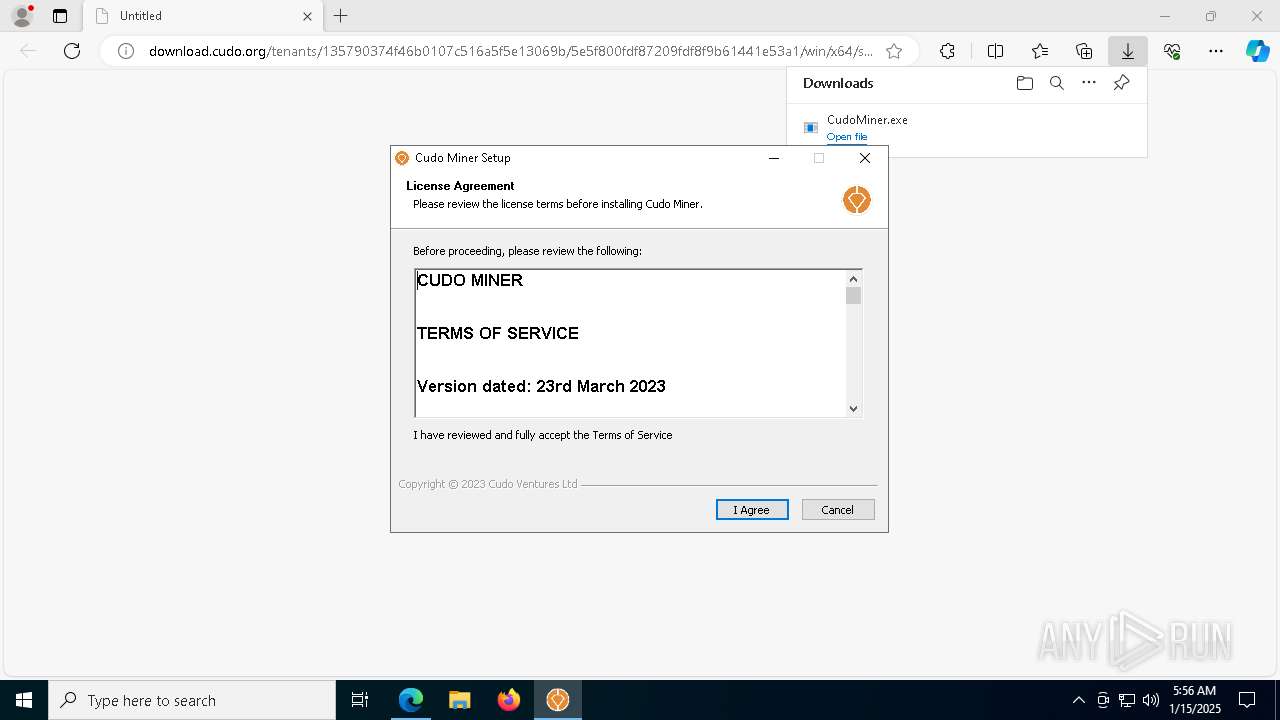
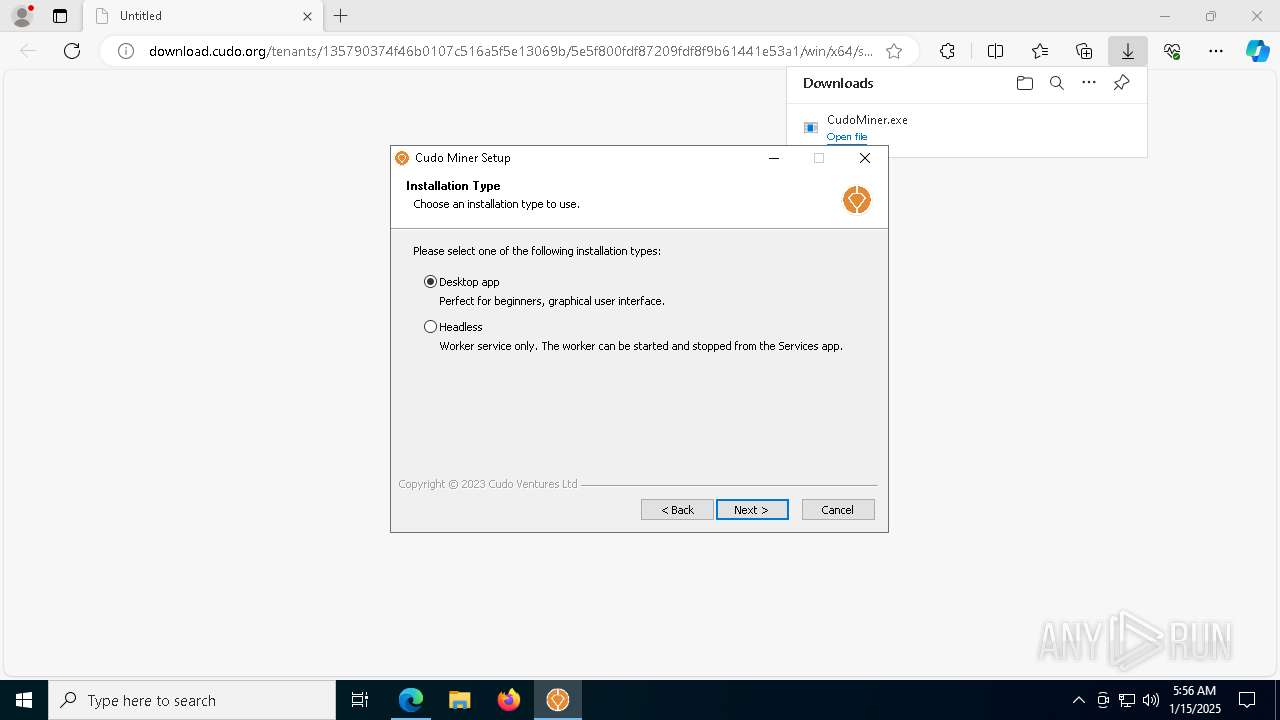
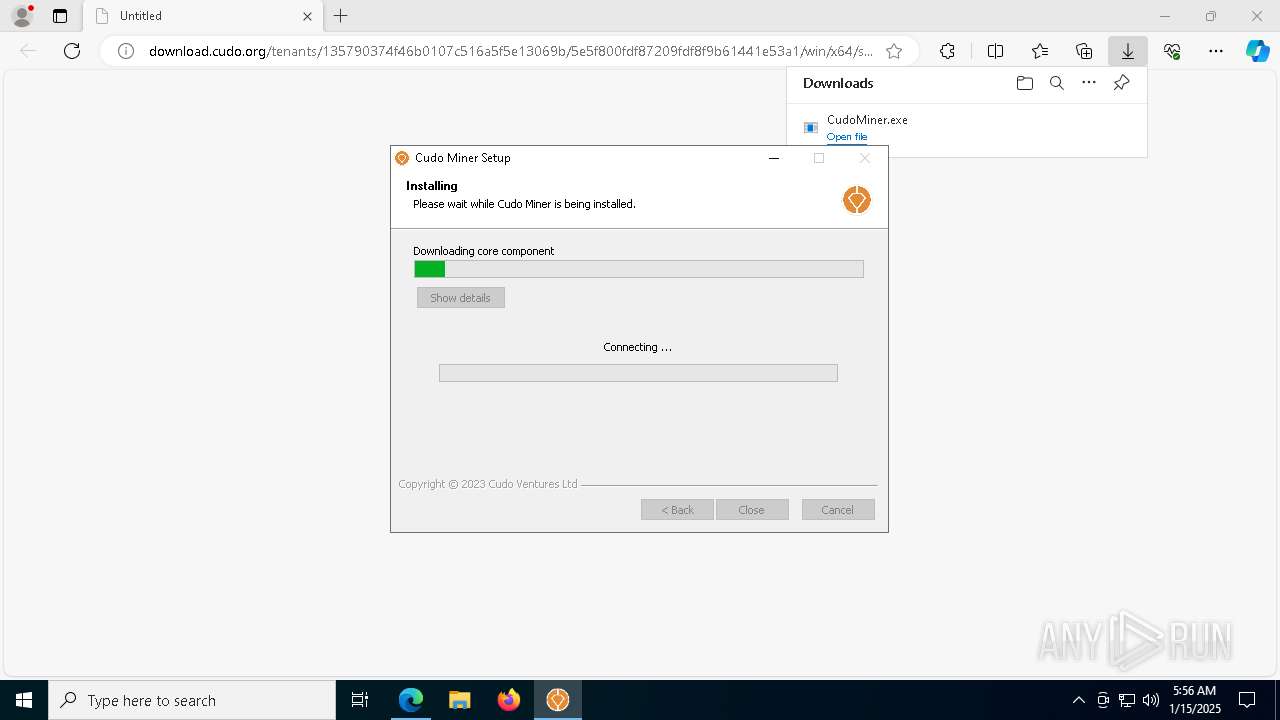
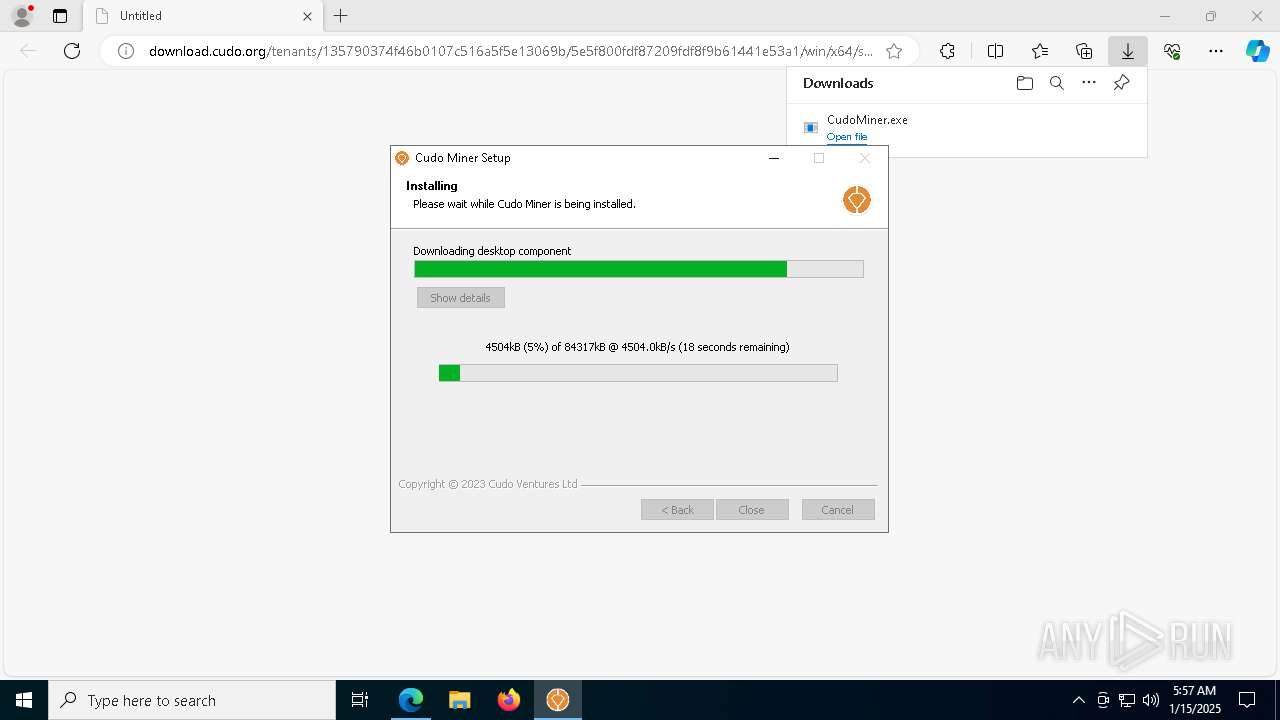
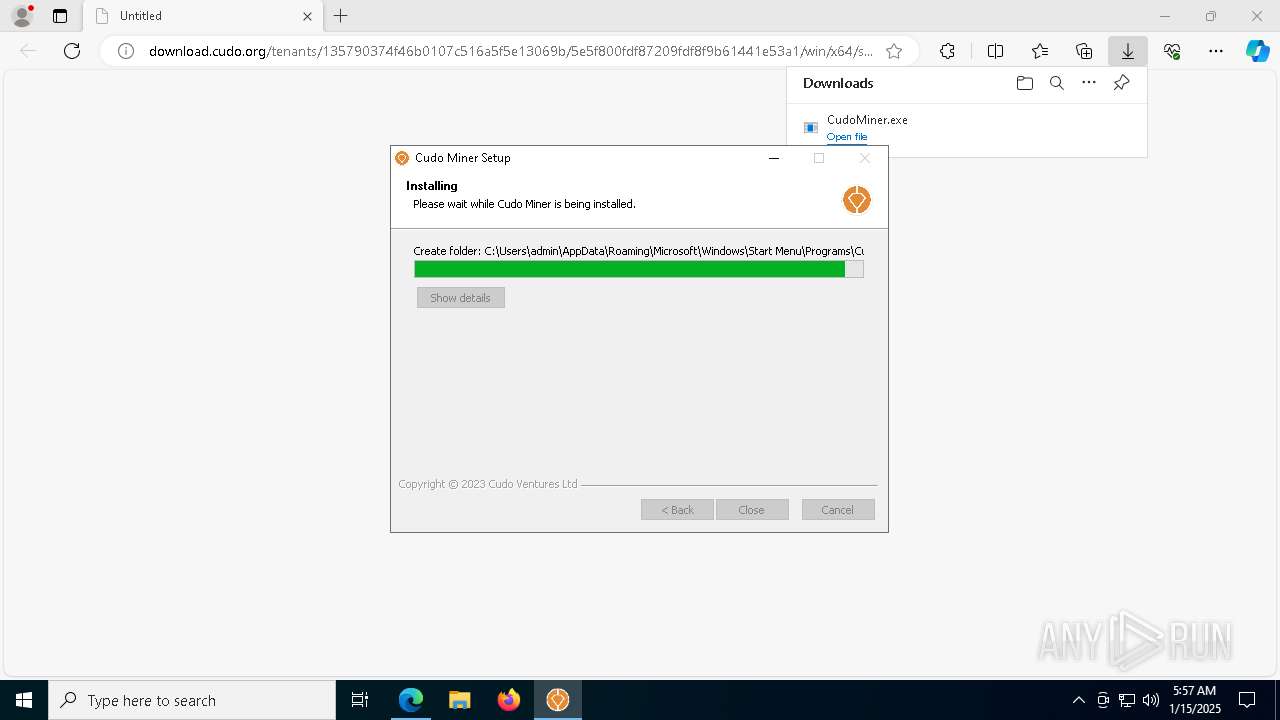
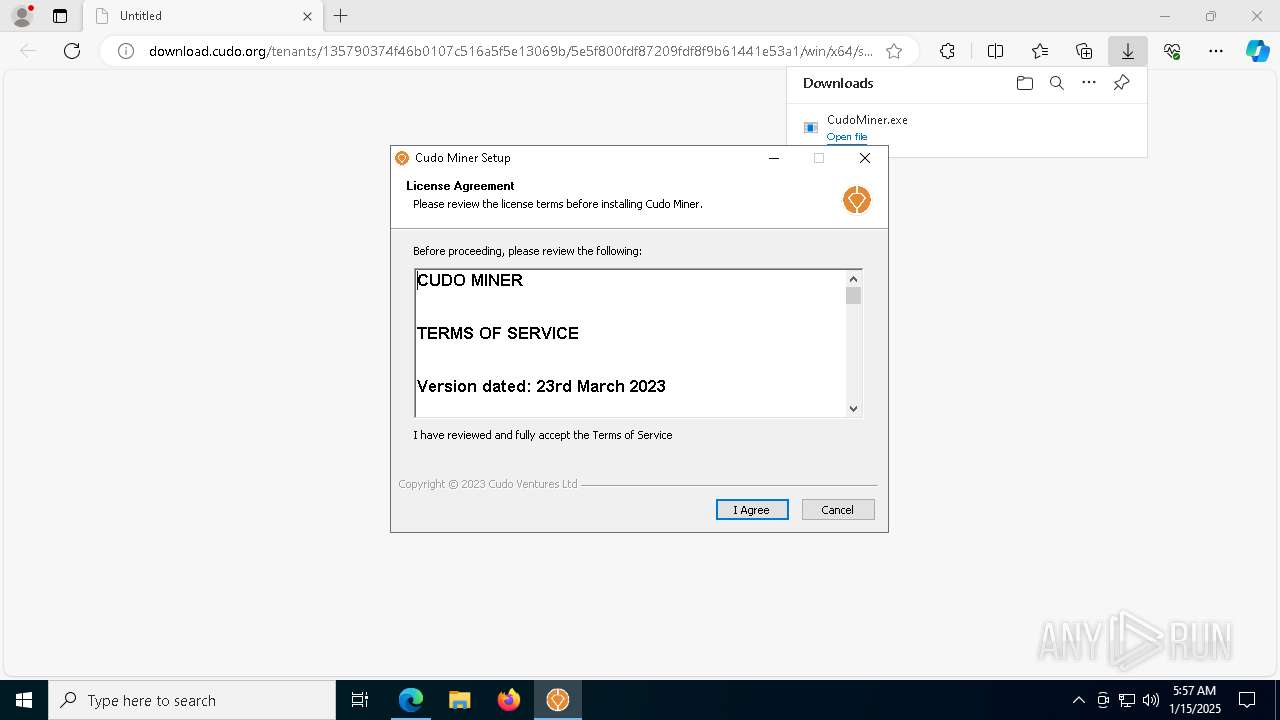
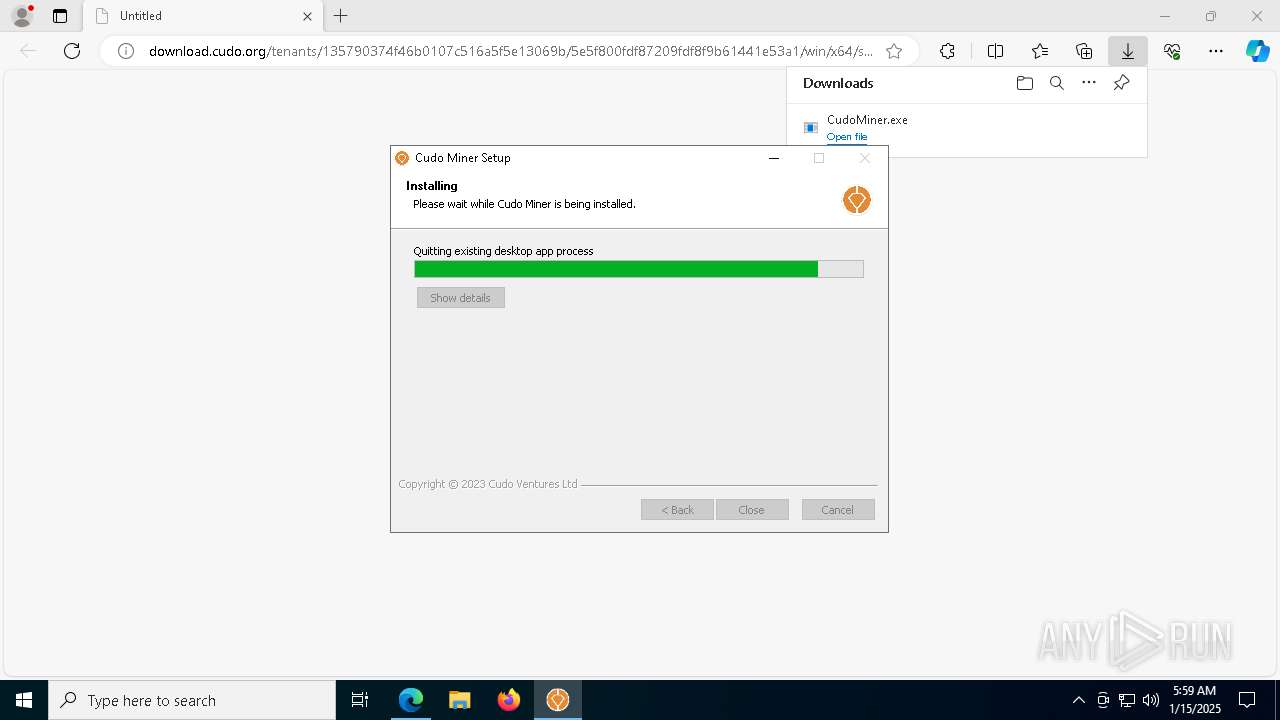
| URL: | download.cudo.org/tenants/135790374f46b0107c516a5f5e13069b/5e5f800fdf87209fdf8f9b61441e53a1/win/x64/stable/CudoMiner.exe |
| Full analysis: | https://app.any.run/tasks/64d1180b-ef15-44df-8820-2d623c63da34 |
| Verdict: | Malicious activity |
| Analysis date: | January 15, 2025, 05:56:20 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | CB4E7B54BE5D7418526A345AF0AFA8CF |
| SHA1: | 52A93957E8A3A8A412CFDB3A4A914618D1182C8D |
| SHA256: | 8411B2E4CE404FE84B47266B2CF3ED434B4F982AA85C64170C0B7737524C14B3 |
| SSDEEP: | 3:ZKWcf9f7RTKBHhcUQDXpBDbdDBIUJMKiuKn8oMzA:Zl09f0ZKD3DBIWly8RzA |
MALICIOUS
Adds exclusions to the Windows Defender exclusion list using PowerShell
- CudoMiner.exe (PID: 5460)
- CudoMiner.exe (PID: 3508)
Changes powershell execution policy (Unrestricted)
- Cudo Miner Core.exe (PID: 8156)
- Cudo Miner Core.exe (PID: 7220)
- Cudo Miner Core.exe (PID: 2212)
- Cudo Miner Core.exe (PID: 4468)
- Cudo Miner Core.exe (PID: 3032)
- Cudo Miner Core.exe (PID: 7888)
- Cudo Miner Core.exe (PID: 648)
- Cudo Miner Core.exe (PID: 8116)
- Cudo Miner Core.exe (PID: 7900)
Bypass execution policy to execute commands
- powershell.exe (PID: 3736)
SUSPICIOUS
Checks Windows Trust Settings
- CudoMiner.exe (PID: 5460)
- cudo-defender-exclusion.exe (PID: 7904)
- cudo-defender-exclusion.exe (PID: 5200)
- CudoMiner.exe (PID: 3508)
- cudo-defender-exclusion.exe (PID: 6492)
- cudo-defender-exclusion.exe (PID: 7260)
Reads security settings of Internet Explorer
- CudoMiner.exe (PID: 5460)
- cudo-defender-exclusion.exe (PID: 7904)
- cudo-defender-exclusion.exe (PID: 5200)
- cudo-defender-exclusion.exe (PID: 6492)
- cudo-defender-exclusion.exe (PID: 7260)
- CudoMiner.exe (PID: 3508)
Node.exe was dropped
- CudoMiner.exe (PID: 5460)
- CudoMiner.exe (PID: 3508)
Drops a system driver (possible attempt to evade defenses)
- CudoMiner.exe (PID: 5460)
Creates a software uninstall entry
- CudoMiner.exe (PID: 5460)
Adds/modifies Windows certificates
- cudo-defender-exclusion.exe (PID: 7904)
Executable content was dropped or overwritten
- CudoMiner.exe (PID: 5460)
- CudoMiner.exe (PID: 3508)
Creates or modifies Windows services
- Updater.exe (PID: 2996)
Executes as Windows Service
- Cudo Miner.exe (PID: 5008)
- Cudo Miner.exe (PID: 4336)
- Cudo Miner.exe (PID: 4576)
- Cudo Miner.exe (PID: 8020)
- Cudo Miner.exe (PID: 6960)
- Cudo Miner.exe (PID: 4520)
- Cudo Miner.exe (PID: 1576)
- Cudo Miner.exe (PID: 2092)
- Cudo Miner.exe (PID: 8052)
Process drops legitimate windows executable
- CudoMiner.exe (PID: 5460)
Starts application with an unusual extension
- cmd.exe (PID: 7236)
- cmd.exe (PID: 424)
- cmd.exe (PID: 2976)
- cmd.exe (PID: 7132)
- cmd.exe (PID: 5308)
- cmd.exe (PID: 2548)
- cmd.exe (PID: 8060)
- cmd.exe (PID: 5876)
- cmd.exe (PID: 7320)
- cmd.exe (PID: 7984)
- cmd.exe (PID: 6860)
- cmd.exe (PID: 7332)
- cmd.exe (PID: 7444)
- cmd.exe (PID: 1380)
- cmd.exe (PID: 4872)
- cmd.exe (PID: 5936)
- cmd.exe (PID: 3808)
- cmd.exe (PID: 5964)
- cmd.exe (PID: 5200)
- cmd.exe (PID: 3896)
Uses ROUTE.EXE to obtain the routing table information
- cmd.exe (PID: 7608)
- cmd.exe (PID: 5912)
- cmd.exe (PID: 7656)
- cmd.exe (PID: 2008)
- cmd.exe (PID: 4360)
- cmd.exe (PID: 4612)
- cmd.exe (PID: 7772)
- cmd.exe (PID: 396)
- cmd.exe (PID: 1588)
- cmd.exe (PID: 7132)
- cmd.exe (PID: 7660)
- cmd.exe (PID: 3524)
- cmd.exe (PID: 4036)
- cmd.exe (PID: 7644)
- cmd.exe (PID: 7752)
- cmd.exe (PID: 6220)
- cmd.exe (PID: 3736)
- cmd.exe (PID: 2428)
Starts CMD.EXE for commands execution
- Cudo Miner Core.exe (PID: 8156)
- NETSTAT.EXE (PID: 7568)
- NETSTAT.EXE (PID: 1512)
- Cudo Miner Core.exe (PID: 7220)
- NETSTAT.EXE (PID: 7348)
- NETSTAT.EXE (PID: 4872)
- Cudo Miner Core.exe (PID: 2212)
- NETSTAT.EXE (PID: 7712)
- NETSTAT.EXE (PID: 7432)
- Cudo Miner Core.exe (PID: 4468)
- NETSTAT.EXE (PID: 3988)
- NETSTAT.EXE (PID: 2548)
- Cudo Miner Core.exe (PID: 3864)
- Cudo Miner Core.exe (PID: 648)
- NETSTAT.EXE (PID: 128)
- Cudo Miner Core.exe (PID: 7900)
- NETSTAT.EXE (PID: 7756)
- NETSTAT.EXE (PID: 236)
- NETSTAT.EXE (PID: 4908)
- Cudo Miner Core.exe (PID: 3032)
- NETSTAT.EXE (PID: 6488)
- NETSTAT.EXE (PID: 1080)
- Cudo Miner Core.exe (PID: 7888)
- NETSTAT.EXE (PID: 5696)
- NETSTAT.EXE (PID: 8184)
- NETSTAT.EXE (PID: 4668)
- Cudo Miner Core.exe (PID: 8116)
- NETSTAT.EXE (PID: 2356)
Uses NSLOOKUP.EXE to check DNS info
- cmd.exe (PID: 6180)
- cmd.exe (PID: 448)
- cmd.exe (PID: 2728)
- cmd.exe (PID: 3724)
- cmd.exe (PID: 3420)
- cmd.exe (PID: 4912)
- cmd.exe (PID: 7468)
- cmd.exe (PID: 8140)
- cmd.exe (PID: 3828)
- cmd.exe (PID: 6168)
The process hides Powershell's copyright startup banner
- Cudo Miner Core.exe (PID: 8156)
- Cudo Miner Core.exe (PID: 7220)
- Cudo Miner Core.exe (PID: 2212)
- Cudo Miner Core.exe (PID: 4468)
- Cudo Miner Core.exe (PID: 648)
- Cudo Miner Core.exe (PID: 7900)
- Cudo Miner Core.exe (PID: 3032)
- Cudo Miner Core.exe (PID: 7888)
- Cudo Miner Core.exe (PID: 8116)
Application launched itself
- Cudo Miner Desktop.exe (PID: 4144)
- Cudo Miner Desktop.exe (PID: 524)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 7664)
- cmd.exe (PID: 1792)
- cmd.exe (PID: 7516)
- cmd.exe (PID: 3848)
- cmd.exe (PID: 7956)
- cmd.exe (PID: 7844)
- cmd.exe (PID: 7800)
- cmd.exe (PID: 4280)
Process uses IPCONFIG to discover network configuration
- cmd.exe (PID: 8048)
- cmd.exe (PID: 1344)
- cmd.exe (PID: 3508)
- cmd.exe (PID: 2436)
- cmd.exe (PID: 3692)
- cmd.exe (PID: 4308)
- cmd.exe (PID: 7984)
- cmd.exe (PID: 776)
The process creates files with name similar to system file names
- CudoMiner.exe (PID: 3508)
The process bypasses the loading of PowerShell profile settings
- Cudo Miner Core.exe (PID: 8156)
Malware-specific behavior (creating "System.dll" in Temp)
- CudoMiner.exe (PID: 3508)
Starts POWERSHELL.EXE for commands execution
- Cudo Miner Core.exe (PID: 8156)
- Cudo Miner Core.exe (PID: 7220)
- Cudo Miner Core.exe (PID: 2212)
- Cudo Miner Core.exe (PID: 4468)
- Cudo Miner Core.exe (PID: 648)
- Cudo Miner Core.exe (PID: 7900)
- Cudo Miner Core.exe (PID: 3032)
- Cudo Miner Core.exe (PID: 7888)
- Cudo Miner Core.exe (PID: 8116)
INFO
Executable content was dropped or overwritten
- msedge.exe (PID: 6572)
- msedge.exe (PID: 6224)
- msedge.exe (PID: 4336)
The process uses the downloaded file
- msedge.exe (PID: 4144)
- msedge.exe (PID: 6224)
- cudo-defender-exclusion.exe (PID: 7904)
- cudo-defender-exclusion.exe (PID: 5200)
- powershell.exe (PID: 420)
- powershell.exe (PID: 6004)
- powershell.exe (PID: 2012)
- powershell.exe (PID: 8032)
- powershell.exe (PID: 876)
- powershell.exe (PID: 3736)
- cudo-defender-exclusion.exe (PID: 6492)
- cudo-defender-exclusion.exe (PID: 7260)
- CudoMiner.exe (PID: 3508)
- powershell.exe (PID: 3060)
- powershell.exe (PID: 5696)
- powershell.exe (PID: 396)
- powershell.exe (PID: 5920)
Reads the computer name
- identity_helper.exe (PID: 7776)
- CudoMiner.exe (PID: 5460)
- cudo-defender-exclusion.exe (PID: 7904)
- cudo-defender-exclusion.exe (PID: 5200)
- Updater.exe (PID: 2996)
- Cudo Miner.exe (PID: 5888)
- Cudo Miner.exe (PID: 5008)
- CudoMiner.exe (PID: 3508)
- Cudo Miner Core.exe (PID: 3864)
- Cudo Miner Core.exe (PID: 7900)
- Cudo Miner Core.exe (PID: 7888)
Reads Environment values
- identity_helper.exe (PID: 7776)
- Cudo Miner Core.exe (PID: 8156)
- Cudo Miner Desktop.exe (PID: 4144)
- Cudo Miner Desktop.exe (PID: 7696)
- Cudo Miner Core.exe (PID: 3864)
- Cudo Miner Core.exe (PID: 4468)
- Cudo Miner Core.exe (PID: 7888)
- Cudo Miner Core.exe (PID: 8116)
Application launched itself
- msedge.exe (PID: 6224)
Checks supported languages
- identity_helper.exe (PID: 7776)
- cudo-defender-exclusion.exe (PID: 7904)
- cudo-defender-exclusion.exe (PID: 5200)
- CudoMiner.exe (PID: 5460)
- Cudo Miner.exe (PID: 5888)
- Cudo Miner.exe (PID: 6496)
- Cudo Miner.exe (PID: 5008)
- chcp.com (PID: 1476)
- chcp.com (PID: 7288)
- Cudo Miner Core.exe (PID: 8156)
- Updater.exe (PID: 2996)
- CudoMiner.exe (PID: 3508)
- Cudo Miner Desktop.exe (PID: 4144)
- Cudo Miner Desktop.exe (PID: 7696)
- Cudo Miner.exe (PID: 7312)
- Cudo Miner Core.exe (PID: 3864)
- chcp.com (PID: 5916)
- cudo-defender-exclusion.exe (PID: 7260)
- Cudo Miner.exe (PID: 4336)
- Cudo Miner Core.exe (PID: 7220)
- Cudo Miner Desktop.exe (PID: 524)
- Cudo Miner Desktop.exe (PID: 4512)
- Cudo Miner.exe (PID: 4576)
- chcp.com (PID: 3656)
- chcp.com (PID: 936)
- Cudo Miner.exe (PID: 6960)
- Cudo Miner Core.exe (PID: 648)
- chcp.com (PID: 8116)
- Cudo Miner.exe (PID: 4520)
- Cudo Miner Core.exe (PID: 7900)
- Cudo Miner.exe (PID: 1576)
- Cudo Miner Core.exe (PID: 3032)
- chcp.com (PID: 5096)
The sample compiled with english language support
- CudoMiner.exe (PID: 5460)
- msedge.exe (PID: 4336)
- CudoMiner.exe (PID: 3508)
Checks proxy server information
- CudoMiner.exe (PID: 5460)
- cudo-defender-exclusion.exe (PID: 7904)
- Cudo Miner Desktop.exe (PID: 4144)
- CudoMiner.exe (PID: 3508)
- Cudo Miner Desktop.exe (PID: 524)
Reads the software policy settings
- CudoMiner.exe (PID: 5460)
- cudo-defender-exclusion.exe (PID: 7904)
- cudo-defender-exclusion.exe (PID: 5200)
Create files in a temporary directory
- CudoMiner.exe (PID: 5460)
- cudo-defender-exclusion.exe (PID: 7904)
- cudo-defender-exclusion.exe (PID: 5200)
- Cudo Miner Desktop.exe (PID: 4144)
- CudoMiner.exe (PID: 3508)
- cudo-defender-exclusion.exe (PID: 6492)
Reads the machine GUID from the registry
- CudoMiner.exe (PID: 5460)
- cudo-defender-exclusion.exe (PID: 7904)
- Cudo Miner.exe (PID: 5888)
- Updater.exe (PID: 2996)
- Cudo Miner.exe (PID: 5008)
- cudo-defender-exclusion.exe (PID: 5200)
- CudoMiner.exe (PID: 3508)
- Cudo Miner.exe (PID: 7312)
- cudo-defender-exclusion.exe (PID: 6492)
- cudo-defender-exclusion.exe (PID: 7260)
- Cudo Miner.exe (PID: 6488)
- Cudo Miner.exe (PID: 7772)
- Cudo Miner.exe (PID: 4576)
- Cudo Miner.exe (PID: 8020)
- Cudo Miner.exe (PID: 2092)
Creates files or folders in the user directory
- CudoMiner.exe (PID: 5460)
- cudo-defender-exclusion.exe (PID: 7904)
- Cudo Miner Desktop.exe (PID: 4144)
- Cudo Miner Desktop.exe (PID: 7696)
- Cudo Miner Desktop.exe (PID: 3488)
Creates files in the program directory
- CudoMiner.exe (PID: 5460)
- Updater.exe (PID: 2996)
- Cudo Miner Core.exe (PID: 8156)
- CudoMiner.exe (PID: 3508)
Checks if a key exists in the options dictionary (POWERSHELL)
- cudo-defender-exclusion.exe (PID: 7904)
- cudo-defender-exclusion.exe (PID: 5200)
- powershell.exe (PID: 3736)
- cudo-defender-exclusion.exe (PID: 6492)
- cudo-defender-exclusion.exe (PID: 7260)
Changes the display of characters in the console
- cmd.exe (PID: 7236)
- cmd.exe (PID: 424)
- cmd.exe (PID: 7132)
- cmd.exe (PID: 5308)
- cmd.exe (PID: 2548)
- cmd.exe (PID: 8060)
- cmd.exe (PID: 5876)
- cmd.exe (PID: 7320)
- cmd.exe (PID: 7984)
- cmd.exe (PID: 6860)
- cmd.exe (PID: 7332)
- cmd.exe (PID: 2976)
- cmd.exe (PID: 7444)
- cmd.exe (PID: 4872)
- cmd.exe (PID: 5936)
- cmd.exe (PID: 5964)
- cmd.exe (PID: 3808)
- cmd.exe (PID: 5200)
- cmd.exe (PID: 3896)
- cmd.exe (PID: 1380)
Reads product name
- Cudo Miner Core.exe (PID: 8156)
- Cudo Miner Desktop.exe (PID: 4144)
- Cudo Miner Desktop.exe (PID: 7696)
- Cudo Miner Core.exe (PID: 3864)
- Cudo Miner Core.exe (PID: 4468)
- Cudo Miner Core.exe (PID: 7888)
- Cudo Miner Core.exe (PID: 8116)
Process checks computer location settings
- Cudo Miner Core.exe (PID: 8156)
- CudoMiner.exe (PID: 5460)
- Cudo Miner Core.exe (PID: 3864)
- Cudo Miner Desktop.exe (PID: 524)
- Cudo Miner Core.exe (PID: 7900)
- Cudo Miner Core.exe (PID: 3032)
Prints a route via ROUTE.EXE
- ROUTE.EXE (PID: 5964)
- ROUTE.EXE (PID: 4528)
- ROUTE.EXE (PID: 7804)
- ROUTE.EXE (PID: 7764)
- ROUTE.EXE (PID: 7384)
- ROUTE.EXE (PID: 3552)
- ROUTE.EXE (PID: 3808)
- ROUTE.EXE (PID: 5876)
- ROUTE.EXE (PID: 3864)
- ROUTE.EXE (PID: 1200)
- ROUTE.EXE (PID: 1328)
- ROUTE.EXE (PID: 7828)
- ROUTE.EXE (PID: 2928)
- ROUTE.EXE (PID: 8024)
- ROUTE.EXE (PID: 6180)
- ROUTE.EXE (PID: 7608)
- ROUTE.EXE (PID: 6216)
- ROUTE.EXE (PID: 3640)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2012)
- powershell.exe (PID: 6004)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
524
Monitored processes
389
Malicious processes
7
Suspicious processes
14
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | netstat -r | C:\Windows\System32\NETSTAT.EXE | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: TCP/IP Netstat Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 188 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --no-appcompat-clear --gpu-preferences=WAAAAAAAAADoAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=4972 --field-trial-handle=2384,i,18258969845595672161,11411201726805362865,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 236 | netstat -r | C:\Windows\System32\NETSTAT.EXE | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: TCP/IP Netstat Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 308 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 396 | C:\WINDOWS\system32\cmd.exe /c "C:\WINDOWS\system32\route.exe" print | C:\Windows\System32\cmd.exe | — | NETSTAT.EXE | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 396 | powershell.exe -NoLogo -InputFormat Text -NoExit -ExecutionPolicy Unrestricted -Command - | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Cudo Miner Core.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 420 | powershell.exe -NoLogo -InputFormat Text -NoExit -ExecutionPolicy Unrestricted -Command - | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Cudo Miner Core.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 420 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 424 | C:\WINDOWS\system32\cmd.exe /d /s /c "chcp" | C:\Windows\System32\cmd.exe | — | Cudo Miner Core.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 432 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Cudo Miner Core.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
160 144
Read events
160 072
Write events
51
Delete events
21
Modification events
| (PID) Process: | (6224) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6224) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6224) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6224) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6224) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 5DE4019F4E8A2F00 | |||
| (PID) Process: | (6224) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: BA030A9F4E8A2F00 | |||
| (PID) Process: | (6224) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328350 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {3F6DE932-7E7D-46EA-A0EB-0D599F159ED4} | |||
| (PID) Process: | (6224) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: BB92289F4E8A2F00 | |||
| (PID) Process: | (6224) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | MicrosoftEdgeAutoLaunch_29EBC4579851B72EE312C449CF839B1A |
Value: "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window --win-session-start | |||
| (PID) Process: | (6224) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\Clients\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\Commands\on-logon-autolaunch |
| Operation: | write | Name: | Enabled |
Value: 0 | |||
Executable files
58
Suspicious files
618
Text files
203
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6224 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF135372.TMP | — | |
MD5:— | SHA256:— | |||
| 6224 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6224 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF135372.TMP | — | |
MD5:— | SHA256:— | |||
| 6224 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6224 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF135382.TMP | — | |
MD5:— | SHA256:— | |||
| 6224 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6224 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF135382.TMP | — | |
MD5:— | SHA256:— | |||
| 6224 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6224 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF135382.TMP | — | |
MD5:— | SHA256:— | |||
| 6224 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
60
TCP/UDP connections
100
DNS requests
89
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
736 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
736 | svchost.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6976 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5460 | CudoMiner.exe | GET | 200 | 142.250.185.195:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5460 | CudoMiner.exe | GET | 200 | 142.250.185.195:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
736 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
736 | svchost.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 2.16.110.170:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6224 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
download.cudo.org |
| malicious |
business.bing.com |
| whitelisted |