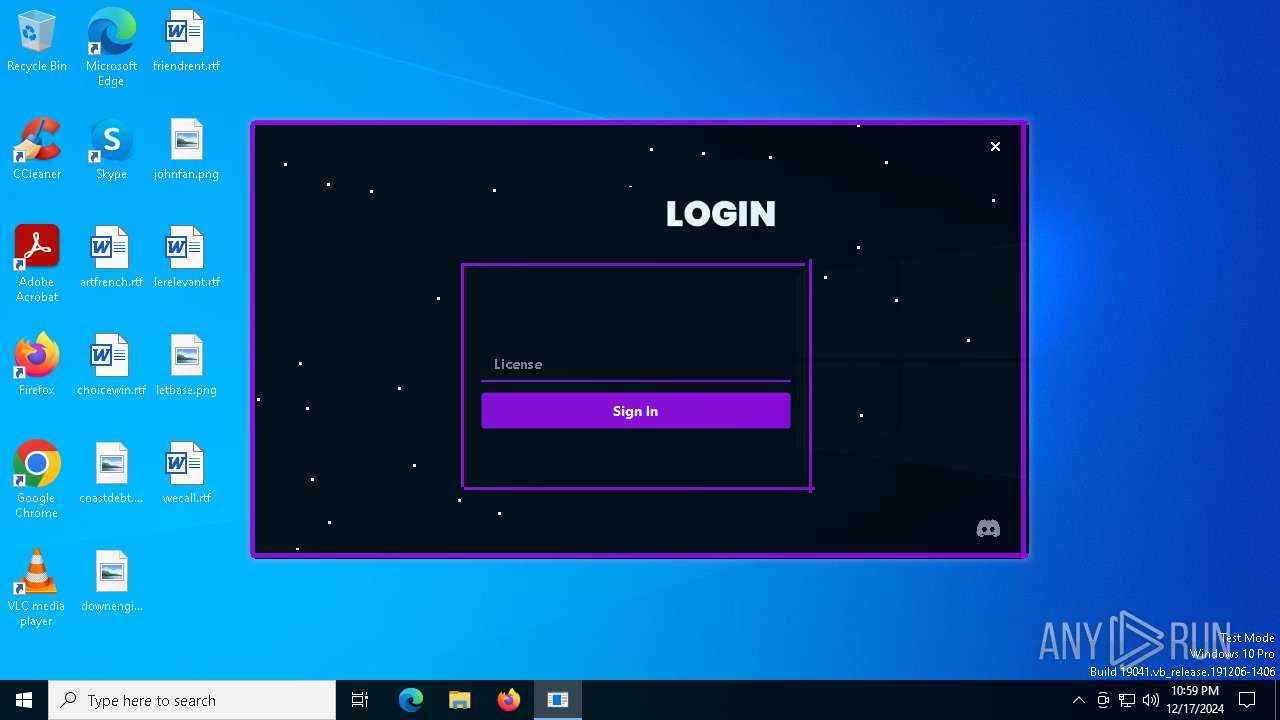
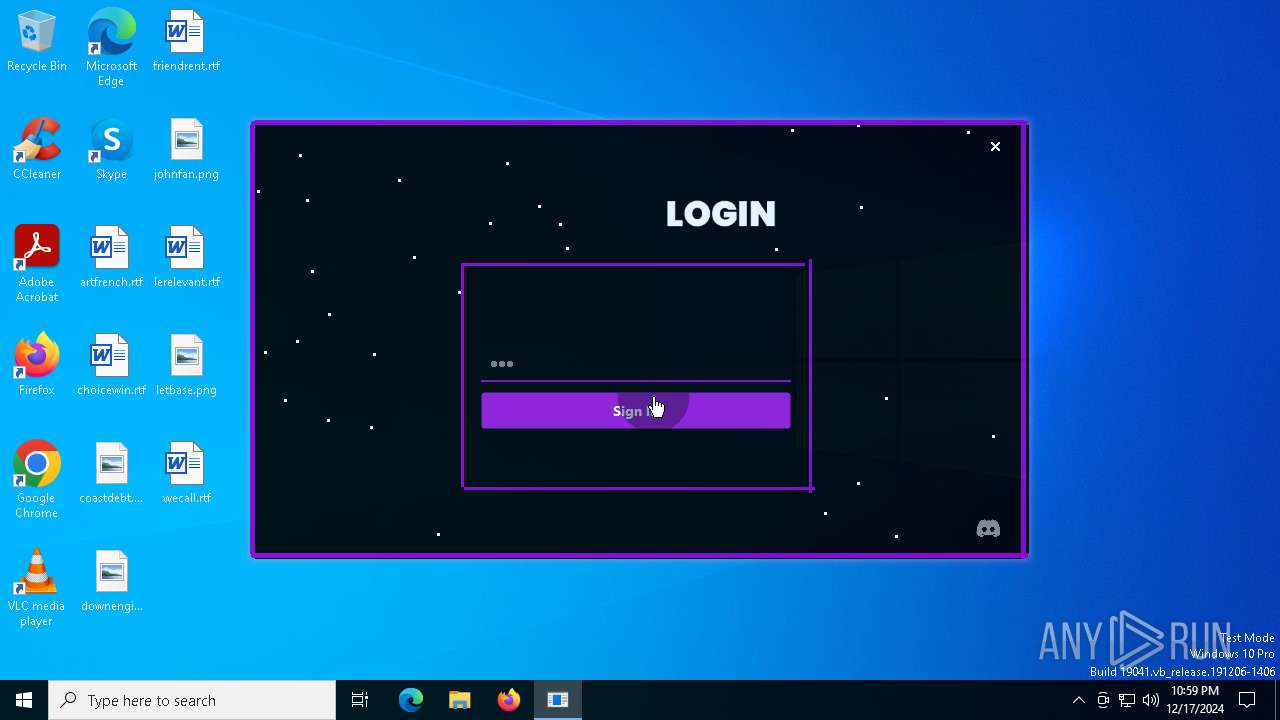
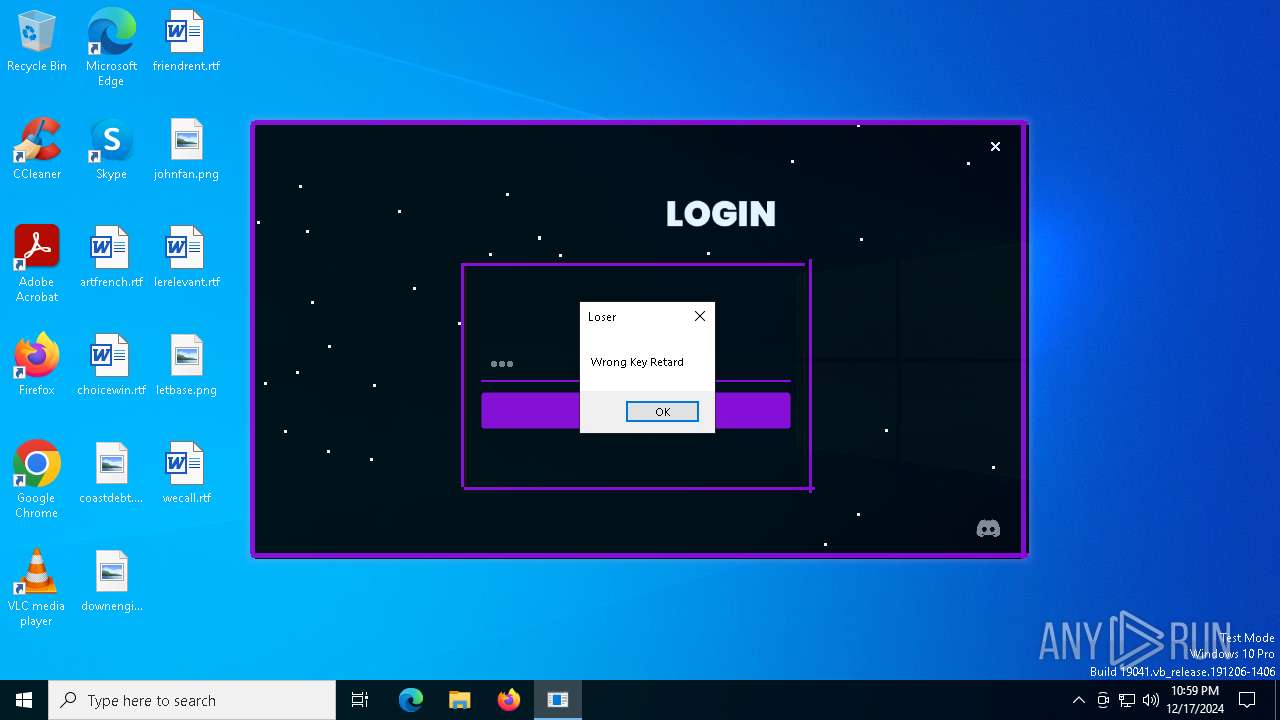
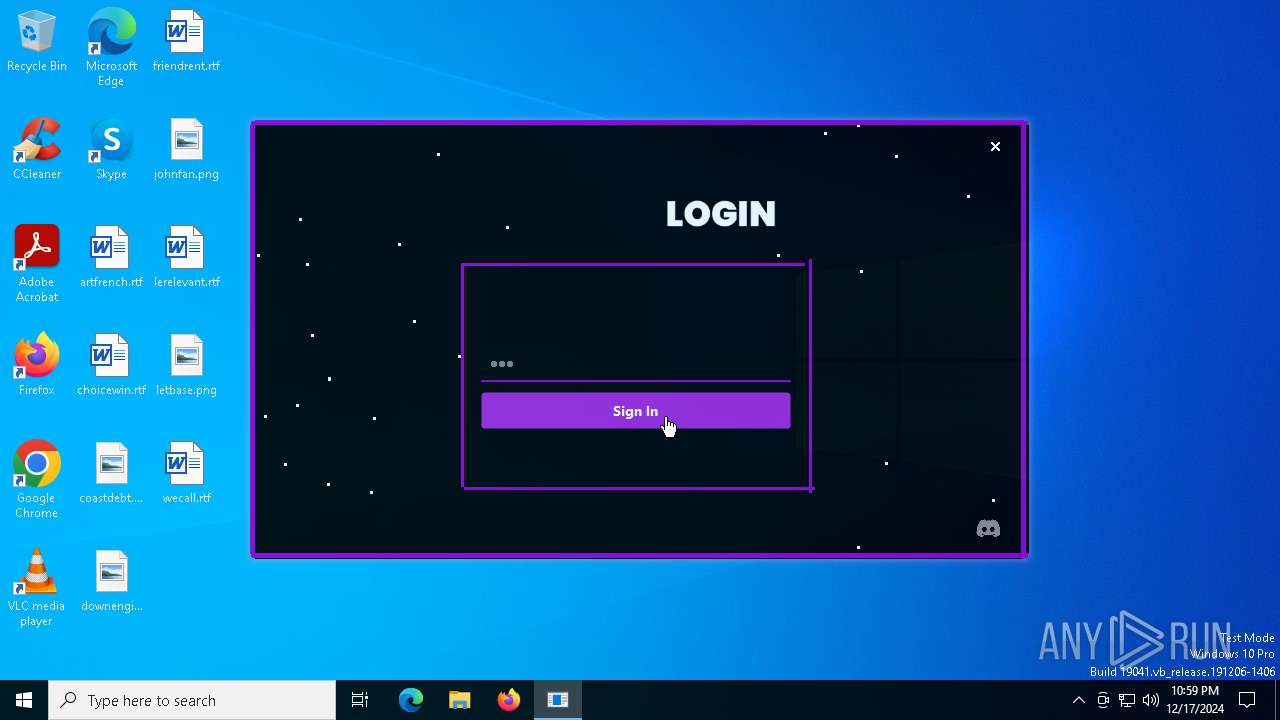
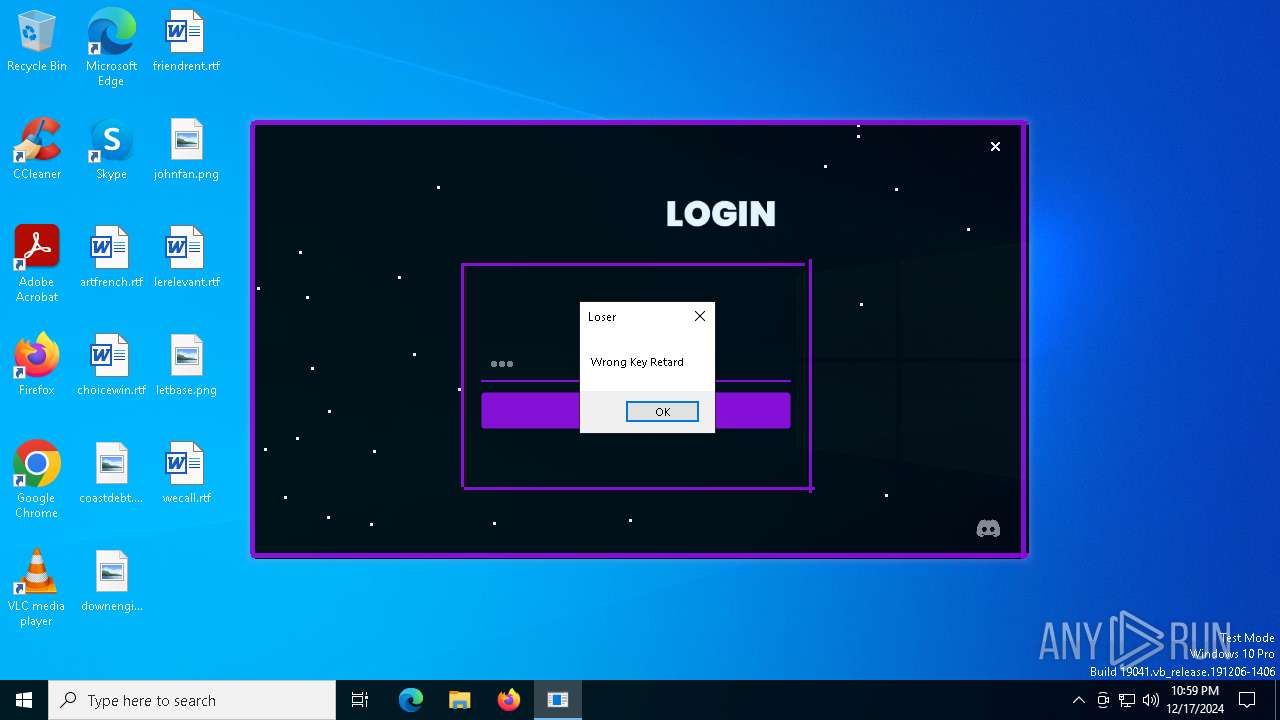
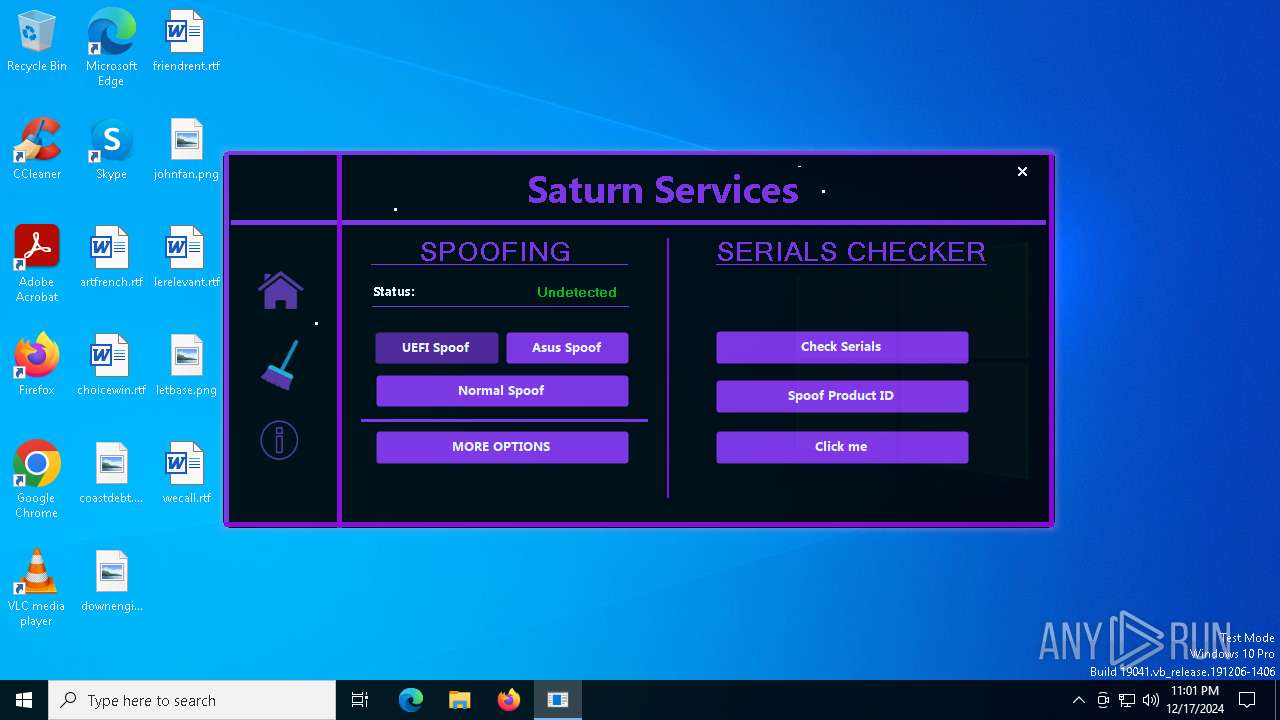
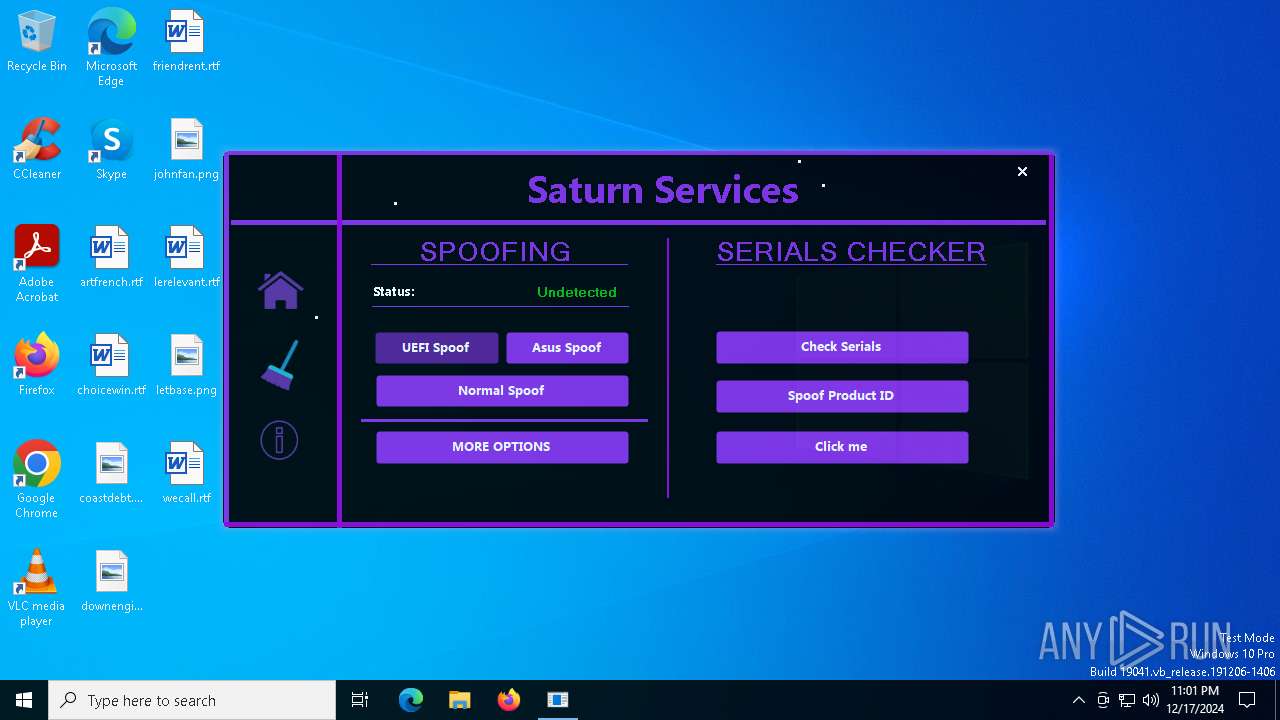
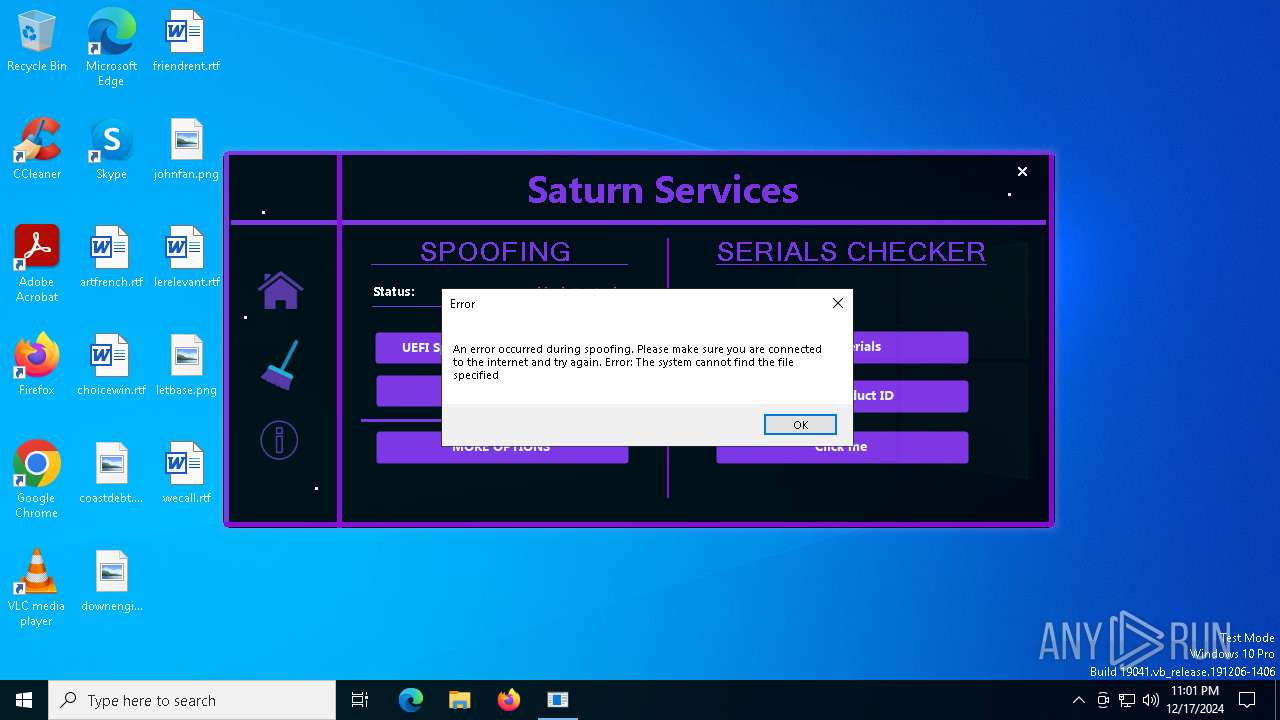
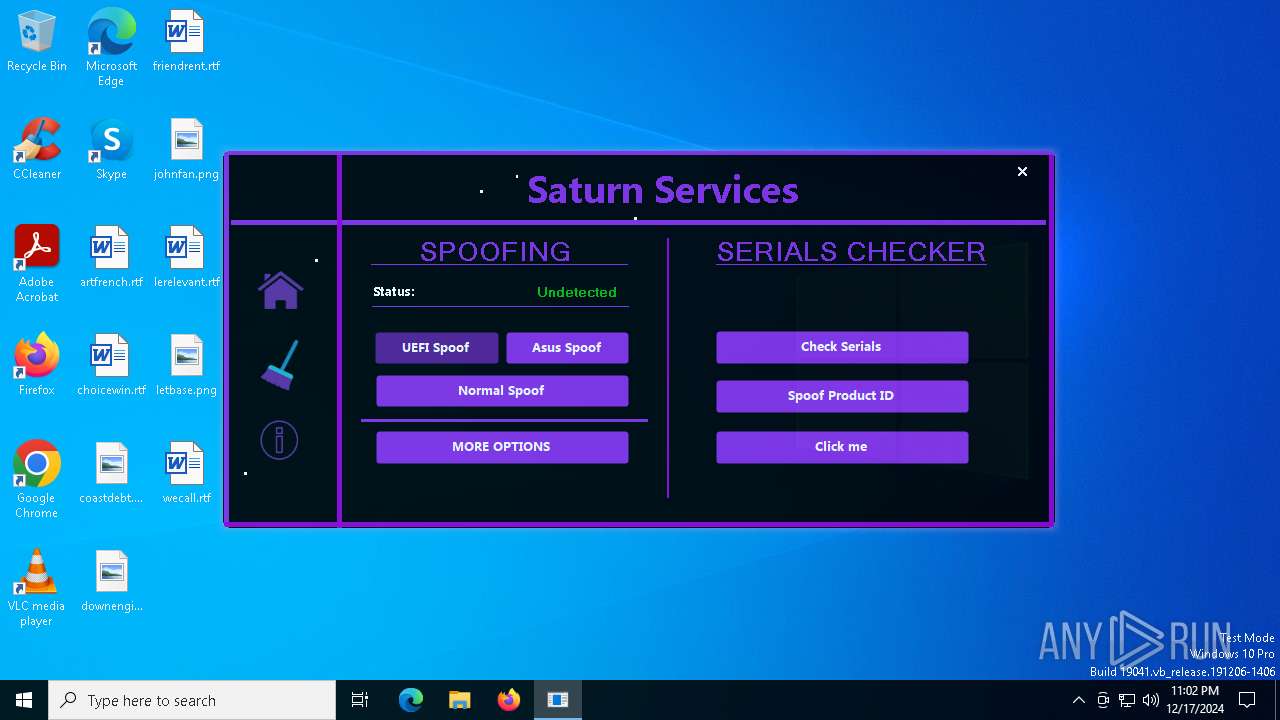
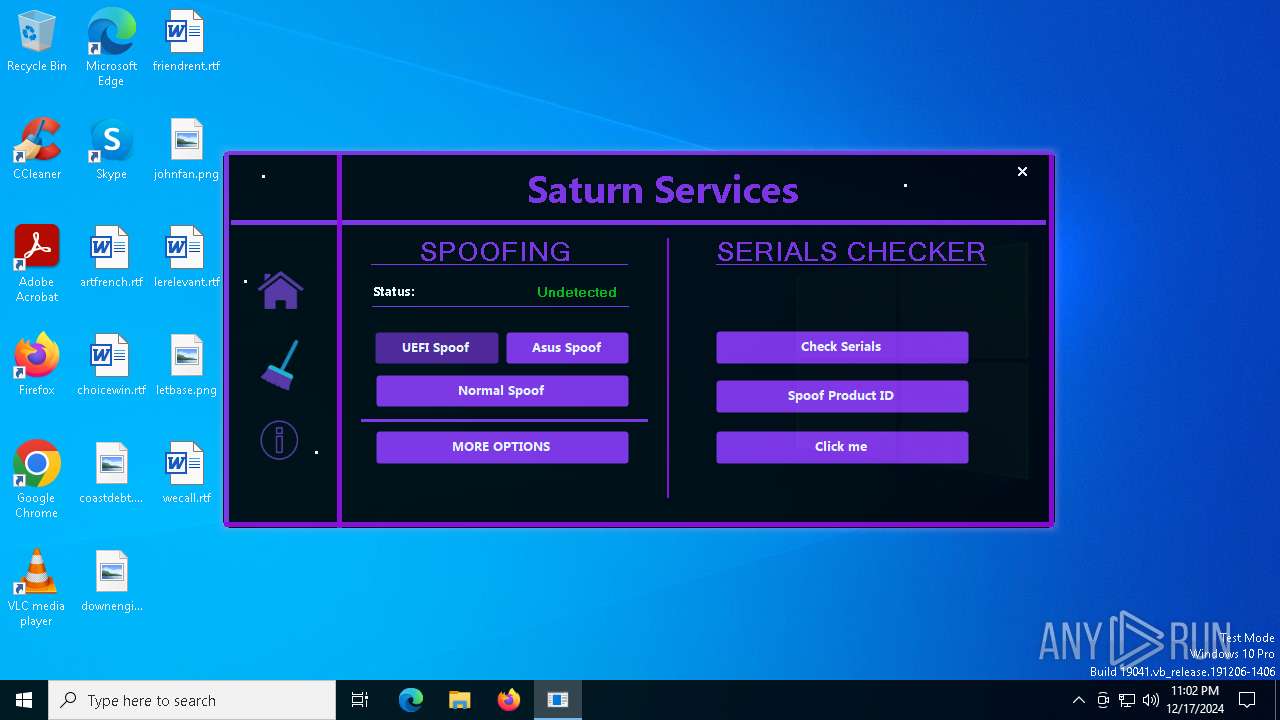
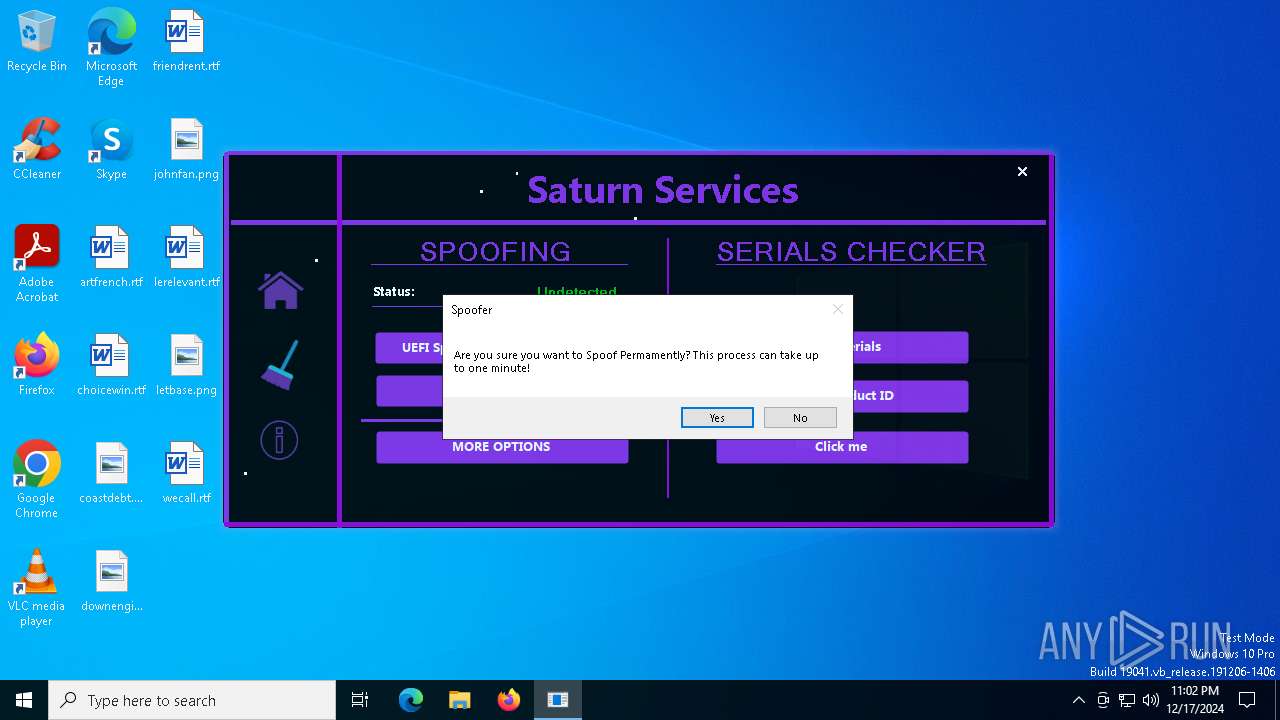
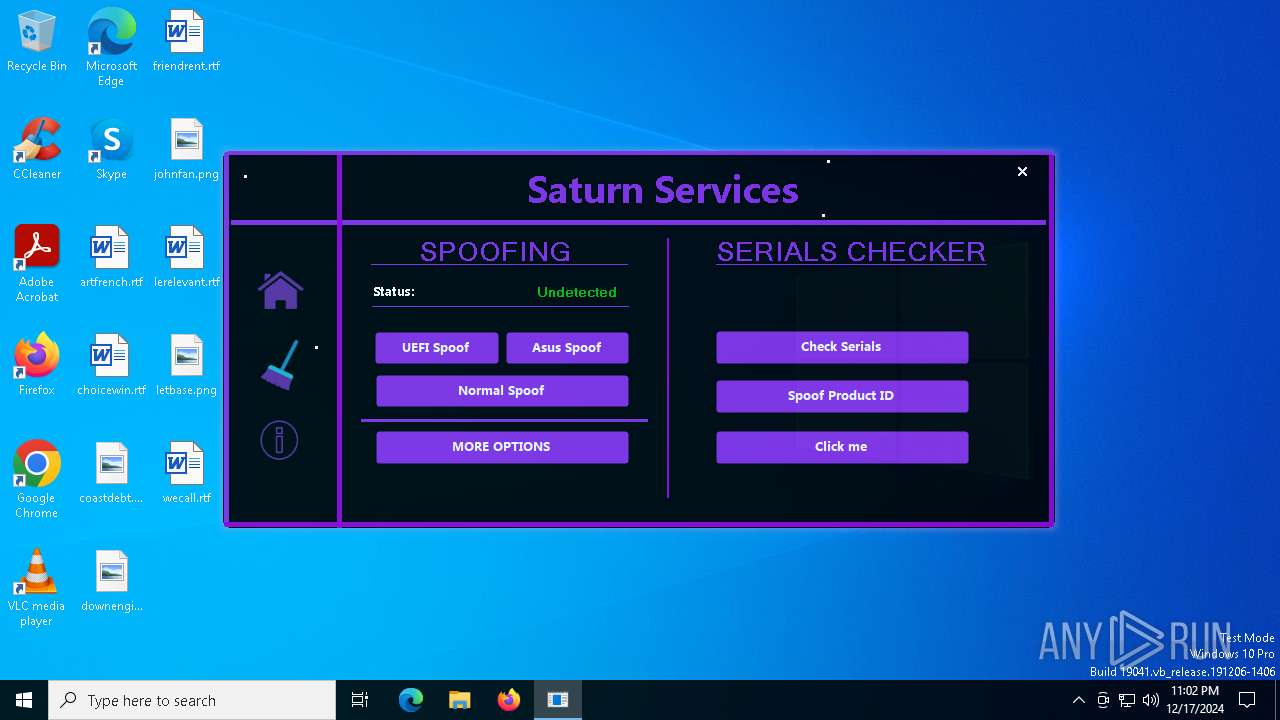
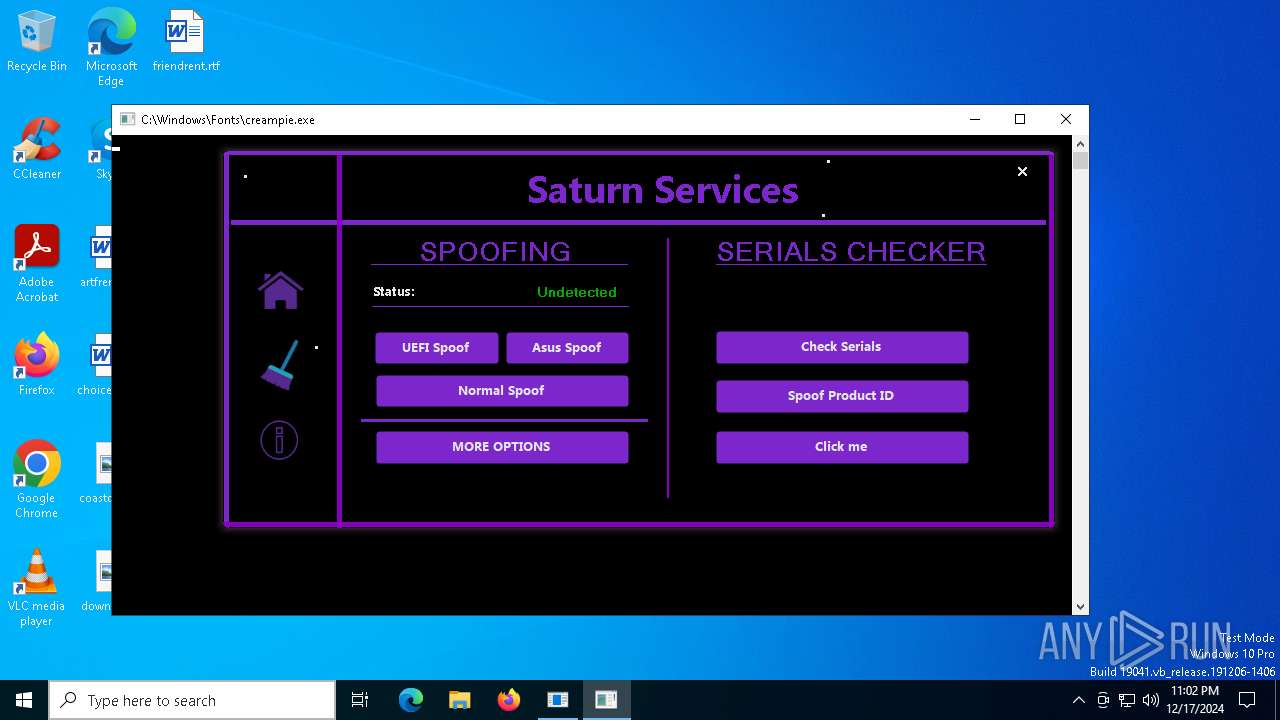
| File name: | Loader.exe |
| Full analysis: | https://app.any.run/tasks/3e945c86-128c-4e96-9fc8-09c7b0a3286d |
| Verdict: | Malicious activity |
| Analysis date: | December 17, 2024, 22:59:08 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 6 sections |
| MD5: | E90F500F8CE1BFC4F5AA32638C945E51 |
| SHA1: | 72A823B82B43990841E46438245E3316E9267B73 |
| SHA256: | 845A876D8CEA057949106E4194C817C5FDD3AF2D3AAEBBC57CDE4A33C3343830 |
| SSDEEP: | 49152:hisNujAiRN54jtrVyMsiDV+XnROhVWvGLZV35+n/aYbP02LmbKKqvWQRGUKgwHFy:hi2w5iVsiBAGVWv8ZV5+nSYzLmxqv3RZ |
MALICIOUS
XORed URL has been found (YARA)
- Loader.exe (PID: 6572)
Executing a file with an untrusted certificate
- creampie.exe (PID: 5208)
SUSPICIOUS
Reads the BIOS version
- Loader.exe (PID: 6572)
There is functionality for taking screenshot (YARA)
- Loader.exe (PID: 6572)
Drops a system driver (possible attempt to evade defenses)
- Loader.exe (PID: 6572)
Executable content was dropped or overwritten
- Loader.exe (PID: 6572)
- creampie.exe (PID: 5208)
Read disk information to detect sandboxing environments
- Loader.exe (PID: 6572)
Reads security settings of Internet Explorer
- Loader.exe (PID: 6572)
Starts CMD.EXE for commands execution
- Loader.exe (PID: 6572)
Hides command output
- cmd.exe (PID: 2612)
The process checks if it is being run in the virtual environment
- Loader.exe (PID: 6840)
- Loader.exe (PID: 6572)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 1376)
INFO
Reads the computer name
- Loader.exe (PID: 6572)
- winxsrcsv64.exe (PID: 6404)
- winxsrcsv64.exe (PID: 1616)
- winxsrcsv64.exe (PID: 6560)
- winxsrcsv64.exe (PID: 6336)
- winxsrcsv64.exe (PID: 5876)
- winxsrcsv64.exe (PID: 3152)
- PLUGScheduler.exe (PID: 1376)
- Loader.exe (PID: 6840)
Reads the machine GUID from the registry
- Loader.exe (PID: 6572)
Checks supported languages
- Loader.exe (PID: 6572)
- winxsrcsv64.exe (PID: 6560)
- winxsrcsv64.exe (PID: 5696)
- winxsrcsv64.exe (PID: 1616)
- winxsrcsv64.exe (PID: 6404)
- winxsrcsv64.exe (PID: 6336)
- winxsrcsv64.exe (PID: 5876)
- winxsrcsv64.exe (PID: 3152)
- winxsrcsv64.exe (PID: 2120)
- Loader.exe (PID: 6840)
Disables trace logs
- Loader.exe (PID: 6572)
Checks proxy server information
- Loader.exe (PID: 6572)
The sample compiled with english language support
- Loader.exe (PID: 6572)
- creampie.exe (PID: 5208)
The process uses the downloaded file
- Loader.exe (PID: 6572)
Manual execution by a user
- Loader.exe (PID: 6840)
- Loader.exe (PID: 6756)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (64.5) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (13.6) |
| .exe | | | Win32 Executable (generic) (9.3) |
| .exe | | | Win16/32 Executable Delphi generic (4.2) |
| .exe | | | Generic Win/DOS Executable (4.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2087:09:07 17:07:02+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 1162752 |
| InitializedDataSize: | 408576 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x18400a |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
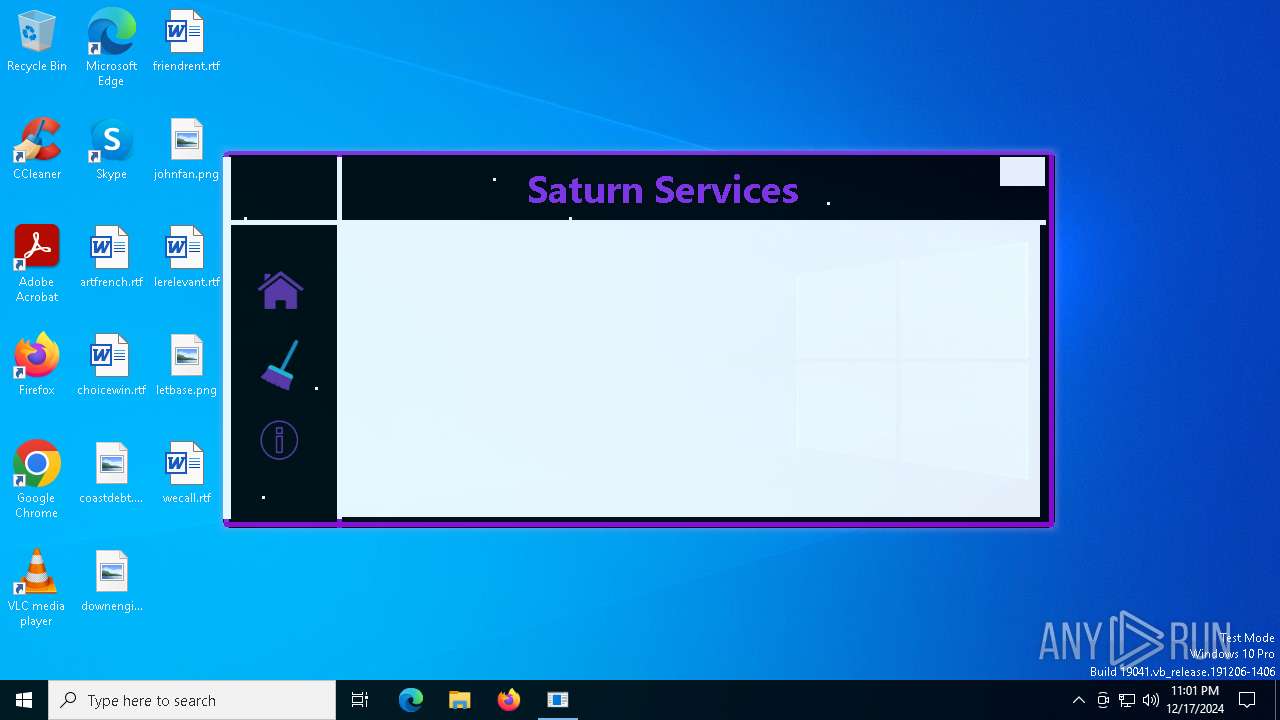
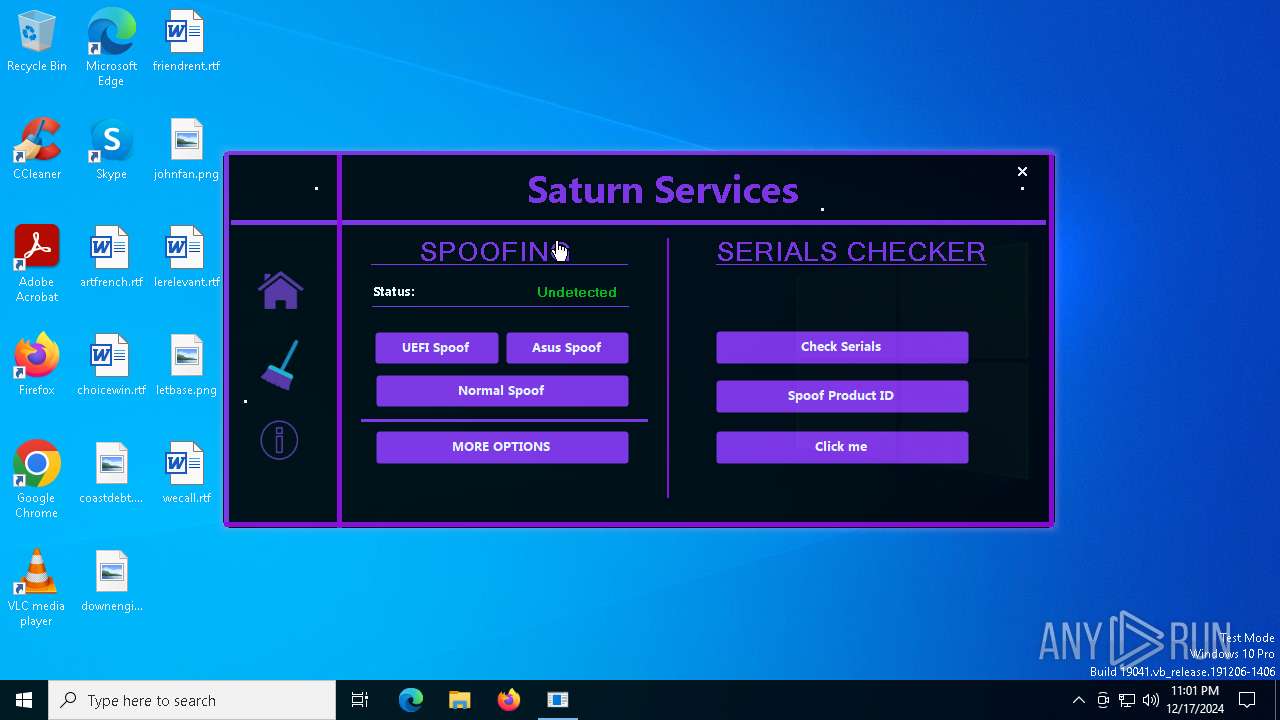
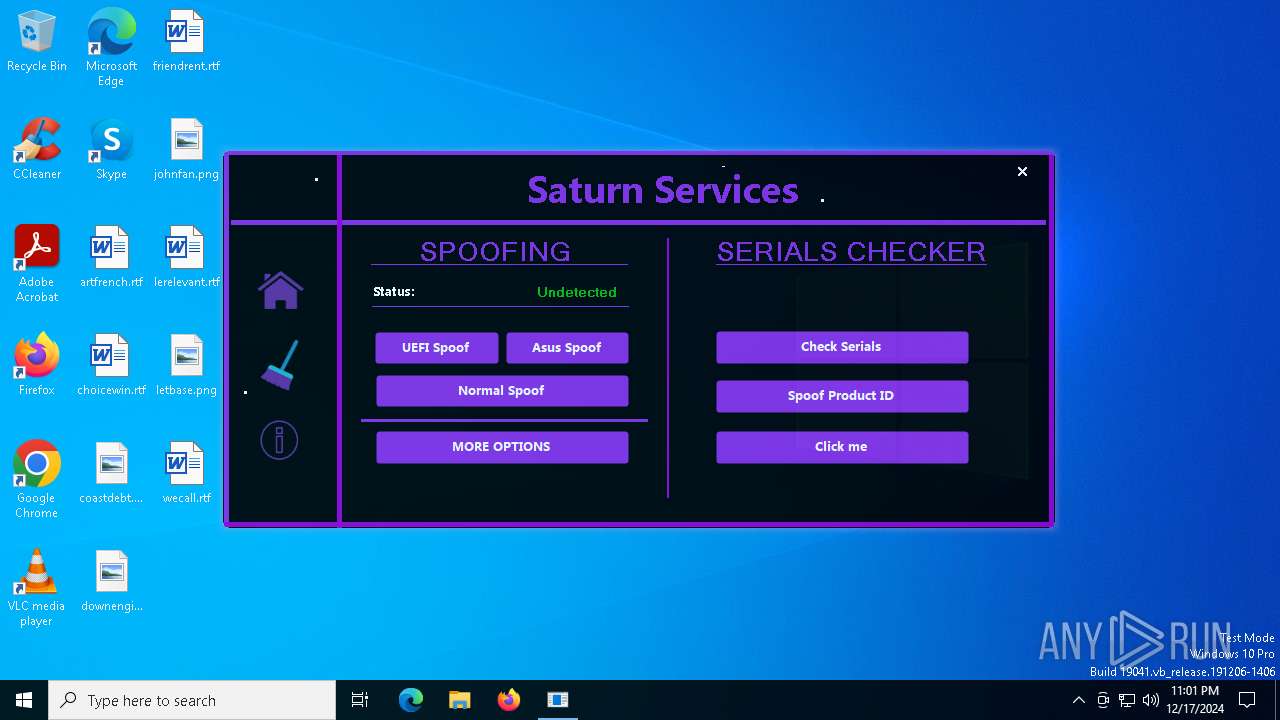
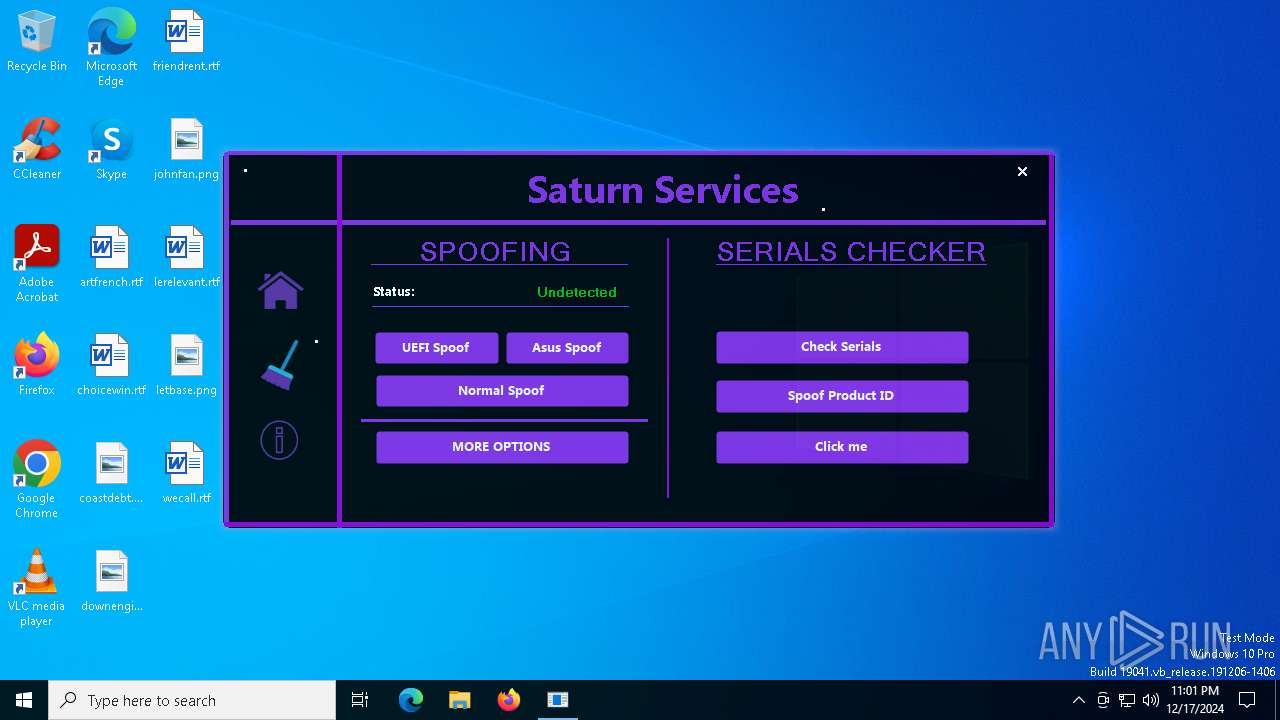
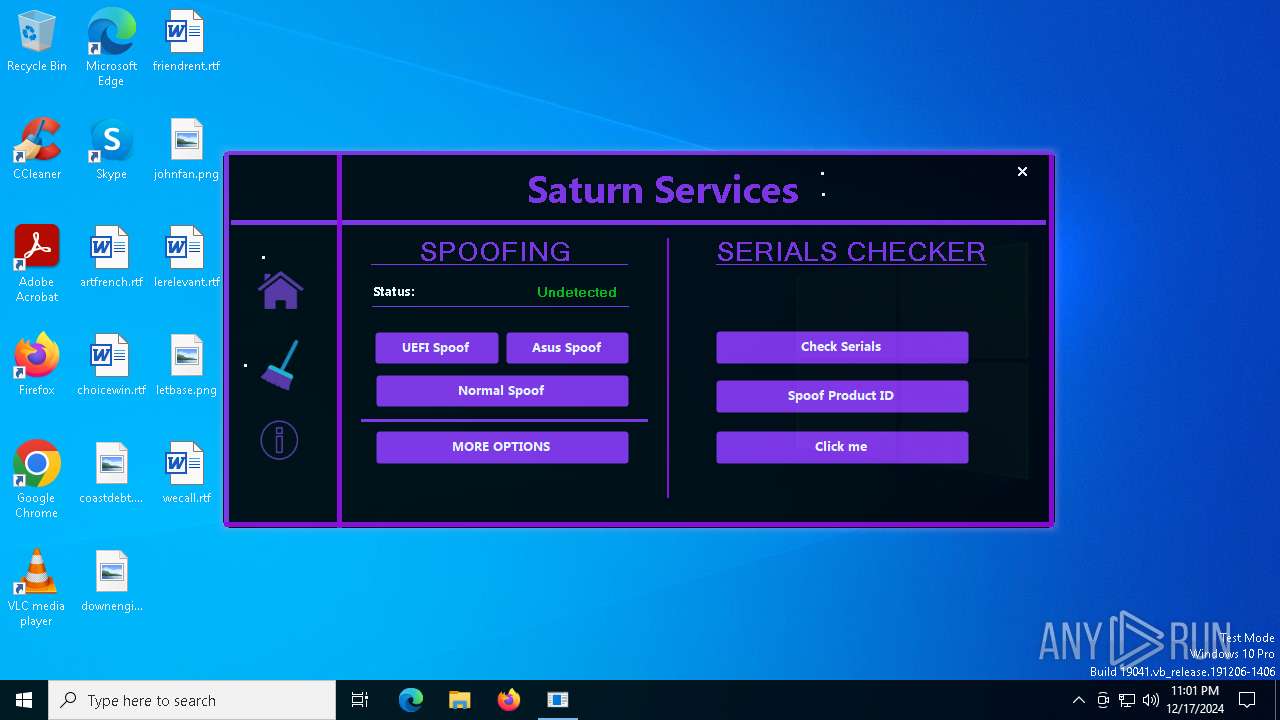
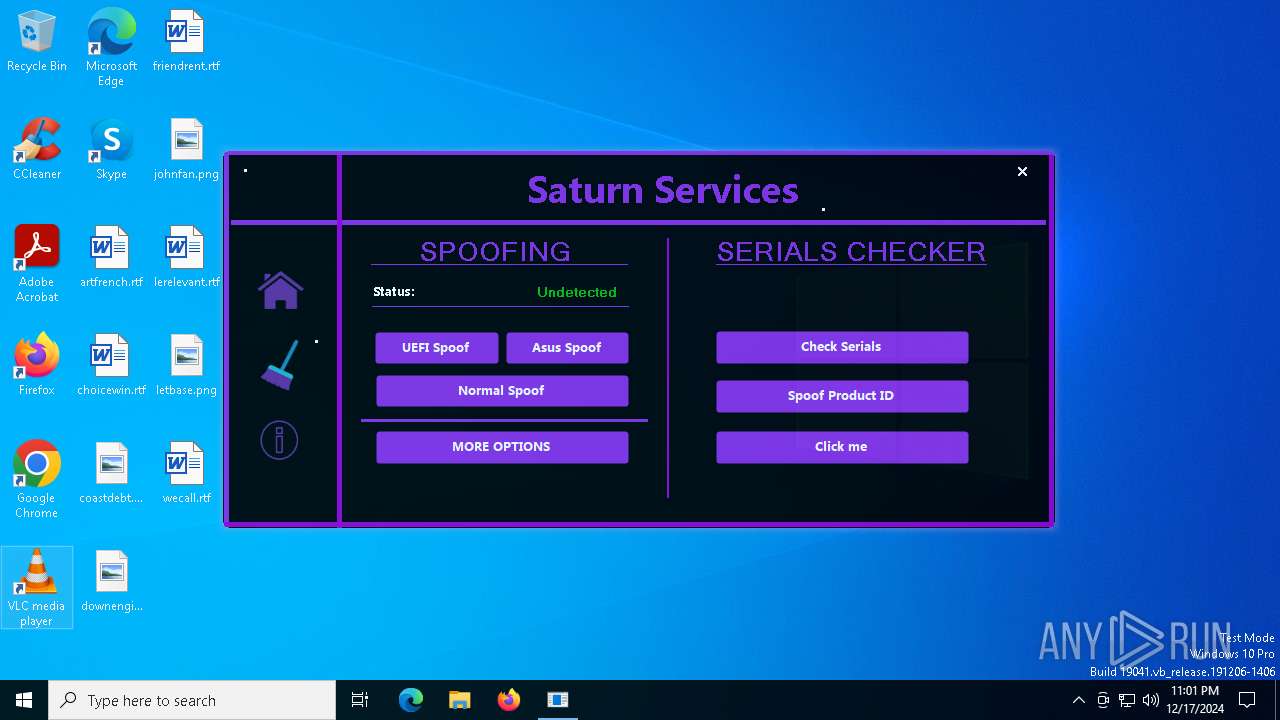
| Comments: | Saturn Services |
| CompanyName: | Saturn Services |
| FileDescription: | Saturn Services |
| FileVersion: | 1.0.0.0 |
| InternalName: | Loader.exe |
| LegalCopyright: | Saturn Services |
| LegalTrademarks: | Saturn Services |
| OriginalFileName: | Loader.exe |
| ProductName: | System Virtualizer |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
280
Monitored processes
42
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 396 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | winxsrcsv64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 448 | "winxsrcsv64.exe" /BT "Default string" | C:\Windows\Fonts\winxsrcsv64.exe | — | Loader.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 224 Modules
| |||||||||||||||
| 1172 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1192 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | winxsrcsv64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1292 | sc stop winmgmt | C:\Windows\SysWOW64\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1051 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1376 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1468 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | winxsrcsv64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1540 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | winxsrcsv64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1616 | "winxsrcsv64.exe" /CS 5ZZVLNTK4NRWGEEH | C:\Windows\Fonts\winxsrcsv64.exe | — | Loader.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 224 Modules
| |||||||||||||||
| 1792 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | winxsrcsv64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 483
Read events
3 466
Write events
17
Delete events
0
Modification events
| (PID) Process: | (6572) Loader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Loader_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6572) Loader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Loader_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6572) Loader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Loader_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6572) Loader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Loader_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (6572) Loader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Loader_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (6572) Loader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Loader_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (6572) Loader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Loader_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (6572) Loader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Loader_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6572) Loader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Loader_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6572) Loader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Loader_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
10
Suspicious files
34
Text files
2
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6572 | Loader.exe | C:\Windows\Fonts\skibnidi.bat | text | |
MD5:80CE921D39B0C2739E3EDCA44FCF253C | SHA256:40A74428BE51EFAF4F65F27312FC3E8946338817B7A07D67B12FD7B837BDB546 | |||
| 6572 | Loader.exe | C:\Windows\Fonts\winxsrcsv64.sys | executable | |
MD5:F900A6E8C788E1330F551783797AF853 | SHA256:71114F4521FC92ABDFAC7D7192F3B7E29FC42E9EADC9320D5A58C9B4432BD9E7 | |||
| 6572 | Loader.exe | C:\Windows\Fonts\winxsrcsv64.exe | executable | |
MD5:91A31F23F3E50BD0A722E605687AED1E | SHA256:818D6D87D0FACC03354BF7B0748467CF61040031248BA8B46045ED9DBE4053D8 | |||
| 6572 | Loader.exe | C:\Windows\Fonts\iqvw64e.sys | executable | |
MD5:A67B478BEB2166013BF4AE4DE6527F6F | SHA256:EFEFD03984E131C6AB6F3A7EC6E47A0176F4BBC9BA59955C1FB81C0FB9735DC8 | |||
| 6572 | Loader.exe | C:\Windows\Fonts\Mac.bat | text | |
MD5:707C798832F76EB383A0501B2773EC32 | SHA256:940F3E68E62AD73C0668E854D821D88EACC8EA8FB8E130E42A34368AE9F5852E | |||
| 6572 | Loader.exe | C:\Windows\Fonts\Disk1.exe | executable | |
MD5:4D867033B27C8A603DE4885B449C4923 | SHA256:22A2484D7FA799E6E71E310141614884F3BC8DAD8AC749B6F1C475B5398A72F3 | |||
| 5208 | creampie.exe | C:\Users\admin\AppData\Local\Temp\kxIKJgHWkr | executable | |
MD5:1898CEDA3247213C084F43637EF163B3 | SHA256:4429F32DB1CC70567919D7D47B844A91CF1329A6CD116F582305F3B7B60CD60B | |||
| 6572 | Loader.exe | C:\Windows\Fonts\amigendrv64.sys | executable | |
MD5:119F0656AB4BB872F79EE5D421E2B9F9 | SHA256:38D87B51F4B69BA2DAE1477684A1415F1A3B578EEE5E1126673B1BEAEFEE9A20 | |||
| 6572 | Loader.exe | C:\Windows\Fonts\niggler.sys | executable | |
MD5:1D4A330B99E381728A2F1AA6694BFC1A | SHA256:B395103A618EC58C406EBD3D02FAB1EA312B60F6E6287F94CA8A6BD5BB429470 | |||
| 6572 | Loader.exe | C:\Windows\Fonts\AMIDEWINx64.exe | executable | |
MD5:64AE4AA4904D3B259DDA8CC53769064F | SHA256:2C67FB6EB81630C917F08295E4FF3B5F777CB41B26F7B09DC36D79F089E61BC4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
53
DNS requests
30
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4896 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6072 | svchost.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6072 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6924 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5628 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6924 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
6072 | svchost.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
6072 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.23.209.179:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1176 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |