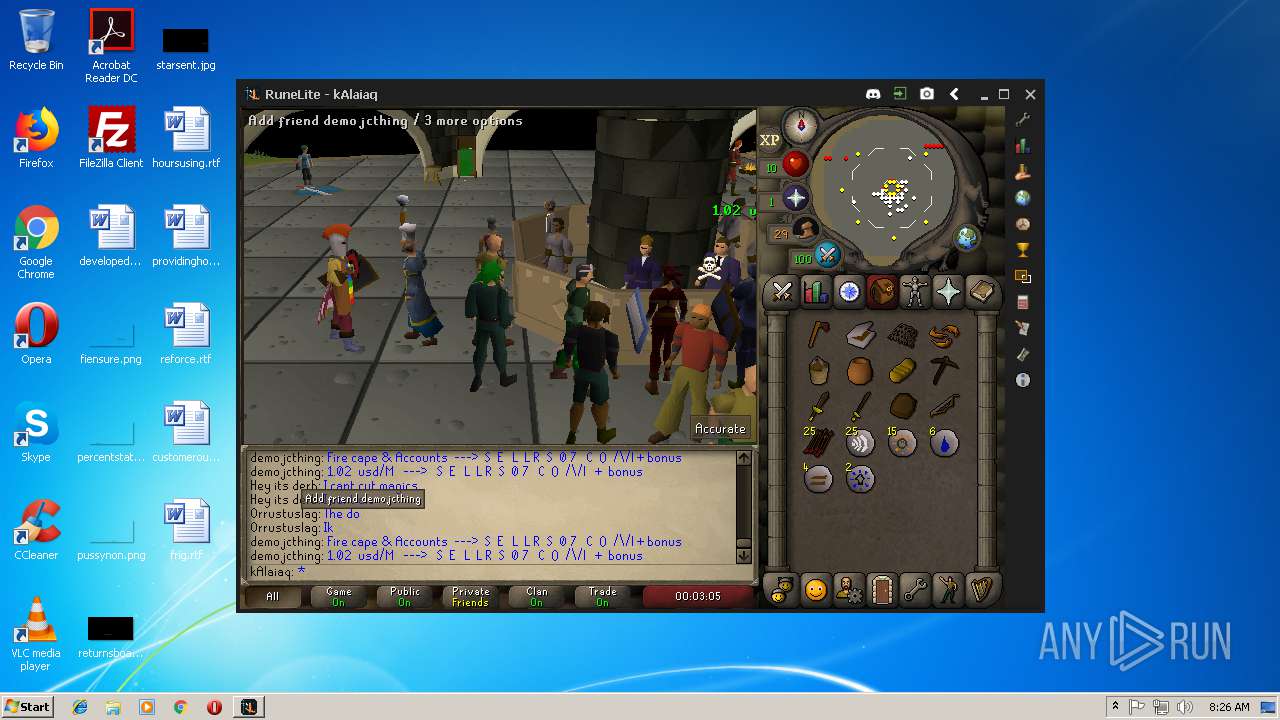
| 3028 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -jar "C:\Users\admin\AppData\Local\Temp\RuneLite (2).jar" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | explorer.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
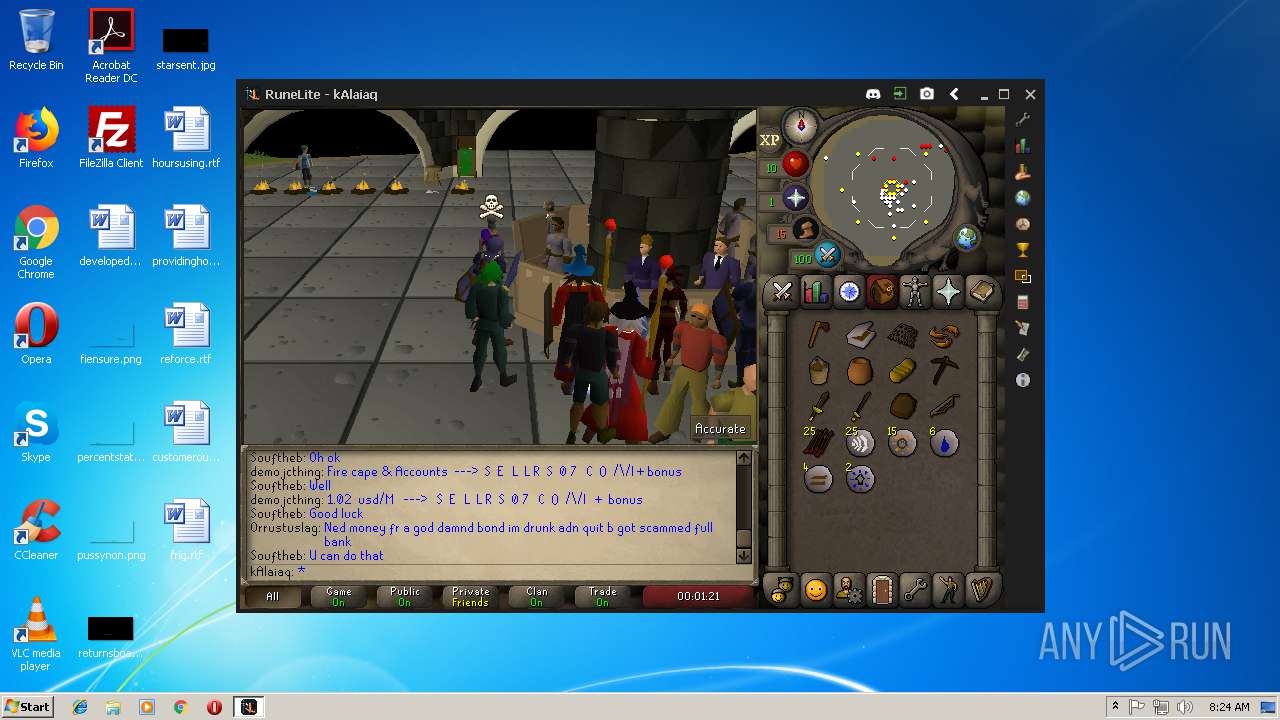
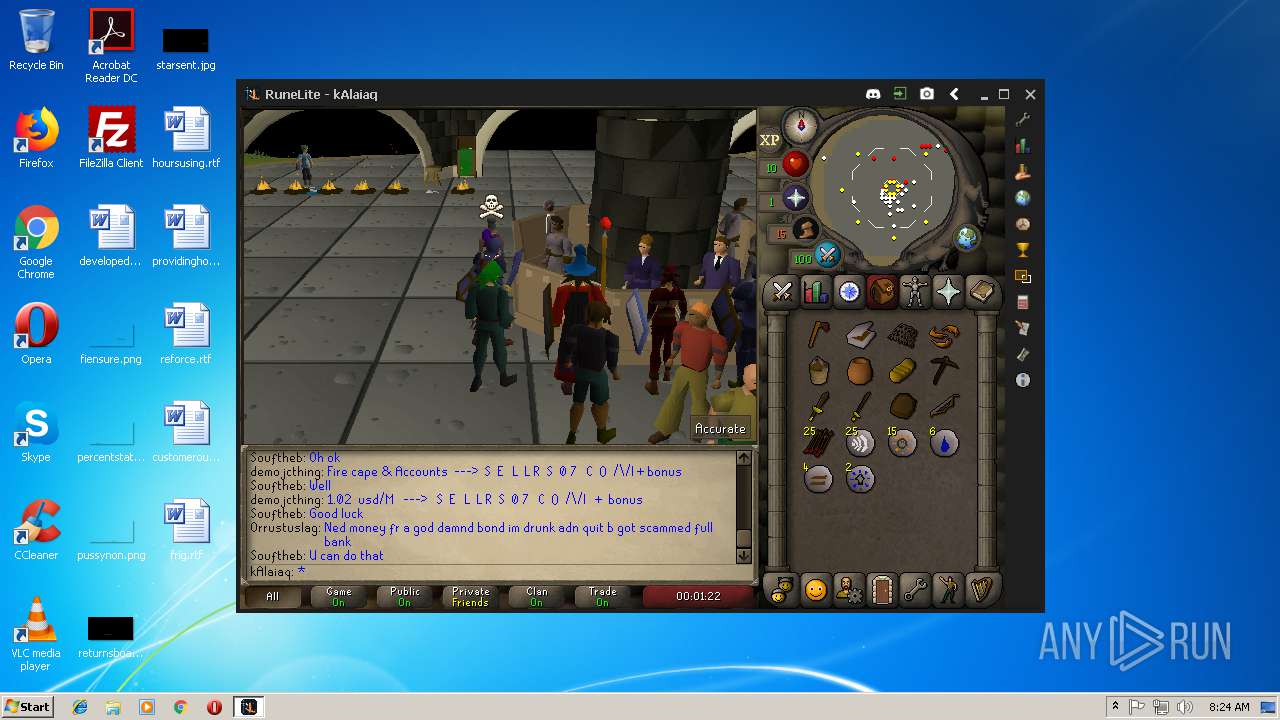
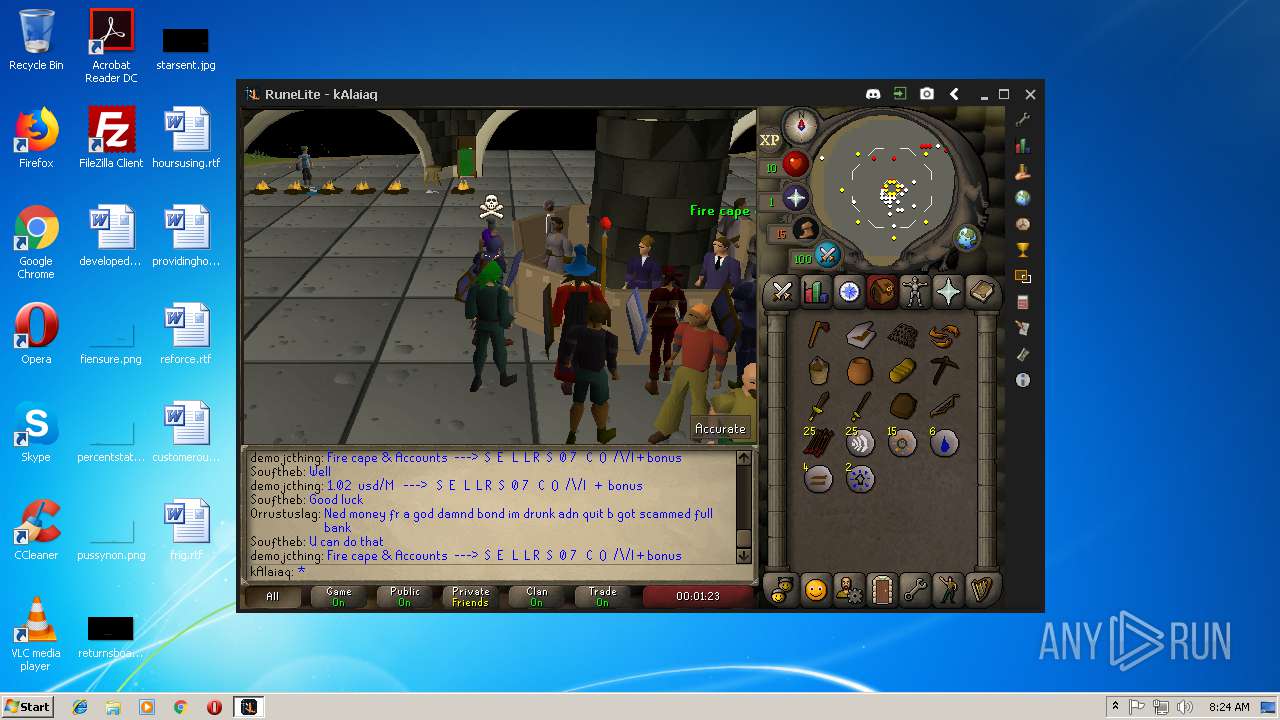
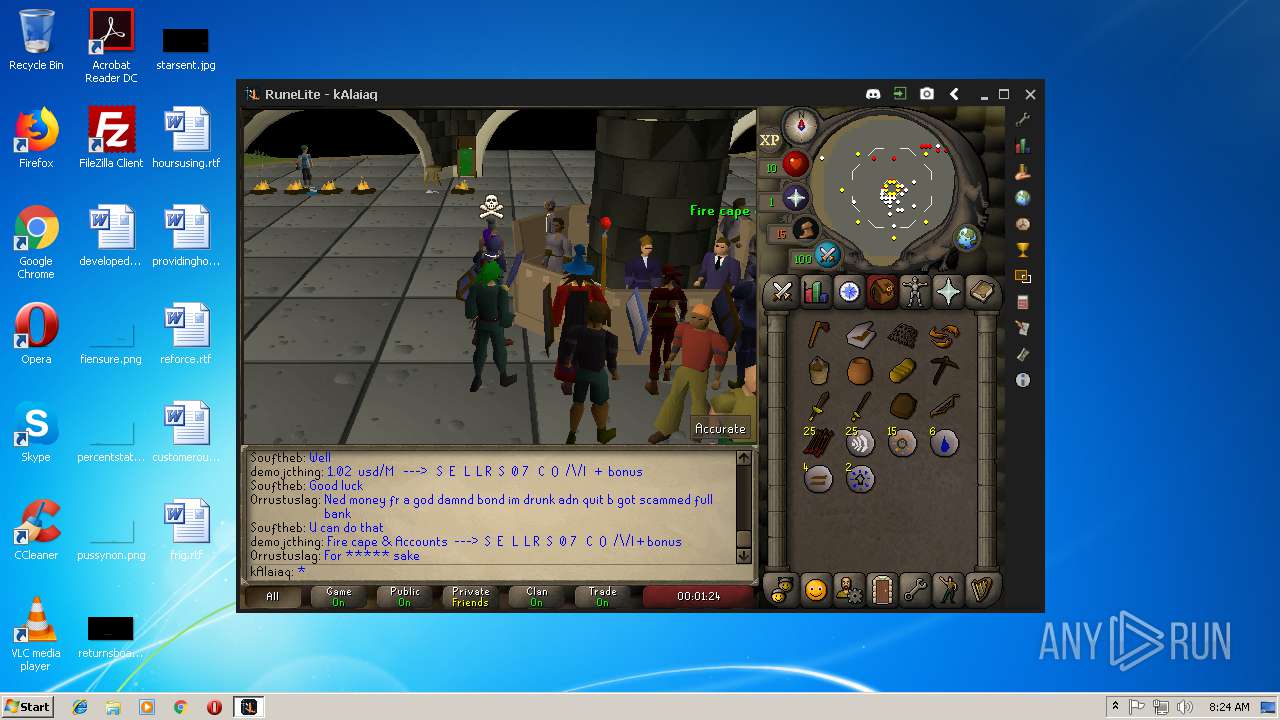
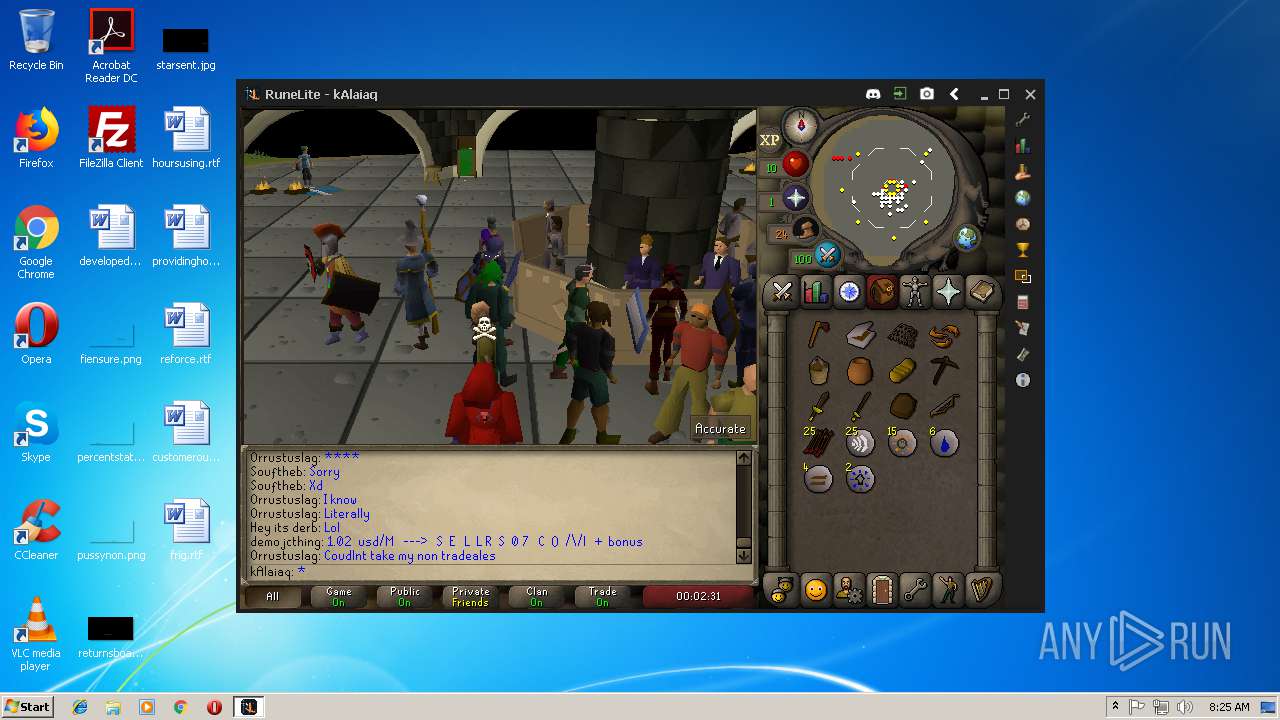
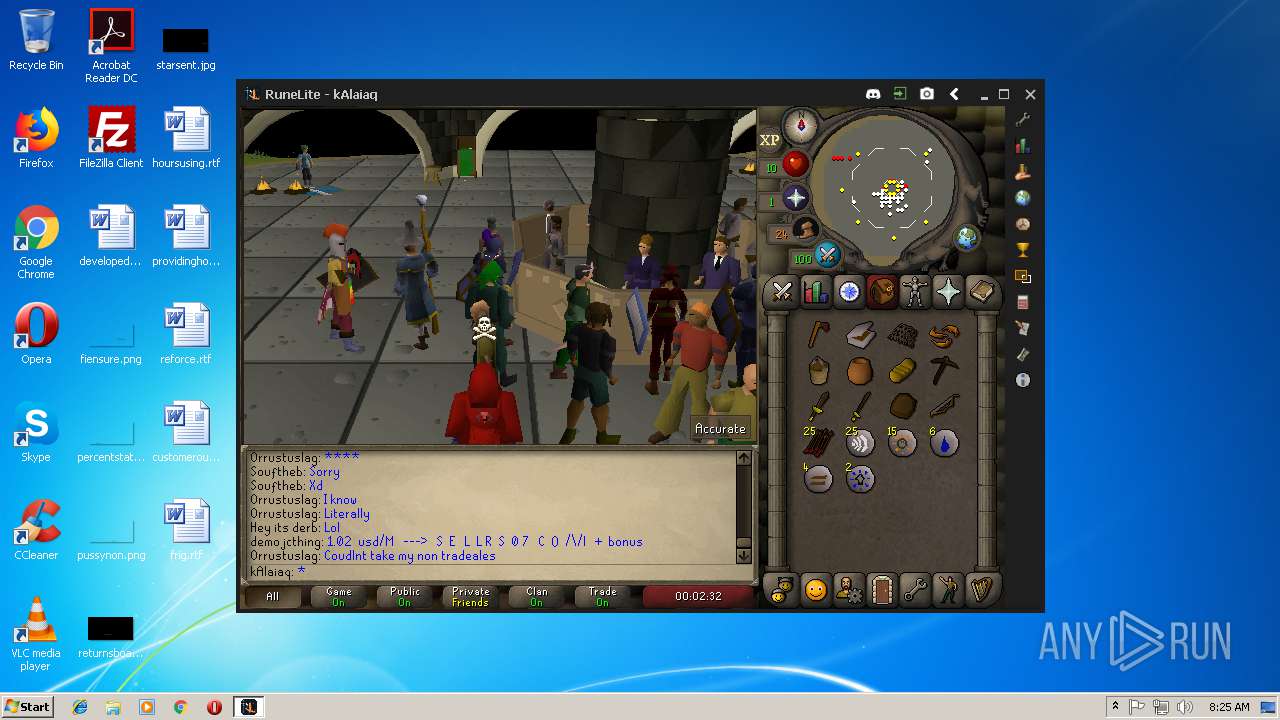
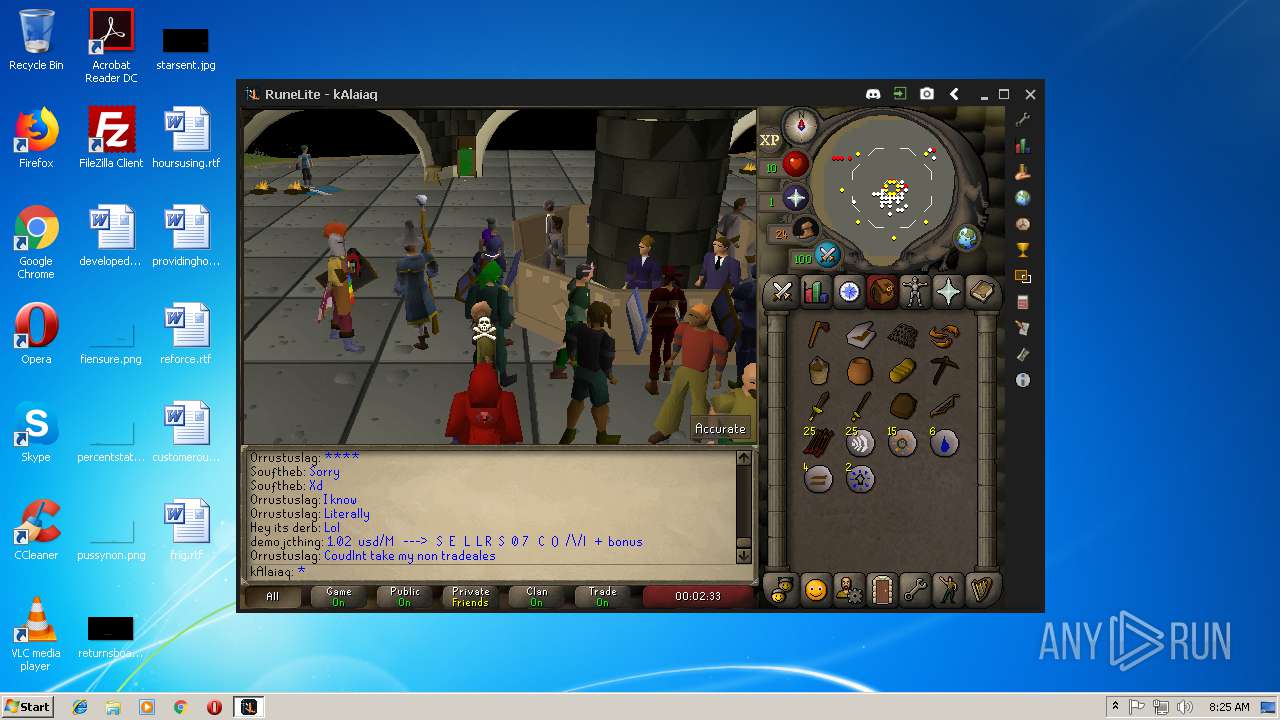
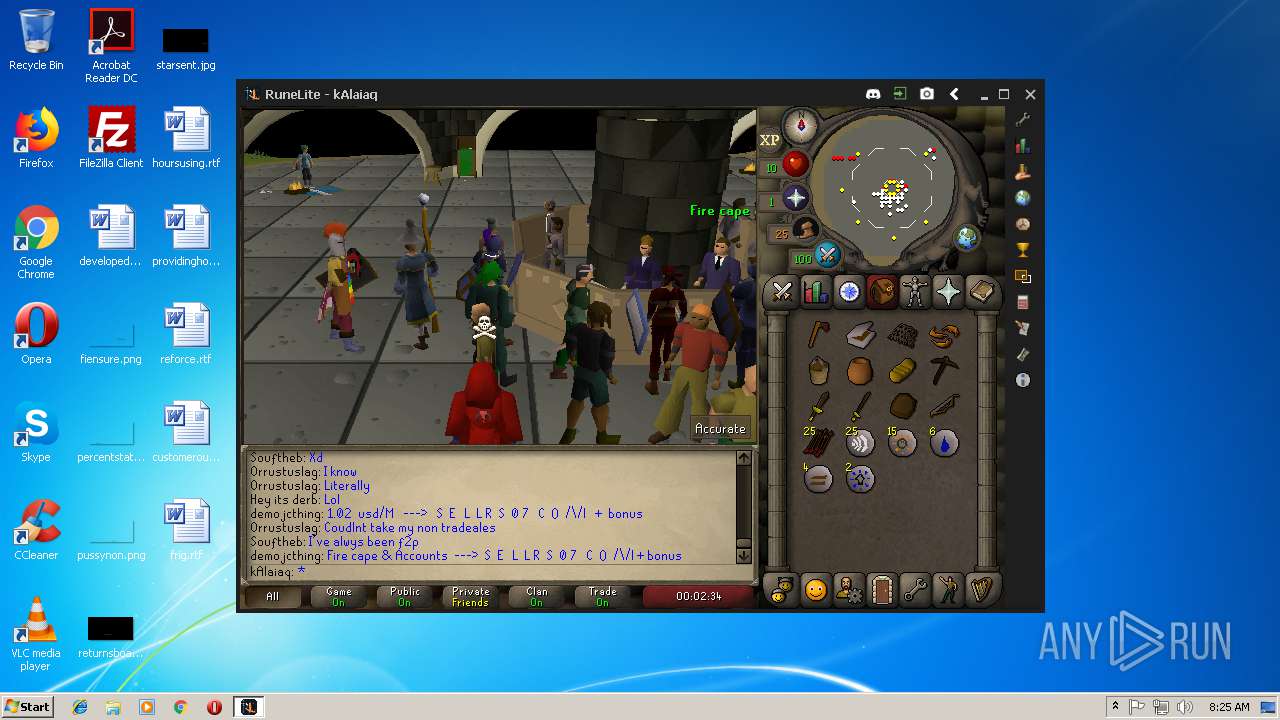
| 3192 | "C:\Program Files\Java\jre1.8.0_92\bin\java.exe" -cp C:\Users\admin\.runelite\repository2\client-1.5.8.jar;C:\Users\admin\.runelite\repository2\slf4j-api-1.7.25.jar;C:\Users\admin\.runelite\repository2\logback-classic-1.2.3.jar;C:\Users\admin\.runelite\repository2\logback-core-1.2.3.jar;C:\Users\admin\.runelite\repository2\jopt-simple-5.0.1.jar;C:\Users\admin\.runelite\repository2\guava-23.2-jre.jar;C:\Users\admin\.runelite\repository2\jsr305-1.3.9.jar;C:\Users\admin\.runelite\repository2\error_prone_annotations-2.0.18.jar;C:\Users\admin\.runelite\repository2\j2objc-annotations-1.1.jar;C:\Users\admin\.runelite\repository2\animal-sniffer-annotations-1.14.jar;C:\Users\admin\.runelite\repository2\guice-4.1.0-no_aop.jar;C:\Users\admin\.runelite\repository2\javax.inject-1.jar;C:\Users\admin\.runelite\repository2\aopalliance-1.0.jar;C:\Users\admin\.runelite\repository2\gson-2.8.5.jar;C:\Users\admin\.runelite\repository2\substance-8.0.02.jar;C:\Users\admin\.runelite\repository2\trident-1.5.00.jar;C:\Users\admin\.runelite\repository2\commons-text-1.2.jar;C:\Users\admin\.runelite\repository2\commons-lang3-3.7.jar;C:\Users\admin\.runelite\repository2\jogl-all-2.3.2.jar;C:\Users\admin\.runelite\repository2\jogl-all-2.3.2-natives-windows-amd64.jar;C:\Users\admin\.runelite\repository2\jogl-all-2.3.2-natives-windows-i586.jar;C:\Users\admin\.runelite\repository2\jogl-all-2.3.2-natives-linux-amd64.jar;C:\Users\admin\.runelite\repository2\jogl-all-2.3.2-natives-linux-i586.jar;C:\Users\admin\.runelite\repository2\gluegen-rt-2.3.2.jar;C:\Users\admin\.runelite\repository2\gluegen-rt-2.3.2-natives-windows-amd64.jar;C:\Users\admin\.runelite\repository2\gluegen-rt-2.3.2-natives-windows-i586.jar;C:\Users\admin\.runelite\repository2\gluegen-rt-2.3.2-natives-linux-amd64.jar;C:\Users\admin\.runelite\repository2\gluegen-rt-2.3.2-natives-linux-i586.jar;C:\Users\admin\.runelite\repository2\jbsdiff-1.0.jar;C:\Users\admin\.runelite\repository2\commons-compress-1.5.jar;C:\Users\admin\.runelite\repository2\jna-4.5.1.jar;C:\Users\admin\.runelite\repository2\jna-platform-4.5.1.jar;C:\Users\admin\.runelite\repository2\runelite-api-1.5.6.1.jar;C:\Users\admin\.runelite\repository2\runescape-api-1.5.6.1.jar;C:\Users\admin\.runelite\repository2\client-patch-1.5.6.1.jar;C:\Users\admin\.runelite\repository2\http-api-1.5.6.1.jar;C:\Users\admin\.runelite\repository2\okhttp-3.7.0.jar;C:\Users\admin\.runelite\repository2\okio-1.12.0.jar;C:\Users\admin\.runelite\repository2\commons-csv-1.4.jar;C:\Users\admin\.runelite\repository2\discord-1.1.jar -Xmx512m -Xss2m -XX:CompileThreshold=1500 -Xincgc -XX:+UseConcMarkSweepGC -XX:+UseParNewGC -Djna.nosys=true -Dsun.java2d.noddraw=false -Dsun.java2d.opengl=false -Djava.net.preferIPv4Stack=true -Djava.net.preferIPv4Addresses=true -Drunelite.launcher.version=1.6.2-SNAPSHOT net.runelite.client.RuneLite | C:\Program Files\Java\jre1.8.0_92\bin\java.exe | javaw.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 3308 | C:\Windows\system32\tasklist.exe | C:\Windows\system32\tasklist.exe | — | java.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
984
Read events
956
Write events
28
Delete events
0
Modification events
| (PID) Process: | (3028) javaw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: javaw.exe | |||
| (PID) Process: | (3192) java.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: java.exe | |||
| (PID) Process: | (3192) java.exe | Key: | HKEY_CLASSES_ROOT\discord-409416265891971072 |
| Operation: | write | Name: | |
Value: URL:Run game 409416265891971072 protocol | |||
| (PID) Process: | (3192) java.exe | Key: | HKEY_CLASSES_ROOT\discord-409416265891971072 |
| Operation: | write | Name: | URL Protocol |
Value: | |||
| (PID) Process: | (3192) java.exe | Key: | HKEY_CLASSES_ROOT\discord-409416265891971072\DefaultIcon |
| Operation: | write | Name: | |
Value: C:\Program Files\Java\jre1.8.0_92\bin\java.exe | |||
| (PID) Process: | (3192) java.exe | Key: | HKEY_CLASSES_ROOT\discord-409416265891971072\shell\open\command |
| Operation: | write | Name: | |
Value: C:\Program Files\Java\jre1.8.0_92\bin\java.exe | |||
| (PID) Process: | (2836) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2836) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2836) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2836) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
11
Suspicious files
35
Text files
23
Unknown types
25
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3028 | javaw.exe | C:\Users\admin\.runelite\repository2\client-1.5.8.jar | java | |
MD5:— | SHA256:— | |||
| 3028 | javaw.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 3028 | javaw.exe | C:\Users\admin\.runelite\repository2\slf4j-api-1.7.25.jar | compressed | |
MD5:CAAFE376AFB7086DCBEE79F780394CA3 | SHA256:18C4A0095D5C1DA6B817592E767BB23D29DD2F560AD74DF75FF3961DBDE25B79 | |||
| 3028 | javaw.exe | C:\Users\admin\.runelite\repository2\logback-classic-1.2.3.jar | compressed | |
MD5:64F7A68F931AED8E5AD8243470440F0B | SHA256:FB53F8539E7FCB8F093A56E138112056EC1DC809EBB020B59D8A36A5EBAC37E0 | |||
| 3028 | javaw.exe | C:\Users\admin\.runelite\repository2\guava-23.2-jre.jar | java | |
MD5:242752D696208279A698FEA5FEAC507D | SHA256:5BE9A7D05BA0CCD74708BC8018AE412255F85843C0B92302E9B9BEFA6ED52564 | |||
| 3028 | javaw.exe | C:\Users\admin\.runelite\repository2\animal-sniffer-annotations-1.14.jar | compressed | |
MD5:9D42E46845C874F1710A9F6A741F6C14 | SHA256:2068320BD6BAD744C3673AB048F67E30BEF8F518996FA380033556600669905D | |||
| 3028 | javaw.exe | C:\Users\admin\.runelite\repository2\guice-4.1.0-no_aop.jar | compressed | |
MD5:8CF17838FD9407BC2C8C39DDF027008F | SHA256:9264C6931C431E928DC64ADC842584D5F57D17B2F3AFF29221F2B3FDEA673DAD | |||
| 3028 | javaw.exe | C:\Users\admin\.runelite\repository2\logback-core-1.2.3.jar | compressed | |
MD5:841FC80C6EDFF60D947A3872A2DB4D45 | SHA256:5946D837FE6F960C02A53EDA7A6926ECC3C758BBDD69AA453EE429F858217F22 | |||
| 3028 | javaw.exe | C:\Users\admin\.runelite\repository2\jsr305-1.3.9.jar | java | |
MD5:1D5A772E400B04BB67A7EF4A0E0996D8 | SHA256:905721A0EEA90A81534ABB7EE6EF4EA2E5E645FA1DEF0A5CD88402DF1B46C9ED | |||
| 3028 | javaw.exe | C:\Users\admin\.runelite\repository2\gson-2.8.5.jar | compressed | |
MD5:089104CB90D8B4E1AA00B1F5FAEF0742 | SHA256:233A0149FC365C9F6EDBD683CFE266B19BDC773BE98EABDAF6B3C924B48E7D81 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
52
TCP/UDP connections
18
DNS requests
191
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3028 | javaw.exe | GET | 200 | 213.199.247.21:80 | http://runelite.site/full.jar | PL | java | 17.3 Mb | suspicious |
3028 | javaw.exe | GET | 200 | 213.199.247.21:80 | http://runelite.site/launcher/bootstrap.json | PL | text | 16.4 Kb | suspicious |
3028 | javaw.exe | GET | 200 | 172.64.143.9:80 | http://static.runelite.net/bootstrap.json.sha256 | US | binary | 512 b | suspicious |
3028 | javaw.exe | GET | 200 | 172.64.143.9:80 | http://mvn.runelite.net/org/slf4j/slf4j-api/1.7.25/slf4j-api-1.7.25.jar | US | compressed | 40.2 Kb | suspicious |
3028 | javaw.exe | GET | 200 | 172.64.142.9:80 | http://repo.runelite.net/net/runelite/pushingpixels/trident/1.5.00/trident-1.5.00.jar | US | java | 77.8 Kb | suspicious |
3028 | javaw.exe | GET | 200 | 172.64.143.9:80 | http://mvn.runelite.net/com/google/code/gson/gson/2.8.5/gson-2.8.5.jar | US | compressed | 235 Kb | suspicious |
3028 | javaw.exe | GET | 200 | 172.64.143.9:80 | http://mvn.runelite.net/ch/qos/logback/logback-core/1.2.3/logback-core-1.2.3.jar | US | compressed | 460 Kb | suspicious |
3028 | javaw.exe | GET | 200 | 172.64.143.9:80 | http://mvn.runelite.net/com/google/guava/guava/23.2-jre/guava-23.2-jre.jar | US | java | 2.53 Mb | suspicious |
3028 | javaw.exe | GET | 200 | 172.64.143.9:80 | http://mvn.runelite.net/org/apache/commons/commons-lang3/3.7/commons-lang3-3.7.jar | US | compressed | 487 Kb | suspicious |
3028 | javaw.exe | GET | 200 | 172.64.143.9:80 | http://mvn.runelite.net/com/google/errorprone/error_prone_annotations/2.0.18/error_prone_annotations-2.0.18.jar | US | compressed | 11.7 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3028 | javaw.exe | 213.199.247.21:80 | runelite.site | Tarr Centrum Innowacyjnosci Sp. Zoo. | PL | suspicious |
3028 | javaw.exe | 172.64.143.9:80 | static.runelite.net | Cloudflare Inc | US | shared |
3028 | javaw.exe | 172.64.142.9:80 | static.runelite.net | Cloudflare Inc | US | shared |
3192 | java.exe | 217.163.53.225:80 | oldschool10a.runescape.com | Level 3 Communications, Inc. | GB | unknown |
3192 | java.exe | 91.235.140.148:80 | oldschool.runescape.com | Level 3 Communications, Inc. | GB | suspicious |
3192 | java.exe | 172.64.142.9:443 | static.runelite.net | Cloudflare Inc | US | shared |
3192 | java.exe | 93.184.220.70:443 | pbs.twimg.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3192 | java.exe | 172.64.143.9:443 | static.runelite.net | Cloudflare Inc | US | shared |
3192 | java.exe | 217.163.53.225:43594 | oldschool10a.runescape.com | Level 3 Communications, Inc. | GB | unknown |
3192 | java.exe | 185.178.208.179:80 | runeliterepo.host | Ddos-guard Ltd | RU | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
runelite.site |
| suspicious |
static.runelite.net |
| suspicious |
mvn.runelite.net |
| suspicious |
repo.runelite.net |
| suspicious |
oldschool.runescape.com |
| suspicious |
oldschool10a.runescape.com |
| unknown |
api.runelite.net |
| suspicious |
pbs.twimg.com |
| whitelisted |
oldschool1.runescape.com |
| unknown |
oldschool2a.runescape.com |
| unknown |