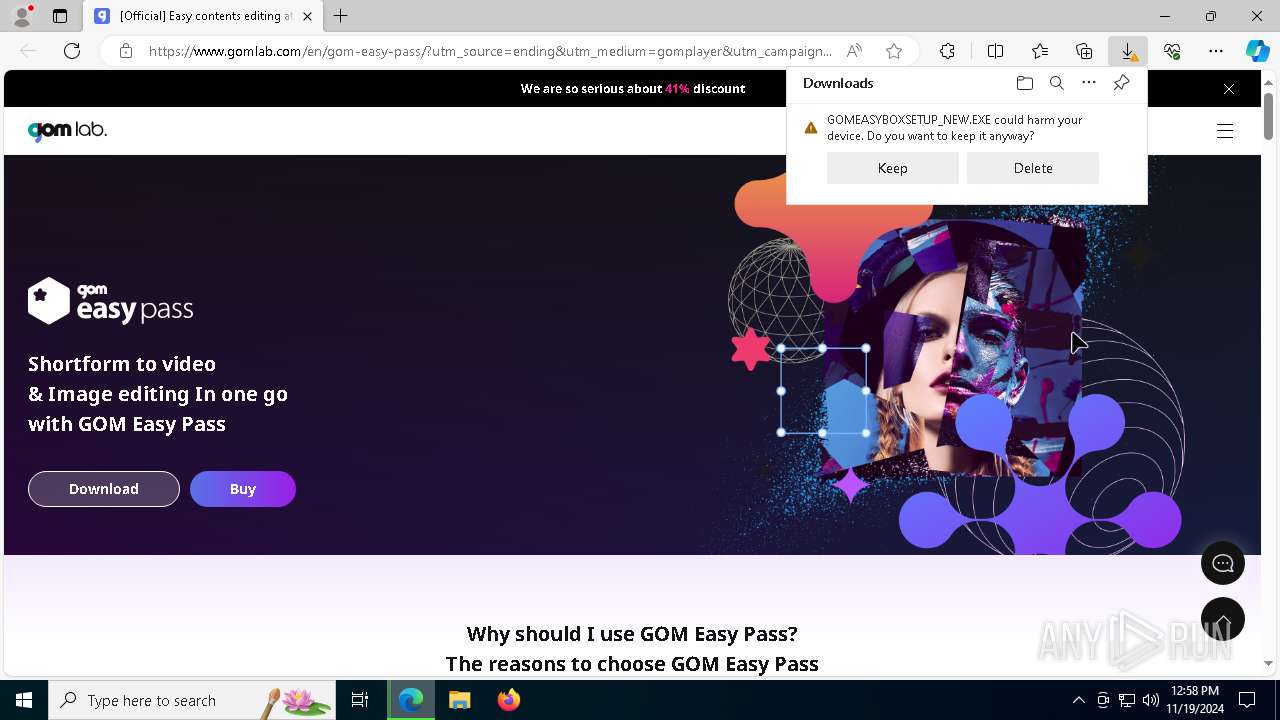
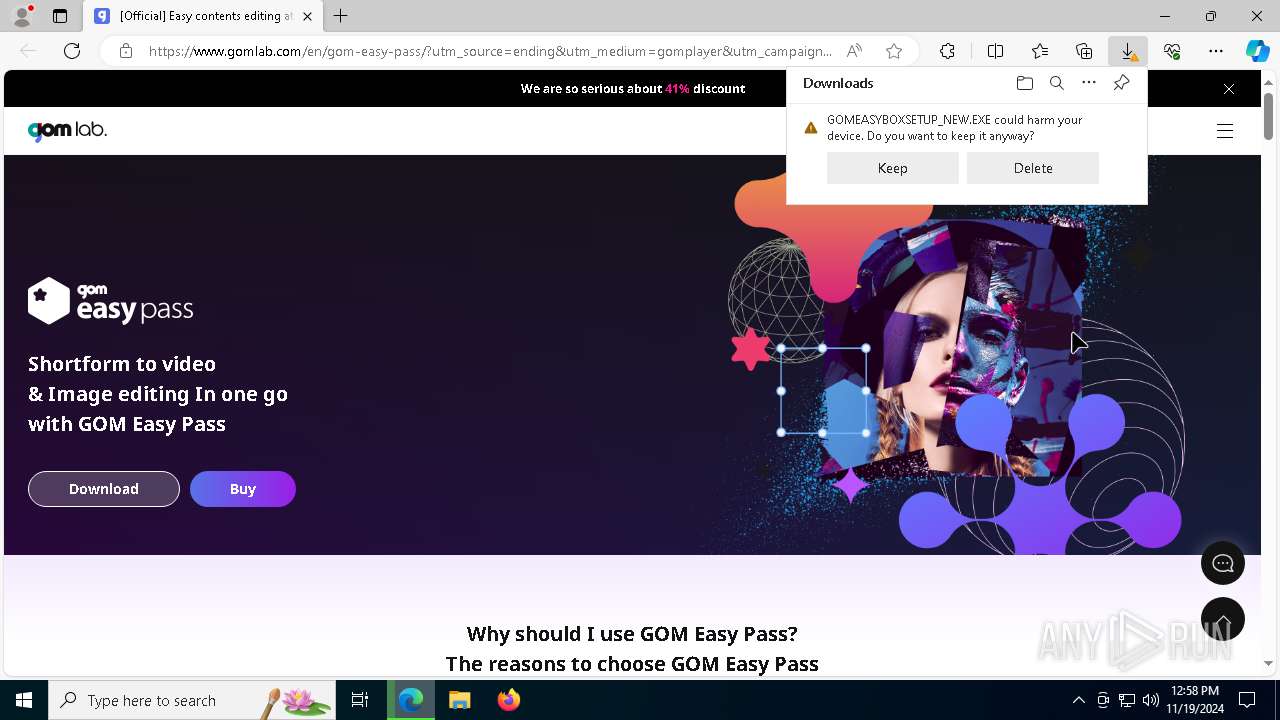
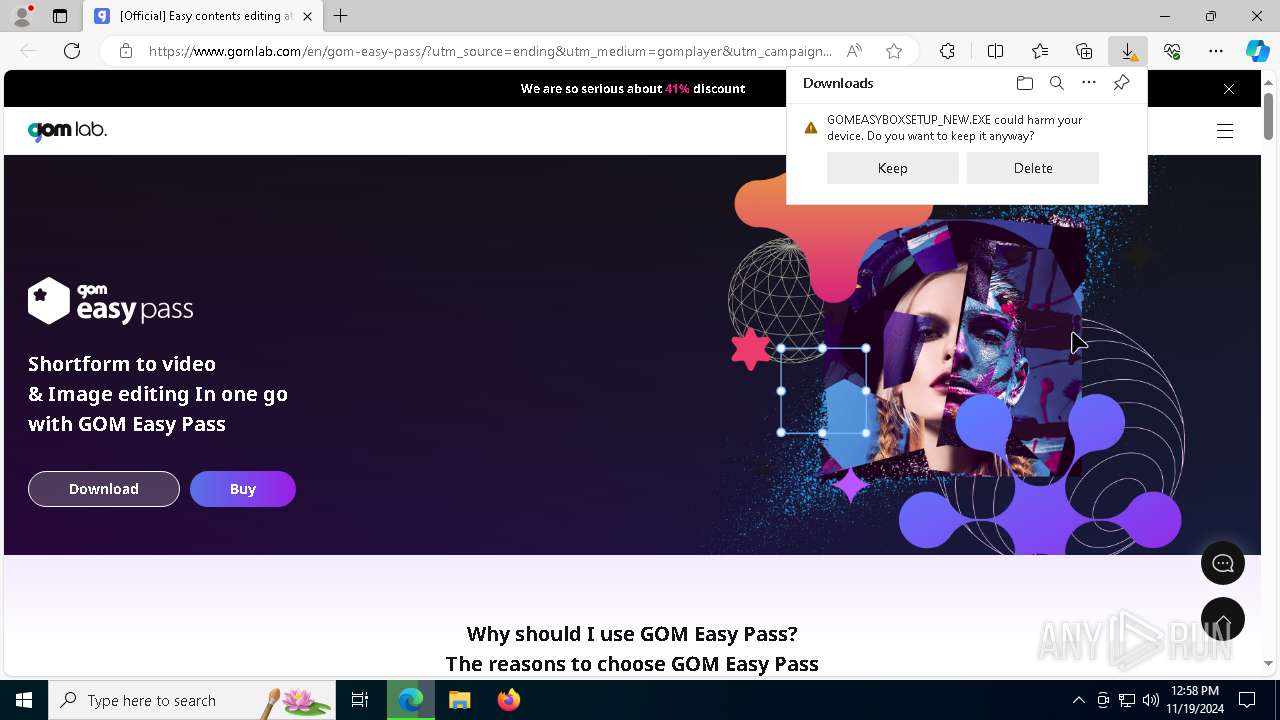
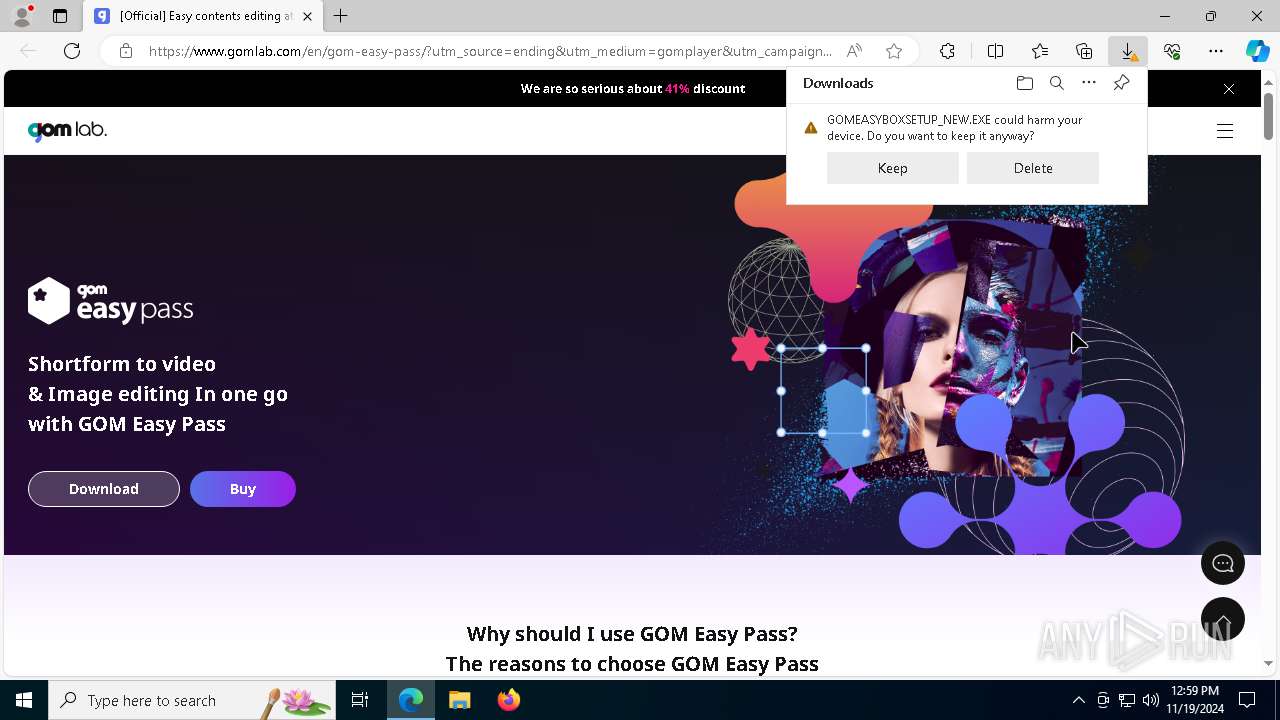
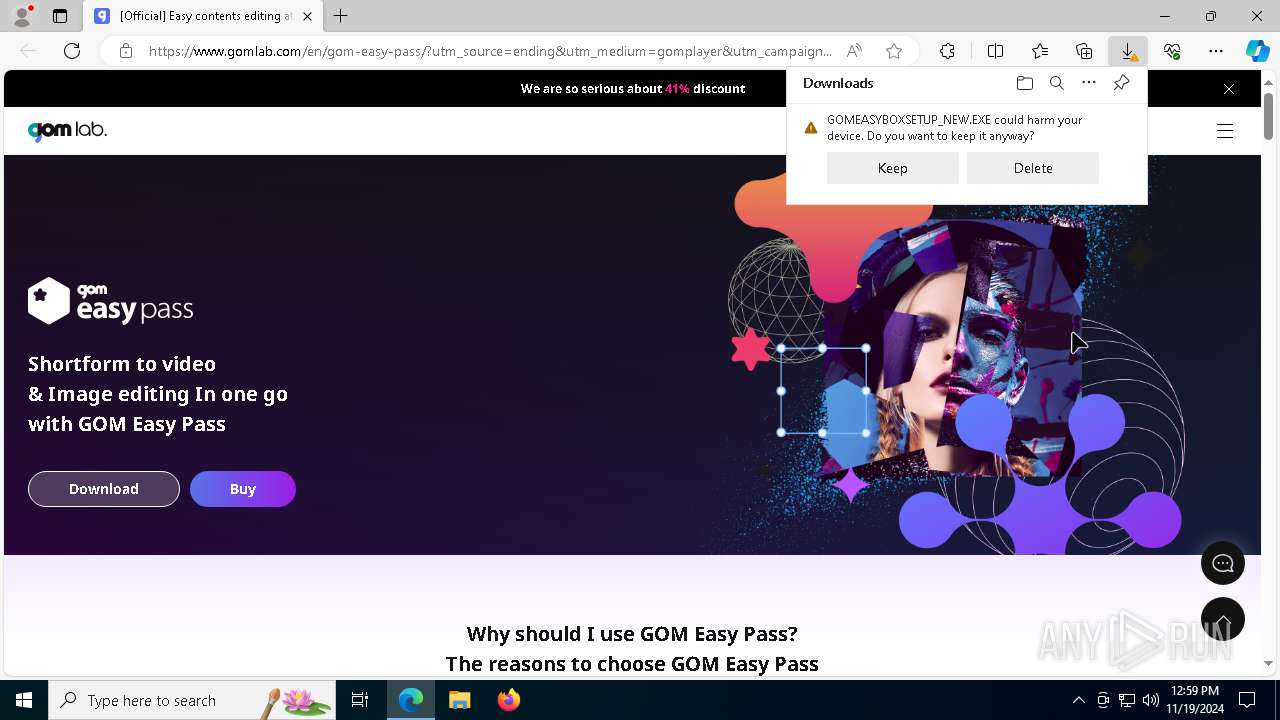
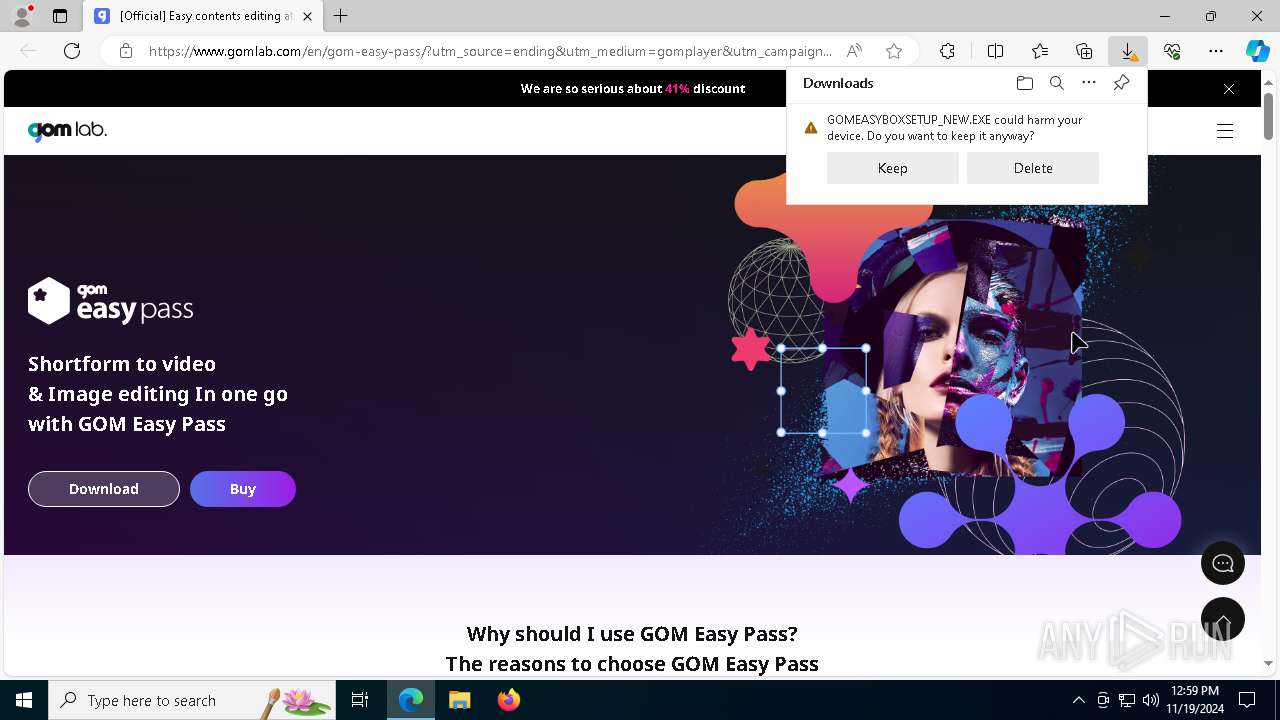
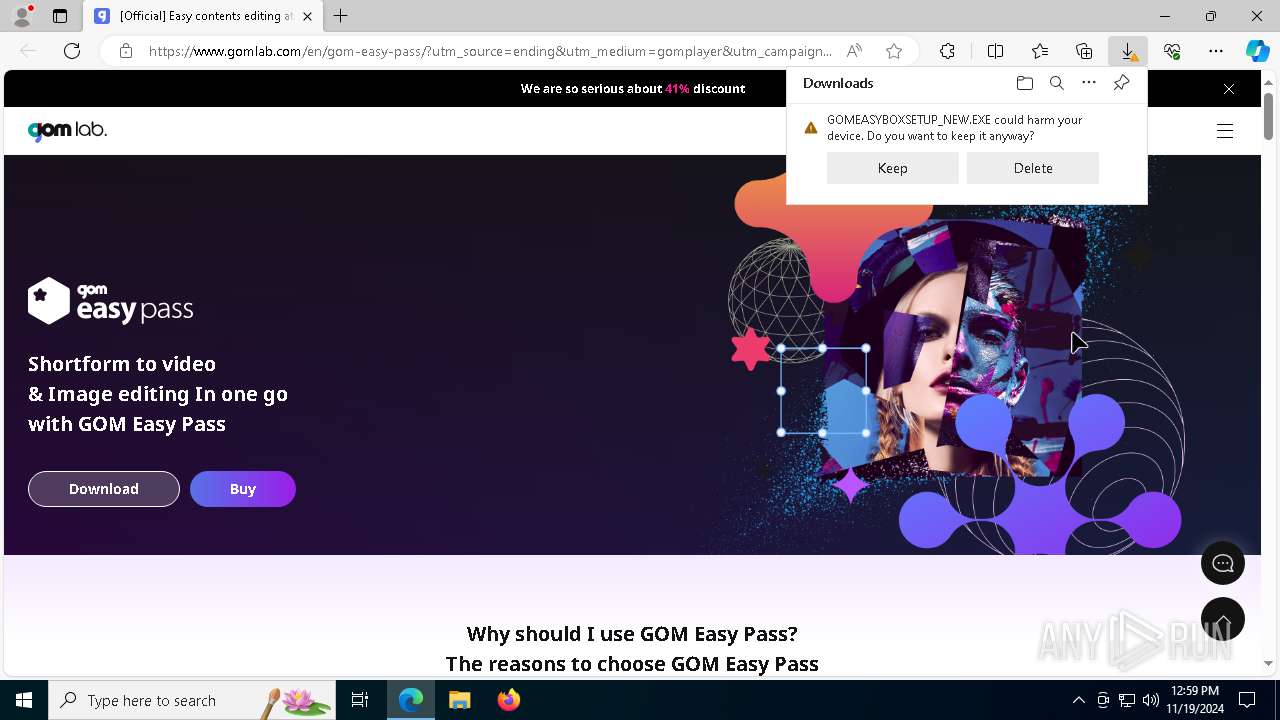
| File name: | 2024-11-19_f7ecab8e4e4d31561a85fae83426a508_bkransomware_floxif_hijackloader |
| Full analysis: | https://app.any.run/tasks/81e4b7c3-df2e-4c2b-8328-e03473b3e028 |
| Verdict: | Malicious activity |
| Analysis date: | November 19, 2024, 12:57:12 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 8 sections |
| MD5: | F7ECAB8E4E4D31561A85FAE83426A508 |
| SHA1: | 5ED0ADF3BD13234AEB6B73E8C458E75B6C6B8E01 |
| SHA256: | 848A30813AF6B5EE7B8C4613CD305DF89A0B1D539C199FE49AFD322F8D3F9BA1 |
| SSDEEP: | 98304:3Sl96U4Eu0Yjr49Hh856GoM6/aRFkoa/4laupLGOUfRA9NnuA044CVxQD+dsZ82X:mobMJ |
MALICIOUS
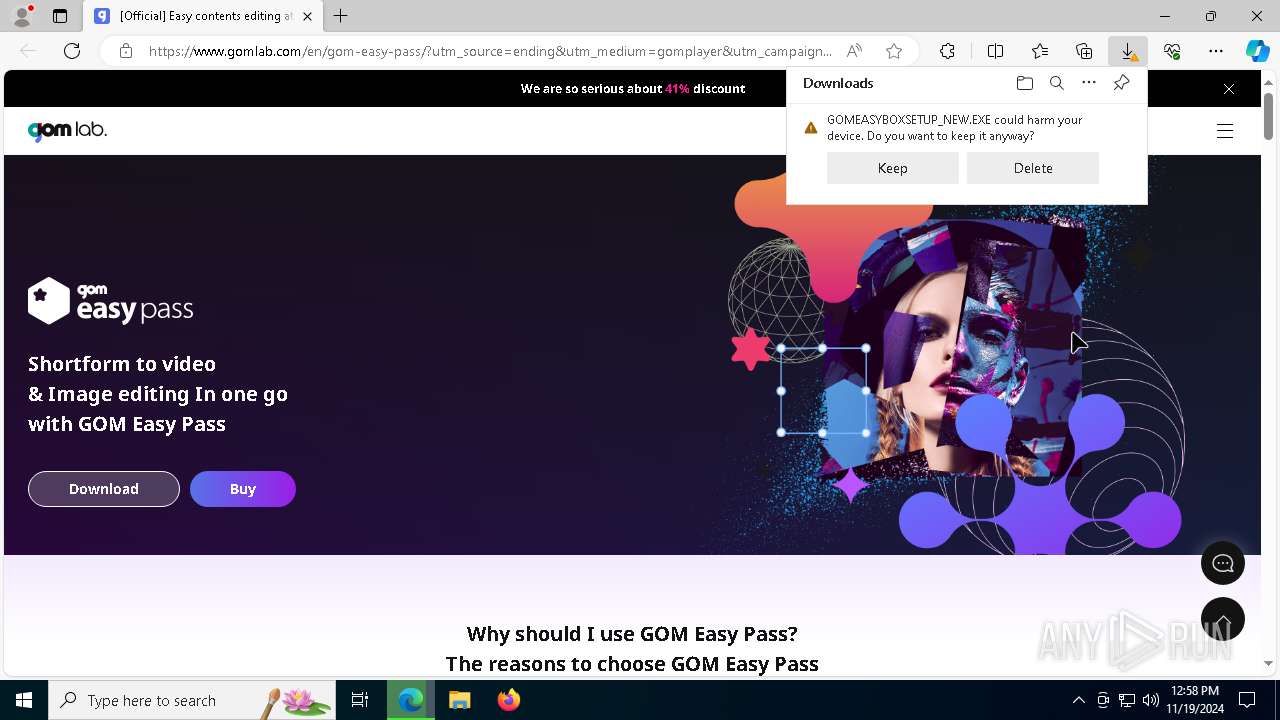
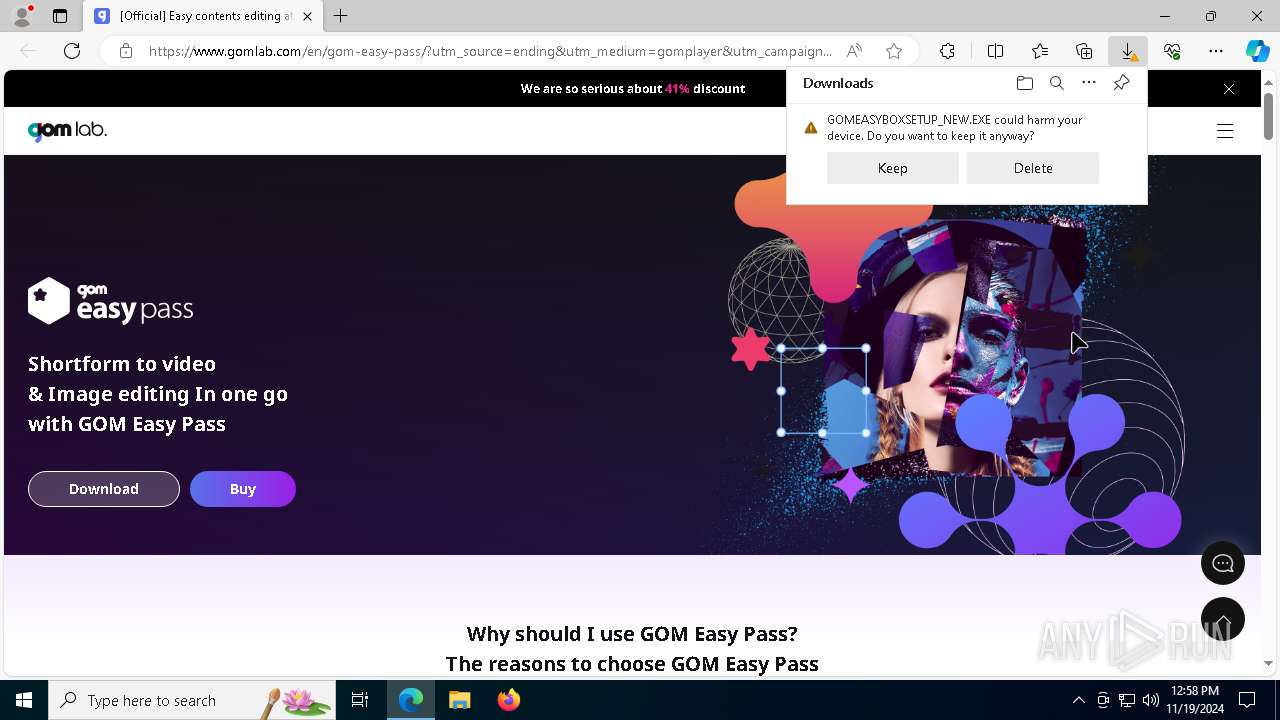
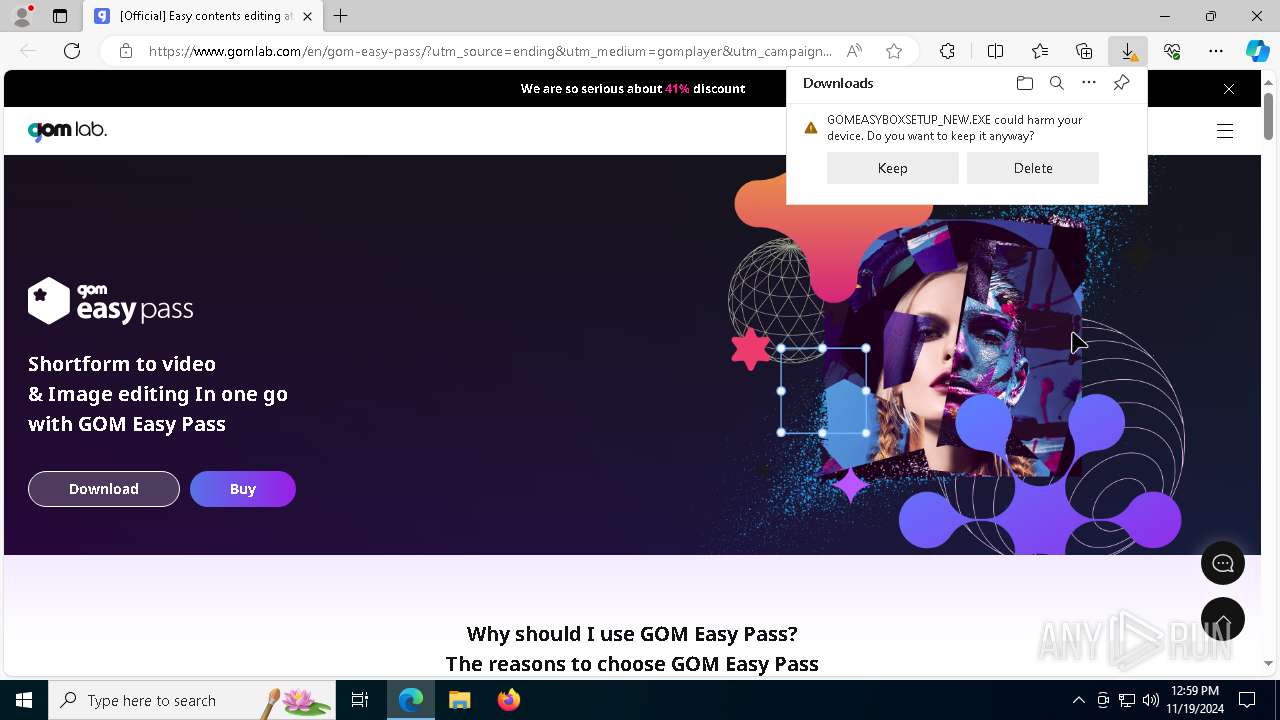
Executing a file with an untrusted certificate
- 2024-11-19_f7ecab8e4e4d31561a85fae83426a508_bkransomware_floxif_hijackloader.exe (PID: 5684)
FLOXIF has been detected (SURICATA)
- 2024-11-19_f7ecab8e4e4d31561a85fae83426a508_bkransomware_floxif_hijackloader.exe (PID: 5684)
Connects to the CnC server
- 2024-11-19_f7ecab8e4e4d31561a85fae83426a508_bkransomware_floxif_hijackloader.exe (PID: 5684)
SUSPICIOUS
Reads security settings of Internet Explorer
- 2024-11-19_f7ecab8e4e4d31561a85fae83426a508_bkransomware_floxif_hijackloader.exe (PID: 5684)
Contacting a server suspected of hosting an CnC
- 2024-11-19_f7ecab8e4e4d31561a85fae83426a508_bkransomware_floxif_hijackloader.exe (PID: 5684)
Process drops legitimate windows executable
- 2024-11-19_f7ecab8e4e4d31561a85fae83426a508_bkransomware_floxif_hijackloader.exe (PID: 5684)
Executable content was dropped or overwritten
- 2024-11-19_f7ecab8e4e4d31561a85fae83426a508_bkransomware_floxif_hijackloader.exe (PID: 5684)
Starts application with an unusual extension
- 2024-11-19_f7ecab8e4e4d31561a85fae83426a508_bkransomware_floxif_hijackloader.exe (PID: 5684)
INFO
Create files in a temporary directory
- 2024-11-19_f7ecab8e4e4d31561a85fae83426a508_bkransomware_floxif_hijackloader.exe (PID: 5684)
Checks proxy server information
- 2024-11-19_f7ecab8e4e4d31561a85fae83426a508_bkransomware_floxif_hijackloader.exe (PID: 5684)
Checks supported languages
- 2024-11-19_f7ecab8e4e4d31561a85fae83426a508_bkransomware_floxif_hijackloader.exe (PID: 5684)
Reads the computer name
- 2024-11-19_f7ecab8e4e4d31561a85fae83426a508_bkransomware_floxif_hijackloader.exe (PID: 5684)
UPX packer has been detected
- 2024-11-19_f7ecab8e4e4d31561a85fae83426a508_bkransomware_floxif_hijackloader.exe (PID: 5684)
Executable content was dropped or overwritten
- msedge.exe (PID: 5308)
- msedge.exe (PID: 1808)
Application launched itself
- msedge.exe (PID: 5308)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:02:19 01:31:56+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 12 |
| CodeSize: | 7898112 |
| InitializedDataSize: | 7235584 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x63d028 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.3.94.5364 |
| ProductVersionNumber: | 2.3.94.5364 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Korean |
| CharacterSet: | Unicode |
| Comments: | - |
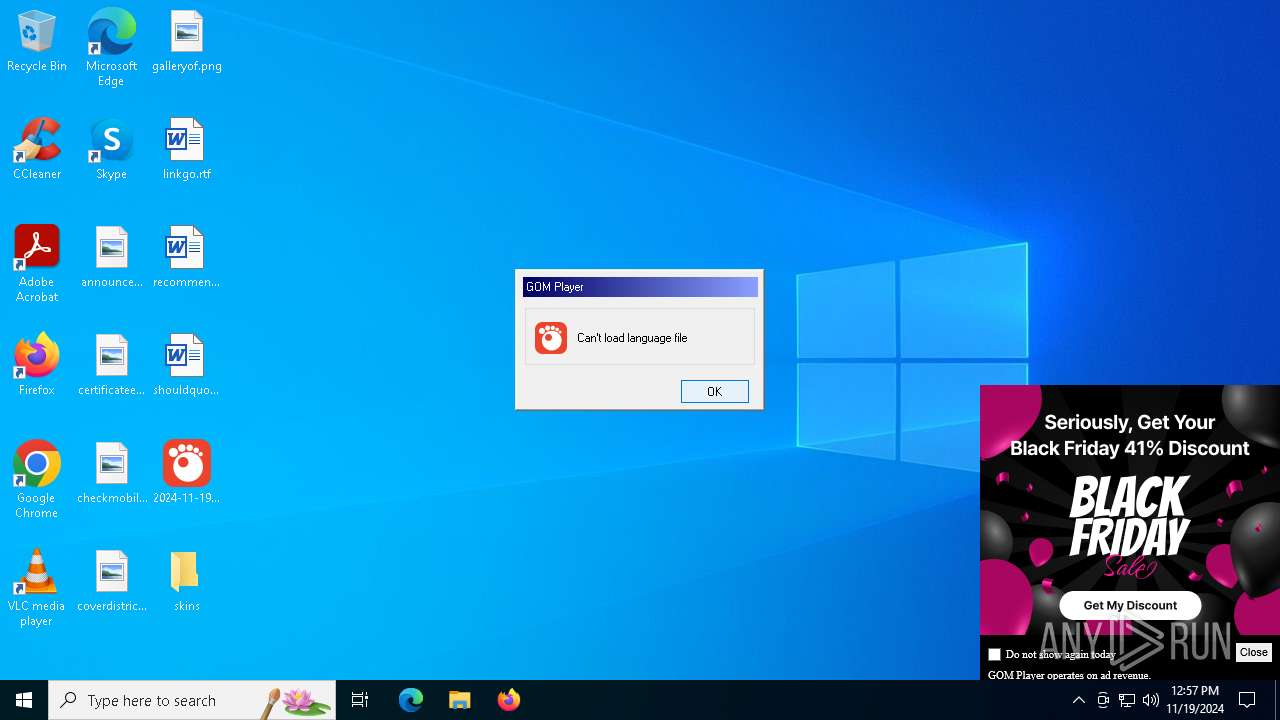
| CompanyName: | GOM & Company |
| FileDescription: | GOM Player |
| FileVersion: | 2, 3, 94, 5364 |
| InternalName: | GOM |
| LegalCopyright: | Copyright 2003 GOM & Company All Rights Reserved. |
| LegalTrademarks: | - |
| OriginalFileName: | GOM.EXE |
| PrivateBuild: | - |
| ProductName: | GOM Player |
| ProductVersion: | 2, 3, 94, 5364 |
| SpecialBuild: | - |
Total processes
165
Monitored processes
49
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Users\admin\AppData\Local\Temp\GOM\Toast.gom" /url=https://mini.gomlab.com/player/html/toast/toast_GLOBAL_N.html /x=65535 /y=65535 /w=300 /h=295 /type=4 /kill=20000 /lastshowtimekey=gom_lst /blockdatekey=gom_bd /newwindowtype=defaultbrowser | C:\Users\admin\AppData\Local\Temp\GOM\Toast.gom | 2024-11-19_f7ecab8e4e4d31561a85fae83426a508_bkransomware_floxif_hijackloader.exe | ||||||||||||
User: admin Company: GOM & Company Integrity Level: MEDIUM Description: Toast Popup Exit code: 0 Version: 1.0.0.5 Modules
| |||||||||||||||
| 908 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=7160 --field-trial-handle=2228,i,7174543495705852492,9542176708251191915,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 3221226029 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1252 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=4640 --field-trial-handle=2228,i,7174543495705852492,9542176708251191915,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1808 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2588 --field-trial-handle=2228,i,7174543495705852492,9542176708251191915,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2380 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4248 --field-trial-handle=2228,i,7174543495705852492,9542176708251191915,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3008 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=8068 --field-trial-handle=2228,i,7174543495705852492,9542176708251191915,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3428 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=18 --mojo-platform-channel-handle=5632 --field-trial-handle=2228,i,7174543495705852492,9542176708251191915,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3508 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_search_indexer.mojom.SearchIndexerInterfaceBroker --lang=en-US --service-sandbox-type=search_indexer --message-loop-type-ui --no-appcompat-clear --mojo-platform-channel-handle=6528 --field-trial-handle=2228,i,7174543495705852492,9542176708251191915,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3876 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7864 --field-trial-handle=2228,i,7174543495705852492,9542176708251191915,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3908 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4172 --field-trial-handle=2228,i,7174543495705852492,9542176708251191915,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
13 627
Read events
12 686
Write events
880
Delete events
61
Modification events
| (PID) Process: | (5684) 2024-11-19_f7ecab8e4e4d31561a85fae83426a508_bkransomware_floxif_hijackloader.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5684) 2024-11-19_f7ecab8e4e4d31561a85fae83426a508_bkransomware_floxif_hijackloader.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5684) 2024-11-19_f7ecab8e4e4d31561a85fae83426a508_bkransomware_floxif_hijackloader.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5684) 2024-11-19_f7ecab8e4e4d31561a85fae83426a508_bkransomware_floxif_hijackloader.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\GRETECH\GOMPLAYER\OPTION |
| Operation: | write | Name: | smver |
Value: 3 | |||
| (PID) Process: | (5684) 2024-11-19_f7ecab8e4e4d31561a85fae83426a508_bkransomware_floxif_hijackloader.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\GRETECH\GOMPLAYER\OPTION |
| Operation: | write | Name: | mode |
Value: 3 | |||
| (PID) Process: | (188) Toast.gom | Key: | HKEY_CURRENT_USER\SOFTWARE\GOM\GOMToast |
| Operation: | write | Name: | gom_lst |
Value: 20241119125732 | |||
| (PID) Process: | (188) Toast.gom | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (188) Toast.gom | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (188) Toast.gom | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5684) 2024-11-19_f7ecab8e4e4d31561a85fae83426a508_bkransomware_floxif_hijackloader.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\GRETECH\GOMPLAYER |
| Operation: | write | Name: | EndingBrowser |
Value: | |||
Executable files
16
Suspicious files
335
Text files
104
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5684 | 2024-11-19_f7ecab8e4e4d31561a85fae83426a508_bkransomware_floxif_hijackloader.exe | C:\Users\admin\AppData\Local\Temp\A1D26E2\B63CF841634.tmp | executable | |
MD5:7740B91AA5877CD86117DB93DC5B0426 | SHA256:44DF3A987AD432EA7942D8923DD2A8E29F3204119274ACE5B0C5181838557564 | |||
| 5684 | 2024-11-19_f7ecab8e4e4d31561a85fae83426a508_bkransomware_floxif_hijackloader.exe | C:\Users\admin\AppData\Local\Temp\conres.dll.000 | text | |
MD5:1130C911BF5DB4B8F7CF9B6F4B457623 | SHA256:EBA08CC8182F379392A97F542B350EA0DBBE5E4009472F35AF20E3D857EAFDF1 | |||
| 5308 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Variations | binary | |
MD5:1C42329800C95BC1DB27E7657711FF1E | SHA256:D58993216FB0CBF52CED6DA4FCAEBFC8FCC7C1A37191954397BA77951B16BE9B | |||
| 5684 | 2024-11-19_f7ecab8e4e4d31561a85fae83426a508_bkransomware_floxif_hijackloader.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8EC9B1D0ABBD7F98B401D425828828CE_3046AF087CC02D0D53E8271E8FC6225D | der | |
MD5:EB3FE1F110062FC14CDDD9D28B2DBCFD | SHA256:CEF514A9ABC0B5D4D94CE42101707C90F3B46B4C51E0F9E6B4CA42A886FED54D | |||
| 5684 | 2024-11-19_f7ecab8e4e4d31561a85fae83426a508_bkransomware_floxif_hijackloader.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C8E534EE129F27D55460CE17FD628216_1130D9B25898B0DB0D4F04DC5B93F141 | der | |
MD5:C5325AF001C52ACA934EADBEA6E052BF | SHA256:9040F3F40AA15886F4EF60141B67E96542AC690A8FD9C9B4D52BDB0CF1B4C773 | |||
| 5684 | 2024-11-19_f7ecab8e4e4d31561a85fae83426a508_bkransomware_floxif_hijackloader.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\698460A0B6E60F2F602361424D832905_7AA1872B10F7F2428A1288E96F0B99FA | binary | |
MD5:9C129F83801107272CB4467C69CA29D4 | SHA256:A760003FA53C17E8590CF87BE92246A3ABEAC1712F47C2D619E895FA2DA5A100 | |||
| 5684 | 2024-11-19_f7ecab8e4e4d31561a85fae83426a508_bkransomware_floxif_hijackloader.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8EC9B1D0ABBD7F98B401D425828828CE_CBECBD5B884BB75B183807EECD99D9AD | binary | |
MD5:3B80AE3D155C6E0A96B6CE519A300950 | SHA256:AC0FC11C5F8A5EC0F853396588BEC95A7C243E92177B64512D33B6795D650AFA | |||
| 5308 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RFef9ad.TMP | — | |
MD5:— | SHA256:— | |||
| 5308 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5684 | 2024-11-19_f7ecab8e4e4d31561a85fae83426a508_bkransomware_floxif_hijackloader.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\698460A0B6E60F2F602361424D832905_8BB23D43DE574E82F2BEE0DF0EC47EEB | der | |
MD5:4302AC33571A665623F83CAA83E9D7B7 | SHA256:85D864FDF43320E3535AD37F3D946A3BD648DF66622CBBCB079B976ABFA7FF41 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
118
TCP/UDP connections
160
DNS requests
158
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4932 | svchost.exe | GET | 200 | 23.48.23.173:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.173:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5024 | RUXIMICS.exe | GET | 200 | 23.48.23.173:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5684 | 2024-11-19_f7ecab8e4e4d31561a85fae83426a508_bkransomware_floxif_hijackloader.exe | GET | 403 | 45.33.2.79:80 | http://www.aieov.com/logo.gif | unknown | — | — | malicious |
4932 | svchost.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5684 | 2024-11-19_f7ecab8e4e4d31561a85fae83426a508_bkransomware_floxif_hijackloader.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
5684 | 2024-11-19_f7ecab8e4e4d31561a85fae83426a508_bkransomware_floxif_hijackloader.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
5684 | 2024-11-19_f7ecab8e4e4d31561a85fae83426a508_bkransomware_floxif_hijackloader.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAsItdjkZt4h6uHSonYxKRY%3D | unknown | — | — | whitelisted |
5684 | 2024-11-19_f7ecab8e4e4d31561a85fae83426a508_bkransomware_floxif_hijackloader.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEAEkCvseOAuKFvFLcZ3008A%3D | unknown | — | — | whitelisted |
5684 | 2024-11-19_f7ecab8e4e4d31561a85fae83426a508_bkransomware_floxif_hijackloader.exe | GET | 404 | 54.196.85.38:80 | http://log.gomlab.com/player/adstrigger?usmid=GOMPLAYER_READ_FAIL&build=&appver=2.3.94.5364&bit=32bit&os=windows1064bit&lang=eng&skin=users&launching=producticon&browser=msedge&type=endingbrowser | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5024 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4932 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.173:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4932 | svchost.exe | 23.48.23.173:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5024 | RUXIMICS.exe | 23.48.23.173:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4932 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5684 | 2024-11-19_f7ecab8e4e4d31561a85fae83426a508_bkransomware_floxif_hijackloader.exe | 45.33.2.79:80 | www.aieov.com | Linode, LLC | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
5isohu.com |
| whitelisted |
www.aieov.com |
| malicious |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
playinfo.gomlab.com |
| whitelisted |
log.gomlab.com |
| unknown |
mini.gomlab.com |
| unknown |
Threats
4 ETPRO signatures available at the full report