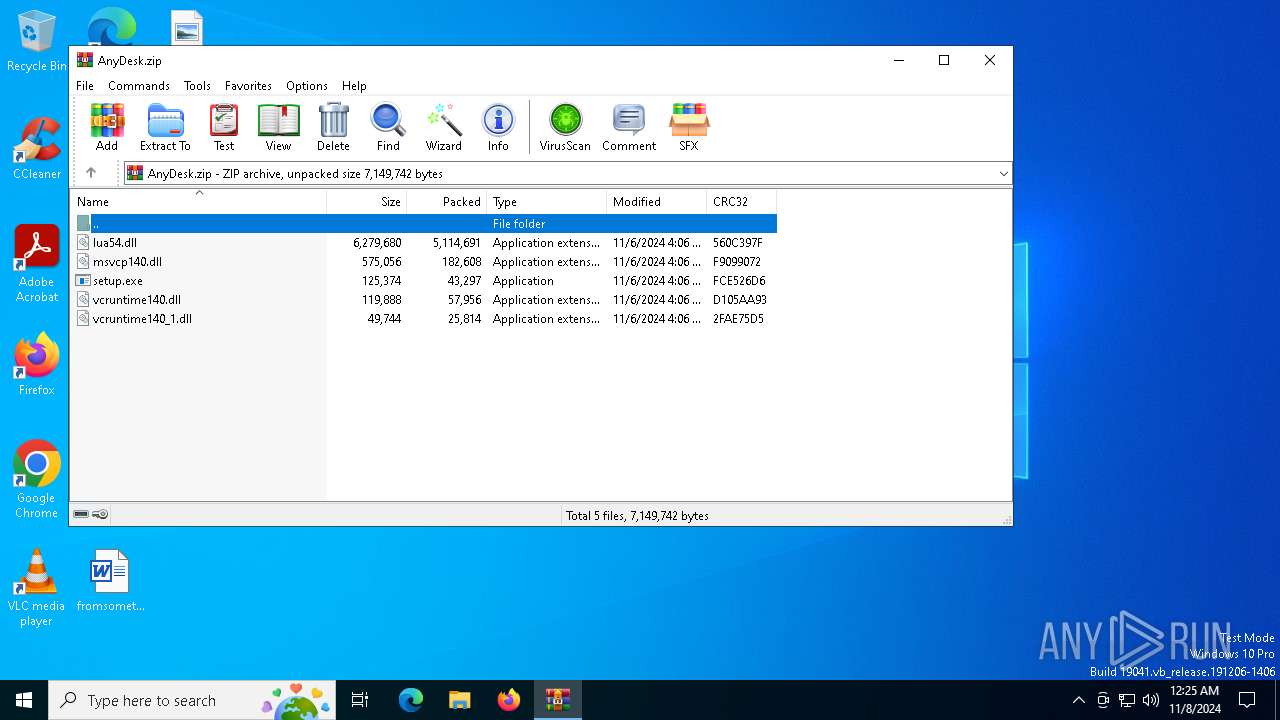
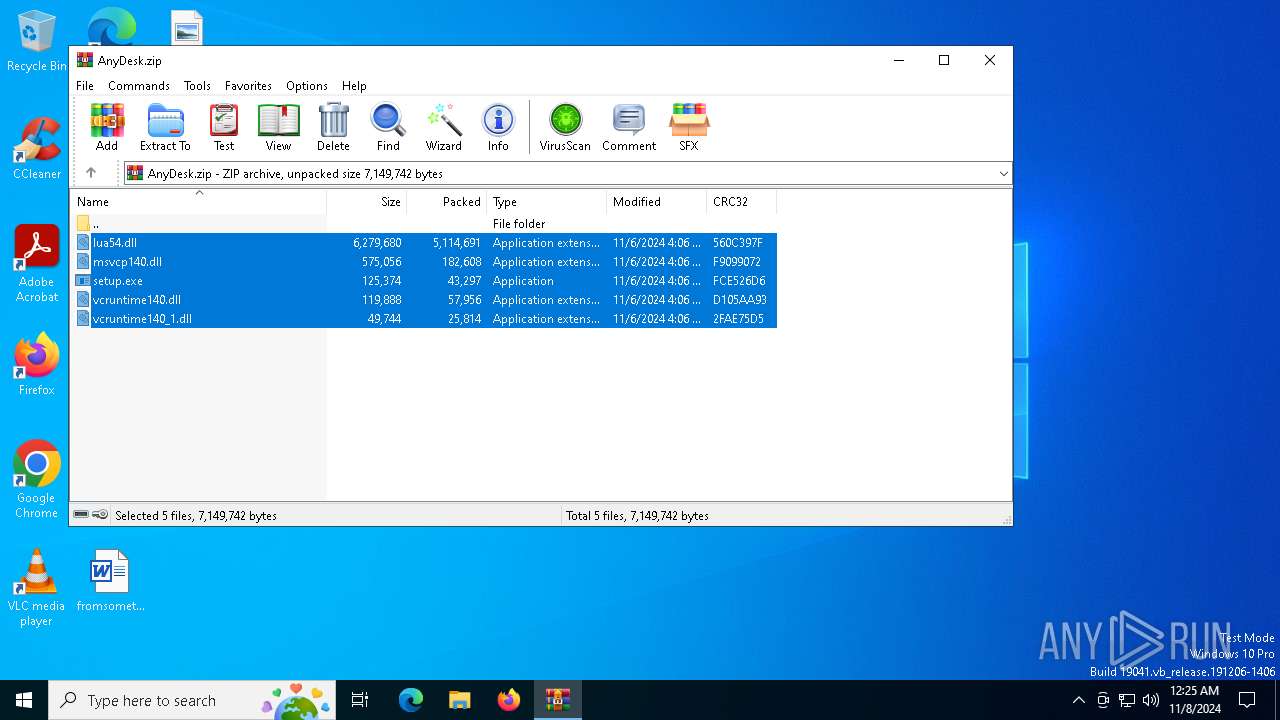
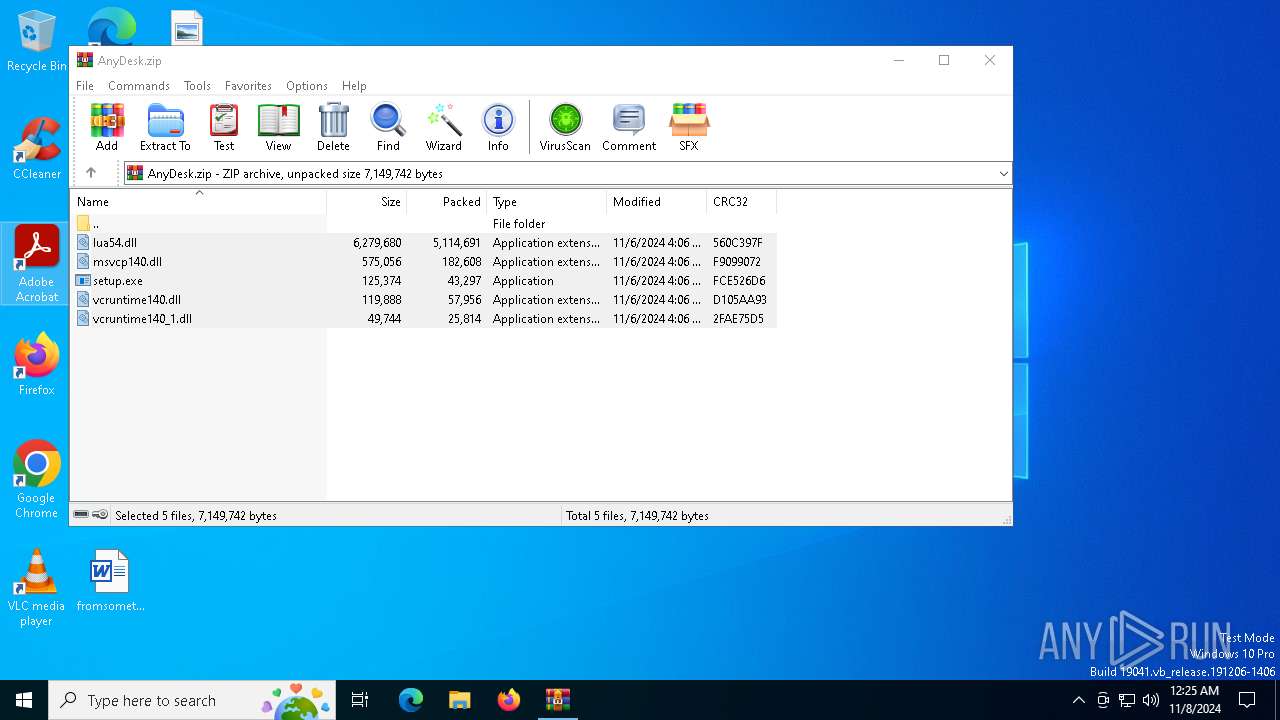
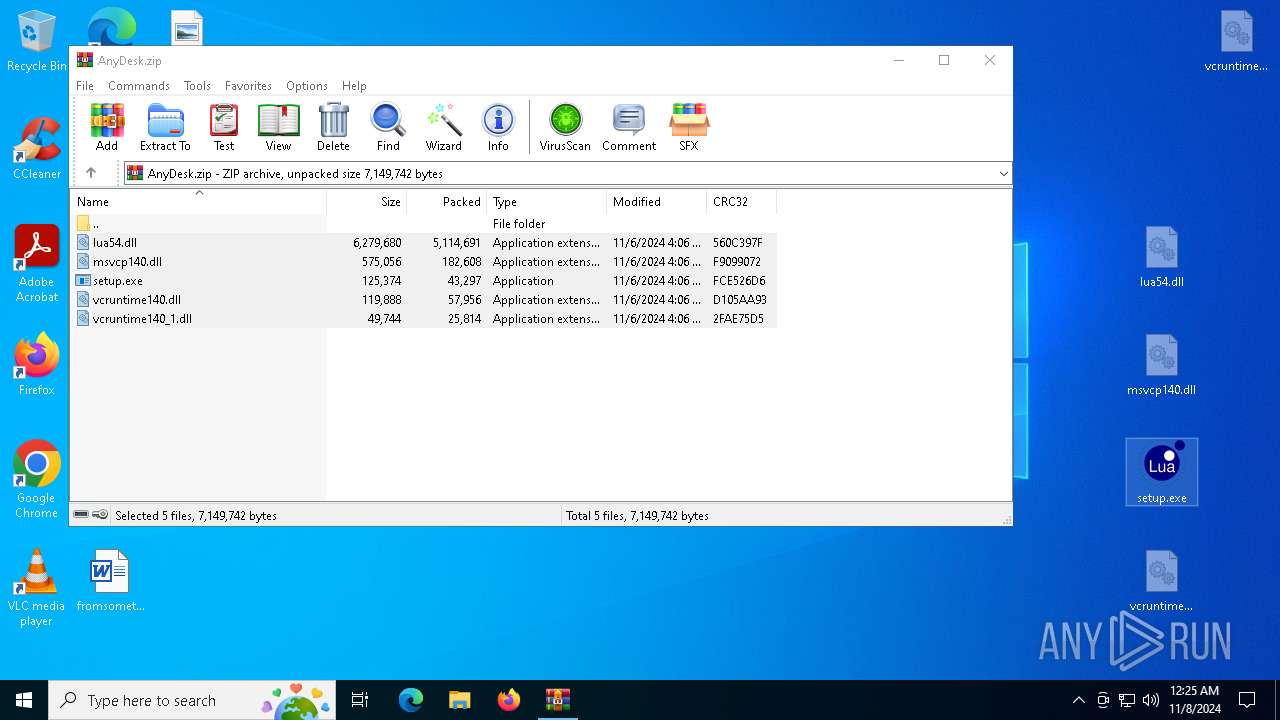
| File name: | AnyDesk.zip |
| Full analysis: | https://app.any.run/tasks/ac55de1a-89ab-4210-bb96-20fcfb242fa5 |
| Verdict: | Malicious activity |
| Analysis date: | November 08, 2024, 00:25:05 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | FC4D778595C9F2019BB7CF90D8D982F4 |
| SHA1: | 9FB6E7D392B0586E941FABDA5D30BD84ACBF2AD4 |
| SHA256: | 83F782D54F4C81DF56F4B50C551CA21070F70E421164CE503B97BDD4D0C2EFF5 |
| SSDEEP: | 98304:hoTXRJnmjv7FNYQcQXa7OlS/98sSmD3Wl6WNgustmkAUfPppAJFnYgTPsnegfWeU:xdWAj8v/cu2 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 300)
The process drops C-runtime libraries
- WinRAR.exe (PID: 300)
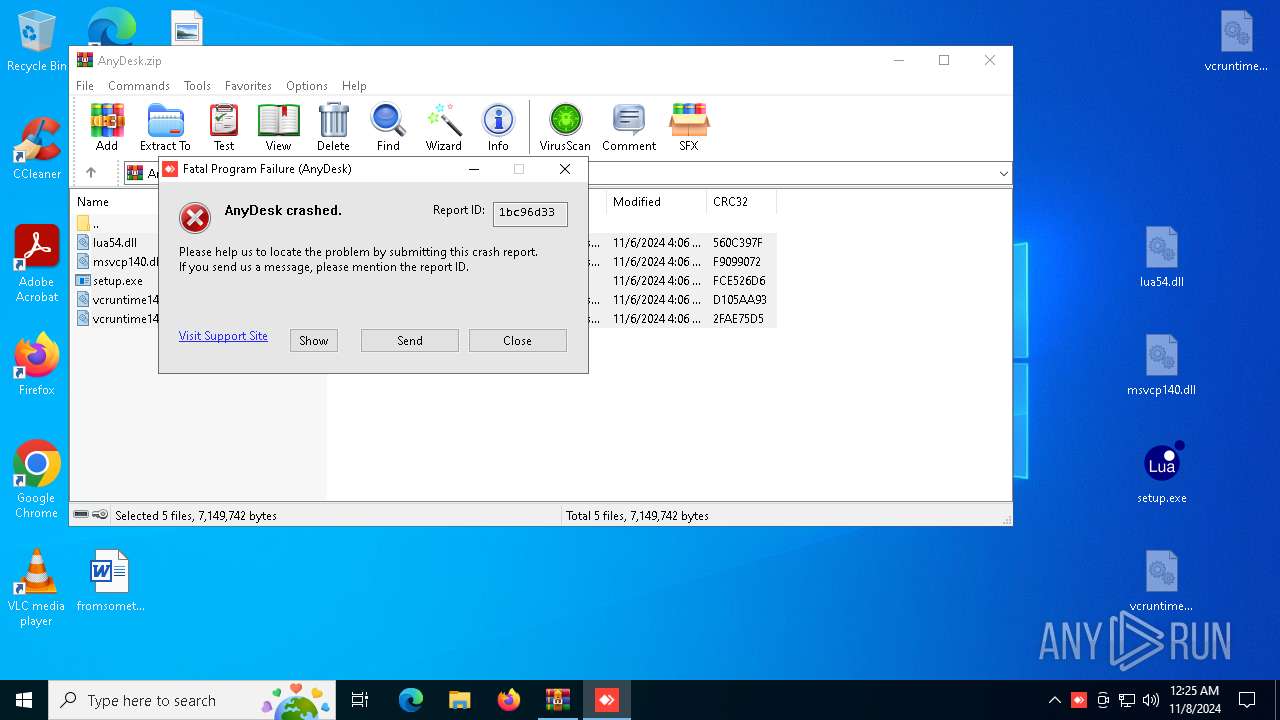
ANYDESK has been found
- setup.exe (PID: 3964)
- DeskAny.exe (PID: 6180)
Executable content was dropped or overwritten
- setup.exe (PID: 3964)
Found AnyDesk certificate that may have been compromised
- DeskAny.exe (PID: 6180)
- DeskAny.exe (PID: 3076)
- DeskAny.exe (PID: 6168)
- DeskAny.exe (PID: 4228)
Application launched itself
- DeskAny.exe (PID: 6180)
INFO
Creates files or folders in the user directory
- setup.exe (PID: 3964)
- DeskAny.exe (PID: 6180)
Manual execution by a user
- setup.exe (PID: 3964)
The process uses the downloaded file
- WinRAR.exe (PID: 300)
- DeskAny.exe (PID: 6180)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 300)
Checks supported languages
- DeskAny.exe (PID: 6168)
- DeskAny.exe (PID: 6180)
- setup.exe (PID: 3964)
- DeskAny.exe (PID: 3076)
- DeskAny.exe (PID: 4228)
Reads the machine GUID from the registry
- DeskAny.exe (PID: 3076)
- DeskAny.exe (PID: 6168)
Reads the computer name
- DeskAny.exe (PID: 6168)
- DeskAny.exe (PID: 3076)
- DeskAny.exe (PID: 6180)
- DeskAny.exe (PID: 4228)
Checks proxy server information
- DeskAny.exe (PID: 6168)
Process checks whether UAC notifications are on
- DeskAny.exe (PID: 6180)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:11:06 08:06:48 |
| ZipCRC: | 0x560c397f |
| ZipCompressedSize: | 5114691 |
| ZipUncompressedSize: | 6279680 |
| ZipFileName: | lua54.dll |
Total processes
143
Monitored processes
10
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\AnyDesk.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1200 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | UCPDMgr.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3076 | "C:\Users\admin\AppData\Local\CiscoSoftware\DeskAny.exe" --local-service | C:\Users\admin\AppData\Local\CiscoSoftware\DeskAny.exe | DeskAny.exe | ||||||||||||
User: admin Company: AnyDesk Software GmbH Integrity Level: MEDIUM Description: AnyDesk Exit code: 0 Version: 7.1.16 Modules
| |||||||||||||||
| 3964 | "C:\Users\admin\Desktop\setup.exe" | C:\Users\admin\Desktop\setup.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4228 | "C:\Users\admin\AppData\Local\CiscoSoftware\DeskAny.exe" --crash-handler | C:\Users\admin\AppData\Local\CiscoSoftware\DeskAny.exe | — | DeskAny.exe | |||||||||||
User: admin Company: AnyDesk Software GmbH Integrity Level: MEDIUM Description: AnyDesk Exit code: 0 Version: 7.1.16 Modules
| |||||||||||||||
| 6168 | "C:\Users\admin\AppData\Local\CiscoSoftware\DeskAny.exe" --local-control | C:\Users\admin\AppData\Local\CiscoSoftware\DeskAny.exe | — | DeskAny.exe | |||||||||||
User: admin Company: AnyDesk Software GmbH Integrity Level: MEDIUM Description: AnyDesk Exit code: 0 Version: 7.1.16 Modules
| |||||||||||||||
| 6180 | C:\Users\admin\AppData\Local\CiscoSoftware\DeskAny.exe | — | setup.exe | ||||||||||||
User: admin Company: AnyDesk Software GmbH Integrity Level: MEDIUM Description: AnyDesk Exit code: 9002 Version: 7.1.16 Modules
| |||||||||||||||
| 6284 | "C:\WINDOWS\system32\UCPDMgr.exe" | C:\Windows\System32\UCPDMgr.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: User Choice Protection Manager Exit code: 0 Version: 1.0.0.414301 Modules
| |||||||||||||||
| 6308 | "C:\WINDOWS\system32\UCPDMgr.exe" | C:\Windows\System32\UCPDMgr.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: User Choice Protection Manager Exit code: 0 Version: 1.0.0.414301 Modules
| |||||||||||||||
| 6380 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | UCPDMgr.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 399
Read events
2 393
Write events
6
Delete events
0
Modification events
| (PID) Process: | (300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\AnyDesk.zip | |||
| (PID) Process: | (300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
6
Suspicious files
2
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa300.33013\vcruntime140_1.dll | executable | |
MD5:7E986E7469D9AB3B1138353418DA1793 | SHA256:0E560532E721B6938DAFE4055EEDD0251BA5EB5994CD96937CEBBCF16A7DDAE5 | |||
| 6180 | DeskAny.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\JHID1HIW20CT9EN22O7J.temp | binary | |
MD5:F16766CCC50F1CE7D9CCEE7EBE51EF66 | SHA256:F61D3BDD710A6BF96BA0AD981CC7CCD36764C6DFF3AF8D40792ACD04EE76F085 | |||
| 300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa300.33013\vcruntime140.dll | executable | |
MD5:C22AB531881B21277BA168E6F311D225 | SHA256:642AE52687A7A6BFB03D0B20DC7E07F4B11CECA634F7EB7BA184D6711AB51A51 | |||
| 6180 | DeskAny.exe | C:\Users\admin\AppData\Roaming\AnyDesk\user.conf | text | |
MD5:5059D0251F3292C45A54E0AB40CCA733 | SHA256:88D22B3A6A8BCB3AB03CFAC5EEF7FDF1CF4C99E17576D05997D2F0DFC96B8189 | |||
| 300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa300.33013\setup.exe | executable | |
MD5:8EB22CBBAACB740BDDF7CE1FF8EEA868 | SHA256:C1757C37D186B1B9868E0B92025D073EF0347ADF2059163D9DFD26EC94258023 | |||
| 3076 | DeskAny.exe | C:\Users\admin\AppData\Roaming\AnyDesk\system.conf | text | |
MD5:0C04AD1083DC5C7C45E3EE2CD344AE38 | SHA256:6452273C017DB7CBE0FFC5B109BBF3F8D3282FB91BFA3C5EABC4FB8F1FC98CB0 | |||
| 300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa300.33013\lua54.dll | executable | |
MD5:71BC07BD6057F445F10422558DC285A2 | SHA256:0685817FD3C777AE291DB1109C14124CE583E97B2AC2F5FF3073CFBFF07D55EB | |||
| 3964 | setup.exe | C:\Users\admin\AppData\Local\CiscoSoftware\DeskAny.exe | executable | |
MD5:17D3CC33A125D39097B58D5F653407D5 | SHA256:BB99D82C785B174928E89E5895121C562B14888D03CA61FF93C0050AF87B07FC | |||
| 6180 | DeskAny.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\75fdacd8330bac18.customDestinations-ms | binary | |
MD5:F16766CCC50F1CE7D9CCEE7EBE51EF66 | SHA256:F61D3BDD710A6BF96BA0AD981CC7CCD36764C6DFF3AF8D40792ACD04EE76F085 | |||
| 6180 | DeskAny.exe | C:\Users\admin\AppData\Roaming\AnyDesk\ad.trace | text | |
MD5:307D5883669CE4A6263E94CDDF78230C | SHA256:40208AFF8DA05689CBA0AC3FE1DE67105F7E8143A2C27E3D9CE760D71FFEA86F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
21
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6944 | svchost.exe | GET | 200 | 23.44.129.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1584 | RUXIMICS.exe | GET | 200 | 23.44.129.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.44.129.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.200.197.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1584 | RUXIMICS.exe | GET | 200 | 23.200.197.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7156 | SIHClient.exe | GET | 200 | 23.200.197.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7156 | SIHClient.exe | GET | 200 | 23.200.197.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.200.197.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 52.183.220.149:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6944 | svchost.exe | 52.183.220.149:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6944 | svchost.exe | 23.44.129.137:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.44.129.137:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
1584 | RUXIMICS.exe | 23.44.129.137:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.200.197.152:80 | www.microsoft.com | AKAMAI-AS | US | whitelisted |
1584 | RUXIMICS.exe | 23.200.197.152:80 | www.microsoft.com | AKAMAI-AS | US | whitelisted |
6944 | svchost.exe | 23.200.197.152:80 | www.microsoft.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
boot.net.anydesk.com |
| whitelisted |
relay-52515283.net.anydesk.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |