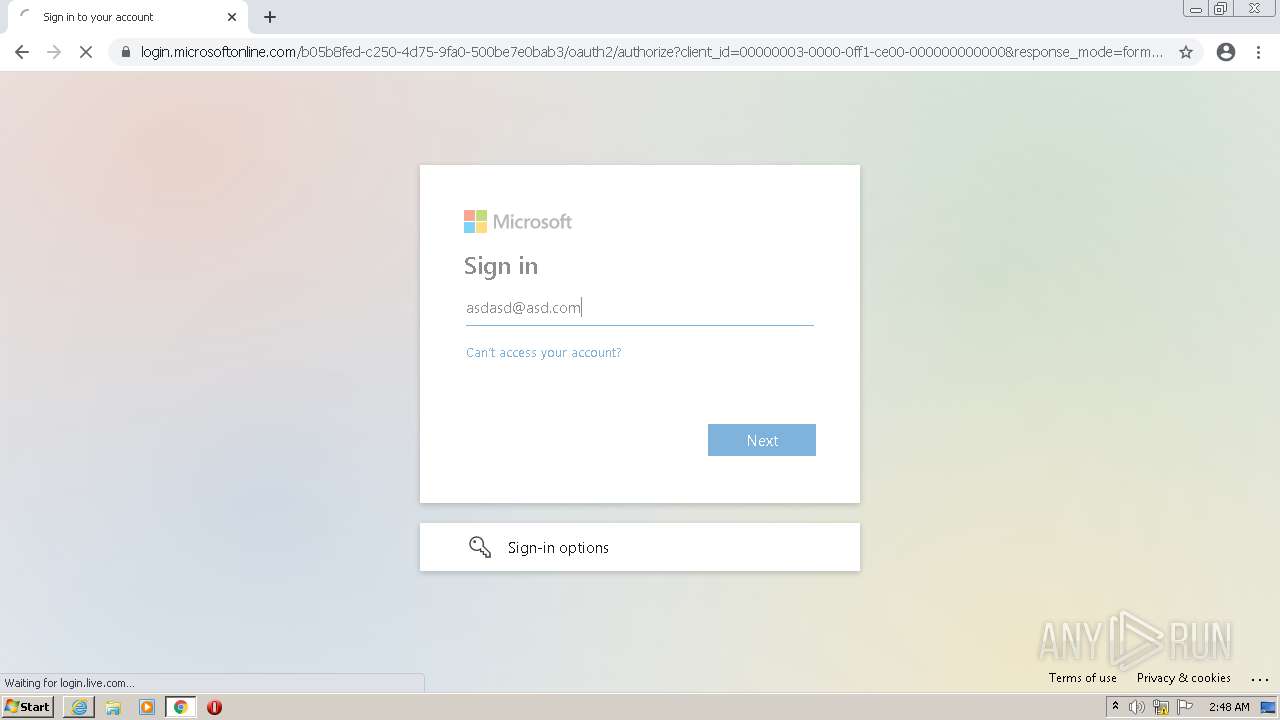
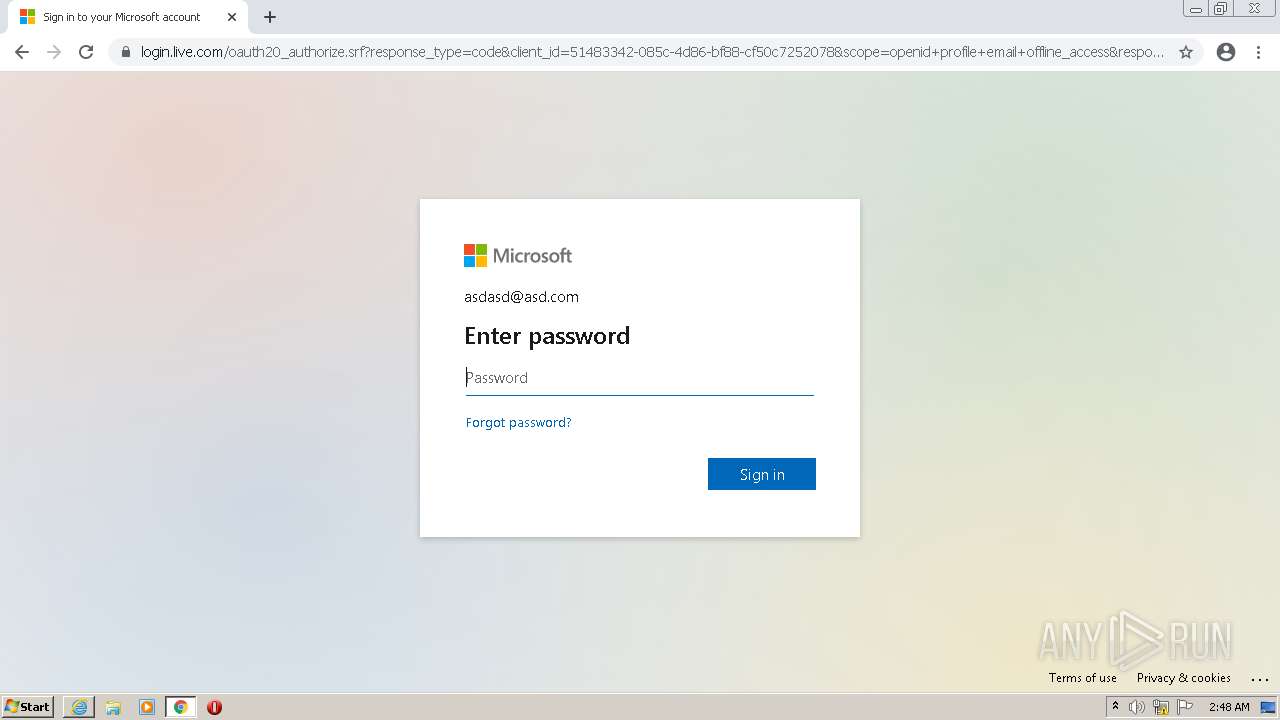
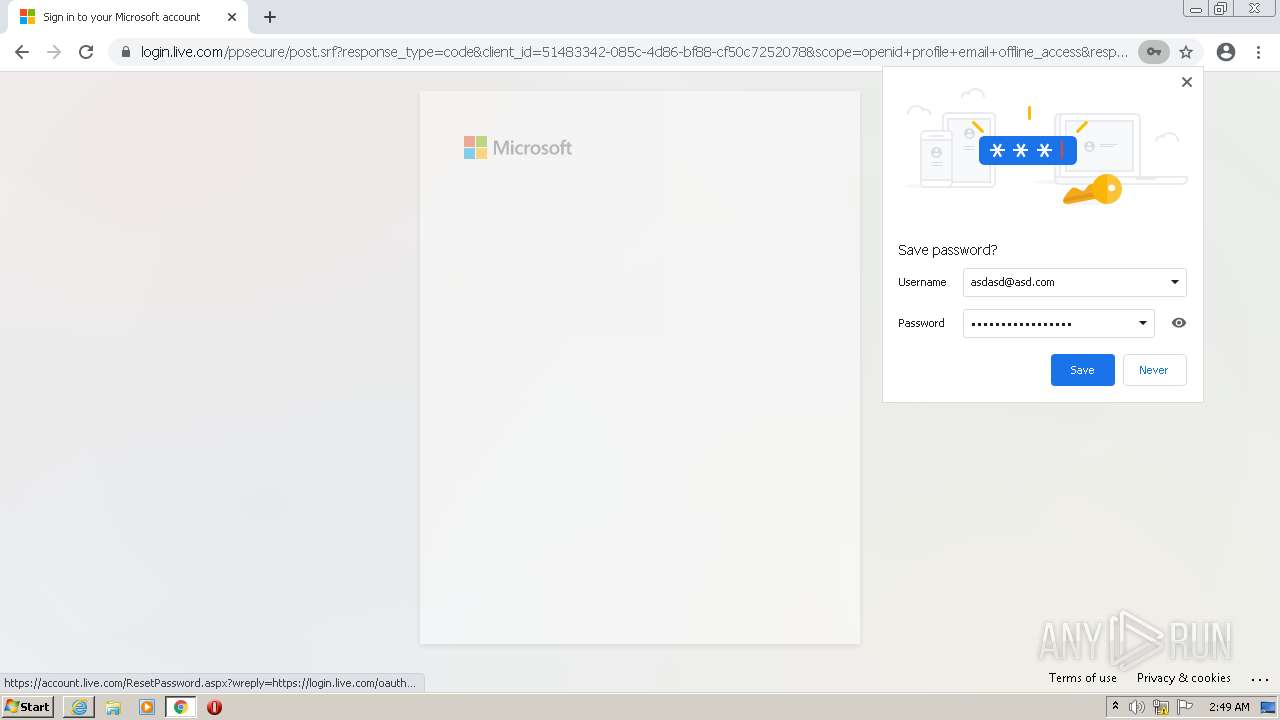
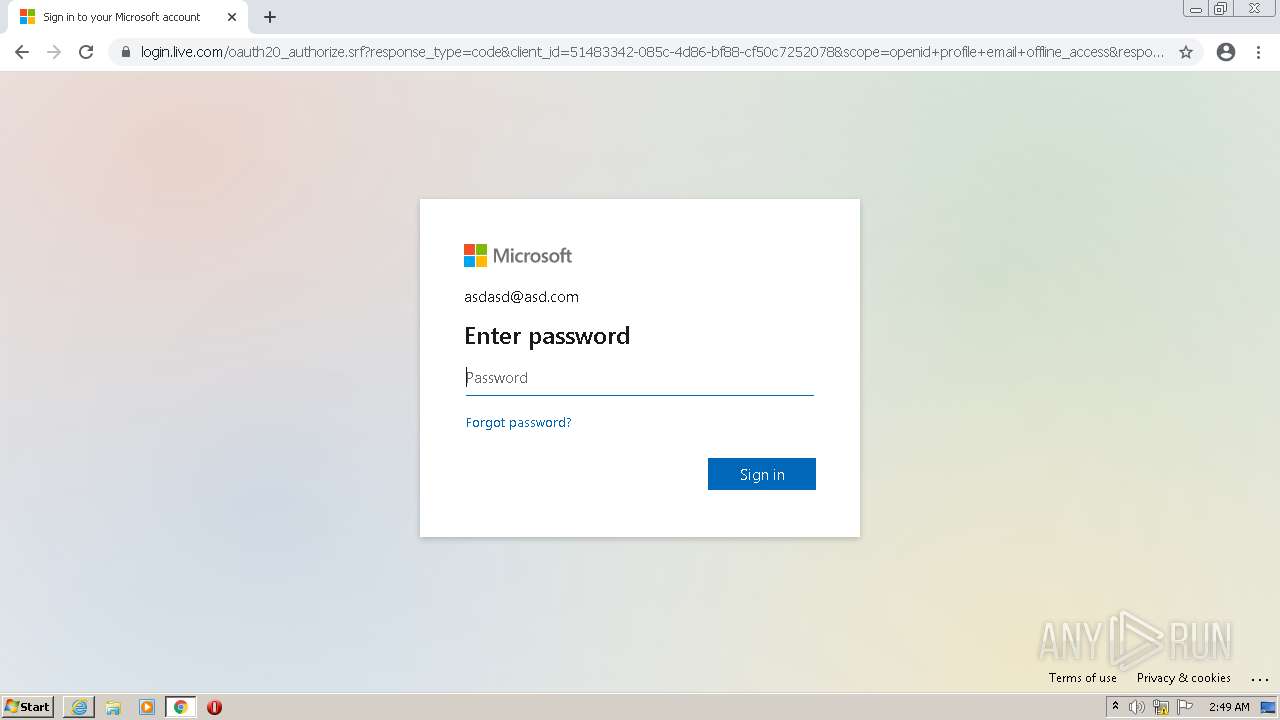
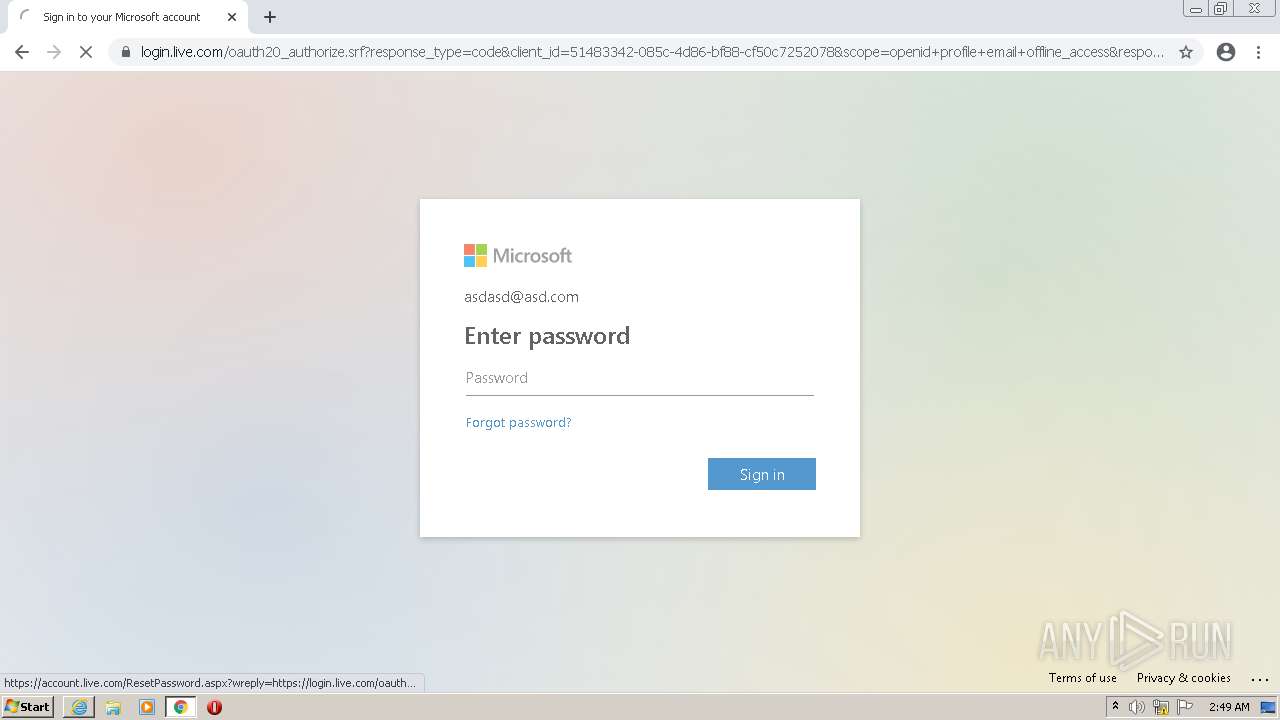
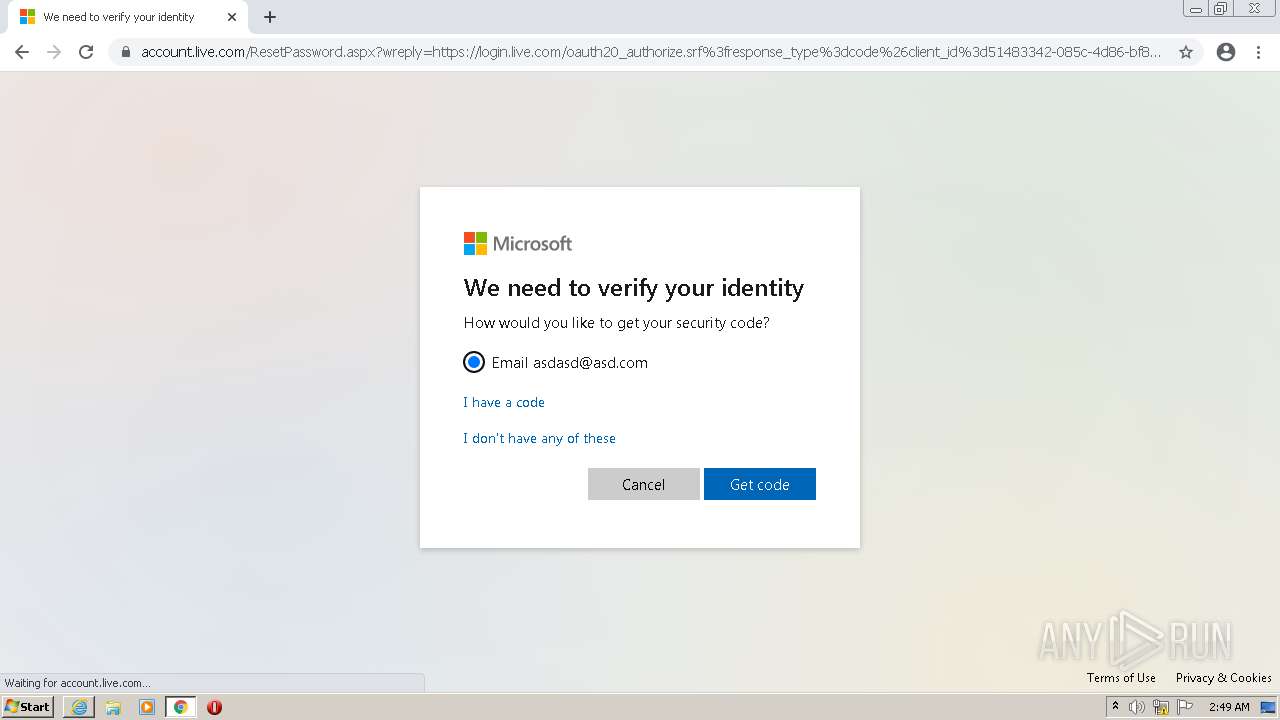
| URL: | https://alpine4corp-my.sharepoint.com/:f:/g/personal/nhackney_qcamfg_com/Ekwud9I5pRdLjG3_nuIP_q4BgCB82RZT19zZqFyWREcUDw?e=LXtKIl |
| Full analysis: | https://app.any.run/tasks/73f16733-31d0-446b-a41f-a358a2e9de95 |
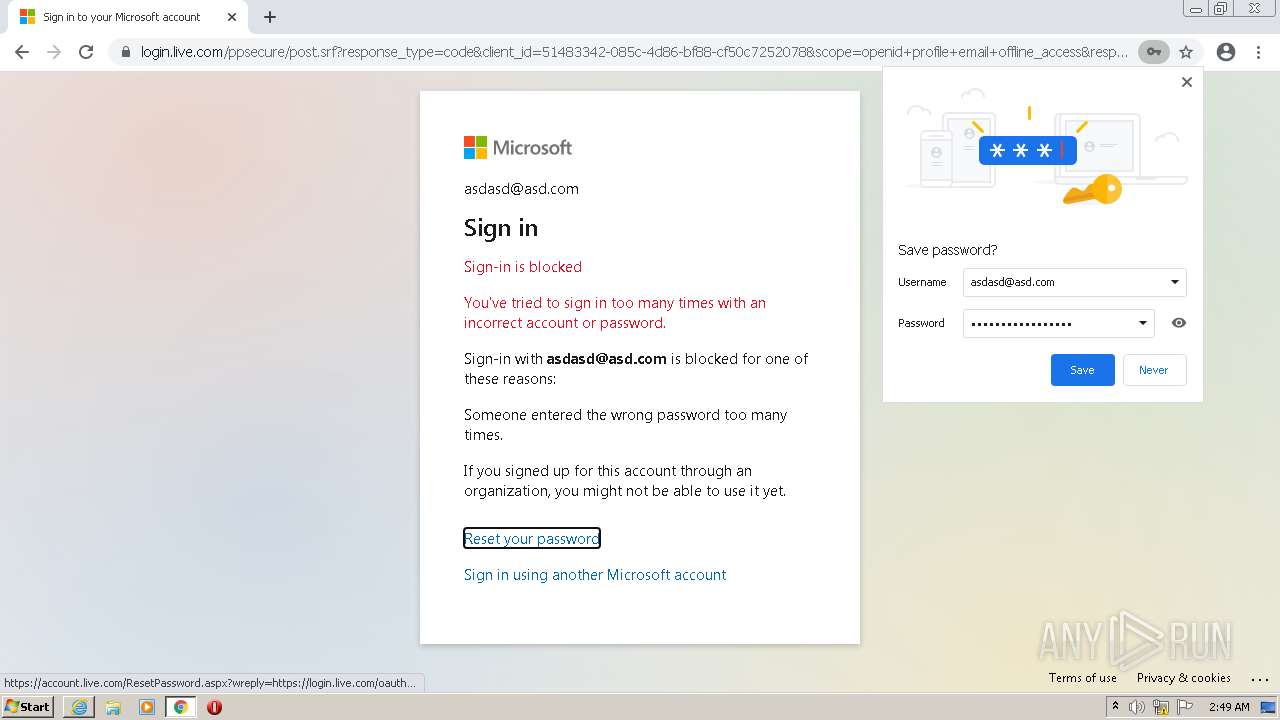
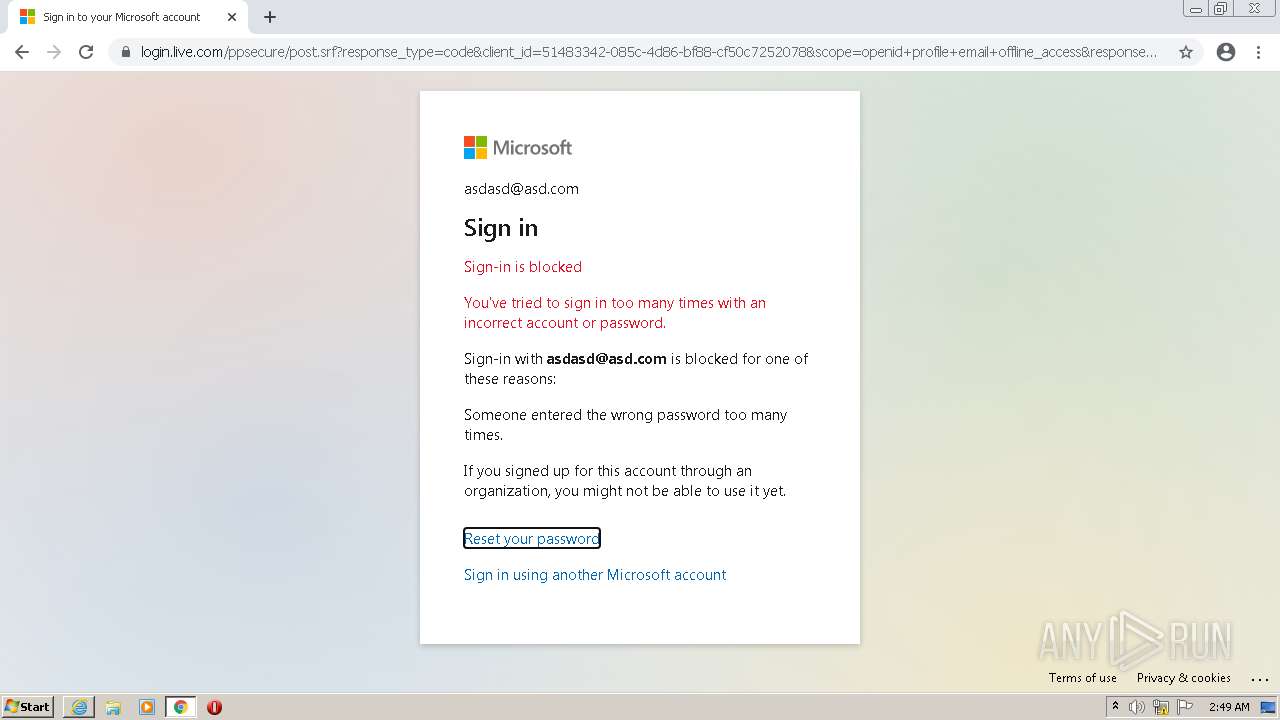
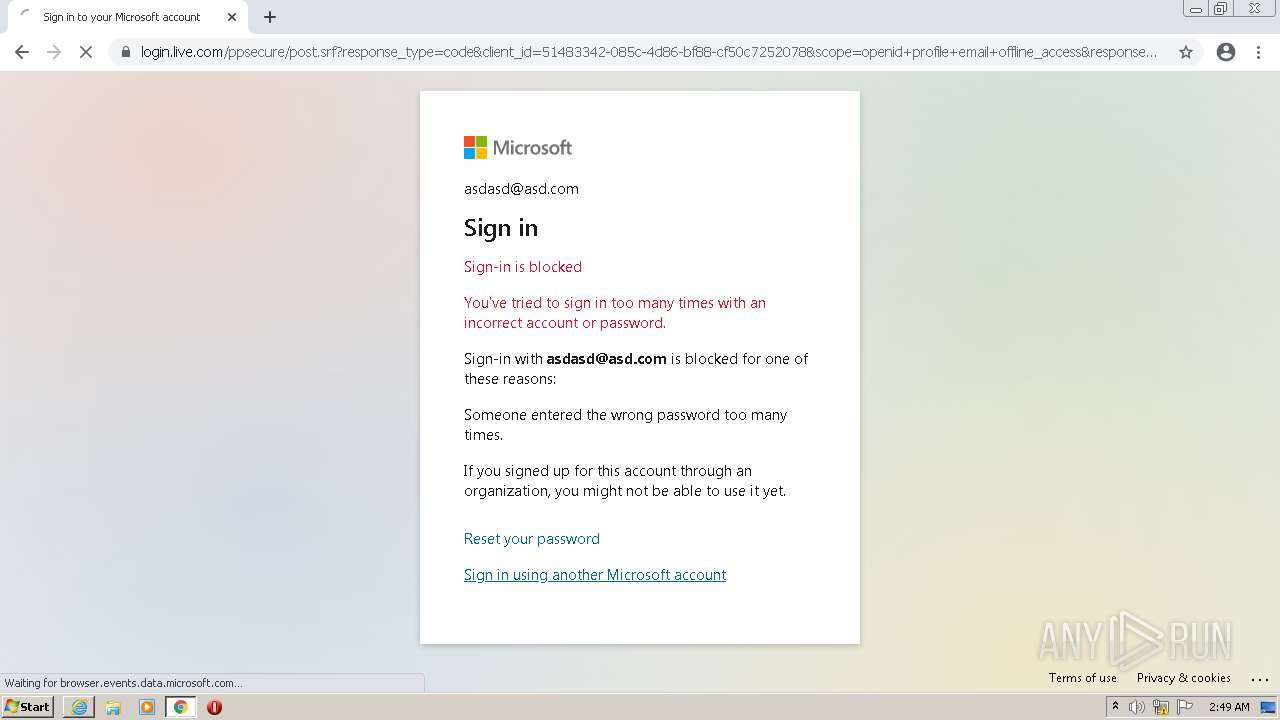
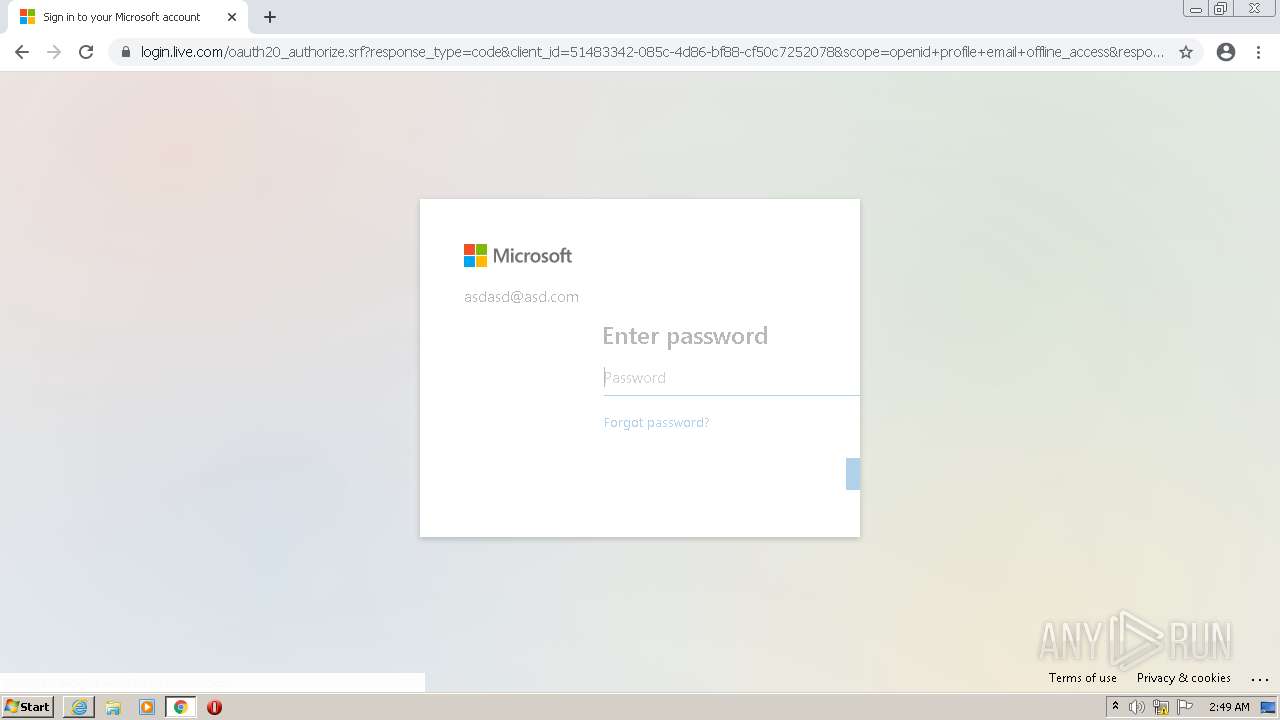
| Verdict: | Malicious activity |
| Analysis date: | January 25, 2022, 02:48:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | DD2F1634C8AF99F28D7E41DBAA8BCD50 |
| SHA1: | F5F29E963DC99C74FDAACC26398761F9F2EED002 |
| SHA256: | 84376AEC0C66D320BE72DCCD9F69EEA8774368FD2711EC51484B40B5F2EA7584 |
| SSDEEP: | 3:N8GM0R/AArL5WJSLNWg+KI7yCpGQsimnd/Hc33sEsNJ:2GM7Af14g+T3Md/Hq3s/J |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3676)
Modifies files in Chrome extension folder
- chrome.exe (PID: 3432)
INFO
Changes internet zones settings
- iexplore.exe (PID: 2760)
Checks supported languages
- iexplore.exe (PID: 2760)
- iexplore.exe (PID: 3676)
- chrome.exe (PID: 3432)
- chrome.exe (PID: 3616)
- chrome.exe (PID: 2188)
- chrome.exe (PID: 2312)
- chrome.exe (PID: 1468)
- chrome.exe (PID: 1908)
- chrome.exe (PID: 444)
- chrome.exe (PID: 2016)
- chrome.exe (PID: 4016)
- chrome.exe (PID: 2552)
- chrome.exe (PID: 2320)
- chrome.exe (PID: 1080)
- chrome.exe (PID: 2232)
- chrome.exe (PID: 3008)
- chrome.exe (PID: 320)
- chrome.exe (PID: 3960)
- chrome.exe (PID: 2748)
- chrome.exe (PID: 2568)
- chrome.exe (PID: 2224)
- chrome.exe (PID: 3028)
Reads the computer name
- iexplore.exe (PID: 2760)
- iexplore.exe (PID: 3676)
- chrome.exe (PID: 3432)
- chrome.exe (PID: 2312)
- chrome.exe (PID: 2188)
- chrome.exe (PID: 4016)
- chrome.exe (PID: 2552)
- chrome.exe (PID: 2224)
- chrome.exe (PID: 3028)
Application launched itself
- iexplore.exe (PID: 2760)
- chrome.exe (PID: 3432)
Checks Windows Trust Settings
- iexplore.exe (PID: 3676)
- iexplore.exe (PID: 2760)
Reads settings of System Certificates
- iexplore.exe (PID: 3676)
- iexplore.exe (PID: 2760)
- chrome.exe (PID: 2188)
Reads internet explorer settings
- iexplore.exe (PID: 3676)
Manual execution by user
- chrome.exe (PID: 3432)
Reads the hosts file
- chrome.exe (PID: 3432)
- chrome.exe (PID: 2188)
Reads the date of Windows installation
- chrome.exe (PID: 3028)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
58
Monitored processes
22
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 320 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,16484386428614322025,9846581310776697884,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2992 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 444 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1024,16484386428614322025,9846581310776697884,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2852 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1080 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1024,16484386428614322025,9846581310776697884,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3572 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1468 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,16484386428614322025,9846581310776697884,131072 --enable-features=PasswordImport --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1212 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1908 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,16484386428614322025,9846581310776697884,131072 --enable-features=PasswordImport --lang=en-US --instant-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1824 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2016 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1024,16484386428614322025,9846581310776697884,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2860 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2188 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=1024,16484386428614322025,9846581310776697884,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --mojo-platform-channel-handle=1308 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2224 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1024,16484386428614322025,9846581310776697884,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1740 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2232 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,16484386428614322025,9846581310776697884,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=15 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3420 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2312 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1024,16484386428614322025,9846581310776697884,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --mojo-platform-channel-handle=1044 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
25 536
Read events
25 297
Write events
237
Delete events
2
Modification events
| (PID) Process: | (2760) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2760) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 50083776 | |||
| (PID) Process: | (2760) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30937494 | |||
| (PID) Process: | (2760) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 350243854 | |||
| (PID) Process: | (2760) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30937494 | |||
| (PID) Process: | (2760) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2760) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2760) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2760) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2760) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
162
Text files
137
Unknown types
23
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3676 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\onedrive[1].htm | html | |
MD5:— | SHA256:— | |||
| 3676 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_1941775A515122A167E3FBACF08992E1 | binary | |
MD5:— | SHA256:— | |||
| 3676 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_1941775A515122A167E3FBACF08992E1 | der | |
MD5:— | SHA256:— | |||
| 2760 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | der | |
MD5:— | SHA256:— | |||
| 2760 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:— | SHA256:— | |||
| 3676 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\plt.resx-plt[1].js | text | |
MD5:— | SHA256:— | |||
| 3676 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\plt.office-ui-fabric-react[1].js | text | |
MD5:— | SHA256:— | |||
| 3676 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2760 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 3676 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\odsp.react.lib-fd9eabf8[1].js | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
79
DNS requests
50
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3676 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEA8XGkjG8iOAkhjNLtbdwOg%3D | US | der | 471 b | whitelisted |
3676 | iexplore.exe | GET | 200 | 104.18.25.243:80 | http://ocsp.msocsp.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRSHuNsR4EZqcsD%2BrdOV%2BEZevGBiwQUtXYMMBHOx5JCTUzHXCzIqQzoC2QCExIAEvdwD%2F35xJ9F9wMAAAAS93A%3D | US | der | 1.70 Kb | whitelisted |
3676 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | der | 1.47 Kb | whitelisted |
3676 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAxq6XzO1ZmDhpCgCp6lMhQ%3D | US | der | 471 b | whitelisted |
2760 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
3676 | iexplore.exe | GET | 200 | 104.18.25.243:80 | http://ocsp.msocsp.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRSHuNsR4EZqcsD%2BrdOV%2BEZevGBiwQUtXYMMBHOx5JCTUzHXCzIqQzoC2QCExIAID0mTAYs5VcQIg4AAAAgPSY%3D | US | der | 1.70 Kb | whitelisted |
3676 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEALnkXH7gCHpP%2BLZg4NMUMA%3D | US | der | 471 b | whitelisted |
3676 | iexplore.exe | GET | 200 | 104.18.25.243:80 | http://ocsp.msocsp.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSjA8CoiHvUecQnjrXXWH08EsBNpAQU%2Fy9%2F4Qb0OPMt7SWNmML%2BDvZs%2FPoCE38AIDfLvRE4agVL6JIAAAAgN8s%3D | US | der | 1.70 Kb | whitelisted |
3676 | iexplore.exe | GET | 200 | 104.18.25.243:80 | http://ocsp.msocsp.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRSHuNsR4EZqcsD%2BrdOV%2BEZevGBiwQUtXYMMBHOx5JCTUzHXCzIqQzoC2QCExIAEvdwD%2F35xJ9F9wMAAAAS93A%3D | US | der | 1.70 Kb | whitelisted |
3676 | iexplore.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBQN1VoiX40jVOMldh7uDThi9DqeewQU1cFnOsKjnfR3UltZEjgp5lVou6UCEzMAJn4pySedhRiAtPIAAAAmfik%3D | US | der | 1.72 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3676 | iexplore.exe | 95.100.128.157:443 | static2.sharepointonline.com | Akamai Technologies, Inc. | — | unknown |
3676 | iexplore.exe | 13.69.109.130:443 | browser.pipe.aria.microsoft.com | Microsoft Corporation | NL | suspicious |
3676 | iexplore.exe | 52.111.229.20:443 | eastus0.pushnp.svc.ms | Microsoft Corporation | US | suspicious |
2760 | iexplore.exe | 13.107.136.9:443 | alpine4corp-my.sharepoint.com | Microsoft Corporation | US | whitelisted |
2188 | chrome.exe | 142.250.179.132:443 | www.google.com | Google Inc. | US | whitelisted |
2188 | chrome.exe | 142.250.186.77:443 | accounts.google.com | Google Inc. | US | suspicious |
3676 | iexplore.exe | 13.107.136.9:443 | alpine4corp-my.sharepoint.com | Microsoft Corporation | US | whitelisted |
3676 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
3676 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2760 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
alpine4corp-my.sharepoint.com |
| suspicious |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
shell.cdn.office.net |
| whitelisted |
modernb.akamai.odsp.cdn.office.net |
| whitelisted |
ocsp.msocsp.com |
| whitelisted |
static2.sharepointonline.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |