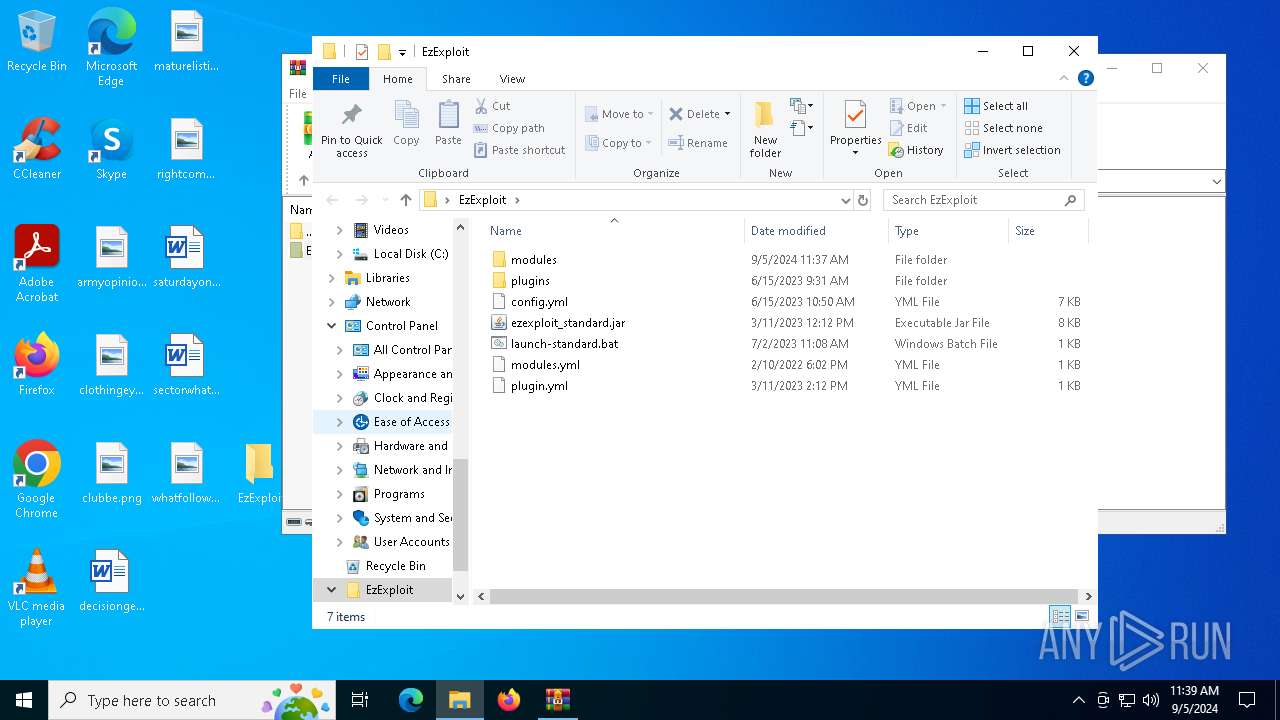
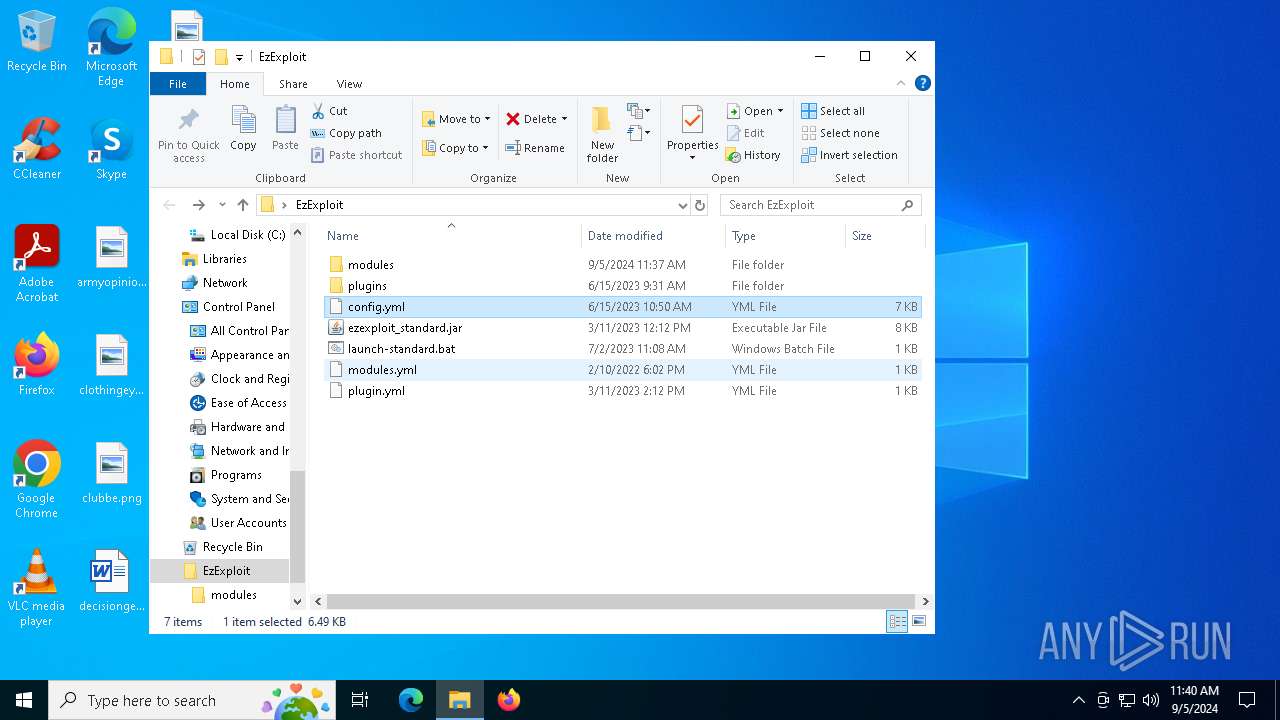
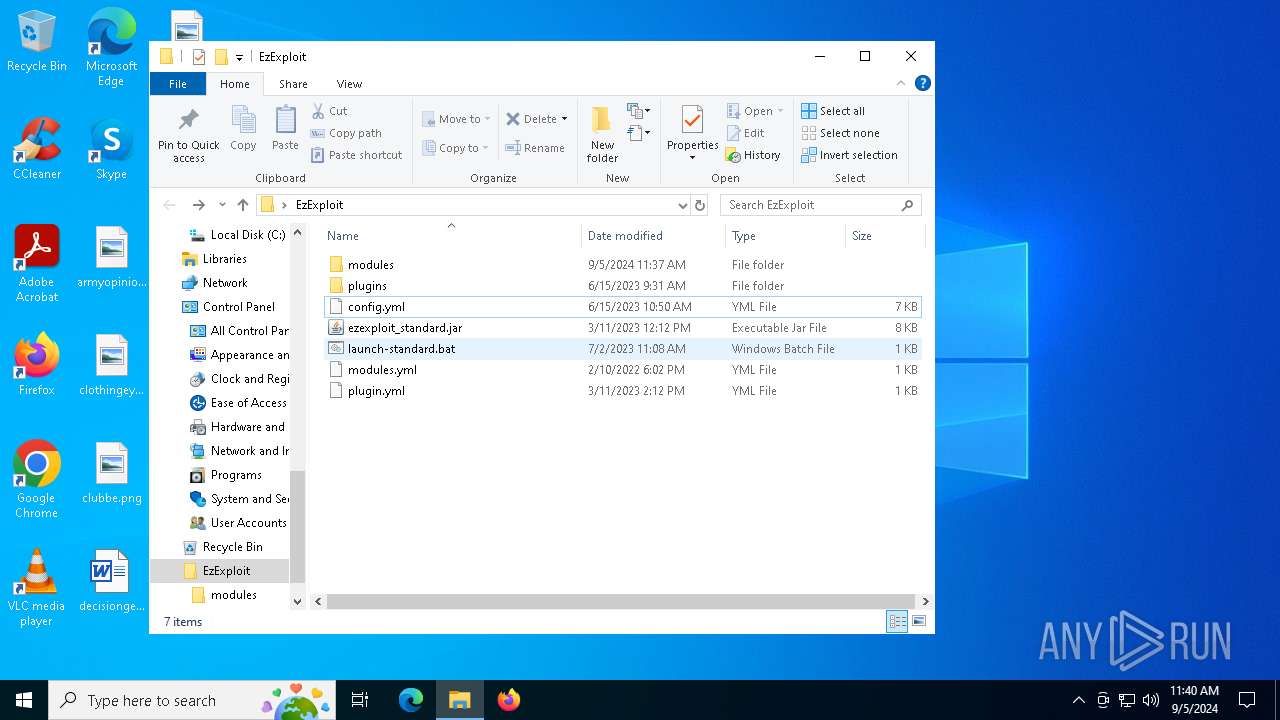
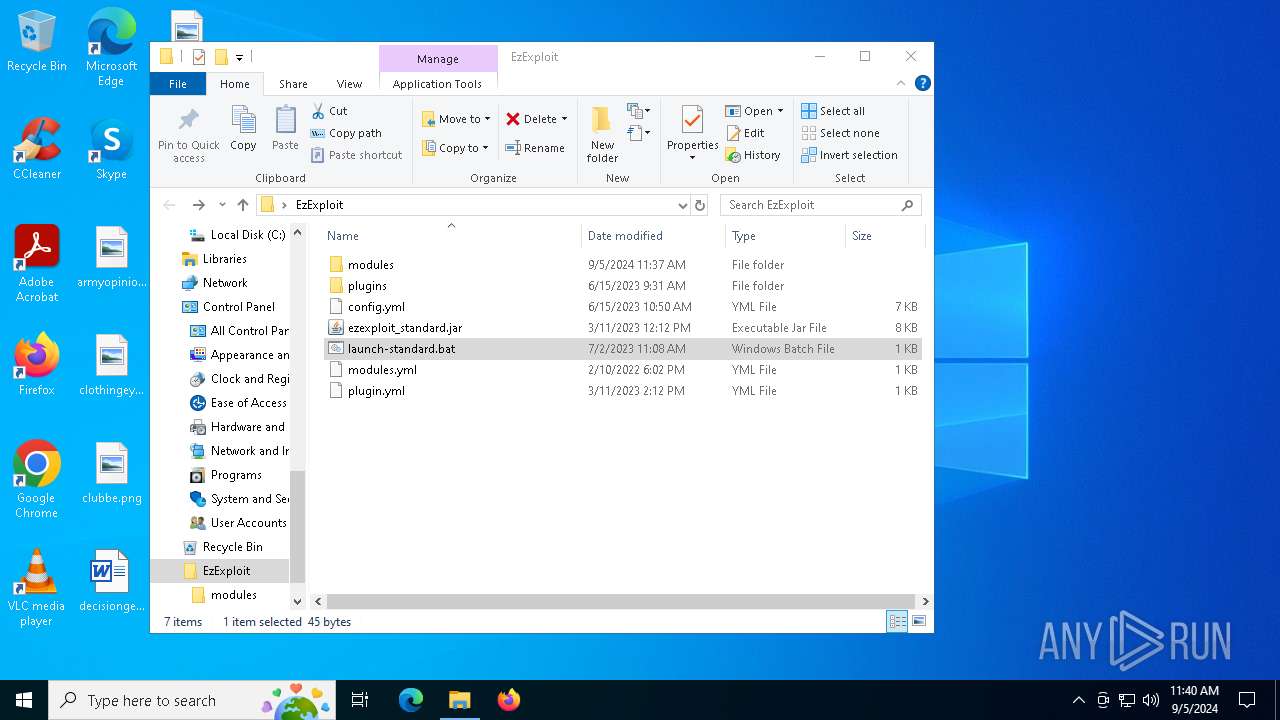
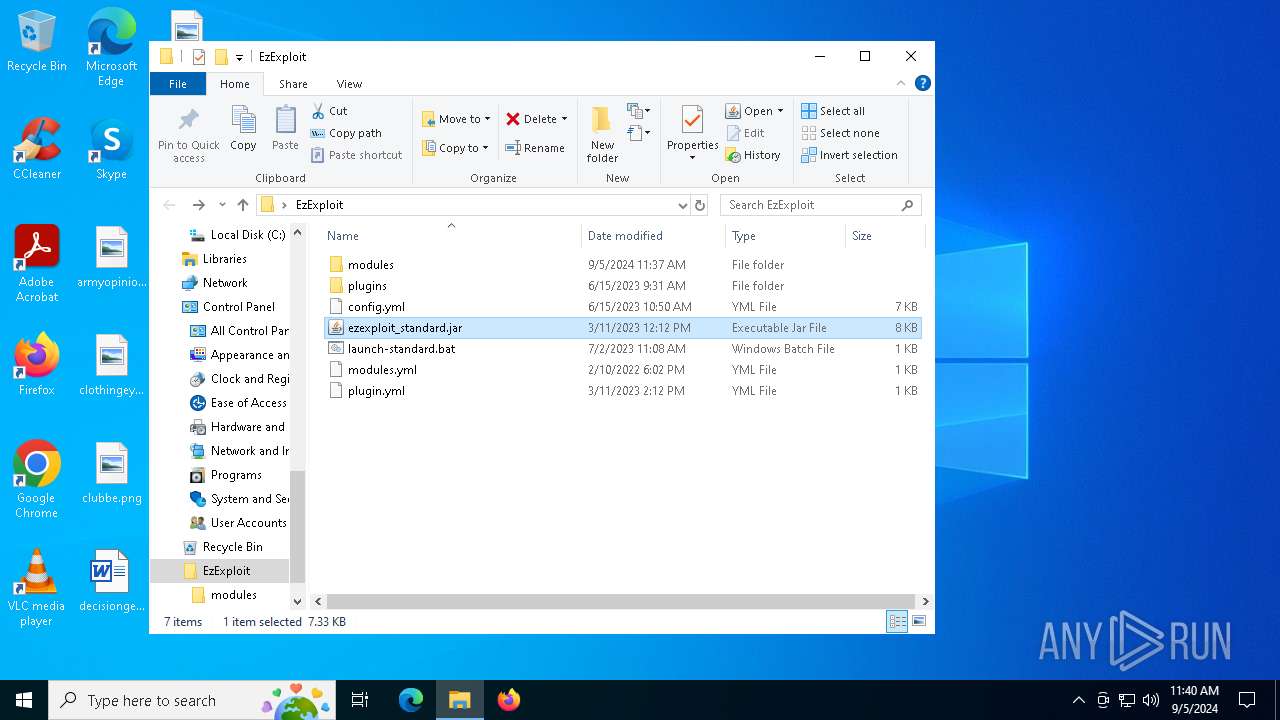
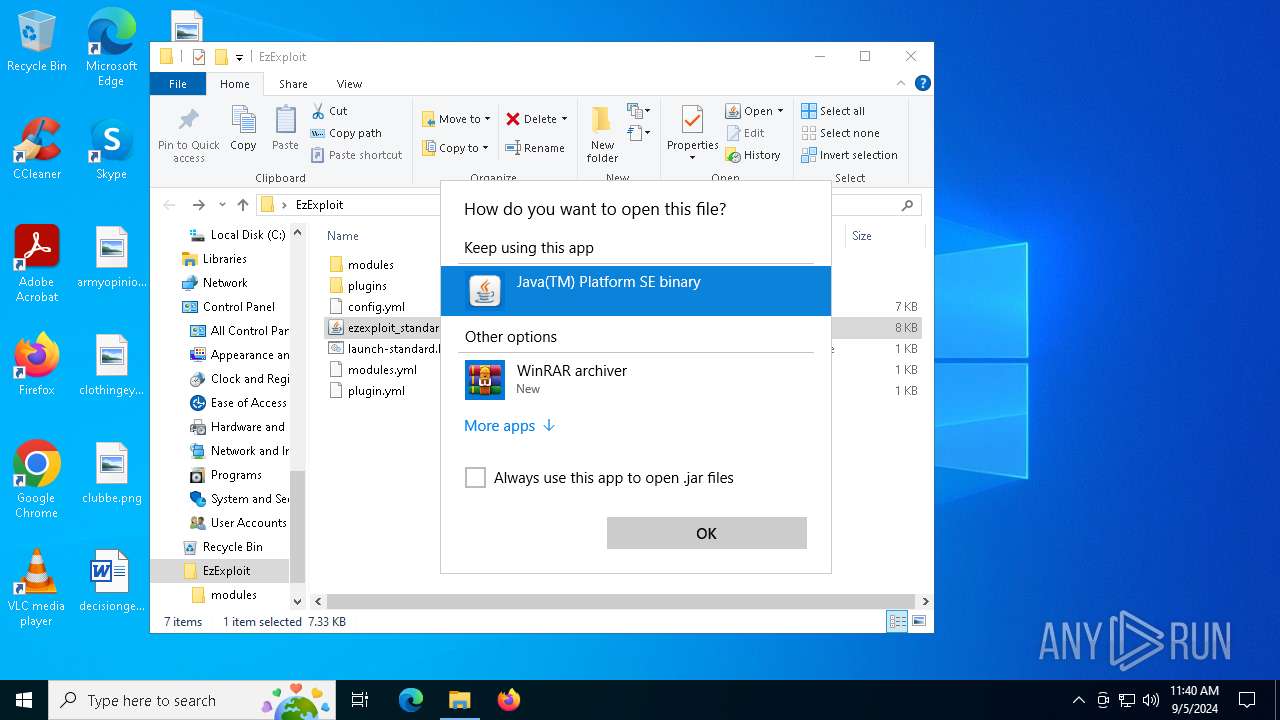
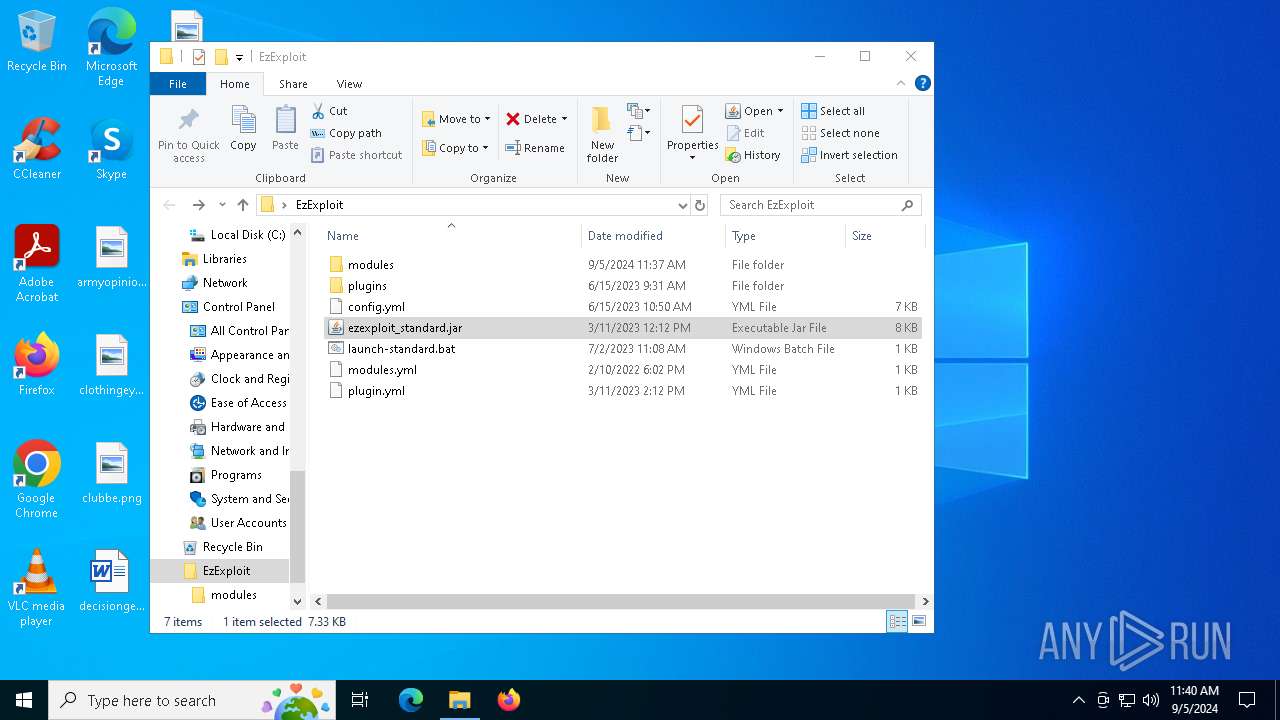
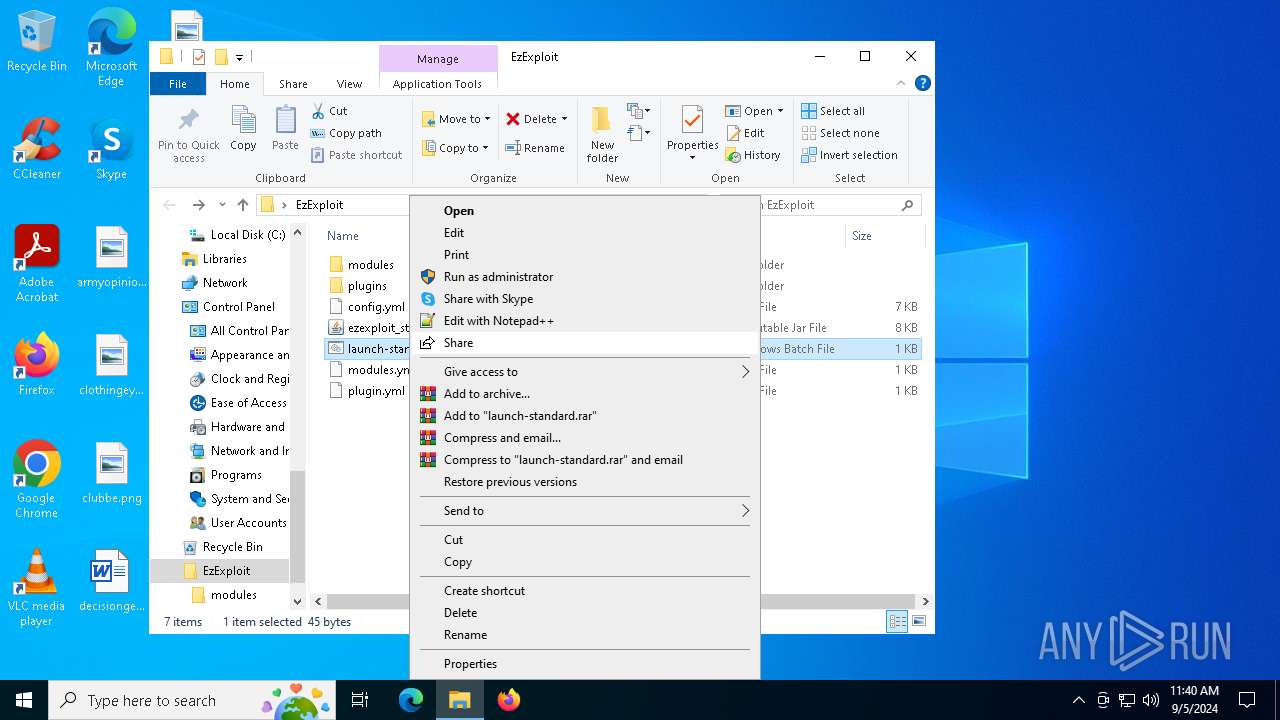
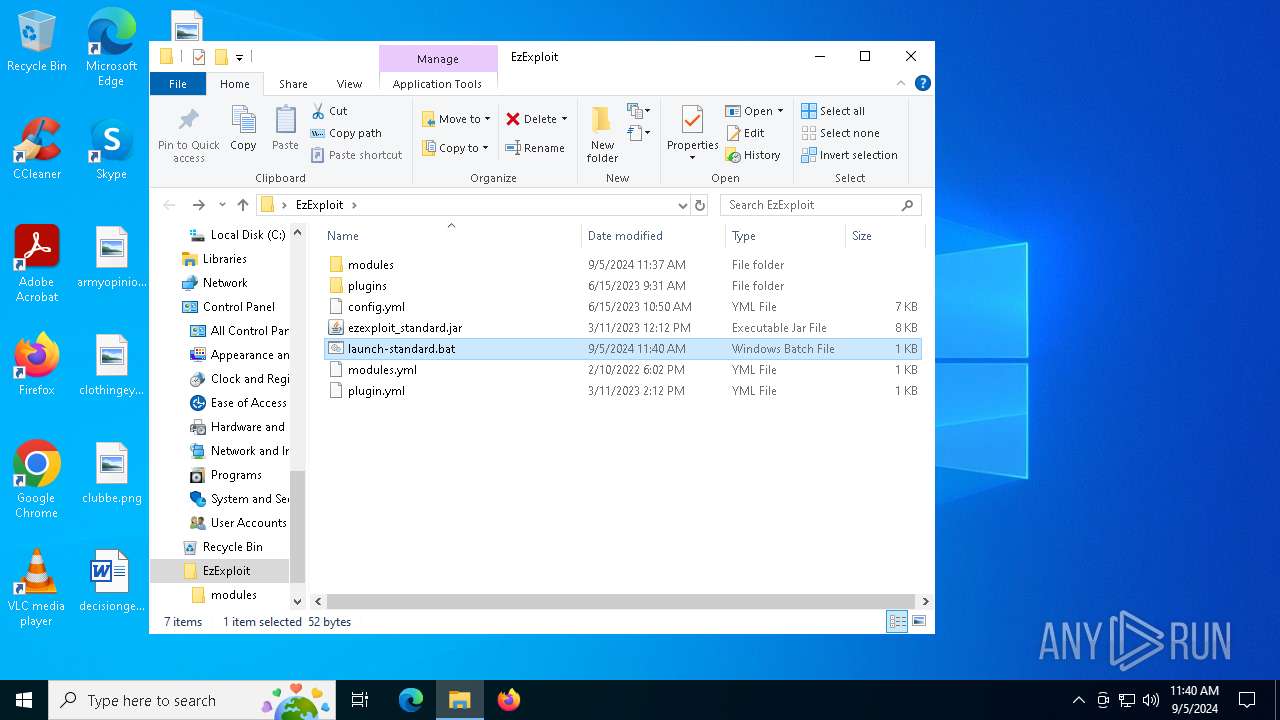
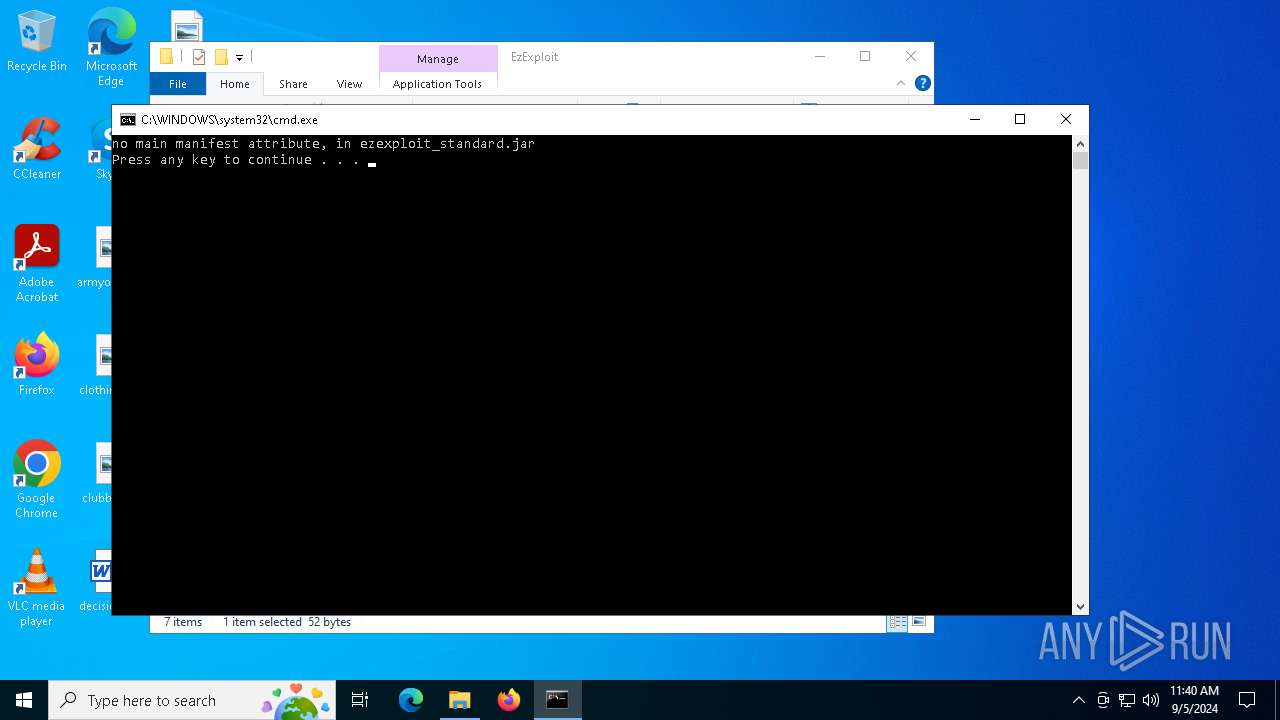
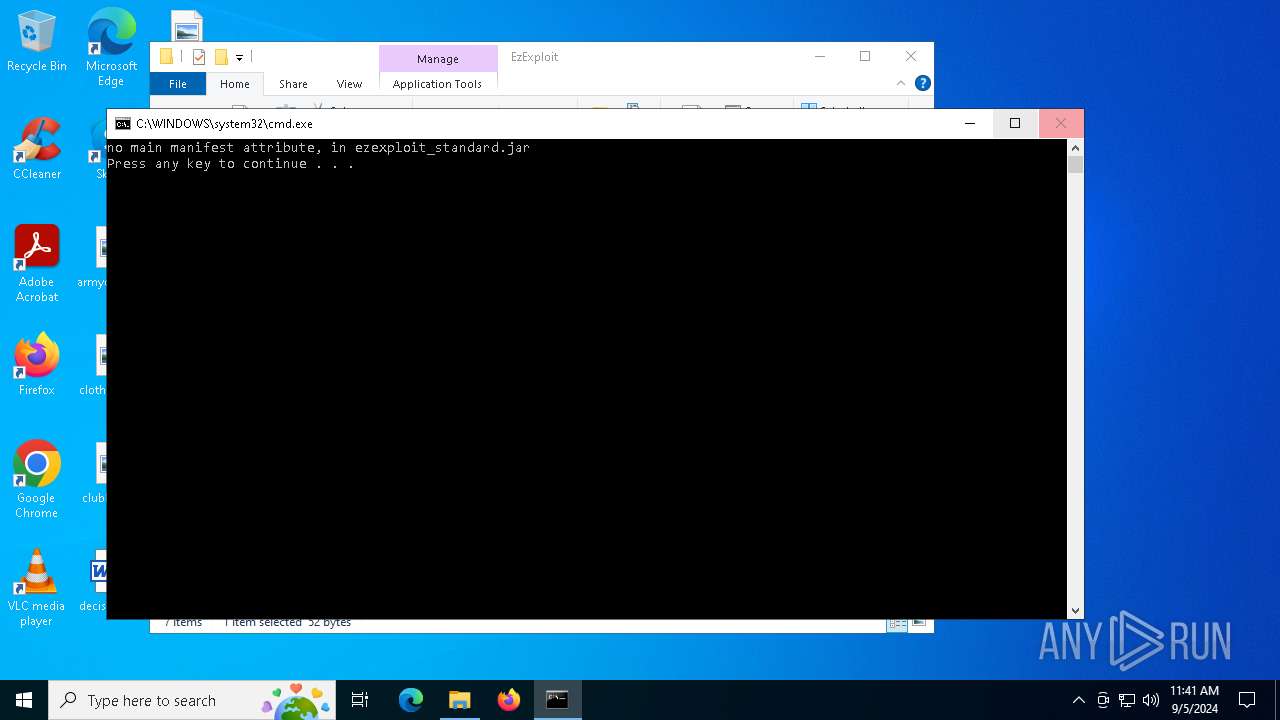
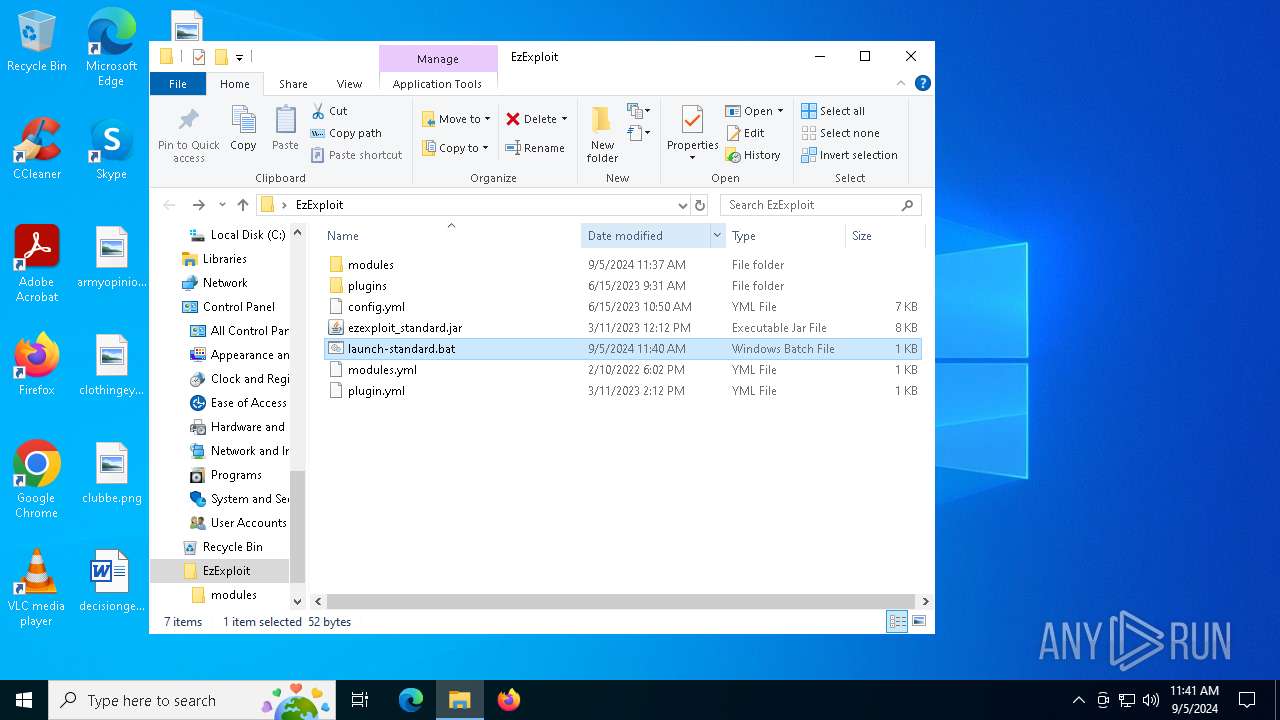
| File name: | EzExploit.zip |
| Full analysis: | https://app.any.run/tasks/8a396627-c085-4568-98f2-f4f239c131c7 |
| Verdict: | Malicious activity |
| Analysis date: | September 05, 2024, 11:39:36 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | D9A446A0754E884AEEF30AEBD8CB6E36 |
| SHA1: | 7867F141F13BBEA869D77483EA2CC85E5DBE204B |
| SHA256: | 8453A4888C6DBE1EC6E127CDF6DCAA16B8312413ADA1FC70477CED568A95BB67 |
| SSDEEP: | 1536:F3IitJGTz36y0Ry8eKoxMXLnswflQrmUUOCeIdcLd9C4TuFcCR1C:FYitQT2TgJEOrmxOCHdcLfC4TwbC |
MALICIOUS
No malicious indicators.SUSPICIOUS
Checks for Java to be installed
- java.exe (PID: 4732)
- java.exe (PID: 4008)
- java.exe (PID: 4316)
- java.exe (PID: 4824)
INFO
Creates files in the program directory
- java.exe (PID: 4732)
The process uses the downloaded file
- WinRAR.exe (PID: 6496)
- OpenWith.exe (PID: 4804)
- OpenWith.exe (PID: 2224)
Checks supported languages
- java.exe (PID: 4732)
- java.exe (PID: 4008)
- javaw.exe (PID: 1448)
- java.exe (PID: 4316)
- java.exe (PID: 4824)
Manual execution by a user
- cmd.exe (PID: 3332)
- cmd.exe (PID: 5744)
- notepad.exe (PID: 7028)
- cmd.exe (PID: 5400)
- notepad.exe (PID: 368)
- cmd.exe (PID: 4164)
Create files in a temporary directory
- java.exe (PID: 4732)
- java.exe (PID: 4008)
- javaw.exe (PID: 1448)
- java.exe (PID: 4316)
- java.exe (PID: 4824)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 4804)
- OpenWith.exe (PID: 2224)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 4804)
- notepad.exe (PID: 4920)
- OpenWith.exe (PID: 2224)
- notepad.exe (PID: 368)
- notepad.exe (PID: 7028)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2023:07:07 16:19:40 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | EzExploit/ |
Total processes
150
Monitored processes
22
Malicious processes
4
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
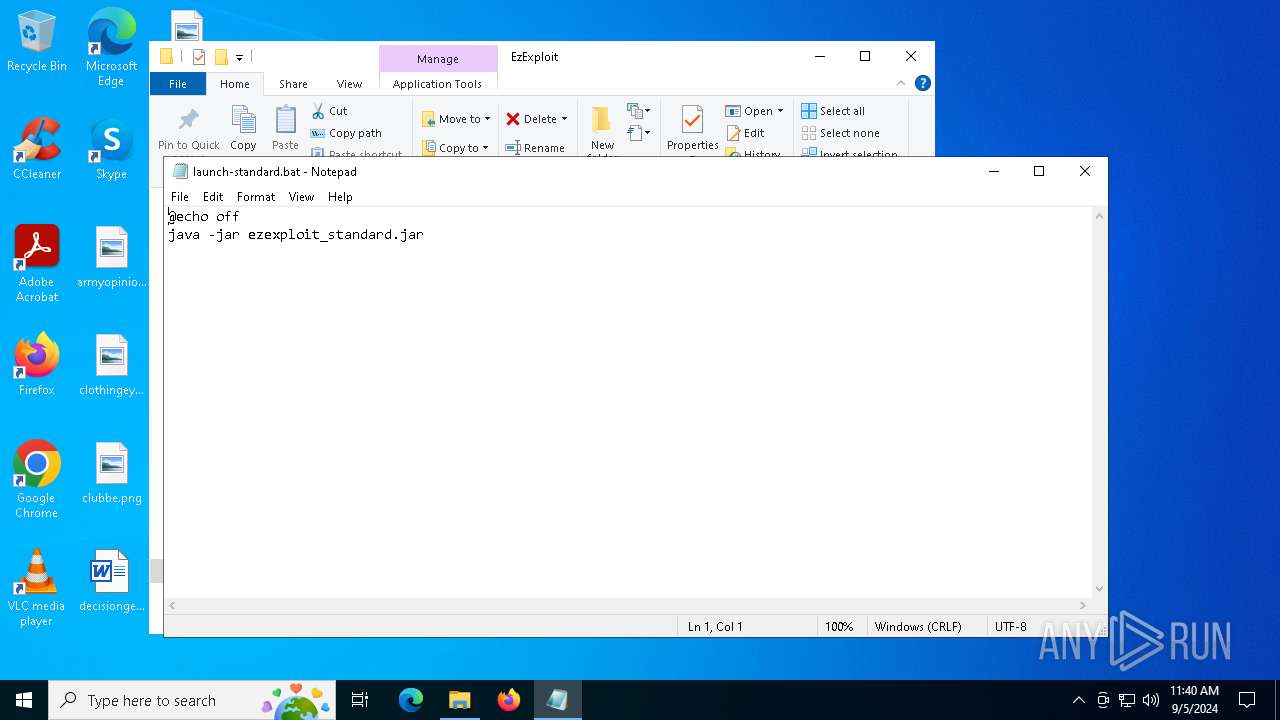
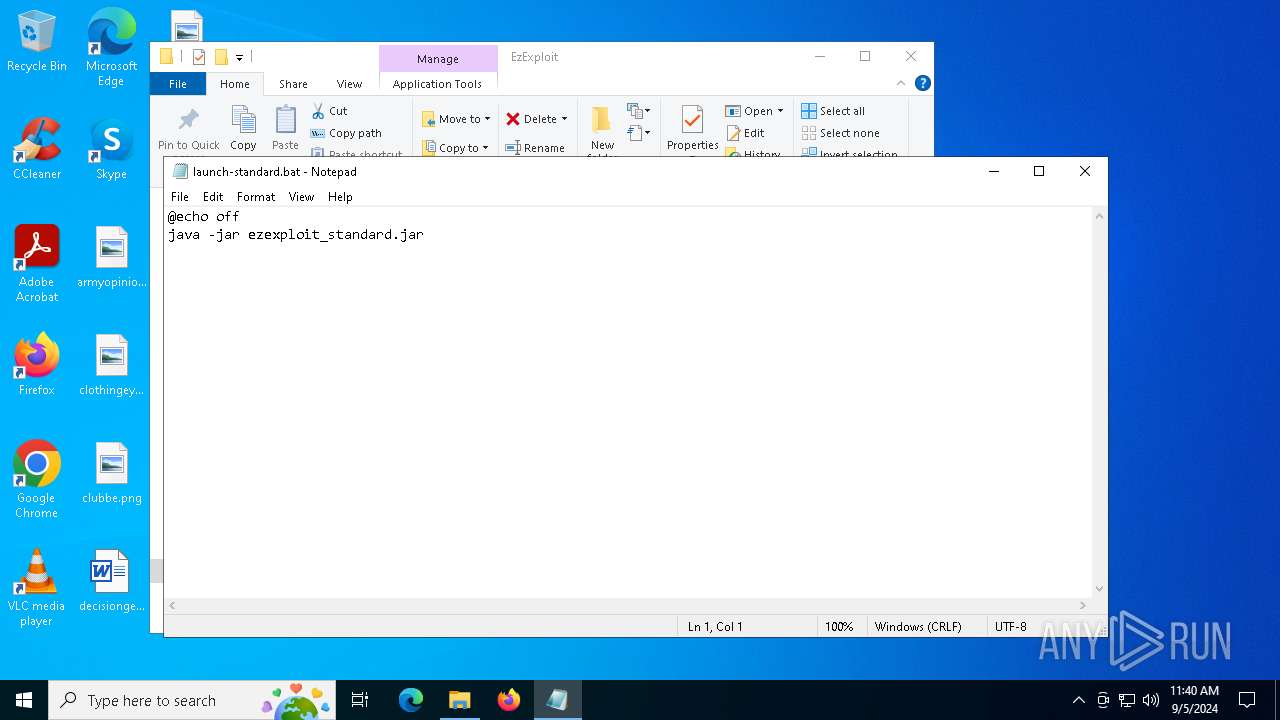
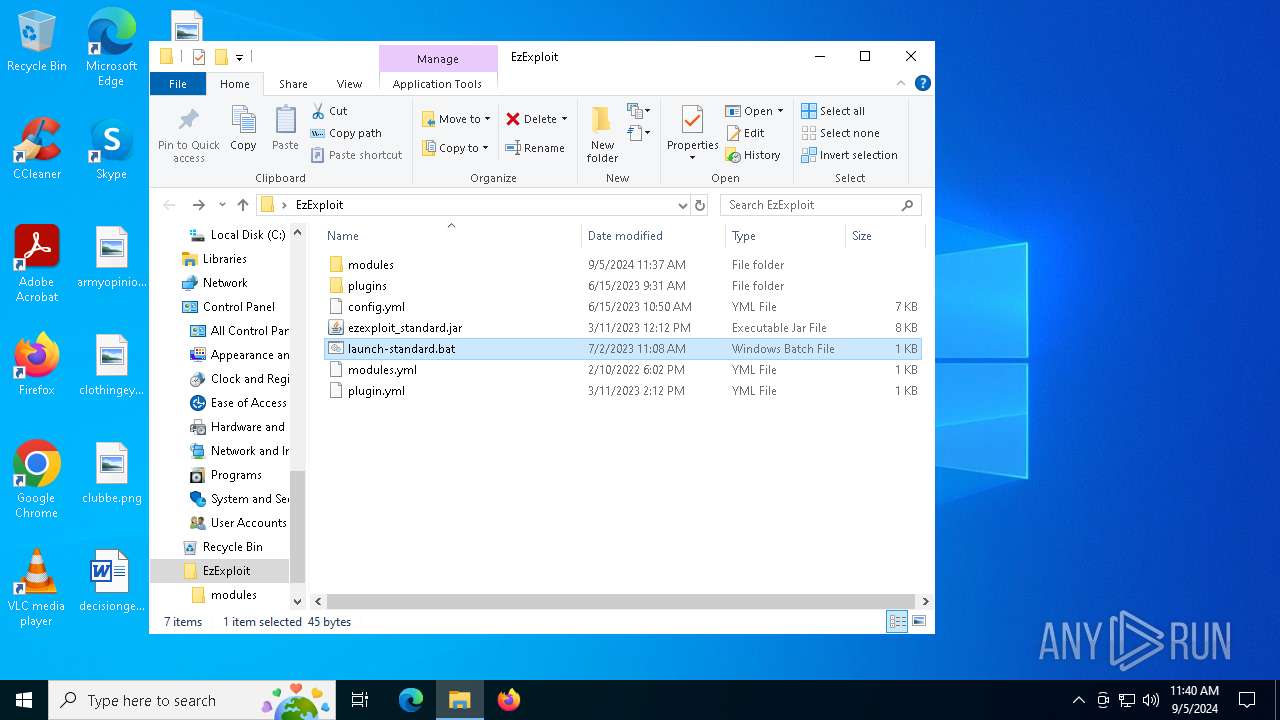
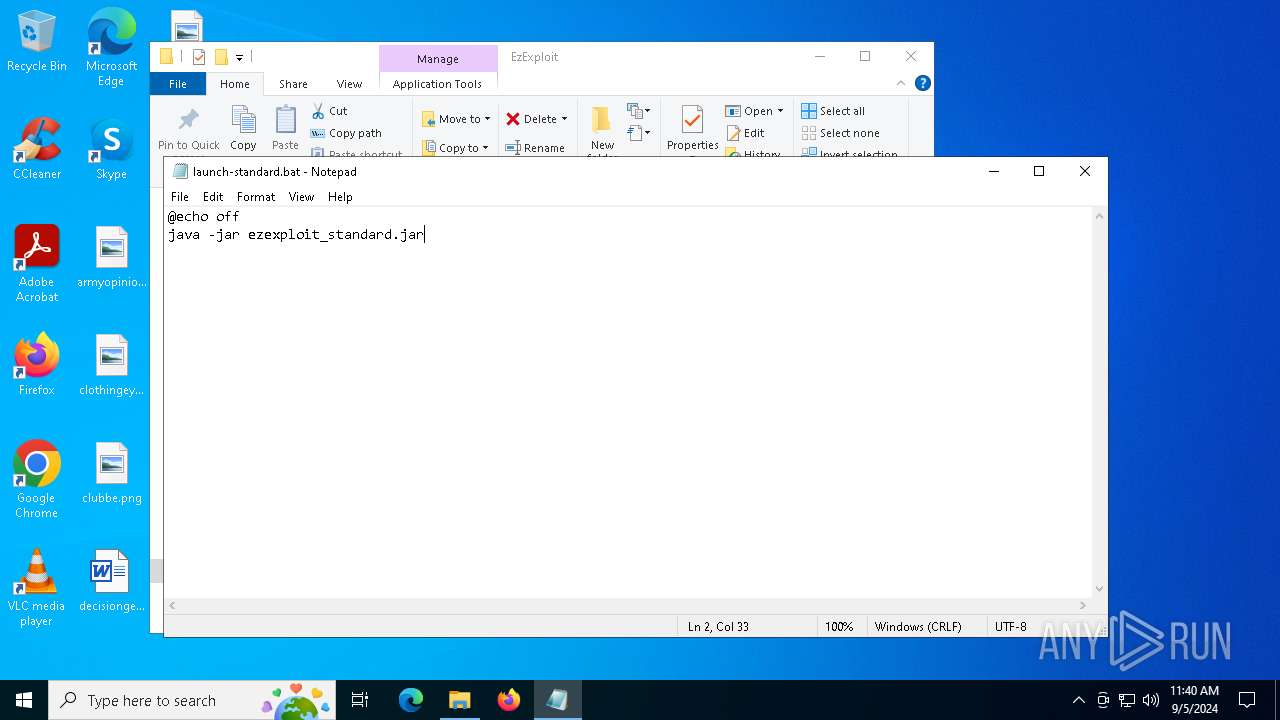
| 368 | "C:\WINDOWS\System32\NOTEPAD.EXE" C:\Users\admin\Desktop\EzExploit\launch-standard.bat | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1448 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -jar "C:\Users\admin\Desktop\EzExploit\ezexploit_standard.jar" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | OpenWith.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 1 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 2224 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2720 | C:\WINDOWS\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | java.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3332 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\EzExploit\launch-standard.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4008 | java -jar ezexploit_standard.jar | C:\Program Files (x86)\Common Files\Oracle\Java\javapath_target_2989500\java.exe | — | cmd.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 1 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 4164 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\EzExploit\launch-standard.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4316 | java -jar ezexploit_standard.jar | C:\Program Files (x86)\Common Files\Oracle\Java\javapath_target_2989500\java.exe | — | cmd.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 1 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 4732 | java -jar ezexploit_standard.jar | C:\Program Files (x86)\Common Files\Oracle\Java\javapath_target_2989500\java.exe | — | cmd.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 1 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 4804 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 327
Read events
5 305
Write events
22
Delete events
0
Modification events
| (PID) Process: | (6496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\EzExploit.zip | |||
| (PID) Process: | (6496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF1201000035000000D20400001E020000 | |||
| (PID) Process: | (6496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (6496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6496) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | psize |
Value: 80 | |||
Executable files
2
Suspicious files
7
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6496 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6496.19995\EzExploit\modules\cmd_server.jar | compressed | |
MD5:7390D87C1E8F52BC6FB77842B54C1A47 | SHA256:70E7C33275AB86E2A79D40DC76153B8BB5A29D9C18BFEEF8605D32CF8CA1AF37 | |||
| 6496 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6496.19995\EzExploit\modules\reconnect_yaml.jar | compressed | |
MD5:D1FDE0D321918ADC22002D9072EF23CA | SHA256:23147BFA63E2AC2ADD7C57480AB579F6A3D3B6091D480E712B610B1B9B79A4E4 | |||
| 6496 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6496.19995\EzExploit\modules\cmd_alert.jar | compressed | |
MD5:56416BFFC290B5531375807E134053F4 | SHA256:785152401573F49A3B1D9A3CF50EDB89B971ACF0BFF4F50C1BA93678B15E92CB | |||
| 6496 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6496.19995\EzExploit\modules\cmd_list.jar | compressed | |
MD5:355849A62628D973A7BBC8C2505E805A | SHA256:F4E62E6285EA6812A02495F31B9C2F7D3EBE753973B8A9F9CCAB2F7B3016AB1D | |||
| 6496 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6496.19995\EzExploit\ezexploit_standard.jar | java | |
MD5:109F51F21C044D3292F4A3EF3E2B5C0D | SHA256:249401D3529E543A99A63ADBCC8E6B09F62CC70C0B5F32D788D0F739CE16905A | |||
| 4732 | java.exe | C:\ProgramData\Oracle\Java\.oracle_jre_usage\17dfc292991c8061.timestamp | text | |
MD5:B1405AB62CE40297E2B0F86B778F7C80 | SHA256:689EDC6930C361FFDF84BAEB8DCE414637A94FEC86508BE0AEC040ECEA882A2B | |||
| 6496 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6496.19995\EzExploit\plugins\VdsPro.jar | compressed | |
MD5:49322DFBB0BEAED49C9DC64C94924FB0 | SHA256:B1BA51E4D0A434601B25CEA274E01D35085FF7D3422B58DCABCF6B0606A5089F | |||
| 6496 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6496.19995\EzExploit\launch-standard.bat | text | |
MD5:94C75B944240C0176898696F27116665 | SHA256:874F32053F82FCC17168D294D239FEDF256958CC9CA90176153A8EB62886B4BE | |||
| 6496 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6496.19995\EzExploit\plugins\RconFix.jar | java | |
MD5:BB0199FAD177D12AC638D2DA61F9A4DF | SHA256:87E3C42B1CDBA0B17983EE04ED656D94EBC2101923F4BA4F6DD96DEA83705751 | |||
| 6496 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6496.19995\EzExploit\modules.yml | text | |
MD5:18F81D9DE7DD889E0277E9F67F7DF9BE | SHA256:75A3D3E3D4023E832463B0020B08325A5CAD6CDB0603B4D25FDACACF3CC2665D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
27
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3652 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
936 | SIHClient.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
936 | SIHClient.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | 40.119.249.228:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.119.249.228:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
4316 | RUXIMICS.exe | 40.119.249.228:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
2120 | MoUsoCoreWorker.exe | 23.32.185.131:80 | www.microsoft.com | AKAMAI-AS | BR | whitelisted |
6872 | svchost.exe | 40.119.249.228:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3652 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |