| File name: | 2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn |
| Full analysis: | https://app.any.run/tasks/0cec56f6-cdf7-4a5c-b4da-b35cb6cc41c0 |
| Verdict: | Malicious activity |
| Analysis date: | May 18, 2025, 21:50:23 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 3 sections |
| MD5: | 7DA5741EF9273045EE13C13498E56615 |
| SHA1: | 1FF521B35D0C2B6547A8918050F0FBAE8BD8E912 |
| SHA256: | 845E53BA606BC56A508D21957BE9E089AAAE63C3DA14AF4C3B3627B62F1AD9AF |
| SSDEEP: | 98304:5cAPD7d+6z/YDtXXrGiITj8f5CY51V5/Zpn43A2iKFnpIxhZIjxRta:tnpIxhZIn0 |
MALICIOUS
JEEFO has been detected
- explorer.exe (PID: 7760)
- svchost.exe (PID: 7800)
- icsys.icn.exe (PID: 7740)
- 2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn.exe (PID: 7612)
Changes the autorun value in the registry
- explorer.exe (PID: 7760)
- svchost.exe (PID: 7800)
SUSPICIOUS
Executable content was dropped or overwritten
- 2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn.exe (PID: 7612)
- icsys.icn.exe (PID: 7740)
- explorer.exe (PID: 7760)
- spoolsv.exe (PID: 7780)
Starts application with an unusual extension
- 2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn.exe (PID: 7612)
Reads security settings of Internet Explorer
- 2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn.exe (PID: 7636)
The process creates files with name similar to system file names
- icsys.icn.exe (PID: 7740)
- spoolsv.exe (PID: 7780)
Starts itself from another location
- icsys.icn.exe (PID: 7740)
- explorer.exe (PID: 7760)
- spoolsv.exe (PID: 7780)
- svchost.exe (PID: 7800)
- 2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn.exe (PID: 7612)
Creates or modifies Windows services
- svchost.exe (PID: 7800)
INFO
Checks supported languages
- 2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn.exe (PID: 7612)
- 2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn.exe (PID: 7636)
- icsys.icn.exe (PID: 7740)
- explorer.exe (PID: 7760)
- spoolsv.exe (PID: 7780)
- svchost.exe (PID: 7800)
- spoolsv.exe (PID: 7820)
The sample compiled with english language support
- 2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn.exe (PID: 7612)
Create files in a temporary directory
- 2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn.exe (PID: 7612)
- 2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn.exe (PID: 7636)
- icsys.icn.exe (PID: 7740)
- explorer.exe (PID: 7760)
- spoolsv.exe (PID: 7780)
- svchost.exe (PID: 7800)
- spoolsv.exe (PID: 7820)
Reads the machine GUID from the registry
- 2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn.exe (PID: 7636)
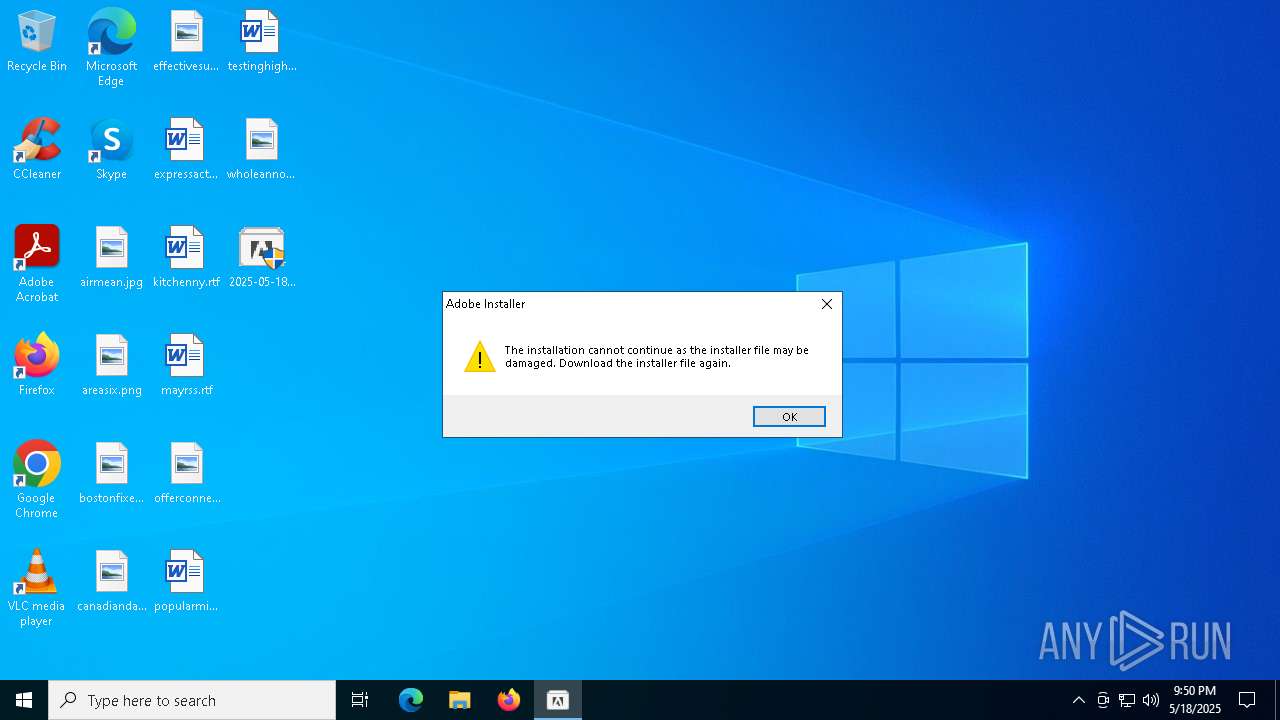
ADOBEINSTALLER mutex has been found
- 2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn.exe (PID: 7636)
Reads the computer name
- 2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn.exe (PID: 7636)
- svchost.exe (PID: 7800)
Auto-launch of the file from Registry key
- explorer.exe (PID: 7760)
- svchost.exe (PID: 7800)
Checks proxy server information
- slui.exe (PID: 8168)
- 2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn.exe (PID: 7636)
Reads the software policy settings
- slui.exe (PID: 8168)
- 2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn.exe (PID: 7636)
Manual execution by a user
- explorer.exe (PID: 7956)
- svchost.exe (PID: 7972)
Creates files or folders in the user directory
- 2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn.exe (PID: 7636)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2013:04:01 07:08:22+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 106496 |
| InitializedDataSize: | 12288 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x290c |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| ProductName: | Project1 |
| FileVersion: | 1 |
| ProductVersion: | 1 |
| InternalName: | TJprojMain |
| OriginalFileName: | TJprojMain.exe |
Total processes
134
Monitored processes
11
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 7524 | "C:\Users\admin\Desktop\2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn.exe" | C:\Users\admin\Desktop\2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.00 Modules
| |||||||||||||||
| 7612 | "C:\Users\admin\Desktop\2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn.exe" | C:\Users\admin\Desktop\2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 7636 | c:\users\admin\desktop\2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn.exe | C:\Users\admin\Desktop\2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn.exe | 2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn.exe | ||||||||||||
User: admin Company: Adobe Inc. Integrity Level: HIGH Description: Adobe Installer Exit code: 1 Version: 5.0.0.354 Modules
| |||||||||||||||
| 7740 | C:\Windows\Resources\Themes\icsys.icn.exe | C:\Windows\Resources\Themes\icsys.icn.exe | 2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 7760 | c:\windows\resources\themes\explorer.exe | C:\Windows\Resources\Themes\explorer.exe | icsys.icn.exe | ||||||||||||
User: admin Integrity Level: HIGH Version: 1.00 Modules
| |||||||||||||||
| 7780 | c:\windows\resources\spoolsv.exe SE | C:\Windows\Resources\spoolsv.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 7800 | c:\windows\resources\svchost.exe | C:\Windows\Resources\svchost.exe | spoolsv.exe | ||||||||||||
User: admin Integrity Level: HIGH Version: 1.00 Modules
| |||||||||||||||
| 7820 | c:\windows\resources\spoolsv.exe PR | C:\Windows\Resources\spoolsv.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 7956 | c:\windows\resources\themes\explorer.exe RO | C:\Windows\Resources\Themes\explorer.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.00 Modules
| |||||||||||||||
| 7972 | c:\windows\resources\svchost.exe RO | C:\Windows\Resources\svchost.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.00 Modules
| |||||||||||||||
Total events
7 103
Read events
7 084
Write events
15
Delete events
4
Modification events
| (PID) Process: | (7612) 2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\VB and VBA Program Settings\Explorer\Process |
| Operation: | write | Name: | LO |
Value: 1 | |||
| (PID) Process: | (7740) icsys.icn.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\VB and VBA Program Settings\Explorer\Process |
| Operation: | write | Name: | LO |
Value: 1 | |||
| (PID) Process: | (7760) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Explorer |
Value: c:\windows\resources\themes\explorer.exe RO | |||
| (PID) Process: | (7760) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Svchost |
Value: c:\windows\resources\svchost.exe RO | |||
| (PID) Process: | (7760) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Explorer |
Value: | |||
| (PID) Process: | (7760) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Svchost |
Value: | |||
| (PID) Process: | (7800) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Explorer |
Value: c:\windows\resources\themes\explorer.exe RO | |||
| (PID) Process: | (7800) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Svchost |
Value: c:\windows\resources\svchost.exe RO | |||
| (PID) Process: | (7800) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Explorer |
Value: | |||
| (PID) Process: | (7800) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Svchost |
Value: | |||
Executable files
5
Suspicious files
8
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7636 | 2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8890A77645B73478F5B1DED18ACBF795_C090A8C88B266C6FF99A97210E92B44D | binary | |
MD5:A39DA9C75FA5D87C94058EAF93AF8814 | SHA256:48D206A3AF05BACFAE6708867382F422F6D89C8B4241E85D45850F34B5D41C86 | |||
| 7636 | 2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn.exe | C:\Users\admin\AppData\Local\Temp\CreativeCloud\ACC\AdobeDownload\HDInstaller.log | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 7636 | 2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\DA3B6E45325D5FFF28CF6BAD6065C907_EA01B8AC2C0BE6E5850A0487D704D929 | binary | |
MD5:3B7A73E88D3A1F253356160D5E47B4AC | SHA256:CECD0C27D9665EEF25593EA193233B365FD8FCD8736BFA37897899FBEC744A3D | |||
| 7636 | 2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\DA3B6E45325D5FFF28CF6BAD6065C907_EA01B8AC2C0BE6E5850A0487D704D929 | binary | |
MD5:762959A82DF2B6A452A4513B40D560FE | SHA256:1392E36A8620A6FE385FEF65C2B3128F072A9218E1B15CFC1CE0B4B86EE74F4D | |||
| 7740 | icsys.icn.exe | C:\Users\admin\AppData\Local\Temp\~DFCDDE4C137B9814D7.TMP | binary | |
MD5:FB534B936CAF5DACB998044549EDF11F | SHA256:8355358B7E40B2ECCDBF8DEB7209230FA9BA698953FD6EBADB1104E72D9CC019 | |||
| 7780 | spoolsv.exe | C:\Windows\Resources\svchost.exe | executable | |
MD5:8067F1A851F9739F8A20F93B87594AE9 | SHA256:8694175E321F34BBC01372575794D344C521D9AC7977187146C88474E487E27C | |||
| 7780 | spoolsv.exe | C:\Users\admin\AppData\Local\Temp\~DFE2178EAAD527F6F9.TMP | binary | |
MD5:2DBD8585D38F65B083A5E675773E2692 | SHA256:04743CE8540B2439A9E8D387549499AEF2524FF74D86C170854EB46FAAF6D6C3 | |||
| 7612 | 2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn.exe | C:\Users\admin\Desktop\2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn.exe | executable | |
MD5:9CFA0D88F0B614D1FF6FC69B703A839A | SHA256:582536081E67975055CCF8DE5353502D7BDA56F2AAFCBEFBB400F3D9012019C9 | |||
| 7612 | 2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn.exe | C:\Windows\Resources\Themes\icsys.icn.exe | executable | |
MD5:76DCBC309C994DF74E55A1698E93DE52 | SHA256:DDA67992C3A1DB7245B3EAF151D08A807D24C6497D70F33401BB2E62AD9FECFD | |||
| 7820 | spoolsv.exe | C:\Users\admin\AppData\Local\Temp\~DF7074B02C36DB9A1A.TMP | binary | |
MD5:404E3E5041612EFBD29BD3B27C364929 | SHA256:7AFF38A60701973D1AFAF7FD0D69757ABA60A649814B51F0A456630AC0219571 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
22
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7636 | 2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSPwl%2BrBFlJbvzLXU1bGW08VysJ2wQUj%2Bh%2B8G0yagAFI8dwl2o6kP9r6tQCEAbyTZ9NsHvX7K0Gf17ibCk%3D | unknown | — | — | whitelisted |
7636 | 2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAPxtOFfOoLxFJZ4s9fYR1w%3D | unknown | — | — | whitelisted |
2616 | RUXIMICS.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2616 | RUXIMICS.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2616 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7636 | 2025-05-18_7da5741ef9273045ee13c13498e56615_black-basta_darkgate_elex_luca-stealer_swisyn.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2616 | RUXIMICS.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
2616 | RUXIMICS.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
7436 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
8168 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |