| URL: | http://0i.pm |
| Full analysis: | https://app.any.run/tasks/cdaa2a6a-392c-458d-906b-a3fbcaaad53e |
| Verdict: | Malicious activity |
| Analysis date: | August 07, 2023, 02:32:42 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 10793923591CA07EE5073B8D30D3DCAD |
| SHA1: | 78970B6EBD99349CC43AA31E7CF1FFBD681F72EB |
| SHA256: | 841145E7A2D622805B570D24D36D42E24790704F7F94C45D96FB2F9B413B5273 |
| SSDEEP: | 3:N1KlI:ClI |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Creates files or folders in the user directory
- MsSpellCheckingFacility.exe (PID: 3116)
Application launched itself
- iexplore.exe (PID: 2880)
The process checks LSA protection
- MsSpellCheckingFacility.exe (PID: 3116)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
39
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 980 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2880 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2880 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://0i.pm" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3116 | "C:\Windows\System32\MsSpellCheckingFacility.exe" -Embedding | C:\Windows\System32\MsSpellCheckingFacility.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Spell Checking Facility Exit code: 0 Version: 6.3.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
5 369
Read events
5 302
Write events
67
Delete events
0
Modification events
| (PID) Process: | (2880) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2880) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2880) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2880) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2880) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2880) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2880) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2880) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2880) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2880) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
11
Text files
33
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
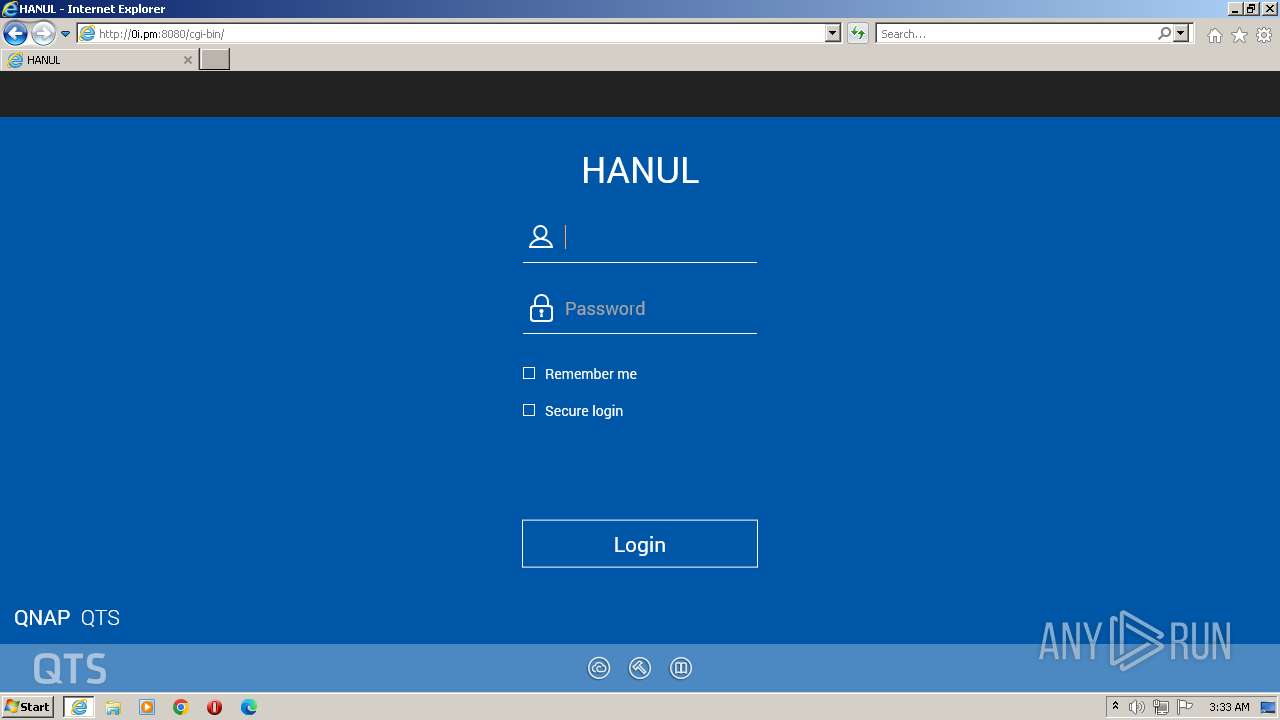
| 980 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\login[1].htm | html | |
MD5:E972D49EE9666FDC2AF33BE48F3BC6CC | SHA256:8FD5B038D7F0B996BFA018CDB0A42D35405C7B8857DB7CCB1E2DC0848AE667EA | |||
| 980 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\redirect[1].htm | html | |
MD5:02DC8BC49EB5F6F8CFF93D765CBF24FC | SHA256:C9ECE3BF47416C098E5580C3322D73821075A4F1DB27E41B24F174C6FE3568B5 | |||
| 980 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\qts-font[1].css | text | |
MD5:F89025143DB4CEDCCB60DCD90E5F5CF5 | SHA256:6065E9DAAD713F1F9276B715E81E70F6D6B3467C8B67DD8363CE9257ACEFC7A4 | |||
| 980 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\login-max-height-768[1].css | text | |
MD5:BC0D968A1E1EF8AAF18B7416741CB4DA | SHA256:DCD1C929E7186CCBCD7CE48440A1C9845ED97CB134246B30238CC16ABA1E533F | |||
| 980 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\moment.min[1].js | text | |
MD5:5A9AC145C76D112746FC21AE57A36472 | SHA256:380C5886471FBE1A8224252BABB3F16A0EEBABE4A4F3AE8CB59E8C08C4769BDA | |||
| 980 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\language[1].js | text | |
MD5:99D2D514617DC71D0B69F687F0496AFC | SHA256:FF7F7A54F40830977C7BE4AC6DBA80488ABB02E149BBB41D0CFE4A7CF3A11D70 | |||
| 980 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\sso-form[1].js | text | |
MD5:A1C0A1F16B9CB89293A6F8645D1B5FD3 | SHA256:3DF8416D821AE5CE3279B6B3F1822138FF59BBC1F2B65B17BE11CF1C8BCB4EAE | |||
| 980 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\promise[1].js | text | |
MD5:DD2EDBF51407B10EFCA01D4AAD25712E | SHA256:E02DD03DCC88697EB710BD39A17D9F6E4843B5EE4B71B9E5512626F1EB2DA700 | |||
| 980 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\qos-core-login[1].js | text | |
MD5:307525FC16A7C8AAD7A55534EEE8F432 | SHA256:634252AF456F84C56FF8E66D7F056D77D17FA1F245B42E47165F7F42BD8D7D07 | |||
| 980 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\watermark[1].css | text | |
MD5:99E5719B3450976B81C8F30768315EA2 | SHA256:133FD6ED862CB8961C11005ECAAF9240BB52BA69ECBCC1C625B90A11B0EFDBF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
37
TCP/UDP connections
29
DNS requests
10
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
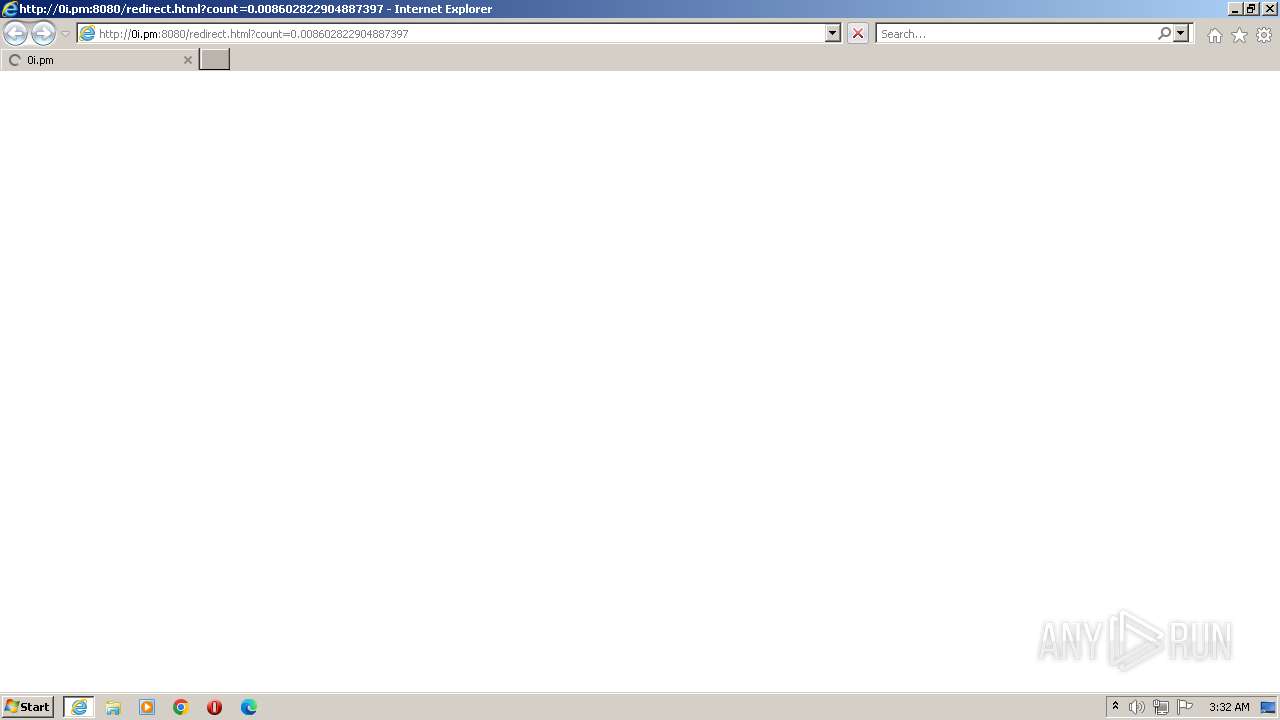
980 | iexplore.exe | GET | 200 | 125.191.5.20:8080 | http://0i.pm:8080/redirect.html?count=0.008602822904887397 | KR | html | 548 b | malicious |
980 | iexplore.exe | GET | 200 | 125.191.5.20:8080 | http://0i.pm:8080/ | KR | html | 360 b | malicious |
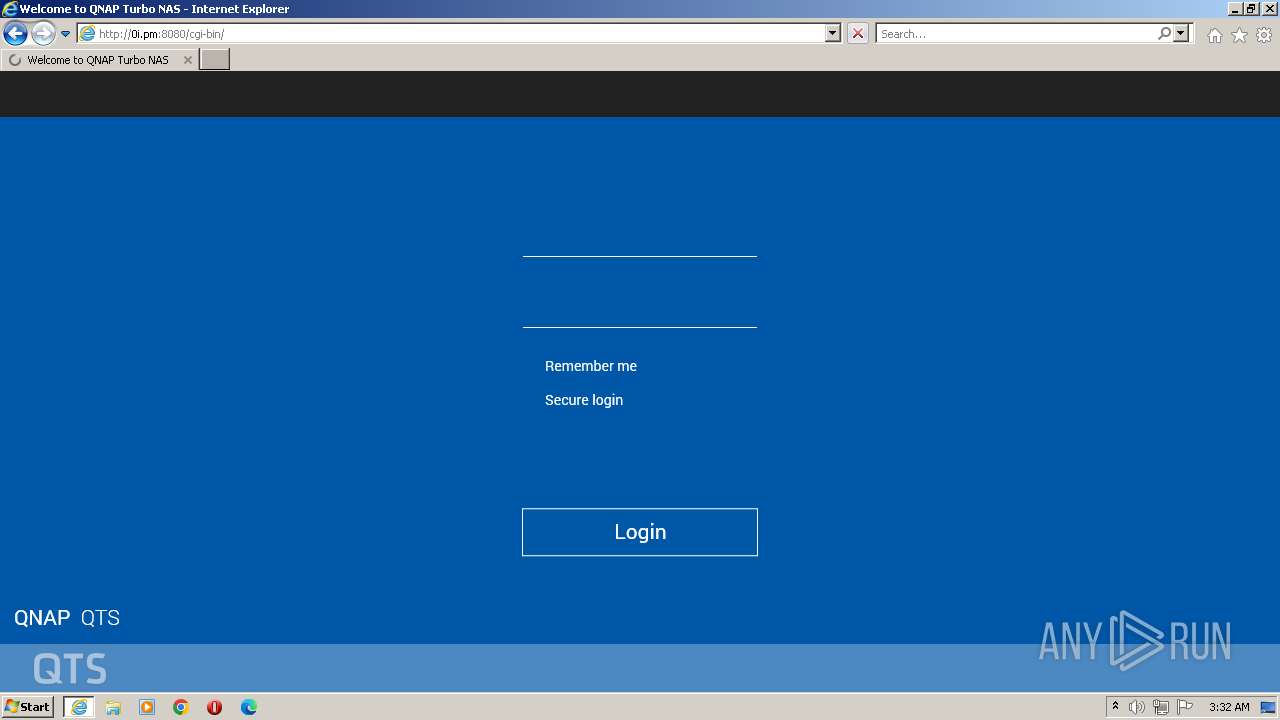
980 | iexplore.exe | GET | 200 | 125.191.5.20:8080 | http://0i.pm:8080/cgi-bin/loginTheme/theme1/login.css?r=form&1606105644 | KR | text | 4.47 Kb | malicious |
980 | iexplore.exe | GET | 302 | 125.191.5.20:8080 | http://0i.pm:8080/cgi-bin/QTS.cgi?count=927909 | KR | compressed | 548 b | malicious |
980 | iexplore.exe | GET | 200 | 125.191.5.20:8080 | http://0i.pm:8080/cgi-bin/css/watermark.css?r=form&1606105644 | KR | text | 258 b | malicious |
980 | iexplore.exe | GET | 200 | 125.191.5.20:8080 | http://0i.pm:8080/libs/monent/moment.min.js?1606105644 | KR | text | 13.6 Kb | malicious |
980 | iexplore.exe | GET | 200 | 125.191.5.20:8080 | http://0i.pm:8080/cgi-bin/language.cgi?1606105644 | KR | text | 4.10 Kb | malicious |
980 | iexplore.exe | GET | 200 | 125.191.5.20:8080 | http://0i.pm:8080/cgi-bin/images/desktop/bg/watermark.svg?1606105644 | KR | image | 3.27 Kb | malicious |
980 | iexplore.exe | GET | 200 | 125.191.5.20:8080 | http://0i.pm:8080/cgi-bin/loginTheme/theme1/login.js?1606105644 | KR | text | 7.67 Kb | malicious |
980 | iexplore.exe | GET | 200 | 125.191.5.20:8080 | http://0i.pm:8080/v3_menu/fonts/Roboto/Roboto-Light.ttf | KR | binary | 136 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
980 | iexplore.exe | 125.191.5.20:80 | 0i.pm | LG POWERCOMM | KR | malicious |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2640 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
980 | iexplore.exe | 125.191.5.20:8080 | 0i.pm | LG POWERCOMM | KR | malicious |
2880 | iexplore.exe | 2.23.209.187:443 | www.bing.com | Akamai International B.V. | GB | suspicious |
2880 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2880 | iexplore.exe | 125.191.5.20:8080 | 0i.pm | LG POWERCOMM | KR | malicious |
2880 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
0i.pm |
| malicious |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
980 | iexplore.exe | Potential Corporate Privacy Violation | ET POLICY Http Client Body contains pwd= in cleartext |