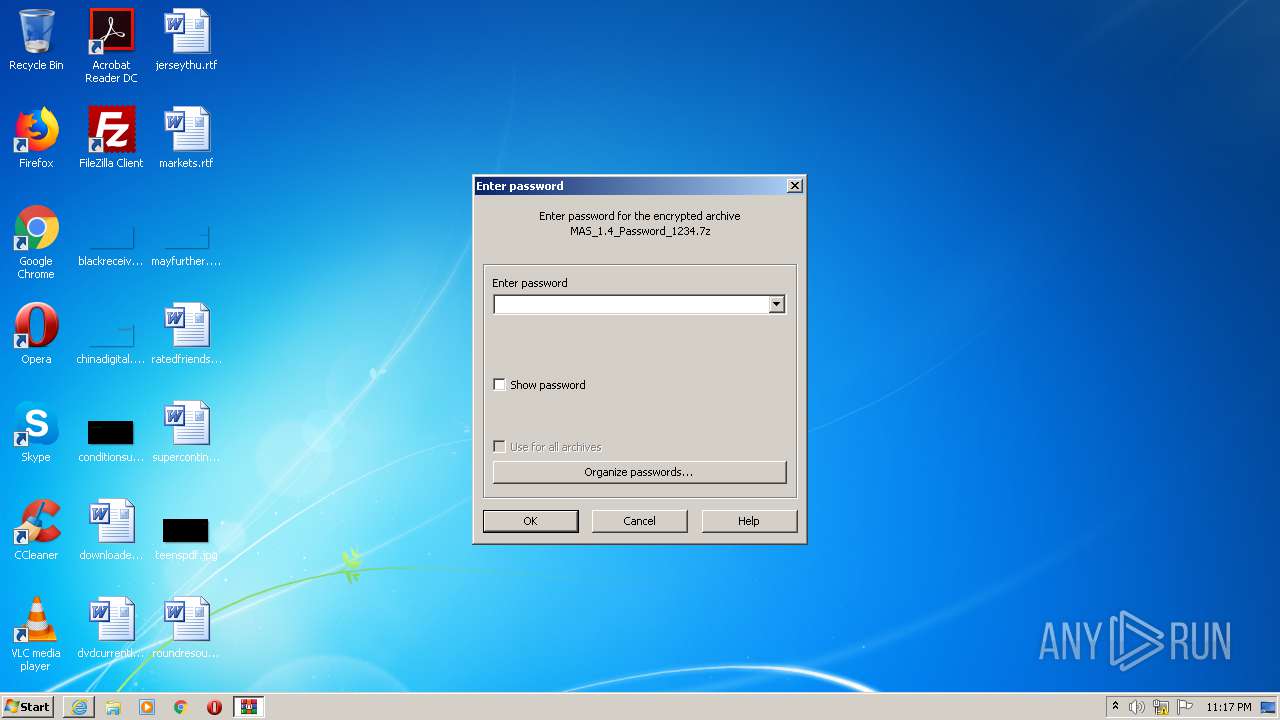
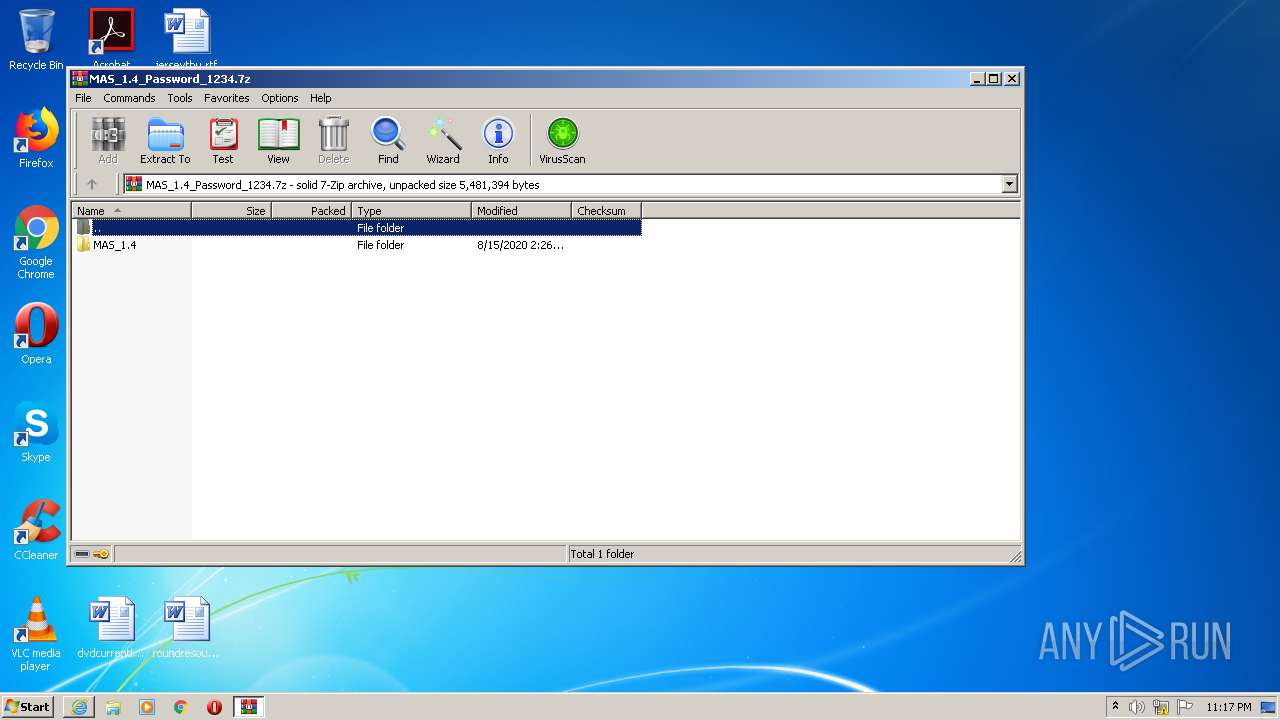
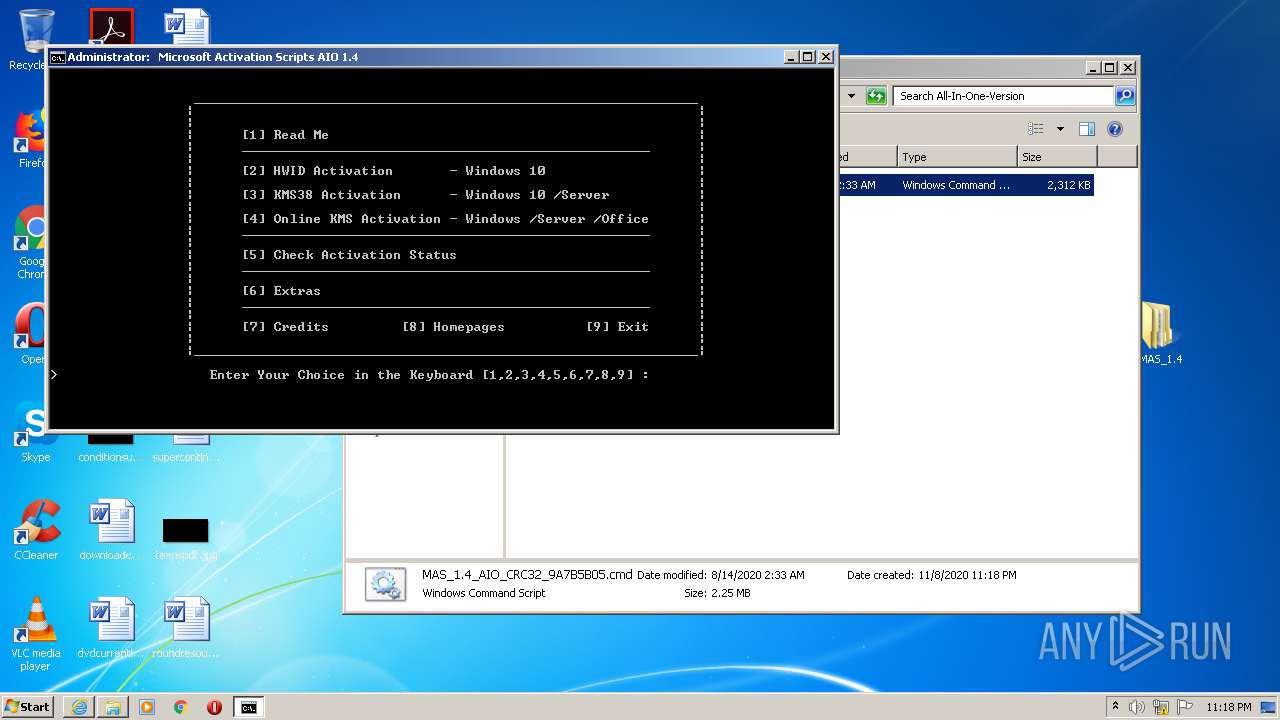
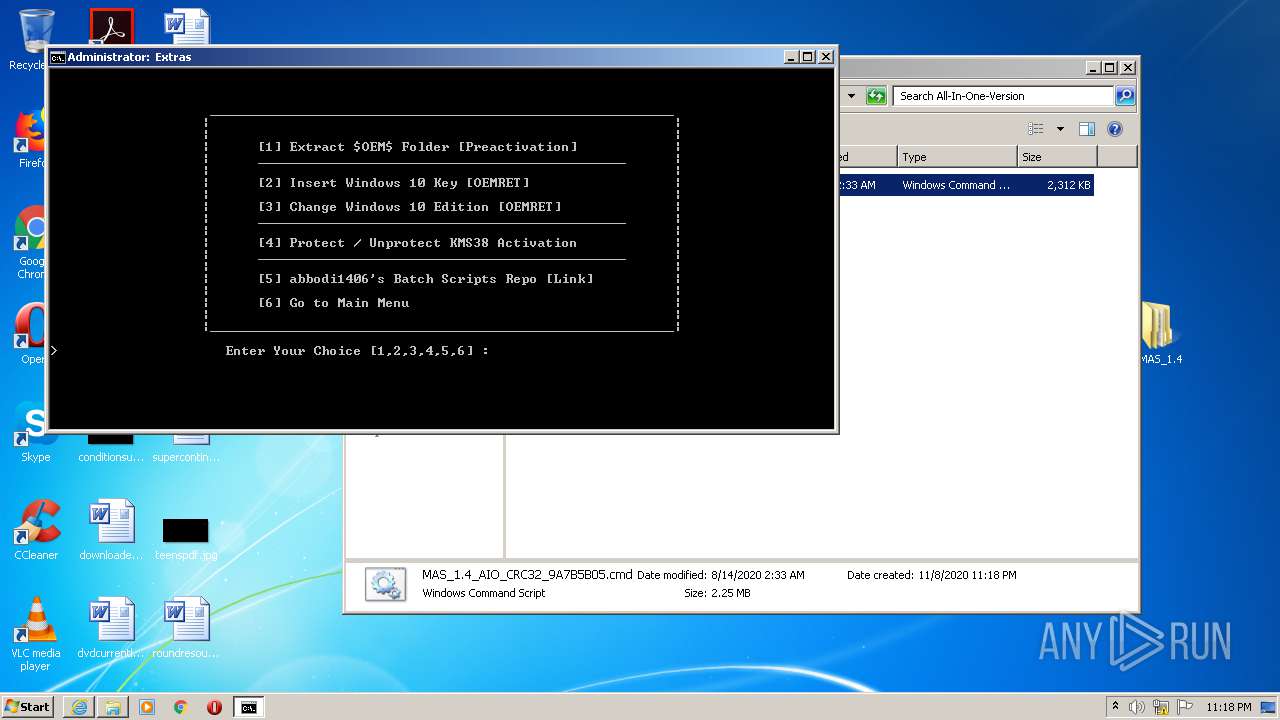
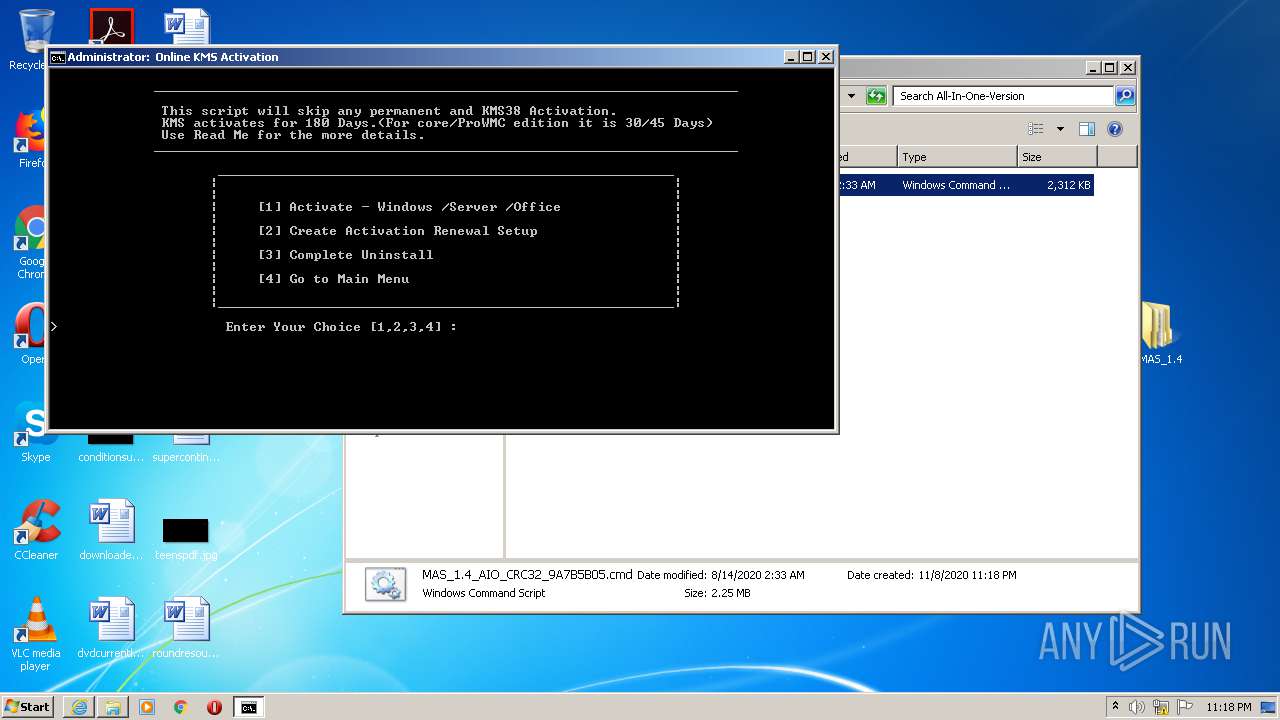
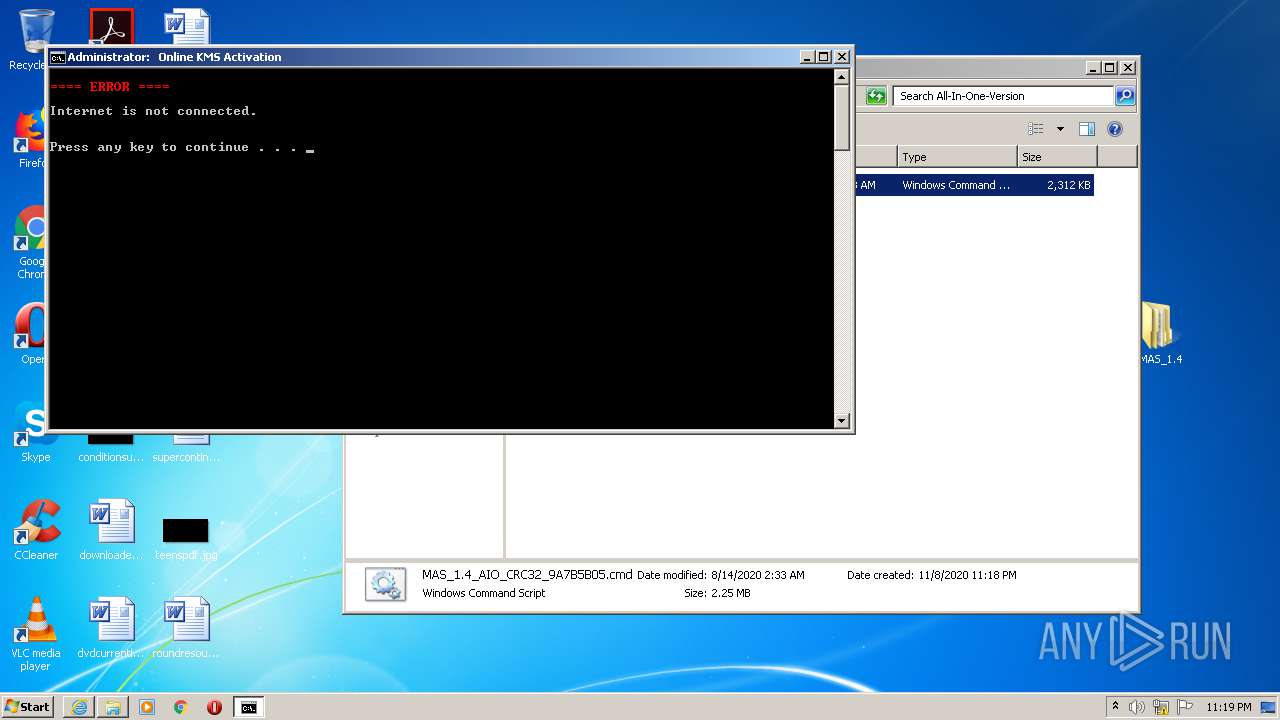
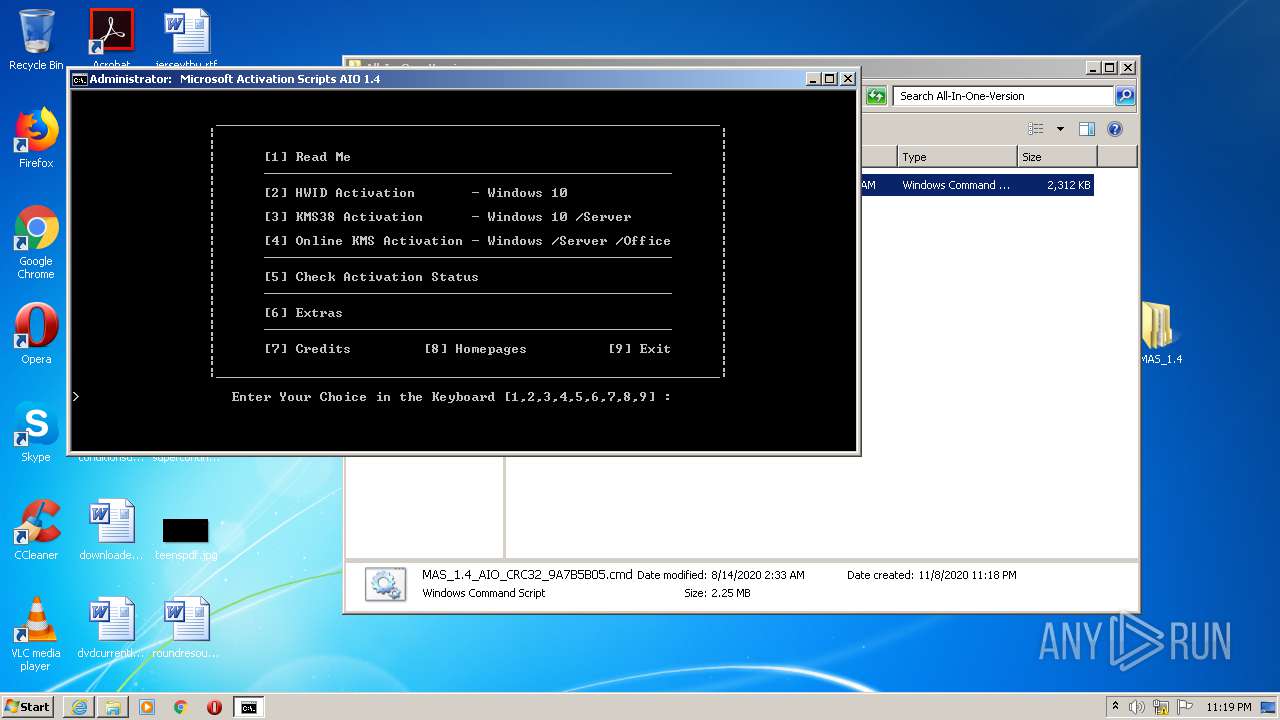
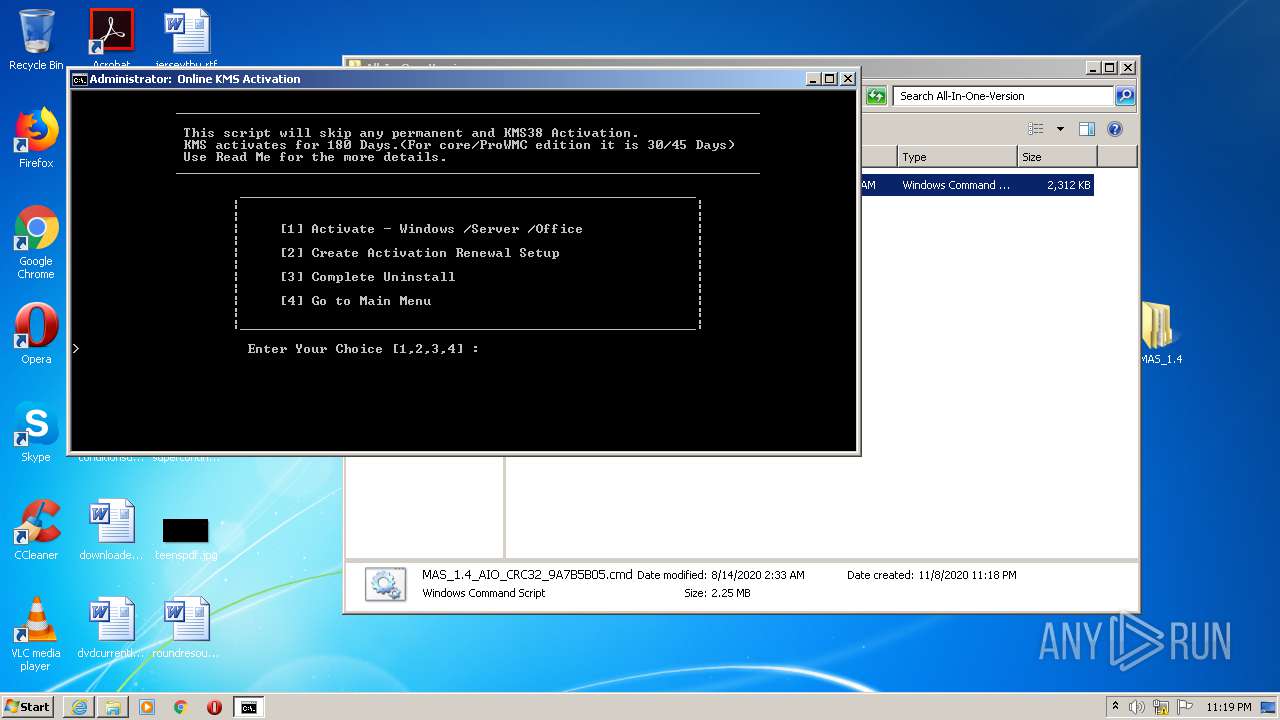
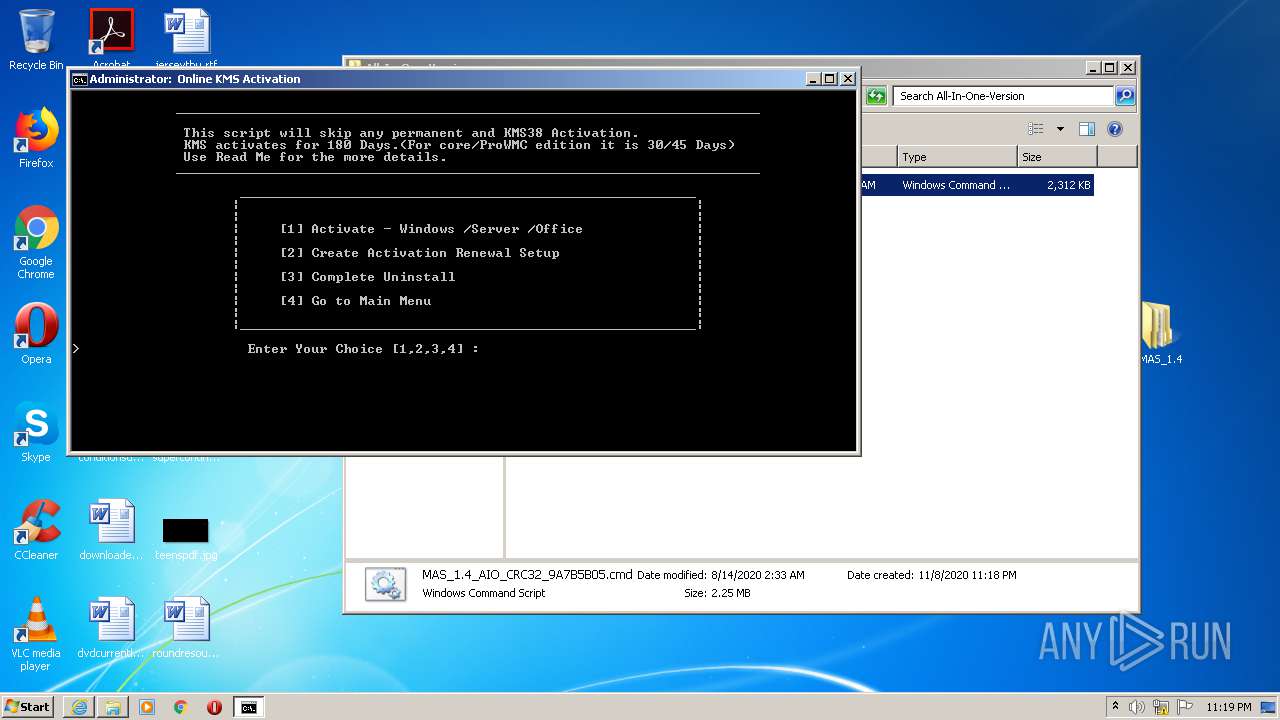
| URL: | https://github.com/massgravel/Microsoft-Activation-Scripts/releases/download/1.4/MAS_1.4_Password_1234.7z |
| Full analysis: | https://app.any.run/tasks/419f8071-969c-4134-afa7-b61251334301 |
| Verdict: | Malicious activity |
| Analysis date: | November 08, 2020, 23:17:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 897944509CD4DC505345AA056C5DE1B3 |
| SHA1: | 3AAE5C3C3C6139B09024B645A6C0077C7A25727F |
| SHA256: | 8477BBF103F66AEF837AC271389A6FE36603390D250D9E8B88751129FE690536 |
| SSDEEP: | 3:N8tEd4PKoHXuukGR3RLLLGXUoKkCU9yeEsn:2uuPKzukGv/LGXU169yBsn |
MALICIOUS
Executes PowerShell scripts
- cmd.exe (PID: 2112)
- cmd.exe (PID: 4048)
- cmd.exe (PID: 2792)
- cmd.exe (PID: 1868)
Starts Visual C# compiler
- powershell.exe (PID: 632)
- powershell.exe (PID: 2400)
SUSPICIOUS
Application launched itself
- cmd.exe (PID: 1768)
- cmd.exe (PID: 2112)
- cmd.exe (PID: 4048)
- cmd.exe (PID: 2792)
- cmd.exe (PID: 1868)
Uses RUNDLL32.EXE to load library
- cscript.exe (PID: 748)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 2112)
- cmd.exe (PID: 1768)
- cmd.exe (PID: 4048)
- cmd.exe (PID: 2700)
- cmd.exe (PID: 2792)
- cmd.exe (PID: 1868)
- cmd.exe (PID: 3084)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3540)
- expand.exe (PID: 2436)
- expand.exe (PID: 3288)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 1768)
- cmd.exe (PID: 2112)
- cscript.exe (PID: 748)
- cmd.exe (PID: 4048)
- cmd.exe (PID: 2792)
- cmd.exe (PID: 1868)
Executes scripts
- cmd.exe (PID: 1768)
Starts CHOICE.EXE (used to create a delay)
- cmd.exe (PID: 2112)
- cmd.exe (PID: 2792)
Creates files in the user directory
- powershell.exe (PID: 2820)
- powershell.exe (PID: 632)
- powershell.exe (PID: 1796)
- powershell.exe (PID: 4056)
- powershell.exe (PID: 2844)
- powershell.exe (PID: 2400)
- powershell.exe (PID: 2960)
- powershell.exe (PID: 2716)
- powershell.exe (PID: 2232)
- powershell.exe (PID: 3728)
Creates files in the Windows directory
- powershell.exe (PID: 632)
- expand.exe (PID: 2436)
- powershell.exe (PID: 1796)
- powershell.exe (PID: 2400)
- expand.exe (PID: 3288)
- powershell.exe (PID: 2960)
Removes files from Windows directory
- expand.exe (PID: 2436)
- powershell.exe (PID: 632)
- cmd.exe (PID: 2792)
- expand.exe (PID: 3288)
- powershell.exe (PID: 2400)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 2328)
- iexplore.exe (PID: 524)
Application launched itself
- iexplore.exe (PID: 2328)
Manual execution by user
- cmd.exe (PID: 1768)
- cmd.exe (PID: 2792)
Changes internet zones settings
- iexplore.exe (PID: 2328)
Creates files in the user directory
- iexplore.exe (PID: 524)
- iexplore.exe (PID: 2328)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2328)
Changes settings of System certificates
- iexplore.exe (PID: 2328)
Reads settings of System Certificates
- iexplore.exe (PID: 2328)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2328)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
103
Monitored processes
57
Malicious processes
7
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 524 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2328 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 568 | reg query HKU\S-1-5-19 | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
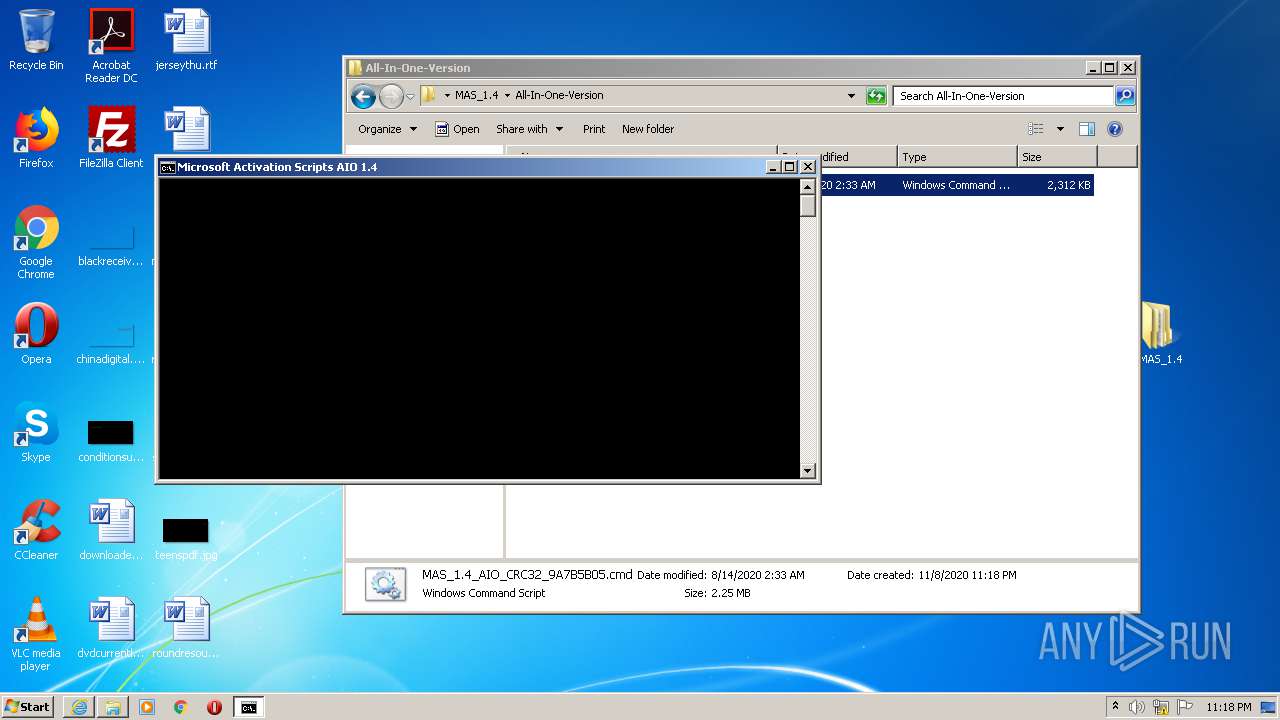
| 632 | powershell "$f=[io.file]::ReadAllText('C:\Users\admin\Desktop\MAS_1.4\All-In-One-Version\MAS_1.4_AIO_CRC32_9A7B5B05.cmd') -split ':cleanospp\:.*';iex ($f[1]);X 1;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 668 | timeout /t 1 | C:\Windows\system32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 748 | cscript //NoLogo "C:\Users\admin\AppData\Local\Temp\admin.vbs" /File:"C:\Users\admin\Desktop\MAS_1.4\All-In-One-Version\MAS_1.4_AIO_CRC32_9A7B5B05.cmd" -el | C:\Windows\system32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 996 | reg query HKU\S-1-5-19 | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1016 | choice /C:123456789 /N /M "> Enter Your Choice in the Keyboard [1,2,3,4,5,6,7,8,9] : " | C:\Windows\system32\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Offers the user a choice Exit code: 4 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1176 | mode con cols=98 lines=30 | C:\Windows\system32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1232 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES96D4.tmp" "c:\Users\admin\AppData\Local\Temp\CSC96D3.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.4940 (Win7SP1.050727-5400) Modules
| |||||||||||||||
| 1288 | choice /C:1234 /N /M "> Enter Your Choice [1,2,3,4] : " | C:\Windows\system32\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Offers the user a choice Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
4 410
Read events
3 767
Write events
642
Delete events
1
Modification events
| (PID) Process: | (2328) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 1841946496 | |||
| (PID) Process: | (2328) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30848549 | |||
| (PID) Process: | (2328) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2328) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2328) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2328) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2328) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2328) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A5000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2328) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2328) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
11
Suspicious files
41
Text files
29
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 524 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab9BC9.tmp | — | |
MD5:— | SHA256:— | |||
| 524 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar9BCA.tmp | — | |
MD5:— | SHA256:— | |||
| 524 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\CH8BIGW1.txt | — | |
MD5:— | SHA256:— | |||
| 2328 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF38C514969631F4BA.TMP | — | |
MD5:— | SHA256:— | |||
| 2328 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\MAS_1.4_Password_1234.7z.cprywjb.partial:Zone.Identifier | — | |
MD5:— | SHA256:— | |||
| 524 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\35DDEDF268117918D1D277A171D8DF7B_B00CE8D5D4CF0E959CFDB61F636A135D | binary | |
MD5:— | SHA256:— | |||
| 524 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_EE9DB89C3D6A328B5FEAFF0ED3C77874 | der | |
MD5:— | SHA256:— | |||
| 524 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EDC238BFF48A31D55A97E1E93892934B_C20E0DA2D0F89FE526E1490F4A2EE5AB | binary | |
MD5:— | SHA256:— | |||
| 524 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\35DDEDF268117918D1D277A171D8DF7B_B00CE8D5D4CF0E959CFDB61F636A135D | der | |
MD5:— | SHA256:— | |||
| 524 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EDC238BFF48A31D55A97E1E93892934B_C20E0DA2D0F89FE526E1490F4A2EE5AB | der | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
13
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2328 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
2328 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
524 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | US | der | 471 b | whitelisted |
524 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAGC%2BAmOouYmuRo7J4Qfua8%3D | US | der | 1.47 Kb | whitelisted |
524 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEAVXyAsoJoOhewoRRJMpa3k%3D | US | der | 471 b | whitelisted |
2328 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
524 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTuqL92L3tjkN67RNFF%2FEdvT6NEzAQUwBKyKHRoRmfpcCV0GgBFWwZ9XEQCEAgt9o7pxpMVvr9yB5s4EP0%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2328 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2328 | iexplore.exe | 204.79.197.200:443 | ieonline.microsoft.com | Microsoft Corporation | US | whitelisted |
524 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2328 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
524 | iexplore.exe | 52.216.28.204:443 | github-production-release-asset-2e65be.s3.amazonaws.com | Amazon.com, Inc. | US | shared |
524 | iexplore.exe | 140.82.121.4:443 | github.com | — | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
github.com |
| malicious |
ocsp.digicert.com |
| whitelisted |
github-production-release-asset-2e65be.s3.amazonaws.com |
| shared |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
csc.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|