| File name: | independert.msi |
| Full analysis: | https://app.any.run/tasks/265b359c-6bbf-4f7a-94fa-091dabafcf1e |
| Verdict: | Malicious activity |
| Analysis date: | December 07, 2024, 21:41:55 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
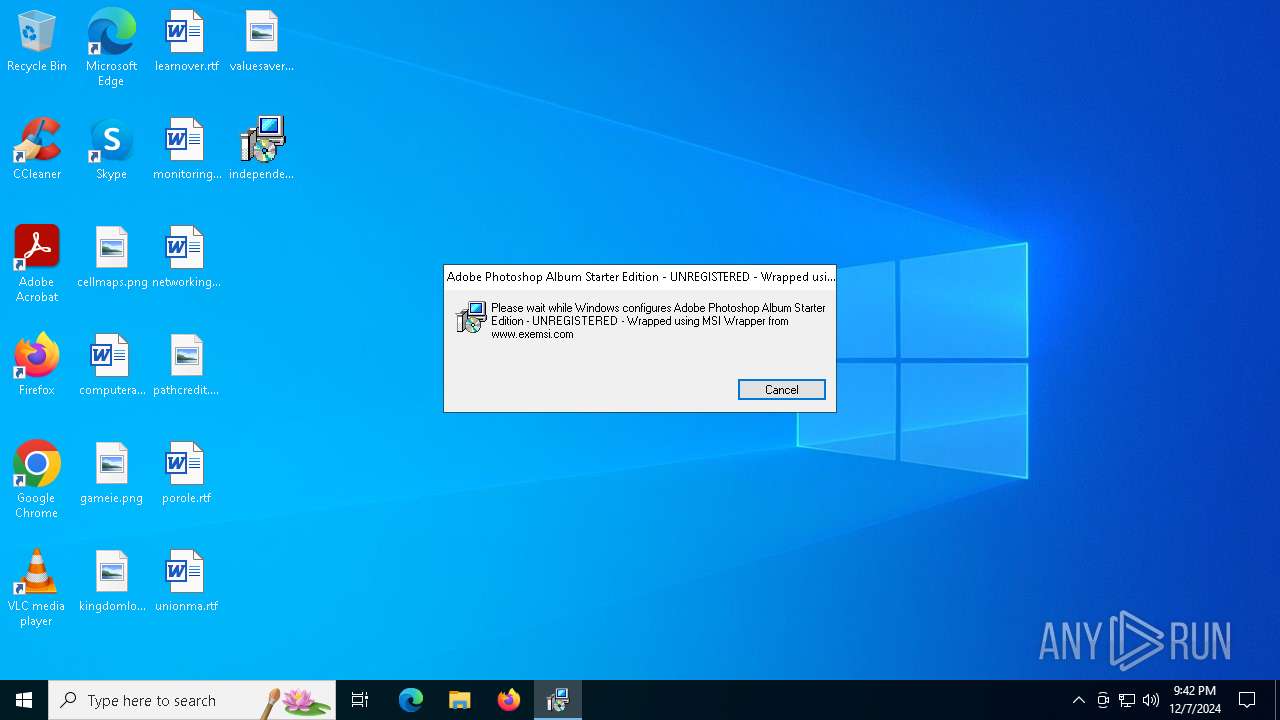
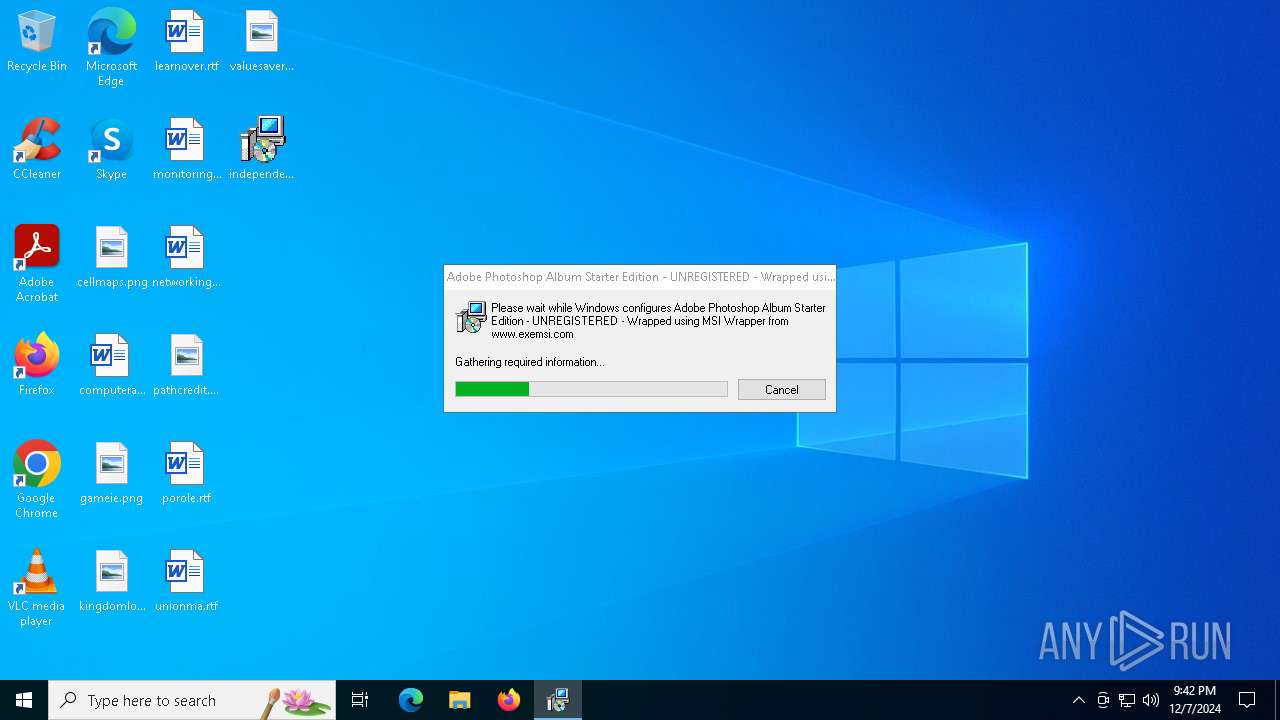
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Code page: 1252, Title: Adobe Photoshop Album Starter Edition - UNREGISTERED - Wrapped using MSI Wrapper from www.exemsi.com 3.2.0.12228, Subject: Adobe Photoshop Album Starter Edition - UNREGISTERED - Wrapped using MSI Wrapper from www.exemsi.com, Author: Adobe Systems Incorporated, Keywords: Installer, Template: Intel;1033, Revision Number: {D07707F8-A6C1-4451-9ECB-911D62F0C679}, Create Time/Date: Sat Jul 23 12:01:26 2022, Last Saved Time/Date: Sat Jul 23 12:01:26 2022, Number of Pages: 200, Number of Words: 12, Name of Creating Application: MSI Wrapper (10.0.51.0), Security: 2 |
| MD5: | 484BEA10F5D2A0C4BDFA342E133033C6 |
| SHA1: | 6860971D489198DF13C64A295999BA3CC7C9C654 |
| SHA256: | 846F339F39E82F358FE5D0985AFDE119563754C9A8030DC237EAC1A963A8BBF4 |
| SSDEEP: | 98304:nU305CHdPQOinvYWWCSbpx2sBFmh5TV+UHqbMGHy+pz3FpjHRycPNGoe8N+expxL:nM3XTJs |
MALICIOUS
Executing a file with an untrusted certificate
- apdproxy.exe (PID: 1580)
XORed URL has been found (YARA)
- msiexec.exe (PID: 6264)
- msiexec.exe (PID: 6380)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 6428)
The process drops C-runtime libraries
- expand.exe (PID: 6180)
Executable content was dropped or overwritten
- apdproxy.exe (PID: 1580)
- expand.exe (PID: 6180)
Process drops legitimate windows executable
- expand.exe (PID: 6180)
Unpacks CAB file
- expand.exe (PID: 6180)
Starts the AutoIt3 executable file
- apdproxy.exe (PID: 1580)
INFO
An automatically generated document
- msiexec.exe (PID: 6264)
Reads the computer name
- msiexec.exe (PID: 6380)
Checks supported languages
- msiexec.exe (PID: 6380)
Manages system restore points
- SrTasks.exe (PID: 7044)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6380)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| Title: | Adobe Photoshop Album Starter Edition - UNREGISTERED - Wrapped using MSI Wrapper from www.exemsi.com 3.2.0.12228 |
|---|---|
| Subject: | Adobe Photoshop Album Starter Edition - UNREGISTERED - Wrapped using MSI Wrapper from www.exemsi.com |
| Author: | Adobe Systems Incorporated |
| Keywords: | Installer |
| Template: | Intel;1033 |
| RevisionNumber: | {D07707F8-A6C1-4451-9ECB-911D62F0C679} |
| CreateDate: | 2022:07:23 12:01:26 |
| ModifyDate: | 2022:07:23 12:01:26 |
| Pages: | 200 |
| Words: | 12 |
| Software: | MSI Wrapper (10.0.51.0) |
| Security: | Read-only recommended |
| CodePage: | Windows Latin 1 (Western European) |
| LocaleIndicator: | 1033 |
| Company: | Adobe Systems Incorporated |
Total processes
130
Monitored processes
10
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1580 | "C:\Users\admin\AppData\Local\Temp\MW-22fb7a87-fa4e-44e9-a83d-e3fde51db22b\files\apdproxy.exe" | C:\Users\admin\AppData\Local\Temp\MW-22fb7a87-fa4e-44e9-a83d-e3fde51db22b\files\apdproxy.exe | msiexec.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Photoshop Album Starter Edition 3.2 component Exit code: 0 Version: 3.2.0.77764 Modules
| |||||||||||||||
| 3780 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | expand.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6180 | "C:\WINDOWS\system32\EXPAND.EXE" -R files.cab -F:* files | C:\Windows\SysWOW64\expand.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: LZ Expansion Utility Exit code: 0 Version: 5.00 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6216 | "c:\temp\Autoit3.exe" c:\temp\script.au3 | C:\temp\Autoit3.exe | — | apdproxy.exe | |||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script Exit code: 0 Version: 3, 3, 14, 5 Modules
| |||||||||||||||
| 6264 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\Desktop\independert.msi | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 1603 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6380 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6428 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7044 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7056 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7128 | C:\Windows\syswow64\MsiExec.exe -Embedding 1A1029F6E2D44ECB0C5E3DDF1BA6C41F | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 715
Read events
3 532
Write events
170
Delete events
13
Modification events
| (PID) Process: | (6380) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 48000000000000004A4DFDDCF048DB01EC1800000C190000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6380) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 48000000000000004A4DFDDCF048DB01EC1800000C190000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6380) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 48000000000000007A1A5ADDF048DB01EC1800000C190000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6380) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 48000000000000007A1A5ADDF048DB01EC1800000C190000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6380) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 48000000000000006BE65EDDF048DB01EC1800000C190000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6380) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000C8FE65DDF048DB01EC1800000C190000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6428) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000DE010DDEF048DB011C1900003C190000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6428) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000AA510FDEF048DB011C190000D4190000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6428) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000AA510FDEF048DB011C19000038190000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6428) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000AA510FDEF048DB011C190000DC190000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
12
Suspicious files
16
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6380 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 6380 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:B478C1C85F24C193D37C02F9619F391C | SHA256:F0063638B20701AC0BE5A83D42757F3A3F4FBE18719C4D9335764C708F729355 | |||
| 6180 | expand.exe | C:\Users\admin\AppData\Local\Temp\MW-22fb7a87-fa4e-44e9-a83d-e3fde51db22b\files\apdboot.dll | executable | |
MD5:7514FA4D5D1162F631ED5FEA0884C0F4 | SHA256:E1F5396D6C9E0D82C45FB48C723460709706398078546BCA83E123CA9EB4036F | |||
| 6380 | msiexec.exe | C:\Windows\Installer\MSIBB45.tmp | executable | |
MD5:D82B3FB861129C5D71F0CD2874F97216 | SHA256:107B32C5B789BE9893F24D5BFE22633D25B7A3CAE80082EF37B30E056869CC5C | |||
| 6380 | msiexec.exe | C:\Windows\Installer\MSIC151.tmp | executable | |
MD5:D82B3FB861129C5D71F0CD2874F97216 | SHA256:107B32C5B789BE9893F24D5BFE22633D25B7A3CAE80082EF37B30E056869CC5C | |||
| 6380 | msiexec.exe | C:\Windows\Installer\13b902.msi | executable | |
MD5:484BEA10F5D2A0C4BDFA342E133033C6 | SHA256:846F339F39E82F358FE5D0985AFDE119563754C9A8030DC237EAC1A963A8BBF4 | |||
| 6380 | msiexec.exe | C:\Windows\Temp\~DF38615008C6E1B80B.TMP | gmc | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 6180 | expand.exe | C:\Users\admin\AppData\Local\Temp\MW-22fb7a87-fa4e-44e9-a83d-e3fde51db22b\files\sqlite3.dll | binary | |
MD5:4BF9A5F13E33C3DCECBE82DC1FEC647D | SHA256:3C3015717FEC9FCB191B2722EFE58FED15C89D553532FE9BA3B6393661AA365E | |||
| 6380 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{c8bd10e0-b1fe-4b12-bb37-7f4269158608}_OnDiskSnapshotProp | binary | |
MD5:B478C1C85F24C193D37C02F9619F391C | SHA256:F0063638B20701AC0BE5A83D42757F3A3F4FBE18719C4D9335764C708F729355 | |||
| 6180 | expand.exe | C:\Users\admin\AppData\Local\Temp\MW-22fb7a87-fa4e-44e9-a83d-e3fde51db22b\files\msvcp71.dll | executable | |
MD5:561FA2ABB31DFA8FAB762145F81667C2 | SHA256:DF96156F6A548FD6FE5672918DE5AE4509D3C810A57BFFD2A91DE45A3ED5B23B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
19
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3032 | RUXIMICS.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2548 | svchost.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 88.221.125.143:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3032 | RUXIMICS.exe | GET | 200 | 88.221.125.143:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2548 | svchost.exe | GET | 200 | 88.221.125.143:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.23.209.187:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2548 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3032 | RUXIMICS.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2548 | svchost.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3032 | RUXIMICS.exe | 88.221.125.143:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 88.221.125.143:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |