| File name: | 2025-06-21_5abad4e59fcccf9f3776cab3c9731c2f_black-basta_cobalt-strike_satacom_vidar |
| Full analysis: | https://app.any.run/tasks/f2a0042c-302f-495d-98f7-426a3dab8d8a |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 11:11:42 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 8 sections |
| MD5: | 5ABAD4E59FCCCF9F3776CAB3C9731C2F |
| SHA1: | C3367CA195879A1145EE44B0823E2B62B8F516EE |
| SHA256: | 843B0E8D7A2F458AC62A83C3D3A9BA6B088B2F67779C67A99538F7D1B325B729 |
| SSDEEP: | 98304:DM0F9R+Mi2wtv+lClt6u3++7vgv4r3zKcsrwwi7J/CkcubGTCJklp/3fZ1+UnxDb:Z1bVbD4s0boXloJrO |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- 2025-06-21_5abad4e59fcccf9f3776cab3c9731c2f_black-basta_cobalt-strike_satacom_vidar.exe (PID: 4192)
Executable content was dropped or overwritten
- 2025-06-21_5abad4e59fcccf9f3776cab3c9731c2f_black-basta_cobalt-strike_satacom_vidar.exe (PID: 4192)
Reads the date of Windows installation
- 2025-06-21_5abad4e59fcccf9f3776cab3c9731c2f_black-basta_cobalt-strike_satacom_vidar.exe (PID: 4192)
Reads security settings of Internet Explorer
- 2025-06-21_5abad4e59fcccf9f3776cab3c9731c2f_black-basta_cobalt-strike_satacom_vidar.exe (PID: 4192)
Checks for external IP
- svchost.exe (PID: 2200)
- FRP.exe (PID: 6312)
There is functionality for taking screenshot (YARA)
- 2025-06-21_5abad4e59fcccf9f3776cab3c9731c2f_black-basta_cobalt-strike_satacom_vidar.exe (PID: 4192)
- FRP.exe (PID: 6312)
INFO
The sample compiled with english language support
- 2025-06-21_5abad4e59fcccf9f3776cab3c9731c2f_black-basta_cobalt-strike_satacom_vidar.exe (PID: 4192)
Reads the computer name
- 2025-06-21_5abad4e59fcccf9f3776cab3c9731c2f_black-basta_cobalt-strike_satacom_vidar.exe (PID: 4192)
- FRP.exe (PID: 6312)
Create files in a temporary directory
- 2025-06-21_5abad4e59fcccf9f3776cab3c9731c2f_black-basta_cobalt-strike_satacom_vidar.exe (PID: 4192)
Checks supported languages
- 2025-06-21_5abad4e59fcccf9f3776cab3c9731c2f_black-basta_cobalt-strike_satacom_vidar.exe (PID: 4192)
- FRP.exe (PID: 6312)
Process checks computer location settings
- 2025-06-21_5abad4e59fcccf9f3776cab3c9731c2f_black-basta_cobalt-strike_satacom_vidar.exe (PID: 4192)
Reads the machine GUID from the registry
- FRP.exe (PID: 6312)
Reads Environment values
- FRP.exe (PID: 6312)
Disables trace logs
- FRP.exe (PID: 6312)
Checks proxy server information
- FRP.exe (PID: 6312)
- slui.exe (PID: 1132)
Reads the software policy settings
- FRP.exe (PID: 6312)
- slui.exe (PID: 1132)
Creates files in the program directory
- FRP.exe (PID: 6312)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:05:12 10:17:07+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.33 |
| CodeSize: | 288768 |
| InitializedDataSize: | 137216 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x32ee0 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
Total processes
134
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1132 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4192 | "C:\Users\admin\Desktop\2025-06-21_5abad4e59fcccf9f3776cab3c9731c2f_black-basta_cobalt-strike_satacom_vidar.exe" | C:\Users\admin\Desktop\2025-06-21_5abad4e59fcccf9f3776cab3c9731c2f_black-basta_cobalt-strike_satacom_vidar.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
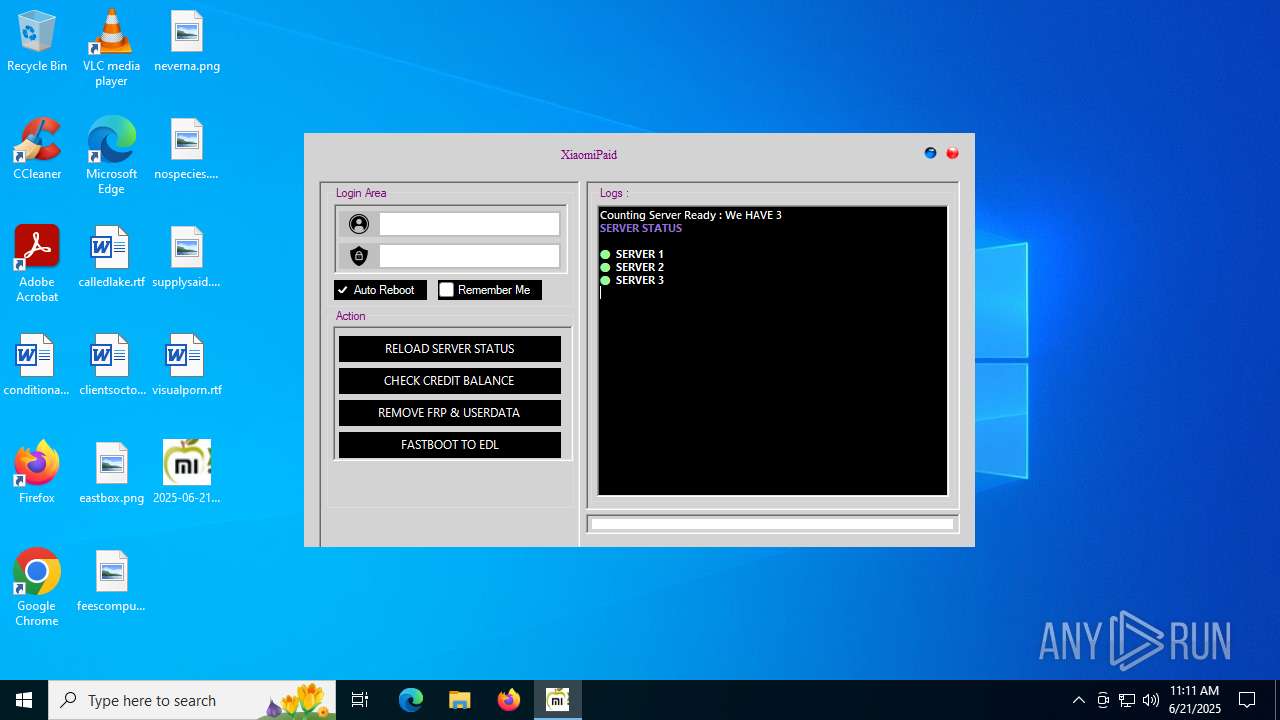
| 6312 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\FRP.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\FRP.exe | 2025-06-21_5abad4e59fcccf9f3776cab3c9731c2f_black-basta_cobalt-strike_satacom_vidar.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: XiaomiPaid & Developed by HXRU Team Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
7 876
Read events
7 862
Write events
14
Delete events
0
Modification events
| (PID) Process: | (6312) FRP.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\FRP_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6312) FRP.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\FRP_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6312) FRP.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\FRP_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6312) FRP.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\FRP_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (6312) FRP.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\FRP_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (6312) FRP.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\FRP_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (6312) FRP.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\FRP_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (6312) FRP.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\FRP_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6312) FRP.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\FRP_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6312) FRP.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\FRP_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
29
Suspicious files
1
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4192 | 2025-06-21_5abad4e59fcccf9f3776cab3c9731c2f_black-basta_cobalt-strike_satacom_vidar.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\System.Threading.Tasks.Extensions.dll | executable | |
MD5:E1E9D7D46E5CD9525C5927DC98D9ECC7 | SHA256:4F81FFD0DC7204DB75AFC35EA4291769B07C440592F28894260EEA76626A23C6 | |||
| 4192 | 2025-06-21_5abad4e59fcccf9f3776cab3c9731c2f_black-basta_cobalt-strike_satacom_vidar.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\FRP.exe | executable | |
MD5:A6A5EDB57BCF99B3E80F8B25BC234B65 | SHA256:79430B67F3DC414D7C32E53C33B5F5790DFDF5CE11D8186715ED4AE009D81C57 | |||
| 4192 | 2025-06-21_5abad4e59fcccf9f3776cab3c9731c2f_black-basta_cobalt-strike_satacom_vidar.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\FRP.exe.config | xml | |
MD5:DE9A517147DE0EF076F8B6C1BB1E2514 | SHA256:CA7A90FBD7FF3AAAD83876E9E2EB9AF36EEBC9426EB6F8942E86C89EC5AD710F | |||
| 4192 | 2025-06-21_5abad4e59fcccf9f3776cab3c9731c2f_black-basta_cobalt-strike_satacom_vidar.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Guna.UI.dll | executable | |
MD5:8673EAE95D67E5EB19F0ECA3111408E8 | SHA256:576D2DE2C9EF5BC1EA9BDD73AE8F408004260037C3B72227EED27E995166276D | |||
| 4192 | 2025-06-21_5abad4e59fcccf9f3776cab3c9731c2f_black-basta_cobalt-strike_satacom_vidar.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Microsoft.Bcl.AsyncInterfaces.dll | executable | |
MD5:7BFC54C1CD6680968D959E3B400FB521 | SHA256:59F2E6DCEACD9435033BB932D4A1ADD7356F72E9EFF1BF5C396AB3F8254AD81D | |||
| 4192 | 2025-06-21_5abad4e59fcccf9f3776cab3c9731c2f_black-basta_cobalt-strike_satacom_vidar.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Newtonsoft.Json.dll | executable | |
MD5:195FFB7167DB3219B217C4FD439EEDD6 | SHA256:E1E27AF7B07EEEDF5CE71A9255F0422816A6FC5849A483C6714E1B472044FA9D | |||
| 4192 | 2025-06-21_5abad4e59fcccf9f3776cab3c9731c2f_black-basta_cobalt-strike_satacom_vidar.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\System.Buffers.dll | executable | |
MD5:ECDFE8EDE869D2CCC6BF99981EA96400 | SHA256:ACCCCFBE45D9F08FFEED9916E37B33E98C65BE012CFFF6E7FA7B67210CE1FEFB | |||
| 4192 | 2025-06-21_5abad4e59fcccf9f3776cab3c9731c2f_black-basta_cobalt-strike_satacom_vidar.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\System.Memory.dll | executable | |
MD5:F09441A1EE47FB3E6571A3A448E05BAF | SHA256:BF3FB84664F4097F1A8A9BC71A51DCF8CF1A905D4080A4D290DA1730866E856F | |||
| 4192 | 2025-06-21_5abad4e59fcccf9f3776cab3c9731c2f_black-basta_cobalt-strike_satacom_vidar.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\System.Text.Json.dll | executable | |
MD5:A29D8FFB65AFD4837B39E0F0EA7A79CE | SHA256:AAD290BABCAEE9D3CB7B2A6E6A885FDC3F60A6A13DF9F972BD249BB608BC5F0D | |||
| 4192 | 2025-06-21_5abad4e59fcccf9f3776cab3c9731c2f_black-basta_cobalt-strike_satacom_vidar.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\System.Text.Encodings.Web.dll | executable | |
MD5:84FBE3BE88F70ECC9EBD332650680ED5 | SHA256:B5CB6B9FDB277A97D975A949EE17BDC57407D20EACE857996540EAAD6DAC487F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
23
DNS requests
9
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 188.114.97.3:443 | https://xiaomipaid.com/apihidden/get_prices.php | unknown | text | 89 b | unknown |
1268 | svchost.exe | GET | 200 | 23.55.104.190:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.55.104.190:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5476 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 188.114.96.3:443 | https://xiaomipaid.com/apihidden/serverstat.php?id=1 | unknown | — | — | unknown |
— | — | POST | 200 | 188.114.97.3:443 | https://xiaomipaid.com/apihidden/server_status.php | unknown | binary | 1.08 Kb | unknown |
6312 | FRP.exe | GET | 200 | 34.117.59.81:80 | http://ipinfo.io/ip | unknown | — | — | whitelisted |
— | — | GET | 200 | 188.114.97.3:443 | https://xiaomipaid.com/apihidden/serverstat.php?id=2 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5476 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 23.55.104.190:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.55.104.190:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5476 | RUXIMICS.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
xiaomipaid.com |
| unknown |
ipinfo.io |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ipinfo .io) |
6312 | FRP.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ipinfo.io |
6312 | FRP.exe | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] An IP address was received from the server as a result of an HTTP request |