| File name: | starter.exe |
| Full analysis: | https://app.any.run/tasks/d0fa9dee-7298-40da-bd4b-1ac00e60395e |
| Verdict: | Malicious activity |
| Analysis date: | December 05, 2022, 20:06:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | D5416A1089DBADC6054227BB58EBD291 |
| SHA1: | DAE118B43D0256F33E5D35C1D06B6D33F88F6010 |
| SHA256: | 841572DA329176A7F23DA214406A8C5D19C4107206DF3D83BFCD8DD6DC906ECF |
| SSDEEP: | 393216:RJU5oNri0Bjaj1cCDu4LAG6vtlCM7NF0JQ+ZEZlB93:5Ou4Zu4LT6rBB6JQ4EJ9 |
MALICIOUS
Application was dropped or rewritten from another process
- Phfocdkc4ugs5.exe (PID: 952)
SUSPICIOUS
Reads the Internet Settings
- starter.exe (PID: 1708)
- Phfocdkc4ugs5.exe (PID: 952)
Reads settings of System Certificates
- starter.exe (PID: 1708)
- Phfocdkc4ugs5.exe (PID: 952)
Starts CMD.EXE for commands execution
- starter.exe (PID: 1708)
Starts CHOICE.EXE to create a delay
- cmd.exe (PID: 2116)
Reads the BIOS version
- Phfocdkc4ugs5.exe (PID: 952)
INFO
Checks supported languages
- starter.exe (PID: 1708)
- Phfocdkc4ugs5.exe (PID: 952)
Reads the computer name
- starter.exe (PID: 1708)
- Phfocdkc4ugs5.exe (PID: 952)
Reads Environment values
- starter.exe (PID: 1708)
- Phfocdkc4ugs5.exe (PID: 952)
Creates a file in a temporary directory
- starter.exe (PID: 1708)
Process checks are UAC notifies on
- Phfocdkc4ugs5.exe (PID: 952)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 2021-Sep-29 23:06:57 |
| Comments: | - |
| CompanyName: | - |
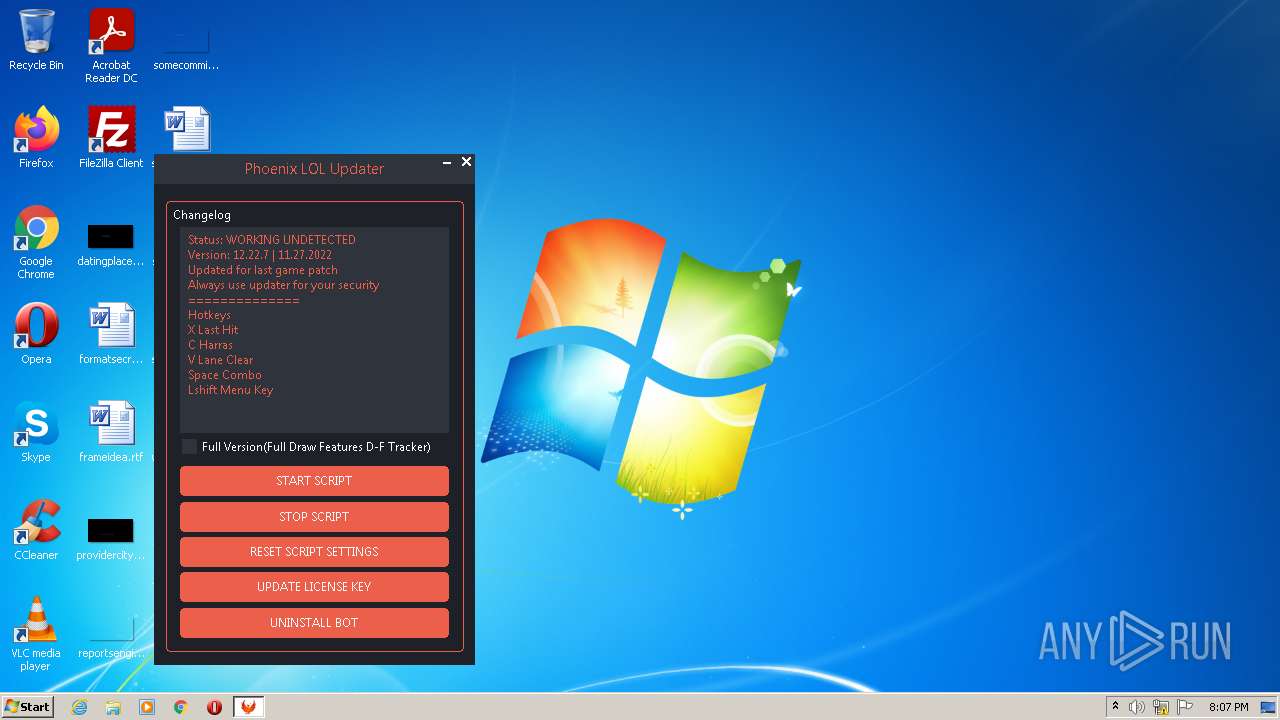
| FileDescription: | Updater |
| FileVersion: | 1.9.0.0 |
| InternalName: | starter.exe |
| LegalCopyright: | Copyright © 2019 |
| LegalTrademarks: | - |
| OriginalFilename: | starter.exe |
| ProductName: | Updater |
| ProductVersion: | 1.9.0.0 |
| Assembly Version: | 1.9.0.0 |
DOS Header
| e_magic: | MZ |
|---|---|
| e_cblp: | 144 |
| e_cp: | 3 |
| e_crlc: | - |
| e_cparhdr: | 4 |
| e_minalloc: | - |
| e_maxalloc: | 65535 |
| e_ss: | - |
| e_sp: | 184 |
| e_csum: | - |
| e_ip: | - |
| e_cs: | - |
| e_ovno: | - |
| e_oemid: | - |
| e_oeminfo: | - |
| e_lfanew: | 128 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| NumberofSections: | 3 |
| TimeDateStamp: | 2021-Sep-29 23:06:57 |
| PointerToSymbolTable: | - |
| NumberOfSymbols: | - |
| SizeOfOptionalHeader: | 224 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 8192 | 19535160 | 19535360 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 7.95973 |
.reloc | 19546112 | 12 | 512 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 0.122276 |
.rsrc | 19554304 | 263388 | 263680 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 3.70959 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 3.62546 | 259112 | UNKNOWN | UNKNOWN | RT_ICON |
32512 | 2.01924 | 20 | UNKNOWN | UNKNOWN | RT_GROUP_ICON |
1 (#2) | 3.27244 | 780 | UNKNOWN | UNKNOWN | RT_VERSION |
1 (#3) | 5.00692 | 3169 | UNKNOWN | UNKNOWN | RT_MANIFEST |
Imports
mscoree.dll |
Total processes
42
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 952 | "C:\Users\admin\AppData\Local\Temp\Phfocdkc4ugs5.exe" | C:\Users\admin\AppData\Local\Temp\Phfocdkc4ugs5.exe | starter.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Updater Exit code: 0 Version: 3.8.0.9 Modules
| |||||||||||||||
| 1116 | choice /C Y /N /D Y /T 5 | C:\Windows\system32\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Offers the user a choice Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1240 | "C:\Users\admin\AppData\Local\Temp\starter.exe" | C:\Users\admin\AppData\Local\Temp\starter.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: Updater Exit code: 3221226540 Version: 1.9.0.0 Modules
| |||||||||||||||
| 1708 | "C:\Users\admin\AppData\Local\Temp\starter.exe" | C:\Users\admin\AppData\Local\Temp\starter.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Description: Updater Exit code: 0 Version: 1.9.0.0 Modules
| |||||||||||||||
| 2116 | "C:\Windows\System32\cmd.exe" /C choice /C Y /N /D Y /T 5 & Del "C:\Users\admin\AppData\Local\Temp\starter.exe" | C:\Windows\System32\cmd.exe | — | starter.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
6 942
Read events
6 882
Write events
60
Delete events
0
Modification events
| (PID) Process: | (1708) starter.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\starter_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1708) starter.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\starter_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (1708) starter.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\starter_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (1708) starter.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\starter_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (1708) starter.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\starter_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (1708) starter.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\starter_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (1708) starter.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\starter_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1708) starter.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\starter_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (1708) starter.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\starter_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (1708) starter.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\starter_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
Executable files
1
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1708 | starter.exe | C:\Users\admin\AppData\Local\Temp\Phfocdkc4ugs5.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
3
Threats
2
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1708 | starter.exe | 185.199.110.133:443 | raw.githubusercontent.com | FASTLY | US | malicious |
1708 | starter.exe | 104.26.12.201:443 | t.ly | CLOUDFLARENET | US | suspicious |
1708 | starter.exe | 162.159.134.233:443 | cdn.discordapp.com | CLOUDFLARENET | — | shared |
952 | Phfocdkc4ugs5.exe | 185.199.110.133:443 | raw.githubusercontent.com | FASTLY | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
raw.githubusercontent.com |
| shared |
t.ly |
| whitelisted |
cdn.discordapp.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
1708 | starter.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |