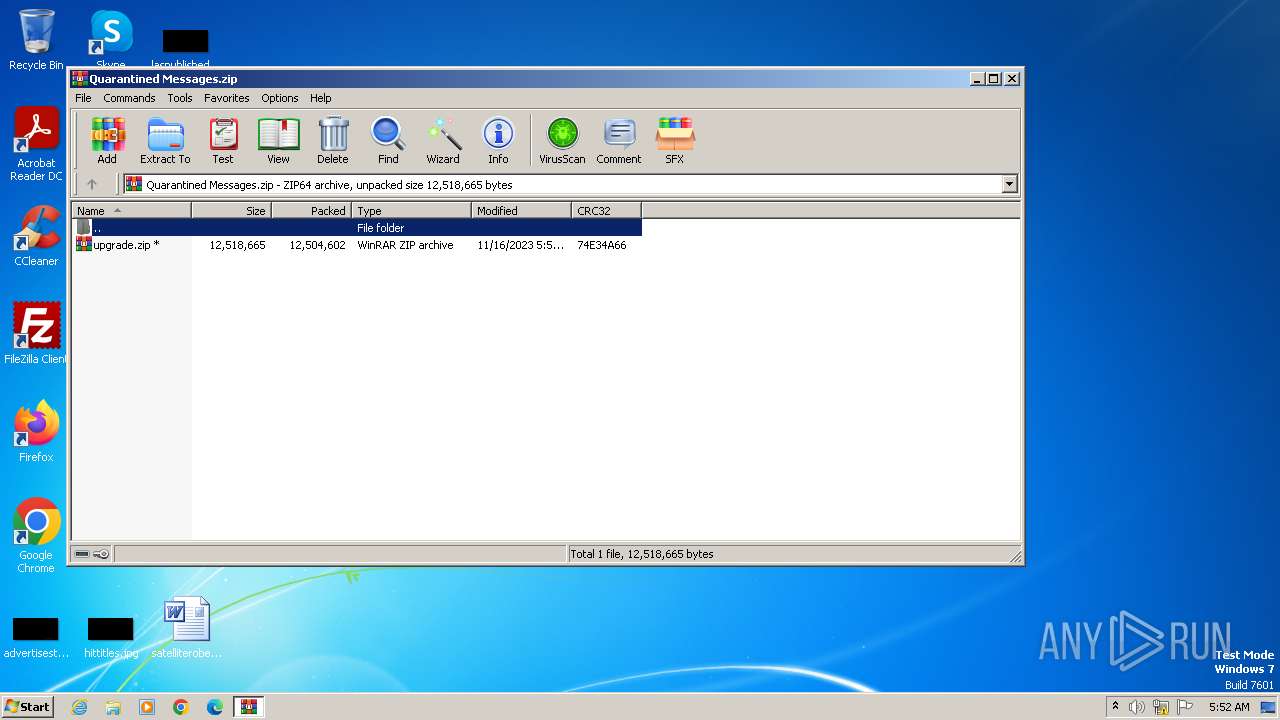
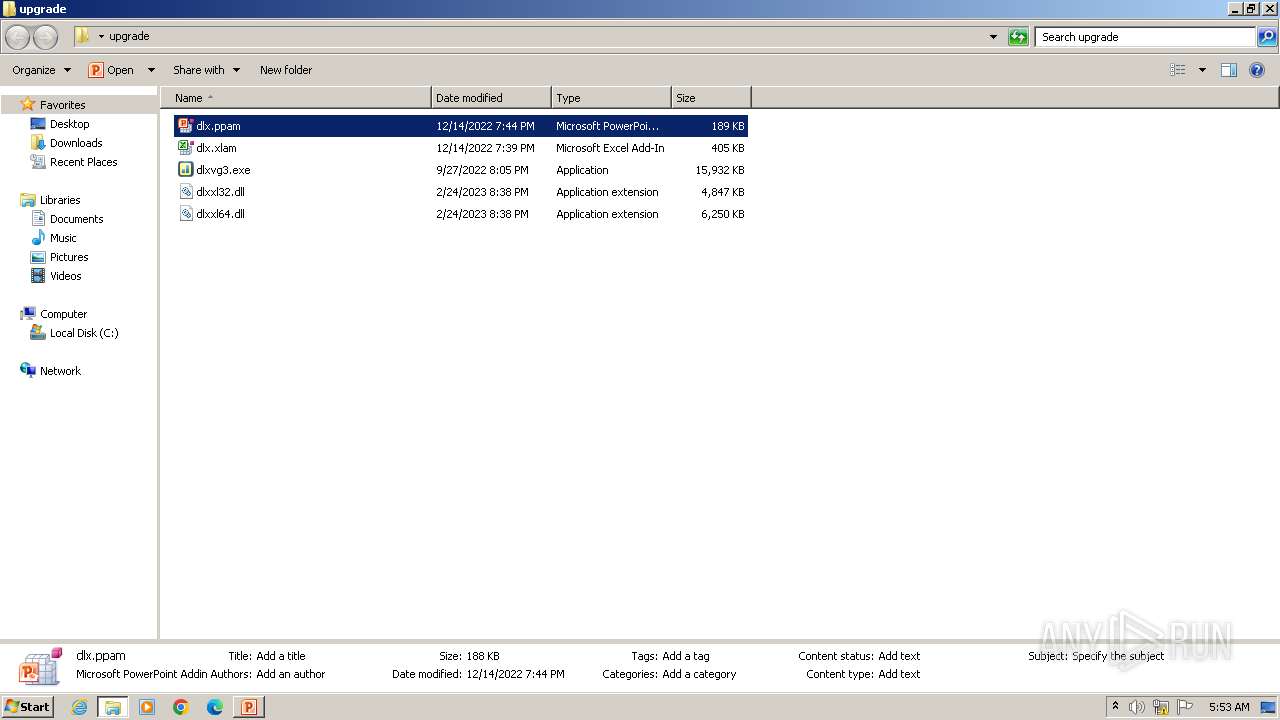
| File name: | Quarantined Messages.zip |
| Full analysis: | https://app.any.run/tasks/48ece2bc-11b6-4c5a-80c9-0a27a6f57d0f |
| Verdict: | Malicious activity |
| Analysis date: | November 16, 2023, 05:52:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| MIME: | application/zip |
| File info: | Zip archive data, at least v4.5 to extract |
| MD5: | B81C80342DCB34B439D74651D6F51E36 |
| SHA1: | 6756216CC96B21FAAA92C564A65D691D59F02E7C |
| SHA256: | 842D52F1920CD6E06DBDA150D4041DE13606A3A0E3F38DC5336CCA2002B061F5 |
| SSDEEP: | 98304:O9jHv1q4HAkkLENorNPGti6HprNIdXLTdmgqu9ipwd4f0Rugmw6NKIzEW6s3/Y4Z:UBxFTPFYBtOskoeePJoa/j+f |
MALICIOUS
No malicious indicators.SUSPICIOUS
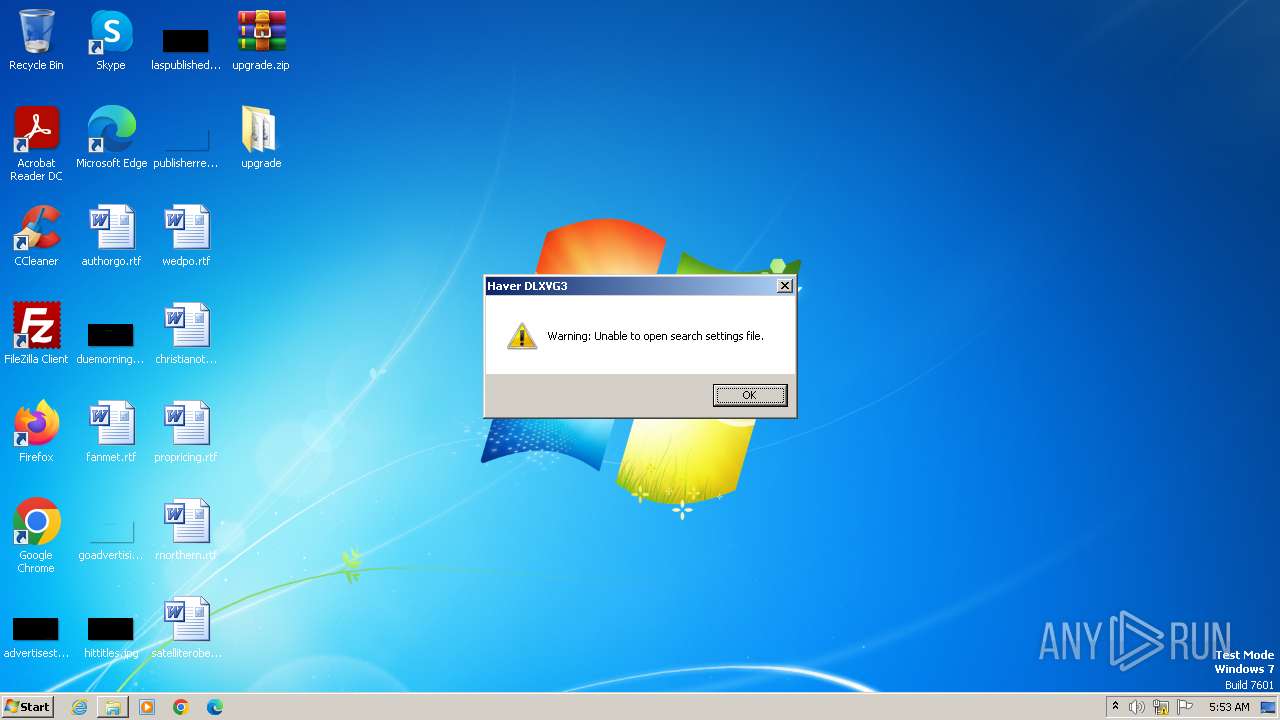
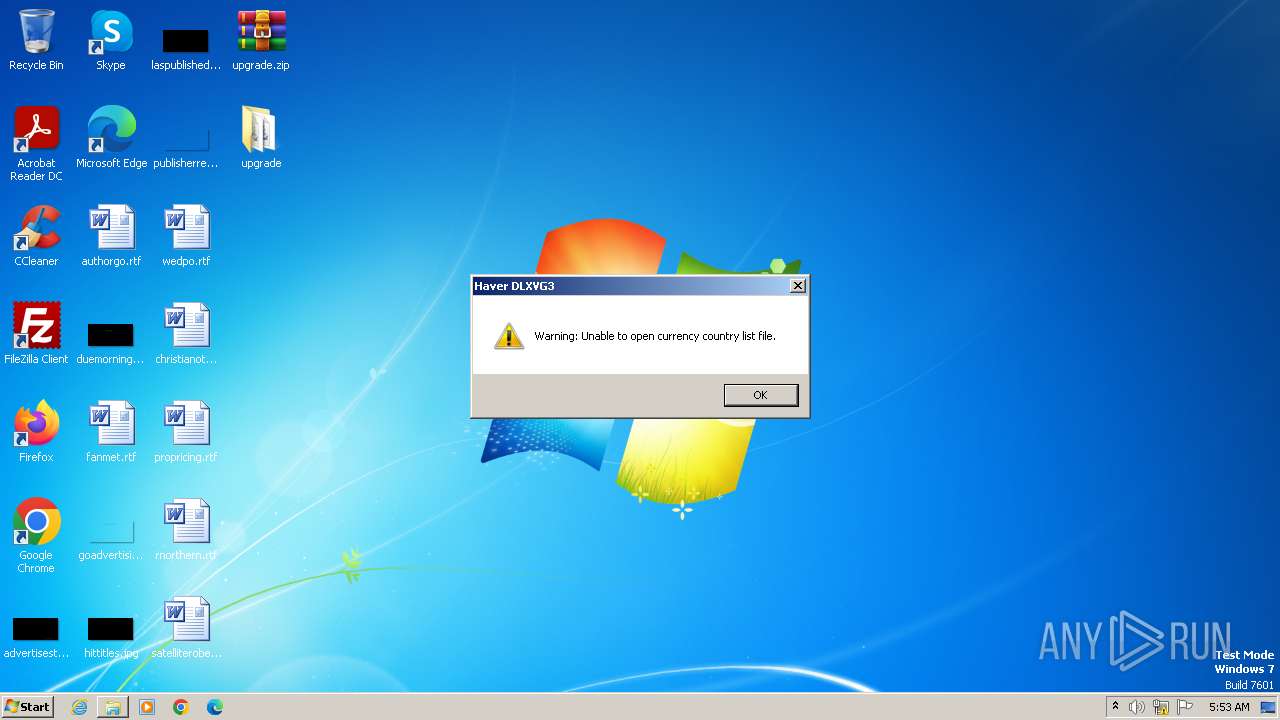
Reads Internet Explorer settings
- dlxvg3.exe (PID: 3668)
Reads the Internet Settings
- dlxvg3.exe (PID: 3668)
Creates FileSystem object to access computer's file system (SCRIPT)
- EXCEL.EXE (PID: 3028)
Reads Microsoft Outlook installation path
- dlxvg3.exe (PID: 3668)
INFO
Reads the computer name
- dlxvg3.exe (PID: 3668)
Reads the machine GUID from the registry
- dlxvg3.exe (PID: 3668)
Create files in a temporary directory
- dlxvg3.exe (PID: 3668)
Checks proxy server information
- dlxvg3.exe (PID: 3668)
Manual execution by a user
- EXCEL.EXE (PID: 3028)
- rundll32.exe (PID: 756)
- WinRAR.exe (PID: 3504)
- dlxvg3.exe (PID: 3668)
- POWERPNT.EXE (PID: 4004)
Checks supported languages
- dlxvg3.exe (PID: 3668)
Reads mouse settings
- EXCEL.EXE (PID: 3028)
- POWERPNT.EXE (PID: 4004)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3504)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 45 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:11:16 05:51:44 |
| ZipCRC: | 0x74e34a66 |
| ZipCompressedSize: | 4294967295 |
| ZipUncompressedSize: | 4294967295 |
| ZipFileName: | upgrade.zip |
Total processes
47
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 756 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\upgrade\dlxxl32.dll | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3028 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\microsoft office\Office14\EXCEL.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3460 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Quarantined Messages.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3504 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\upgrade.zip" C:\Users\admin\Desktop\upgrade\ | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
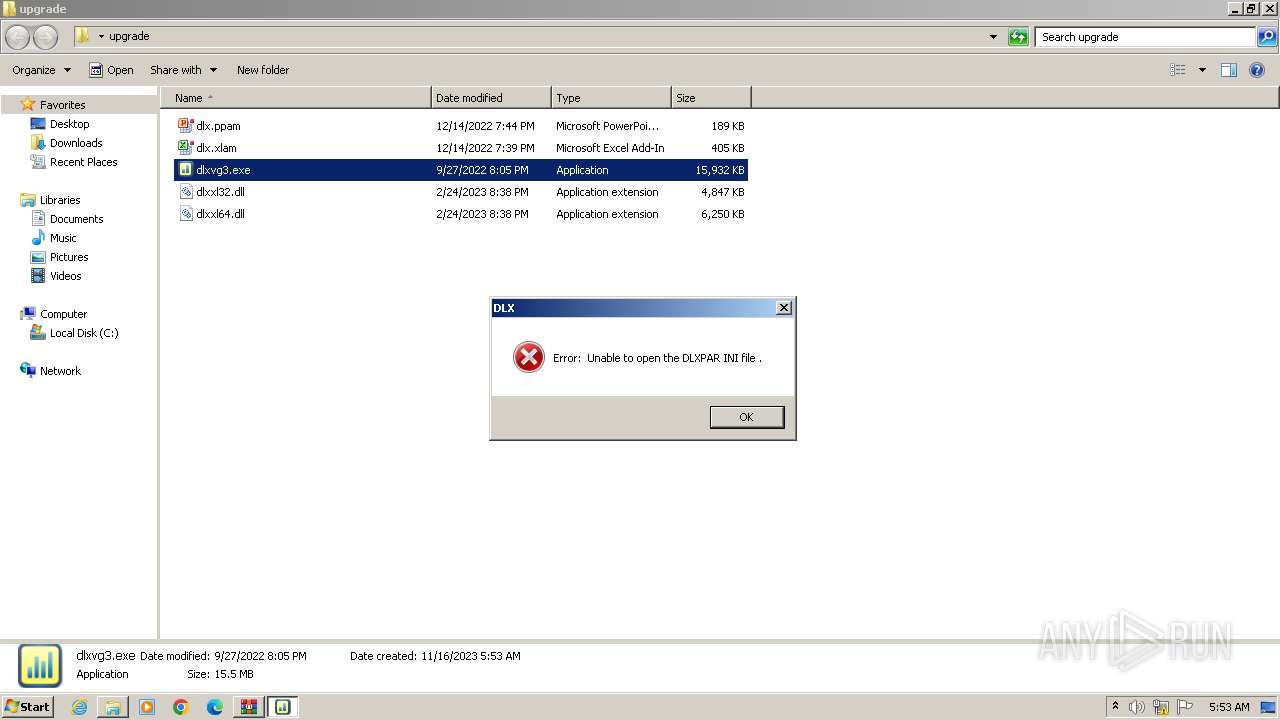
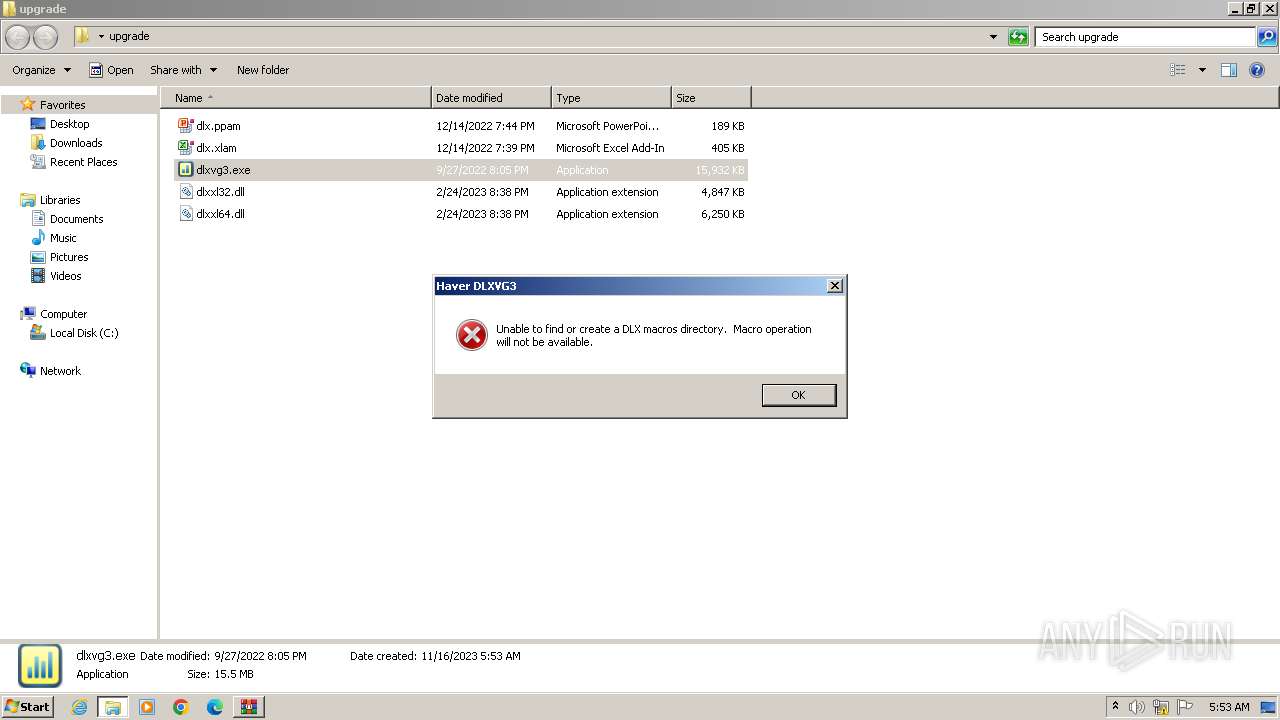
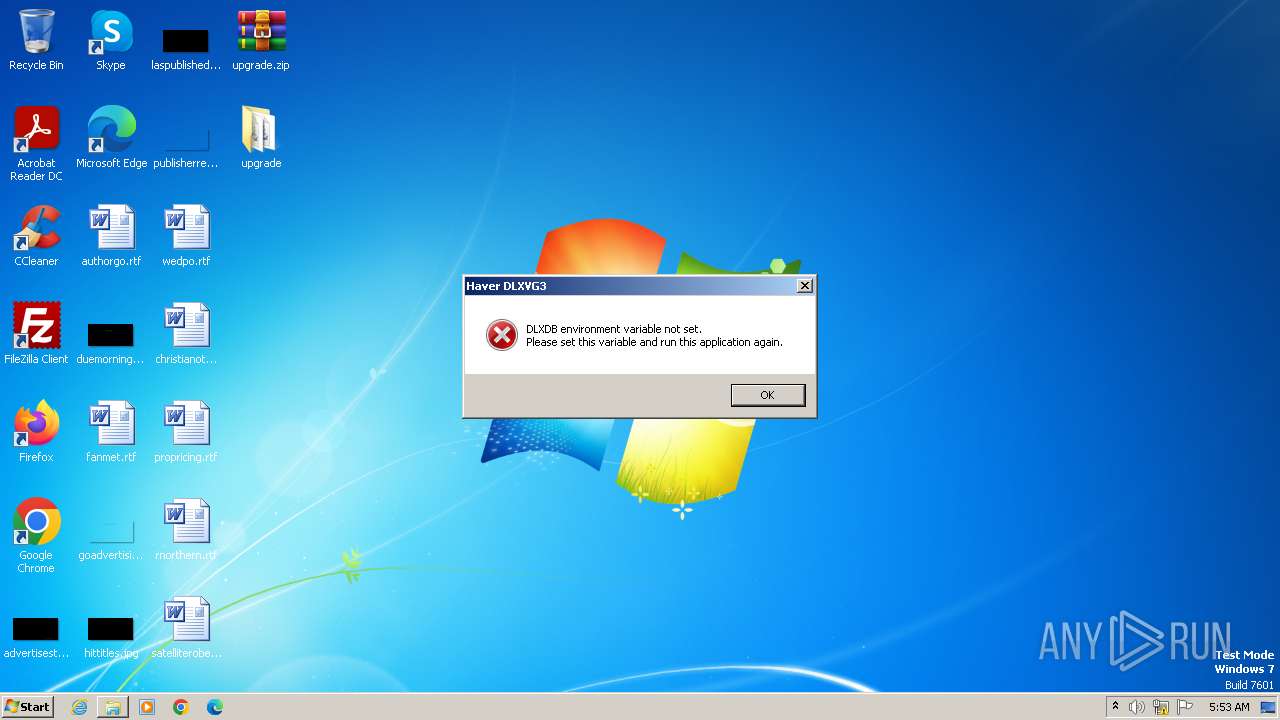
| 3668 | "C:\Users\admin\Desktop\upgrade\dlxvg3.exe" | C:\Users\admin\Desktop\upgrade\dlxvg3.exe | — | explorer.exe | |||||||||||
User: admin Company: Haver Analytics Inc. Integrity Level: MEDIUM Description: Haver DLXVG3 Exit code: 0 Version: 5.3.2.9 Modules
| |||||||||||||||
| 4004 | "C:\Program Files\Microsoft Office\Office14\POWERPNT.EXE" "C:\Users\admin\Desktop\upgrade\dlx.ppam" | C:\Program Files\Microsoft Office\Office14\POWERPNT.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft PowerPoint Exit code: 0 Version: 14.0.6009.1000 Modules
| |||||||||||||||
Total events
3 908
Read events
3 787
Write events
101
Delete events
20
Modification events
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3460) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3504) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3504) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
4
Suspicious files
7
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4004 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Temp\CVR6FE0.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3028 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVRA057.tmp.cvr | — | |
MD5:— | SHA256:— | |||
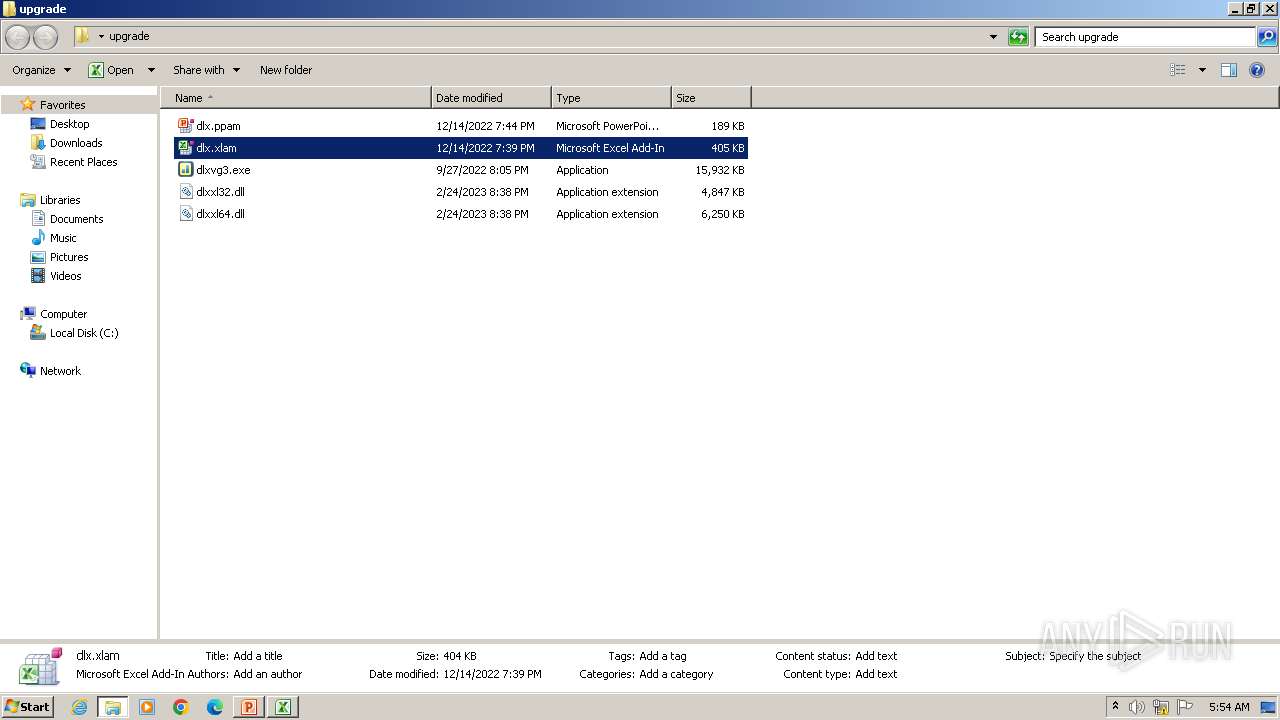
| 3504 | WinRAR.exe | C:\Users\admin\Desktop\upgrade\dlx.xlam | document | |
MD5:E3AAF055CD1CD5D69BB010B9ED26D8B8 | SHA256:E0F9D72B6EBAD23CE3591E06852BEFD34483FE56FD0EF90C68769DA902A59CA1 | |||
| 3504 | WinRAR.exe | C:\Users\admin\Desktop\upgrade\dlxxl32.dll | executable | |
MD5:0EED838488E17CAE2B5948E0F5DA2DBB | SHA256:A7C26F119B909EFE9734415B44052CD43810237F35051D8956D6DF9CBE3232E4 | |||
| 3668 | dlxvg3.exe | C:\Users\admin\AppData\Local\Temp\@temp.htm | text | |
MD5:E9767BE8092050427FFC3A2F1D4B3B7B | SHA256:9C28A83690B8FC6015BB21B820735507402D8869A7BAE78C3133BCAAD8622433 | |||
| 4004 | POWERPNT.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\dlx.ppam.LNK | binary | |
MD5:21492A6A9DBBF8F8C08EAE103B8AFA86 | SHA256:A15312C591A6B1F19F2999E3737F433007C0FAEAAE4054277BEF902D3218235C | |||
| 3668 | dlxvg3.exe | C:\Users\admin\AppData\Local\Temp\DLXVG3_new.LOG | text | |
MD5:40F55D868515ED3857148A1E0DE82AB1 | SHA256:F3390C7A18757C51355C294730B702C61CD7FFE7DE47861F18A732E726414235 | |||
| 3504 | WinRAR.exe | C:\Users\admin\Desktop\upgrade\dlxxl64.dll | executable | |
MD5:089BC585DFCC776D48D3330D5410C871 | SHA256:10AC743728CA6511D20AB091F8122B22B0A5EB244C3ABE3B967985A39CB93668 | |||
| 4004 | POWERPNT.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:4C9D83F0CF3CABA76DE1FD723AA45E03 | SHA256:AAB81438E28474827B94E7227415693D69B3EF1B652706DF54BD6DC26FCF0979 | |||
| 3028 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\dlx.xlam.LNK | binary | |
MD5:EA05BF5BA89BD21175B57B612A89735D | SHA256:B7232A4F06B1B783BD36A8B56ED0428BFA4E3C8CD5AD2EAD6900922F02372767 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |